國
立
交
通
大
學
資訊科學與工程研究所
碩 士 論 文
低儲存量及常數計算量的
公開金鑰廣播加密系統
Public Key Broadcast Encryption with Low Number of Keys and
Constant Decryption Time
研 究 生:劉易儒
指導教授:曾文貴 教授
低儲存量及常數計算量的公開金鑰廣播加密系統
Public Key Broadcast Encryption with Low Number of Keys and
Constant Decryption Time
研 究 生:劉易儒 Student:Yi-Ru Liu
指導教授:曾文貴 Advisor:Wen-Guey Tzeng
國 立 交 通 大 學
資 訊 科 學 與 工 程 研 究 所
碩 士 論 文
A ThesisSubmitted to Institute of Computer Science and Engineering College of Computer Science
National Chiao Tung University in partial Fulfillment of the Requirements
for the Degree of Master
in
Computer Science June 2007
Hsinchu, Taiwan, Republic of China
低儲存量及常數計算量的公開金鑰廣播加密系統
學生:劉易儒
指導教授:曾文貴博士
資訊科學與工程研究所
國立交通大學
摘要
在此篇論文中,我們提出了兩個公開金鑰廣播加密系統;第一種方法,我們把它稱為 BE-PI,它能夠達到O( r )的表頭長度(Header Size)、O( r )的計算量、O( 1 )的
公開金鑰儲存量及 的私密金鑰儲存量,其中r代表註銷使用者個數,n代 表使用者個數,這是首次在傳輸量O( r ) 的狀況下達到儲存量 的公開金鑰 廣播加密系統。另一種方法,我們把它稱做為 PK-SD-PI 系統,它可以做到 O( r ) 的表頭長度,O( 1 )的公開金鑰儲存量及 的私密金鑰儲存量,但它只需 要 O( 1 )的計算量;此外,藉由和 LSD 類似的方式,我們可以再把它改變成 PK-LSD-PI,並得到 O( 1 )的公開金鑰儲存量、 的私密金鑰儲存量及O( kr ) 表頭長度之間的取捨。另外,利用我們的方法,也能降低之前公開金鑰背叛者追 蹤方法中,公開金鑰數量至 O( 1 )。我們廣播加密的方法,在選擇明文攻擊模式下 (CPA),具有抵擋完全共謀的安全性,經過些許改變,我們可以使我們系統達到抵 擋選擇密文攻擊(CCA)的安全性。 ) (log n O ) (log n O ) (log2n O ) (log11/k O + 關鍵字:廣播加密、撤銷機制、背叛者追蹤
Public Key Broadcast Encryption with Low Number of Keys and
Constant Decryption Time
Student: Yi-Ru Liu
Advisor: Dr. Wen-Guey Tzeng
Institute of Computer Science and Computer Engineering
National Chiao Tung University
Abstract
We proposed two public-key broadcast encryption schemes. The first scheme, called the BE-PI scheme, has O( r ) header size, O( r ) computation cost, O( 1 ) public keys and
private keys, where r is the number of revoked users and n is the number of users. This is the first public-key BE(broadcast encryption) scheme that with
private keys under O( r ) header size. The other scheme, we call it PK-SD-PI scheme, has O( r ) header size, O( 1 ) public keys, private keys and only O( 1 ) computation cost. By using similar technique in LSD. We can convert it to PK-LSD-PI scheme, has O( 1 ) public keys and private keys with header size tradeoff. Using our method, it also can reduce public key size to O( 1 ) in public traitor tracing scheme. Our BE system is static full-collusion resistant secure under chosen plain attack (CPA). With little modification, it can also against chosen cipher attack (CCA). ) (log n O ) (log n O ) (log2 n O ) (log1 1/k O + O(kr)
誌
謝
我首先要感謝我的指導老師曾文貴教授,在我碩士班的學習
過程中,帶領我深入了解密碼學及資訊安全的領域,老師認真的研究
精神,亦使我受益良多。另外我要感謝口試委員,交大資工蔡錫鈞教
授、清大資工孫宏民教授及中央研究院資訊科學研究所呂及人教授,
在論文上給我許多的建議與指導,讓我的論文更加完善。除此之外,
我要感謝實驗室學長朱成康和學姐林孝盈的指導,實驗室同學陳仕
烽、周昆逸、實驗室學弟沈宣佐、陳宏達、高翎恩、曾智揚及學妹廖
怡翔,和你們一起討論和學習是一件愉快的事。
最後,我要感謝我的父母,不論在精神或物質上都給我極大
的支持,讓我在無後顧之憂的情況下可以順利完成學業。在此,以此
文獻給所有我想感謝的人。
Contents
Chapter1 Introduction ...1
Chapter2 Relative Work...3
2.1Private Key Broadcast Encryption...4
2.2Public Key Broadcast Encryption ...15
2.3Tracing Traitor...18
Chapter3 Background...21
3.1Bilinear Groups...21 3.2 CBDH assumption...21 3.3 CDH assumption ...21 3.4Broadcast encryption ...22Chapter4 Our Scheme ...24
4.1The BE-PI scheme ...24
4.2The BE-PI-2 scheme ...27
4.3The PK-SD-PI scheme ...31
4.4The PK-LSD-PI scheme...34
Chapter5 Security Analysis...35
5.1The BE-PI scheme ...35
5.3The BE-PI-2 scheme ...38
5.4The PK-SD-PI-2 scheme...39
5.5The BE-PI-2 and PK-SD-PI-2 scheme with reducing header size ...40
5.6The BE-PI scheme with IND-CCA security...41
Chapter6 Conclusion ...43
Chapter1
Introduction
Broadcast Encryption schemes enable a center to deliver encrypted data to a large set S of N users. For any set S , we can deliver an encrypted message to users u∈S, while the users u∉S cannot get information about the message. Such schemes are useful in pay-TV systems, the distribution of copyrighted material on encrypted CD/DVD disks, internet multicasting of video, music and magazines, etc..
In 1993, Noar and Fiat [1] formalized the basic definitions and paradigms of this field. A broadcasted message M is usually sent in the form <Hdr(S,k),Ek(M)>, where k is a session key for encrypting M via a symmetric encryption method E . An authorized
user in S can use his private keys to decrypt the session key k from Hdr(S,k), then use k to decrypt message M .The performance measures of a broadcast encryption scheme are the header size, the size of private keys held by each user, the size of public keys and the time for decryption. A broadcast encryption scheme should be able to resist the collusion attack from revoked users. A scheme is fully collusion-resistant if even all
revoked users collude, they get no information about the broadcasted message.
Broadcast encryption schemes can be static or dynamic. For a dynamic broadcast encryption scheme, the private keys of a user can be update from time to time, while the private keys of a user in a static broadcast encryption scheme remain the same through the lifetime of the system. Broadcast encryption schemes can be public-key or secret-key. For a public key broadcast encryption scheme, any one can broadcast a message to an arbitrary group of authorized users by using the public system parameters, while for a
secret-key broadcast encryption scheme, only the special dealer, who knows all secrets of the system can broadcast a message.
