New Visual Secret Sharing Schemes With Non-Expansible Shadow Size Using Non-binary Sub Pixel
全文
(2) visual system so that we can easily recover the. represented by the Boolean “or” of rows i1 , i2 , … ir in. shared secret using the eyes of human being. For a. S. The gray level of this recovered image is. (k, n) VSS scheme, k or more participants can get. proportional to the Hamming weight of the “or”ed. the shared secret by stacking their shadows. m-vector. methods for VSS schemes, we use several sub. gray level is interpreted by the user’s visual system. pixels in the shadow to represent a pixel in the. as black, and if H( v ) ≦ d – á m, the result is. original secret image, i.e., the size of shadow is. interpreted as white.. r v . For the fixed threshold 1 ≦ d ≦ m r (transparencies). In the previous construction and relative difference á > 0, if H( v )≧ d, this r. larger than the original image. Here we define the Pixel Expansion = (the size of the shadow) / (the. DEFINITION 1.. A (k, n) VSS Scheme can be. size of the secret image). For example the Pixel. shown as two collections of n × m Boolean function. Expansion of Shamir’s (2, 2), (2, n) and optimal (k,. matrices B0 and B1 . When sharing a white (resp.. k) VSS schemes are 2, n, and 2k-1 .. black) pixel, the dealer randomly chooses one row. In this paper, we will propose the new VSS. of the Boolean matrix B0 (resp. B1 ) to a relative. schemes with non-expansible shadow size. That is. shadow. The chosen matrix defines the gray level of. the Pixel Expansion of our scheme is 1. Our. the m sub pixels in every one of the n shadows. A. method is to expand the binary level (only “black”. VSS Scheme is considered valid if the following. and “white”) of the sub pixel to non-binary level. conditions are met [1] :. (gray level) instead of expanding their shadow size.. 1. For any S in B0 (resp. B1 ), the “or”ed. r. r v of. This paper is organized as the following. In section. any k of the n rows satisfies H ( v ) ≦ d –. 2, we will describe the conventional VSS scheme.. ám (resp. H ( v ) ≧ d).. r. In section 3, we propose our VSS schemes and also. 2. For any subset {i 1 , i 2 , …, i q } of {1, 2, …, n} with. define the new contrast and security conditions.. q < k, the two collections of q×m matrices. Section 4 gives the experimental results and our. obtained by restricting each n×m matrices in. definition of the contrast. Section 5 concludes the. Bi , i∈ {0, 1}, to rows i1 , i2 , …, iq are not. paper.. visual in the sense that they contain the same matrices with the same frequencies.. 2 The Basic VSS Scheme As described in [1], in a (k, n) VSS scheme,. The first condition is called contrast and the. the original image consists of a collection of black. second condition is called security. Due to the. and white pixels. Each original pixel is divided into. security condition, we cannot get any information. m black and white sub pixels in n shadows. VSS. about the shared secret if we do not have more than. Scheme can be described by n × m Boolean matrix. k shadows.. S = [sij ], where sij = 1 if and only if the jth sub pixel. For the basic (2, 2) VSS scheme, we will. in the ith shadow is black, otherwise sij = 0. When. stack two shadows to recover the shared secret, and. shadows i1 , i2 , … ir , are stacked together in a way. “black” is 2B and “white” is 1B1W in the. which properly aligns the sub pixels, we see a. recovered image. We cannot get any information. recovered image whose black sub pixels are. from any one shadow, because every pixel in the.
