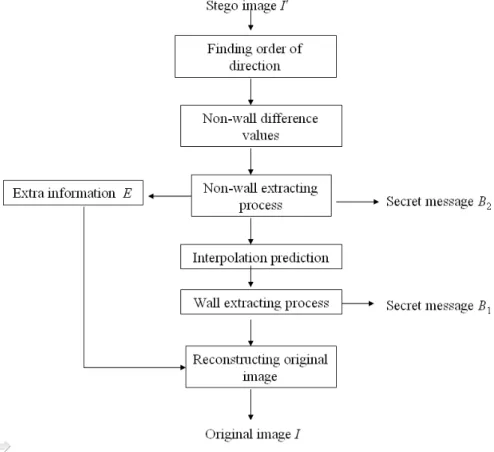
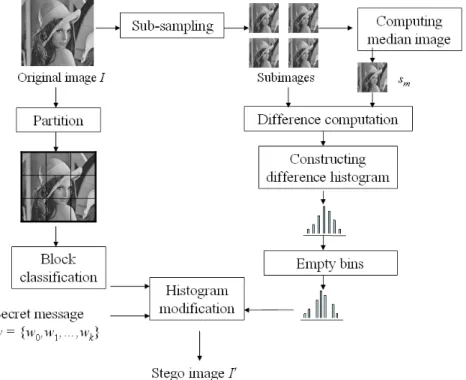
Reversible data hiding for high quality images exploiting interpolation and direction order mechanism
全文
數據
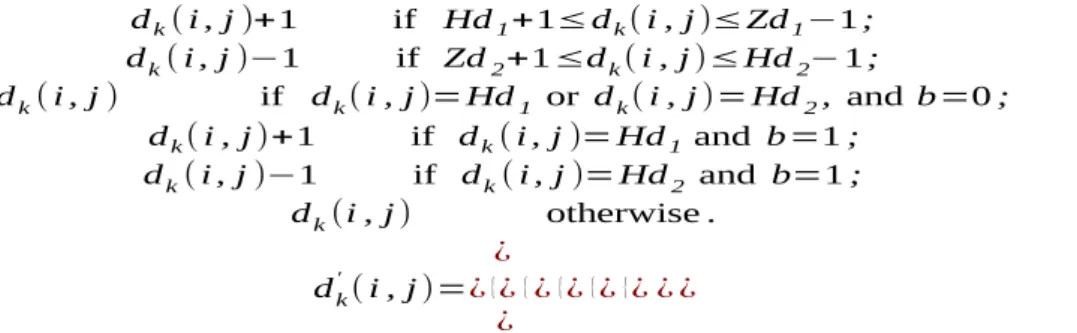
相關文件
Bandlimited signals From the point of view of the preceding discussion, the problem for interpolation, is high frequencies, and the best thing a signal can be is a finite
• 57 MMX instructions are defined to perform the parallel operations on multiple data elements packed into 64-bit data types. • These include add, subtract, multiply, compare ,
• 57 MMX instructions are defined to perform the parallel operations on multiple data elements packed into 64-bit data types. • These include add, subtract, multiply, compare ,
– The The readLine readLine method is the same method used to read method is the same method used to read from the keyboard, but in this case it would read from a
• 57 MMX instructions are defined to perform the parallel operations on multiple data elements packed into 64-bit data types.. • These include add, subtract, multiply, compare ,
Piecewise polynomial interpolation: divide the interval into a collection of subintervals and construct different approximation on each subinterval. The simplest piecewise
Promote project learning, mathematical modeling, and problem-based learning to strengthen the ability to integrate and apply knowledge and skills, and make. calculated
Monopolies in synchronous distributed systems (Peleg 1998; Peleg