Another Two-level Pointer Strategy for Location Management in PCS Networks
全文
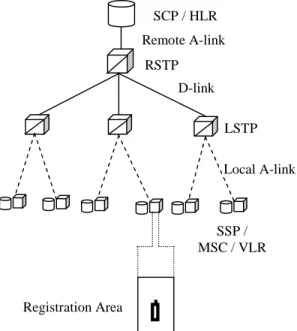
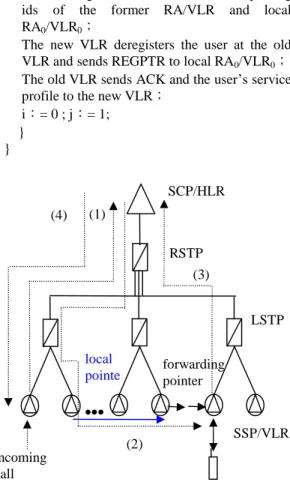
(2) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan. The user registers at the new RA/VLR, passing ids of the former RA/VLR and local RA0/VLR0; The new VLR deregisters the user at the old VLR and sends REGPTR to local RA0/VLR0; The old VLR sends ACK and the user’s service profile to the new VLR; i:= 0 ; j:= 1; }. collocated with the MSC, and the combination of MSC/VLR is to evolve to be SS7 compatible. The outline of this paper is as follows. Section 2 gives the proposed strategy. Section 3 presents the analytic model. Performance comparisons between the proposed strategy and other strategies are given in Section 4. Section 5 concludes the paper.. 2. The Proposed Strategy } We modify the IS-41 scheme [1,2] and pointer forwarding strategies [4,7] to obtain another twolevel pointer strategy as follows. When a user moves from one RA to another, it informs the switch (and VLR) at the new RA it arrives at. The switch at the new RA determines whether to employ the basic MOVE (when the user turns on the mobile) or the MOVE in our two-level pointer scheme. We use the following pseudo-code to describe the AnotherptrMOVE() and AnotherptrFIND() procedures in our scheme (also illustrated in Figures 2 and 3).. SCP/HLR (4). RSTP (3) LSTP local pointe r •••. HLR REGPTR. REGPTR REGPTR REGPTR REGPTR SSP/ MSC regptr regptr regptr VLR regptr. Figure 3. The AnotherptrFIND ( ) procedure.. regptr. i =1 j =0. i =2 j =0. •••. R. i =K-1 j =0. i =0 j =1. AnotherptrFIND(){ A call to a user is detected at the local switch; if the called user is in the same RA then return; The switch queries the called user’s HLR; HLR responds to the caller’s switch with local RA0/VLR0; The caller’s switch queries local RA0/VLR0; While ( the queried VLR is not the called user’s current VLR) The VLR queries the next VLR in the pointer chain (local pointer or forwarding pointer); / * The called user’s VLR has been found */ i :=0; j:=0; The called user’s current VLR sends user location to HLR; HLR sends the user’s location to the caller’s switch; }. R. R. SSP/VLR. incoming call. REGPTR. R. forwarding pointer. (2). regptr. R. (1). i =1 j =1. i =0 j =0 Figure 2. The AnotherptrMOVE() procedure. AnotherptrMOVE(){ /* The forwarding pointer i is initially set to be 0 and the local pointer j is 0 */ if(i < K-1 and j ≤ 1){ The user registers at the new RA / VLR, passing ids of the former RA/VLR and local RA0/VLR0; The new VLR deregisters the user at the old VLR; The old VLR sends ACK and the user’s service profile to the new VLR; i:= i + 1; } else if ( i ≥ K-1 and j ≤ 1) {. 75.
