A Topology Control Algorithm for Constructing
Power Efficient Wireless Ad Hoc Networks
Szu-Chi Wang
Dept of Electrical EngineeringNational Taiwan University Taipei, Taiwan wsc@lion.ee.ntu.edu.tw
David S. L. Wei
Dept of Computer and Information Science Fordham University
Bronx, New York wei@dsm.fordham.edu
Sy-Yen Kuo
Dept of Electrical Engineering National Taiwan University
Taipei, Taiwan sykuo@cc.ee.ntu.edu.tw
Abstract - In this paper, we present a localized algorithm for
constructing power efficient topology for wireless ad hoc networks. Each mobile node determines its own transmission power based only on local information. The proposed algorithm first constructs the constrained Gabriel graph from the given unit disk graph and then reduces the total transmission power by allowing each node individually excises some replaceable links. The constructed topology is sparse, has a constant bounded power stretch factor, and the total transmission power is lower than those obtained from other proposed algorithms. In addition, compared with others, our algorithm requires lower time complexity to generate a solution, and can thus further save the energy for each mobile node. We demonstrate the performance improvements of our algorithm through simulations.
I. INTRODUCTION
A wireless ad hoc network is formed from mobile nodes without using an infrastructure. Each mobile node is responsible for serving not only as a user but also as a router. The connectivity of the network is maintained through the corporation of all nodes of the network. On the one hand, without a need of a fixed infrastructure allows the network to be easily deployed in areas where a communication infrastructure does not exist (e.g. due to an earthquake or flood) or the construction of a fixed infrastructure is inconvenient or impossible (e.g. on a battlefield or in space). On the other hand, the lack of a physical backbone infrastructure poses a strong need of topology control of the network. It is known that the performance of a protocol for an ad hoc network can be enhanced if the protocol is designed based on overlaying a virtual infrastructure on the ad hoc network. Also, due to the finite power supply of a mobile computer, power conservation has been widely used as a primary control parameter in the design of protocols for wireless ad hoc networks. Therefore, the problem of power-efficient topology control has been attracting more and more researchers from the areas of mobile computing and networking. In this paper, we present an algorithm for constructing power-efficient topology for wireless ad hoc networks. A wireless ad hoc network can be modeled by a
weighted directed graph G = (V, E), where V represents the set of all mobile nodes and E represents the set of possible interconnections between pairs of mobile nodes. For each edge (u, v) ∈ E, node v must be in the transmission range of node u. We use ||uv|| to denote the Euclidean distance between node u and node v. The weight of the edge (u, v) is the power consumed for transmitting signal from node u to node v. Its value can be formulated as ||uv||β in the most widely-used power-attenuation model, where β is a real constant between 2 and 5 depending on the wireless transmission environment. This power consumption is typically called transmitter power and is treated as the major part of power consumption to transmit signals. Like most of the previous works and for the purpose of performance comparisons, we do not count the power consumed at the receiver node in this paper. Throughout the paper, we use the terms link and edge interchangeably.
In this paper, we assume that all the mobile nodes are distributed in a two-dimensional plane and each mobile node has a GPS receiver on board for acquiring its own location information. We assume that initially all mobile nodes are operated at full transmission power and have the transmission radius equal to one unit by a proper scaling. Consequently, the resulted graph G will be a unit-disk graph (denoted as UDG (V)) and there is an edge between two nodes if and only if their Euclidean distance is at most one. We assume that UDG (V) is strongly connected. All of the mobile nodes have unique identifiers (ID) numbered from 1 to N, where N = |V|. Each mobile node can individually adjust its own transmission power. We assume that omni-directional antennas are used by all mobile nodes to transmit and receive signals. Wireless ad hoc networks are power constrained, and it is thus undesirable to ask each node to transmit with maximum power. Otherwise, the total transmission power will often be unnecessarily high and the transmission interference will occur more frequently. As a result, each mobile node should adjust its transmission power to potentially reduce the total transmission power while still maintain network connectivity.
Due to the characteristics of wireless ad hoc networks, it is preferred that the underlying network topology can be
constructed in a localized manner. Stojmenovic et al. first give the definition of a localized algorithm [1]. A localized algorithm requires the transmission only over small distances. It also dramatically reduces the interference levels among nodes. In our case, a distributed transmission power control algorithm is called localized if every node u can decide its transmission power based only on the information of the nodes reachable in a constant number of hops. We assume that there is no node failure and the communication channel is reliable in this paper.
