A
Simple
Resource
Advertisement and
Discovery
4. .T
Protocol for Large and Dense MANETs
Jean-Lien C. Wu
andShun-Te Wang
Department of Electronic Engineering
National Taiwan
University ofScience and Technology
43,Keelung Road, Section
4,Taipei 106, Taiwan
c
w,
w angsd
1
@nlhyper.e
t.
ntust.edu
.
tw
Abstract With remarkable advances in wireless technologks, applications of mobile ad hoc networks will be in widespread use in the near future. Thus, the geographical network environments
may become large and dense. In such network environments, a
large number of resource discovery queries may be generated
when specific resources or services are needed. In this paper, we
propose a simple resource advertisement and discovery (SRAD)
protocol for applications in mobile ad hoc networks. The SRAD
protocol self-organizes a proximity networkand works in a fully
distributed architecture without centralized control and
management. The simulation results show that the SRAD protocol
can achieve the same level of performance as in the
broadcast-based protocols while generating fewer transmitted
messages in large and dense mobile ad hoc networks.
Index Terms--service discovery, MANET, resource discovery,
large and dense, protocol, SRAD
1. INTRoDUCTION
ith recent advances in wireless technologies as well as the availability of pervasive computing devices such as personal digital assistants (PDAs), smart phones and even electric watches, wireless communications and networking are experiencing a renaissance, and applications of mobile
ad
hoc networks @IANETs) may be in widespread use thus the network environment becomes large and dense. Mobile users may request the desired services, resources or intormation anytime and anywhere, hence, the provision of resource advertisement and discovery mechanism for large and dense MANETs becomes necessary [ 11.
Resource discovery
allows client nodes to look for remote resources or services and cany out transactions with other nodes. General ad hoc routing protocols, however, are not suitable for resource or service discovery because the destination address of the resource is usually unknown when needed.A large and dense network environment implies a large-scale network with high density of mobile node population. Here, “large-scale” is relative to the radio coverage of mobile nodes. If the network diameter, i.e., the ratio of network topology area to a mobile node’s radio coverage area, is larger than 8, the network is said to be large [2]. On the other hand, the density of * Tlus work was supported by National Science Council under Contract No. NSC93-2213-E-011-071.
Chun-Yen Hsu
Dept.
of ComputerScience and Information Engineering
National
TaiwanUniversity of Science
andTechnology
43,
Keelung
Road,
Section
4, Taipei 106, Taiwanyen@nlhyper
.
e t .ntus t.edu. tw
mobile node population is defined as the ratio of the total r d o
coverage area of all mobile nodes to the geographical network area, that is, N d I A , where Nis the number of mobile nodes, P is
the radius of the coverage area of a mobile node, and A is the geographical area of the network [3]. In this paper, we define a dense network environment as the density of mobile node population being Brc, namely, a mobile node has an average of
(Sa ~ 1) neighboring nodes in its radio coverage.
A resource discovery protocol provides client applications for discovering the existence of services provided by server applications. Generally, a service can also be defined as hardware such as prinier. In this paper, we consider that a
resource could vary fkom information-orient services such as weather reports or provision of location information, data-oriented services such as music downloading, or
commerce-based services such as ticket subscribing, or public services such as printers and cameras.
Mobile nodes can look for their desired resources using broadcast simply by flooding. However, this will result in some serious problems such as the wastage of bandwidth, and a large
amount of power consumption in mobile nodes. Hence, the
design of an efficient resource discovery protocol must tradeoff the performance measures such as kit rate and the cost, e.g., the
number of transmitted messages. Here we define hit rate as the ratio of the number of successhl attempts on the desired resource information to the total number of queries.
We propose in this paper
a simple resource advertisement and
discovery (SR4D) protocol for applications in large and dense MANETs. The architecture of theS R A D
protocol is fully distributed, without centralized control and management. In addtion, a resource description and management scheme is devised to share loads among mobile nodes.U. RELATEDWORK
There already exist considerable efforts on service discovery standardized by different industrial consortiums and organizations. Protocols such as Sun’s Jini [4], Service Location Protocoi (SLP) of IETF [SI, Salutation and Salutation-lite fiom the Salutation Consortium [6], Universal Plug and Play (UPnP) from the UPnP Forum [7], and Service Discovery Protocol (SDP) for personal area connectivity of Bluetooth [E], have been proposed to facilitate applications to discover services available on stable networked devices. These protocols are primarily centralized or semi-centralized in their
architectures, m e m o r e , an implicit assumption is that the underlying network is reliable for communications. These higher layer protocols are thus not suitable for MANETs.
