Data Hiding and Image Authentication for Color-Palette Images
全文
(2) [1][5][6][8][13][14] and most of them can be seen as. provides the ability to localize the altered areas. substitution systems. Such methods try to substitute. within the image. Fragile watermark systems can be. redundant parts of the image with the secret message.. classified into two types, spatial-domain fragile. The main disadvantage is the relative weakness. watermarking. against modifications. Recently, the development of. transformed-domain watermarking one [3][7][9]. In. new robust watermarking techniques led to advances. this study, we propose a novel method for. in the construction of robust and secure image data. simultaneously embedding binary data and fragile. hiding systems.. watermark signal within digital color-palette images.. system. [2][10][11][12]. or. Image authentication, on the contrary, is a technique for verifying the integrity and fidelity of an image.. The. uses. of. fragile. watermarks. and. semi-fragile watermarks are two of the techniques. 2. Characteristics of Color-palette Images and a Palette-sorting Algorithm In. order. to. hide. information. within. a. developed for image authentication. A fragile. color-palette image, some characteristics of them. watermark is a kind of watermark that is designed to. must be identified:. be easily destroyed if the watermarked image is manipulated. in. the. slightest. manner.. 1.. Image. authentication can be achieved by inspecting whether. most 256 colors; 2.. the embedded signal is destroyed. But in some applications, on the other hand, “information preserving”. operations. compression). should. (such be. as. JPEG. considered. as. between. an. information. a color palette is used for storing 256 colors used in the image;. 3.. every pixel can be thought as an index. lossy. number, which is a reference to the color. legal. palette, and so every pixel needs one byte. operations. A semi-fragile watermark, which tells the difference. every color-palette image contains at. of storage.. preserving. In this study, the proposed method is closely. operation and an information altering one (such as. dependent on the pixel’s index number within the. feature replacement), is hence designed to point out. color palette. But almost every image processing. real tampering and ignore legal operations in the. software has a different method to store the palette. authentication process.. data. Even when we just re-save the same image by. In the recent years, proposed systems that are. different software, the palette data may be different. used for verifying the authenticity of a digital image. from the original one. As a result, we will first sort. may be categorized into two types, the signature. the color palette before the hiding process to make it. system [4] and the fragile watermark system. In a. in the dark-to-bright order. After sorting, we may. signature system, a digest of the data to be. reference the same palette data. This will facilitate. authenticated is obtained by the use of cryptographic. the subsequent hiding process.. hash functions. The recipient verifies the signature by. Let pi = ( Ri , Gi , Bi ) be the i-th color within. examining the digest of the data and using a. the color palette, where 0 ≤ i ≤ 255 . To sort the. verification algorithm to determine if the data are. palette colors, we first calculate. authentic. A disadvantage of the signature system is. µ ( pi ) =ω 1×Ri 2 + ω 2 × Gi 2 + ω 3 × Bi 2. (1). ω1 , ω 2 , and. that the additional signature must be stored and. for every color in the palette, where. transmitted separately from the protected image. A. ω 3 are weighting values that make color such as. fragile watermark system, on the contrary, embeds. (140,130,120) to be different from (130,140,120), and ω1 ≠ ω 2 ≠ ω 3 . Then we sort µ ( pi ) in a. the authentication information inside the image and.