(3) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan. moves require K-1 forwarding pointer creations and 1 local pointer creation). The local pointer is always created for the last i moves. Thus, K ∞ i i (3) M′ = ∑ [( i − )S1 + S 2 ] α (i ) K K i=0 Cost F′ is derived as follows. After the last BasicMOVE operation (if any), the user traverses i (i − K ) local pointers and i i−K K − K K forwarding pointers. Thus, we obtain. 3. The Analytic Model In this section, we develop an analytic model (the same as in [5,7]) to study the performance of our twolevel pointer scheme based on different parameters for different classes of users. We characterize users by their call-to mobility ratios (CMRs). The CMR of a user is defined as the expected number of calls to a user during the period when the user visits an RA. (Note that the CMR is defined here in terms of calls received by a particular user, not calls originating from the user.) If the user’s call arrival rate is a mean rate λ, and the time the user resides in a given RA has a mean 1/µ, then the CMR, denoted as p, is given by. λ CMR = p = µ. F′ = F +. i . . ∞. ∑ { i − K K T i=0. i i − K − K K. (1). We define CB and CF to be the total cost for maintaining users’ information (location updating) and locating the user (location tracking) between two consecutive calls for the IS-41 basic scheme and for our pointer scheme. The following notations will be used in our analysis: M′ = expected cost of all AnotherptrMOVEs between two consecutive calls. F′ = average cost of the AnotherptrFIND. M = total cost of all the BasicMOVEs between two consecutive calls. m = cost of a single invocation of the BasicMOVE. F = cost of a single BasicFIND. S1 = cost of setting up a forwarding pointer between VLRs during an AnotherptrMOVE. S2 = cost of setting up a local pointer between VLRs and local VLR during an AnotherptrMOVE. T1 = cost of traversing a forwarding pointer between VLRs during an AnotherptrFIND. T2 = cost of traversing a local pointer between VLRs and local VLR during an AnotherptrFIND. K = the threshold number of RAs (that a user moves across) to set up a local pointer between two consecutive calls; also the threshold number of forwarding pointers in a chain. Then, we have (2) CB = M + F = m / p + F Before deriving formulas for our another twolevel pointer scheme, we make the following assumptions: (1). The call arrivals to a user form a Poisson process with arrival rate λ. (2). The residence time of a user at an RA is a random variable with a general density function f m (t ) and the Laplace transform.. T 2 . 1. +. }α (i ). (4). α (i ) be the probability that there are K RA crossings between two call arrivals. Probability α (i ) Let. is expressed as in [5,7]. α (i) = =. µ [ 1 − ƒm * (λ ) λ. ]2 [. ]i−1. ƒm * (λ ). (1 − g )2 g i −1. (5). p ∞. ƒ m (s) = ∫ ƒ m (t ) e −st dt *. (6). t =0. From (5), (6) and the two assumptions, we can rewrite (3) and (4) as. M′ =. S1 (1 − g )g K −1 (S 2 − S1 ) + p p(1 − g K ). F′= F +. (7). T1 (T 2 − KT 1 )(1 − g )g K −1 − + p p 1− gK. (. ). T2 (8) (1 − g ) g K − 1 g p − ( g ) 1 We assume that the RA residence time of a user is Gamma distributed with mean 1 / µ. The Laplace transform of a Gamma distribution is K −1. γ. γµ fm * (s ) = . Thus we have, λ + γµ γ. γ γµ = g = fm * (λ ) = λ + γµ p +γ. γ. . . In particular, when γ = 1, we have an exponential distribution for the RA residence time. We first consider the situation when the RA residence time is exponentially distributed. By setting γ = 1, we have. g=. Suppose that a user crosses i RA boundaries between two consecutive calls. Then, there are i i − forwarding pointer creations (every K K . 1 1+ p. Thus, (7) and (8) can be rewritten as. 76.