In the research field of peer-to-peer (PZP) computing, many fully distributed systems, algorithms and protocols have been proposed. The Gnutellu protocol is simple, efficient and fault-tolerant but it uses flooding that causes high network traffic. The Freenet system is a distributed information storage system that can pool unused disk space across thousands of desktop computers to create a collaborative virtual file system, however, it is usually used to find files shared by anonymous authors. Other protocols like CAN, Chord, Pustty, Tapesoy,
and Tomudo, have their structured P2P architectures that can guarantee reliability, availability, and access quality [9, 10, 113.
However, they are based on the construction of a distributed hash fable which requires management overhead as
performance penalty.
A resource discovery and service location system named Intentional Naming System (INS) [I21 integrates name resolution and message delivery to offer application-layer anycast and multicast. But it requires that some devices or computers in a network can potentially act as name resolvers to form an application-level overlay network and route client requests to the appropriate services.
A novel content location protocol called GCLP for MANETs can be found in [ 131. The GCLP makes use of physical location information to lower proactive traffic while reducing query cost. In GCLP, advertisement and discovery messages are sent in four
fixed opposite geographical directions, however, in this way, it
may not work we11 in an ad hoc network environment where nodes are not uniformly deployed in a geographical area.
111. THE SRAD
PROTOCOL
If a resource discovery protocol heavily relies on network-wide broadcast, mobile nodes will experience considerable power consumption. Besides, resource discovery mechanism must be designed properly so that users can discover the resource efficiently while the cost is minimized. In this paper, we assume that mobile nodes reside in a two-dimensional plane and have the capability of location awareness that their location infomation can be obtained precisely. By using the location information, the performance of the networking protocol can be improved.
3.1. Concepts of
SRAD
protocol designMobile nodes are assumed to be peers that they have symmetric roles. Individual peers voluntariiy contribute resources to the network. Rather than being divided into clients and servers, a node may act as both a client and a server. For convenience, a mobile node providing service or resource information is called a server, and a node interested in certain resource provided by a server is called a client. A server periodically advertises its information by disseminating the advertisement messages within a certain resource area. Nodes that lie in the resource area will cache the resource information
of the server. When being queried, the node that has the cache of
the resource information will send a reply to the client node, and after the client node receives the reply, the resource discovery operation is completed.
3.2. Resource description and management scheme
In the application layer, the location information of a restaurant, for example, can be described using a resource descriptor in this form: < infomution-orient. location.
restaurant >. Then, the resource descriptor is encoded as a 128-bit resource key using the
MD5
algorithm. In this way, a resource descriptor can be encoded as a unique number calledresource key.
In order to share loads among mobile nodes, the SRAD protocol is devised to let server nodes advemse their resource information along one of the twenty line trajectories uniformly distributed on a plane. Hence, the resource key will then be used to determine a direction (or angle) for information dissemination using a hashing function. To do so, the modulo-k scheme is chosen as the hashing function. In this paper, we let k be 20 to divide 180 degrees into 20 parts. Then, using the tangent function, we can easily get a slope of a line trajectory. Here we call it the main slope (S,).