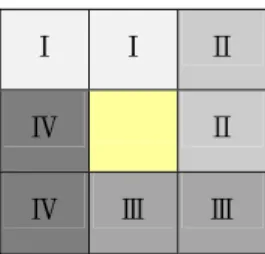
(3) descending order to obtain a sorted palette. Fig. 1 (a) shows a color palette before sorting and Fig. 1 (b). µ ( β x , β y ) = ( R x − R y ) 2 + (G x − G y ) 2 + ( B x − B y ) 2 ,. (2). shows the sorted result of Fig. 1 (a).. Ⅰ. Ⅰ. Ⅱ. Ⅳ. Ⅱ. Ⅳ. Ⅲ. Ⅲ. Figure 2. A 3× 3 block.. (a) (b) Figure 1. The color palette before and after sorting. (a) The color palette before sorting. (b) The color palette after sorting.. 3. Data Hiding Scheme by Palette Index Replacement In this section, the proposed method for. where 0 ≤ x , y ≤ 255 .The algorithm for embedding a bit of annotation, say si , can be expressed briefly as follows. Step 1:. first from a 3x3 block. Name the two involved pixels as α1 and α 2 . Step2:. color indices. will be described. An even-odd relationship between. sorted palette β , respectively. Step3:. in Section 3.3.. be the annotation that will be hidden into C, which has L characters in length. And let. β. be the sorted. palette, with βι ( 0 ≤ ι ≤ 255 ) being a color inside β that has index. ι.. Before the embedding. process, S must first be converted into a binary form. S = s1s2 ......s8 ......sL*8−1sL*8 according to the ASCII codes of the characters in S. As Fig. 2 shows, we hide the binary data into the four marked area (Ⅰ, Ⅱ, Ⅲ, and Ⅳ ) of every 3x3 block in C, and leave the central pixel unchanged, which will be used for hiding fragile information as described in Section 4. Let the Euclidean distance between the two colors be. Use the following rule to judge whether. ι1 and ι2 are even or odd numbers:. Section 3.2. Some experimental results will be shown. 3.1 Proposed Data Hiding Method Let C be a cover image of size M × N . Let S. ι1 and ι2 of the two. selected pixels α1 and α 2 from the. two pixels is utilized to embed or extract a binary bit. 3.1. And the extracting process will be described in. By viewing every pixel as an index number in the color-palette image, get the. embedding and extracting binary data information. The embedding process will be described in Section. Select a two-pixel block (Ⅰ,Ⅱ,Ⅲ or Ⅳ). Step4:. true if ι mod 2 = 0; (3) isEven(ι ) = false if ι mod 2 = 1. In the case that and si = 1. isEven (ι1 ) ≠ isEven (ι2 ) , modify one of the pixels by another color in. β. to. make the two indices either both even or both odd in a quality preserving fashion. Let β r and β r be two candidate 2. 1. colors that will be used to replace α1 or. α 2 , respectively. Choose the color β r to 1. be the one among. β that has minimal. Euclidean distance to α1 and satisfy the condition isEven (ι1 ) ≠ isEven ( r1 ) . On the other hand, choose the candidate color β r to be the one among β that 2. has minimal Euclidean distance to α 2 and. satisfy. the. condition. that.
(4) isEven (ι2 ) ≠ isEven ( r2 ) .. And. then. embedding result, an extraction process needs either a. modify one of the pixels by following. lookup table or the source image to obtain the secret. condition:. message. This is inconvenient for the receiver to get. if µ (α 1 , β r1 ) > µ (α 2 , β r2 ) replace α 2 by β r2 , if µ (α 1 , β r1 ) < µ (α 2 , β r2 ) replace α 1 by β r1 .. (4). only the stego-image is needed to extract the. isEven (ι1 ) = isEven (ι2 ) , just leave the. annotation message. Because the annotation embedded in the image. In. another. case. that. si = 0. and. can be any kind of description with an unfixed length,. isEven (ι1 ) = isEven (ι2 ) , modify one of. in our implementation the length of the annotation is. the pixels to make one of the index be. first embedded before the annotation content is. even and the other be odd. Perform. treated. As a result, the length information must first. similar operations in Step 4 to obtain two candidate colors β r and β r 2 from β. be extracted in the extraction process so that we can. and use them to replace α1 or α 2. ending the process.. 1. In. source image or a table. In our proposed method,. Otherwise, in the case that si = 1 and two pixels unchanged. Step5:. the secret message because the user has to keep the. know how many blocks should be examined before Let E be the stego-image to be processed,. β. according to the condition listed in Eq. (4). Otherwise, if and si = 0. be the sorted palette of E, and si be the i-th. isEven (ι1 ) ≠ isEven (ι2 ) , just leave the. extracted bit of the annotation data. The process of. two pixels unchanged.. extracting a bit from the stego-image is described. the. proposed. method,. the. even-odd. below:. relationship of the two chosen pixels is utilized to. Step1:. Choose a two-pixel block (see Figure 2). embed a binary bit of annotation information. The. from a 3× 3 block of E. And name the. indices ι1 and ι2 are tuned up to become both even. two involved pixels α1 and α 2 .. or both odd to represent the fact that a “1” is. Step2:. Get the indices ι1 and ι2 of α1 and. embedded. On the contrary, a “0” is embedded by. α 2 , respectively, from β according to. adjusting the indices of the two chosen pixels to. their RGB values.. become different in the even-odd relation, that is, for one index to become even and the other to become is odd. There is a good chance that the original indices just fit these two constraints. In this kind of situation, what we have to do is just to leave the two pixels. Step3:. The annotation si can be determined by the following rule: 1 si = 0 . if ι1 and ι2 are both even or both odd;. (5). otherwise.. unchanged. On the other hand, when the indices of. In the entire extraction process, we first extract. the two pixels do not meet the constraints, a color. the first l bits of the data that compose a number. with its index satisfying to the constraints described. that is the value of the length of the annotation. in Step 4 and Step 5 must be found to replace the. embedded in E. Then we can know how many. corresponding pixel. In order to preserve the quality. two-pixel blocks we should examine and after. of the stego-image, the color with the minimal. repeating the above-mentioned process by l × 8. Euclidean distance to the corresponding pixel is the. times, we can get the binary form of the extracted. best candidate for replacement.. annotation S = s1s2 ......s8 ......sl*8−1sl*8 . According to. 3.2 Data Extraction Process. the ASCII codes, S is then converted into character. In some conventional methods, besides the. form that finally results in the embedded annotation..