Hereafter we adopt several definitions given in [2]. Let f be a complete transmission power assignment on V and Gf be the associated communication graph. Obviously, Gf ⊆ G. The total transmission power of f is defined as sc (f) = Σv∈V f (v), where f (v) is the minimum transmission power needed to reach all of the neighbors of v in Gf. Given an h-hop (unicast) path Π (u, v) from node u to node v in Gf, the path is expressed as Π (u, v) = v0v1…vh-1vh, where u = v0, v = vh. The total transmission power consumption of this path is defined as:
∑
= − = Π h i i i v v v u p 1 1 || || )) , ( ( β .Given a communication graph H, the least-power path between node u and node v, denoted by Πmin (u, v), is a path whose total transmission power consumption is the minimum among all of the paths that connect these two nodes in H. Let pH (u, v) stand for p (Πmin (u, v)). The power stretch factor of the graph Gf with respect to G is then defined as:
)) , ( / ) , ( ( max ) ( , p u v p uv G G G V v u Gf = ∈ f ρ .
The two most widely used energy conservation approaches in literature are: (1) reducing the transmission power of each node; and (2) reducing the total power consumed by all nodes involved in one communication session. The later can be achieved by preserving the least-power paths in the underlying network. However, these two approaches may offset each other, and a discussion of it can be found in [3]. The major concern of our work is to develop a localized topology control algorithm where each mobile node makes a decision about its transmission power based on only its local information. These locally made decisions collectively ensure global network connectivity and the network topology controlled by the transmission power of each node must be power efficient. More precisely, the proposed algorithm must achieve the following objectives: (1) a complete transmission power assignment with low total transmission power, (2) a constant bounded power stretch factor, and (3) a sparse network, namely a constant bounded average node degree.
The rest of this paper is organized as follows. Section II briefly introduces the related works. Section III describes the basic ideas and the details of our algorithms. Performance evaluation is performed via simulations in Section V. The extension of the proposed algorithm to mobile network is discussed in Section V. We conclude the paper in Section VI.
II. PREVIOUS WORKS
In [4] Rodoplu and Meng described a distributed protocol for constructing a topology that guarantees the least-power path between every pair of nodes that are connected in a given (UDG) graph. Recently, Li et al. [5] proposed a protocol based on their results but performs better and is computationally simpler. In [6] Li and Wan proposed a distributed position-based protocol to construct an enclosure graph for conserving power in one communication session. Their protocol is more time and space efficient than [4]. All of these works focus on constructing a subgraph of G that contains the minimum-power topology, namely, a subgraph that includes the union of all of the least-power paths. On the other hand, the problems of finding a complete transmission power assignment with optimization criteria of the maximum/total transmission power assigned has been studied in [7-9]. However, the proposed transmission power assignment approaches in [8, 9] with objective of minimizing the total transmission power are all centralized and cannot be transformed to localized algorithms. The trade-off between sparseness and power efficiency of the topology is discussed in [2]. In [2] Li et al. studied the power efficiency property of several well-known proximity graphs, such as the constrained Gabriel graph (denoted by GG (G)), the constrained relative neighborhood graph (denoted by RNG (G)), and the constrained Yao graph (denoted by YGk (G)), over a graph G. They also showed that if G = UDG (V) the power stretch factor of GG (G) is always one, and the power stretch factors of RNG (G) and YGk (G) could be as large as N – 1 and 1 / (1 – 2sin (k/π)), respectively. However, they also showed that the total transmission power of these geometry structures could be arbitrarily larger than the minimum total power needed to maintain the strong connectivity of the network.