3.3 Resource advertisement and discovery
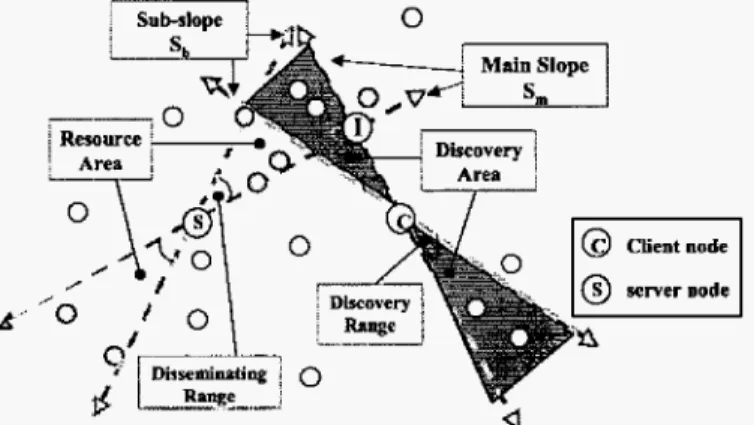
As shown in Figure 1, the resource advertisement is performed on the basis of the line trajectory
with
main slope anda tolerance that forms a resource urea. Mobile nodes that lie within the resource area must cache the resource information. Resource discovery is performed on the basis of another perpendicular line trajectory that forms a discovery area. Note that the disseminating runge is a tolerance of an angle to allow the resource information to be disseminated. The dkcuvery
rmge is a tolerance of an angle to allow the resource information to be discovered. If a node in both resource area and discovery area has the resource information, or a node coming
from the resource area just moves to the discovery area holds
the resource information, it must send a reply to the client node. 3.3. I Line-based (LB) SRAD protocol
A. Resource advertisement
The server node advertises its resource information using an advertisement
(ADV)
packet every Ti,,,-, seconds.Xnt-,
depends on the speed of the mobile node, in a highly dynamic situation, it is desirable to have a small Tint-,. The ADV packet contains the following fields:
< Packet type, Source ID, Server’s Coordinate, Sequence Number, Resource Key, Hop Count, Lifetime, Main Slope >
The Hop Count field is used as hop count limitation that
confines the distance an A D V can travel. The Source ID and Sequence Number fields are used to distinguish duplicate advertisements. The Lifetime field in ADV packet defines the lifetime of the resource information to be cached. High mobility server nodes in a MANET will set a small lifetime for this resource entry. This cached resource entry would be deleted once its lifetime expires. Each entry in the cache contains the following fields:
< Server ID, Resource Key, Server’s Coordinate, Previous ID,
Sequence Number, Lifetime >
When a node receives an ADV packet with new sequence number, it calculates whether itself lies in the resource area or not. If true, the resource information is recorded in the cache for a specified lifetime. Then, the node decrements the value of the Hop Count field in the ADV packet by one, and broadcasts it
again if the value of Hop Count is larger than zero; otherwise, the ADV packet is discarded. Because an
ADV
packet keeps the server's coordinate and the main slope of a line trajectory, a node can determine whether itself is located in the resource area by some calculations.This advertisement process will be carried out until the value of Hop Count field in the ADV packet reaches zero. In this way, the ADV packet is broadcasted
within
a confined resource area roughly along a line trajectory to avoid flooding the network.k "
Figure I . Resource area and discovery area. B. Resource Discovery
When a client wants to find a resource or service, it first checks if it has cached the resource information that has not expired. If false, it calculates the resource key using the encoding process as described in section 3.2. Thus, the client
can
obtainthe same resource key
its what server obtains. Using that resource key, the client node can calculate the main slope ofa line trajectory to disseminate a resource request (RREQ) packet for resource discovery.
