ConMap: A Novel Framework for Optimizing Multicast Energy in Delay-constrained Mobile Wireless Networks
Xinzhe Fu
1, Zhiying Xu
2, Qianyang Peng
1, Jie You
2, Luoyi Fu
1, Xinbing Wang
1,2, Songwu Lu
3Department of {Computer Science1, Electrical Engineering2}, Shanghai Jiao Tong University, China Department of Computer Science, University of California, Los Angeles, USA3
Email: {fxz0114, xuzhiying, az950512, youjie9412, yiluofu, xwang8}@sjtu.edu.cn, slu@cs.ucla.edu
ABSTRACT
This paper studies the problem of optimizing multicast energy con- sumption in delay-constrained mobile wireless networks, where information from the source needs to be delivered to all the k des- tinations within an imposed delay constraint. Most existing works simply focus on deriving transmission schemes with the minimum transmitting energy, overlooking the energy consumption at the receiver side. Therefore, in this paper, we propose ConMap, a novel and general framework for efficient transmission scheme design that jointly optimizes both the transmitting and receiving energy. In doing so, we formulate our problem of designing min- imum energy transmission scheme, called DeMEM, as a combina- torial optimization one, and prove that the approximation ratio of any polynomial time algorithm for DeMEM cannot be better than
1
4ln k. Aiming to provide more efficient approximation schemes, the proposed ConMap first converts DeMEM into an equivalent di- rected Steiner tree problem through creating auxiliary graph gad- gets to capture energy consumption, then maps the computed tree back into a transmission scheme. The advantages of ConMap are threefolded: i) Generality– ConMap exhibits strong applicability to a wide range of energy models; ii) Flexibility– Any algorithm designed for the problem of directed Steiner tree can be embed- ded into our ConMap framework to achieve different performance guarantees and complexities; iii) Efficiency– ConMap preserves the approximation ratio of the embedded Steiner tree algorithm, to which only slight overhead will be incurred. The three features are then empirically validated, with ConMap also yielding near- optimal transmission schemes compared to a brute-force exact al- gorithm. To our best knowledge, this is the first work that jointly considers both the transmitting and receiving energy in the design of multicast transmission schemes in mobile wireless networks.
1 INTRODUCTION
With the surge of mobile data traffic, energy consumption in com- munication is rising radically in recent years. As reported by a survey [1] where Telecom Italia is said to be the second largest consumer in Italy, energy consumption of mobile communication is already ranking the top. Hence, energy saving becomes a crucial issue that receives considerable attention in the design and imple- mentation of mobile wireless networks.
As the majority of nodes are battery powered, a key problem of energy cost reduction in mobile wireless networks is to find a route with minimum total energy consumption for a given communica- tion session [2]. Under such circumstance, multicast turns out to be more efficient due to the increasing demand of information shar- ing in those communication scenarios. It outperforms unicast by aggregating multiple flows from the same source so that network
resources such as capacity and energy can be saved. However, as a traffic pattern that generalizes both unicast and broadcast, the issue of minimum-energy multicast is far more complicated com- pared to that of minimum-energy unicast, which is essentially a shortest path problem in static network.
Among existing works that indeed study the minimum-energy multicast problem, most of them [3, 4] are limited to static net- works, which fail to well characterize many realistic scenarios where users are manifested to be moving. Consequently, the potential energy saving brought with mobility is also overlooked. Another concern lies in that the state of art mostly focuses on optimizing the energy consumed only at the transmitting side [5, 6], but do not take into consideration the receiving energy, which, as suggested by empirical studies [7, 8], is as significant as the transmission cost.
Furthermore, due to the possible collisions and retransmissions in multicast/broadcast protocols, the energy consumption is not syn- onymous at transmitting and receiving sides. Interpreted in a more detailed way, the energy consumption of the transmitting side is usually determined by transmitting power, while at the receiving side, taking reliable MAC layer multicast as an example [9], the energy consumption may depend on the number of intended re- cipients as each transmission involves waiting for feedback from the receivers and resending the missing packets. Such inherent het- erogeneity between transmitting and receiving energy can also be found in many other real applications such as wireless multihop networks [10] and full-duplex energy harvesting infrastructures [11]. Therefore, it is difficult to directly embed the receiving en- ergy into existing algorithms. These motivate us to propose a gen- eral framework that jointly optimizes both the transmitting and receiving energy in mobile wireless networks.
In addition to the energy, our framework needs to incorporate the latency, another crucial performance metric, of which the de- mand varies in different scenarios. Real time applications such as video conferencing and traffic monitoring require the network latency to be fairly small, whereas in other networks (e.g. satel- lites network), network delay is not so critical. Hence, it is rea- sonable to add to the network a delay constraint, meaning that all the packages must be delivered within a time length of D. Based on that, all the above cases can be well characterized by simply adjusting the size of D. Following this, there emerge a flurry of studies that quest for the relationship between delay constraint and other network performances. For instance, Small et al. show that relaxing delay constraint can bring about energy reduction or throughput gain [12]. Ra et al. propose an online algorithm for achieving near optimal energy-delay tradeoff in smartphone appli- cations [13]. However, current literature on energy-delay tradeoff is limited to some specific applications, where the main goal is to
empirically optimize the tradeoff without the corresponding the- oretical exploration [13, 14]. Under such circumstance, two ques- tions still remain open:
• How hard it is to achieve the minimum multicast energy under delay constraint in mobile wireless networks?
• How should we efficiently design such optimal multicast transmission schemes with minimum energy consumption in delay-constrained mobile wireless networks?
We therefore present a first look into the problem of multicast en- ergy consumption optimization in delay-constrained wireless mo- bile networks, with both transmitting and receiving energy consid- ered. Specifically, we consider a multicast session with k destina- tions selected in advance from all the n nodes in the network. With time divided into equal slots, we impose a delay constraint D on the multicast session in the sense that packets from the source must be delivered to all the k destinations within D time slots. We aim to efficiently design multicast routing schemes that achieve the min- imum transmitting and receiving energy. Unlike traditional multi- cast in wired network, which is essentially a minimum Steiner tree problem, the issue becomes more complicated when it comes to mobile wireless mulitcast. First, network topology is time-varying due to the mobility of nodes. This makes the task of designing an optimal transmission scheme rather challenging since the same tree may correspond to many different transmission schemes. Sec- ond, the “broadcast nature” in wireless communication, to a large extent, complicates the calculation of energy consumption since it cannot be obtained by simply taking the summation of edge weights in a minimum Steiner tree problem.
