行政院國家科學委員會專題研究計畫 成果報告
給隱私權保護與著作權管理使用的語意式 web 規範互通語
言
研究成果報告(精簡版)
計 畫 類 別 : 個別型
計 畫 編 號 : NSC 98-2221-E-004-009-
執 行 期 間 : 98 年 08 月 01 日至 99 年 10 月 31 日
執 行 單 位 : 國立政治大學資訊科學系
計 畫 主 持 人 : 胡毓忠
計畫參與人員: 碩士班研究生-兼任助理人員:楊協達
碩士班研究生-兼任助理人員:楊竣展
碩士班研究生-兼任助理人員:吳建輝
碩士班研究生-兼任助理人員:郭弘毅
報 告 附 件 : 國際合作計畫研究心得報告
處 理 方 式 : 本計畫可公開查詢
中 華 民 國 99 年 12 月 27 日
1
行政院國家科學委員會補助專題研究計畫 成果報告
(計畫名稱)
給隱私權保護與著作權管理使用的語意式 web 規範互通語言
Semantics-enabled Web Policy Interchange Format (SewPIF) for Privacy
Protection and Digital Rights Management
計畫類別:■個別型計畫 □整合型計畫
計畫編號:NSC 98-2221-E-004-009
執行期間:2009 年 8 月 1 日至 2010 年 10 月 31 日
執行機構及系所:國立政治大學資訊科學系
計畫主持人:胡毓忠
共同主持人:
計畫參與人員:郭弘毅、吳建輝、楊竣展、楊協達
成果報告類型(依經費核定清單規定繳交):■精簡報告 □完整報告
本計畫除繳交成果報告外,另頇繳交以下出國心得報告:
□赴國外出差或研習心得報告
□赴大陸地區出差或研習心得報告
■出席國際學術會議心得報告
□國際合作研究計畫國外研究報告
處理方式:
除列管計畫及下列情形者外,得立即公開查詢
□涉及專利或其他智慧財產權,□一年□二年後可公開查詢
附件一
2
中 華 民 國 99 年 12 月 6 日
國科會補助專題研究計畫成果報告自評表
請就研究內容與原計畫相符程度、達成預期目標情況、研究成果之學術或應用價
值(簡要敘述成果所代表之意義、價值、影響或進一步發展之可能性)、是否適
合在學術期刊發表或申請專利、主要發現或其他有關價值等,作一綜合評估。
1. 請就研究內容與原計畫相符程度、達成預期目標情況作一綜合評估
■達成目標
□ 未達成目標(請說明,以 100 字為限)
□ 實驗失敗
□ 因故實驗中斷
□ 其他原因
說明:
建構一個 SemPIF 語意式電腦規範互通的架構, 在這個 SemPIF 的規範架構平台,電腦的規範
可以運用語意式規範語言來加以表示。我們可以更進一步利用 meta-PIF 的概念(也就是規範
的規範)來提供規範之間整合時的管理與優先度的設定以便於規範之間衝突無法解決的窘境。
我們落實個人資料分享與保護及著作權數位內容保護可以利用這個 SemPIF 的規範架構平台
來實踐。
我們已經將研究成果發表於 2 項知名的國際研討會,RuleML09 與 Web Intelligence (WI) 10
與一個和語意網有關的專書 Introduction to the Semantic Web: Concepts, Technologies and
Applications 篇章。另有一篇論文已完成投稿的工作,而另外一篇論文則在修定並且準備再投
稿。
3
2. 研究成果在學術期刊發表或申請專利等情形:
論文:■已發表 ■未發表之文稿 □撰寫中 □無
專利:□已獲得 □申請中 □無
技轉:□已技轉 □洽談中 □無
其他:
(以 100 字為限)
(已經發表的論文與已經投稿的論文請參考附錄)
Challenges for Rule Systems on the Web", The International RuleML Symposium on Rule
Interchange and Applications (RuleML 2009), Las Vegas, Neveda, USA, Nov. 5-7, 2009,
Springer-Verlag, LNCS 5858
Hu, Y. J. and H. Boley, SemPIF: A Semantic Meta-Policy Interchange Format for Multiple
Web Policies, 2010 ACM/IEEE Web Intelligence (WI) Conference, Aug. 31-Sep. 3, 2010.
Hu, Y. J., Unifying Semantic Privacy Protection Web Policies for Digital Rights Management
(DRM) System, (Book Chapter), Introduction to the Semantic Web: Concepts, Technologies
and Applications, iConcept, 2010.
Hu, Y. J. and Jiun-Jan Yang , A Semantic Privacy-Preserving Model for Data Sharing and
Integration, The International Conference on Web Intelligence, Mining and Semantics
(WIMS'11) , 2011 (submitted).
Hu, Y. J. et al., Reasoning Personal Privacy Intentions on the Social Web", 2010, (In
Revision).
學生碩士畢業論文:
郭弘毅、使用本體論與規則執行企業隱私保護規範
吳建輝、個人隱私揭露意願之推論
4
3. 請依學術成就、技術創新、社會影響等方面,評估研究成果之學術或應用價值
(簡要敘述成果所代表之意義、價值、影響或進一步發展之可能性)(以 500
字為限)
本研究案的學術成果的意義與價值在於解決 Web(全球資訊網)資料流通、分享、與保護的
問題。並且能夠透過語意網的本體論和規則兩大知識系統表達與具體落實執行能力讓電腦
軟體可以正確解讀出具有語意式的 Web 規範。利用標準的 Web 語言如 OWL, RIF 等來表示隱
私權保護與著作權保護的規範可以讓規範所需要表達語意可以更明確以避免混淆不清的窘
境。除了可以提升原有 XML 為基礎的權力表達語言如 ODRL, XrML, P3P, XACML 的缺失之外
也可以讓現有的規範語言如 Rein, KaOS 可以透過這個 SemPIF 互通語言的架構來達成互通
與規範整合的目的。
語意式電腦規範的價值在於找出人類法治規範可以落實到 Web 環境中自動化執行的概念與
規則讓電腦系統可以有效且自動化的來解讀和執行以避免完全用人類手動式處理規範的困
境。除此之外可以達成資訊有效分享與保護的目的,系統可以在資料分享與保護時在事先
與進行中的程序來加以檢驗,避免事後的冗長訴訟程序與資料不當揭露與使用所產生的副
作用。
本研究案的進一步發展可以將參照個人資料保護法與著作權保護法等法治規範將相對應的
語意式電腦規範運用到雲端運算的環境中,來解決雲端環境資料分享與保護的目的,讓雲
端中資料的個人資料保護與數位內容的著作權保護可以透過此電腦規範的表示與執行得到
適當的解決。
附件四
5
國科會補助專題研究計畫項下出席國際學術會議心得報告
日期:99 年 12 月 07 日
一、參加會議經過
本研討會於 2010 年 8 月 31-9 月 3 日於加拿大多倫多市的 York 大學舉行。York 大學位於多倫多市
近郊約 1 個多小時車程的郊區,附近的大學則有位於多倫多市世界知名的多倫多大學。
8 月 31 日的研討會首日進行的是 Workshop。9 月 1 日至 9 月 3 日則是正式的研討會。研討會分成
兩部分來進行:Web Intelligence, Intelligent Agent。在這個基礎上論文的發表大致上分成幾
個 track 來進行論文的發表。Web Information Retrieval and Filtering, Web Mining, Semantics
and Ontology Engineering, Social Network Analysis, Web Services, Distributed Problem
Solving, etc。從這些 tracks 的觀察我們可以知道這個研討會涵蓋面非常的廣,但是主要著重的
還是 Web Mining 以及 Web Information Retrieval。計畫主持人發表論文 SemPIF: A Semantic
Meta-Policy Interchange Format for Multiple Web Policies 所排定的時段是在 9 月 3 日早上
的 Semantics and Ontology Engineering IV 的場次。我也順便主持了這個場次其他演講者的論
文發表。本場次的演講共有 5 位的論文發表者,其中有一位大陸東北大學的研究學者並未出席,
另外德州大學的論文發表者則請人代打。另外則有京都大學、多倫多大學、及本人(代表政治大
學)
。本研討會在 9 月 2 日晚上舉辦餐宴於多倫多港上的遊輪上,台灣也有不少的學者參與此盛會。
計畫編號
NSC 98-2221-E-004-009
計畫名稱
給隱私權保護與著作權管理使用的語意式 web 規範互通語言
出國人員
姓名
胡毓忠
服務機構
及職稱
國立政治大學資訊科學系教授
會議時間
2010 年 8 月 31 日至
2010 年 9 月 3 日
會議地點
加拿大多倫多市
會議名稱
(中文)
IEEE/WIC/ACM Web 智慧與智慧型代理者技術國際研討會
(英文)
IEEE/WIC/ACM International Conference on Web Intelligence and
Intelligent Agent Technology
發表論文
題目
(中文)提供多重 Web 規範交換的語意式 meta 規範格式
(英文)
SemPIF: A Semantic Meta-Policy Interchange Format for Multiple Web
Policies
6
二、與會心得
對於本研討(IEEE/WIC/ACM Web 智慧與智慧型代理者技術國際研討會)會計畫主持人在過去幾年都
是這個研討會 Web Intelligence (WI)的論文評審委員(Program Committee)。這個研討會雖然在
語意網和智慧型代理者的知名度沒有 International Semantic Web Conference (ISWC), World
Wide Web (WWW), 以及 Autonomous Agent and Multi-Agent System (AAMAS)來得大。但是根據
往年和今年的經驗總論文的投稿數量也都可以達到 300-400 篇左右。主要的投稿來源還是來自於
大陸的學者以及分佈在世界各地大學與研究單位的大陸學者。這個國際研討會的論文有被收錄到
IEEE Explore 的數位圖書資料庫,因此這也是吸引人投稿的因素之一。除此之外,本國際研討會
也能夠每年分別在世界的五大洲選定國家來舉辦。整體來說研討會的論文主要議題還是在 Web
Intelligence (WI)的部分,因此對於 Intelligent Agent 這一部份的學術成果發表顯得比較弱勢。
實際上論文審稿作業也是 Web Intelligence, Intelligent Agent 分開審稿的方式來進行。因此
其審稿委員的聘任和論文的挑選與評定也是分別去進行的。除此之外,在這個研討會發表的論文
如果有獲得前幾名的殊榮還有機會在修稿並延伸之後在 WIAT 的期刊刊登。
三、考察參觀活動(無是項活動者略)
無。
四、建議
這幾年隨著大陸經濟起飛與學者國際化參與意願的提升,使得各項研討會都可以看到大陸學者的
大量參與並且發表論文。除了他們在過去幾年在海外求學之後定居於當地形成一個有利的學術網
絡之外,大陸的內陸學者只要有意願並且經費許可的情況之下都會主動的出國並且參加。除此之
外,世界知名的電腦科學研討會也陸陸續續在組織運作上佔有很重要的一席之地,這是我們台灣
學者必頇要體認的一項事實。
五、攜回資料名稱及內容
研討會論文議事錄一本與全論文集光碟片一張。
六、其他
Challenges for Rule Systems on the Web
Yuh-Jong Hu1, Ching-Long Yeh2, and Wolfgang Laun31 Emerging Network Technology (ENT) Lab.
Department of Computer Science National Chengchi University, Taipei, Taiwan
hu@cs.nccu.edu.tw
2 Department of Computer Science Engineering
Tatung University, Taipei, Taiwan chingyeh@cse.ttu.edu.tw
3 Thales Rail Signalling Solutions
GmbH, Austria wolfgang.laun@gmail.com
Abstract. The RuleML Challenge started in 2007 with the objective of
inspiring the issues of implementation for management, integration, in-teroperation and interchange of rules in an open distributed environment, such as the Web. Rules are usually classified as three types: deductive rules, normative rules, and reactive rules. The reactive rules are further classified as ECA rules and production rules. The study of combina-tion rule and ontology is traced back to an earlier active rule system for relational and object-oriented (OO) databases. Recently, this issue has become one of the most important research problems in the Semantic Web. Once we consider a computer executable policy as a declarative set of rules and ontologies that guides the behavior of entities within a system, we have a flexible way to implement real world policies with-out rewriting the computer code, as we did before. Fortunately, we have de facto rule markup languages, such as RuleML or RIF to achieve the portability and interchange of rules for different rule systems. Otherwise, executing real-life rule-based applications on the Web is almost impos-sible. Several commercial or open source rule engines are available for the rule-based applications. However, we still need a standard rule lan-guage and benchmark for not only to compare the rule systems but also to measure the progress in the field. Finally, a number of real-life rule-based use cases will be investigated to demonstrate the applicability of current rule systems on the Web.
