sufficiently low, over a few tens of kilometres of fibre, to allow AM/VSB lightwave systems to operate from 50 to 550 MHz in the 155Onm fibre window.
Conclusions: The feasibility of operating an analogue light- wave system over dispersive fibre using a directly modulated DFB laser has been demonstrated for the first time. The effect of fibre dispersion was to produce carrier suppression and second order sum products. By limiting the modulation depth to the linear region of the laser, a single octave, eight channel, broadcast quality, video transmission system was operated over 100 km of dispersive fibre.
Acknowledgments: We thank A. R. Beaumont and S. A.
Al-
Chalabi for helpful discussions, S. F. Carter for the use and characterisation of the fibre and the Director of Network Technology, Research and Technology, British Telecom for permission to publish this letter.P. A. ROSHER S . C. FENNING
6th Februury 1990 British Telecom Research Loboratories
Martlesham Heath, Ipswich, Suffolk IPS 7RE, United Kingdom References
Jerrold Cableoptin, December 1990
OLSHANSKY, R., and LANZISUU, v. A.: ‘60-channel FM video sub- camer multiplexed optical communication system’, Electron. Lett.,
1987,23, pp. 119&1198
CHINEN, K., GEN-EI, K., PIDOEON, R. E., and RANG, H. H.: ‘Forty-two- channel analog transmission using a low noise DFB laser module’. OFC 90, Paper ThG4
UPADHYAWLA, L. c., LIPSON, I., and HUANG, s. Y.: ‘Trunk quality Lightwave transmission of multiple AM NTSC signals’. OFC 90, Paper WH3
WAY, w. I., CHOY, M. M., VI-YAN, A., ANDREJCO, M., SAIFI, M., and LIN, G.: ‘Multichannel AM-VSB television signal transmission using an erbiumdoped optical fiber power amplifiers’, Phot. Tech. Lett.,
1989,1, pp. 343-345
MESLENER, G. I.: ‘Chromatic dispersion induced distortion of modu- lated monochromatic light employing direct detection’, IEEE J. Quantum Electron., 1984, QEM, (10)
MENDIS, F. v. c., and ROSHER, P. A.: ‘CNR requirements for subcarrier-multiplexed multichannel video FM transmission in optical fibre’, Electron. Lett., 1989, 25, pp. 72-14
THROUGHPUT PERFORMANCE
OF
MULTISTAGE INTERCONNECTION NETWORKS IN PRESENCE O F MULTIPLE M E M O R Y HOT SPOTSIndexing terms: Memories, Networks
A recursive formula to evaluate the throughput performance of multistage interconnection networks having two memory hot spots is derived. Classes of nonuniform traffic pattern are defined according to the relative locations of the hot spots. Numerical results show that the degradations are roughly the same under different classes of nonuniform trafiic pattern. Introduction: Most results regarding the performance of multistage interconnection networks (MINs) have been derived based on uniform traffic models. A uniform traffic model means that each processor independently generates memory access requests with identical rates and each memory module (MM) is equally likely to be the destination of any request. In a real world system, it is likely that one or more MMs store common variables of all processors and hence will be accessed more frequently than the others. This type of locality results in the
so
called ‘hot spot’ nonuniform traffic pattern. The bandwidth degradation of unbuffered MINs caused by the existence of a single hot MM had been studied in Reference 3. In this letter systems with multiple hot spots are considered.System model: The study is focussed on systems with two hot MMs. The MIN studied in this letter consists of n stages, each 536
stage has d - ’ crossbar networks of size a x a. For mathe- matical tractability, we make the following assumptions: (a) The number of independent processors is equal to the number of MMs and is denoted by N = a”.
(b) The network is operated synchronously and requests are not combined.
(c) The requests generated by a processor are independent of the requests generated by the other processors. The requests generated in a network cycle are also independent of the requests generated in the previous cycles.
(d)
Each processor generates at most one request in a network cycle and the probability that a processor generates a request in a network cycle is equal to r(0 5 r 5 1).(e) One of the hot MMs attracts requests with probability h ,
+
(1 - h ,-
h,)/N, the other with probability h,+
(1-
h ,-
h,)/N. A cool (nonhot) MM attracts requests with probabil- ity (1 - h ,-
h,)/N.U) Blocked requests are lost.
