※大學學術追求卓越發展延續計畫執行報告格式
Explanation for the Form of the Annual/Midterm/Final Report “Program for Promoting Academic Excellence of Universities((((Phase II)))” )
※ The Annual/Midterm/Final Report contains the following sections:
I COVER
II FORM1 BASIC INFORMATION OF THE PROGRAM
III FORM2 LIST OF WORKS,EXPENDITURES,MANPOWER, AND MATCHING SUPPORTS FROM THE PARTICIPATING INSTITUTES(REALITY).
IV FORM3 STATISTICS ON RESEARCH OUTCOMES OF THIS PROGRAM
V FORM4 EXECUTIVE SUMMARY ON RESEARCH OUTCOMES OF THIS PROGRAM VI APPENDIX I MINUTES FROM PROGRAMDISCUSSION MEETINGS
VII APPENDIX II
1. PUBLICATION LIST(CONFERENCES,JOURNALS,BOOKS,BOOK CHAPTERS,etc.) 2. PATENT LIST
3. INVENTION LIST
4. LIST OF WORKSHOPS/CONFERENCES HOSTED BY THE PROGRAM 5. LIST OF PERSONAL ACHIEVEMENTS OF THE PIS
6. LIST OF TECHNOLOGY TRANSFERS 7. LIST OF TECHNOLOGY SERVICES
VIII APPENDIX III LIST OF PUBLICATIONS IN “TOP”JOURNALS AND CONFERENCES
IX APPENDIX IV SLIDES ON SCIENCE AND TECHNOLOGY BREAKTHROUGHS (TWO SLIDES FOR EACH BREAKTHROUGH)
X APPENDIX V SELF-ASSESSMENT (Add extra lines or columns if needed.)
2
I.COVER
Program for Promoting Academic Excellence of Universities(((Phase II)( )))
Final Report 下一世代資訊通訊網路尖端技術與應用 下一世代資訊通訊網路尖端技術與應用下一世代資訊通訊網路尖端技術與應用 下一世代資訊通訊網路尖端技術與應用((((二二二二)))) 子計畫五 子計畫五 子計畫五 子計畫五::::網路安全網路安全網路安全網路安全
Advanced Technologies and Applications for Next Generation Information Communication Networks (II)
Sub Project 5: Network Security
NSC96-2752-E-009-006-PAE
Overall Duration: April 2004 - June 2008 Report Duration: April 2007 - May 2008
National Tsing Hua University National Chiao Tung University
II.(FORM1) BASIC INFORMATION OF THE PROGRAM
Program Title:Advanced Technologies and Applications for Next Generation Information Communication Networks (II)
Sub Project 5:Network Security
下一世代資訊通訊網路尖端技術與應用(二) 子計畫五:網路安全
Serial No.: NSC96-2752-E-009-006-PAE Affiliation
National Tsing Hua University National Chiao Tung University
Name Wen-Hsiang Tsai 蔡文祥 Name Yaw-Chung Chen 陳耀宗
Tel: (03) 5731206 Tel: (03)573-1864 Fax: (03) 5731205 Fax: (03)572-7842 P ri n ci p al I n v es ti g at o r E-mail whtsai@cs.nctu.edu.tw P ro g ra m C o o rd in at o r E-mail ycchen@cs.nctu.edu.tw Expenditures1 (in NT$1,000) Manpower2:Full time/Part time(Person-Months)
Projected Actual Projected Actual
FY 2004 5008.300 5149.078 27/310 24/313
FY 2005 6180.000 6057.439 21/403 24/400
FY 2006 6129.000 5430.260 24/410 36/398
FY 2007 6321.000 5946.193 24/400 24/408
Overall 23638.300 22582.970 96/1523 108/1511
Notes: 1,2 Please explain large differences between projected and actual figures.
6
III.(FORM 2)LIST OF WORKS,EXPENDITURES,MANPOWER, AND MATCHING SUPPORTS FROM THE PARTICIPATING INSTITUTES((((REALITY)))).
Serial No.:
NSC93-2752-E-009-006-PAE NSC94-2752-E-009-006-PAE NSC95-2752-E-009-015-PAE NSC96-2752-E-009-006-PAE
Program Title:Sub Project 5:Network Security
子計畫五:網路安全
Expenditures (in NT$1,000) Manpower (person-month) Research Item
(Include sub projects)
Major tasks and objectives
Salary Seminar/ Conferenc e-related expenses Project- related expenses Cost for Hardware & Software Total Principal Investigat ors Consultants Research/ Teaching Personnel Supporting Staff Total
Matching Supports from the Participating Institutes (in English & Chinese)
1.Active Information Hiding Techniques 4,212.665 26.970 546.255 696.204 5,482.094 72 - 298 0 370 2.Security Knowledge Warehousing Technology 2,666.712 729.811 369.756 732.196 4,498.475 144 - 243 36 423 3.Advanced Research on Pluggable Secure
Framework for Middleware
4,318.573 428.541 265.495 859.342 5,871.951 144 - 340 36 520 Sub-Project 5:
Network Security
4.High Performance P2P Security Gateway 2,807.426 420.643 483.834 227.293 3,939.196 72 - 210 24 306
IV.(FORM 3)STATISTICS ON RESEARCH OUTCOME OF THIS PROGRAM
LISTING TOTAL DOMESTIC INTERNATIONAL SIGNIFICANT1 CITATIONS2 TECHNOLOGYTRANSFER
JOURNALS 52 7 45 CONFERENCES 58 10 48 PUBLISHED ARTICLES TECHNOLOGY REPORTS PENDING 2 2 - PATENTS GRANTED 1 1 -
COPYRIGHTED INVENTIONS ITEM
ITEM 5 5
WORKSHOPS/CONFERENCES3
PARTICIPANTS 340 340
HOURS
TRAINING COURSES
(WORKSHOPS/CONFERENCES) PARTICIPANTS
HONORS/AWARDS4 8 8
KEYNOTES GIVEN BY PIS
PERSONAL ACHIEVEMENTS
EDITOR FOR JOURNALS 1 1
ITEM LICENSING FEE TECHNOLOGY TRANSFERS ROYALTY
INDUSTRY STANDARDS5 ITEM
ITEM - - -
TECHNOLOGICAL SERVICES6
SERVICE FEE - - -
1 Indicate the number of items that are significant. The criterion for “significant” is defined by the PIs of the program. For example, it may refer to Top journals (i.e., those with impact factors in the upper 15%) in the area of research, or conferences that are very selective in accepting submitted papers (i.e., at an acceptance rate no greater than 30%). Please specify the criteria in Appendix IV.
2 Indicate the number of citations. The criterion for “citations” refers to citations by other research teams, i.e., exclude self-citations. 3
8
V.(FORM4) EXECUTIVE SUMMARY ON RESEARCH OUTCOMES OF THIS PROGRAM
(Please state the followings concisely and clearly)
1. General Description of the Program: Including Objectives of the Program
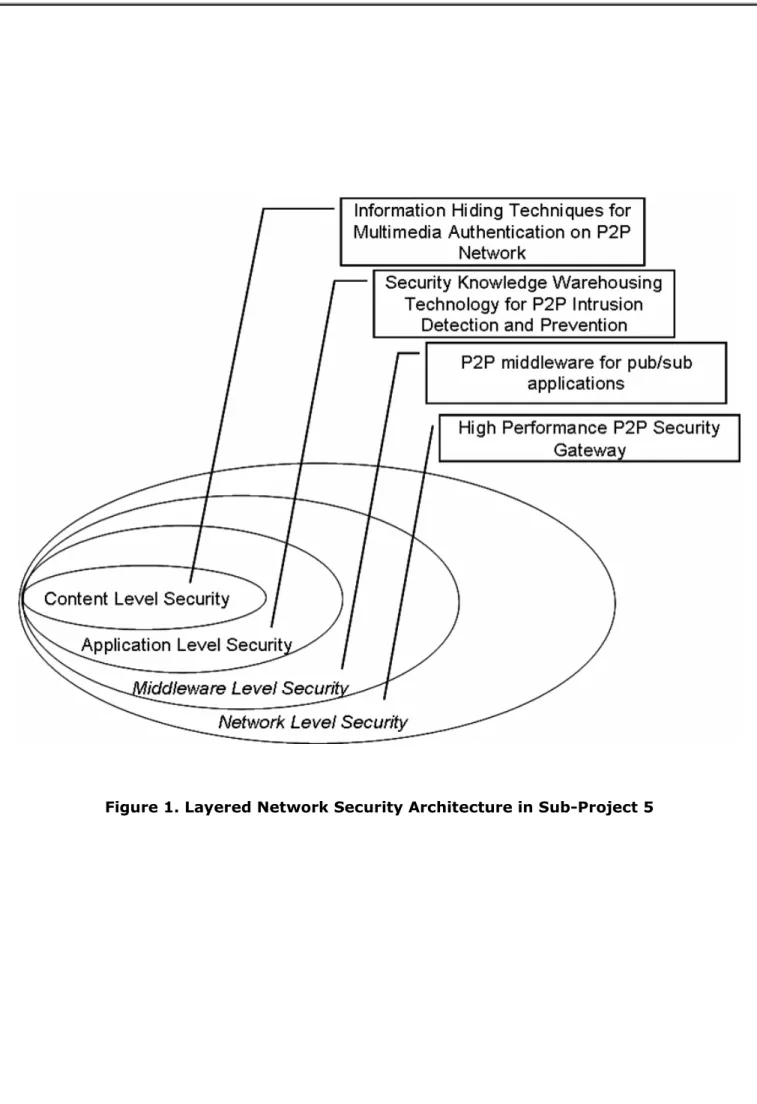
In this sub-project, we investigate key issues related to network security, which could be viewed in various aspects. Since nowadays most software systems are exposed to the Internet, these systems may be attacked by hostile users or affected by various virus, worms or Trojan programs. To protect software systems in the private sectors, we need techniques to guard the private software systems. These techniques can be divided in four levels: network level, middleware level, application level and content level, as shown in Figure 1. The network entrance is the first gate, we try to block out the incoming data packets which may be harmful here. Since the P2P traffic occupies more than half of the Internet traffic volume, and a large portion of such traffic may be harmful, thus we try to investigate efficient techniques which can accommodate the P2P traffic in a cost-effective way. However, there are various attack behaviors which can not be identified based on examining the individual packet; instead we need the knowledge in security domain including attack patterns and detection methods, which are evolutional over time in a changing environment. Therefore we have investigated dynamic knowledge acquisition methods to acquire these useful embedded rules based upon a designed worm concept hierarchy. Furthermore, to accommodate various harmful data, we need to build a knowledge warehouse framework that keeps all related information regarding the security knowledge. By comparing with the information in the warehouse, we should be able to judge whether the received data is safe or not. In addition, based on efficient incremental mining as the operators through the knowledge warehouse, we could extract suitable knowledge for assisting the decision of security maintenance. Besides, a large amount of knowledge including triggered alarms dramatically increases daily; we could also acquire useful knowledge for improving security strength. However, it is still difficult to detect and to block out harmful traffic completely, so some of them may still break into the private network domain and thus into the proprietary computer systems, therefore we need a middleware level security, which is to protect the computer software system from being affected even the harmful data intrude into the system. To ease the development, deployment, monitoring, and resource restriction of distributed system software, we have developed a plug-and-play security middleware framework. To validate the usefulness of the middleware, some typical application domains are also considered and implemented (such as grid computing, home automation, and P2P pub/sub system). If unfortunately the system has been broken through and the private information has been accessed, we still can prevent the important information from been read, that is, the information can not be displayed meaningfully to human beings so that the intruder is unable to understand the content of the stolen information. These tasks are categorized into four research topics which have been investigated in this subproject.