1
Introduction
The RuleML Challenge competitions started in 20071, so the RuleML-2009
Chal-lenge will be the third year for the rule system competition. We offer participants the chance to demonstrate their commercial and open source tools, use cases, and applications for rule related technologies. For the past two RuleML Challenge
1 RuleML-2007 Challenge, http://2007.ruleml.org/index-Dateien/Page787.htm
G. Governatori, J. Hall, and A. Paschke (Eds.): RuleML 2009, LNCS 5858, pp. 4–16, 2009. c
Challenges for Rule Systems on the Web 5
competitions, only a minimum set of requirements was given for evaluating the submitted demo systems. The criteria were that declarative rules should have to play a central role in the application, and that the demo systems should preferably be embedded into a Web-based or distributed environment, etc. The Challenge winners were selected and 1st and 2nd places were awarded with pres-tigious prizes.
The RuleML-2009 Challenge follows similar processes and the evaluation cri-teria are the same as in the previous two events. But we consider inviting more participants to submit their rule related systems in this year. In the RuleML-2009 Challenge, we organize events as two tracks, one is by invitation, to demonstrate a commercial or open source environment for its rule systems, and the other is open to general public for a real system competition. In addition to the demo systems with reports submitted to the RuleML Challenge website2, it is also
possible to submit demo papers describing research and technical details, and the selected papers will be published in additional special Challenge proceed-ings, such as CEURS. A final selection of revised papers from the Challenge proceedings will be resubmitted to a special issue of a journal for publishing. In this RuleML Challenge survey paper, we point out the possible research and implementation challenges for rule systems on the Web that are related to the Challenge competition events in the forthcoming years.
1.1 Challenges for Rule Systems
Rules as human understandable policies are everywhere in our daily life to im-pose human behaviors. For example, before you take a flight, you need to read airline check-in and boarding time rules in the policy statement of your booking itinerary receipt. If you violate any rule you might miss your plane. Related situations in this scenario of using rules are early-bird conference registration, special discount hotel reservation, payment and refund policies, etc. These rules as policies are represented as human understandable natural language. However, we still need to transform these natural language policies into computer pro-gramming rules for computer system understanding and automatic execution. Sometimes, not all of the rules imposed on a human are necessarily and possi-bly represented as software programs to accomplish automatic execution in our computer systems. Usually, these rules restrict only human behavior, without di-rect connection with any software system. For example, we have law for privacy protection and digital rights management but not all of privacy rights and dig-ital rights for human are required to be represented and evaluated in computer systems.
There are several challenges while implementing rule systems on the Web. Rules should be allowed to cope with the data model, such as RDB/OO-DB, or a knowledge base, such as an ontology, to permit query and modification ser-vices on the data models. Policies imposed on human behavior are declared in some policy language by the combination of rules and an ontology (or database), and these policies can be automatically interpreted and executed by a computer.
6 Y.-J. Hu, C.-L. Yeh, and W. Laun
There should be a standard language and framework for rule systems to enable rule interchange services on the Web. A certain number of use cases are easily represented and executed by rule and ontology reasoning engines with rule in-terchange and ontology merging standards to ensure rule interoperability and ontology compatibility.
In the early computer development stage, imperative programming languages such as C and Java were used to represent rules and execute them on a com-puter system. But these rules are inflexible and not easy to maintain when they are distributed on the Web and require interchange and integration between rule systems. Moreover, imperative programming languages are not appropriate to express concepts of human policies as computerized rules. Recently, people use declarative programming to specify the rules and execute them automati-cally, where XML is used as a standard syntax representation for interchange of declarative rules, such as RuleML [1], RIF [2], etc.
Even though an XML-based standard rule language and framework provides rule interchange service, pure XML cannot specify a well-defined semantics for rules. So people in the standard rule community constructed a logic foundation behind rule languages and their framework, to preserve the integrity of syntax and semantics of rules interchange for various rule systems. Similarly, OMG SBVR intends to define the vocabulary and rules for documenting semantics of business vocabulary, facts, and rules, as well as an XMI schema for interchange of business vocabularies and rules among organizations and between software tools3.
In this paper, we first introduce the classification of rules, then, in section 2, we address the issue of rules, and databases and ontologies . In section 3, the current status of a declarative policy as the combination of ontology and rules will be introduced. In addition, Semantic Web Service (SWS) processes also require a declarative policy to express and execute Web Service rules to control information sharing and service execution. In section 4, we examine current different rule management systems and engines. In section 5, we investigate different rule interchange languages. In section 6, we look into the use cases that are possibly represented and executed by the rule systems. Finally, we conclude this study in section 7.