We approach the problem of multicast energy optimization in delay-constrained wireless mobile networks by formulating it as a combinatorial optimization problem called the DeMEM problem.
Upon theoretical analysis on the approximation hardness of the De- MEM problem, we propose a novel energy optimizing framework called ConMap. Particularly, ConMap realizes multicast transmis- sion in three major steps. First, it constructs an intermediate graph resulted from snapshots of graph states taken under D different slots and auxiliary gadgets for transmitting and receiving energy;
Second, it builds a Steiner tree in that intermediate graph spanning all the destinations; Finally, it maps the obtained tree in that inter- mediate graph back into a multicast transmission scheme in the original network. The proposed ConMap flexibly allows us to em- bed any directed Steiner tree algorithm into it, and turns out to be efficiently implementable with only a polynomial time complexity as well as preserving the approximation ratio of the underlying di- rected Steiner tree algorithms. Our main contributions are listed as follows:
• We prove that the approximation ratio of DeMEM prob- lem in mobile wireless networks cannot be better than
1
4ln k for any polynomial-time algorithm, which is an even stronger result than demonstration of its NP-hardness.
• We propose ConMap, a novel framework that jointly opti- mizes the transmitting and receiving energy in the multi- cast session and harnesses the results of existing directed Steiner tree algorithms to achieve a good approximation for DeMEM. Our framework does not rely on any specific characterization of energy consumption and is thus appli- cable to a broad range of applications.
• We empirically evaluate the performance of ConMap on real datasets, where ConMap exhibits good applicability to real network traces and yields near optimal transmis- sion schemes compared to a brute-force exact algorithm.
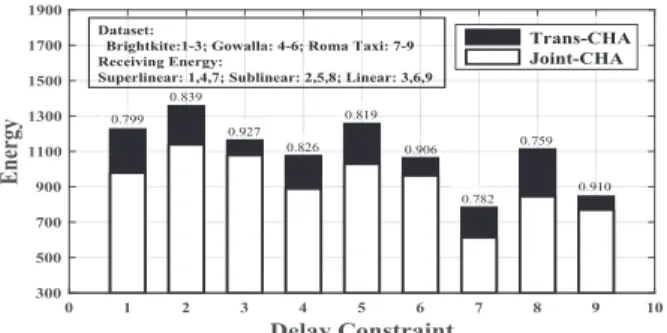
We also demonstrate the significance of jointly optimizing transmitting and receiving cost by showing that incorpo- rating receiving energy into ConMap leads to transmis- sion schemes of lower energy consumption.
The rest of this paper is organized as follows: Section 2 is con- tributed to literature review and we introduce our network and en- ergy models in Section 3. We prove the approximation hardness of DeMEM in Section 4. The approximation framework, ConMap, is proposed in Sections 5 and 6. We conduct simulations to evaluate the performance of our framework in Section 7 and give conclud- ing remarks in Section 8.
2 RELATED WORK
In the literature, the problem of transmitting energy consumption optimization is referred to as Minimum-Energy Multicast (MEM) problem, and has been extensively studied in static networks. Since both MEM problem and Minimum-Energy Broadcast (MEB) prob- lem, a special case of MEM, are proven to be NP-hard [15–17], the community focuses on designing efficient heuristics. Wieselthier et al. study the MEM problem using the same approach as the MEB problem and propose three greedy heuristics [3, 16]. Wan et al. prove that both MEM problem and MEB problem can be approximated within constant ratio [4, 18]. Liang et al. propose approximation algorithms for MEB problem where the nodes have discrete transmission power levels [17]. Existing works also relate to the extensions of MEM and MEB such as MEM and MEB prob- lem with reception cost [9, 19], duty-cycle-aware MEM [6] and delay-constrained MEM [5]. Furthermore, energy efficient mul- ticast/broadcast algorithms for specific applications is also an ac- tive topic [20]. However, as noted earlier, prior literature only fo- cuses on the minimization of transmitting energy, relies on the assumption that the receiving energy is directly proportional to the number of receivers [19] or considers the receiving energy in the context of network-wide broadcast [9]. In contrast, the pro- posed framework in our work jointly minimizes the transmitting and receiving energy, with applicability to more general scenarios.
In spite of a flurry of works addressing the issue of MEM in static networks, little is known about the energy consumption in mobile scenarios. As two exceptions, Wu et al. [21] study MEM in mobile ad hoc networks using network coding, but their focus is on energy gain from network coding rather than mobility. Guo et al. [2] propose an efficient Distributed Minimum Energy Multicast algorithm, but how delay constraint affects the energy consump- tion is not considered. In many cases where the timely delivery of messages is not of primary concern, relaxing delay constraint can bring gain in many aspects such as capacity and energy [12].
Considerable efforts have been made to investigate the theoretical delay-capacity relationship in large scale static and mobile wireless networks [22–24].
Despite those dedications to multicast energy optimization, as far as we know, there are no prior work, other than ours, that con- siders the problem of jointly optimizing transmitting and receiving energy of multicast in mobile wireless networks.
3 MODELS AND ASSUMPTIONS 3.1 Mobile Wireless Network Model
We adopt the mobile wireless network model in [25] that can be reproduced as follows: time is divided into discrete time slots and the nodes remain static within a time slot. With reasonable predic- tion of nodes’ future movements, a mobile network can be modeled as a sequence of static graphsG = {G1,G2, . . .}, with each static graph interpreted as a snapshot of nodes’ positions in a time slot.
Specifically, denoted as Gt(V, Et,wt) ∈ G, each static graph is a weighted directed graph with V ={v1,v2, . . . ,vn} corresponding to the n network nodes. Et ⊆ V × V denotes the edge set and wt : Et 7→ R+ assigns each edge a corresponding weight. An edge e = (vi,vj) ∈ Et means that vi can send messages to vj in time slot t with minimum transmission power wt(e).
3.2 Multicast Model
We consider a wireless multicast session with a source s ∈ V and destination nodes set T ⊆ V in mobile network G. We impose an integral delay constraint D on the multicast session in the sense that the message must be delivered to all nodes in T within D slots.