(3) shadow is represented as 1B1W.. and n γ n × 1 matrices, respectively. When sharing a white (resp. black) pixel, the dealer first randomly. 3 The Proposed VSS Scheme with Non-Expansible Shadow Size. chooses one column matrix in C0 (resp. C1 ), and. In this section, we use new definition of sub. matrix to a relative shadow. The chosen matrix. pixel to construct the VSS schemes. Instead of. defines the gray level of one sub pixel in every one. expanding the original pixel into m sub pixels , we. of the n shadows. A NEVSS Scheme is considered. expand the gray level of the sub pixel as a. valid if the following conditions are met :. substitute. The new gray sub pixel is shown in. 1.. then randomly selects one row of this column. For these n λ (resp. n γ ) matrices in C0 (resp.. Fig.1(a), where a sub pixel is a fixed gray level,. C1 ), the “ADD”ed value of any k -tuple column. and the operation between sub pixels is the. vector. “ADDITION”. It means that a gray sub pixel. 2.. r r r v satisfies G( v )∈λ (resp. G( v )∈γ).. The two sets λ and γ satisfy that |Pλ-Pγ| is. “ADD” a gray sub pixel will cause a more gray sub. great enough such that we can distinguish the. pixel. The stacking operation for the conventional. “black” and “white”, where Pλ and Pγ are the. VSS scheme is “OR” shown in Fig.1(b). The major. probabilities of the dominant color in the set λ. difference between two schemes is that our scheme. and γ, respectively.. uses non-binary operation and the conventional. 3.. For any subset {i 1 , i2 , …, iq } of {1, 2, …, n}. r. with q < k, the G( v ) in. scheme uses Boolean operation.. C0 and C1 are. same with the same frequencies. As a replacement for using n × m Boolean matrix,. we. therefore. define. n ×1 matrix. The first two conditions are called contrast. P = [ p i ] where p i = 1 iff the sub pixel in ith and the third condition is called security. Note that shadow is gray level, otherwise p i = 0 . When the two sets λ and γ are chosen to let us see the shadows i1 , i 2 ,..., ir are stacked, we can “black” and “ white”, and the dominant color means represent. it. by. “ADD”. operation. of. rows. the color with the biggest contrast relative other. i1 , i 2 ,..., ir in P. The gray level of this combined r sub pixel G( v ) is denoted by the “ADD”ed value r r of this r-tuple column vector v , i.e., G( v )= i1 + i 2 + ... + i r .. colors in the set λ and γ. From the definition, C0 and C1 are n × 1 matrices, so the Pixel Expansion is 1; however B0 and B1 are n × m matrices, and thus the Pixel Expansion is m.. Next we use the DEFINITION 2 to show the formal required conditions of the proposed VSS scheme with non-expansible shadow size. As convenience, we herein use the abbreviation NEVSS (Non-Expansible VSS) scheme to denote our scheme.. 3.1 A (2, 2) NEVSS Scheme For the description of the construction, we first define the notation. µi, j to represent the n×1. column matrices with the Hamming weight i of every column vector, and j denotes the matrices. DEFINITION 2. A (k, n) NEVSS scheme can be shown as two collections C 0 and C 1 consisting of n λ. belong Cj where j∈{0, 1}. For example n =3,. µ2 , 0.
(4) are. three. 3× 1. column. matrices. shown. µ2 , 0. 0 1 1 = {1 0 1} and µ2 , 0 belongs C0 . 1 1 0. as. C0 = {µ0 ,0 , µ2 , 0 } , and C1 = {µ1,1 } . Fig. 2(a)~(d) are the shared secret, shadow 1, shadow 2, and the recovered image shadow 1 + shadow 2. We can observe that the shadow size is not expansible from the following figures, and the gray level “1”. Construction 1 : Let C0 and C1 be the two white. is used to represent “black” and gray level “0” and. and black collections of 2×1 matrices for a (2, 2). “2” are used to represent “white”.. NEVSS scheme. Then,. and. C0 = {µ0 ,0 , µ2 , 0 } ,. 3.2 A (2, n) NEVSS Scheme We now describe our 2-out-of-n NEVSS. C1 = {µ1,1 } .. scheme based on the new gray sub pixel.. Theorem 1: The scheme from Construction 1 is a (2, Construction 2 : Let C0 and C1 be the two white 2) NEVSS scheme with non-expansible shadow. and black collections of n×1 column matrices for a. size. (2, n) NEVSS scheme. Then, Proof:. Since. C0 = {µ0 ,0 , µ2 , 0 } C1 = {µ1,1 }. the. matrices. 0 1 = { } 0 1 0 1 = { } , 1 0. and. so. C1 = {µn / 2 , 1 }. and. C0 = {µ0 ,0 , µn , 0 } ,. for. even. n. or. C1 = {µ n / 2 , 1 , µ n / 2 +1, 1 } for odd n.. 0 1 = {G( ), G( )} = {0, 2} and Theorem 2: The scheme from Construction 2 is a (2, 0 1 0 1 n) NEVSS scheme with non-expansible shadow γ = {G ( ), G ( )} = {1, 1} when stacking size. 1 0 λ. two shadows. The dominant color is “0” (white),. Proof:. because “0” is the biggest contrast among the. C0 = {µ0 ,0 , µn , 0 } and. colors “0”, “1”, and “2” in λ and γ. Now, Pλ=1/2 Pγ=0, the difference Pλ-Pγ=1/2, thus holds the second condition. For a proof of the third condition “security”, note that we randomly chooses one column matrix in C0. λ. For. even. n,. since. shadow every pixel will be “0”(white) or “1”(gray) half and half, and one cannot see any thing from the shadow.. £. = {G( µ0 , 0 ), G( µn , 0 )} = {0, 2} and γ = n. n. n. 08 18 67 28 67 67 { 0,K ,0 , 1, K,1 , 2, K,2 } when stacking any. two shadows, where n 0 =. C02 × Cnn −/ 22 , n 1 =. C12 × Cnn /−22−1 , n 2 = C22 × Cnn −/ 22− 2 . The probability of “0” and “2” in λ are all 0.5; however the probability. Example 1 : For a (2, 2) NEVSS scheme and. collections. C1 = {µn / 2 , 1 } , so. and C1 , and then randomly selects one row of this column matrix to a relative shadow. So for each. the. of. “0”. and. “2”. in. γ.