2
Rule and Data Model
2.1 The Classification of RulesRules are classified as three types: deductive rules (or derivation rules), nor-mative rules (or integrity rules), and reactive rules (or active rules). One can use deductive rules and facts to trigger a forward or backward reasoning en-gine to derive implicit facts. Normative rules pose constraints on the data or on the business logic to ensure their consistency in the database or knowledge
Challenges for Rule Systems on the Web 7
base. Without reactive rules, we cannot update a database or knowledge base by using deductive rules only.
Reactive rules are further subdivided into event-condition-action (ECA) rules and production rules. ECA rules are rules of the form ON Event IF Condition
DO Action, where Action should be executed if the Event occurs, provided that
the Condition holds. Production rules are rules of the form IF Condition DO
Action, where Condition queries the working memory containing the data on
which the rules operate. Action should be executed whenever a change to the underlying database makes Condition true [2].
In reactive rules, we verify the satisfaction of conditions and also execute the action whenever message arrival or timer event triggers the rule. Declarative rules extend their executive power by the combination of rule semantics and imperative programming in the action part.
2.2 Rules and Databases
As early as 1980, Ullman pointed out the principles of the integration of database and knowledge base systems [3] [4]. The foundation of database is relation algebra with SQL as a declarative database query language. However, first order logic (FOL) was also proposed as a way to represent “knowledge” and as a language for expressing operations on relations. The roots of relational theory is logic, and so we cannot deny that the foundation of relational DBMS is based on logic [5]. The simplest data model of FOL is “Datalog”, which was coined to suggest a version of Prolog suitable for database systems where it does not allow function symbols in Datalog’s predicate arguments. In the IDEA methodology, deductive rules and reactive rules were built on top of the object-oriented (OO) database as a way to express operations on the OO data model [6].
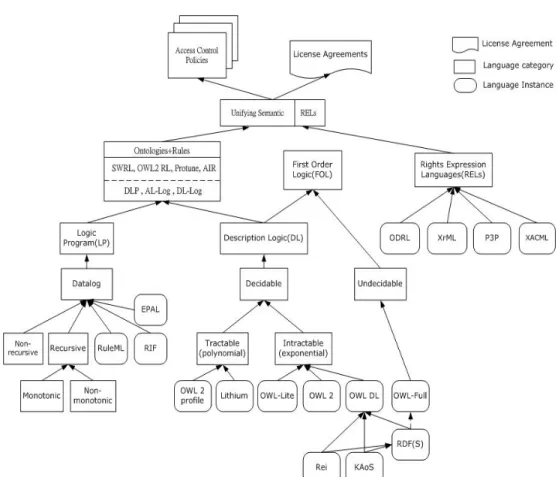
2.3 Rules and Ontologies
Concepts of the Semantic Web have been proposed by Tim Berners-Lee et al. since 2001 [7]. Graph-based RDF(S), including RDF and RDF-schema were the first standardized ontology languages to represent an ontology’s schema and instances. Then, standardized ontology languages based on Description Logic (DL) [8], i.e., OWL-DL (later OWL 2), enhanced RDF(S) that plays the major role of knowledge representation for the Semantic Web. However, the logic pro-gram (LP) rule language was also introduced because of the limited expressive power of a DL-based ontology language in some situations, such as property chaining, and the manipulation of events, states, and actions.
Initially, the “rule” layer was laid on top of the “ontology” layer in the Seman-tic Web layered architecture but it has undergone several revisions reflecting the evolution of layers4. The most recent layered architecture of rule and ontology
layers is one where they sit side by side to reflect their equal status but with some basic assumption differences between ontology and rule, such as the open world
8 Y.-J. Hu, C.-L. Yeh, and W. Laun
assumption (OWA) vs. the closed world assumption (CWA), or the non-unique name assumption (non-UNA) vs. the unique name assumption (UNA) [9].
It will be a challenge to resolve these basic assumption differences when we combine rule and ontology to execute rule systems on the Web.
Rules and RDF(S). Inspired from F-Logic, TRIPLE5 was one of the
earli-est rule languages using Horn rules to access the RDF datasets. Another rule language called Notation3 (N3) uses a CWA forward reasoning engine to access the ontologies generated from RDF(S)6. SPARQL is another W3C standardized
query language for querying RDF datasets. SPARQL queries are represented as Datalog rules so SPARQL’sCONSTRUCT queries are viewed as deductive rules, which create new RDF triples from the RDF datasets.
Rules and OWL. In addition to the Semantic Web Rule Language (SWRL)
[10], Rule Interchange Format (RIF) is an emerging rule interchange language from W3C RIF WG [2]. It intends to provide core and extend languages with a common exchange syntax for all of the classification rule languages, i.e., de-ductive, normative, and reactive rules. The requirements of integrating different types of rules with possible data (and meta data) accessing representation, i.e., RDB, XML, RDF, and OWL, drive the development of a RIF core interchange format, theRIF Core, and its extensions, RIF dialects. Another recent develop-ment is to combine RIF and OWL 2 in RIF, RDF, and OWL that specifies the interactions between RIF, RDF and OWL for their compatibilities7.
2.4 Combination of Rule and Ontology
A one-way knowledge flow exists from an ontology module to a rule module for knowledge acquisition, where an ontology module’s instances are imported as basic facts and filtered with conditions in the rules. This passive knowledge query only uses deductive rules. If a rule engine derives implicit new facts not in an ontology module and furthermore updates new facts back to an ontology module, then it provides another reverse knowledge flow from a rule module to an ontology module. In this two-way knowledge flow process, normative and reactive rules are also required to check the knowledge consistency and trigger the message passing for updating the ontology’s knowledge base.
The idea of combining rules and ontologies is to fulfill a goal of two-way knowl-edge flow. The combination is classified as two types: tightly coupled integration and loosely coupled integration [11]. In the tightly coupled integration model, all of the terms in the rule’s body and head are specified in the ontology schema, but in the loosely coupled integration model we do not have this requirement. So, some rules have their own defined terms in the rules’ body or head. This loosely coupled integration model enhances the expressive power of ontology and rule as compared to the tightly coupled one.
5 http://triple.semanticweb.org/
6 http://www.w3.org/2000/10/swap/doc/cwm 7 http://www.w3.org/2005/rules/wiki/OWLRL
Challenges for Rule Systems on the Web 9
Description Logic Program (DLP) [12] and SWRL are two well-known tightly coupled integration models. In general, both DL and LP are subsets of FOL in knowledge representation but each has its own part that cannot be expressed in the other part. DLP only takes intersection of DL and LP so knowledge repre-sentation in this model is limited. In SWRL, the major knowledge reprerepre-sentation is OWL-DL with additional Datalog rules from LP to enhance the lack of prop-erty chaining in OWL-DL. In SWRL, DL-safe is the condition where variables occurring in each rule’s head are also required to occur in its body to ensure the decidable reasoning of the rule engine. The availability of SWRL rule and ontology integration development in the popular Prot´eg´e environment8 makes
the SWRL model the most attractive one for people to use.
In the loosely coupled integration, DL-log [13], AL-log [14], and DL+Log [15] are three well-known models. In these models, rules are extended to Horn rules. Besides, not all of the terms in rules are required from ontology so rule module in these models provides more powerful knowledge representation and rule reason-ing than the ones in SWRL. However, none of loosely coupled integration models provide standardized XML markup languages and a development environment, as SWRL does in Prot´eg´e. Obviously, this will be a challenge to represent and execute rule systems for loosely coupled integration on the Web. Moreover, the reactive rules [16] have not been seriously considered in all of the ontology and rule integration models. This will be the biggest impediment to implement rule and ontology systems for distributed applications on the Web.
3
Policy as Ontology and/or Rule
Since computers understand the data semantics in the Semantic Web, people are much more satisfied with the search results when a semantic search engine is fully developed. Policy-aware Web extends Semantic Web that provides comput-erized policies, such as privacy protection or digital rights management policies for computers to understand and execute automatically [17]. However, pure rule and/or ontology languages are not explicit enough to represent policies that reg-ulate human behavior in the real world. We need a well-defined policy language that describes the concepts of rights, obligation, conditions, resources, etc. be-tween resource owner and user to represent and execute access control policies of resources on the Web.