Our scheme is stateless public-key broadcast encryption system. The first stateless broadcast encryption system was proposed by Naor and Litspiech in 2001 [12]. They regard the problem of “designing stateless broadcast encryption as” “solving subset cover problem”. They present two methods .One is “Complete Subtree”(CS) technique. In the CS algorithm, everyone needs to storeO(logn) keys with O(rlog(n/r))header size, where n is the number of users and r is the number of revoked users. Another
major improvement of there idea was the “subset diffenrence”(SD) technique. They use pseudorandom function to reduce the number of keys for an user needs to store. They also break the lower bound based on the information security. In the SD algorithm, everyone needs to store O(log2 n) keys with O(r) header size. In 2003, Dodis and Fazio
[6] introduce how to transform a secret-key to a public-key BE system. They use “Identity-Based Encryption (IBE)” and “ Hierarchical Identity-Based Encryption (HIBE)”technique to transform CS and SD to public-key broadcast encryption scheme with O(1) public key and keeps private key parameter. In 2005, Boneh [4] proposed a
pulic-key broadcast encryption system with short ciphertext and private key. However, this scheme needs very large public-key storage space ( O( n ) ) and receivers need to use
all public keys for decryption message.
First of our public BE scheme has O(logn)private keys and only O( r ) header
size. The other one can reduce PK-SD computation cost to O(1). Our scheme is static secure based on CBDH problem under CPA mode. We can build it with CCA secure by applying Fujisaka and Okamoto method[9].
Chapter2
Relative Work
Consider two trivial BE systems. If we assign everyone with only one key*, and we revoke r users .Then we will need to send n-r encrypted message to each user. The
header size is O( n ). On the other hand, if we assign 2 to each user **. The header size n will become O( 1 ) but there are too many keys (O(2n−1) )need to be stored. How to get good performance between header size and storage size is the major problem.
Following table is the performance of stateless broadcast encryption schemes.
Private-key Broadcast Encryption:
Method Header Size Priv. key Size Comp. cost
* O(n) O(n− r) O(1)
** O(1) O(2n−1) O(n)
CS[12] O(rlog(n/r)) O(logn) O(loglogn)
PRSG or OWF- based SD[12] O(r) O(log2n) O(log n) LSD[13] O(kr) O(log1+1/k n) O(logn) Jho[14] ) ) 1 /( ) 2 ( 1 ( c p r p N p r O + − + + + ) (cp O O(c) SIC[15] O(kr) O(log n) O(n1 k/ ) RSA Accumulator-based
Asano[16] O(rloga(n/r)+ r) O(1) (2 log )
2
n
O a
SIC[15] O(kr) O(1) O((n1/klog2n)/k)
Public-key Broadcast Encryption:
Method Header Size Priv.key Size Pub. Key Size Decryption Comp.cost CS-PK[6] O(rlog(n/r)) O(logn) O(1) O(1)
SD-PK[6] O(r) O(log2n) O(1) O(log n)
LSD-PK[6] O(kr) O(log1+1/kn) O(1) O(log n)
BGW(i) [4] O(1) O(1) O(n) O(n)
BGW(ii)[4] O( n) O(1) O( n) O( n)
Our BE-PI O(r) O(log n) O(1) O(r)
Our PK-SD-PI
) (r
O O(log2n) O(1) O(1)
For designing stateless broadcast encryption schemes. We can regard it as an subset-cover problem:
For a set N={1,2,3,…,n} How to set subset S1,S2,...Sw ⊂N such that for any N R⊂ we can find t i i i
S
S
S
,
,...,
2 1 whereS
i1∪
S
i2∪
...
∪
S
it =N \RIn the above system. We can regard N as users. All set S has an unique key i K , i
elements in S are the users who have key K . t is the header size for sending message to i
subset N \R. Key size for each user is the number of subsets a user belongs to.
2.1Private Key Broadcast Encryption
In private key BE system, only the server who knows all secrets can broadcast encrypted message. Here we introduce CS, SD, LSD and SIC schemes.
2.1.1 Complete Subtree (CS) Scheme
This scheme was proposed by Noar[12] in 2001. The collection of subsets
N S S
tree with N leaves. For any node v in the full binary tree , the subset i S is the i
collection of receivers u that correspond to the leaves of the subtree rooted at node
i
v .Following picture (Fig1) is an example
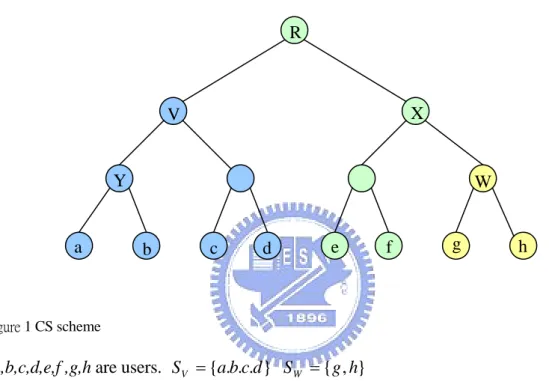
Figure 1 CS scheme
a,b,c,d,e,f ,g,h are users. SV ={a.b.c.d} SW ={g,h}
The key assignment method simply assign each subset S an independent and i
random value K . It is easy to see that each user only needs to store valuei K where i is i
nodes on the path from root to user. For example, user b needs to store Kb,KY,KV,KR.
In a full binary tree, we know that the height of the tree is log , so the key size for each n
user is O(logn). V b a c d W e f R Y X g h
Figure 2 Revoke d in CS scheme
For a given set R of revoked receivers, we remove the edges and nodes from revoked receivers to root, and we get subtree
1
i
S ,…, t
i
S . If we revoke user d in figure 1.
we get SY,Sc,SX (Fig 2.). The header will be like : > =<S ,S ,S ,E (k),E (k),E (k) Hdr X c Y K K K X c Y .
The cover size of CS scheme is at most rlog(n/r).
2.1.2 Subset Difference(SD) Scheme
Disadvantage of the Complete Subtree method is that N \R may be partitioned into rlog(n/r) subsets. It is large. Now we want to reduce the partition size.
