0167-4048(95)00028-3
Compurers G Serurity Vol. 15, No. I, pp. 73-X1, 1996 Copyright 01996 Elsevier Science Limited Printed in Great Britain. All rights reserved 0167-404W96 $15.00
An access control
based on
scheme
Chinese
theorem
remainder
and time
stamp concept
Min-Shiang Hwang)* Wen-Guey Tzeng’
and Wei-Pang Yang’
‘Department of Computer and Information Science, Natiorral Chiao Tung University, Hsinrhu, Taiwan 300, ROC
ZTelecommunication Laboratories, Ministry oJ Transportation and Commrrnications, Chung-Li, Taiwan 320, ROC
In this paper we propose a new dynamic access control method for the computer system with frequently inserted, deleted and updated users/files. Our method, based on the concepts of the access control matrix, key-lock-pair, time stamp and Chinese remainder theorem, associates each user with a user key and a user lock and each file with a file key and a file lock. Our method can achieve the following four goals. (1) By a simple module operation on the keys and locks of the user and the file, we can reveal the access right of a user to a file. (2) When a user/file is added to the computer system, we only assign a key and a lock to the user/file with- out affecting the keys and locks of the other users/files in the system. (3) When a user/file is deleted from the computer system, we simply erase the entry of the user/file in the com- puter system. (4) When the access right of a user to a file is updated, we merely modify the key and lock of the user or the file without affecting the keys and locks of the other users/ tiles in the system. The main contribution of our method is that the action of inserting, deleting a user/file, or updating the access right of a user to a file can be done by modifying
only one key and one lock, which could not be achieved simultaneously before.
Keywords: Access control matrix, Chinese remainder theorem, Dynamic, Key-lock-pair, Time stamp.
1. Introduction
I
n today’s computer systems, how to prevent an unauthorized user (process, utility program, etc.) from altering, destroying or disclosing a file (disk, magnetic tape, printer or memory segment) is an important issue in the field of computer security. The general concept of such prevention is called access control which, in a computer system, is to verity the access right of the user to the file when a user requests access.M-S. Hwang et alJAn access control scheme
The most straight forward implementation of access control for a computer is to use a matrix [ 11, called the access control matrix, in which the entry of the ith row and jth column records the access right of the ith user over the jth file. When a user makes a request to access a file, the access control system grants the request only if the corresponding entry in the access control matrix records such a privilege. A drawback of the access control matrix method is that when the access control matrix is sparse and stored directly, the efficiency of space usage is quite low. Therefore several methods [2-91 are proposed to resolve this problem.
The capability-list and access-list systems are among the earliest [3]. However, they usually trade time for space, e.g. to check the access right of a user to a file in the access-list system, in the worst case the entire list must be checked, which is time consuming. Therefore many approaches have been proposed for access control of com- puter systems in the literature [9-l 11. Among them, the “key-lock” concept is plausible.
In a key-lock access control system, each user pos- sesses a key and each file has a lock. When a user requests the access of a file, the key-lock access control system verifies the access right of the user to the file by making some operation on the user’s key and the file’s lock. Thus the important issues in key-lock access control methods include the effectiveness of maintaining keys and locks. In the following we review some previous key- lock access control methods. The single-key-lock method of Wu and Hwang [9] uses an TV x WI key matrix and n m-tuple lock vectors. The method is time-consuming, not only in the retrieval of access right, but also in maintaining keys and locks while inserting and deleting a user/file and updating the access right of a user to a file. Fur- thermore, the storage space required by the method is O(m2 +mn) for m users and n files, which is more than that of the access control matrix method. The key-lock-pair method of
Chang [4] is based on Chinese remainder theo- rem. The method cannot delete a user/file without overhauling all keys and locks. The key-lock-pair method of Chang and Jiang [5] is based on binary operations. Again, this method also needs to re- compute all the keys in the system when inserting a user/file to the system. The two-key-lock-pair method of Chang and Jan [12] is also based on Chinese remainder theorem. While deleting a user/file, this method has to re-compute almost all keys. The single-key-lock method of Laih et al. [8] is based on the idea of Newton’s interpolating polynomial. The method is basically the same as the access control matrix except that the access right vectors of files are r+aced by lock vectors. Strictly speaking, when inierting a user/file all keys and lock vectors have to be updated in this method. The two-key-lock-pair method of Jan et al. [7] is based on the concept ofp-adic numbers. The main purpose of the method is for dynamic access control, which means users/files are inser- ted into and deleted from a computer system fre-
quently. However, this method needs to
re-compute all keys and locks while deleting a user/file or updating the access right of a user to a file. The storage space required by this method is the same as that of the access control matrix method. The single-key-lock method of Hwang et al. [6] is based on prime factorization. Again, this method also needs to re-compute all locks while inserting and deleting a user and updating the access right of a user to a file.