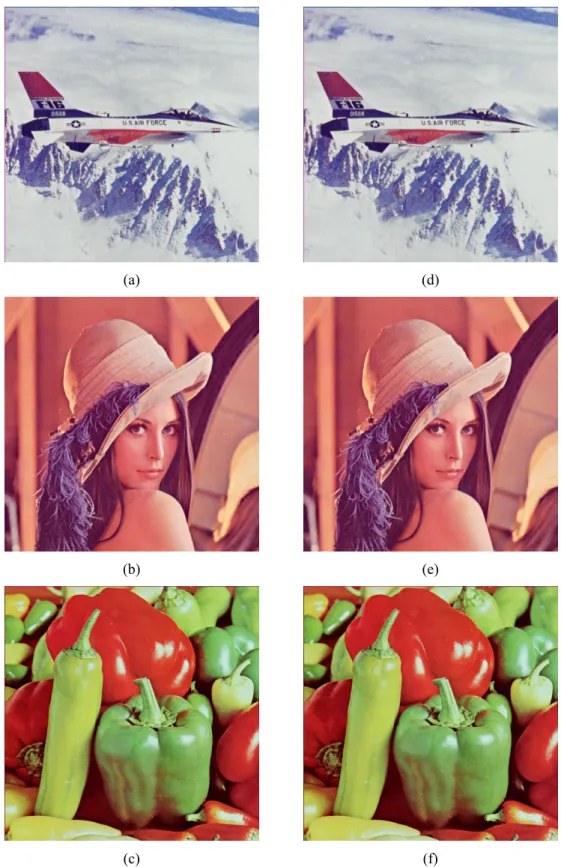
(5) 3.3 Experimental Results Ⅰ. In our experiments, the images “Lena”, “Baboon”, and “Pepper” with size 512 × 512 ,. Ⅰ. Ⅳ. Ⅱ Ⅱ. which are shown in Fig. 3(a), (b), and (c), are used as Ⅳ. the cover images. And Fig. 3(d), (e), and (f) are the. Ⅲ. Ⅲ. stego-images after embedding 10,000 characters. The PSNR values of the stego-images are listed in Table 1.. We utilize the surrounding four two-pixel blocks (I, II,. The PSNR values are high, which mean that only. III and IV) to embed the secret data by using the. little perceptual effect is created during the. method described in Section 3. After embedding,. annotation embedding process. And the embedded. every block’s central pixel is still unchanged. This. annotation can be extracted without any error,. pixel is hence used for embedding the fragile. according to the experimental results.. watermark. To embed the fragile watermark into a. 3× 3 block B, the algorithm can be shown as the Table 1. The PSNR values after embedding 10,000 characters. Lena Baboon Pepper PSNR 39.0 35.0 37.0. following steps: Step 1:. Calculate the mean value. µ. of B,. which can generally represent the color feature of a block. And the central pixel. 4. Authentication Scheme by Nearest Palette Color Replacement Method In. this. section,. a. novel. method. of the block is supposed to be close to. µ for Step2:. Find a color β k from. µ. to. And the verification processes can be proceeded. distance. without referencing the original image. In Section 3,. k. the secret data is embedded in the surrounding eight. strength factor.. unchanged. In the proposed method, the central pixel of every 3 × 3 block is utilized to embed the fragile watermark.. The. fragile. watermark. is the mean color. is not contained in β .. watermarked image can be detected and localized.. pixels of a 3× 3 block and the central pixel is left. µ. of a block, there is a good chance that it. authenticating the integrity and fidelity of the color-palette image is proposed. Alternations to the. in color. Since. Step3:. mod Q. β that is closest. according to the Euclidean of the RGB values, and = 0 . Here Q is a watermark. Replace the color value of central pixel of the block by β k .. The magnitude of Q in Step 2 is a tradeoff. embedding. between the probability to prove the tampering and. process will be shown in Section 4.1. The. the quality of the stego-image. When Q is a small. authenticating process will be described in Section. value, the quality of stego-image is relatively higher. 4.2. And several experimental results are shown in. because the candidate colors could be more so that. Section 4.3.. we can find a closer color for replacing the central. 4.1 Proposed Fragile Embedding Method. Watermark. Let C be a cover image of size M × N ,. β. be the sorted palette of C, and β i be the i-th color in. β ( 0 ≤ i ≤ 255 ). The cover image C is first divided into non-overlapping 3 × 3 image blocks, like the one shown below.. pixel of every 3× 3 block. But the opportunity of proving and localizing the tampering will became relatively lower. On the contrary, if Q is large, the image quality will become poorer but the probability of detecting tampering will become higher. The detailed data about the influence of Q and some discussions will be shown in Section 4.3..