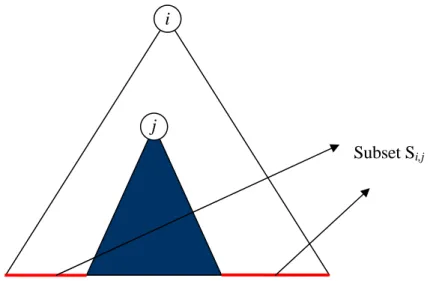
Consequently, we needs to increase subsets. A Subset Si,j in SD scheme is the Si −Sj
in CS scheme (Fig3.). V b a c W e f R Y X g h d
Figure 3 Subset Si,j in SD scheme
SD scheme partitions the non-revoked receivers into at most 2r-1 subsets. However, there are O(n) subsets for an user belongs in. It means that everyone needs to store
) (n
O keys. It is very impractical, so we use pseudorandom function to derive keys from parent’s label. Let G:{0,1}n →{0,1}3n be a pseudo-random sequence generator that triples the input, whose output length is three times the length of the input; For each node
i v . We assign it a labeli n 3 } 1 , 0 {
= . Let GR(S) denote the left third of the output of G
on seed S , GR(S) the right third and GM(S) the middle third. We say that n
n
G{0,1} →{0,1}3 is a pseudo-random sequence generator if no polynomial-time adversary can distinguish the output of G on a randomly chosen seed from a truly random string of similar length. Now, consider the subtree T (root at i v ). i jL and jR
are i's left and right child. We will use the following top-down labeling process. The root is assigned a label L .The label i
L
j i
L, is computed from GL(Li)and
R
j i
L, is computed fromGR(Li).The key Ki,j of set Si,j is derived from GM(Li, j). Therefore, if we get the label value of v , we can derive all keysi Ki,j={Ki,j| j is an descendant of i} of subset Si,j. Now, each user only needs to store Labeli,j= {labeli,j| i is ancestor of u ,
i
j
and for each i , j is the sibling of nodes on the path from user to i }.For example :
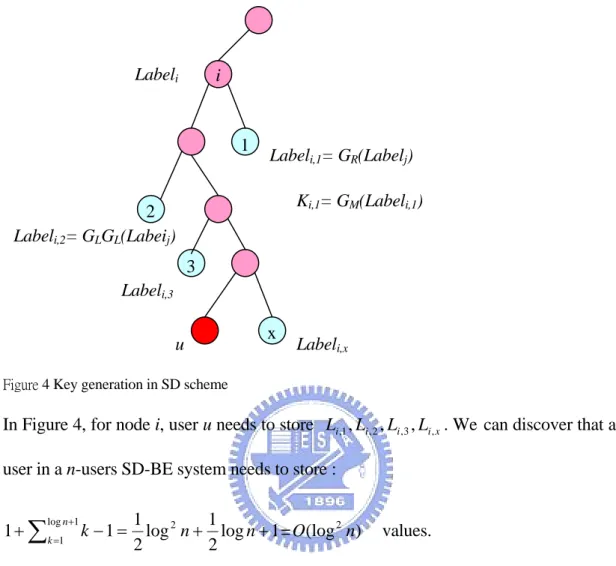
Figure 4 Key generation in SD scheme
In Figure 4, for node i, user u needs to store Li,1,Li,2,Li,3,Li,x. We can discover that an
user in a n-users SD-BE system needs to store :
1 log 2 1 log 2 1 1 1 log 1 2 1 − = + + +
∑
=n+ k n n k = (log ) 2 n O values.The Cover. For a set R of revoked receivers, we find Steiner Tree ST(R) with the property that any u∈N\R that is below a leaf of tree has been covered. We start by making T =ST(R) and then iteratively remove nodes from T until T consists of just
a single node:
1. Find two leaves v and i v in T such that there least-common-ancestor j v
does not contain any other leaf of T . Let v and l v be the two children of k v .v is k
ancestor of v and j v is ancestor of l v . (i v =l v =k v when there is only one leaf left) 2. If vl ≠ then add the subset vi Sl,i to the collection; likewise, if vk ≠ add the vj
subset Sk,j to the collection.
3. Remove from T all the descendants of v and make it a leaf
u Labeli
Labeli,1= GR(Labelj)
Labeli,3 1 2 3 x i
Ki,1= GM(Labeli,1)
Labeli,2= GLGL(Labeij)
A cover in SD scheme contains at most 2r-1 subsets for any set of r revocations.
2.1.3 LSD Scheme
In 2002, Halevy and Shamir propose Layer Subset Difference (LSD) method which can reduce key size to O(log1+1/k) with header size O(kr).
Here we describe the simplest version of the Layered Subset Difference scheme where k=2.
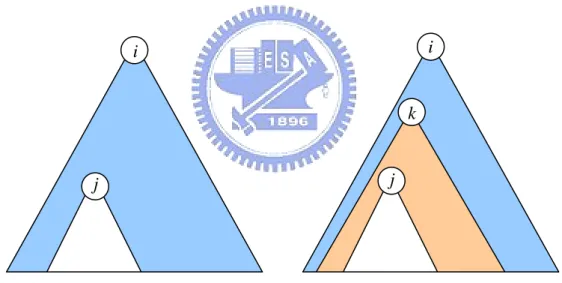
In LSD, set partition is the same as SD scheme. A set Si,j we can split it into
j k k
i S
S, ∪ , ( k is a descendant of i and j is a descendant of k). Figure 5 demonstrates the set Si,k ∪Sk,j =Si,j.
Figure 5 Subset in LSD
We define some of the logn levels as “special”. The root is considered to be at special level, and in addition we consider every level of depth
) log(n
t⋅ for t=1... log(n)as special. We define set Si,j is an useful set if i and
j belong to the same layer or i is at a special layer. Any set in SD we can present by at
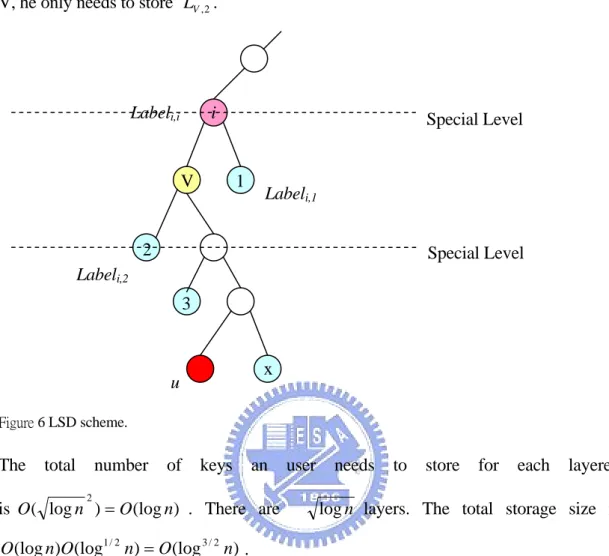
most two useful sets. The keys need to be stored for each user u is similar to SD scheme, but it only need to store Li,j where Si,j is an useful set. For example, user u in Figure6
i i
k
for ascendant i. The labels he needs to store is the same in SD scheme, but for ascendant V, he only needs to store LV,2.
Figure 6 LSD scheme.
The total number of keys an user needs to store for each layered is O( logn2)=O(logn) . There are logn layers. The total storage size is
) (log ) (log ) (log 1/2 3/2 n O n O n O = .
Any subset in SD scheme is at most divided into two subsets in this scheme. So header size is at most 4r-2.
Using the similar method, we can divide a subset S\R into more subsets and get )
(log11/ n
O + k storage size with O(kr) header size tradeoff.
2.1.4 SIC Scheme
Addrapadung proposed Subset Incremental Chain (SIC) [15] scheme in 2005. This scheme improves storage size to O(logn)and header size to O(r) with O(n)
computation cost. Using RSA-Accumulator technique, it can reduce storage size to O(1) , but it needs more computation for finding primes. This scheme also can be layered. We introduce no layered situation.
u Labeli,i Labeli,1 Labeli,2 1 2 i V 3 x Special Level Special Level
Graph-decomposition.
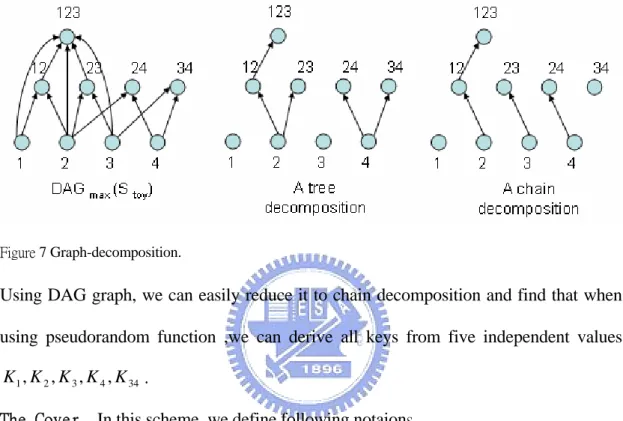
This paper’s authors give a method to analyze the relationship between keys. For any set S, we can regard it as a node . If set A⊂ there is a direct path from A to B . In B
following example Stoy ={{1},{2},{3},{4},{1,2},{2,3},{2,4},{3,4},{1,2,3}}
Figure 7 Graph-decomposition.