III. OUR LOCALIZED TOPOLOGY CONTROL ALGORITHM A. Observations
For simplicity, we first assume that each node in the network is stationary. However, our algorithm can be easily modified to adapt to the mobile environment as discussed in Section V. Considering a complete transmission power assignment f, there is obviously a tradeoff between sc (f) and
ρGf (G), i.e. over reducing the transmission power of each
node may diminish least-power paths or vice versa. The problem of finding a complete transmission power assignment f whose total transmission power is the minimum among all of the complete assignments is called the min-total assignment problem. However, no localized algorithm for the min-total assignment problem has been given. Moreover, this problem is NP-hard and it is still an open question for the best approximation ratio. Therefore, our algorithm is designed in such a way that we first construct a subgraph H = (V, E’) from G, where E’ ⊆ E, and H has a constant bounded power stretch factor. After that, the total transmission power is minimized as much as possible. The basic idea is using the local information of each node to excise some logical links of the subgraph while still keeps the power stretch factor being
bounded by a constant c. Unlike the algorithms for constructing power efficient topologies proposed in [2], we do not aim to construct a topology that guarantees a constant bounded node degree (though our algorithm may generate a such one) in this paper. The main reason is that, as shown in [2], a geometry structure with a constant bounded node degree may contain very limited least-power paths between any two nodes. Our design goal is to preserve as many of these least-power paths as possible. Moreover, as mentioned in [3], further eliminating edges may result in more congestion and hence worse throughput and fault tolerance in the long run.
B. The Algorithm
Our algorithm consists of two phases. In the first phase we construct the constrained Gabriel graph GG (G) over the unit disk graph G = UDG (V). We choose the constrained Gabriel graph simply because it can be constructed locally and efficiently and has a power stretch factor of one. In addition, the constrained Gabriel graph was used as a subgraph in several important routing protocols, for example, the FACE routing protocol [10] and the GPSR routing protocol [11]. Nevertheless, any other geometry structure that guarantees a constant bounded power stretch factor can be used in the first phase. Suppose that GG (G) is associated with a transmission power assignment f. For each node u, if a logical link (u, v) of GG (G) satisfies the equation ||uv||β = f (u), then (u, v) is called a critical link. The transmission radius associated with f (u) is denoted by radius (u). For each node u, the amount of transmission power saved by excising all its critical link(s) is denoted by ps (u). The priority of node u is a pair pri (u) = <ps (u), ID>. Let pri (v1) = (ps (v1), ID1) and pri (v2) = (ps (v2), ID2). Then, pri (v1) > pri (v2) if ps (v1) > ps (v2) or (ps (v1) = ps (v2) and ID1 < ID2). Each node is only required to know the locations, priorities and the transmission radiuses of the nodes within its two-hop neighborhood of UDG (V). The information about the one-hop neighbors can be obtained by using some form of beacon messages that are sent periodically and asynchronously by each node to declare its presence. To obtain the information of two-hop neighbors, a common solution is that each node attaches the list of its own one-hop neighbors, while sending the beacon messages. These two kinds of information are extensively used to facilitate message routing and broadcasting in wireless ad hoc networks and therefore, the cost of maintaining such information can be amortized. In fact, with the knowledge of node position, Calinescu [12] recently proposed a connected-dominating-set based approach for collecting the two-hop neighborhood information with O (N) communications.
In the second phase, we reduce the total transmission power by trying to eliminate all the critical link(s) that are replaceable with alternative paths. For each critical link (u, v), node u tries to search another path that reaches node v based on its local information. We call such path the replacing path of (u, v). Whenever a node u found that itself has the highest priority and ps (u) > 0 within its two-hop neighborhood, it
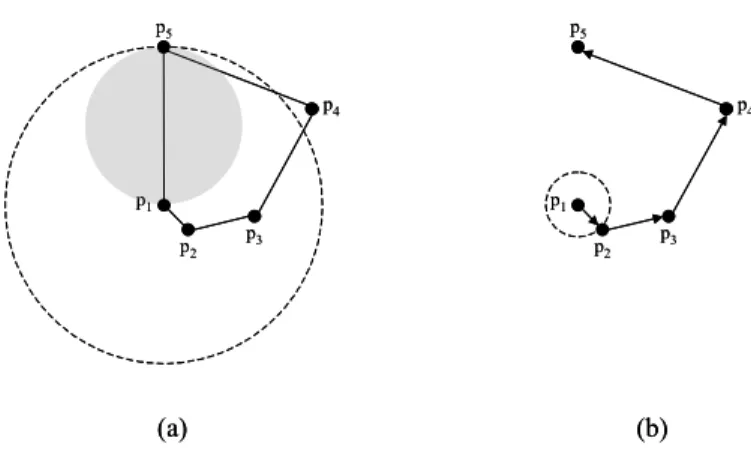