Performance analysis: To analyse the throughput per- formance, the relative locations of the two hot MMs must be known. For an n-stage MIN, the outputs can be numbered from top to bottom by a-ary sequences of length n. Without loss of generality, we assume the upmost output to be a hot MM which attracts requests with probability h,
+
(1- h,
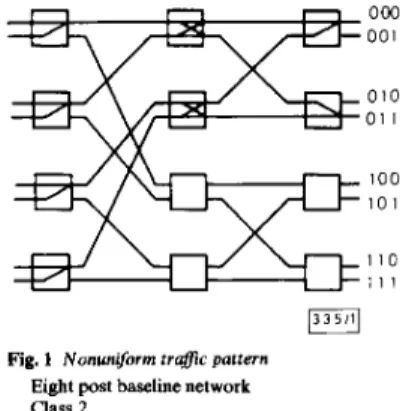
- h,)/N. Define the traffic as the class i nonuniform pattern if the ith digit, counted from right to left, of the a-ary represen- tation of the other hot MM is the leftmost digit which is not a 0. Fig. 1 illustrates an example of class 2 nonuniform tra& pattern of a three-stage baseline network. For convenience, we call the traffic pattern of the degenerated case (i.e. only one hot MM which attracts requests with probability h ,
+
h,+
(1 - h, - h,)/N) the class 0 nonuniform traffic pattern.000 001 010 01 I I00 IO I I 1 0 1 1 1
Fig. 1 Nonunform trafic pattern Eight post baseline network Class 2
Let us consider the uniform traffic model (h, = h, = 0) first. Let
S&;
r ) denote the throughput of an n-stage MIN with input rate r. ThenS&;
r) can be computed by(1) (2)
S&; r ) = as&
-
1; r’) r’ = 1-
(1-
r/a)” whereThe boundary condition of eqn. 1 is given by SdO, r ) = r. Next, let us consider systems having a single hot spot. Let S,(n; r, h) denote the throughput of an n-stage MIN under the single hot spot nonuniform traffic. Then we have
S,(n; r, h) = SI(n
-
1; r’, h’) + ( a-
l)Su(n-
1; r”) ( 3 ) where ah 1+
(a - 1)h h‘= (4)and
The boundary condition of eqn. 3 is given by S,(O; r, h ) = r for 0 I h I 1. Eqn. 3 results in different throughput performance from that given in Reference 3. The reason is that the model in Reference 3 allows each processor to independently generate two requests in a network cycle. It is not difficult to derive eqns. 4 and 6. Let us consider the expression for h’ given in eqn. 5. Suppose a hot port (i.e. a link which can reach the hot MM) which is an output of a switching element at stage 1 receives a request. Let t, and td denote the probabilities that the request received by the hot port is destined to the hot MM and a regular MM reachable from the hot port, respectively. It is clear that t , is equal to the probability that the request is destined to the hot MM provided it is destined to one of the MMs reachable from the hot port. After some calculations, we conclude that t, = [ h
+
(1 - h ) / N ] / [ h+
( 1 - h)/u]. It is also possible to show that t , = [(l-
h ) / N ] / [ h+
( 1 - , h ) / u ] . The excess probability for the hot MM of a request received by the hot port is equal to h’ = u h / [ 1+
( U - l ) h ] .Finally, let us consider systems having two hot MMs. Let S(n, i ; r, h , , h,) denote the throughput of an n-stage MIN under the class i nonuniform traffic pattern. Then we have S(n, i ; r, h , , h , ) = S(n - 1, i ; r’,
h;,
h,)+
(U - l)S,,(n - 1; r”) S,(n-
1; r*, h*)+
S,(n - 1; r**, h**)+
( U-
2 ) S d n O s i s n - 1 i = n where-2
-h2)1u
h* = 1+
(a - l ) h , - h , r(l -2
-
hz)10
r** = 1 - 1 - rh, -[
h** = 1+
(U-
1)hz-
h , andThe boundary condition of eqn. 7 is given by S(0, 0; r, hi, h,) = r. The above expressions can be verified by the same arguments we gave for the case of single hot MM.
Results and discussion: Fig. 2 shows the bandwidth (i.e., the throughput when r = 1) of a 10-stage MIN with a = 2 for various values of h , and h , under different classes of nonuni- form traffic pattern. In this Figure, we choose h , = h , = h. One can see that a higher degree of nonuniformity (i.e. a larger value of h ) results in a more severe bandwidth degrada- ELECTRONICS LE77ER.S 12th April 1990 Vol. 26 No. 8
tion. According to our numerical results, the bandwidth deg- radations under different classes of nonuniform trallic pattern are roughly the same. For example, when h , = h , = 0.1, the degradation is within 11.63% (class 3) and 13.01% (class 10).
j335121
excess probobtlity h Fig. 2 Bandwidth against request probability
1024 x 1024 MIN
a = 2
Although we focus our study on systems having two hot MMs, the analysis provided in this letter can be generalised to evaluate the throughput performance
of
systems having more than two hot MMs.T.-H. LEE 28th November 1989
Department of Communication Engineering National Chiao Tung Uniuersity Hsinchu, Taiwan, Republic of China References
P R I S ~ , a. F., and NORTON, v. A.: “‘Hot spot“ contention and combining in multistage interconnection networks’, IEEE Trans.,
1985, C-34, pp. 934-948
THOMAS, R. H.: ‘Behanour of the Butterfly parallel processor in the presena of memory hot spots’. Proc. 1986 Int. Cod. on Parallel Processing, Aug. 1986, pp. 6 5 0
mMBoRTsI$ A., and HALAISIS, c.: ‘Perfonnana of crossbar inter- connection networks in presence of hot spots’, Electron. Lett.,
1988.2.4, pp. 182-184
mmnms, A., and HALAISIS, c.: ‘Behaviour of circuit-switched multistage networks in presence of memory hot spot’, Electron. Lett., 1989, t5, pp. 83S834
FAST ALGORITHM FOR REAL JOINT TIME-FREQUENCY TRANSFORMATlONS OF TIME-VARYING SIGNALS
Indexing terms: Signal processing, Mathematical techniques, Fourier transforms
Instead of using the FFT, all the real joint timefrequency transformations (JTFT) can be evaluated by the same e@- cient transformation algorithm, using different time-indexed autowrrelation functions. The approach presented dramat- ically reduces the computation load. Our research suggests that a software package or a custom VLSI chip may imple- ment real JTFTs.
Introduction: Most joint time-frequency transformations (JTFT) known can be written as the Fourier transformation of the time-indexed auto-correlation function
JTFT(t, w) = R(t, ~ ) e - j ” ~ dz
- m
i
where the time-indexed auto-correlation function R(t, T) deter- mines the properties of JTFT. The most prominent subclass