None of the above methods can achieve optimal- ity of updating one key for each operation (e.g. inserting a user/file, deleting a user/file or updat- ing the access rights of a user to a file) while using a reasonable amount of storage space. In this paper we propose an access control method which is based on Chinese remainder theorem and the concept of time stamp. Our method achieves real dynamicism in the sense that performing one inserting, deleting or updating need only modify one key. Therefore the time complexity of each operation is dramatically reduced. Also, like those methods of Chang [4], Jan et al. [7] and Hwang et
Computers 8 Security, Vol. 75, No. I
al. [6], our method uses only O(m + n) storage space for m users and n files.’
Thus, we can say that our method achieves opti- mality in the sense of the number of key updating for each operation and the amount of storage space usage for keys and locks. However, like most key-lock-pair and two-key-lock-pair access control methods, our method suffers the overflow problem of keys and locks. For practical applica- tions this problem can be dealt by some conven- tional solutions, e.g. by grouping relevant users and files such that the number of items in each level is small enough to make the size of keys and locks reasonable [ 121.
In the next section we review Jan’s two-key-lock- pair mechanism [7], from where we get our idea. In Section 3 we present our new dynamic access control method and in Section 4 we discuss prac- tical issues.
2. Review of a two-key-lock-pair
method
In this section we review the two-key-lock-pair access control method of Jan et al. [7]. In a two- key-lock-pair access control system, users and files are treated symmetrically, i.e. each user possesses a key and a lock and so does each file. The two-key- lock-pair scheme of Jan et al. [7] is shown in Fig. 1. There are two tables in the scheme, one is the user key-lock table and the other is the file key- lock table. The user key-lock table has three col- umns: the key column K, the lock column L and the number column NF which denotes the num- ber of files in the computer system when the user is inserted into the system. The file key-lock table also has three columns: the key column K’, the lock column L’ and the number column NU which denotes the number of users in the com- puter system when the file is inserted into the system. Let t be the total number of distinct access rights. For example, t = 5 if the access right could be “none” which is denoted by number 0; “read”
‘We ignore the overflow issue here.
denoted by 1; “write” denoted by 2; “execute” denoted by 3; “own” denoted by 4. Let rV be the number which denotes the access right of user i to file j. The key values of user i and file j are defined as
I(I=l;l+rizt+...+ri,NF,tNF’~’ and
(1)
Kj’ = rlj + rzj t + . . . + rNu,, t,“-‘{ (2) respectively. The lock values of user i and file j are t I-’ and tl-’ respectively. Then the access right r.
of user i to file j can be derived by the keys and locks of user i and file j as
LKi/L;J mod t if i>NU,,
rii =
i L 2$/L,
J
mod t otherwise. (3)We illustrate the above description by the follow- ing example. Let U1, Ua, . . ., U6 and F,, F,, . . . F, be the six users and the six files which are added to the system in the sequence U,, F1, FZ, U,, U,,
F3, U4, F4, Us, Ug, F5, Fb. The corresponding access rights of users to files are shown in Table 1. The corresponding user and file key-lock tables are shown in Tables 2 and 3. It can be seen that when user 1 is deleted from the system, all key and lock values of files have to be re-computed.