starts a search for the replacing path(s). The searching process is based on Dijkstra’s algorithm. However, for each node u, no global knowledge of the network topology is available. Our solution is to ask u to construct a local topology view, namely a subgraph G’ (u) = (V’, E’), on top of GG (G) based on the location and transmission radius information of the nodes in its vicinity. A node vi belongs to V’ if vi is within u’s two-hop neighborhood of UDG (V). An edge (vi, vj) belongs to E’ if ||vivj|| ≤ radius (vi) and (vi, vj) belongs to the edges of GG (G). The edge weight of G’ is defined the same as that of GG (G). After the construction of G’ (u), node u removes each critical link and applies Dijkstra’s algorithm on it to search for the shortest path Πmin (u, v). Node u saves the result by an ID list including all of the intermediate nodes of Πmin (u, v). If no such path exists or p (Πmin (u, v)) is more than c times larger than the weight of edge (u, v) in G, then the searching procedure is ended. The replacing path of node u is set as an empty list and ps (u) is set to 0. Otherwise, Πmin (u, v) is the eligible replacing path of (u, v), and (u, v) can be excised. For example, assume that Fig. 1(a) is the local topology view constructed by p1 based on its local information. The solid lines are the logical links of GG (G) and are all bi-directional. The area covered by the dashed line is the transmission range of p1, which is decided by the directed link (p1, p5). Note that there should be no other node in the gray area. If p1 found an alternative path Π (p1, p5) = p1p2p3p4p5 and p (Π (p1, p5)) < c⋅||p1p5||β, where c is a predetermined constant, then p1 can excise (p1, p5). This way, the transmission range (and thus the transmission power) of p1 can be largely reduced, as shown in Fig. 1(b).
p1 p2 p3 p4 p5 p1 p2 p3 p4 p5 (a) (b) p1 p2 p3 p4 p5 p1 p2 p3 p4 p5 (a) (b)
Figure 1. Illustrative example.
If all the critical link(s) can be excised, the priority of u is recalculated by the same rule, with the critical link(s) decided by a new value of f (u) that corresponds to the minimum operational power needed to cover the remaining logical links. Node u then disseminates its new priority and replacing path(s) to its two-hop neighborhood by a notification message. Each constituent link in the replacing path(s) is called as a replacing link. The start node of each replacing link adds a replacing tag to this link. For each node w with ps
(w) > 0, if w receives a notification message, it first checks if any of its critical link(s) is tagged as replacing. If so, w sets ps (w) to 0 and disseminates its new priority to its two-hop neighborhood. Otherwise, if node w found that its priority is the local maximum within its two-hop neighborhood, it starts to search the replacing path(s) of its critical link(s) following the above steps. The idea of using two-hop neighborhood information can be generalized by using k-hop neighborhood information, where the value of k can be chosen depending on the value of c. The algorithm in pseudo code format for each node, say node u, is given in Fig. 2. L is the logical links decided by u. LTV (k) is the local topology view constructed using the k-hop neighborhood information of u. After applying Dijkstra’s algorithm on LTV (k), the weights of all shortest paths are stored in an array dist [N] ordered by the IDs of the destination nodes. Note that if a node v is unreachable from u in LTV (k), then dist [v] = ∞. The notification message is a tuple nm = <id, pri, radius, replacing_path> that records the ID, priority, transmission radius, and replacing path(s) of the sender node, respectively.
For each node u:
L← { (u, v) | (u, v) ∈ GG (G) };
iteration← 0; decide pri;
send a beacon message to the k-hop neighborhood; on receipt of a notification message nm do
update the information of node nm.id; for each link (u, v) ∈ L do
if ((u, v) ∈ nm.replacing_path) then (u, v).tag ← replacing; on update of local information do
if (pri.ps > 0 and pri is the max priority in the k-hop neighborhood and iteration < i) then
shrink← true; construct LTV (k);
apply Dijkstra’s algorithm on LTV (k); for each critical link (u, v) ∈ L do
if ((u, v).tag = replacing or dist [v] > c * ||uv||β)) then
shrink← false;
pri.ps← 0; break; if (shrink) then
L← L – { (u, v) | (u, v) is a critical link }; update pri.ps;
iteration← iteration + 1;
send a notification message to the k-hop neighborhood;
Figure 2. Algorithm EGG running at each node.