10
2. Breakthroughs and Major Achievements
Technology State-of-the-art Breakthroughs
Information hiding techniques for multimedia authentication on P2P Networks
Very few studies about authentication of files of various formats
A complete study on authentication techniques for verifying the integrity and fidelity of files of various formats after they are transmitted through P2P networks: a. proposing more precise and secure
authentication techniques for various popular file formats;
b. using secret keys in the authentication processes, which enhance security protection of the transmitted files; c. detecting not only the spatial tampering
performed on video sequences but also the temporal tampering performed on image frames
Since digital media contents transmitted through P2P networks could be tampered with illegally, it is necessary to verify the integrity and fidelity of concerned images and videos after they are transmitted. In the past, most studies on information hiding are about watermarking for copyright protection. There are few investigations about authentication of multimedia and files of other formats. Accordingly, we propose five authentication techniques for various popular file formats for more areas of applications:
a. binary image;
b. grayscale document image; c. color image;
d. flash file; e. video.
By means of these authentication techniques, users can detect whether the digital media content has been tampered with or not. Furthermore, the tampered regions can be marked and displayed to help users confirm the digital media contents’ authenticity. Additionally, to enhance the security level, we use secret keys to encrypt the authentication signals so as to protect signals from being forged by malicious users.
Technology State-of-the-art Breakthroughs Dynamic knowledge acquisition Knowledge warehousing VODKA TEA WISE TOARM NOM LNOM a. Dynamic knowledge b. Trend of inference log c. Incremental mining d. Performance
Although lots of well-known domain knowledge can be acquired from experts and technical reports, many unknown or variant security problems derived from old one are still emerging to threaten the cyber world due to the change of environment as time goes on. Hence, we have developed Variant Objects Discovering Knowledge Acquisition (VODKA), a new knowledge acquisition methodology, in the first year to iteratively discover the variants derived from original objects. In the second year, we proposed the Trend Evolution Acquisition methodology (TEA) to construct the worm knowledge base and the worm concept hierarchy based upon VODKA. The TEA enhances the VOKDA by integrating the context information including the frequencies of fired rules and the trend of inference log. A Worm Immune Service Expert system (WISE) is also implemented to evaluate the proposed methods. In the third year, besides integrating the VODKA and TEA into a dynamic EMCUD to help experts iteratively acquiring dynamic knowledge in a single site, several heuristics are proposed to collaboratively extract useful dynamic knowledge in a collaborative environment. To deal with the dramatically increasing knowledge, we propose a new knowledge warehouse framework in the third year to store knowledge instead of usual data, doing so would be useful for storing the security knowledge, including pre-defined parameters, context attributes, content attributes, and negative-border information. Three algorithms including Three-phase Online Association Rule Mining (TOARM), Negative-Border Online Mining (NOM), and Lattice-based NOM (LNOM) are proposed and implemented to efficiently extract deep knowledge and to discover the useful worm signatures and patterns to identify the possible attackers in our knowledge warehouse. To handle extremely large alerts, we have proposed Meaningful Report System (Mrs.) to reduce false alarms and further feedback to security product to decrease false alarms and to alleviate the loads of system administrator in the last year. Adaptive Speedup Algorithm for Pattern-matching (ASAP) is also developed to improve the misuse detector’s power and efficiency.
12
Technology State-of-the-art Breakthroughs
Grid computing Globus Toolkit 4 (GT4) a. Throughput: * 2
b. Reasonable programming style Heterogeneous
home automation
X10, UPnP, HAVi, Jini, OSGi
c. Event-driven pub/sub model d. Heterogeneous integration e. Scalability
P2P pub/sub system
Viceroy f. failure recovery & replication
Regarding the middleware, we have designed a modern security core architecture called Fast Java Messaging version 2 (FJM2) middleware. FJM2 has remarkable performance and persistence features; on top of which we add more flexible mechanisms, such as pluggable interface layer, pluggable modules layer, CODEX (content-based filtering) layer, resource monitoring/restriction layer, grid computing framework, and other application supports. These mechanisms are still lacked in commercial products, and therefore make FJM2 a more secure and flexible middleware for mission-critical distributed applications.
During the past years, our main breakthroughs are threefold. The first is the grid computing infrastructure. Our
FJM2-based grid computing solution outperforms the industry-standard Globus Toolkit 4 (GT4) in that the 1-to-1 and 1-to-3 throughput are twice as much better than that of GT4. We also have more reasonable programming style, while the
The second is the heterogeneous home automation platform. Our MHAP (MOM-based home automation platform) solution introduces the message-oriented middleware (MOM) into home automation systems and provides event-driven publish-subscribe facilities. In this way heterogeneous integration of a variety of home automation devices and platforms (such as X10, UPnP, HAVi, Jini, and OSGi) is possible, and the interoperation model among them is also improved.
The third is to undertake a pilot study on the possibility of introducing publish/subscribe mechanism into P2P system. In this preliminary study, we choose a P2P protocol/algorithm: Viceroy as the research target. We improve the Viceroy’s “level ring” topology, and achieve better failure handling, replication, and concurrent stabilization.
0.063 0.107 0.350 2.000 8.178 16.600 110.199 440.797 1365.333 8.135 55.662 191.629 940.947 0.650 0.034 0.058 0.243 3.704 0 200 400 600 800 1000 1200 1400 1600
Message Size ( Bytes )
T hr ou gh pu t ( K B yt es /s ) PFJM WS GT4 Java WS Core 0.063 0.133 0.533 2 8.533 32 136.533 546.133 2184.533 16.516 66.065 205.026 1057.032 4.129 0.258 0.065 0.058 1.032 0 500 1000 1500 2000 2500
Message Size ( Bytes )
T hr ou gh pu t ( K B yt es /s ) PFJM WS GT4 Java WS Core
14
Technology State-of-the-art Breakthroughs
TCP Splicing Transport Layer Algorithm a. Network Layer Algorithm (* Performance improvement) P2P Gateway Less than 5 million packets
per second in name-brand commercial products (Year 2006)
6 million packets per second can be achieved by using our scheme, with much less cost. (Year 2006) P2P Gateway
(version 2) a. Expensive Proprietary Architecture b. Vendor re-configurability
(Year 2007)
a. Cost effective commodity network processor
b. User re-configurability (Year 2007)
Internet Protocol version 6 (IPv6) was devised in mid 90’s. IPv6 extends the IP address from 32 bits to 128 bits and completely solves the insufficiency of IP addresses. However, the transition to 128-bit IPv6 addresses has been proceeding slowly. The problem of NAT (Network Address Translation) would remain until IPv6 become popular world wide. We have developed a system to solve the problem of NAT. To avoid the inconvenience of the related work, the main guideline of this work is to make the system easier to be deployed. Furthermore, peer-to-peer network structure is introduced to this system to improve performance. In addition, we have developed two new techniques: Passive TCP Splice and Pure TCP Splice to improve system performance. This system can be applied to IPv4/IPv6 Translation and Firewall Traversal, as well as P2P Gateway. Furthermore, it can support computer peripherals which connect to home network.