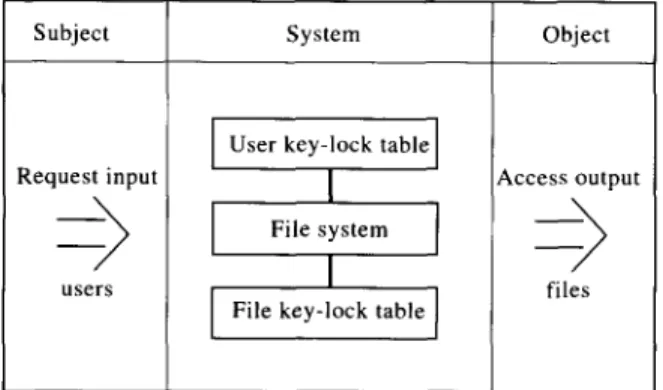
Subject System 1 Object
Request input Access output
files
M.-S. Hwang et alJAn access control scheme
3. New dynamic access control method
In this section we propose a new dynamic two- key-lock-pair method for information protection of computer systems. Since our two-key-lock-pair access control method is based on Chineseremainder theorem, we first introduce the
theorem.
Theorem 1 (Chinese remainder theorem). (I/ Let PI, Pz, . ., P, be pairwise relatively prime integers and let n=P1xP2x...xP,. Then the system of equations
X=Ximod P,fori=I,2 ,..., t
has a common solution X in the range [0, n - l]. By Chinese remainder theorem, we can use two sets {L,,
L27 . . ., LL,} and {L’,, Li, . . . . LL} of primes as the
lock values of users and files respectively. Let rO be the number that denotes the access right of user i to file j. Then we can calculate two sets {K,, K2, . . .) K,,,) and {K’,, Ki, . . . . KL} of key values for users and files respectively, by the equations
TABLE 1. An access control matrix
Ki=r,modLjforj= 1,2, . . ..NFi. I<i<m; (4)
K;=rtimodL,fori=1,2 ,,.., Nj,ll;ign, (5)
where NF, is the number of files in the system when user i is added to the system and NUj is the number of users in the system when file j is added to the system. After this, we can see that the access right of user i to file j can be computed by the equation
Ki mod Lj if NUj<i, rii =
K, mod L, otherwise.
We use the following example to explicate the above method.
Example 1. Consider a file system as depicted in Table 1. The sequence of users and files being added into the system is the same as that in Section 2. By the above method we maintain two key-lock tables for users and files as in Tables 4 and 5. Zf we want to compute the access right r54 of user 5 to file 4, then we find that NU, is 4 in the file key-lock table. Since NU, < 5, by equa- tion 6, the access right of user 5 tofile 4 is
r54 = KS mod LI, =255mod 11 u1 4 4 0 1 4 2 u, 2 1 3 0 4 3 u, 1 1 2 1 0 3 u, 2 1 0 4 3 2 US 0 3 3 2 4 2 UC 2 3 3 0 2 3
TABLE 2. The user key-lock table
K# L, W U, Null 5” 0 UZ 7 U, 6 ;: 2 2 U, 7 53 3 US 340 54 4 UC, 92 5” 4 = 2.
It is easy to see that if we want to delete a user/ file, we have to update many key values in the user and file key-lock tables. In order to solve this
TABLE 3. The file key-lock table
K’ I
L:
NU,
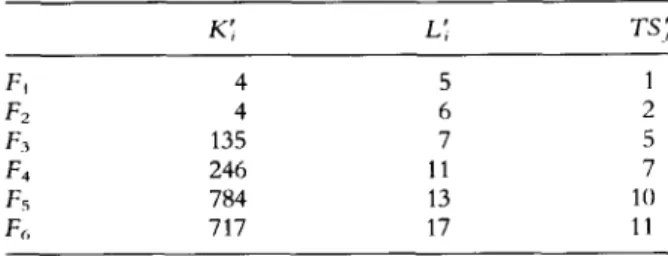
F1 4 5” 1 FZ 4 5’ 1 F3 65 52 3 F4 526 5” 4 & 9149 54 6 F, 10967 55 6Computers & Security, Vol. 75, No. I
problem, we introduce the concept of time stamp to replace NU and NF in the user and file key- lock tables.
Time stamp has a unique property of identifying the sequence of users and files added to system. We can assign a distinct time stamp number to the user/file when a user/file is added to the system. Therefore, when deleting a user/file, we simply remove the user/file entry from the user/file key- lock table and the order of users and files in the system is not changed. On the other hand, delet- ing a user or file from the system when using NU and NF results in confusion about which formula should be used in equation (6). For example, when we delete U3 and U, from Table 4 (thus 4 users remains in the system) and add a new file (F,) to the system with NU, = 4, by equation (6) r76 will be computed with K, and Lr6. Obviously, it is not correct.