Using DAG graph, we can easily reduce it to chain decomposition and find that when using pseudorandom function ,we can derive all keys from five independent values
34 4 3 2 1,K ,K ,K ,K K .
The Cover. In this scheme, we define following notaions For i, j∈N ={1,2,...,n} and i< denote: j
}}, ,..., { },..., 1 , { }, {{ : }}, ,..., { },..., 1 , { }, {{ : i j j j j j i j i i i i j i − = ← + = →
l :The leftmost leaf under v v
r :The rightmost leaf under v v
BTL:The set of internal nodes which are left children
BTR:The set of internal nodes which are right children
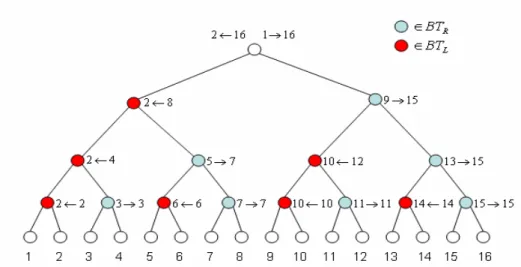
For root, we assign 1→n and 2←n. For each internal node, if v∈BTL we
assign it lv + 1←rv , otherwise v∈BTR we assign it lv →rv −1.A 16 users
Figure 8 Sets of SIC scheme
All sets in SIC scheme are:
U
U
L R BT v v BT v v v v SIC l r l r n n S ∈ ∈ ← ∪ → ∪ − → ∪ ← + = ( 1 ) ( 1) (1 ) (2 )Using previous graph decomposition method. We can arrange all sets into chain decomposition graph. For instance, we can arrange all sets in Figure8 into Figure 9.
1 1,2 1,2,3 1,...,4 1,...,5 1,...,6 1,...,7 1,...,8 … 1,...,16 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 3,4 2,3,4 5,6 5,6,7 7,8 6,7,8 5,...,8 4,...,8 3,...,8 2,...,8 9,...,15 9,10 9,10,11 9,...,12 9,...,13 9,...,14 11,12 10,11,12 13,14 13,14,15 3,...,16 2,...,16 4,...,16 5,...,16 6,...,16 7,...,16
Figure 9 Chain decomposition.
1. Based on PRSG:
Choosing an PRSG n n
G:{0,1} →{0,1} . For each chain, we only need to generate an independent value for root, then all nodes above it can be derived from root. For example, )K123 =G(K12)=G2(K1 . In each chain, user stores keys for subsets which he belongs to and nearest to the root. For example in the Fig.8, our paradigm with the chain decomposition in the Figure9 point out user2 needs to store the keys
12 16 ~ 2 8 ~ 2 234 2,K ,K ,K ,K
K .Since one user is at most in logn+1chains, the storage size for each user is O(logn).
2. Based on RSA-Accumulator
We construct a Maximin Matrix An×m .
n = The number of users. m = The number of chains.
Maximin Matrix Definition:
For a set system X, for all S∈SX there exist j:1≤ j≤m where
ij S N i ij S i a min \ a max∈ < ∈
Consider a chain decomposition {G1,...,GM}∈SX
For each chain Gj :S1 → ...→Sl we construct j' column vector s
w w ij i S S S i otherwise if if l w a \ 0 1 1 + ∈ ∈ ⎪ ⎩ ⎪ ⎨ ⎧ =
Then we choose a random number s, a big integer N = pq and n distinct primes p . j
Compute secret value p(u) and assign to each user.
N
s
u
p
m j pauj jmod
)
(
1∏
==
N s S k m j p i saij j mod ) ( 1 ) (max
∏
= ∈ =User can derive key k(S) if u∈S:
N
u
p
S
k
m j p i saij auj jmod
)
(
)
(
1 ) (max∏
= − ∈=
If u∉S, 0(maxi∈S aij −auj)< .User does not know the factor of N, so he can not compute it on exponentiation. Following figure is an exhibition:
1 1,2 1,2,3 1,...,4 1,...,5 1,...,6 1,...,7 1,...,8 2 3 4 5 6 7 8 3,4 2,3,4 5,6 5,6,7 7,8 6,7,8 5,...,8 4,...,8 3,...,8 2,...,8 ⎥ ⎥ ⎥ ⎥ ⎥ ⎥ ⎥ ⎥ ⎥ ⎥ ⎥ ⎦ ⎤ ⎢ ⎢ ⎢ ⎢ ⎢ ⎢ ⎢ ⎢ ⎢ ⎢ ⎢ ⎣ ⎡ 0 1 1 3 3 1 1 7 1 0 1 2 3 1 1 6 2 1 0 1 3 1 1 5 3 1 1 0 3 1 1 4 4 1 1 3 0 1 1 3 5 1 1 3 1 0 1 2 6 1 1 3 2 1 0 1 7 1 1 3 3 1 1 0 SIC T ) ( 10 21 31 43 53 16 17 87
)
1
(
s
p p p p p p p pp
=
) ( 17 12 31 43 53 16 17 80)
8
(
s
p p p p p p p pp
=
Maximin matrixFigure 10 Translate decomposition chain into Maximin matrix.
User 1 can derive subset key K123 by:
0 8 0 7 0 6 0 5 0 4 0 3 0 2 2 1 7 8 1 7 1 6 3 5 3 4 1 3 1 2 2 1
(
1
)
)
123
(
s
p p p p p p p pp
p p p p p p p pk
=
=
Security of this scheme is based on RSA Assumption. Using this scheme , everyone only needs to store O(1) keys , but needs to compute Maximin matrix and find n primes. The header size of SIC scheme is at most 2r-1. It is same as SD scheme.
2.2Public Key Broadcast Encryption
In Public key BE system, everyone can broadcast encrypted message without any secret. Dodis and Fazio [6] showed how to translate the SD and LSD methods to the public key setting, while having a fixed constant size public key.
The main idea is Identity Based Encryption (IBE) [8] and Hierarchical Identity Based Encryption (HIBE) [2]. IBE is a public encryption system. In this system we can input any string and generate a pair of keys. Public key can be generated by everyone and the correspondent private key for user only can be generated by private key generator (PKG) .Advantage of this technique is that we can use our e-mail address or phone number to be our public key. Such that people do not need to store any public key. It saves a lot of storage space. HIBE is an enhancement of IBE. In HIBE, everyone has a unique Hierarchical ID and each user can derive his descendant users. We can send encrypted message to any user and only receiver’s ascendants can decrypt it ( include receiver). For example, if an user’s HID is tw.nctu.cs . He can decrypt all message which pattern is like tw.nctu.cs.* , but he can not decrypt messages like tw.nctu.ee or tw.gov …etc.