Therefore, for a mulicast session, we only need to consider the net- work snapshots within the delay constraint. Hence, in the sequel, we truncate the mobile networkG into D static graphs denoted as {G1,G2, . . . ,GD}.
Since we aim to design a minimum energy transmission scheme for a delay-constrained multicast session in a mobile wireless net- work, we next formally define the notion of transmission scheme.
We refer to the process of some transmitter transmitting message to the intended receivers as a transmission. A transmission scheme specifies the transmitter, intended receivers, timing and transmis- sion power of each transmission.
Definition 3.1. A transmission scheme π⊆ V ×2V×{1, . . . , D}×
R+is a sequence of tuples{(u,V′, t,p)}, where a tupleτ = (uτ,Vτ, tτ,pτ)∈ π denotes that node uτ should transmit to the nodes in Vτ at time slot tτwith power pτ.
Also, in a transmission scheme π , we define a node to be “reached in time slot t” in a recursive way as follows: (i) the source s is reached in time slot 1, (ii) if a node is reached in time slot t, then it is reached in time slot t′for all t′ ≥ t, and (iii) if a node u is reached in time slot t and (u,V′, t,p) ∈ π, then all nodes in V′are reached in time slot t.
Now, we give the definition of reasonable transmission scheme and will restrict our consideration to the set of reasonable trans- mission schemes in the sequel. Intuitively, a scheme is said to be reasonable if it is feasible, without redundancy and qualified for the delay constrained multicast session.
Definition 3.2. A transmission scheme π is reasonable if it ob- serves the following conditions: (i) For all τ = (u,V′, t,p) ∈ π, it satisfies that u is reached in t and for allv∈ V′, e = (u,v) ∈ Etand p≥ maxe =(u,v)∈Et,v ∈V′{wt(e)}. (ii) For all τ = (u,V′, t,p) ∈ π, no node in V′is reached before t. (iii) All nodes in T are reached in time slot D.
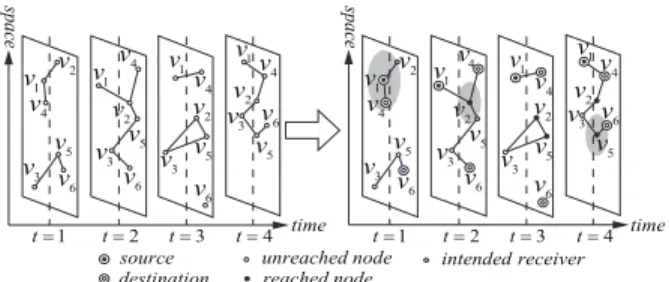
Figure 1 illustrates an example of a mobile wireless network, along with a reasonable transmission scheme proposed under a multicast session in the network.
time
space
1
t = t =2 t =3 t =4 time
space
source
destination reached nodeunreached node intended receiver
v1 v1
v1 v1
v2
v2
v2
v2
v3 v3 v3
v3
v4
v4
v4
v4
v5 v5 v5 v5
v6
v6
v6
v6
1
t = t =2 t =3 t =4
v1 v1
v1 v1
v2
v2
v2
v2
v3 v3 v3
v3
v4
v4
v4
v4
v5 v5 v5 v5
v6
v6
v6
v6
Figure 1: A mobile wireless network and a reasonable transmis- sion scheme for a multicast session in the network; (a) a mobile wireless network (a sequence of snapshots); (b) a reasonable trans- mission scheme for a multicast session in the network with v1being the source, v4, v6being the destinations and a delay constraint of four time slots.
3.3 Energy Model
For a transmission specified by tuple τ = (uτ,Vτ, tτ,pτ), we model the energy consumption of this transmission as
E(τ ) = pτ+f (|Vτ|),
where the first part denotes the energy consumed by the transmit- ter side and f is a function of the number of intended receivers that can represent the receiving energy. Note that our framework does not restrict to any specific f and the choice of f may depend on practical settings [7, 9], which will be specified in Section 6. It follows that the energy consumption of a transmission scheme π is given by:
E(π) =∑
τ∈πE(τ ).
Now we formulate the DeMEM problem as follows.
Definition 3.3. (The DeMEM Problem) Given a mobile wireless networkG = {G1,G2, . . . ,GD}, a source node s, a set T of destina- tion nodes, and a delay constraint D, the goal is to find a reasonable transmission scheme with minimum energy consumption.
We note that in the definitions above, we make the following characterizations of communication in mobile wireless networks.
First, we assume that the transmission rate is much faster than that of the nodes’ mobility. In other words, it is feasible to transmit multiple times to different receivers in a single time slot. This may not be desirable if we only consider transmission cost. However, it can bring possible gain when we take the receiving energy into ac- count. Second, we can utilize the wireless broadcast nature during communications, i.e., different nodes can be reached within one transmission as long as the transmission power is large enough.
4 APPROXIMATION HARDNESS
In this section we analyze the approximation hardness of DeMEM problem. We show that even without receiving energy (i.e., f = 0), the DeMEM problem cannot be approximated within a logarit- mic factor in polynomial time by reduction from acyclic directed Steiner tree problem.
Theorem 4.1. The DeMEM problem cannot be approximated within a factor better than14ln k unless NP⊆ DTIME(npolylogn), where k is the number of destinations.
Proof. Consider an instance of acyclic directed Steiner tree problem defined by an acyclic directed graph G(V, E) and an edge cost function d : E → R+, a root r ∈ V and a set of vertices S ⊆ V with |S| = k. The goal is to find a minimum cost Steiner tree (arborescence) covering all vertices in S. Based on these, we
will construct an instance of the DeMEM problem by encoding the graph information into a mobile wireless network.
To begin with, we do a topological sort on the graph and get a sequence of nodes following the topological order. Without loss of generality, we only consider the nodes that do not lie before the root r in the sequence, i.e., a truncated sequence{r = v0,v1, . . .}.
Then, we sort the relevant edges according to the order of their out- going nodes in the truncated sequence into{e0, e1, . . . , el}. From this sequence, we will build a mobile wireless networkG.
First, we set V′as the set of nodes that appear in the truncated sequence. Then, for any generic edge ei = (ui,vi)in the edge sequence, we add (ui,vi)into Gi(V′, Ei,wi)and set its cost as wi(e) = d(e). The constructed networkG consists of static graphs {G1,G2, . . . ,Gl} where each static graph has only one edge. Fur- ther, we designate r as the source, the nodes corresponding to the vertices in S as the destinations, and set the delay constraint D = l, the receiving energy function as zero. By above procedures, we have an instance of DeMEM problem and now we show that it is equivalent to the original acyclic directed Steiner tree instance.