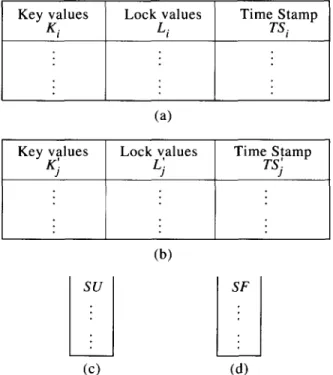
The data structure used in our scheme consists of one user-key-lock table, one file key-lock table, one user prime number stack (SU) and one file prime number stack (SF), which are shown in Fig. 2. The user (file) key-lock table has three
TABLE 4. The user key-lock table
UI Nllll 5 0 u2 7 6 2 u, 1 7 2 u4 7 11 3 us 255 13 4 u, 297 17 4
TABLE 5. The file key-lock table
K’ ,
L;
NV,
F1 4 5 1 F2 4 6 1 F3 135 7 3 F4 246 11 4 Fs 784 13 6 F, 717 17 6columns: key value column, lock value column and time stamp column. When a user i is added to the system, the system assigns the current time stamp number to the user and pops a prime num- ber from the user prime number stack as the lock of the user. The key value of the user i is com- puted by the system of equations
K, = rti mod L,‘, for all existentfiles j,
where rY is the access right of the user i to the file j. When a file is added to the system its key value, lock value and time stamp are similarly computed. We use Example 1 in this section to show our method. The resulting user/file key-lock tables are shown in Tables 6-9.
In the following subsections we give algorithms, based on our two-key-lock-pair access control method, for inserting a user/file, checking access
Key values Kj Lock values Lj TimeT;!amp J
I
:
I
I
:
1
I
:
I
I
I
(b)
cc>
(4
Fig. 2. Data structure of (a) the user key-lock table, (b) the file key-lock table, (c) the user prime number stack (Su) and (d) the file prime number stack (SF).
M.-S. Hwang et alJAn access control scheme
right of a user to a file, changing the access right of a user to a file and deleting a user/file.
3.1 Inserting a new user/file
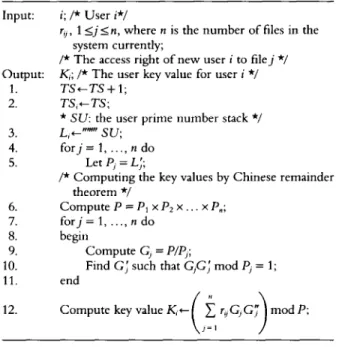
When inserting a new user to the system, we assign the value of the current time stamp as the time stamp of the user and pop a prime number from the user prime number stack as the lock value of the user. Then we compute the key value of the user by equation (4) using the access rights, which are inputs, of the user to the files in the system and using the lock values of the files in the system. To add a new file to the system the proce- dure is similar to adding a new user to the system, except that we use the lock values of users. The algorithm for inserting a new user to the system is given in Table 10.
verify the access right of the user to the file. If the time stamp value of the user is greater than that of the file, i.e. user i is added to the system after tile j, we use the key of the user and the lock of the file to verify the access right of the user to the file. The algorithm for checking access right of a user to a file is given in Table 11. The following example shows verification of access requests. Example 2. Let us consider Example 1 again. Zf an access request (Vi) FjJ RJ = (3, 4, 1) occurs, the system fetches the time stamps TSJ and TS: from the user and jile key-lock tables. Since TS, = 4 < TS; = 7
r34 = K; mod L3 = 246 mod 7 3.2 Checking access right
To check the access right of user i to file j, we first compare the time stamp values TS, and TSJ of the user and the file. If the time stamp value of the user is smaller than that of the file, i.e. user i is added to the system before file j, we use the lock of the user and the key of the file to
= 1.