Following [18], policies are considered as knowledge bases, allowing deontic classes, properties, and access control rules. This has the advantage that many operations are automated, thereby reducing ad hoc program coding to a mini-mum and enabling automated documentation. Regulations imposed on human behavior and activity are simulated by computerized policies that are specified by using policy languages, such as Rei or KAoS [19]. The semantics of these policy languages is only DL-based, and needs to be further extended by using LP-based semantics of rule languages, such as RuleML, RIF or Protune [20]. Recently, AIR (AMORD In RDF) is a policy language that considers using both
10 Y.-J. Hu, C.-L. Yeh, and W. Laun
RDF ontology language and N3 rule language for the privacy protection policy execution9.
3.1 Policy for Semantic Web Services
The idea of Web Services in the SOA of distributed software systems has be-come a tremendous success. Semantic Web Services (SWS) employ Semantic Web technology in the Web Services area: service functionality, service inputs and outputs, preconditions and effects, etc.; all are expressed and executed in knowledge representation languages, i.e., ontology and rule languages [21]. A policy can be considered in the SWS because of using similar ontology and rule languages’ semantics on the Policy-aware Web. Thus policies are represented and executed as Web Service rules for the compliance of human regulations to control information sharing and service execution.
One of the challenges to implement rule systems on the Policy-aware Web is how to design and implement rules as computerized policy by the integration of rule and ontology. This computerized policy imitates human regulation for controlling information sharing and service execution for a composite web ser-vice on the Web. And the ultimate goal is the satisfaction of legal regulation compliance from the execution of a computerized policy. This idea is similar to the Legal Knowledge Interchange Format (LKIF) proposed in the past EU FP6 project [22].
4
Rule Management Systems and Engines
Before looking into the details of rule management systems, we need to decide about a rule management systems implementation platform. If we choose a rule system that is also embedded in the Semantic Web development environment, then we have several advantages. First, it provides sufficient facilities to imple-ment subsystems for rules and the data model. Second, both the ontology and rule languages used in the Semantic Web are complementary to each other so we can leverage on the declarative knowledge representation. Third, we have a standard query language or a rule language to support the access of underlying knowledge bases for ontology or rule bases. Finally, if applications are embed-ded in Java or some other popular imperative programming language, we have language typing, control flow, and interaction mechanism available for the im-plementation of application system on the Web.
4.1 Rule Systems in the Semantic Web Framework
The SemWebCentral10is one of the well-known websites providing Open Source
development tools for the Semantic Web. The Semantic Web system develop-ment framework can be subdivided into three subsystem modules: an applica-tion module, a controller module and a view module. The applicaapplica-tion module
9 http://dig.csail.mit.edu/TAMI/2007/amord/air-specs.html 10 http://www.semwebcentral.org/
Challenges for Rule Systems on the Web 11
contains reasoning functions, including task and inference, domain schema and knowledge base. The controller module handles interactions with the user and functions in the application model. The view module provides output for the user. The Semantic Web system development framework usually includes two development parts, one is for ontology and the other is for rule. For example, Prot´eg´e has been successfully developed for ontology and rule, such as Jena11 and Jess12. The Jena rule engine was integrated in the Semantic Web system
development framework Prot´eg´e for having rule-based inference with the access to knowledge base in the ontologies of RDF and OWL13. In addition, the
sys-tem for development of ontology and rule combination, such as SWRL is also available in the Prot´eg´e with SWRLTab14.
4.2 Standalone Rule Systems
A number of standalone rule systems have been investigated by the RIF Working Group15. A rule system is defined as a piece of software that implements or supports a rule language in some way (e.g., a rule engine or a rule editor). Among the RIF list, some rule systems are developed for commercial usage but others are for open source purposes. Based on the classification of rule types, some rule systems are developed for a deductive rule engine but others are implemented for a reactive rule engine.
Commercial Rule Systems. IBM ILOG Business Rule Management Systems
(BRMS)16 provides a complete BRMS for analysts, architects and developers, featuring tools of rule authoring and rule management besides its rule engine. In fact, ILOG JRules is one of the best-known production rule systems. JBoss Drools17Enterprise BRMS is a well-known open source rule system which pro-vides perfect integration with the service-oriented architecture (SOA) Web ser-vice solutions. On the other hand, existing rule systems, such as Prova18 and ruleCore19 are also available for ECA rules inference. For more details about
reactive rules on the Web please refer to [16].
Some commercial rule systems are developed from a matured prototype of the Semantic Web middleware, such as OntoBroker20. Oracle Business Rules
integrates with the Business Process Execution Language (BPEL) and tries to enrich decision making for processes in the SOA21. In general, commercial rule
11 http://jena.sourceforge.net/ 12 http://www.jessrules.com/
13 http://protege.stanford.edu/plugins/owl/jena-integration.html 14 http://protege.cim3.net/cgi-bin/wiki.pl?SWRLTab
15 http://www.w3.org/2005/rules/wg/wiki/List of Rule Systems 16 http://ilog.com/products/businessrules/index.cfm 17 http://www.jboss.com 18 http://www.prova.ws 19 http://www.rulecore.com 20 http://www.ontoprise.de 21 http://www.oracle.com/technology/products/ias/business rules/index.html
12 Y.-J. Hu, C.-L. Yeh, and W. Laun
systems use proprietary rule languages for the development of the rule bases so we need a standard rule interchange language, such as RIF to obtain rule interoperability among these rule systems.
Academic Rule Systems. The academic ECA rule system XChange, with its
integration of the Web query language Xcerpt, provides the access of data sources to obtain information on the dynamic Web. Other academic rule systems are de-ductive reasoning rule engines, such as jDREW and its object-oriented extension OO jDREW22. An Object-Oriented Knowledge Base Language FLORA-2 pro-vides frame-based logic reasoning engine with the knowledge base development environment23.
Logic programming systems are also used to develop rule-based applications. For example, Logic Programming Associates Prolog provides a complete rule development environment with a graphical interface for rule editing24. Thea is a
Prolog library for generating and manipulating OWL content on the Semantic Web. The Thea OWL parser uses SWI-Prolog’s Semantic Web library for parsing RDF/XML serialization of OWL documents into RDF triples, and then it builds a representation of the OWL ontology25.
One of the challenges for implementing rule systems on the Web is to be aware of the current rule management systems, including commercial and aca-demic ones, and, furthermore, an understanding of their system features and which rule type reasoning they can support. Moreover, we need to investigate the possible application domains they intent to accomplish through the under-lying rule interchange standard.
4.3 Performance Benchmark for Rule Systems
It is not easy to propose an acceptable measurement benchmark to evaluate the performance of current rule systems because rule systems vary considerably with respect to rule syntax and features. In [23], a set of benchmarks were pro-posed for analyzing and comparing the performance of numerous rule systems. In this OpenRuleBench, they include five rule technologies to compare with: Prolog-based, deductive databases, production rules, triple engines, and general knowledge bases. Jena and OntoBroker we mentioned before were also two of the selective rule systems in their comparison list. We envision that the benchmark performance evaluation output will be just one of the criteria for people to decide for which rule system they are going to adopt in their application development.
5
Rule Interchange Languages
In early expert systems, a specific language, such as Prolog or LISP was used to en-code expert domain knowledge into rules and facts, for execution in a standalone
22 http://www.jdrew.org/oojdrew/ 23 http://flora.sourceforge.net/ 24 http://www.lpa.co.uk/
Challenges for Rule Systems on the Web 13
system. However, when rules and facts are created in different rule systems and distributed on the Web, we need a rule standard exchange language for the inter-change of heterogeneous rule formats. Otherwise, we cannot implement an appli-cation, such as composite (semantic) web services that might require rules created and distributed in the different rule systems [21]. Therefore, a common rule mat facilitates decision making on the network environment with multiple rule for-mats. For example, the therapeutic guideline recommendation rules for diabetes type 2 are constructed with the combination of clinical and therapeutic criteria as the condition part and therapeutic options as the actions. When users or organi-zations switch rules from one rule product to another, they can employ the rule interchange technologies without re-developing their rules.
Proposed rule interchange languages include RuleML [1], REWERSE Rule Markup Language (R2ML) [24], and W3C RIF26, where R2ML attempts at
in-tegrating aspects of RuleML, SWRL, and Object Constraint Language (OCL). The most recent W3C RIF27 was proposed to achieve the objective of rules
in-terchange and interoperability for major rule systems. These rule inin-terchange languages provide XML schemata to guarantee the comparability of rule syntax and semantics from source to target rule systems and vice versa. The other im-portant rule language is Semantics of Business Vocabulary and Business Rules (SBVR), submitted by Business Rule Group (BRG) to OMG on the standard-ization of semantics for business vocabulary and rules28.