Since P2P traffic contributes most of the Internet traffic nowadays. P2P detection needs a high speed examination of the payload contents. The examination requires fast pattern matching techniques, which has been well investigated. In the project, we have also done the P2P filtering by further improving the performance by taking advantage of parallel mechanisms. We have developed a system in restricting P2P traffic and allow normal packets flow to pass. We employ Signature-Based method, checking application-layer payload, on classification P2P traffic. There are many popular P2P protocols we could correctly analysis and filter, such as eMule, eDonkey, BT, and so on. Although the Signature-Based is admitted best method in terms of accuracy, inefficiency is the drawback on this method due to comparison on every packet flow through the system. To overcome its inefficiency, we build the system on Intel IXP425 network processor embedded system. We fully utilize the three micro-engines (MEs), the special-purpose processor, on IXP425 processor to speed-up P2P traffic classification. The system takes advantage of parallel mechanisms from IXP425 processor. The experiment result shows that the throughput of the system can easily achieve multi-megabits per second, with equipment which only cost few hundred USD.
3. Categorized Summary of Research Outcomes. The criteria for top conferences and journals should be given and introduced briefly in the beginning of this section. In each research area, please give a brief summary on the research outcomes associated with the area. Note that the summaries should be consistent with the statistics given in Form3. Please list and number each research outcomes in sorted order in Appendix II, and list all the publications in top conferences and journals in Appendix III.
In the past 4 years, we have been working intensively on the investigation of network security. Since system for network security is complicated, we divided the system into four levels. Each level deals with different task. The most inner level is dealing with the protection of the various digital contents including video, flash, and binary documents, we have developed techniques which prevent the contents from being read correctly even it is stolen. Also, we developed a plug-and-play P2P platform for home automation. This system runs across the Internet and outperforms the state-of-the-art commercial system. We have also developed knowledge warehousing technology as well as knowledge acquisition system so that we could accommodate various security problems such as virus, worm, and intrusion much precisely and quickly. We also investigated and developed cost-effective P2P gateway so that we could deal with the ever increasing P2P traffic in an affordable and effective way. All these systems have been prototyped and work successfully. Some technologies have been extended to be deployed in the commercial applications.
Our research outcomes are of great academic importance, and we have 52 journal papers and 58 conference papers in these four years, not including the submitted ones, published under the program. One ROC patent is granted, 2 patents are pending.
4. Program Management: the Mechanism for Promoting Collaboration and Integration among the Institutes Involved
一、後卓越計畫—網路安全 96 年度第一次子計畫會議 時間:96 年 7 月 13 日(星期五) 16:00 地點:工三館 513 會議室 二、後卓越計畫—網路安全 96 年度第二次子計畫會議 時間:96 年 10 月 2 日(星期二) 14:00 地點:工三館 412 研討室 三、後卓越計畫—網路安全 96 年度子計畫五成果發表討論會議 時間:97 年 2 月 27 日(星期三) 10:00 地點:工三館 412 研討室
5. A Summary of the Post-Program Plan(Including the Detailed Description of Budget and Plan Adjustment of the next year)
16
VI.APPENDIX I:MINUTES FROM PROGRAM DISCUSSION MEETINGS
Main Project::: :
2004/05/04 -- Program Integration Meeting 一、時間:93 年 05 月 04 日(二)12:00 二、地點:清大資電館 447 會議室 三、會議主席:陳副校長文村、蔡文祥副校長 四、與會人員: 黃能富教授、馮開明教授、楊啟瑞教授、張明峰教授、曾煜棋教授、 陳耀宗教授、曾憲雄教授、陳良弼教授、金仲達教授、(張正尚教授、 林盈達教授、鄭聖慶博士、林一平教授、簡榮宏教授、許健平教授、 袁賢銘教授、許雅三教授請假) 五、會議記錄: 黃齡照 六、決議 (一)各子計畫目前的人事規劃為 4~7 位教授。 (二)計畫績效評估方式,視國科會的規定後再議。 (三)行政管理 1. 每一季開會一次,安排半天的時間,請每個子計畫報告研究進度,並希望每一位 主持人都能出席參加。時間訂於 3 月、6 月、9 月與 12 月的月底,下一次會議時 間為 9 月。 2. 子計畫與跨子計畫間的協調會議請自訂時間。 3. 計畫定期於期中舉辦成果發表會,期末為國科會考評。(第一年成果發表會訂於 期末) 4. 建構總計畫與各子計畫網頁資料。
2004/10/18 -- Program Integration Meeting 一、時間:93 年 10 月 18 日 (一) 中午 12 點整 二、地點:交大浩然圖書館八樓第一會議室 三、會議主席:蔡文祥 校長、陳文村 副校長 四、與會人員: 蔡文祥校長、陳文村副校長、簡榮宏教授、金仲達教授、張正尚教授、李端 興教授、黃能富教授、楊啟瑞教授、林盈達教授、陳智弘教授、李詩偉教授、 鄭聖慶博士、林一平教授、張明峰教授、曾煜棋教授、曾憲雄教授、陳耀宗 教授、張玉山副教授、王家祥教授 (請假:許健平教授、袁賢銘教授、陳良弼 教授、許雅三教授) 五、會議記錄: 卓怡慧 六、決議 (一)行政管理 1. 下一次總計畫會議時間定於 12 月,兩校共同邀請學術界或法人單位擔任審查委員 進行成果展示發表會及相關績效評估。 2. 往後兩校總計畫聯合會議,以每季舉行一次為原則。報告內容除研究進度與成果 外,建議加入計畫相關的學術活動(邀訪學者)與產學合作等項目的報告。 3. 後卓越計畫相關智慧財產權歸屬性(專利權、著作權等) ,請事先諮詢學校法務部 門。 4. 請各子計畫注意經費運用進度;並請各子計畫助理隨時更新經費餘額,通知並提 醒主持人經費運用進度。
18 2005/05/13 -- Program Integration Meeting
一、時間:94 年 05 月 13 日星期五 中午 12 點整 二、地點:交通大學電資大樓 203 會議室 蘭成廳 三、會議主席:蔡文祥 校長、陳文村 校長 四、與會人員: 蔡文祥、陳文村、邱瀞德、李端興、馮明開、楊啓瑞(請假)、林盈達、 田伯隆、李詩偉、林一平、張明峰、簡榮宏、曾煜棋、陳耀宗、張玉山、 曾憲雄(林順傑代)、金仲達、吳宜鴻、蕭宏章 五、會議記錄: 王慧敏 六、核閱: 七、決議 (一) 各分項計畫製作可技轉項目的說明單,格式可參考企業的產品或技術簡介, 並由金仲達教授與簡榮宏教授協調,訂定於 6 月底 ITRE 的時間舉辦說明會。 (二) 由於每季只舉辦一次兩校協調會議,請所有參與計劃的教授都來出席開會。 (三) 開會投影片請各分項提早一周繳交,格式請儘量統一,以便彙整。