2.2.1 Public key -Complete Subtree (PK-CS) Scheme
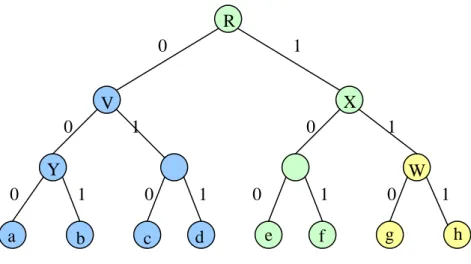
The main idea of this method is rename all sets (nodes) with an unique ID, then we can use IDE scheme. First, we let ID(root)= R . Then , the ID of left child we concatenate 0 after parent’s ID, and ID of right child we concatenate 1 after parent’s ID. In Figure11 ID(Y)=R00 , ID(b)=R001 , ID(W)=R11
Figure 11 ID of PK-CS scheme
The size of private key for each user needs to store is the same as CS scheme. In figure10 , user b needs to store the private keys where ID=R001 , ID=R00 , ID=R0 and ID=R . The public key size isO(1).This is equal to IBE system. Header size and computation cost are equal to CS scheme. For any people want to send encrypted message, he can find set covers of users, then uses public keys of these ID .
2.2.2 Public key -Subset Different (PK-SD) Scheme
Transfer SD scheme is similar with CS scheme. The hard problem is that, in this system all values of sets are not independent. Parent’s value can derive child’s value. The answer to solve this question is HIBE system. We define following notations:
i
v :Node i
j i
S, :Set Si −Sj . It is same as SD scheme.
i
L : Label of node i.
j i
L, : Label of set Si,j. It can be derived from L . i
PRI j i
K, :private key of setSi,j PUB j i
K, :public key of set Si,j
V b a c d W e f R Y X 0 1 0 0 0 0 0 0 1 1 1 1 1 1 g h
ID(x),HID(x): The object’s name of x
The ID of each node v is the same as PK-CS scheme. We need to give an unique i
HID for each Li,j.
Figure 12 HID of PK-SD scheme
In above Figure ID(vv)=R0 ID(v )=R001 b
For root , ID(root)= R
For label L , HID(i L )=ID(i v ) i
For label Li,j i ≠ j , HID(Li,j)=(ID(L ),[ID(i v )\ID(j v )]) i
[ID(v )\ID(j v )]: The different between ID(i v ) with ID(j v ). For each different i
symbol. We use “,” to separate it.
Now, each label has an unique HID and same relationship in SD-scheme. For example, In above figure:
HID(LV,b)=( R0, 0, 1 ) HID(LR,e)=( R,1,0,0 ) HID for keys Ki,j, HID(Si,j)=(HID(Li,j),2)
We can use HIBE system to derive all value properly. The number of values for each user need to store in PK-SD is equal to SD scheme. Each user stores the private keys of
V b a c d W e f R Y X 0 1 0 0 0 0 0 0 1 1 1 1 1 1 g h
HID(Li,j), where Li,j is the label needs to be stored in SD scheme. However, in HIBE system , private key length is linear to max level which is O(logn). By sharing some parameter, the private key size is about twice of SD scheme (O(log2n)).By using the HIBE technique in [2]. The header size is still O( r ), the public key size is O(1), and the computation cost is O(logn)exponentiations for key derivation.
2.3Tracing Traitor
In a BE system, message was encrypted and only the subscribers can decrypt the ciphertext. However, a traitor (malicious subscriber) may clone his decoder and sell the pirate decoder for profits. A traitor tracing scheme is a scheme with capability to find these pirate users. A traitor tracing scheme is fully k-resilient if it can point out all traitors where the number of traitors is less than k.
2.3.1 Dynamic Shares Scheme
Tzeng and Tzeng[21] proposed an efficient fully k-resilient Public-Key Traitor
Tracing scheme by using dynamic shares. There scheme needs O(k) header size, )
1 (
O private keys, O(k) public keys and O(k) computation cost.
System setup. Center select a large prime q and select a degree-z polynomial z≥2k
∑
= = z t t tx q a x f 0 (mod ) )( with coefficient over Z . The user’s secret key is q f(x) and public keys are g,ga0,gf(1),...,gf(z)
Registration. When a receiver i, i>z registers, the center give the receiver i a decoder with the share (i,f(i))(private key)
We call (j,f(j)) an unused share if it has not been assigned to any receiver.
Encryption. The sender randomly selects unused shares
)) ( ,
(j1 f j1 ,(j2, f(j2)),…, (jz, f(jz)) and a random number r∈Zq, and a session key s. The sender computes the enabling block
) , ( ),..., , ( ), , ( , , 1 ( ) ) ( 1 ) ( 1 2 1 0 r rf j rf j rf jz ra g j g j g j g sg T =
And broadcast T,E'(s,M) where E' is a secret-key cipher.
Decryption. When receiving T,E'(s,M) , the receiver compute s by
∏
− = + = = ∑ = ⋅ =− 1 0 ) ) ( ) ( ( ) ( ) ( 0 0 1 0 0 0 /[( ) ( ) ] / / z t ra ra i f x f r ra x rf i f r ra s g sg g sg g g sg z t t t z t t z λ λ λ λ Where x0 = j1,x1 = j2,...,xz−1 = jz and xz =i∏
≤ ≠ ≤ − = z t j j t j t x x x 0λ are lagrange coefficients.
He then uses s to decrypt E'(s,M) to obtaion M
Traitor Tracing. There are two black box traitor tracing algorithms for following situations.
I. If pirate decoder’s key is not linear combination of shares.
1. For every possible m-receiver set
{
c1,c2,...,cm}
, m≤k ,(a) Randomly select z-m unused shares
{
j1,..., jz−m}
and construct a test) , ( ' ,E s M T where ) , ( ),..., , ( ), , ( ), , ( ),..., , ( ), , ( , , ) ( ) ( 2 ) ( 1 ) ( ) ( 2 ) ( 1 2 1 2 1 0 m z m j rf m z j rf j rf c rf m c rf c rf r ra g j g j g j g c g c g c g sg T − − =
(b) Feed T,E'(s,M) to the decoder.
(c) If the pirate decoder does not output correct M ,
{
c1,c2,...,cm}
is apossible traitor set.
2. Output the smallest of all possible traitor sets found in Step 1c.
II. If pirate decoder’s key is linear combination of shares.
1. For every possible m-receiver set
{
c1,c2,...,cm}
, m≤k ,(a) Randomly select a degree-z polynomial h(x)=
∑
iz=0aizi that passes)) ( , ( )),..., ( , ( )), ( , (c1 f c1 c2 f c2 cm f cm points.
) , ( ' ,E s M T where 0, ,( 1, (1)),( 2, ( 2)),...,( , rh(jz)) z j rh j rh r ra g j g j g j g sg T =
(c) Feed T,E'(s,M) to the decoder.
(d) If the pirate decoder outputs correct M ,
{
c1,c2,...,cm}
is a possibletraitor set.
Chapter3
Background
3.1Bilinear Groups
We use bilinear maps and bilinear map groups.