One of the challenges to apply rule systems on the Web is to finalize a rule interchange language to provide a rule interchange framework and format of rules for current major rule systems. When agents proceed towards a two way rule interchange, a rule interchange language with the framework ensures the compatibility of rules’ syntax and semantics between rule systems. The related challenge is the requirement to have a software development system and a run-time environment for people to build, design, and implement standardized rule interchange formats to automatically extract and transform rules from different rule systems on the Web.
6
Use Cases with Rules
Rules are used to express computational or business logic in the information systems which do not have explicit control flow, so rules are more suitable for execution in the dynamic situations for business collaborations. Along with the rapid development of the Web, multiparty collaborations for carrying out busi-ness services in this environment are more significant than ever before. For ex-ample, when a credit card transaction is requested from a merchant, a customer needs a payment authorization from the merchant and the card issuer (the bank) to accomplish a successful transaction service. In this case, both merchant and bank have their own policies as rules to conduct their authorization processes.
26 http://www.w3.org/TR/rif-bld/
27 http://www.w3.org/2005/rules/wiki/RIF Working Group 28 http://www.businessrulesgroup.org/sbvr.shtml
14 Y.-J. Hu, C.-L. Yeh, and W. Laun
If both parties are required to combine their policies, we hope they can trans-form the rules into a trans-formal common rule trans-format, such as RIF. For example, rules from the bank are directly imported by the merchant and processed with his local rule engine to derive an authorization decision. In addition, this situ-ation can be extended to other relevant web services for conducting composite web services. Another use case is a seller, posting his price discount and refund policies for execution as rules on his website, to attract potential customers for making a purchase decision from his selling goods. Moreover, a vendor advertises his lead time policies in formal rules to attract customers and also as a part of contract negotiation in the supply chain management.
Use cases such as the ones we have shown above are categorized by the W3C RIF Working Group as a type of policy-based transaction authorization policy for access control with the interchange of human-oriented business rules. Several other interesting use cases focusing on different application domains are also available on this website29. Another interesting use case study was proposed
by the Business Rule Group (BRG) to use SBVR for illustrating business rule concepts of EU-Rent, EU-Fly, and EU-Stay. They are available on the BRG website30. The challenge here is whether we have enough use cases that can be accomplished by current rule systems on the Web to convince people to adopt and use this technology.
7
Conclusion
In this study, we outlined the objectives of RuleML-Challenge competitions started in 2007. Alos, we have elaborated the possible research and implemen-tation challenges for rule systems on the Web that are closely related to the Challenge competition events in the forthcoming years.
The first challenge is to perfectly implement rule systems with the data model, either from a relational or object-oriented database or from a DL-based knowl-edge base. The second challenge is to enable computerized policies, created in a policy language that is compliant with human legal regulations. In addition to the legalized policy implementation with policies created from the policy lan-guage, computerized policy can be shown as a combination of ontology and/or rule languages for the purpose of information sharing and web service execu-tion. The third challenge is full awareness of current available commercial and open source rule management systems and, moreover, finding out the pros and cons of each rule system by a standard evaluation benchmark to verify its scal-ability and performance. The fourth challenge is to achieve rule interoperscal-ability using available rule interchange languages for rules created and distributed on the Web. The fifth challenge is to demonstrate sufficient use cases implemented from rule systems, while interchanging their rules through one of rule interchange language.
29 http://www.w3.org/2005/rules/wg/wiki/Use Cases 30 http://www.businessrulesgroup.org/egsbrg.shtml
Challenges for Rule Systems on the Web 15
Acknowledgements
This research was partially supported by the NSC Taiwan under Grant No. NSC 95-2221-E004-001-MY3 and NSC 98-2918-E-004-003.
References
1. Boley, H.: The ruleML family of web rule languages. In: Alferes, J.J., Bailey, J., May, W., Schwertel, U. (eds.) PPSWR 2006. LNCS, vol. 4187, pp. 1–17. Springer, Heidelberg (2006)
2. Boley, H., Kifer, M., P˘atrˆanjan, P.-L., Polleres, A.: Rule interchange on the web. In: Antoniou, G., Aßmann, U., Baroglio, C., Decker, S., Henze, N., Patranjan, P.-L., Tolksdorf, R. (eds.) Reasoning Web. LNCS, vol. 4636, pp. 269–309. Springer, Heidelberg (2007)
3. Ullman, D.J.: Principles of Database and Knowledge-Base Systems Volume I. Com-puter Science Press, Rockville (1988)
4. Ullman, D.J.: Principles of Database and Knowledge-Base Systems Volume II. Computer Science Press, Rockville (1989)
5. Date, C.J.: Logic and Databases: The Roots of Relational Theory. Trafford Pub-lishing (2007)
6. Ceri, S., Fraternali, P.: Designing Database Applications with Objects and Rules: The IDEA Methodology. Addison-Wesley, Reading (1997)
7. Berners-Lee, T., et al.: The semantic web. Scientific American (2001)
8. Brachman, J.R., Levesque, H.J.: Knowledge Representation and Reasoning. Mor-gan Kaufmann, San Francisco (2004)
9. Patel-Schneider, F.P., Horrocks, I.: A comparison of two modelling paradigms in the semantic web. Journal of Web Semantics, 240–250 (2007)
10. Horrocks, I., et al.: SWRL: A semantic web rule language combining OWL and RuleML (2004)
11. Maluszynski, J.: Hybrid integration of rules and DL-based ontologies. In: Maluszyn-ski, J. (ed.) Combining Rules and Ontologies. A survey. EU FP6 Network of Ex-cellence (NoE), pp. 55–72. REWERSE (2005)
12. Grosof, N.B., et al.: Description logic programs: Combining logic programs with description logic. In: World Wide Web 2003, Budapest, Hungary, pp. 48–65 (2003) 13. Motik, B., Sattler, U., Studer, R.: Query answering for OWL-DL with rules. In: McIlraith, S.A., Plexousakis, D., van Harmelen, F. (eds.) ISWC 2004. LNCS, vol. 3298, pp. 549–563. Springer, Heidelberg (2004)
14. Donini, M.F., et al.: AL-log: Integrating datalog and description logics. Journal of Intelligent Information Systems 10, 227–252 (1998)
15. Rosati, R.: DL+log: Tight integration of description logics and disjunctive dat-alog. In: Proc. of the 10th International Conference on Principles of Knowledge Representation and Reasoning, KR (2006)
16. Berstel, B., Bonnard, P., Bry, F., Eckert, M., P˘atrˆanjan, P.-L.: Reactive rules on the web. In: Antoniou, G., Aßmann, U., Baroglio, C., Decker, S., Henze, N., Patranjan, P.-L., Tolksdorf, R. (eds.) Reasoning Web. LNCS, vol. 4636, pp. 183–239. Springer, Heidelberg (2007)
17. Weitzner, D.J., et al.: Creating a policy-aware web: Discretionary, rule-based ac-cess for the world wide web. In: Ferrari, E., Thuraisingham, B. (eds.) Web and Information Security, pp. 1–31. Idea Group Inc., USA (2006)
16 Y.-J. Hu, C.-L. Yeh, and W. Laun
18. Bonatti, P., Olmedilla, D.: Policy language specification, enforcement, and inte-gration. project deliverable D2, working group I2. Technical report, REWERSE (2005)
19. Tonti, G., Bradshaw, J.M., Jeffers, R., Montanari, R., Suri, N., Uszok, A.: Semantic web languages for policy representation and reasoning: A comparison of KAoS, Rei, and Ponder. In: Fensel, D., Sycara, K., Mylopoulos, J. (eds.) ISWC 2003. LNCS, vol. 2870, pp. 419–437. Springer, Heidelberg (2003)
20. Antonious, G., et al.: Rule-based policy specification. In: Security in Decentralized Data Management, Springer, Heidelberg (2007)
21. Studer, R., Grimm, S., Abecker, A.: Semantic Web Services: Concepts, Technolo-gies and Applications. Springer, Heidelberg (1990)
22. Gordon, F.T.: The legal knowledge interchange format (LKIF). Estrella deliverable d4.1, Fraunhofer FOKUS Germany (2008)
23. Liang, S., Fodor, P., Wan, H., Kifer, M.: Openrulebench: an analysis of the perfor-mance of rule engines. In: Word Wide Web 2009, pp. 601–610 (2009)
24. Wagner, G., Dam´asio, C.V., Antoniou, G.: Towards a general web rule language. International Journal Web Engineering and Technology 2 (2005)
SemPIF: A Semantic Meta-Policy Interchange
Format for Multiple Web Policies
Yuh-Jong Hu
Dept. of Computer Science
NCCU, Taipei, Taiwan
hu AT cs.nccu.edu.tw
Harold Boley
IIT – e-Business,
NRC-CNRC, Canada,
Harold.Boley AT nrc.gc.ca
Abstract—We propose a semantics-enabled layered policy
architecture for the exchange and management of multiple policies created by different policy languages on the Web. This architecture consists of four layers: Unifying Logic (UNL), Policy Interchange Format (PIF), Privacy Protection/DRM (PPD), and Domain Specific Applications (DSA). A meta-Policy Interchange Format (meta-PIF) layer is also introduced, side by side with the corresponding PIF layer, allowing agents in the facilitator to provide uniform services of interchange, reconciliation, and combination of policies. This SemPIF architecture extends W3C’s Semantic Web architecture to permit the reuse of earlier work. A scenario of agents in the facilitator employing SemPIF for Digital Rights Management (DRM) and privacy protection policies on digital library subscription services will be demonstrated.