(6) (a). (d). (b). (e). (c). (f). Figure 3. The cover images and stego-image with 10,000 characters embedded. (a) Cover image “Lena”. (b) Cover image “Baboon”. (c) Cover image “Pepper”. (d) Stego-image “Lena” with 10,000 characters embedded. (e) Stego-image “Baboon” with 10,000 characters embedded. (f) Stego-image “Pepper” with 10,000 characters embedded ..
(7) 4.2 Authentication Process. we altered Lena’s hair color and paste some wig on. The authentication process can proceed without. her hat. In Fig. 5(c), we cropped two green peppers. referencing the original image in our proposed. and pasted them onto different parts of the. method. Let T be the image that is suspicious of being tampered. And let β be the sorted palette of. stego-image. The experimental results showed that. T, and β i be the i-th color in β ( 0 ≤ i ≤ 255 ). To. Fig. 6 are the embedded results of “Lena” by. authenticate whether T has been tampered, we first. applying different Q values. When Q becomes larger,. divide T into 3× 3 non-overlapping blocks. For. the quality of the stego-image goes down. In Fig. 6 (c). every block, we focus on the central pixel p and get the palette index k of p from β , where the RGB. and Fig. 6 (d), we can find some false contouring. values of β k are equal to those of p. In the. are only 4 or 2 colors can be used for replacing the. embedding process described in Section 4.1, the. central pixel of every 3x3 block. The relation. central pixel of every block is replaced by the color. between the size of Q and the PSNR values of the. whose index is a multiple of Q. Therefore, k should. stego-image is shown in Table 3.. the altered areas are accurately marked out.. effect on the girl’s shoulder and cheek because there. be a multiple of Q if this block has not been tampered with. That is, if k is a multiple of Q, the block is judged as not being tampered with. On the other hand, the block is decided as being tampered with if k is not. Table 3. The PSNR values of stego-image by applying different Q values. Q=16 Q=32 Q=64 Q=128 PSNR 33.2 32.2 29.0 25.0. a multiple of Q. For visualization, we replace the block by its. 5. Discussions. inverse color if the authentication result indicates the. In this thesis, a system that embeds annotation. block has been altered. This will help us to localize. data and a fragile watermark simultaneously within. the tampering area in the suspicious image.. the color-palette image has been proposed. The color-palette image contains a palette with all the. 4.3 Experimental Results. colors used in that image. In order to reference the. In our experiments, we use three cover images. palette in the same order, the color palette is first. as shown in Fig. 4(a), (b), and (c) with size. reordered from dark to bright. In the embedding. 512 × 512 . And Fig. 4 (d), (e), (f) are the images. process, the annotations are embedded in the eight. after embedding a fragile watermark with Q = 8. We. surrounding pixels of a 3× 3 block. To embed a bit. almost cannot tell the difference between the cover. of data, two pixels are first selected and the indices of. and the stego-images. The PSNR values are shown in. these two pixels are obtained from the color palette.. Table 2.. The indices are tuned up to become both even or both odd if a “1” is to be embedded. Otherwise, the indices. Table 2. PSNR values of watermarked images. Jet Lena Pepper PSNR 36.0 35.4 34.2 Figs. 5(a), (b), and (c) are the images that have been tampered. And the authentication results are shown in Figs. 5(d), (e), and (f). In Fig. 5(a), we tampered the stego-image by rubbing the characters and the flag on the body of the airplane. In Fig. 5(b),. are tuned up to become different in the even-odd relation, that is, with one even and the other odd. To embed the fragile watermark, the mean value of every 3× 3 block is calculated. And the central pixel is replaced by a color that is closest to the mean value of the block. And the magnitude of the index of this color must be a multiple times of the value of a predefined watermark strength factor..
(8) (a). (d). (b). (e). (c). (f). Figure 4. The cover images and the fragile watermarked images (a) Cover image “Jet”. (b) Cover image “Lena”. (c) Cover image “Pepper”. (d) Watermarked image “Jet”. (e) Watermarked image “Lena”. (f) Watermarked image “Pepper”..