It’s not hard to see that there is a tradeoff while searching for the relaying paths: if some critical link(s) of the nodes with lower priorities are chosen for composing the replacing paths of the nodes with higher priorities, the transmission power of those low-priority nodes cannot be reduced. However, if we exclude all the critical link(s) while applying Dijkstra’s algorithm, the possibility of failing to find an eligible replacing path will increase. We use a simple heuristic for further decreasing the total transmission power: applying Dijkstra’s algorithm on a subgraph of LTV (k) with all of the critical link(s) removed. If not all of the eligible replacing path(s) can be found, then Dijkstra’s algorithm is applied again on LTV (k). The remaining steps are the same as above.
C. Correctness
It is easy to see that the constructed topology has the following properties: (1) strongly connected; (2) sparse; (3) having a power stretch factor bounded by c; (4) planar. Due to the limited space, we only offer a sketch of the proof. First, since our algorithm just excises the logical links of GG (G), the constructed topology is a subgraph of GG (G) and is thus a sparse and planar graph. Second, the strong connectivity is guaranteed since the excision occurs only when all of the eligible replacing path(s) of the critical link(s) can be found. Third, the power stretch factor is bounded by c since the power stretch factor of GG (G) is one and each constituent link l of the least-power path can only be replaced by a path whose total transmission power consumption is at most c times larger than l’s link weight. Each link comprised in the replacing path is marked by a replacing tag, and will not be excised in the future.
D. Complexity
The cost of Dijkstra’s algorithm is O (V log V + E) provided that the priority queue is implemented in a Fibonacci heap. Since each node uses a subgraph of GG as the input to Dijkstra’s algorithm, and GG (G) is sparse and can be constructed by an O (V log V) time algorithm, the time complexity for each node to search all of the replacing path(s) is thus O (V log V). If the number of times of executing the searching procedure for each node is bounded by a constant i, the total time complexity of each node is O (V log V). Therefore, our algorithm outperforms those proposed in [4, 5] in terms of time complexity. Time complexity should be also a major concern in designing a localized power-efficient topology control algorithm, as the algorithm has to be frequently executed by each individual node in order to maintain the connectivity of the network in a power-efficient manner. The computations spent in running of the algorithm certainly consume power from the node.
IV. SIMULATION RESULTS
In this section, we measure the performance of our algorithm via simulations. As mentioned in Section I, we were most interested in the power stretch factor and total transmission power of the topologies constructed by the localized algorithms with similar design goals. We chose the algorithm proposed by Li and Halpern [5] (denoted by SMECN) since it performs significantly better than the algorithm proposed by Rodoplu and Meng [4] in terms of total transmission power. Likewise, the constrained Gabriel graph (denoted by GG) outperforms all other topologies described in [2] in terms of the above two criteria. It is thus chosen for comparison here. Our algorithm was operated with c = 2 and i = 1. We experimented it with the two strategies described in Section III, i.e. applying Dijkstra’s algorithm once (denoted by EGG-1) and twice (denoted by EGG-2). We measured the power efficiency of each constructed topology H by the following metrics: (1) total transmission power
(denoted by tpc), and (2) power stretch mean (denoted by psm), which is defined as:
2 , / ) ) , ( ) , ( ( N v u p v u p psm V v u G H
∑
∈ = .psm is a modification of the power stretch factor since all the above topologies clearly have a power stretch factor bounded by a very small constant. This metric is more suitable to further evaluate the energy conservation for a communication session. The power attenuation constant β
was set to 2 and 4. For simplicity, we simulated only a static network, that is, we assume that nodes do not move. The transmitter range R is fixed at 500 meters. The map sizes are equal to s × R by s × R, for s = 1, 3, 5. The x and y coordinates of each node are selected at random in the interval [0, m], where m is the map size. The experimentation was performed for N = 100. The experimental results are summarized in Table I and Table II. Each value in the two tables is the average of 50 independent experimental results. tpc is normalized to lie in between 0 and 1.