2005/09/26 -- Program Integration Meeting 一、時間:94 年 09 月 26 日星期一 中午 12 點整 二、地點:清華大學資電館 447 會議室 三、會議主席:蔡文祥 校長、陳文村 校長 四、與會人員: 張正尚教授、邱瀞德教授、許雅三教授、闕宏時、許育豪、吳自強博士後、 陳奕錡、 王慧敏、羅志鵬(代替楊啟瑞)、陳靜雯、林一平教授、簡榮宏教 授、曾煜棋教授、張明峰教授、施明婷、陳文村教授、黃啟富、王瓊瑩、陳 耀宗教授、蔡文祥教授、曾憲雄教授、葉秉哲博士後、姚維民、林順傑、金 仲達教授、林華君教授、廖文瑜 五、會議記錄: 廖文瑜 六、討論議題: (一) 增加國際合作的機會,如:舉辦或多參加國際研討會、收取國外的博士後研究員。 (二) 邀請專家學者來台短期訪問或演講時,可請他們做計劃的批評、評論,如:10 月郭宗 傑教授來訪、11 月游本中教授來訪時。 (三) 請金仲達教授及簡榮宏教授,根據以往審查委員的意見,列表出該著重的項目,分配 至各子計畫並加強其進度成果。 (四) 預定 11 月舉辦自評會議,邀請國外學者 2-3 位為審查委員。
20 2005/12/16 -- Program Integration Meeting 一、時間:94 年 1 2 月 16 日(星期五)12:00 二、地點:交通大學電資大樓 203 會室蘭成廳 三、會議主席:陳文村校長、蔡文祥校長 四、出席人員:張正尚教授、黃能富教授、邱瀞德教授、吳仁銘教授、 楊啟瑞教授、林盈達教授、陳智弘教授、田伯隆教授、 林一平教授、張明峰教授、曾煜棋教授、簡榮宏教授、 楊舜仁教授、陳志成教授、張志勇教授、金仲達教授、 陳良弼教授、李政崑教授、王家祥教授、陳宜欣教授、 及各子計畫相關研究助理人員等 五、會議記錄:何卉蓁 六、報告事項: 總計畫及各分項計畫研究工作進度報告。 七、決議事項: (一)研發智財成果:請各分項計畫彙整所完成研發技術成果資料及專利智財數據,舉凡 技術移轉項目、專利智財、學術論文、技術報告等。作為本年度國科會期中成果報 告研發呈現,並冀達成本計畫預期目標。 (二)技術移轉、產學合作:本計畫仍將繼續秉持創新科技研發、以達追求學術卓越發展 之目標,同時積極與產業界技術合作交流,運用本計畫研發成果進行技術移轉。 (三)擬訂於下次兩校計畫聯席會議時,再次檢討本計畫研發進度及產學合作之執行狀況。
2006/09/22 -- Program Integration Meeting 一、時間:95 年 09 月 22 日(五)14:00 二、地點:交通大學工程三館 345 會議室 三、會議主席:陳文村校長、蔡文祥校長 四、與會人員:金仲達教授、林盈達教授、張正尚教授、馮開明教授、 楊啟瑞教授、張明峰教授、曾煜棋教授、曾憲雄教授、 楊舜仁教授、簡榮宏教授、許健平教授、袁賢銘教授、 陳宜欣教授、葉秉哲博後、詹振隆博後、吳志強博後、 曲衍旭博士、林君怡助理、林玫靜助理、沈上翔助理、 吳佳蓉助理、徐文靜助理、張巧涵助理、曹瑜珊助理 五、會議記錄:張巧涵 六、討論事項: 1. 審查意見中,哪些是我們要改進的?哪些不用或無法改進? 2. 如何增加內部技術對話與成功經驗分享? 3. 如何增加國際知名度? 4. 如何聚焦 challenging issues/impact/benchmark/state-of-the-art? 七、決議: 1.成果展現(前卓+後卓)技轉、paper 等參數並編 brochure。 2.三大主題內部增加交流,內部交流時安排經驗傳承。 3.各主題分開請專家(3~5 位)作一天的 review 和 comment(12 月之前)。 4.請準備格式讓各子計畫寫報告來符合評審的期望(明年 2 月之前,今年 12 月底初稿)。 5.各子計畫的會議紀錄納入總計畫當檔案或附件。 6.安排大約 4 月和 11 月各一次的經驗傳承研討會。 7.下一次每三個月一次的報告分成三大主題。三大主題報告期前,三大主題 先個別開會、 整合,並依第 4 點的格式報告。 8.後卓越計畫註冊申請網站:iWIN.org.tw 或 iWIN.edu.tw (iWIN.nthu.edu.tw 及 iWIN.nctu.edu.tw)
22 2006/11/22 -- Program Integration Meeting 一、時間:95 年 11 月 22 日(三)14:00 二、地點:交通大學工程三館 345 會議室 三、會議主席:金仲達教授、林盈達教授 四、與會人員:蔡文祥校長、林一平教授、楊舜仁教授、卓傳育博後、吳志強博後、闕宏時博 士生、趙子萱博士生、許育豪博士生、梁睿琦博士生、何承遠博士生、楊凱超 博士生、李皇辰博士生、巫芳璟博士、賴婉婷碩士、陳叡儀碩士生、鐘凱馨、 吳至仁、陳建中、王宗志、 林君怡助理、林玫靜助理、沈上翔助理、吳佳蓉助 理、張巧涵助理、蔡靜怡助理 五、會議記錄:張巧涵 六、報告事項:林ㄧ平教授經驗傳承會議 七、傳承會議內容大綱: (一)寫作論文方面: 1.Writing style 很重要,其中要特別注意: (1)名詞定義 (2)文法用字用詞 (3)logic 2.Response to reviews 的態度: (1)constructive 意見要虛心接納
(2)遇到別人 reject 你的 paper 不用爭論。重要是要看看對方的意見,reject 不 一定是負面的 3.如何讓你的 paper 被別人看,願意做 citation 的動作: (1)先上網被看,吸取別人意見,修改論文 (2)把你的 paper 寄給該領域的專家,請他們看看 (二)給教授的建議: 1.做研究最好是系列性的,例如:一系列 papers 2.如果你的學生有出國的機會,幫他作名片 3.當 reviewer 時,寫的 review 不要太隨便 4.寫書是 promotion 效果最大的,尤其是技術性的教科書: (1)寫國際教科書,要找好的出版商
(2)好的出版商就有好的 editor,可以幫你修改你的文法;另外好的出版商 也有好的 channel (3)第一本書找有名學者合作(國際合作/co-author) (三)建議 for 博士生/ junior 教授: 1.博班學生帶名片、負責在 timely 給知名人士 2.conference 時可以見到很多人,要善用 3.很多人只看 SCI journals 4.投稿策略(類型. 先 try A 級) 5.多拿獎: (1)recognition (2)建階梯 for senior 教授,讓他們有依據往上爬 (3)拿獎可以證明你的成就,讓你有信心,相對的你對自己的要求也會變高 (四)學生的論文 Quality Control:
1.一段時間 focus on 一個學生(pipelined 而不是 parallel),直到論文出去為止,才再 focus on 第二個學生
2.要求學生自動看規格標準缺什麼
3.學生要把論文拿給老師看之前,要做最好的準備
(五)時間分配:
1.Email 而不是 conference,因為 conference 很花時間 2.Reuse 過去 efforts(第二本書 3 個月完成)
3.熱忱、善用剩餘時間、reorganize 相關事情 4.晚上與週末繼續玩研究
24
2006/11/30 -- Program Integration Meeting
一、時間:95 年 11 月 30 日(四)10:00
二、地點:交通大學工程三館 412 會議室
三、會議主席:金仲達教授、林盈達教授
四、與會人員:卓傳育、許育豪、黃啟富、顏在賢、羅志鵬、蘇淑茵、林君怡、
沈上翔、張巧涵
五、會議記錄:徐文靜
六、報告事項:
1、針對 95 年 9 月 22 日總計畫會議中的決議事項,報告、投影片及網頁格式之討論。 2、95/09/22 會議決議事項
a、 成果展現(前卓+後卓)技轉、paper 等參數並編 brochure。
b、 三大主題內部增加交流,內部交流時安排經驗傳承。 c、 各主題分開請專家(3~5 位)作一天的 review 和 comment(12 月之前)。 d、 請準備格式讓各子計畫寫報告來符合評審的期望(明年 2 月之前,今年 12 月底初 稿)。 e、 各子計畫的會議紀錄納入總計畫當檔案或附件。 f、 安排大約 4 月和 11 月各一次的經驗傳承研討會。 g、 下一次每三個月一次的報告分成三大主題。三大主題報告期前,三大主題先個別 開會、整合,並依第 4 點的格式報告。 h、 後卓越計畫註冊申請網站:iWIN.org.tw 或 iWIN.edu.tw (iWIN.nthu.edu.tw 及 iWIN.nctu.edu.tw)
七、決議事項:
(ㄧ)、國科會所規定之報告內容主要部份 I. BASIC INFORMATION OF THIS SUB-PROJECTII.EXECUTIVE SUMMARY ON RESEARCH OUTCOMES OF THIS PROJECT
1.GENERAL DESCRIPTION OF THE PROJECT:INCLUDING OBJECTIVES OF THE PROJECT 2.BREAKTHROUGHS AND MAJOR ACHIEVEMENTS
3.CATEGORIZED SUMMARY OF RESEARCH OUTCOMES. 4.ASUMMARY OF THE POST-PROJECT PLAN
5.INTERNATIONAL COOPERATION ACTIVITIES
IV.LIST OF WORKS,EXPENDITURES,MANPOWER, AND MATCHING SUPPORTS FROM THE PARTICIPATING INSTITUTES
V.APPENDIX I VI.APPENDIX II
(二)、針對後卓越計畫的報告、投影片及網頁內容,有以下決議:
1. II.EXECUTIVE SUMMARY ON RESEARCH OUTCOMES OF THIS PROJECT 2. BREAKTHROUGHS AND MAJOR ACHIEVEMENTS 應附下表
Subproject Technology State-of-the-art
(technology researcher、 affiliation)
Breakthroughs
(verbal description on transfer、 citation、comparable project) RDM LDI W.Smith Berkeley 10G v.s 5G
2. II. EXECUTIVE SUMMARY ON RESEARCH OUTCOMES OF THIS PROJECT 4. A Summary of the Post-Project Plan 應附下表
各子計畫的部份,針對 Breakthroughs 提出 2 個 technology(不超過 3 個),從過去到現在及 未來作一個時間表的呈現,說明其中的連貫及發展。 2000~2004 2005~2006 2007~2008 Tech 1. Tech 2. Tech 3. 3.決議 1 與 2 所提的 technology 以 2 個為原則,不超過 3 個。 4.投影片呈現內容與報告格式內容相同,包含 I~V 部分,其中 II 的第 2 節及第 4 節要先附上 決議 1 及決議 2 的表格。 5.網頁:以公告性質為主 (1).保留總計劃的部份,並將英文格式更改成與中文格式相同。
26
(4).子計畫的網頁內容要包含 II、III、VI 的報告內容,且 VI 的部份要有 URL 連結可下載資
料。
(5).將所有資料歸納於總計劃的主機之下,以便管理,再由計畫助理負責更新。 (6).網頁更新的部份於 2007/02/28 前,資料收集完成後,亦更新完成。
2007/01/08 -- Program Integration Meeting
一、 時間:96 年 01 月 08 日(星期一)14:00
二、 地點:清華大學電資館 447 會議室
三、 會議主席:陳文村校長、蔡文祥校長
四、 出席人員:張正尚教授、黃能富教授、邱瀞德教授、馮開明教授、
i.
楊啟瑞教授、林盈達教授、田伯隆教授、林一平教授、
ii.