1. G and G1 are two (multiplicative) cyclic groups of prime order q; 2. g is a generator of G
3. eˆ is a bilinear map eˆ:G×G→G1
eˆ has the following properties: 1.For all u,v∈Gq and x,y∈Zq,
xy y x v u e v u eˆ( , )= ˆ( , )
2.Let g be a generator of G, we have eˆ(g,g)= g1 ≠1 is a generator of G1
3.2 CBDH assumption
The CBDH problem is to compute eˆ(g,g)abc from give (g,ga,gb,gc), where g is random generators of Gq and a,b,c are random over Zq. We say that CBDH is
hard t, )−
( ε if for any probabilistic algorithm A with time bound t, there is some k0
such that for any k ≥ , k0
Pr[ ( , , , )= ˆ( , ) : ←⎯⎯ \{1}, , , ←⎯⎯ q]≤ε u q u abc c b a Z c b a G g g g e g g g g A
3.3 CDH assumption
The CDH problem is to compute gab from give (g,ga,gb), where g is random generators of Gq and a,b are random over Zq. We say that CDH is (t,ε)−hard if for any probabilistic algorithm A with time bound t, there is some k0 such that for any
0 k k≥ , Pr[ ( , , )= : ←⎯⎯ \{1}, , ←⎯⎯ q]≤ε u q u ab b a Z b a G g g g g g A
3.4Broadcast encryption
A public-key BE scheme consist of three probability polynomial-time algorithms: -Setup(1z,ID,U). let U ={U1,U2,...,UN}. It takes as input the security parameter z, a system identity ID and a set U of users and output a public key PK and N
private key sets SK1,SK2,...,SKN, one for each user in U .
-Enc(PK,S,M). It takes as input the public key PK, a set S ⊆ of authorized users U
and a message M . It outputs a pair Hdr(S,m),C of the ciphertext header and body, where m is a randomly generated session key and C is the ciphertext of M encrypted by m via some standard symmetric encryption scheme, e.g AES.
-Dec(PK,SKk,Hdr(S,m),C)).It takes as input the public key PK , the private key
k
SK of user Uk , the header Hdr(S,m) and the body C. If Uk ∉ , it cannot S
decrypt C to obtain the message M . If Uk∈ , it can decrypt the header S
) , (S m
Hdr to obtain the session key m and then uses m to decrypt the ciphertext body C for message M .
The system is correct if all users in S can get the broadcasted message M .
Security. We describe the indistinguishability security against the adaptive chosen ciphertext attack(IND-CCA security) for broadcast encryption[4] as follows. Here, we focus on the security of the session key, which in turn guarantees the security of the ciphertext body C . Let Enc* and Dec* be like Enc and Dec except that message M and the ciphertext body C are ignored. The security is defined by an adversary A and a challenger C via the following game.
Init. The adversary A choose a system identity ID and a subset S*⊆Uof users that it wants to attack.
Setup. The challenger C runs )Setup(1z,ID,U to generate a public key PK and private key sets SK1,SK2,...,SKN. The challenger C gives *SKi,Ui ∉S to A .
Query phase 1. The adversary A issues decryption queries Qi,1≤i≤n of form ),
, ,
(Uk S Hdr S ⊆S* , Uk∈S and the challenger C responds with
), , , (
* PK SK Hdr
Dec k which is the session key encrypted in Hdr.
Challenge. The challenger C runs Enc*(PK,S*) and output Hdr*(S*,m), where
m is randomly chosen. Then, C choose a random bit b and a random session key m* and sets mb =m and m1−b =m*. C gives Hdr*((S*,m),m0,m1)to A .
Query phase 2. The adversary A issues decryption queries Qi,n+1≤i≤qD of form ),(Uk,S,Hdr S ⊆S* , Uk ∈S and the challenger C responds with
) , , ( * PK SK Hdr Dec k .
Guess. A outputs a guess b’ for b.
In the above the adversary A is static since it choose the target user set S*
before the system setup. Let:
, 1 }] 1 , 0 { *), , ( * * ), , , 1 ( ) , ( , * : ) , *, , , ( Pr[ 2 ) ( \ * 0 1 , − ⎯⎯ ← ← ← ⊆ = ⋅ = − u z U S U O cca ind A b S PK Enc Hdr U ID Setup SK PK U S b m m Hdr SK PK A z Adv π Where *}SKU ={SKi :1≤i≤N} and SKU\S* ={SKi :Ui ∉S .
Definition 1. A public-key BE scheme Π=(Setup,Enc,Dec) is
CCA IND
q
t, , D)− −
( ε secure if for all t-time bounded adversary A that makes at most
D
q decryption queries, we have Adv ,Π− (z)<ε
cca ind
Chapter4
Our Scheme
We show two public BE schemes with different performance tradeoff. First, we introduce our main idea of construction. In BE-PI scheme, we use
⎡
logn⎤
+1 polynomials )fi(x on exponents with degree 2i (i=0 to⎡
logn⎤
), and the secrets of) ( t
i u
f are shared to all users ut. When sending an encrypted message to U \R, we broadcast information about fi(R). Then all users in U \R can compute fi(0) and
decrypt the message. In PK-SD-PI scheme, deployment is similar to SD scheme, all users are leaves of the tree. We use polynomials with degree 1. In this scheme not all user’s shares are over the same polynomial. An polynomial f v(x)
j only pass point
)) ( ,
(ut fjv ut where ut are v’s descendants of level j. Users only get secret shares of
) ( t
v j w
f ,where v is an ancestor of user and w j are index of nodes on the path from user to v .When broadcasting to a subset Si,t in SD scheme, we broadcast fji(t) in this scheme. For each scheme ,we present two methods for implementation. The first one has smaller storage size and decryption cost. The second one can reduce header size with slight modification.
4.1The BE-PI scheme
4.1.1 BE-PI scheme
1. Setup(1z,ID,U): z is the security parameter, ID is the identity name of the system, and }U ={U1,U2,...,Un is the set of users in the system. Let Gq and G1 be the bilinear groups with the pairing function eˆ, where q is a large prime. This bilinear system as described above is of security parameter z. Then, the system dealer does
the following:
z Choose a cryptographically secure hash function H :{0,1}*→Gq. z Choose a secure symmetric encryption scheme E with key space Gq. z Choose a generator g of group Gq, and let lg=logg and g1 =eˆ(g,g)
z Compute )g () H(ID||"f"||i|| j i
j
a
= for 0≤i≤
⎣
log2 n⎦
andi
j 2
0≤ ≤ ,
where “f” means polynomial-related parameters.
Remark. The underlined polynomials, are, 0≤i≤
⎡
log2n⎤
,
∑
= = i j j i j i x a x f 2 0 ) ( ) ( (mod q)The system dealer does not know the coefficients a(ji) =lgH(ID||" f"||i|| j)
But, this does not matter.
z Randomly choose a secret ρ∈Zq and compute
ρ
g . z Publish the public key PK =(ID,H,E,Gq,G1,eˆ,g,gρ)
z Assign a set SKk ={sk,0,sk,1,...,sk,⎡logN⎤} of private keys to user ,
1
, k N
Uk ≤ < where sk,i =(gρfi(k))
ρ is the master key of the system.