The client firstly generates a RREQ packet and initiates the resource discovery process. Note that for resource discovery, the FUWQ packet is disseminated along a line trajectory perpendicular to the line trajectory used in the resource advertisement process. The nodes that lie in both the resource area and discovery area can send a resource reply (RREP) packet to the client node using unicast to complete the resource discovery process. Moreover, if a node coming from the
resource area just moves to the discovery area, it will also send a
RREP packet to the client node. The RREP packet consists of the following fields:
< Packet type, Sequence Number, Server's ID, Server's Coordinate, Resource Key, Hop Count, Coordinate of the Reply Node, Main Slope, Lifetime
When a node receives a RREQ packet, it first checks whether the RREQ packet is a duplicated one. If true, the RREQ packet is discarded. Otherwise, if it has cached the resource information, it then sends back a RREP packet drectly to complete the resource discovery process, or else it then determines whether or not itself lies in the discovery area using
geometry calculations. If the node lies in the discovery area and does not have the desired resource information, then, the node decrements the value of the Hop Count field in the RREQ packet by one, and broadcasts it again if the value of Hop Count is larger than zero; otherwise, the RFtEQ packet is discarded. A resource discovery process fails if the client node does not receive the RREP packet within TRm, the maximum tolerable round trip time. TRn is set according to the average number of hops the RREQ packet is expected to travel. If resource discovery processes fail frequently,
T
,
,
and the value of the Hop Count field in the RREQ packets can be set larger.3.3.2 Enhanced line-bused (ELB) SRAD protocol
It is possible that a server is located at the geographical border of the network and no neighboring node lies on the discovery trajectory or resource area. Besides, because the geometric coverage area near the server is small, some nodes may be close to the server but could not recognize the resources of the semer. Hence, the enhanced line-based (ELB) SRAD protocol is proposed. The ELB protocol uses two main slopes that form two line trajectories perpendicular to each other to disseminate the
ADV
and RREQ packets.In the ELB protocol, the resource discovery process is the same as that of the LB protocoI based on one selected main slope. But if the fisst
resource discovery process fails, the client
node will try to send another RREQ packet using the other main slope.3.3.3 Cross-line-bused (CLB) SRALI protocol
To increase hit rate and consider that mobile nodes m a y not be uniformly distributed in the network, the cross-line-based (CLB)
S R A D
protocol is proposed. In the CLB protocol, the resource advertisement process is the same as that of the ELB protocol based on two main slopes. But the former discovers resource based on two main slopes at the same time. Theperformance penalty of the CLB protocol is that the transmitted message overhead is more than that of the ELB protocol since it discovers resource along two line trajectories.
w.
SIMULATIONSTUDYFor comparisons, an on-demand (OD) resource discovery protocol modified from the AODV routing protocoI to support resource discovery is implemented in simulations.
The performance metrics to be observed include:
Number of transmitted messages: the total number of broadcast messages in the network.
Average hit rate: the ratio of the total number of successful resource discoveries to the total number of queries.
Average hop-count: the number of hop-counts between the client nodes and the reply node that is located at the discovery area.
Besides, how moving speed of mobile nodes affects the performance of the SRAD protocol will also be discussed.
4.1 SimuIation merrics
Each mobile node has a communication range of 100 meters. Nodes are uniformly distributed and confined to a region of 500m x 50Om and 1 OOOm x 1 OOOm, respectively, in simulations.
Every node randomly selects a destination point and a speed in an interval of [0, V-] ktn/hr after a pause time
P
seconds. When the mobile node reaches the destination, the same process is repeated. In the simulation, the pause time is set to be 100 seconds and the value of V,, varies fiom 7.2 kmlhr to 57.6kmrhr.
The simulation parameters are summarized in Table I. The disseminating range and discovery range are tolerances of angle in degrees to allow the resource information to be disseminated and discovered as shown in Figure 1.
\
Metria
Total no. of messages
-
ELB CLB OD
Protocol LB
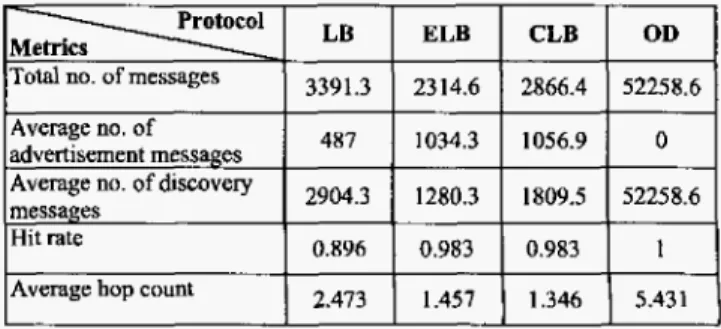
3391.3 2314.6 2866.4 52258.6
TABLE I. Simulation Parameters
Average no. of
advertisement messages messages Average no. Of discovery
I
EnvironmentI
HighlyI
LargeandI
487 1034.3 1056.9 0
2904.3 1280.3 1809.5 52258.6
Parameters dense dense
Total number of nodes 100 to 500
7.2 to 57.6 7.2 to 57.6
Hit rate
Average bop count
4.2 Simulation results
A. Comparison of LB, ELB and CLB protocols in hit rate
In
the simulation results, we find that the more nodes in the network, the higher the average hit rate. The larger the discovery range in degrees, the higher the average hit rate. The LB protocol has lower average hit rate than the ELB and CLBprotocols in a relatively sparse network because it discovers resource infomation only along a line trajectory. In a highly dense network, these protocols all have high average hit rate approaching loo%, because there are so many redundant nodes caching the resource information.