For a Steiner tree in G, if it contains edges{ey1, ey2, . . . , eyj}, then obviously the corresponding transmission scheme with tu- ples{(uy1, {vy1},y1,d(ey1)), . . . , (uyj, {vyj},yj,d(eyj))} is reason- able. Conversely, consider a reasonable transmission scheme for the mobile wireless network. Since in each time slot there only exists one edge, each tuple in a reasonable transmission scheme corresponds to some edge in the acyclic graph G. And from the requirements for the scheme to be reasonable, it follows that those edges form a Steiner tree in G. Most importantly, the energy con- sumption of a reasonable transmission scheme equals to the cost of its corresponding Steiner tree and all the reduction processes are implementable in polynomial time. Therefore, the above reduction is an approximation preserving reduction. Since for a fixed k there is no efficient14ln k approximation for acyclic directed Steiner tree problem unless NP⊆ DTIME(npolylogn) [26], we obtain the same approximation hardness for DeMEM problem. □
5 THE APPROXIMATION FRAMEWORK:
CONMAP
Since by Theorem 4.1, even approximating the DeMEM problem better than a logarithmic factor is NP-hard, it is unlikely that the DeMEM problem can be solved in polynomial time. Therefore, we need to design efficient approximation scheme to trade complexity for the optimality of the transmission scheme. In this section, we therefore propose a novel approximation framework – ConMap, which effectively achieves such tradeoff by transforming our De- MEM problem into a directed Steiner tree problem.
Given a specific DeMEM problem instance, ConMap first con- verts the mobile wireless network graph to an intermediate graph, then adopts established algorithms to compute an approximate minimum Steiner tree in the intermediate graph, and finally uses the computed Steiner tree to construct a near optimal transmission scheme for the original DeMEM problem. As we will disclose in the sequel, all the conversion processes are efficiently implementable, with a polynomial time complexity and the size of the intermedi- ate graph being polynomial to that of the original network graph.
Also, we can embed different algorithms for directed Steiner tree to obtain various performance guarantees.
Here for clearance and convenience, we first consider DeMEM problem without receiving energy and will demonstrate in Section 6 how to integrate the receiving energy into the optimization.
5.1 Conversion into an Intermediate Graph
To derive an energy efficient transmission scheme, we firstly need to generate an intermediate graph so that the mobility of nodes and the broadcast nature of wireless environment can be captured.
Note that the intermediate graph is a directed layered graph, with each layer corresponding to the network at a certain time slot.
Given a mobile wireless networkG = {G1,G2, . . . ,GD}, before we construct an intermediate graph, we adopt previous assump- tion [17] that there are pv adjustable transmitting power levels for a generic node v. Note that even for nodes with infinitely ad- justable transmitting power, there are at most (|V |−1) power levels that need to be taken into consideration. Upon the power level as- signment, we can now construct an intermediate graph at layer t by applying to all nodes the procedures listed as follows, with the resulting layer denoted as Lt:
(1) Create a vertex in Lt for each node in Gt and call these vertices “original vertices”.
(2) For the pupower levels of node u, add a set of vertices de- noted as{
wu1,wu2, . . . ,wupu
}to the graph Lt. Hereby, without ambiguity, we will also refer to these vertices as
“power levels” and their labels as their corresponding trans- mission powers.
(3) Add a directed edge from u to each of its power levels and set the edge’s weight as the transmission power consumed by u when transmitting at that power level.
(4) Add edges from wu jto all the vertices that can be covered by u when transmitting at power level j and assign their weights as zero. Formally, a vertex v can be covered by u at power level j if and only if∃e = (u,v) ∈ Et and wt(e)≤ wu j.
Upon the construction of D layers that correspond to D time slots, we connect them into the intermediate graph. Starting from L1, we establish the relation of adjacent layers by adding zero-weight edges between the original vertices in them that correspond to the same node in different time slots. These edges resemble the tem- poral links in the model of [25], with their directions following the chronological order. With all the operations above, we complete the construction of the intermediate graph denoted asL, which, in the sequel, will be demonstrated to well capture both node mo- bility and the broadcast nature of wireless networks.
5.2 Computation of the Steiner Tree
We designate in L1the vertex that corresponds to the source node in the network as the root r and in LD the original vertices that correspond to k destinations as terminals. Therefore, the DeMEM problem is equivalent to establishing a minimum Steiner tree rooted at r spanning all k terminals in the intermediate graphL. Recall that in the intermediate graph, the weight of edges from original vertices to their power levels equals to the transmission power.
And the weights of edges from power levels to the original ver- tices they cover are zero. It follows that the weight assignment ensures that the summation of the weights of edges in a Steiner tree characterizes the energy consumption of a wireless multicast
session. In addition, the directed layering structure of the inter- mediate graph captures the nodes’ mobility and ensures that the Steiner tree inL will be generated following the chronological or- der. Hence, the intermediate graphL is an accurate abstraction of mobile wireless network.
Since our task now becomes computing the minimum Steiner tree in a directed graph, we can adopt existing efficient approxi- mate algorithms [27, 28] to fulfill our purpose. For completeness, we present one as the following lemma.
Lemma 5.1. There exists an algorithm that provides an l(l− 1)k1l approximation to Steiner tree problem in directed graph in time O(nlkl+ n2k + nm)where n is the number of vertices, k is the number of ter- minals and m is the number of edges. Specifically, set l = log k, we get an 2 log2kapproximation in time O((nk)log k)[27, 29].
Through implementation of the Steiner tree algorithm, we ob- tain an approximate Steiner tree in our intermediate graph, which will serve as the basis for the construction of transmission scheme.
5.3 Mapping into the Transmission Scheme
Based on the Steiner tree we computed, we proceed to design the corresponding transmission scheme. First, we present a crucial property of the conversion process.
Lemma 5.2. For an instanceM of DeMEM problem, let M′be the directed Steiner tree instance converted fromM by ConMap frame- work. Each reasonable transmission scheme inM corresponds to a valid Steiner tree inM′, and the energy consumption of the scheme equals to the cost of its corresponding Steiner tree.