張明峰教授、曾煜棋教授、簡榮宏教授、楊舜仁教授、
iii.
陳志成教授、張志勇教授、金仲達教授、陳耀宗教授、
iv.
曾憲雄教授、袁賢銘教授、葉秉哲博士、金仲達教授、
v.
陳宜欣教授、及各子計畫相關研究助理人員等
五、 會議記錄:徐文靜
六、 報告事項:總計畫及各分項計畫研究工作進度報告。
七、 決議事項:
1. 報告格式請統一,並附上 95/11/30 開會決議中應附之表格(請參照 95/11/30 會議紀 錄)。 2. 各分項計劃於一月 15 日之前繳交成果報告,以便總計畫彙整。 3. 各計畫報告於一月底上傳至國科會。28
2007/04/20 -- Program Integration Meeting
一、時間:96 年 04 月 20 日(五)14:00 二、地點:交通大學工程三館 427 會議室 三、會議主席:陳文村校長、蔡文祥校長 四、與會人員:金仲達教授、林盈達教授、張正尚教授、馮開明教授、 楊啟瑞教授、張明峰教授、曾煜棋教授、曾憲雄教授、 楊舜仁教授、簡榮宏教授、許健平教授、袁賢銘教授、 陳宜欣教授、葉秉哲博後、詹振隆博後、曲衍旭博士、 林君怡助理、林玫靜助理、何承遠助理、吳佳蓉助理、 徐文靜助理、楊耀萱助理、何佳文助理、蔡靜怡助理 五、會議記錄:楊耀萱 六、計畫進度成果報告
2007/10/12 -- Program Integration Meeting
一、時間:96 年 10 月 12 日(五)14:00 二、地點:清華大學資電館 4 樓 447 會議室 三、會議主席:陳文村校長、蔡文祥校長 四、與會人員:金仲達教授、陳耀宗教授、張正尚教授、馮開明教授、林華君教授、 楊啟瑞教授、張明峰教授、曾煜棋教授、曾憲雄教授、黃能富教授 楊舜仁教授、簡榮宏教授、許健平教授、袁賢銘教授、葉秉哲博後、 詹振隆博後、施汝霖博後、陳柏諭博班生、田柏隆博班生、 曲衍旭博士、王竣聰、黃冠霖、林君怡助理、林玫靜助理、 何承遠助理、徐文靜助理、楊耀萱助理、何佳文助理、蔡靜怡助理 五、會議記錄:徐文靜 六、計畫進度成果報告 七、討論事項: 1.後卓越成果展時間及方式? 2.持續合作之議題? 八、決議: 1.預計於 1 月初發表成果展,將技轉項目及自評合於成果展中。 2.建議各計畫討論後,於下一次會議討論清、交未來合作議題。30 VII.APPENDIX II:
1. PUBLICATION LIST((C(( ONFERENCES,JOURNALS,BOOKS,BOOK CHAPTERS,etc.)))) 2. PATENT LIST
3. INVENTION LIST
4. LIST OF WORKSHOPS/CONFERENCES HOSTED BY THE PROGRAM 5. LIST OF PERSONAL ACHIEVEMENTS OF THE PIS
6. LIST OF TECHNOLOGY TRANSFERS 7. LIST OF TECHNOLOGY SERVICES
1. PUBLICATION LIST (CONFERENCES,JOURNALS,BOOKS,BOOK CHAPTERS,etc.)
JOURNALS
1. C. H. Tzeng, Z. F. Yang, and W. H. Tsai (2004). 「Adaptive data hiding in palette images by color
ordering and mapping with security protection,」 IEEE Transactions on Communications, Vol. 52, No. 4, pp. 791-800. (SCI, EI)
2. C. H. Tzeng and W. H. Tsai (2004). 「A combined approach to integrity protection and verification
of palette images using fragile watermarks and digital signatures,」 IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, Vol. E87-A, No. 6, pp. 1612-1619. (SCI)
3. C. C. Lin and W. H. Tsai (2004). 「Secret multimedia information sharing with data hiding capability
by simple logic operations,」 Pattern Recognition and Image Analysis, Vol. 14, No. 4, pp. 594-600.
4. C. C. Lin and W. H. Tsai (2004). 「Secret image sharing with steganography and authentication,」
Journal of Systems & Software, Vol. 73, No. 3, pp. 405-414. (EI)
5. Y. C. Chiu and W. H. Tsai (2006). 「Copyright Protection by Watermarking for Color Images
against Print-and-Scan Operations Using Coding and Synchronization of Peak Locations in Discrete Fourier Transform Domain, 」 Journal of Information Science and Engineering, Vol. 22, No. 3, pp. 483-496. (SCI)
6. T. Y. Liu and W. H. Tsai (2007). 「A New steganographic method for data hiding in Microsoft Word
documents by a change tracking technique, 」IEEE Transactions on Information Forensics and Security, Vol. 2, No. 1, pp. 24-30.
7. I. S. Lee and W. H. Tsai (2007). 「Data hiding in binary images with distortion-minimizing
capabilities by optimal block pattern coding and dynamic programming techniques, 」 IEICE Transactions on Information and Systems, Vol. E90-D, No. 8, pp. 1142-1150. (SCI)
8. Shun-Chieh Lin and Shian-Shyong Tseng (2004) 「Constructing Detection Knowledge for DDoS
Intrusion Tolerance,」 Expert Systems With Applications, Vol. 27, No. 3, pp.379-390. (2004/2/11 submitted, 2004/5/11 accepted) [SCI, EI]
9. Shun-Chieh Lin, Po-Chih Huang, Shian-Shyong Tseng, and Nien-Yi Jan (2006), 「Knowledge
Acquisition Assist in Analyzing Network Behaviors,」 to appear in WSEAS Transaction on Computers. [EI]
10. Shun-Chieh Lin, Chien-Hao Wen, Shian-Shyong Tseng, and Yao-Tsung Lin (2006) 「Rule Base
Partitioning for Constructing Meta-rule,」 accepted by Journal of Internet Technology with minor revision. [EI]
11. C. Y. Wang, S. S. Tseng, T. P. Hong and Yian-Shu Chu (2007/01), 「Online generation of association rules under multidimensional consideration based on negative-border,」 Journal of Information Science and Engineering Vol. 23, No. 1. pp. 233-242 (SCI, EI)
12. Shian-Shyong Tseng, Kenny Huang, Johannes Chiang (2007),」Internet exchange traffic sharing and
market competition,」 Journal of Internet Technology Vol. 8, No.1. (EI)
13. S. S. Tseng, P. C. Sue, J. M. Su, J. F. Weng, and W. N. Tsai(2007), 「A new approach for
constructing the concept map,」 Computer and Education 49, pp.691-707. (SSCI)
14. M. T. Chen, B.M.T. Lin, and S. S. Tseng (2007), 「Multicast routing and wavelength assignment
with delay constraint in WDM network with heterogeneous capability,」 to appear in Journal of Network & Computer Applications. (SCI) In Press, Corrected Proof, Available online 18 August 2006
15. Shun-Chieh Lin, Shian-Shyong Tseng, Wen-Guey Tzeng, and Shyan-Ming Yuan (2007) 「A
framework of high confidence e-healthcare information system,」 Asian Journal of Health and Information Sciences Vol. 1, No. 2, pp.176-188.
16. Yian-Shu Chu, Shian-Shyong Tseng, Chin-Hsuan Chang, Chang-Sheng Chen (2007), 「 A
Learning-by-Doing Remedial Tutoring System for Building and Managing SIP/ENUM DNS Servers,」 International Journal of Electrical Engineering Volume 14, No. 1, 2007, pp. 33-38. (EI)
17. Shun-Chieh Lin, Chia-Wen Teng, and Shian-Shyong Tseng (2007) 「 Capturing Evolutional
Knowledge using Time Interval Tracing,」 Journal of Advanced Computational Intelligence & Intelligent Informatics, Vol.11, No. 4, pp. 373-380.
18. W. H. Tarng, M.Y. Chang, L. K. Lai, S. S. Tseng and J. F. Weng (2007): 「An Adaptive Web-based
Learning System for the Scientific Concepts of Water Cycle in Primary Schools」, Journal of Advanced Technology for Learning, Vol. 4, No. 2, P208-1093 2007. (EI)
19. Wen-Chung Shih, Chao-Tung Yang, and Shian-Shyong Tseng, (2007), 「A Performance-based
Parallel Loop Scheduling on Grid Environments,」 Journal of Supercomputing, 41(3), pp. 247-267. [SCI, EI].
20. Hsiao-Han Chen, Wei-Hsun Lee, Shian-Shyong Tseng,(2007) 「 A Spatiotemporal Traffic
Bottlenecks Mining Model for Discovering Bottlenecks in Urban Network, 」 World Congress on Intelligent Transportation System, Oct. 10-Oct. 13, 2007, Beijing, China.