Keywords-semantic web; ontology and rule; computer policy;
privacy protection; digital rights management
I. INTRODUCTION
In the Semantic Web, information is given well-defined meaning to better enable computers and people to work in cooperation. The well-known Semantic Web layered archi-tecture1 has undergone revisions reflecting the evolution of layers such as the Description Logic (DL)-based ontology language OWL [1], the Horn Logic (HL)-based rule language RIF [2], and their relationship. On the other hand, policy languages, such as Rei [3], KAoS [4], Protune [5], have also been proposed – on the basis of DL and LP – to allow agents understand policies and to enforce these policies as intended by their semantics. However, the semantic bases of policy languages vary considerably, ranging from DL to HL to Logic Programming (LP), e.g. leading to different stances w.r.t. the unique name assumption (UNA) and the closed world assumption (CWA) [6]. This makes policies created in these policy languages hard to interchange and combine with each other.
Policies are formulated and treated as knowledge bases, i.e. ontologies and rules (O + R). Many operations can be auto-mated, thereby reducing ad-hoc program coding to a minimum and enabling automated documentation [5]. Policy frameworks also need to support interoperability. Moreover, the context of a policy is itself described in a machine-understandable way.
1http://www.w3.org/2007/03/layerCake.svg
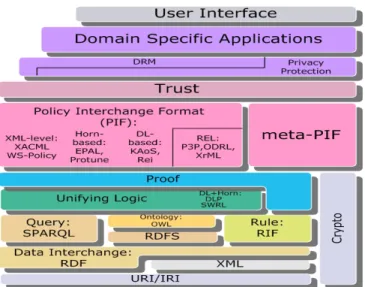
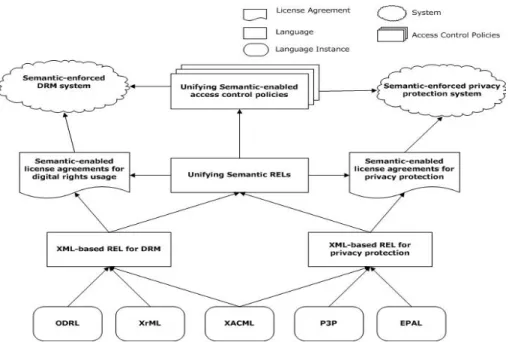
Therefore, we propose a semantics-enabled policy architecture consisting of four layers: Unifying Logic (UNL), Policy/meta-Policy Interchange Format (PIF/meta-PIF), Privacy Protec-tion/DRM (PPD), and Domain Specific Applications (DSA). Here UNL directly corresponds to the layer “Unifying Logic” of the most recent version of the Semantic Web architecture. We also introduce a meta-PIF layer, side by side with the corresponding PIF layer, allowing software agents in the fa-cilitator, to provide the management functions of interchange, reconciliation, and combination of policies. The Policy Web architecture can be viewed as an extension of the Semantic Web architecture shown as Fig. 1.
Fig. 1. SemPIF: A semantics-enabled layered policy model centered on semantic policy interchange format (PIF) and meta-PIF.
PIF is built on DL-based ontologies and LP-based rules, i.e. O + R, that allow agents in the facilitator to support interchange services of policies created from different policy languages. In addition, we may use PIF to specify meta-policies for managing meta-policies created from different policy languages. A meta-policy is a policy about policies that provides a set of rules for realizing services needed for the management of policies. Moreover, a meta-policy consists of a set of rules for setting up the priority of polices to coordinate,
2010 IEEE/WIC/ACM International Conference on Web Intelligence and Intelligent Agent Technology
978-0-7695-4191-4/10 $26.00 © 2010 IEEE DOI 10.1109/WI-IAT.2010.238
enforce, and even negotiate policies [7].
In a particular policy language framework, policy man-agement services could be implemented as meta-policies as shown in the Rei framework [3] or it could be implemented as policy administration tools as shown in KAoS [4]. In the Protune framework, the role of meta-policies is in governing the behavior to reduce ad-hoc programming efforts and to im-prove policy readability and maintainability. However, policy management services in these frameworks were only allowed to operate within their own environments. For added flexibility, SemPIF allows agents in the facilitator to use meta-policies providing the management services of policy interchange, combination, and negotiation across multiple heterogeneous domains.
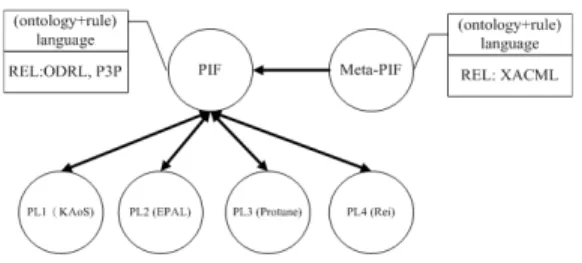
In contrast to other policy languages, such as KAoS, Rei, and Protune, PIF follows W3C O + R standards [8] and strives to provide a mechanism for agents to preserve different policy syntaxes and semantics throughout its policy integration and interchange. In addition, agents can use meta-PIF, provid-ing further management and reconciliation services of PIF-enabled multiple policies across various domains (see Fig. 2).
Fig. 2. Policy integration and interchange for various policy languages (PL) through PIF and meta-PIF in the SemPIF
An XML-based Rights Expression Language (REL) lacks semantic expressive power so it is a restricted form of policy language in the PIF layer. Currently, there are three RELs available, i.e. P3P for privacy protection as well as ODRL and XrML for DRM. Unfortunately, policies created from these XML-level RELs lack formal semantics, which prevents agents from automatically and accurately interpreting and processing these policies.
A formal semantic model for policies could be expressed and enforced as a combination ofO + R. Obviously, if we do not know what are the available expressive features of each
O + R combination, then we cannot decide which
combina-tion will be the best one to represent the formal semantics of RELs. We have shown the semantics of DRM policies in PPD as a homogeneous combination ofO + R, i.e. SWRL, where bothO + R are embedded in a logical language L, to structure the semantics of ODRL [9]. We also have shown the semantics of privacy protection policies in PPD as a hybrid combination of O + R, i.e. DL+log, where a strict separation between the rule predicates and ontology predicates, to formalize the semantics of P3P in the PIF layer [10].
Another issue addressed by our investigation of the DRM vs. privacy usage control problem is the following. While
DRM systems are collecting personal information for usage control, it is quite possible that they might also invade privacy rights. To reconcile this conflict, the (O + R) language in meta-PIF permits agents to enforce the fine-grained mapping and merging of ontologies with interchangeable rules from policies on privacy protection and DRM. This paves the way for accomplishing the objective of unifying multiple Web policies through SemPIF.
Finally, we will show a scenario for digital library sub-scription services in a client-server model and demonstrate how to use it by agents in the facilitator to eliminate possible conflicts between a server’s DRM policies and a client’s privacy protection policies.
II. SEMANTICWEBLAYEREDARCHITECTURE
We have both Web markup languages and Semantic Web languages in the Semantic Web Layered Architecture (SWLA) (see Fig. 1). XML / XML Schema and URI/IRI references constitute the foundation, which provides interoperable syntax for RELs at the PIF layer. The semantics of RELs need to be formalized with one of theO + R combinations from the UNL, to provide meanings for policies. For Semantic Web languages, we have ontology languages, rule languages, and a combination of ontology and rule languages, i.e. O + R languages. The ontology languages include the graph-based RDF(S) and the DL-based OWL. The Horn-based rule lan-guages and their extensions to LP-based rule lanlan-guages include RIF and RuleML. SWRL is a Semantic Web language using a combination of OWL-DL ontologies and Datalog RuleML rules so it is an O + R language [11]. OWL 2 RL and its combination with RIF is another emerging O + R language that can be compared with DLP2.