2. Enc(PK,S,M): , \ { , ,..., } 2 1 i il i U U U S U R U
S ⊆ = = is the set of revoked users,
where l≥1. M is the sent message. The broadcaster does the following: z Let α =
⎡
log2l⎤
and L=2α.z Randomly select distinct il+1,il+2,...,iL >n . These U l t L t
i , +1≤ ≤ are
dummy users.
z Randomly select a session key m∈Gq
z Randomly select r∈Zq and compute 1≤t≤ L
r L j i i rf t tj j f ID H g ( ( ||" "|| || ) ) 0 ) (
∏
= = α αz The ciphertext header Hdr(S,m) is ) ) , ( ˆ , ( ),..., ) , ( ˆ , ( , ) , ( ˆ , ( , , ) , ( ˆ , ( (0) 1 (1) 2 (2) f (i ) r L r i f r i f r r f L g g e i g g e i g g e i g g g e m ρ α ρ α ρ α ρ α α Let b e g gf ij r grf ij j L j = ˆ( , ) = ,1≤ ≤ ) ( 1 ) ( ρ ρ α
z The ciphertext body is C =Em(M)
3. Dec(PK,SKk,Hdr(S,m),C):Uk ∈S. The user Uk does the following
z Compute ( ) 1 ) ( 0 ˆ( , ) k f r k f r g g g e b = ρ = ρα
z Use the header and Lagrange interpolation method to compute
∏
= = L j j j f r b g 0 1 ) 0 ( λ α ρ where q i k i i i i i i i i i i i i L j j j j j j L j j j − ⋅ ⋅⋅ − − ⋅ ⋅⋅ − = − ⋅⋅ ⋅ − − ⋅⋅ ⋅ − = + − + − 0 1 1 0 1 1 0 ), (mod ) ( ) )( ( ) ( ) ( ) )( ( ) ( λz Compute the session key
(2) ) , ( ˆ ) 0 ( 1 ) 0 ( 1 ) 0 ( 1 ) 0 ( m g g m g g g e m f r f r f r r f = = α α α α ρ ρ ρ ρ
z Use m to decrypt the ciphertext body C to obtain the message M.
Correctness. We can easily see that the scheme is correct by Equation (2)
(This technique with single polynomial can reduce public key size to O(1)of traitor tracing scheme in section 2.3 [21].)
4.1.2 Performance analysis
For each system, the public key is (ID,H,E,Gq,G1,eˆ,gρ), which is of size )
1 (
O . Since all systems can use the same (H,E,Gq,G1,eˆ,g), the real public key specific to a system is simply (ID,gρ). Each system dealer has a secret ρ for assigning private keys to its users. Each user Uk holds private keys
⎡ ⎤}
,..., ,
{ k,0 k,1 k,logn
k s s s
SK = , which each corresponds to a share of polynomial fi in
users are revoked, we choose the polynomial fα of degree 2 for encrypting the α session key, where 2α−1 <r≤2α. Thus, the header size is O(2α)=O(r). It is actually no more than 2r.
Since evaluation of a hash function is much faster than computation of a pairing and a modular exponentiation, we omit the cost or evaluating hash functions. To prepare a header, the broadcaster needs to do 2α +1 parings. However, broadcaster can precomputeeˆ(gρ,gfα(0)),eˆ(gρ,gfα(i1)),eˆ(gρ,gfα(i2)),...,eˆ(gρ,gfα(iL))before
broadcasting. Then broadcaster only need 2α +2 modular exponentiations, which is O( r ) modular exponentiations .Or broadcaster can send
( , ˆ( , (0)) , ,(1, (1)),(2, (2)),...,( , rf (iL))) L i rf i rf r r f g i g i g i g g g e m ρ α α α α α instead of r i f r i f r i f r r f L g g e g g e g g e i g g g e mˆ( , ) , ,( ,ˆ( , ) ,ˆ( , ) ,...,ˆ( , ) , (α ρ α(0) 1 ρ α(1) ρ α(2) ρ α( )
Receivers can compute ˆ( , f (i))r ˆ( , rf (i))
g g e g
g
e ρ α = ρ α by itself. Then the broadcaster
only need to compute 1 paring and O( r ) modular exponentiations. For a user in S to decrypt a header, the user needs to perform 1 paring functions and O( r ) modular exponentiations.
4.2The BE-PI-2 scheme
This scheme is slightly different to BE-PI scheme. Each user is not over the same polynomial F(x)=ρf(x) . In this scheme, every user u owns unique shares overFru(x)=ru f(x) where ru is a random value assigned by KDC.
4.2.1 BE-PI-2 scheme
1. Setup(1z,ID,U): z is the security parameter, ID is the identity name of the system, and }U ={U1,U2,...,Un is the set of users in the system. Let Gq and G1 be the bilinear groups with the pairing function eˆ, where q is a large prime. This bilinear system as described above is of security parameter z. Then, the system dealer does the following:
z Choose a cryptographically secure hash function H :{0,1}*→Gq. z Choose a secure symmetric encryption scheme E with key space Gq. z Choose a generator g of group Gq, and let lg=logg and g1 =eˆ(g,g)
z Compute )hi =H(ID||"h"||i for 1≤i≤
⎡
log2n⎤
, where “h” indicates theh-related hash values.
z Compute )ga(ji) = H(ID||"f"||i|| j
for 0≤i≤
⎣
log2 n⎦
and 0≤ j≤2i , where “f” means polynomial-related parameters.Remark. The underlined polynomials, are, 0≤i≤
⎡
log2n⎤
,
∑
= = i j j i j i x a x f 2 0 ) ( ) ( (mod q)The system dealer does not know the coefficients a(ji) =lgH(ID||" f"||i|| j)
But, this does not matter.
z Randomly choose a secret ρ∈Zq and compute gρ. z Publish the public key PK =(ID,H,E,Gq,G1,eˆ,g,gρ)
z Assign a set SKk ={sk,0,sk,1,...,sk,⎡logn⎤} of private keys to user , 1 , k n Uk ≤ < where ( , , ) ) 0 ( ) ( , ρ i f r k f r r i k g g g h s = k k i k i ρ i
h is the master key of the system.
and rk,i is randomly chosen from Zq,1≤i≤
⎡
logn⎤
.2. Enc(PK,S,M): , \ { , ,..., } 2 1 i il i U U U S U R U
S ⊆ = = is the set of revoked users,
where l≥1. M is the sent message. The broadcaster does the following: z Let α =
⎡
log2l⎤
and L=2α.z Compute )hα =H(ID||"h"||α .
z Randomly select distinct il+1,il+2,...,iL >n . These U l t L t
i , +1≤ ≤ are
dummy users.
z Randomly select r∈Zq and compute 1≤t≤ L r L j i i rf j t t H ID f j g ( ( ||" "|| || ) ) 0 ) (
∏
= = α αz The ciphertext header Hdr(S,m) is
)) , ),...( , ( ), , ( , , ) , ( ˆ , ( 1 (1) 2 (2) rf (iL) L i rf i rf r r g i g i g i g h g e m α α α α ρ α
z The ciphertext body is C =Em(M)
3. Dec(PK,SKk,Hdr(S,m),C):Uk ∈S. The user Uk does the following
z Compute ( ) 1 ) ( 0 ˆ( , ) k f rr k f r r g k g k g e b = α = α z Compute ( ) 1 ) ( ) , ( ˆ rk rf ij rrkf ij j e g g g b = α = α
z Use the header and Lagrange interpolation method to compute
∏
= = L j j f r j b g 0 ) 0 ( λ ρα where q i k i i i i i i i i i i i i L j j j j j j L j j j = − ⋅⋅ ⋅ − − ⋅⋅ ⋅ − − ⋅⋅ ⋅ − − ⋅⋅ ⋅ − = + − + − 0 1 1 0 1 1 0 ), (mod ) ( ) )( ( ) ( ) ( ) )( ( ) ( λz Compute the session key
) (2' ) , ( ˆ ) , ( ˆ ) , ( ˆ ) , ( ˆ ) 0 ( 1 ) 0 ( 1 ) 0 ( ) 0 ( 1 m g h g e g h g e m h g g e g h g e m f rr r f rr r f r r f rr r k k k k = ⋅ ⋅ = ⋅ α α α α ρ α α ρ ρ α α ρ
z Use m to decrypt the ciphertext body C to obtain the message M.