21. Shun-Chieh Lin, Shian-Shyong Tseng, and Chia-Wen Teng (2008/02) 「Dynamic EMCUD for
knowledge acquisition,」 Expert Systems with Applications Vol.34 , Issue 2 pp.833-844. (SCI, EI)
22. Yian-Shu Chu, Shian-Shyong Tseng, Yu-Jie Tsai, and Ren-Jei Luo, 「An Intelligent Questionnaire
Analysis Expert System,」 Expert Systems with Applications, Volume 40, Issue 3, 2008. (SCI)
23. Shian-Shyong Tseng and Shun-Chieh Lin (2008) 「 VODKA: Variant Objects Discovering
Knowledge Acquisition,」 to appear in Expert Systems with Applications [SCI,EI]
24. W.-C. Chen, S. S. Tseng, and T.-P. Hong (2008) 「An efficient bit-based feature selection method,」
to appear in Expert Systems with Applications [SCI,EI]
25. Chao-Tung Yang, Wen-Chung Shih, and Shian-Shyong Tseng, (2008), 「Dynamic Partitioning of
Loop Iterations on Heterogeneous PC Clusters,」 Journal of Supercomputing. Vol.44(1),P1-23 [SCI, EI]
32
27. Wen-Chung Shih, Shian-Shyong Tseng, and Chao-Tung Yang, 「Using Taxonomic Indexing Trees
to Efficiently Retrieve SCORM-compliant Documents in e-Learning Grids,」 to appear in Journal of Educational Technology & Society. . (2007/7/23 accepted) [SSCI].
28. Shian-Shyong Tseng, Jun-Ming Su, Gwo-Jen Hwang, Gwo-Haur Hwang, Chin-Chung Tsai and
Chang-Jiun Tsai,」An Object-Oriented Course Framework for Developing Adaptive Learning Systems,」 to appear in Journal of Educational Technology & Society. . (2007/10 accepted) [SSCI].
29. Wen-Chung Shih, Shian-Shyong Tseng, and Chao-Tung Yang, 「Wiki-based Rapid Prototyping for
Teaching-Material Design in e-Learning Grids,」 Computers & Education. (2007/10/22 accepted) [SSCI].
30. Wei-Hsun Lee, Shian-Shyong Tseng, and Sheng-Han Tsai, 「A Knowledge base Real-Time Travel
Time Prediction System for Urban Network」, Expert System with Applications. [SCI, EI] (accepted)
31. Yaw-Chung Chen and Wen-Yen Chen, 「An Agent-Based Metric for Quality of Services over
Wireless Networks,” Accepted by Journal of Systems and Software.
32. Wen-Kang Jia and Yaw-Chung Chen, 「Performance Evaluation of Ethernet Frame Burst Mode in
EPON Downstream Link, 」 ERTI Journal, Vol. 30, No. 2, April 2008, pp. 290-300.
33. Cheng-Yuan Ho, Yaw-Chung Chen, Yi-Cheng Chan, and Cheng-Yun Ho, 「Fast Retransmit and
Fast Recovery Schemes of Transport Protocols: A Survey and Taxonomy,」 Computer Networks, Vol. 52, Issue 6, pp. 1308-1327, April 2008.
34. Cheng-Yuan Ho, Yi-Cheng Chan, and Yaw-Chung Chen, 「 WARD: a transmission control
protocol-friendly stateless active queue management scheme,」 IET Communications, Vol. 1, Issue 6, pp. 1179-1186, December 2007.
35. Cheng-Yuan Ho, Yi-Cheng Chan, and Yaw-Chung Chen, 「WARD: A Deterministic Fluid Model,」
IET Communications, Vol. 1, Issue 4, pp. 711-717, August 2007.
36. Cheng-Yuan Ho, Yi-Cheng Chan, and Yaw-Chung Chen, 「TCP-Ho: A Congestion Control
Algorithm with Design and Performance Evaluation,」 IEICE Transactions on Communications, Vol. E90-B, No. 3, pp. 516-526, March 2007.
37. Cheng-Yuan Ho, Yaw-Chung Chen, and Cheng-Yun Ho, 「Improving Performance of Delay-based
TCPs with Rerouting,」 IEEE Communications Letters, Vol. 11, Issue 1, pp. 88-90, January 2007.
38. Cheng-Yuan Ho, Yi-Cheng Chan, and Yaw-Chung Chen, 「Gallop-Vegas: An Enhanced Slow-Start
Mechanism for TCP Vegas,」 Journal of Communications and Networks (KICS), Vol. 8, No. 3, pp.351-359, September 2006.
39. Cheng-Yuan Ho and Yaw-Chung Chen, 「Snug-Vegas and Snug-Reno: Performance Improvement
of TCP over Heterogeneous Networks,」 IEE Proceedings – Communications, Vol. 153, Issue 2, pp. 169-176, April 2006.
40. Yuan-Rung Yang, Chia-Tai Chan and Yaw-Chung Chen, "Improving Performance of XCP over
High Bandwidth-Delay Product Networks," GESTS International Transactions on Computer Science and Engineering, Vol. 28, No. 1 February 2006, pp. 133-144.
41. Y. C. Chen, P. C. Wang, C. L. Lee and C. T. Chan, “Performance Improvement of Hardware-based
Packet Classification Algorithm,” Lecture Notes in Computer Science (LNCS), Vol. 3421, pp. 728-736, April 2005. [SCI-Expanded, EI]
42. Yi-Cheng Chan, Chia-Tai Chan, and Yaw-Chung Chen, “RoVegas: A router-based congestion
avoidance mechanism for TCP Vegas,” Computer Communications, Vol. 27, Issue 16, pp. 1624-1636, October 2004.[SCI-Expanded, EI]
43. Yi-Cheng Chan, Chia-Tai Chan, and Yaw-Chung Chen, “RedVegas: Performance Improvement of
TCP Vegas over Heterogeneous Networks,” IEICE Trans. Fundamentals, Vol. E87-A, No. 7, pp. 1672-1680, July 2004. [SCI-Expanded, EI]
44. Ping-Jer Yeh, Ruey-Shyang Wu, and Shyan-Ming Yuan, 「Distributed System Management through
Automated Injection, 」WSEAS Transactions on Business and Economics, Issue 4, Vol. 3, ISSN 1109-9526, pp. 276–283, April 2006.
45. Mu-Chi Sung, Ming-Chun Cheng, Zhi Xin Fan, Ping-Jer Yeh, Shyan-Ming Yuan, Chia-Yuan Huang, Lo-Chuan Hu, 「An Experimental Study toward Failure Impact on OpenAIS,」WSEAS Transactions on Communications, Vol. 5, Issue 6, pp. 1067–1073, June 2006. [EI]
46. Ming-Chun Cheng, Shyan-Ming Yuan, 「A Real-time One-to-Many Video Broadcasting System, 」
WSEAS Transactions on Computers, Vol 5, No 6, pp. 1154–1161, June 2006. [EI]
47. Tsun-Yu Hsiao, Shyan-Ming Yuan, 「 A Scalable and Flexible Management Framework for
Distributed Computing System, 」WSEAS Transactions on Computers, Vol 5, No 6, pp. 1162–1168, June 2006. [EI]
48. Ruey-Shyang Wu, Shyan-Ming Yuan, 「An Adaptive Architecture for Secure Message Oriented
Middleware, 」 WSEAS Transactions on Information Science and Applications, Vol 3, No 7, pp. 1239–1246, July 2006 [EI]
49. Chi-Huang Chiu, Hsien-Tang Lin, Ping-Jer Yeh, and Shyan-Ming Yuan, 「An OSGi Platform
Connecting Heterogeneous Smart Home Appliances from Mobile Devices,」 WSEAS Transactions on Computers, Vol 5, No 7, pp. 1549–1555, July 2006. [EI]
50. Ping-Jer Yeh, Winston Lo, Yung-Yu Chen, Shyan-Ming Yuan, 「 A Persistent and Durable
Extension to Globus Toolkit Java WS Core, 」 to appear in WSEAS Transactons on Computers, Issue 2, Volume 6, Feb 2007. [EI]
51. Ming-Chun Cheng and Shyan-Ming Yuan, 「 An Adaptive and Unified Mobile Application
Development Framework for Java, 」Journal of Information Science and Engineering, Vol. 23, No. 5, pp. 1391-405, Sep 2007. [SCI]
52. Ruey-Shyang Wu, Fengyi Lin, Anderson Liang, Shyan-Ming Yuan, 「A Reference Model for
Building Enterprise Computing Platform and Its Based Integration Framework, 」 International Journal of Technology Management, Vol. 38, No.4 pp. 439 - 462 , 2007. [SSCI]
CONFERENCES
1. P. M. Huang, D. C. Wu, and W. H. Tsai (2004/06). 「A novel block-based authentication technique
for binary images by block pixel rearrangements, 」Proceedings of 2004 IEEE International Conference on Multimedia & Expo (ICME 2004), Taipei, Taiwan, Republic of China.
2. Wei-Liang Lin and Wen-Hsiang Tsai (2004/12). 「Data Hiding in Image Mosaics by Visible
Boundary Regions and Its Copyright Protection Application against Print-And-Scan Attacks,」 Proceedings of 2004 International Computer Symposium (ICS 2004), Taipei, Taiwan, Republic of China.
3. Y. C. Chiu and W. H. Tsai (2004/08). 「Copyright protection by watermarking for Color Images
against Rotation and Scaling Attacks Using Peak Detection and Synchronization in Discrete Fourier Transform Domain, 」Proceedings of Third Workshop on Digital Archives Technologies, Taipei, Taiwan, pp. 207-213, August 5-6, 2004.
4. Y. C. Chiu and W. H. Tsai (2004/08). 「Copyright protection by watermarking for color images
against print-and-scan operations using coding and synchronization of peak locations in discrete Fourier transform domain,」 Proceedings of 2004 Conference on Computer Vision, Graphics and Image Processing, Hualien, Taiwan, Republic of China.