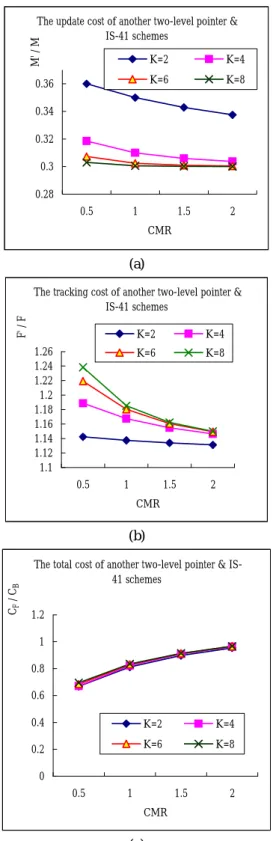
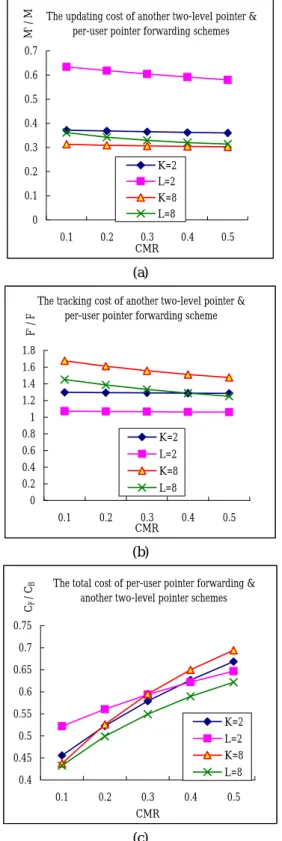
(4) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. S1 S 2 − S1 + p (1 + p )K − 1 T KT 1 F′ = F + T 2 + 1 − p (1 + p ) K − 1 M′ =. (12). have to be traversed, leading to the high set up cost. Without HLR updating for all MOVEs, pointer creations can result in cost reduction. Especially when p decreases with a longer pointer chain, setting up pointers can save more registration at the HLR. However, a long pointer chain increases the FIND penalty in general. But another two-level pointer can solve this problem by using local pointers to decrease the length of the pointer chain and also the delay time for setting up the call. Figures 5(a), 5(b) and 5(c) show the plots when N increases from 1.5 to 3. Even in this case, the cost of setting up a local pointer is slightly less than the cost of updating the HLR. The performance of another two-level pointer under CMR = 1 also excels that of the IS-41 scheme. Figures 6(a), 6(b) and 6(c) show cost comparisons between our scheme and the peruser forwarding strategy [5] under CMR ≤ 0.5. Figure 6(a) indicates that another two-level pointer saves more cost than the per-user forwarding in the MOVE procedure. In the FIND procedure in Figure 6(b), another two-level pointer is shown to yield more tracking cost. The total cost of another two-level pointer strategy is slightly higher than that of the peruser forwarding strategy, as shown in Figure 6(c). Based on the above result, it is observed that the proposed another two-level pointer strategy is suitable for users who change PCS registration areas frequently but receive calls less frequently.. (13). 5. Conclusions. (9) (10). From (9) and (10) we obtain. CF = M ′ + F′ = F + T2 +. (S 1 + T1 ) p. (S − S 1 ) − KT1 + 2 K (1 + p ) − 1 . (11). 4. Performance Comparison In the IS-41 scheme, updating the HLR and performing a BasicFIND involve the same number of messages between HLR and VLR databases, so we set m = F. Without loss of generality, we can normalize m = 1. We also assume that the cost of setting up a forwarding pointer is about twice the cost of traversing it, since twice as many messages are involved. That is, we set S1 = 2T1 and S2 = 2T2. We consider S1 = δ with δ < 1. Since the local pointer is more expensive than the forwarding pointer in terms of the setup cost, we can assume S2 = NS1 with N > 1. It is reasonable to assume that S2 < 1, too. From (2), (9), (10) and (11), we obtain. CB = 1 +. 1 p. (N − 1)δ p M′ =δ + M (1 + p )K − 1 F′ Nδ δ Kδ = 1+ + − F 2 2 p 2[ (1 + p )K − 1. ]. In this paper, we propose a new location management scheme, called another two-level pointer strategy. To update information, we use the local pointer to replace registration at the HLR, thus reducing the signaling traffic and database load of the HLR. A local pointer can maintain a user’s location information at the HLR useful. In location tracking, the