B.
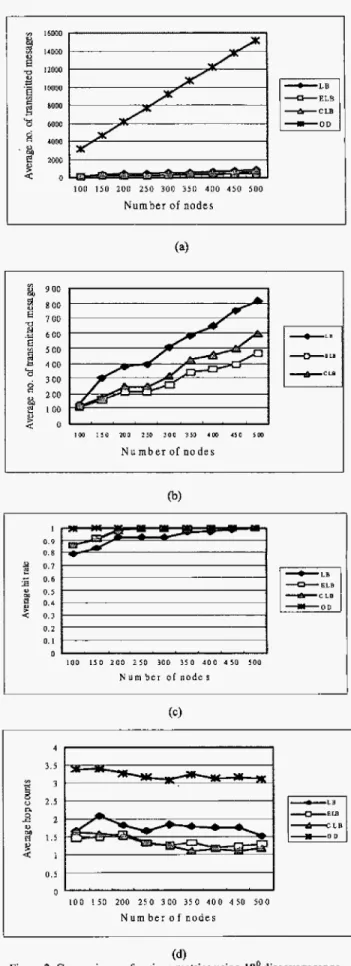
Comparisons of LB, ELB, CLB and OD protocolsFigure 2 gives the results
with
18' discovery range in a region of 500m x 500m. Figure 2(a) shows that the OD protocol introduces much more overhead than the other three protocols as the number of nodes increases, because it discovers resource information simply by flooding. The LB, ELB and CLB protocols just advertise and discover resource information along confined trajectories, thus they produce much fewer transmitted messages.Figure 2@) shows that the ELB protocol introduces fewer overheads than the CLB and LB protocols. The CLB protocol uses two discovery trajectories, so it produces more overhead than the ELB protocol does. Note that although the ELB and CLB protocols use two advertisement trajectories, they produce fewer messages in the network. This is because more client nodes may have cached the advertised resource information prior to sending the query messages. Figure 2(c) indicates that the OD protocol can achieve the highest hit rate. The ht rate for LB, ELB and CLB protocols improves when the density of mobile node population increases. Figure 2(d) shows that the average hop counts needed to obtain the resource information.
0.896 0.983 0.983 1
2.473 1.457 1.346 5,431 That is, the three SRAD protocols can find resource information efficiently and quickly compared to the OD protocol.
To improve the hit rate of the LE3 protocol in sparse network environments, the discovery range of a client node can be
enlarged to 36'. In a region of SOOm x 500111, we find in the simulations that using 36' discovery range in low density network environments makes the hit rate efficiently improved fiom 78%, 86% and 86% to 92%, 96% and 96%, respectively for the LB, ELB and CLB protocols. Moreover, either in low or highly dense environment, the three SRAD protocols can
achieve good hit rate. That is, in the network that has high density of mobile node population, the three SRAD protocols have the same hit rate of over 99% as high as that of the OD protocol.
Although using 36' discover range doubles the number of transmitted messages in using 18' discover range, the LB, ELB and CLB protocols have fewer overheads than that of the OD
protocol. Besides, the LB, ELB and CL3 protocols need fewer hop counts to get resource information compared to the OD protocol.
C. The effect of the speed
of mobile nodes
In the simulation results, we find that the moving speed of mobile nodes does not significantly affect the hit rate either in highly dense or in large and dense network environments. This is because the discovery time, i.e., the latency in discovering the desired resource, is so short that only few mobile nodes that have cached the resource information can Ieave the discovery area within that period of time.
D. A comprehensive comparison
Table I1 shows the comparison of various metrics in terms of average total number of transmitted messages, average number of advertisement and hscovery messages, average hit rate, and average hop count for OD and the three SRAD protocols for large and dense network environment. The result shows that about 52,258 transmitted messages are generated using the OD protocol. Nevertheless, using the LB protocol guarantees a hrt rate of 89.6% and its overhead is only 6.5% of that of the OD protocol. Because in E L 3 and CLB protocols, more nodes may have cached the advertised resource information and can send a reply directly to the
source
of query in the discovery process, these two protocols generate fewer messages in the network than the LB protocol does. Hence, using the ELB and CLB protocols guarantees a hit rate of 98.3% and their overhead are respectively 4.4% and 5.5% of that of the OD protocol.TABLE
n.