5. K. L. Huang and W. H. Tsai (2004/08). 「Secret sharing with steganographic effects for HTML
documents,」 Proceedings of 2004 Conference on Computer Vision, Graphics and Image Processing, Hualien, Taiwan, Republic of China.
34
7. T. Y. Liu and W. H. Tsai (2005/6). 「Active quotation authentication in Microsoft Word documents
using block signatures,」 3rd International Conference on Information Technology: Research and Education (ITRE 2005), Hsinchu, Taiwan, Republic of China.
8. Y. C. Chuang and W. H. Tsai (2005/8). 「 Active copyright protection of html files by a
watermarking technique,」 Proceedings of 2005 Conference on Computer Vision, Graphics and Image Processing, Taipei, Taiwan, Republic of China.
9. L. Y. Weng and W. H. Tsai (2005/8). 「Integrity authentication of grayscale document images
surviving print-and-scan attacks, 」 Proceedings of 2005 Conference on Computer Vision, Graphics and Image Processing, Taipei, Taiwan, Republic of China.
10. Y. Y. Yang, D. C. Wu and W. H. Tsai (2005/9). 「Watermarking of numerical databases using
spread spectrum techniques,」 Proceedings of 4th Workshop on Digital Archives Technologies, pp.79-84, Taipei, Taiwan, Republic of China.
11. S. C. Hung, D. C. Wu, and W. H. Tsai (2005/12). 「Data hiding in stained glass images,」
Proceedings of 2005 International Symposium on Intelligent Signal Processing and Communications Systems, pp. 129-132, Hong Kong.
12. K. F. Chien and W. H. Tsai (2006/08). 「Authentication of surveillance video sequences and
contents by hiding motion vector information,」 Proceedings of 2006 Conference on Computer Vision, Graphics and Image Processing, Taoyuan, Taiwan, Republic of China.
13. C. Y. Hsu and W. H. Tsai (2006/08). 「Creation of a new type of image - circular dotted image - for
data hiding by a dot overlapping scheme,」 Proceedings of 2006 Conference on Computer Vision, Graphics and Image Processing, Taoyuan, Taiwan, Republic of China.
14. Y. L. Wang and W. H. Tsai (2006/08). 「Lossless visible watermarking for copyright protection of
H.263 videos,」 Proceedings of 2006 Conference on Computer Vision, Graphics and Image Processing, Taoyuan, Taiwan, Republic of China.
15. P. P. Chen and W. H. Tsai (2006/08-09). 「Copyright protection of palette images by a robust
lossless visible watermarking technique,」 Proceedings of 5th Workshop on Digital Archives Technologies, Taipei, Taiwan, Republic of China
16. I. S. Lee and W. H. Tsai (2007/08), 「 Data hiding in grayscale images by dynamic programming
based on a human visual model, 」 Proceedings of 2007 Conference on Computer Vision, Graphics and Image Processing, Miaoli, Taiwan, Republic of China.
17. Wen-Yi Hsin, Shian-Shyong Tseng, Shun-Chieh Lin (2005) 「A Study of Alert-Based Collaborative
Defense,」 in Proc. of The 8th International Symposium on Parallel Architectures, Algorithms & Networks (ISPAN 2005), Dec. 7-9, 2005, Las Vegas, Nevada, U.S.A., pp. 148-153.
18. W. C. Shih, C. T. Tung, and S. S. Tseng (2005/03),」 A hybrid parallel loop scheduling scheme on
grid environments,」 in Proc. of 4th International Conference on Grid and Cooperative Computing (GCC 2005), Nov. 30-Dec. 3, 2005, Beijing, China and Lecture Notes in Computer Sciences ,Vol. 3795, pp. 370-381. [SCI]
19. Chien-Hao Wen, Shun-Chieh Lin, Shian-Shyong Tseng, and Yao-Tsung Lin (2005) 「Rule Base
Partitioning for Constructing Meta-rule, 」 Proc. of TAAI 2005 (CDROM), Dec. 2-3, 2005, Kaohsiung, Taiwan, R.O.C.
20. Chia-Wen Teng, Shun-Chieh Lin, and Shian-Shyong Tseng (2005) 「Evolution in Knowledge
Acquisition method with Time Interval Tracing Oriented,」 Proc. of TAAI 2005 (CDROM), Dec. 2-3, 2005, Kaohsiung, Taiwan, R.O.C.
21. Wen-Yi Hsin, Shian-Shyong Tseng, and Shun-Chieh Lin (2005) 「Designing a Collaborative
22. Shun-Chieh Lin, Po-Chih Huang, Shian-Shyong Tseng, and Nien-Yi Jan (2006), 「Analyzing Network Behaviors with Knowledge Acquisition and Data Warehousing,」 to appear in the proceedings of the 10th WSEAS CSCC Multiconference, Athens, Greece, 13-15, July.
23. Shun-Chieh Lin, Yao-Tsung Lin, Shian-Shyong Tseng, and Nien-Yi Jan (2006) 「 Ontology
Discovery Using Cases Clustering,」 to appear in the proceedings of SCIS & ISIS 2006, Tokyo, Japan.
24. Wen-Chung Shih, Chao-Tung Yang, Chun-Jen Chen, and Shian-Shyong Tseng, (2007), 「Parallel
Loop Scheduling Using Knowledge-Based Workload Estimation on Grid Environments,」 in Proc. of the IEEE/IPSJ International Symposium on Applications and the Internet (SAINT 2007), Jan. 15-19, 2007, Hiroshima, Japan. [EI]
25. Jui-Feng Weng, Shian-Shyong Tseng, Jun-Ming Su, Yang-Ching Fan(2007)」 Constructing a Test
Item Generator for Program Debugging Assessment,」 The 2007 International Conference on Frontiers in Education: Computer Science and Computer Engineering (FECS'07), June 6-July 7, Las Vegas, U.S.A.
26. W. H. Tarng, M.Y. Chang, L. K. Lai, S. S. Tseng and J. F. Weng (2007): An Adaptive Web-based
Learning System for the Scientific Concepts of Water Cycle in Primary Schools, Journal of Advanced Technology for Learning, Vol.2, No. 2, 2007. (EI)
27. H.N. Lin, S.S. Tseng, J.F. Weng, H.Y. Lin and J.M. Su,(2007), 「An Iterative, Collaborative
Ontology Construction Scheme,」ICICIC2007, Kumamoto, Sep. 5-7, 2007.
28. Shian-Shyong Tseng, Jui-Feng Weng, Huan-Yu Lin, Ang-Jui Tsai, and Jun-Ming SU(2007),
「 Ontology-based Topic Analyzer for Programming Learning Forum, 」 15th International Conference on Computers in Education, Nov.5-9, 2007, Hiroshima, Japan.
29. Wen-Chung Shih and Shian-Shyong Tseng, (2008), 「 Folksonomy-based Indexing for
Location-aware Retrieval of Learning Contents,」 The 5th IEEE International Conference on Wireless, Mobile, and Ubiquitous Technology in Education (WMUTE 2008), Mar. 23-26, 2008, Beijing, China. (The Best Paper Award)
30. Huan-Yu Lin, Shian-Shyong Tseng*, Jui-Feng Weng, Jun-Ming Su, (2008), 「 Collaborative
Interpretative Service Assisted Design System Based on Hierarchical Case Based Approach, 」 IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing (SUTC 2008),11-13 June 2008 in Taichung, Taiwan
31. K. Y. Ho and Y. C. Chen, 「「「Performance Evaluation of IPv6 Packet Classification with Caching,「 」」」」
To appear on Proceedings of ChinaCom, August 25-27, 2008, Hangzhou, China
32. Li-Che Hung and Yaw-Chung Chen, 「「「「Parallel Table Lookup for Next Generation Internet,」」」To 」
appear on IEEE COMPSAC 2008, Turku, Finland, July 28 - August 1, 2008.
33. Cheng-Yueh Liu and Yaw-Chung Chen, 「「「An Adaptive Bandwidth Request Scheme for QoS 「
Support in WiMAX Polling Services, 」」」」To appear on The 10th International Workshop on
Multimedia Network Systems and Applications, Beijing, China, June 17-20, 2008
34. Ashraf D. Milhim and Yaw-Chung Chen, 「「「「An Adaptive Polling Scheme to Improve Voice
Transmission over Wireless LANs. 」」」」 Proceedings of 2007 ACS/IEEE International Conference on
Computer Systems and Applications, May 13-16, Amman, Jordan, pp. 146-152.
36
Gwangju, Korea, September 2006, pp. 63541L-1-63541L-11.
37. Ming-Chuan Hsu and Yaw-Chung Chen, 「Enhanced PCF Protocols for Real-time Multimedia
Services over 802.11 Wireless Networks, 」 Proceedings of 26th IEEE International Conference on
Distributed Computing Systems Workshops, July 2006, Lisbon, Potugal.
38. Wen-Kang Jia and Yaw-Chung Chen, 「Performance and Traffic Behavior Analysis of Frame
Bursting for GbE CSMA/CD SISO Networks, 」 Proceedings of Joint International Conferences on Optical Internet and Next Generation Network (COIN-NGNCON 2006), Jeju, Korea
39. Cheng-Yuan Ho, Yi-Cheng Chan, and Yaw-Chung Chen, 「A TCP-Friendly Stateless AQM Scheme
for Fair Bandwidth Allocation, 」 Proceedings of IEEE ICAS 2005 & ICNS 2005, Papeete, Tahiti, French Polynesia, October 2005, pp. 14-19. [SCI, EI]
40. Cheng-Yuan Ho, Chen-Hwa Shih, Yaw-Chung Chen, and Yi-Cheng Chan, 「Aided Congestion
Avoidance Mechanism for TCP Vegas, 」 Proceedings of Third International Conference, ICCNMC 2005, Zhanggjijie, China, August 2005, pp. 961 – 971.