Because r34 = 1 is equal to the request access right 1, the access request is accepted. On the other hand, assume that another access request (Vi, F,, RJ = (5, 4, 3) occurs. The system fetches time stamps TSs and TS; from user and-file key-lock tables. Since TSs = 8 > TS: = 7
TABLE 6. The user key-lock table
K UI Null LJ1 7 LJ.3 1 LJ‘J 7 u, 255 UC 297 L, TS 5 0 6 3 7 4 11 6 13 8 17 Y
TABLE 8. The user prime number stack (SU) 19
23 29 31 37
TABLE 7. The file key-lock table
K F, 4 F2 4 F3 135 F4 246 FS 784 F<> 717 L: 3: 5 1 6 2 7 5 11 7 13 10 17 11
TABLE 9. The file prime number stack (SF)
19 23 29 31 37
Computers 8 Security, Vol. 75, No. I
TABLE 10. Algorithm for inserting a new user to the system Input: i; /* User i*/
rY, 1 <j I n, where n is the number of files in the system currently;
/* The access right of new user i to file j */ Output: K,; /* The user key value for user i */
1. TS+T.S+ 1; 2. TS,tTS;
* SU: the user prime number stack */
3. L,t”*” su;
4. forj= 1, . . . . n do 5. Let ZJ, = L;;
/* Computing the key values by Chinese remainder theorem */
6. ComputeP=P,xP,x...xP,; 7. forj=l,...,ndo 8. begin
9. Compute G, = P/P,,;
10. Find C; such that G,GJ mod P, = 1; 11. end
12. Compute key value K,+
TABLE 11. Algorithm for checking access right
Input: (i, j, R,); /* User i, file j and the request access right of user i to file j */
Output: Acceptance or rejection; 1. if TS; < TS, 2. then r,,tK, mod LJ 3. else r,,tK; mod L,; 4. ifR,<r;, 5. then “accepted” 6. else “rejected”; rs4 = KS mod L; =255mod 11 = 2.
Because rJ4 = 2 is smaller than the request access right 3,
the access request is rejected.
3.3 Changing access right
When the access right is changed from rV into
Y;, we first compare the time stamp values TS,
and TS,! of the user and the file. If TS, > TSj, we re-compute the user key Ki by using all lock
values LJ of files with time stamp less than TSi. By Chinese remainder theorem, we can compute the new K, from the old Ki according to the equation
K+[Ki+(ri-rq)GiGI] modP, (7)
where L,, Lz, . . ., L, are the lock values of t
files with time stamp less than TSi,
P=L,xL*x... x L,, G, = P/L; and GI is the value such that Gi X G! mod Li = 1. If TSi < TSj, the
equation becomes
(8)
The following example shows how to change the access right of a user to a file.
Example 3. Assume that the access right r4bz is changed from 1 to 2, the system fetches the time stamps TS4 and
TS; from the user and file key-lock tables. Since TS;=2<TS4=6
K4 = W4 + (r & - rd2) G4~ ;] mod p4
= (7+ 175) mod 210 = 182.
3.4 Deleting a user/file
By Chinese remainder theorem, a user can be arbitrarily deleted from the user key-lock table. The deletion will not affect the previously dis- cussed actions. To avoid using large prime num- bers as lock values, which would result in large key values, we can recycle the released prime numbers by pushing it back to the user prime number stack. The prime number is then reserved for future users. The algorithm for deleting a user from the system is given in Table 12. To delete a file from the system the procedure is similar to deleting a user from the system.
The following example shows how to delete a user from the computer system.
M.-S. Hwang et al/An access control
scheme
Example 4. Let us consider Example 1 again. Assume that user 3 is deleted from the system. We only delete the entry of user 3 from the user key-lock table, and the prime L3 = 7 is then reserved for future users by pushing it back to the user prime number stack.
4.
Practical issues
The most serious problems of key-lock-pair access control methods is the overflow problem of key values and the complexity of arithmetic operations on overflowed numbers [ 10,111.
In order to overcome these overflow problems such that the system can be practical, two approa- ches are proposed. One can group relevant users and files into classes so that each class consists of less files and users and the overflow problem can be controlled within some tolerable limit [ 121. The other is to decompose key values in B-based form. Key values K, (for i = 1, 2, . . ., m) are decomposed as follows
K,=C~B’-‘+C~~,_~~B’-*+...+Ci~B+C,~ (9)
where all coefficient (C,,) of B satisfy 0 I Clk >B fork = 1, 2, . . . . j.