A. Unifying Logic
PIF and Sem-PIF are built on the unifying logic of DL-based ontologies and LP-DL-based rules [6]. In the UNL layer, DL is a subset of the First Order Logic (FOL). DL provides a basic logic foundation for an ontology language, such as OWL 2. Similarly, Horn logic and LP provides a basic logic foundation for rule languages, such as RIF or RuleML. One of LP’s characteristics, procedural attachment, is not included in DL (or FOL) but this feature is very important for the execution of policy’s actions.
DLP was introduced as the intersection of DL and LP [12], which has quite limited expressive power when compared to other O + R combinations, such as AL-log, DL-log, etc. [13] [14]. The homogeneous O + R combination of DL and Datalog provides the logic foundation of SWRL. These combinations of O + R have much more expressive power than DLP regarding O + R, which is needed for Sem-PIF. However, given the ongoing O + R research3, we have not fixed yet any one combination for SemPIF’s representation and enforcement requirements.
2The combination of OWL 2 and RIF has been shown in
http://www.w3.org/2005/rules/wiki/OWLRL.
3See, e.g., ONTORULE http://ontorule-project.eu/.
B. Policy Interchange Format
The PIF layer consists of regular DL-based policy lan-guages, such as Rei, KAoS; or Horn-based policy lanlan-guages, such as EPAL [15], and XML-syntax policy languages, such as XACML [16]. P3P and EPAL were proposed as policy languages for privacy protection in the corresponding client-server and client-server-client-server models [17] [18]. As REL sublayer, ODRL and XrML were proposed for designing DRM poli-cies [19] [20]. DL-based or Horn-based logic can be used as foundations to underpin these RELs with explicitly defined semantics for policy languages.
A policy’s explicit representation in terms of ontologies or rules depends on what the underlying logic foundation of your policy language is. If policies are created from a DL-based policy language, such as Rei or KAoS, then ordinary policies are shown as T Box ontology schemas and ABox instances. Otherwise, with policies created from LP-based policy languages, such as EPAL, ordinary policies are sets of rules and facts using unary or binary predicates.
These policy languages in the PIF layer do not fully utilize the syntax and semantics expressive power of OWL or RDF(S) shown in the SWLA. Therefore, we do not expect these policy languages to be able to leverage the power of existing ontology or rule languages. Another restriction is policies created from different policy languages might not be able to interchange or negotiate with each other. This calls for the use of SemPIF to achieve policy interchange, combination, reconciliation, and negotiation.
C. Privacy Protection and DRM
Privacy protection and DRM are introduced as independent but intertwined layers on top of PIF / meta-PIF and the Trust layer (see Fig. 1). This relationship reflects that access rights enforcements for these two domains are closely related with each other. In [21], the authors proposed that a DRM system should consider user-desirable privacy rights indicated in the Fair Information Principles (FIP), such as data collec-tion, retencollec-tion, use, disclosure, and destruccollec-tion, etc., when it enforces privacy protection policies. Otherwise, user privacy rights might be violated. A scenario will be demonstrated to show how agents in the facilitator employ SemPIF to integrate DRM and privacy protection policies (see section III).
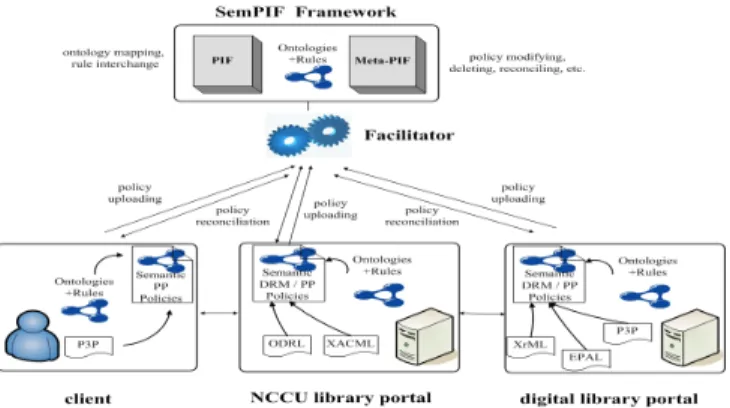
III. ASCENARIO OF DIGITAL LIBRARY SUBSCRIPTION
Protection policies are created from various policy lan-guages, such as ODRL, P3P, XACML, and EPAL, for enforc-ing DRM and privacy protection. This access-control scenario is extended from policy-aware access control for the open Web environment [22]. Agents in the facilitator use PIF-based policies to provide services of integrating semantics-enabled protection policies between a client and a server. Moreover, Agents use meta-PIF-based policies to manage policies, which permits clients and a server to compromise on their respective rights and obligations(see Fig. 3).
Fig. 3. Agents in the facilitator provide policy interchange services with PIF-based policies and policy management services with meta-PIF-PIF-based policies
A. Web server’s policies
The NCCU university library has subscribed to IEEE,
ACM, and Springer digital library services, which provide
a set ofeJournal article access rights for authorized students and staff. There are two types of policy for an IEEE Web server: one for DRM and the other for the declaration of privacy statements.
1) Policies in the IEEE server: The IEEE publisher
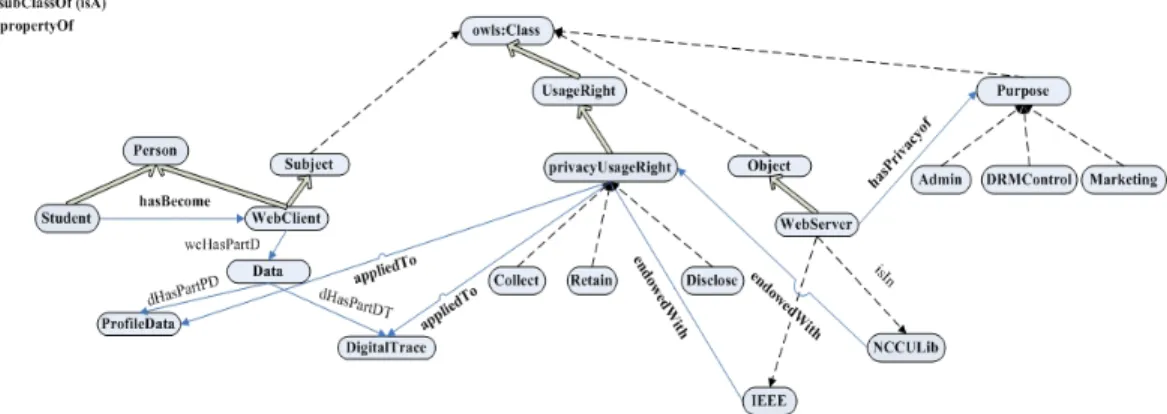
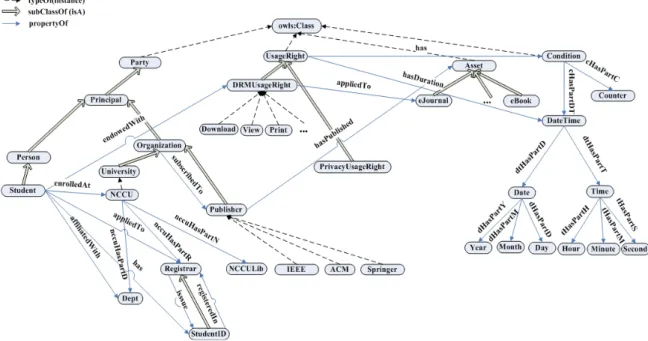
has two PIF-based policies: policy(drm1 − IEEE) for DRM and policy(pp1 − IEEE) for privacy declaration. policy(drm1 − IEEE) indicates that the policy’s name is drm1-IEEE, which corresponds to a URI as a policy indicator for agents to apply a meta-PIF policy to manage it. The pred-icates of each RIF rule are specified in PIF-based ontologies (see Fig. 4 and Fig. 5).
• policy(drm1 − IEEE):
If a student owns a valid student ID issued by a department of a university, e.g. a registrar, and its library is one of the subscribers on the IEEE publisher’s list, then the student is endowed with DRM usage rights
{download, view, print} for eJournals from a Web
server of the IEEE publisher’s delegation.