41. Yaw-Chung Chen, Pi-Chung Wang, Chun-Liang Lee, and Chia-Tai Chan, 「Performance
Improvement of Hardware-based Packet Classification Algorithm, 」Proceedings of 4th International Conference on Networking 2005 (ICN’05), Reunion Island, France, April 2005, pp. 728-736.
42. Cheng-Yuan Ho, Yi-Cheng Chan, and Yaw-Chung Chen, 「An Efficient Mechanism of TCP-Vegas
on Mobile IP Networks,」 Proceedings of IEEE INFOCOM 2005, Vol. 4, pp. 2776-2780 & IEEE Global Internet Symposium in conjunction with IEEE INFOCOM 2005, Miami, Florida, USA, March 2005, pp. 1-5.
43. Cheng-Yuan Ho, Yi-Cheng Chan, and Yaw-Chung Chen, 「An Enhanced Slow-Start Mechanism for
TCP Vegas,」Proceedings of IEEE ICPADS 2005, Vol. 1, Fukuoka Institute of Technology (FIT), Fukuoka, Japan, July 2005. [EI] (The 11th International Conference on Parallel and Distributed Systems), pp.405-411.
44. Yuan-Rung Yang, Chia-Tai Chan, Pi-Chung Wang and Yaw-Chung Chen, 「Performance
Enhancement of XCP for High Bandwidth-Delay Product Networks, 」 7th International Conference
on Advanced Communication Technology (ICACT’05), Phoenix Park, Korea, February 2005, pp. 456-461.
45. Yi-Cheng Chan, Chia-Tai Chan, Yaw-Chung Chen, and Cheng-Yuan Ho, 「 Performance
Improvement of Congestion Avoidance Mechanism for TCP Vegas, 」IEEE ICPADS’2004, Newport Beach, California, USA, July 2004, pp. 605-612. [EI]
46. Ruey-Shyang Wu, Shyan-Ming Yuan, 「A Pluggable Security Framework on Message Oriented
Middleware,」The 5th WSEAS International Conference on Applied Computer Science (ACOS '06), Hangzhou, China, April 16–18, 2006.
47. Tsun-Yu Hsiao, Ko-Hsu Su, Shyan-Ming Yuan, 「 A Scalability Model for Managing
Distributed-organized Internet Services,」 The 5th WSEAS International Conference on Applied Computer Science (ACOS '06), Hangzhou, China, April 16–18, 2006.
48. Mu-Chi Sung, Ming-Chun Cheng, Zhi Xin Fan, Ping-Jer Yeh, Shyan-Ming Yuan, Chia-Yuan Huang,
Lo-Chuan Hu, 「Failure impact on OpenAIS: an experimental evaluation, 」 Proceedings of the 5th WSEAS International Conference on Telecommunications and Informatics, Istanbul, Turkey, pp. 469–455, May 27–29, 2006.
49. Chi-Huang Chiu, Hsien-Tang Lin, Ping-Jer Yeh, Shyan-Ming Yuan, 「An Extensible Application
Platform for Heterogeneous Smart Home Appliances and Mobile Devices,」 Proceedings of the 5th WSEAS International Conference on Telecommunications and Informatics, Istanbul, Turkey, pp. 491–496, May 27–29, 2006.
50. Ping-Jer Yeh, Ruey-Shyang Wu, Shyan-Ming Yuan, 「 Automatic Injection of Management Mechanism to Applications,」 Proceedings of the 10th WSEAS International Conference on Computers, Athens, Greece, pp. 980–985, July 13–15, 2006.
51. Ping-Jer Yeh, Yung-Yu Chen, Winston Lo, Shyan-Ming Yuan, 「Extending Globus Toolkit Java WS
Core to Support Reliable Grid Messaging Services,」 Proceedings of the International Conference on Data Networks, Communications and Computers (DNCOCO 2006), Bucharest, Romania, Oct 2006.
52. Ping-Jer Yeh, Jie-Tsung Li, Shyan-Ming Yuan, 「Tracking the Changes of Dynamic Web Pages in
the Existence of URL Rewriting,」Proceedings of the Australasian Data Mining Conference (AusDM 06), Nov 29-30, 2006, Sydney, Australia.
53. Ruey-Shyang Wu, Kuo-Jung Su, Shyan-Ming Yuan, 「FJM2: A Decentralized JMS System, 」
Proceedings of the 2nd International Conference on Trends in Enterprise Application Architecture (TEAA 2006), Nov 29-Dec 1, 2006, Berlin, Germany.
54. Liang-Yen Lin, Ming-Chun Cheng, Shyan-Ming Yuan, 「 Standards-based User Interface
Technology for Universal Home Domination, 」Proceedings of the 2006 International Conference on Hybrid Information Technology (ICHIT 2006), Nov 9-11, 2006, Cheju Island, Korea.
55. Chun-Yuan Chen, Chi-Huang Chiu, Shyan-Ming Yuan, 「 MOM-based Home Automation
Platform,」 Proceedings of the 2006 International Workshop on Smart Home (IWSH06), Nov 10-11, 2006, Cheju Island, Korea.
56. Chia-Feng Lin, Tut Chi Io, Shyan-Ming Yuan, 「An Easy-To-Use Feed Middleware for Application
Development with RSS/Atom Feeds,」 International Conference on Convergence Information Technology 2007 (ICCIT07), November 21-23, 2007, Gyeongju, Korea.
57. Chi-Huang Chiu, Ruey-Shyang Wu, Chi-Io Tut, Hsien-Tang Lin and Shyan-Ming Yuan, 「Next
Generation Notification System: Integrating Instant Messengers and Web Service, 」 International Conference on Convergence Information Technology 2007 (ICCIT07), pp. 1781-1786, Gyeongju, Korea, Nov 2007.
58. Yung-Wei Kao, Pin-Yin Peng, Sheau-Ling Hsieh, Shyan-Ming Yuan, 「A Client Framework for
Massively Multiplayer Online Games on Mobile Devices, 」 International Conference on Convergence Information Technology 2007 (ICCIT07), pp. 48-53, Gyeongju, Korea, Nov 2007. 2.PATENT LIST
賈文康,「雙向雙向雙向 IP 分享裝置雙向 分享裝置分享裝置分享裝置」, Nov. 2007 (中華民國發明專利第 I291295 號) (註: 賈文康同學為後卓
越計畫第五子計畫博士生研究助理)
C. R. Wu and W. H. Tsai (2007). “A landmark-based vehicle location system and its technique,” Republic of China Patent, No. I 274971, 2007.
Y. C. Chuang, W. H. Tsai, and Y. C. Tsai (2007). “A method for protecting the content of vector graphics format,” Republic of China Patent, No. I 288892, 2007.
4. LIST OF WORKSHOPS/CONFERENCES HOSTED BY THE PROGRAM
[1] Workshop : Data mining and network applications workshop VIII, 2006/09/15-16, Taichung. (Participants : 30)
38
5. LIST OF PERSONAL ACHIEVEMENTS OF THE PIS
Good Paper Award (W. H. Tsai, Y. C. Chiu), Chinese Image Processing & Pattern Recognition Society 2004 Good Paper Award (W. H. Tsai, C. J. Lai), Chinese Image Processing & Pattern Recognition Society 2004 Good Paper Award (W. H. Tsai, L. Y. Weng), Chinese Image Processing & Pattern Recognition Society 2005
Good Paper Award (W. H. Tsai, C. Y. Hsu), Chinese Image Processing & Pattern Recognition Society 2006 Good Paper Award (W. H. Tsai, K. F. Chien), Chinese Image Processing & Pattern Recognition Society 2006
Best Paper Award (Y. C. Chen and W. Y. Chen) IEEE COMPSAC 2006, Sept. 2006, Chicago 2006 Good Paper Award (W. H. Tsai, I. S. Lee), Chinese Image Processing & Pattern Recognition Society 2007 National Digital Achieve Project Contest on Digital Watermarking Technology --- 1st Prize (W. H. Tsai and students) 2004
Journal Editors W. H. Tsai
Editor-in-Chief, Asian Journal of Health and Information Sciences (AJHIS) 2006~
Editor-in-Chief, Asian Journal of Management and Humanity Sciences (AJHIS) 2006~
S. S. Tseng
Co-Editor-in-Chief of Asian Journal of Health and Information Sciences(AJHIS) 2006~
6. LIST OF TECHNOLOGY TRANSFERS
7. LIST OF TECHNOLOGY SERVICES
W. H. Tsai
Member of Review Committee of National Award for Information Application Products
Member of Review Committee of National Network Security Projects (supervised by Executive Yuan) Member of Review Committee of III Innovative R&D Projects
Member of Review Committee of III R&D Group Achievements
S. S. Tseng
教育部─大專校院資訊人才培育先導型計畫-總聯盟計畫辦公室 計劃時程: 95 年 1 月 1 日到 95 年 12 月 31 日
考選部─國家考試電腦化測驗試題研發