Comparison of various performance m e h c s with 1000 nodesV. CONCLUSIONS
In this paper, we propose the SRAD protocol for resource advertisement and discovery in large and dense MANETs. The SRAD protocol self-organizes aproximity network and works in a fully distributed architecture Without centralized control and management. It assures the client nodes that if more than one server nodes advertise resource information described by the same resource descriptor, the most proximate server will first be discovered. Besides, the SRAD protocol can quickly locate tbe desired resource within a few hop counts in a limited discovery time, even in a network of dynamic topology. It also guarantees a very high hit rate as compared to that of the on-demand protocol that simply uses flooding. Moreover, the SRAD protocols can work well in either sparse or highly dense wireless
networks.
The simulation resuits show that the SRAD protocol can achieve the same level of performance as in the broadcast-based on-demand protocol, while generating fewer transmitted messages in large and dense mobile ad hoc networks. Furthermore, the
S R A D
protocol has three variations considering the redundancy of line trajectories for resource advertisement and discovery. The ELB and CLB protocols can guarantee a higher hit rate and generate fewer messages than the LB protocol, however, the LB protocol needs fewer nodes to cache the advertised resource information than the ELB and CLB protocols. If an ad hoc network consists of limited-memory nodes, the LE protocol may be preferable.REFERENCES
D. Saha and A. Mukhejee, “Pervasive computing: a paradigm for the 21st century,” IEEE Computer Mag., vol. 36, no. 3, March 2003, pp. J. Liu, E. Li, Q. Zhang and W. Zhu, “Service locating for large-scale mobile ad hoc network,” International Joumol of Wireless Information
Networh, vol. 10, no. I , Jan. 2003, pp. 33-40.
W. -T. Chen and W. -T. Lee, “Dynamic AODV backup routing in dense
mobile ad-hoc networks,” In Proc. of Wireless On-Demand Network System P O N S ZOO$), Trento, Italy, Jan. 21-23, 2004, vol. 2928 of LNCS, Springer-Verlag, pp. 156168.
Sun Microsystems, Technical White Paper: Jini Architectural Overview,
Dec. 1999, http://www.sun.com/jini/.
E. Guttman, “Service location protocol: automatic discovery of iP network services,” IEEE Internet Compuiing Mag., vol. 3, no. 4, The Salutation Consortium, http://www.salutation.org/.
The Universal Plug and Play Forum, hap://www.upnp.org/.
Bluetooth website, Specificdun OJ the Blueroorh Sysrm, wi.2, 2001. http://www.bluetooth.comi.
C. Lindemann and 0. P. Waldhorst, “A distributed search service for peer-to-peer file sharing in mobile applications,” In Proc. of the 2nd intemtional Conference on Peer-to-Peer Computing (P2P 2002) ,
LinkGuing, Sweden, S a t . 5-7,2002. up. 73-80. 25-3 I.
July-AugW 1999, pp. 71-80.
[lo] M. RipeGu, “Peer-k-p& architecture case study: Gnutella network,” In
Proc. of the 1st International Conference on Peer-to-Peer Computing (P2P ZOOI), Linkfiping, Sweden, August, 2001, pp. 27-29.
[ I I ] H. -C. Hsiaa and C. -T. King, “Tamado: a capability-aware peer-to-peer storage overlay,”Jaurnal of Porallel and Distributed Computing, vol. 64,
no. 6, June 2004, pp. 747-758.
[I21 W. Adjie-Winoto, E. Schwartz, H . Balakrishnan and J. Lilley, ”The
design and implementation of an intentional naming system,” In Proc. of rhe 7th ACM Symposium on Operating System Principles, Dec. 12-1 5, 1999, Charleston, South Carokina, USA, pp. 186-201.
[ 131 J. Tchakmov and N. Vaidya, “Efficient content location in wireless ad
hoc networks,” In Proc. of IEEE International Conference on Mobile Daia Management (MDM ZOO#), Berkeley, California, USA, Jan. 19-22,
2004, pp. 74-87. I6WO e! I4000 l2mO I0000