To avoid overflow computations, B has to be cho- sen to be less than the square root of 2’ and larger than lock value Li (i.e. B’RS2’ and L;<B for i=12 1 , ..., m). Here we assume that the computer system is in I-bits integer wordlength.
K, is thus represented by
(C, ,
Ci( j - l), . . , C,a, Gil). Using this representation of keys they can be stored without overflow problem.TABLE 12. Algori.thm for deleting a user from system Input:
1. 2.
i; /* User i */
/* Delete the entry for the user from user key-lock table */
PUSH L, to the user prime number stack (SU); Delete U, from the user key-lock table;
5.
Conclusion
We have proposed a new two-key-lock-pair access control method based on Chinese remainder the- orem and the concept of time stamp for file pro- tection systems. Its advantageous properties include:
??When a user requests the access of a file, our scheme can easily reveal the access right of the user to the file.
??To delete a user/file from the system, the scheme need only delete the key value of the user/file.
??To insert a user/file, the scheme need only compute the key value of the user/file.
O-TO change the access right of a user to a file, the scheme need only modify the key value of the user or the file.
The lock value (a prime number) is recyclable. This property avoids using large prime num- bers as lock values, which will reduce the size of a key value when users and files are inserted into and deleted from the system frequently. The complexity of storage space for keys and locks of m users and n files is only O(m+n) when the overflow problem of key and lock values is ignored.
Consider upgrading a computer system so that a “new” access right, e.g. “read & execute”, is pro- vided. By our scheme the keys and the locks of the existing users and files do not have to be changed. The only thing our scheme has to do is to accommodate this new access right for future users and files. Some previous schemes, e.g. [7-91, do not have this property. The complexity issues about the access control methods are thor- oughly discussed in [6] and we refer interested readers to this paper.
Computers & Security, Vol. 15, No. I
Acknowledgements
The authors wish to thank many anonymous referees for their suggestions to improve this paper. Part of this research was supported by the National Science Council, Taiwan, ROC, under contract No. NSC83-0408-E-009-039.
References
[II VI [31 [41 [51D.E.R. Denning, Cryptography and Data Security, Addison-
Wesley, Reading, MA, 1982.
R.W. Conway, W.L. Maxwell and W.C. Morgan, On the implementation of security measures in information system. Communications of the ACM, 15 (4) (Apr. 1972) 211-220.
G.S. Graham and P. J. Denning, Protection-principles and practice, Proceedings of the Spring Joint Computer Con- ference 40, pp. 417-429, AFIPS, Montrale, NJ, 1972.
C.C. Chang, On the design of a key-lock-pair mech- anism in information protection system, BIT, 26 (1986) 410-417.
C.K Chang and T.M. Jiang, A binary single-key-lock
[61 [71 VI [91 [lOI [111 [=I
system for access control, IEEE Tramactions on Computer, 38 (10) (1989) 1462-1466.
J.J. Hwang, B.M. Shao and P.C. Wang, A new access control method using prime factorization, The Computer
Journal, 35 (1) (1992) 16-20.
J.K. Jan, C.C. Chang and S. J. Wang, A dynamic key- lock-pair access control scheme, Computers G Security, 10
(1991) 129-139.
C.S. Laih, L. Harn and J.Y. Lee, On the design of a single-key-lock mechanism based on Newton’s interpo- lating polynomial, IEEE Tramactions on Software Engineer-
ing, 15 (9) (Sep. 1989) 1135-1137.
M.L. Wu and T.Y. Hwang, Access control with single- key-lock, IEEE Transactions on Sojware Engineering, 10 (2) (1984) 185-191.
M.-S. Hwang and W.-P. Yang, A new dynamic access control scheme based on subject-object-list, Data G Knowledge Engineering, 14 (1) (1994) 45-56.
M.-S. Hwang, W.-G. Tzeng and W.-P. Yang, A two-key- lock-pair access control method using prime factoriza- tion and time stamp, IEICE Transactions on Informarion and Systems, E77-D (9) (1994) 1042-1046.
CC. Chang and J.K. Jan, An access control scheme for new users and files, International Journal of Policy Informa-