Proof. We describe a procedure that maps a reasonable trans- mission scheme π forM to an edges set ET that forms a Steiner tree forM′. For each tuple (u,V′, t,p) ∈ π, we add the edge from uto the power level corresponding to p in layer Lt together with the edges from the aforementioned power level to the original ver- tices of vertices in V′of Lt into ET. Finally, we add the neces- sary inter-layer edges into the set. The edge set constructed by the above procedure will be a valid Steiner tree forM′. In the sequel, we refer to the Steiner trees that have corresponding transmission
schemes as being in canonical form. □
From the proof of Lemma 5.2, we note that the energy con- sumption of any scheme is no less than the cost of the optimal Steiner tree in the constructed instance. Therefore, a transmission strategy mapped from an α-optimal Steiner tree is guaranteed to be an α-optimal transmission scheme. However, the Steiner tree computed in the intermediate graph may exhibit “aberrant phe- nomena” so that it has no corresponding reasonable transmission scheme. Hence, in the final phase of ConMap, before we map our computed Steiner tree back into a transmission scheme, we need to prune it into canonical form.
The possible aberrant phenomena that can cause a Steiner tree ET not to have its corresponding reasonable transmission scheme are: (i) there is an edge from an original vertex to one of its power levels in ET, but no edge goes out of that power level, and (ii) there are edges from different power levels to multiple original vertices that correspond to the same network node, leading to redundant transmissions. To deal with the first case, we delete those edges from original vertices to their “dangling” power levels. For the sec- ond case, we keep the edge with the original vertex in the earliest
power level original node source destination
t =1
2 t =
3 t = 1( )
v s
1( ) v s
1( ) v s
v2
v2
v2 v3
v3
v3
4( )1 v d
4( )1 v d
4( )1 v d 5( )2 v d
5( )2 v d
5( )2 v d w12
w11
w21 w22 w23
w31 w32
w51 w52
Figure 2: Illustration of ConMap on a five-node mobile network with a delay constraint of three time slots.
time slot and delete other redundant edges. Then, we add neces- sary inter-layer edges to reconnect the resulting edge set into a Steiner tree. Note that the above two procedures do not increase the cost of the resulting Steiner tree. Therefore, the pruned Steiner tree can only be closer to optimal.
After describing the three main stages of the framework, we summarize ConMap in Algorithm 1.
Algorithm 1: ConMap Steiner Framework for DeMEM Input: An instance of the DeMEM problemM Output: A transmission scheme π forM
1 Based onM, construct its corresponding intermediate graph L and form an instance of directed Steiner tree M′.
2 Compute a (approximate) minimum Steiner tree ET inL for M′.
3 Prune ET into canonical form.
4 Convert the pruned ET to its corresponding transmission scheme π forM.
5.4 Illustration of ConMap
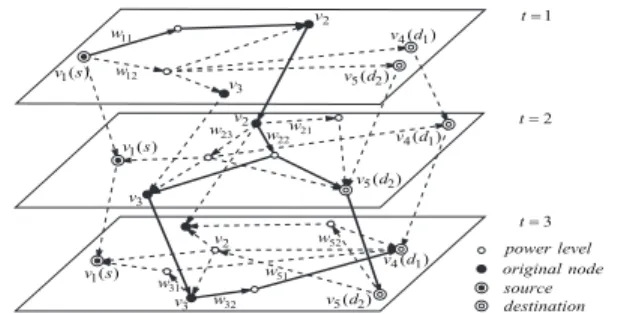
Now we illustrate our proposed framework, ConMap, using an ex- ample of a five-node mobile network, where multicast is between one source and two destinations with a delay constraint of three time slots. Figure 2 shows the intermediate graph of the network.
Note that we omit some of the power levels due to space limitations.
As shown in the figure, v1corresponds to the source, v4and v5
correspond to the destinations. The solid lines denote the Steiner tree the algorithm computes in the intermediate graph. Here, the transmission scheme is{(v1, {v2}, 1,w11), (v2, {v3,v5}, 2,w22), (v3, {v4}, 3,w32)}, which can be interpreted as follows: In the first
time slot, the source transmits to v2using power w11; In the sec- ond time slot, v2transmits to v3and v5using power w22; In the last time slot, v3transmits to v4using power w32.
5.5 Performance Analysis of ConMap
We proceed to provide analysis on the performance of the Con- Map framework in terms of running time and approximation ratio.
Without loss of generality, we assume the approximation guaran- tee of embedded algorithms for directed Steiner tree only depends on the number of terminals in the graph [26, 27].
Theorem 5.3. For a mobile network with n nodes, let k be the number of destinations and D be the delay constraint. Suppose the di- rected Steiner tree algorithm embedded in ConMap runs inT (|V |, |E|,k) time and achieves an approximation ratio of д(k) on graph G(V, E).
Then ConMap returns a transmission scheme of which the energy cost is less than д(k) times the optimal one in time O(T (Dn2, Dn3)).
Proof. First, we focus on the time complexity of ConMap. In the first phase, since there are at most (n− 1) power levels for each node and the intermediate graph contains D layers, it takes a time of O(Dn3)to construct such an intermediate graph. Note that the intermediate graph has at most Dn2vertices and Dn3edges.
Hence, the time complexity of phase 2 is O(T (Dn2, Dn3)). As for phase 3, the pruning and the converting process can both be done by traversing the tree, which takes O(Dn3)time. Hence, the total running time is O(T (Dn2, Dn3)). Obviously the approximation ratio of the whole framework is determined by the second phase.
By Lemma 5.2 and the fact that the number of terminals in the intermediate graph equals to the number of destinations we con- clude that the approximation ratio of the proposed framework well preserves that obtained under the Steiner tree algorithm. □
6 INTEGRATION OF RECEIVING ENERGY
In this section, we illustrate how to integrate the optimization of receiving energy in our ConMap framework. Adopting the same assumption in [9], we consider the receiving energy of a multicast transmission grows sublinearly, linearly or superlinearly with re- spect to the number of intended receivers. The reasonability of this assumption is supported by Johnson et al. [9] through a theoretical abstraction of practical scenarios with different underlying proto- cols. Accordingly, we also divide the optimization technique into three regimes where the receiving energy function f is sublinear, linear or superlinear respectively.