locating cost of local pointers may be a little more than that of the forwarding pointers, but it is worthwhile as the length of the pointer chain can be shortened and the delay time for setting up the call can be reduced. Moreover, the user’s location information at the HLR can be updated and reused after “found”. Our studies indicate that our another two-level pointer scheme is suitable for users who change PCS registration areas frequently but receive calls less frequently (the total cost of our another twolevel pointer strategy is especially lower under CMR < 0.3). The overall result of performance comparison demonstrates that our new scheme outperforms the IS-41 scheme.. (14). CF p = { 1 + N δ + 3δ + CB 1+ p 2 2p. [2 (N − 1 ) − K ]δ } K 2[ ( 1 + p ) − 1 ]. (15). In Figures 4, 5 and 6, we plot the costs as function of CMR for various values of K, N and δ. Figure 4(a) shows that when δ = 0.3 and N = 1.5, another twolevel pointer can result in 60 – 70 percent reductions in location update cost compared to the IS-41 basic scheme. Figure 4(b) indicates that the FIND cost of another two-level pointer scheme is higher than that of the basic scheme. The reason is that the call to the user needs to traverse the pointer chain to find the user’s current location. However, our another twolevel pointer scheme can result in a 5 – 35 percent reduction in the total cost as shown in Figure 4(c). We observe that both the relative MOVE and FIND costs are decreasing functions of p (CMR). When p is small, the user crosses RAs more frequently. The pointers need to be set up and a long chain of pointers. 77.
(5) Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. 0.36. K=2. K=4. K=6. K=8. The update cost of another two-level pointer & IS-41 schemes. M' / M. M' / M. The update cost of another two-level pointer & IS-41 schemes. K=2 K=6. 0.6. K=4 K=8. 0.55 0.34. 0.5 0.45. 0.32. 0.4. 0.3. 0.35. 0.28. 0.25. 0.3 0.5. 1. 1.5. 2. 0.5. 1. CMR. 2. CMR. The tracking cost of another two-level pointer & IS-41 schemes. The tracking cost of another two-level pointer & IS-41 schemes. K=2. K=4. K=6. 0.5. 1. F' / F. (a). F' / F. (a). 1.26 1.24 1.22 1.2 1.18 1.16 1.14 1.12 1.1. 1.36 1.34 1.32 1.3 1.28 1.26 1.24 1.22 1.2. K=8. 1.5. 2. 0.5. K=2. K=4. K=6. K=8. 1. CMR. 1.5. 2. CMR. (b). (b). The total cost of another two-level pointer & IS41 schemes. The total cost of another two-level pointer & IS41 schemes. CF / CB. CF / CB. 1.5. 1.2 1.15 1.1 1.05 1 0.95 0.9 0.85 0.8 0.75 0.7. 1.2 1 0.8 0.6 0.4. K=2. K=4. 0.2. K=6. K=8. 0 0.5. 1. 1.5. 0.5. 2. 1. K=2. K=4. K=6. K=8. CMR. 1.5. 2. CMR. (c) Figure 5. Relative cost of another two-level pointer and IS-41 schemes with δ = 0.3 and N = 3 (a) the MOVE cost M′ / M (b) the FIND cost F′ / F (c) the total cost CF / CB.. (c) Figure 4. Relative cost of another two-level pointer and IS-41 schemes with δ = 0.3 and N = 1.5 (a) the MOVE cost M′ / M (b) the FIND cost F′ / F (c) the total cost CF / CB.. 78.