Table I shows that the topology constructed by our algorithm has a tpc of about 30% less than that of GG and SMECN in most cases. One the other hand, the increase in its psm is less than 5%. This means that the total transmission power can be decreased significantly while conserving most of the least-power paths. This trend is more obvious when β = 4. As shown in Table II, if we compare EGG-1/EGG-2 with GG, the tpc of GG is much larger than that of EGG-1/EGG-2, but their difference in psm is almost negligible. The tpc of SMECM is also higher than that of EGG-1/EGG-2 in this case. Notice that the time complexity of SMECM is O (V2), but ours is only O (V log V). One can also see that by applying Dijkstra’s algorithm twice indeed can further reduce tpc at a cost of a slight increase in psm. The experimental results indicate that our algorithm can prolong both the node and the network lifetime and thus improve the energy efficiency in wireless ad hoc networks.
V. DEALING WITH MOBILITY
The above discussions are all performed on the stationary networks, that is, every node is assumed to be static. While taking node movement into consideration, each node must be able to adjust its transmission power dynamically. The basic idea for achieving network reconfiguration is that all the mobile nodes send beacon messages with full transmission power and run the proposed algorithm periodically. However, it is too costly if many nodes move at high speed. As mentioned in many previous works (e.g., [6]), node movement can be viewed as two events, namely node addition and node deletion. Therefore, what we should solve turns out to be finding an efficient way to add a new node to and remove a node from the network. Our algorithm uses the k-hop neighborhood information in a way that network reconfiguration can be solved more efficiently. For node addition, the new node v broadcasts its position information with full transmission power. Each node u that received this
TABLE I. The performance measurements of different topologies with β = 2
tpc psm 1.0 0.99992 0.666025 tpc psm 1.0 1.0 1.0 1.0 0.99995 1.0 1.02792 0.669387 1.02764 GG SMECN EGG-1, k=2 EGG-2, k=2 0.641633 1.03955 0.644607 1.03934 s = 1 s = 3 tpc psm s = 5 1.0 1.0 0.99994 1.0 0.724976 1.03409 0.708392 1.04131 0.666025 1.02792 0.669387 1.02764 EGG-1, k=3 EGG-2, k=3 0.641633 1.03955 0.644534 1.03953 0.724745 1.03411 0.707691 1.04135 tpc psm 1.0 0.99992 0.666025 tpc psm 1.0 1.0 1.0 1.0 0.99995 1.0 1.02792 0.669387 1.02764 GG SMECN EGG-1, k=2 EGG-2, k=2 0.641633 1.03955 0.644607 1.03934 s = 1 s = 3 tpc psm s = 5 1.0 1.0 0.99994 1.0 0.724976 1.03409 0.708392 1.04131 0.666025 1.02792 0.669387 1.02764 EGG-1, k=3 EGG-2, k=3 0.641633 1.03955 0.644534 1.03953 0.724745 1.03411 0.707691 1.04135
TABLE II. The performance measurements of different topologies with β = 4
tpc psm 1.0 0.49970 0.405776 tpc psm 1.0 1.0 1.0 1.0 0.50571 1.0 1.00945 0.408402 1.00963 GG SMECN EGG-1, k=2 EGG-2, k=2 0.393086 1.02337 0.39657 1.02172 s = 1 s = 3 tpc psm s = 5 1.0 1.0 0.65060 1.0 0.53725 1.01206 0.523476 1.02237 0.405776 1.00945 0.408072 1.00962 EGG-1, k=3 EGG-2, k=3 0.393086 1.02337 0.395919 1.02174 0.519015 1.01158 0.503721 1.02264 tpc psm 1.0 0.49970 0.405776 tpc psm 1.0 1.0 1.0 1.0 0.50571 1.0 1.00945 0.408402 1.00963 GG SMECN EGG-1, k=2 EGG-2, k=2 0.393086 1.02337 0.39657 1.02172 s = 1 s = 3 tpc psm s = 5 1.0 1.0 0.65060 1.0 0.53725 1.01206 0.523476 1.02237 0.405776 1.00945 0.408072 1.00962 EGG-1, k=3 EGG-2, k=3 0.393086 1.02337 0.395919 1.02174 0.519015 1.01158 0.503721 1.02264
it is too costly if many nodes move at high speed. As mentioned in many previous works (e.g., [6]), node movement information checks if (u, v) is a new logical link of GG (G). If so, u updates its logical links and informs v to add link (v, u). For node deletion, if a removed node v changes the transmission radius of some node u, then u updates the critical link(s). If some node found that its ps value becomes larger than 0, then it updates its priority and re-executes the searching procedure if there is a need. In addition, though the moving distance of a moving node v comprised in the relaying path could affect the power stretch factor of the generated topology, it is not hard to see that node v only affects the logical links of the nodes within its k-hop neighborhood. If some node w is aware of that the movement of node v will break the replacing path of node u, then node w informs node u to re-execute the searching procedure and disseminates its new replacing path if there is one. Obviously, the communications and computations of the reconfiguration process can be performed locally, which is preferred for wireless ad hoc networks.