6.1 Linear Receiving Energy Functions
In this case, the receiving energy of a transmission is directly pro- portional to the number of receivers. Hence, we can suppose f (k) = Ak. The optimization combined with receiving energy can be eas- ily integrated into the framework by setting the weights of all the edges from power levels to original vertices in the intermediate graph as A instead of zero and keeping the conversion procedures and the pruning process unchanged. We can easily verify that this modification does not influence the complexity and approximation ratio of the framework.
6.2 Sublinear and Superlinear Receiving Energy Functions
When the receiving energy is not linear with regard to the num- ber of receivers, the straightforward modification made in the case of linearity is not applicable. We therefore present a new way to tackle this and merge the consideration of sublinear and superlin- ear receiving energy into our ConMap framework.
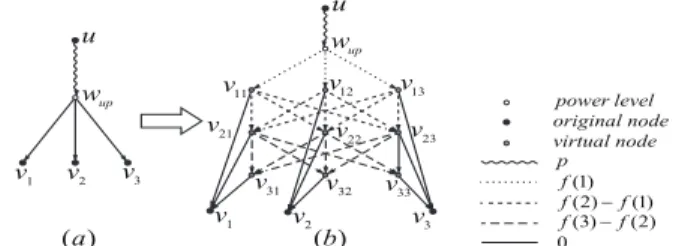
Construction of intermediate graph: The main idea lies in that instead of adding a simple edge from each power level of trans- mitters to their receivers, we create gadgets in the intermediate graph that charges the Steiner trees for the cost corresponding to receiving energy.
For a power level wup (recall the definition in Section 5.1) of original vertex u that covers k receiving nodes v1,v2, . . . ,vk, the construction of the gadget is as follows. First, we create k rows of new vertices, with each row containing k vertices, which, in the sequel, will be referred to as “virtual vertices”. We denote the ver- tices in row i as vi1,vi2, . . . ,vik. Second, we add a zero-weight edge from each virtual vertex to its corresponding receiving node (e.g, from v11,v21, . . . ,vk 1to v1). Then, for the virtual vertices in two adjacent rows, we insert edges between them such that
v11 v12 v13 v21
v22 v23 v31 v32 v33
power level original node virtual node
(1)(2) (1) (3) (2) 0
ff f f −f
−
u
u
v1 v2 v3
p
v1 v2 v3 wup
wup
( )a ( )b
Figure 3: Illustration of the gadgets for receiving energy: (a) the original gadget in ConMap without receiving energy for a power level of original vertex u and the nodes v1, v2, v3that u can cover transmitting at power p. (b) the corresponding gadget ConMap cre- ates for this power level of u when considering the receiving energy.
the subgraph formed by the nodes in each two adjacent rows is a complete bipartite graph. The direction of these edges is from the row with lower index to the row with higher index. And we set the weights of all the edges between row i and row i + 1 as f (i + 1)− f (i). Finally, we add edges from vp to all the virtual vertices in the first row and set their weights as f (1). An example of the gadget is shown in Figure 3.
We justify the above construction by proving a similar argu- ment as Lemma 5.2 that each reasonable transmission scheme cor- responds to a valid Steiner tree in the intermediate graph with the cost of the tree equal to its total energy consumption. Indeed, for a tuple τ ={uτ, {v1,v2, . . . ,vm},pτ, tτ}, it can be encoded as a sub- graph consisting of an edge from the original vertex corresponding to uτto its power level pτ in Lt, edges that form a path traversing one of each receiver node’s corresponding virtual nodes once in the gadget on some row (e.g. v11,v22, . . . ,vmm) and edges from the traversed virtual vertices in the gadget to their corresponding receiver nodes (e.g. (v11,v1), (v22,v2), . . . , (vmm,vm)). It is easy to verify that the total weight of this subgraph equals to the en- ergy consumption of the transmission. And also as in the proof of Lemma 5.2, we add necessary edges between different layers, relating a reasonable transmission scheme to a Steiner tree.
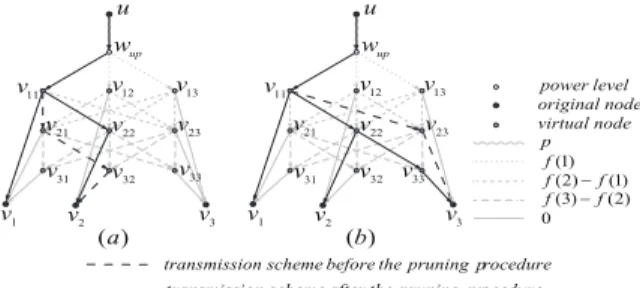
After the computation of a Steiner tree in the intermediate graph, however, the existence of the gadgets complicates the pruning pro- cess. In addition to the pruning procedures mentioned in the pre- vious section, we also need to consider the aberrant phenomena caused by the edges in the gadgets. The pruning process is demon- strated in Figure 4 using two illustrative cases. Taking Figure 4(b) for example, the constructed steiner tree entails two receivers v1
andv2in the transmission but the edges that the algorithm chooses in the gadget are (v11,v1), (v11,v22), (v22,v2), (v11,v23), (v23,v3) instead of the path (v11,v22), (v22,v33)and edges (v11,v1), (v22,v2), (v33,v3), whereas the latter are the ones that correspond to a legit-
imate transmission scheme. Therefore, we incorporate searching such aberrant subgraphs in the gadgets and correct them to the legitimate ones in the pruning process of the framework.
Performance Analysis of ConMap with receiving energy:
In terms of the change of cost of the tree brought by the pruning process, since when f is sublinear, f (i + 2)− f (i + 1) ≤ f (i + 1)− f (i) for all i and when f is superlinear, f (i + 2) − f (i + 1) ≥
f (i + 1)− f (i) for all i, the pruning process does not increase the cost of the resulting tree when f is sublinear and increases the cost to a factor of at mostk f (1)f (k ) when f is superlinear. For com- plexity issues, an m-receiver gadget contains at most m2vertices
v11 v12 v13
v21 v22 v23
v31 v32 v33
v11 v12 v13
v21 v22 v23
v31 v32 v33
transmission scheme before the pruning procedure transmission scheme after the pruning procedure
u u
power level original node virtual node
(1)(2) (1) (3) (2) 0
ff f f −f
−
v1 v2 v3 v1 v2 v3
wup wup
p
( )b ( )a
Figure 4: Illustration of two pruning processes of converting the computed Steiner tree in the intermediate graph into canonical form. (a) and (b) are two cases of the conversion.
and m3edges. Hence, all the gadgets in the intermediate graph contain at most Dn4vertices and Dn5edges. Hence, if we use a Steiner tree algorithm with a time complexity ofT (|V |, |E|,k) and an approximation ratio of д(k), our Conmap framework will yield a д(k)-approximation of the optimal transmission scheme for sub- linear cost functions and aд(k )f (k )
k f (1) -approximation for superlinear cost functions in a time complexity of O(T (Dn4, Dn5,k)).