?st#Student∧?id#StudentID∧?st[own →?id]
∧?uni[nccuHasPartR →?rg]∧?st[enrolledAt →?uni] ∧?rg[issue →?id]∧?uni[nccuhasPartN →?lib] ∧?lib[subscribedTo → IEEE]
∧IEEE[hasPublished →?ejr]
∧IEEE[endowedWith →?rgt]∧?rgt[appliedTo →?ejr] ∧IEEE[delegate →?st] =⇒?st[endowedWith →?d] ∧?st[endowedWith →?v] ∧?st[endowedWith →?p] ∧?d#Download∧?d[appliedTo →?ejr] ∧?v#View∧?v[appliedTo →?ejr] ∧?p#Print∧?p[appliedTo →?ejr]. • policy(pp1 − IEEE):
If a person is endowed with DRM usage rights from a Web server of the IEEE’s publisher and this publisher has the purpose of enforcing DRM control for collecting,
Fig. 4. A PIF-based ontology for privacy protection policies
retaining, and disclosing a person’s data, then the IEEE publisher is endowed with privacy usage rights
{collect, retain, disclose} on this data from a
person’s delegation, including profiles and digital traces in the Web server under condition of a retention period of two months after the data are first collected.
?per[endowedWith →?drmr]∧?drmr[appliedTo →?ejr]
∧IEEE[hasPublished →?ejr] ∧IEEE[hasPrivacyOf → DRMControl]
∧?per[dHasPartPD →?prf]∧?per[dHasPartDT →?dif] ∧?per[endowedWith →?ppr]∧?per[delegate → IEEE] ∧Retain[hasDuration → =2Month]
∧?sdtime[dHasPartD →?dtime] ∧?edtime[dHasPartD →?dtime]
∧subtract-dateTimes(?edtime, ?sdtime) ≤ Retain
=⇒ IEEE[endowedWith →?ppr]
∧?ppr[appliedTo →?prf] ∧?ppr[appliedTo →?dit].
In policy(drm1 − IEEE), we use ODRL basic primi-tive vocabulariesprincipal, asset, right, or obligation to define a license agreement between principals, i.e., library, registrar, university, and publisher. Similarly, in policy(pp1 − IEEE), we use P3P basic primitive vocabular-ies, such as user, owner, purpose, rights, obligation to define a privacy protection agreement between data user and data owner. All of the basic vocabularies are defined in the DRM or privacy protection ontology’s schema (see Fig. 4 and Fig. 5), so the semantics of ODRL and P3P RELs are formalized. Furthermore, policies specified in other policy languages for DRM and privacy protection can be mapped to the PIF-based policies for the purposes of policy interchange and integration.
2) Policies in a Web client: A student, John, as a Web client has privacy protection policies, i.e., policy(pp3 − John), policy(pp4 − John) to address how and what of his personal data can (or cannot) be collected, retained, or disclosed from a Web server. Here we show the policies in natural language only.
• policy(pp3 − John):
If aneJournal distributor from{ACM, IEEE, Springer} has the purpose of enforcing DRM control by collect-ing, retaincollect-ing, and disclosing data on John as the Web client, then it is endowed with privacy usage rights
{collect, retain} on the profiles of John as the Web
client under the condition of a retention period of less than thirty days after the profiles are first collected.
• policy(pp4 − John):
If the distributor IEEEJournal has the purpose of en-forcing DRM control by collecting, retaining, and disclos-ing data on John as the Web client, then IEEE is endowed with the privacy usage rights {collect, retain} from the digital traces of John as the Web client, where the data retention period is less than fourteen days after the trace data are first collected.
IV. SEMPIFFORMULTIPLEWEBPOLICIES
Agents in the facilitator provide policy interchange to avoid possibly inconsistent or ambiguous syntax and semantics be-tween source and target policies.
A. Meta-PIF
We envision several important issues in the design of agents while using SemPIF as a mediation architecture to enforce pol-icy management services, such as polpol-icy sequencing, adding, deleting, merging, etc.
• In the SemPIF architecture, agents use PIF to provide basic interchange services of various policy languages.
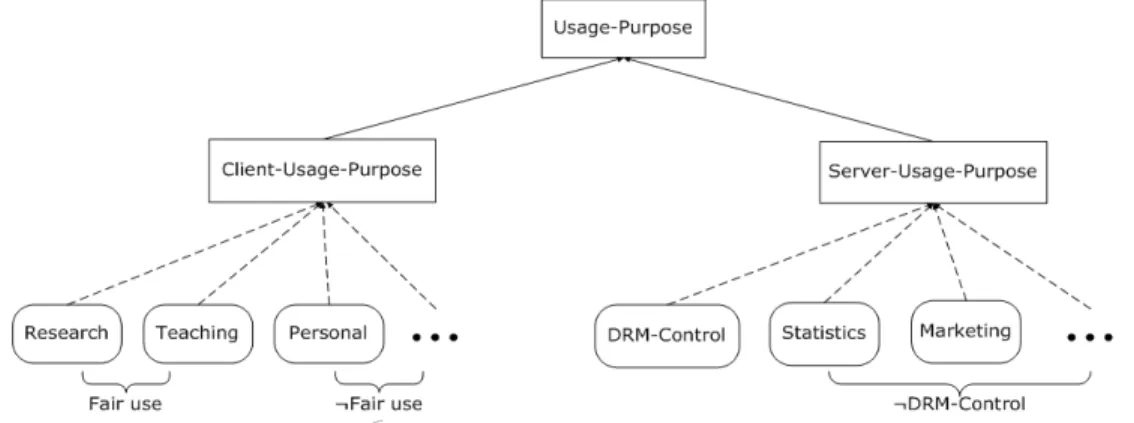
• The basic vocabularies of PIF for interchange of policies are specified in the various REL policy languages, such as P3P or ODRL. They are principal, subject(owner), object(user), resource(asset), right, obligation, purpose, and condition. In addition, access right vocabularies for privacy protection and DRM are different. We have {collect, retain, disclose}, etc. for privacy protection and we have {download, view, print}, etc. for DRM.
• Most of the basic vocabularies for meta-PIF are the same as PIF’s except some of them are directly related to
Fig. 5. A PIF-based ontology for DRM policies
PIF-based policies. The policy itself is introduced as a resource with respective users, rights, and conditions, etc. for agents to enforce its policy management services.
• Meta-PIF is a meta-policy language for PIF and only provides management services for PIF-based policies. If meta-PIF attempts to provide an interchange format for different meta-policies in PIF, then we also have to provide policy management interoperability services for different policy languages. This requires further study.
B. Agents in the facilitator enable meta-PIF policies
We use P3P basic vocabularies to specify data owner (or subject), user (or object), type, right, obligation as ontology classes with associated properties to formalize the semantics of privacy protection [10]. Furthermore, we also use Datalog-based rules to decide whether a Web server is allowed tocollect, retain, or disclose a particular client’s profiles and digital traces. Policies are defined as a combination of
O + R. In order to unify policies from a client and a server,
we allow agents in the facilitator to collect client and server’s ontologies, and to enable SemPIF policy transformation and management services shown as follows:
1) Ontologies mapping and aligning
We map and align vocabularies from domain dependent ontologies of DRM and privacy protection policies. In Section III scenario, the vocabularies of class ”Student, Publisher” in policy(drm1 − IEEE)
and policy(pp1 − IEEE) correspond to
”WebClient, WebServer” vocabularies of class in policy(pp3 − John) to policy(pp4 − John). Furthermore, we align the ontology schemas constructed with the vocabularies of class and property.
2) Semantics mediation and unification
We mediate and unify the semantic differences of vocabularies and schemas in the ontologies belong-ing to different protection policies. For example, a condition ofRetain[hasDuration → =2Month] in the policy(pp1 − IEEE) corresponds to a condition of ”retention period less than fourteen days” in the policy(pp4 − John).
3) Conflicts resolving
Agents initiate the reconciliation processes between conflicting policies using the meta-PIF framework. In this example, IEEE declares its intention to collect, retain, and disclose a Web user’s data in the policy(pp1 − IEEE) for two months. The data include a Web user’s profiles and digital traces. Web user John does not allow an IEEE Web server to disclose his personal profile to the other partners. Thus, policies between policy(pp1 − IEEE) and policy(pp3 − John), policy(pp4 − John) are inconsistent. Agents enable a policy priority-setting with meta-PIF-based policies to avoid the policy conflicts. In this example, an agent gives a higher priority to a client’spolicy(pp3 − John) and policy(pp5 − John) than to a server’s policy(pp1 − IEEE). The defeasible logic of a meta-PIF’s expression, Overrides(policy(?pid1), policy(?pid2)),
for resolving conflicts of policies is a possible solution, where policy(?pid1) is bound to policy(pp3 − John) and policy(pp4 − John); policy(?pid2) is bound to policy(pp1 − IEEE). This negotiation protocol requires further study.