(9) (a). (d). (b). (e). (c). (f). Figure 5. The suspicious images and their verification results. (a) Tampered “Jet”. (b) Tampered ”Lena”. (c) Tampered “Pepper”. (d) Verification result of tampered “Jet”. (e) Verification result of tampered “Lena”. (f) Verification result of tampered “Pepper”..
(10) (a) Q = 16. (b) Q = 32. (c) Q = 64. (d) Q = 128. Figure 6. The watermarked image with different Q values. (a) Watermarked image with Q = 16. (b) Watermarked image with Q = 32. (c) Watermarked image with Q = 64. (d) Watermarked image with Q = 128.. References:. Processing, vol. 2, pp. 409-413, Chicago, Illinois, 1998.. [1] D. C. Wu and W. H. Tsai, “Embedding of Any. [4] D. Stinson, Cryptography Theory and Practice,. Type of Data in Images Based on a Human Visual. CRC Press, Boca Raton, 1995.. Model and Multiple-Based Number Conversion,”. [5] E. H. Adelson, “Digital signal encoding and. accepted and to appear in Pattern Recognition. decoding apparatus,” U.S. Patent 4939515,1990.. Letters.. [6] H. Y. Chang, “Data hiding and watermarking in. [2] D. C. Wu and W. H. Tsai, “A Method for Creating. color images by wavelet transforms,” Master thesis,. Perceptually Based Fragile Watermarks for Digital. Department of Computer and Information Science,. Image Verification,” submitted to IEEE Transactions. National Chiao Tung University, Taiwan, Republic of. on Multimedia.. China, 1999.. [3] D. Kundur and D. Hanzinakos, “Towards a Tell-. [7] J. Fridrich, “Image watermarking for tamper. Tale Watermarking Technique for Tamper-Proofing,”. detection,” in Proc. IEEE International Conference. in Proc. IEEE International Conference on Image. on Image Processing, vol. II, 1998, pp. 404-408..
(11) [8] M. S. Liaw and L. H. Chen, "An effective data hiding method," in Proc. IPPR Conf. on Computer. Vision, Graphics, and Image Processing, Taiwan, R.O.C., 1997, pp.146-153. [9] M. Wu and B. Liu, “Watermarking for image authentication,”. in. Proc.. IEEE. International. Conference on Image Processing, vol. II, pp. 437-441, Chicago, Illinois, October 1998. [10] P. W. Wong, “A public key watermark for image verification and authentication,” in Proc. IEEE. International Conference on Image Processing, vol. II, 1998, pp. 455-459. [11] R. van Schyndel, A. Tirkel, and C. Osborne, “A Digital Watermark,” Proceeding of the IEEE. International Conference on Image Processing, vol 2, pp. 86-90, Austion, Texas, November 1994. [12] S. Walton, “Information authentication for a slippery new age,” Dr. Dobbs Journal, vol. 20, no. 4, pp. 18-26, April 1995. [13] T. K. Yen, “Image hiding by random bit replacement and frequency transformations,” Master. thesis, Department of Computer and Information Science, National Chiao Tung University, Taiwan, Republic of China, 1998. [14] T. S. Chen, C. C. Chang, and M. S. Hwang, “A virtual image cryptosystem based upon vector quantization,”. IEEE. Transactions. on. Image. Processing, vol. 7, no. 10, pp. 1485-1488, 1998..
(12)
數據


相關文件
In the third quarter of 2013, visitor arrivals increased by 6.6%; per-capita spending of visitors grew by 4.6%; exports of gaming services rose by 13.3% in real terms; guests of
The economy of Macao expanded by 21.1% in real terms in the third quarter of 2011, attributable to the increase in exports of services, private consumption expenditure and
In taking up the study of disease, you leave the exact and certain for the inexact and doubtful and enter a realm in which to a great extent the certainties are replaced
In this research, we use conventional RGB (Red, Green, Blue) images as input data. The conventional RGB image is demosaiced from raw image by using the color interpolation
Upon reception of a valid write command (CMD24 or CMD25 in the SD Memory Card protocol), the card will respond with a response token and will wait for a data block to be sent from
We do it by reducing the first order system to a vectorial Schr¨ odinger type equation containing conductivity coefficient in matrix potential coefficient as in [3], [13] and use
Wang, Solving pseudomonotone variational inequalities and pseudocon- vex optimization problems using the projection neural network, IEEE Transactions on Neural Networks 17
Define instead the imaginary.. potential, magnetic field, lattice…) Dirac-BdG Hamiltonian:. with small, and matrix