6.3 An Alternative Gadget Construction
As mentioned in the previous section, ConMap framework increases the approximation ratio of the embedding Steiner tree algorithm by a factor up tok f (1)f (k ) when the receiving energy function is su- perlinear. Therefore, we propose a second method of constructing gadgets in ConMap to capture the receiving energy that can elim- inate this factor for superlinear receiving energy functions. The method produces polynomial number of additional nodes when the maximum number of neighbors of a node in the network is logarithmic to the total number of nodes.
The construction works as follows. Starting from the original intermediate graph constructed in Section 5, for each power level, we add a new vertex for each possible combination of receiving nodes and refer these vertices as receiving levels. Then, we add edges from each power level to all their corresponding receiving levels and from the receiving levels to all their corresponding re- ceivers. The first set of edges are assigned with weights equal to the receiving energy, i.e, f (k) for a receiving level with k receivers.
And the second set of edges are zero-weighted ones.
Now, we justify the validity of the construction. In the gadgets constructed as above, a tuple (u,V′, t,p) in a transmission scheme corresponds to a subgraph consisting of an edge from the original vertex associated with u to its power level corresponding to p in Lt, an edge from the aforementioned power level to the receiving level corresponding to V′as the intended receivers and edges from the receiving level to all the vertices associated with nodes in V′ at time slot t. For the pruning procedure, apart from the first one mentioned in the previous section, we also need to guarantee that the receiving levels included in the computed Steiner tree is con- nected to all its receivers. If not, we can replace this receiving level with the receiving level that corresponds to the set of connected re- ceivers only. This, again, will not increase the cost of the resulting Steiner tree, and thereby the approximation ratio can be preserved.
In terms of the time complexity of the framework, suppose the embedded Steiner tree algorithm runs inT (|V |, |E|,k) time. In this case, the number of additional vertices in a gadget is of O(2∆).
Hence, the total time complexity of ConMap that applies this alter- native gadget construction method becomes O(T (2∆Dn2, 2∆Dn3)).
Therefore, this method is suitable for implementation only when the maximum degree of a node is no larger than logarithmic to the total number of nodes in the network. An example of this alterna- tive construction is illustrated in Figure 5.
power level original node receiving level
(1)(2) 0(3)
ff f
v1 v2 v3
u
1, ,2 3
p p p
p1 p2 p3 u1
w wu2 wu3
Figure 5:An alternative construction of receiving gadgets.
7 EXPERIMENTS
In this section, we empirically evaluate the performance of Con- Map framework. We discuss our experimental settings in Section 7.1 and present detailed empirical results in subsequent sections.
7.1 Experimental Setup
We validate the effectiveness of our ConMap framework based on three real datasets. The basic descriptions of the three data sets are presented as follows.
• Brightkite Social Network [30]: Brightkite is a location- based networking service provider where users share their locations by checking-in. We consider the users as net- work nodes and use their location information at different timestamps to create mobility trace.
• Gowalla Social Network [30]: Gowalla is a location- based social networking website where users share their locations by checking-in. Similarly, we consider users as network nodes and use their location information to cre- ate mobility trace.
• Roma Taxi [31]: This dataset contains mobility traces of taxi cabs in Rome, Italy. It contains GPS coordinates of approximately 320 taxis collected over 30 days.
Parameter setting: For each dataset, we extract ten groups data of 50 nodes in 100 time slots and normalize the distance be- tween nodes into the range of 10 to 5000 for consistency. We designate one source and four/six destinations and set the delay constraint of the multicast session from 10 to 100 time slots. Due to space limitations, we defer all the graphical representation of results in the scenarios of four destinations to Appendix A. Fur- thermore, for the energy model, we adopt a widely used assump- tion that the transmission energy is α power of the transmission range [3, 4]. And for receiving energy, we select f (k) = 50k, f (k) = 100k12 and f (k) = 20k2where k is the number of in- tended receivers in a transmission as the representatives of linear, sublinear and superlinear functions of receiving energy, respec- tively. Note that we are interested in the relative quantity of en- ergy consumption, and thus we do not relate the amount of energy consumption to specific physical quantity.
Algorithms used for performance comparison: To justify the performance and flexibility of our ConMap framework, we embed three different algorithms in ConMap for computing the
Delay Constraint
10 20 30 40 50 60 70 80 90 100
Energy
400 600 800 1000 1200 1400 1600 1800 2000 2200
2400 ConMap-CHA
ConMap-SPT ConMap-MST Brute Force
Dataset: Brightkite Receiving Energy: Linear
(a)
Delay Constraint
10 20 30 40 50 60 70 80 90 100
Energy
400 600 800 1000 1200 1400 1600 1800 2000 2200
2400 ConMap-CHA
ConMap-SPT ConMap-MST
Dataset: Brightkite Receiving Energy: Sublinear
(b)
Delay Constraint
10 20 30 40 50 60 70 80 90 100
Energy
400 600 800 1000 1200 1400 1600 1800 2000 2200
2400 ConMap-CHA
ConMap-SPT ConMap-MST
Dataset: Brightkite Receiving Energy: Superlinear
(c)
Delay Constraint
10 20 30 40 50 60 70 80 90 100
Energy
400 600 800 1000 1200 1400 1600 1800 2000 2200
2400 ConMap-CHA
ConMap-SPT ConMap-MST Brute Force
Dataset: Gowalla Receiving Energy: Linear
(d)
Delay Constraint
10 20 30 40 50 60 70 80 90 100
Energy
400 600 800 1000 1200 1400 1600 1800 2000 2200
2400 ConMap-CHA
ConMap-SPT ConMap-MST
Dataset: Gowalla Receiving Energy: Sublinear
(e)
Delay Constraint
10 20 30 40 50 60 70 80 90 100
Energy
400 600 800 1000 1200 1400 1600 1800 2000 2200
2400 ConMap-CHA
ConMap-SPT ConMap-MST
Dataset: Gowalla Receiving Energy: Superlinear
(f)
Delay Constraint
10 20 30 40 50 60 70 80 90 100
Energy
400 600 800 1000 1200 1400 1600 1800 2000 2200
2400 ConMap-CHA
ConMap-SPT ConMap-MST Brute Force
Dataset: Roma Taxi Receiving Energy: Linear
(g)
Delay Constraint
10 20 30 40 50 60 70 80 90 100
Energy
100 300 500 700 900 1100 1300 1500 1700 1900
2100 ConMap-CHA
ConMap-SPT ConMap-MST
Dataset: Roma Taxi Receiving Energy: Sublinear
(h)
Delay Constraint
10 20 30 40 50 60 70 80 90 100
Energy
100 300 500 700 900 1100 1300 1500
1700 ConMap-CHA
ConMap-SPT ConMap-MST
Dataset: Roma Taxi Receiving Energy: Superlinear
(i)
Figure 6: The energy consumption of the transmission schemes yielded by the three/four algorithms under different scenarios with six destinations. The dataset and receiving energy function are labeled in the figures.