Correctness. We can easily see that the scheme is correct by Equation (2’)
4.2.2 Performance analysis
In this scheme, we need two more pairing computation than BE-PI scheme, and the storage size is twice as BE-PI scheme. However, we can reduce header size with following change.
4.2.3 Reduce BE-PI-2 header size
, 1 , k n Uk ≤ ≤ ⎡ ⎤ ) ,..., , , , ( } ,..., , , { ) ( ) ( ) ( ) 0 ( ) 0 ( ) 0 ( log , 1 , 0 , , 1 , 0 , 2 1 2 1 r f r f r f k r f k r f k f r r n k k k k k k L k k L k k k g g g h g g g g s s s z z SK ρ ⋅⋅ ⋅ = =
When broadcasting message to S \R, where { , ,..., }
2
1 i il
i U U
U
R= is the set of l
revoked users, we select index of functions c1,c2,...cw where 2c1 +2c2 +...+2cw =l
We can present l in binary string, so all c can be found easily, and v1,...,vt are remainder index of functions. Then the header Hdr(S,m) is
)) , ),...( , ( ), , ( ), , ( , , , ) , ( ˆ , ( ( v1(0) v2(0) ... vt(0)) 1 c1(1) 2 c1(2) 3 c2(2) rfcw(iL) L i rf i rf i rf f f f r r r g i g i g i g i g g h g e m l ρ + + +
Decryption: Users not in R can Compute eˆ(gρ,h)r by
r f f f f f f r r r f f f f f f r r rf r rf r rf r f f f r r f f f r r rf k rf k rf k f f f r k k r h g e g g e h g e g g e g g e g g e g g e g g e h g g e g z e g z e g z e g z e z g e cw r c r c t v v v k cw r c r c t v v v k kw c k c k c k t v v v k L k kw c c c t v v v ) , ( ˆ ) , ( ˆ ) , ( ˆ ) , ( ˆ ) , ( ˆ ) , ( ˆ ) , ( ˆ ) , ( ) , ( ˆ ) , ( ˆ ) , ( ˆ ) , ( ˆ ) , ( ˆ ) , ( ˆ )) 0 ( ... ) 0 ( ) 0 ( ) 0 ( ... ) 0 ( ) 0 ( ( )) 0 ( ... ) 0 ( ) 0 ( ) 0 ( ... ) 0 ( ) 0 ( ( ) 0 ( ) 0 ( ) 0 ( ) 0 ( ... ) 0 ( ) 0 ( ( )) 0 ( ... ) 0 ( ) 0 ( ( ) 0 ( 0 , ) 0 ( 0 , ) 0 ( 0 , ) 0 ( ... ) 0 ( ) 0 ( ( 0 , 1 , 1 2 1 1 2 1 2 1 2 1 2 1 2 1 2 1 ρ ρ ρ = = ⋅⋅ ⋅ = ⋅⋅ ⋅ + + + + + + + + + + + + + + + + + + + + + + + ) If k∉R, all ˆ( ,0, rfcd(0)) k g z
e ,1≤d ≤tcan be computed from shares
),... , ( ), , ( ), ,
(i1 grfcd(i1) i2 grfcd(i2) i3 grfcd(i2) and private keys grk,grkfc(k). )
4.3The PK-SD-PI scheme
4.3.1 The PK-SD-PI scheme
) ( ) ( 2 x f i ) ( ) ( 3 x f i ) ( ) ( 4 x f i 1 i i= 2 i 3 i 4 i t v U1 U2 U3 U4 U5 U6 U7 U8 -U1 holds -U3 holds
-For subset , is broadcasted so that U3and U4 cannot decrypt, but others can.
) ( ), ( ), ( 4 ) ( 4 3 ) ( 3 2 ) ( 2 i f i f i f i i i ) ( ), ( ), ( () 4 ) ( 3 2 ) ( 2 i f t f v f i i i t i S, () ) ( 3 t f i
Figure 13: Level polynomials, private keys and broadcasted shares for subtree Ti
We now present our PK-SD-PI scheme, which is constructed by using the polynomial interpolation technique on the collection of subsets in SD scheme.The system setup is similar to that of the BE-PI scheme. Consider a complete binary tree T of
⎡
logn⎤
+1 levels. The nodes in T are numbered differently. Each user in U is associated with a different leaf node in T. We call a complete subtree rooted at node i as “subtree T ”. iFor each subtree T of i η levels ( Level 1 to level η from top to bottom), we define the degree-1 polynomials fj(i)(x)=a(ji,1)x+a(ji,0)(modq)
Wherea(ji,)0 =lgH(ID||"sd"||i|| j||0)anda(ji,1) =lgH(ID||"sd"||i|| j||1),2≤ j≤η
For a user U in subtree k T of i η levels, he is given the private keys ,, fj(i)(ij)
j i
k g
s = ρ
For 2≤ j≤η, where nodes i1,i2,...,iη are the nodes in the path from node i to the leaf node for U (including both ends). We can read k sk,i,j as the private key of U k
(including both ends). We can read sk,i,j as the private key of U for the jth level of k
subtree T . In Figure 1, the private keys ( in the unmasked form) of i U1 and U for 3
subtree T with i η =4 are given.
Recall that in the SD scheme, the collection C of subset is }, , node of parent a is node : {Si,t i t i≠t
Where Si,t denotes the set of users in subtree T , but not in subtree i T . By our design, t
if the header contains a masked share for fj(i)(t), where node t is in the j-th level of subtree T , only user i U ink Si,t can decrypt the header by using his private key sk,i,j, that is, the masked form of fj(i)(s), for some s≠ , In Figure 13, the share t f3(i)(t) is broadcasted so that only the user in Si,t can decrypt the header.
For a set R of revoked users, let
z zt i t i t i S S S S , , , 1 2 12 1 , 1 , ,...,
= be a subset cover for U\R, the
header is like
)),
)
,
(
,
)
,
(
(
,
),...
)
,
(
,
)
,
(
(
),
)
,
(
,
)
,
(
(
,
,
(
) ( ) 0 ( ) ( ) 0 ( ) ( ) 0 ( ) ( ) ( 2 ) 2 ( 2 ) 2 ( 2 1 ) 1 ( 1 ) 1 ( 1 r t f r f r t f r f r t f r f r z z i z j z i z j i j i j i j i jg
g
e
g
g
me
g
g
e
g
g
me
g
g
e
g
g
me
g
S
ρ ρ ρ ρ ρ ρwhere node t is in the k jk − level of subtree th k
i
T , 1≤k≤ z. For decryption, a non-revoked user fins an appropriate subset
j jt
i
S , in the header and applies the Lagrange interpolation to compute the session key m.
4.3.2 Performance analysis
The public key is O ( 1 ), which is the same as that of the BE-PI scheme. Each user belongs to at most
⎡
logn⎤
+1 subtrees and each subtree has at most⎡
logn⎤
+1 levels. For the subtree of η levels, the user in the subtree hold η-1 private keys. Thus, the total number of shares (private keys) held by each user is⎡
⎤
⎡ ⎤⎡
log⎤
)/2 log ( 2 log 1 i n n n i = +∑
= , which is (log ) 2 nO . According to [12], the number z of subsets in a subset cover is at most 2|R|−1, which is O( r ).