(6) M' / M. Int. Computer Symposium, Dec. 15-17, 2004, Taipei, Taiwan.. References. The updating cost of another two-level pointer & per-user pointer forwarding schemes. [1] EIA/TIA, “Cellular Radio Telecommunications Inter-system Operations,” Technical Report IS-41 ( Revision B ), EIA/TIA, 1991. [2] D. R. Wilson, “Signaling System No. 7, IS-41 and Cellular Telephony Networking,” Proc. IEEE, Vol. 80, No. 4, pp. 652-664, Apr. 1992. [3] Z. Mao and C. Douligeris, “An Integrated Strategy for Location Tracking in Mobile Networks,” IEEE Networks Commun. Conf., pp.777-781, 2000. [4] R. Jain, Y.-B. Lin, Charles Lo, and S. Mohan, “A Forwarding Strategy to Reduce Network Impacts of PCS,” Applied Research, Bellcore, Morristown, NJ07960, 1995. [5] R. Jain, and Y.-B. Lin, “An Auxiliary User Location Strategy Employing Forwarding Pointers to Reduce Network Impacts of PCS,” ACM-JCM Wireless Networks, pp.197-210, 1995. [6] R. Jain, Y.-B. Lin, C. Lo and S. Mohan, “A Forwarding Strategy to Reduce Network Impacts of PCS,” IEEE J. Select. Areas Commun., Vol.15, Oct. 1995. [7] W. Ma, and Y. Fang, “Two-level Pointer Forwarding Strategy for Location Management in PCS Networks,” IEEE Trans. Mobile Computing, Vol.1, pp.32-45, 2001. [8] K.-L. Sue and C.-C. Tseng, “One-step Pointer Forwarding Strategy for Location Tracking in Distributed HLR Environment,” IEEE J. Select. Areas Commun., Vol.15, pp.1455-1466, 1997. [9] S. Mohan and R. Jain, “Two User Location Strategies for Personal Communications Services,” IEEE Pers. Commun., pp.42-50, First Quarter 1994.. 0.7 0.6 0.5 0.4 0.3 K=2 L=2 K=8 L=8. 0.2 0.1 0 0.1. 0.2. 0.3 CMR. 0.4. 0.5. F' / F. (a) The tracking cost of another two-level pointer & per-user pointer forwarding scheme. 1.8 1.6 1.4 1.2 1 0.8 0.6 0.4 0.2 0. K=2 L=2 K=8 L=8 0.1. 0.2. 0.3 CMR. 0.4. 0.5. CF / CB. (b) The total cost of per-user pointer forwarding & another two-level pointer schemes. 0.75 0.7 0.65 0.6 0.55. K=2 L=2 K=8 L=8. 0.5 0.45 0.4 0.1. 0.2. 0.3 CMR. 0.4. 0.5. (c) Figure 6. Relative cost of another two-level pointer and per-user pointer forwarding schemes with δ = 0.3 and N = 3 (a) the MOVE cost M′ / M (b) the FIND cost F′ / F (c) the total cost CF / CB.. 79.
(7)
數據
相關文件
We do it by reducing the first order system to a vectorial Schr¨ odinger type equation containing conductivity coefficient in matrix potential coefficient as in [3], [13] and use
The aim of this theme is to study the factors affecting industrial location using iron and steel industry and information technology industry as examples. Iron and steel industry
For example, Ko, Chen and Yang [22] proposed two kinds of neural networks with different SOCCP functions for solving the second-order cone program; Sun, Chen and Ko [29] gave two
¾ Relocation, which modifies the object program so that it can be loaded at an address different from the location originally specified.. ¾ Linking, which combines two or
For the data sets used in this thesis we find that F-score performs well when the number of features is large, and for small data the two methods using the gradient of the
Secondly, the key frame and several visual features (soil and grass color percentage, object number, motion vector, skin detection, player’s location) for each shot are extracted and
The outcome of the research has that users’ “user background variable” and “the overall satisfaction” show significant difference, users’ “ actual feeling for service
Then using location quotient(L.Q.)to analyze of the basic industries in the metropolitan area, and population and employment multiplier of Hsinchu Area and Miaoli Area are analyzed