Steiner tree in the intermediate graph. The first one is the SPT heuristic [3, 4]. It constructs the Steiner tree by finding the short- est path from the source to all the destinations. The second one is the MST heuristic [3, 4] that computes the Steiner tree by firstly establishing a minimum spanning arborescence and then pruning the unnecessary edges. And the last one is the approximation al- gorithm for directed Steiner tree problem proposed by Charikar et al. [27] and further improved in [29]. We also implement a brute- force algorithm to obtain the exact solutions for linear receiving energy function as the baseline. However, for the cases of sublin- ear and suplinear settings, the brute-force algorithm exhibits pro- hibitively large time complexity, and we thus do not present the corresponding exact results here.
7.2 Evaluation of ConMap Framework
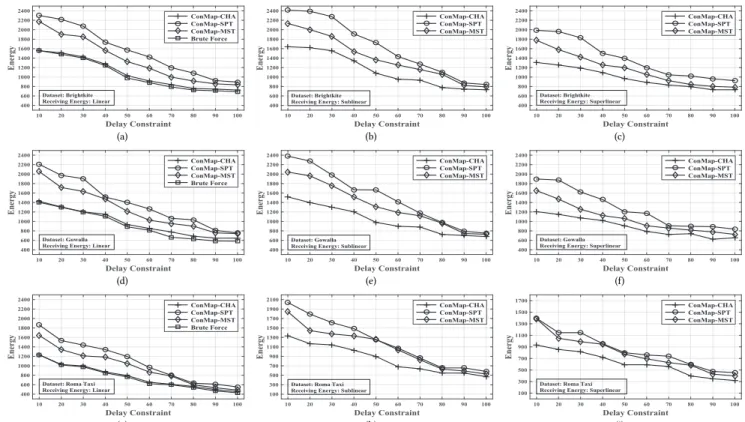
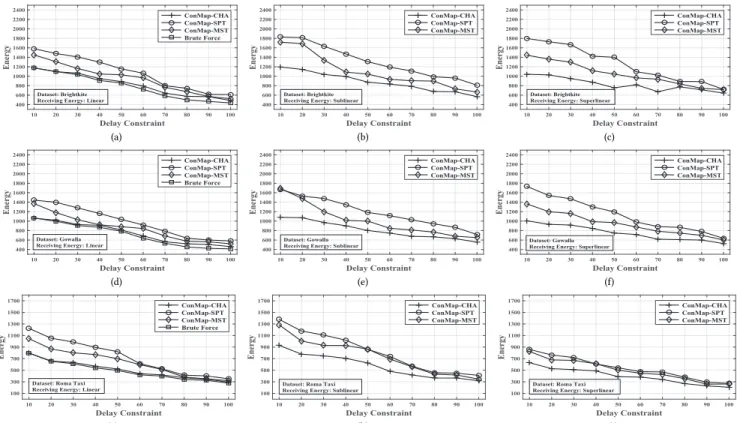
First, we investigate the performance of the proposed ConMap Framework. For each group of data under three different receiv- ing energy functions, we apply the ConMap framework embed- ded with three directed Steiner tree algorithms mentioned above and name them ConMap-SPT, ConMap-MST, ConMap-CHA respectively. Imposing a delay constraint from 10 to 100 time slots, we compute the average energy consumption for the transmission schemes designed for the ten groups of data by each algorithm. Ad- ditionally, we run a brute-force algorithm on each group of data under linear receiving energy function to present the cost of the optimal transmission scheme for comparison. The results are plot- ted in Figure 6 (and Figure 8 in Appendix A).
As demonstrated in Figures 6(a), 6(d) and 6(g), when embed- ded with the Charikar’s approximation algorithm [27] that has
a logarithmic approximation ratio and the receiving energy func- tion is linear, the energy consumption of the transmission schemes yielded by ConMap is only 9.1% and 2.6% higher than the optimal ones derived by the brute force algorithm in Brightkite, Gowalla and Roma Taxi datasets respectively. This verifies the conclusion that the ConMap framework indeed preserves the approximation ratio of the embedded directed Steiner tree algorithms, as we have proved theoretically in Theorem 5.3. We conjecture that the sim- ulation results under superlinear and sublinear receiving energy functions still enjoy such property. However, as deriving the opti- mal transmission scheme in such cases is too computationally in- tensive, we leave the comparisons between ConMap and the brute force algorithm under superlinear and sublinear receiving energy functions as future work.
Apart from the Charikar’s approximation algorithm which has relatively high time complexity, we can also embed faster heuris- tics into the framework to achieve the tradeoff between the opti- mality of the derived transmission schemes and the complexity of the algorithms. Figure 6 also shows this flexibility of ConMap, as we can more efficiently obtain transmission schemes that lead to more energy consumption by embedding SPT or MST heuristics in the framework. Furthermore, it turns out that although the approx- imation ratio of MST and SPT heuristic can be proportional to the number of nodes [4] in worst cases, the performance of ConMap- MST and ConMap-SPT are significantly better when applied on real life datasets under differnet settings. The simulation results indicate that in each scenario, the average approximation ratio is less than 1.4 for ConMap-MST and is less than 1.6 for ConMap-SPT.
This demonstrates the generality of the ConMap framework.