VI. CONCLUSIONS
In this paper, we show how to construct and maintain a power-efficient topology in wireless ad hoc networks in a distributed and localized manner. We develop a distributed algorithm that requires only local information for constructing and maintaining a logical topology on the unit disk graph. The proposed algorithm first constructs the constrained Gabriel graph from the given unit disk graph. After that, the total transmission power can be reduced via searching for the replacing path of each critical link. The topology constructed by our algorithm has several desired features such as sparse and constant bounded power stretch factor. The simulation results show that our algorithm outperforms others in terms of total transmission power. In addition, our algorithm requires lower time complexity and
can thus further save the energy for each mobile node, as computations also consume power from a mobile computer. Furthermore, the topology constructed by our algorithm helps other programs save energy in two ways, as stated in [5]. First, it suffices for each node to use the transmission power computed by our algorithm to send periodic beacon messages. Second, the routing algorithm can be restricted to using the edges of this subgraph to find an energy-efficient path for a communication session.
REFERENCES
[1] I. Stojmenovic and X. Lin, “Power-aware Localized Routing in Wireless Networks,” IEEE International Parallel and Distributed
Processing Symposium, 2000.
[2] X.-Y. Li, P.-J. Wan, Y. Wang, and O. Frieder, “Sparse Power Efficient Topology for Wireless Networks,” HICSS, Hawaii, 2002.
[3] R. Wattenhofer, L. Li, P. Bahl, and Y. M. Wang, “Distributed Topology Control for Power Efficient Operation in Multihop Wireless Ad Hoc Networks,” IEEE INFOCOM 2001, pp. 1388-1397, April 2001. [4] V. Rodoplu and T. H. Meng, “Minimum Energy Mobile Wireless
Networks,” IEEE J. Selected Areas in Communications, 17(8):1333-1344, August 1999.
[5] L. Li and J. Halpern, “Minimum Energy Mobile Wireless Networks Revisited,” IEEE International Conference on Communications (ICC), June 2001.
[6] X.-Y. Li and P.-J. Wan , “Constructing Minimum Energy Mobile Wireless Networks,” ACM Symposium on Mobile Ad Hoc Networking
and Computing (MobiHoc), Long Beach, California, Oct 4-5, 2001.
[7] R. Ramanathan and R. Rosales-Hain, “Topology Control of Multihop Wireless Networks Using Transmit Power Adjustment,” IEEE
INFOCOM, 2000.
[8] L. Kirousis, E. Kranakis, D. krizanc, and A. Pelc, “Power Consumption in Packet Radio Networks,” Symposium on Theoretical Aspects of
Computer Science (STACS ’97), 1997.
[9] G. Calinescu, I. Mandoiu, and A. Zelikovsky, “Symmetric Connectivity with Minimum Power Consumption in Radio Networks,” IFIP-TCS, 2002.
[10] I. Stojmenovic and S. Datta, “Power and Cost Aware Localized Routing with Guaranteed Delivery in Wireless Networks,” Proc.
Seventh IEEE Symposium on Computers and Communications (ISCC),
2002.
[11] B. Karp and H. T. Kung, “GPSR: Greedy perimeter stateless routing for wireless networks,” ACM/IEEE International Conference on Mobile
Computing and Networking (MobiCom), 2000.
[12] G. Calinescu, “Computing 2-hop Neighborhoods in Ad Hoc Wireless
Networks,” 2nd International Conference
on AD-HOC Networks and Wireless (ADHOC-NOW ’03), October