(5) =. n0 n0 + n1 + n 2. C 02 × C nn −/ 22. n−2. “1”. n2 n0 + n1 + n 2. C02 × Cnn −/ 22 + C12 × C nn /−22−1 + C22 × C nn −/ 22−2. 1 1 + 2n. =. +1. =. =. =. 0 0 1 1 1 0 C1 = {µ1,1 , µ2 ,1 } = {0 1 0 1 0 1 } . 1 0 0 0 1 1 . n−2 0 1 , and the probability of 4n − 4 λ= {G ( 0 ), G ( 1 )} 0 1. ={0,. 2},. and. γ =. γ. in. 2n n1 2n 0 0 1 1 1 0 n−2 = = = . n0 + n1 + n 2 {G( 0 ), G( 1 ), G( 0 ), G( 1 ), G ( 0 ), G( 1 )} 4n − 4 1 + 2n +1 n−2 1 0 0 0 1 1 Since “0” is the dominant color among “0”, “1”, and “2”, and Pλ=1/2, Pγ=. ={0, 1, 1, 2, 1, 1} when shadow 1 and shadow 2 are n−2 ≒1/4 for large n. stacked. The dominant color is “0”, Pλ=1/2, Pγ=1/6, 4n − 4. The difference Pλ-Pγ=1/4, thus holds the second. thus the difference Pλ-Pγ=1/3. Fig.3(a)~(f) are. condition, and our (2, n) NEVSS scheme can show. shadow 1, shadow2, shadow 3, and the recovered. the shared secret correctly due to the difference. image shadow 1 + shadow 2, shadow 2 + shadow 3,. probability.. shadow 1 + shadow 3. We can observe that the. For a proof of the third condition “security”, the. shadow size is not expansible from the following. r probability of G( v )=0 in C0 is 1/2, and the C nn −/ 12 r probabilityr of G( v )=0 in C1 is = 1 / 2 . As C nn / 2 r the same reason, the probability of G( v )=1 in C0 is r 1/2, and the number of G( v )=1 in C1 is C nn −/ 12 −1 = 1 / 2 . So, it satisfies that “0”(white) and Cnn / 2. figures.. Example 3 : For a (2, 4) NEVSS scheme, the two white and black collections C0 and C1 of 4×1 column matrices are shown below :. 0 1 0 1 C0 = {µ0 ,0 , µ4 , 0 } = { } , 0 1 0 1 1 0 1 0 1 0 1 0 0 1 0 1 C1 = {µ2 ,1 } = { } 0 1 1 0 0 1 0 1 0 1 1 0. “1”(gray) half and half, and one cannot see any thing from the shadow.. For odd n, using the same approach, we can get the similar result.. £. Example 2 : For a (2, 3) NEVSS scheme and. 0 1 C0 = {µ0 ,0 , µ3, 0 } = {0 1} 0 1. .. ,. 3.3 A (k, k) NEVSS Scheme Construction 3 : Let C0 and C1 be the two white and black collections of k×1 Boolean matrices for a.
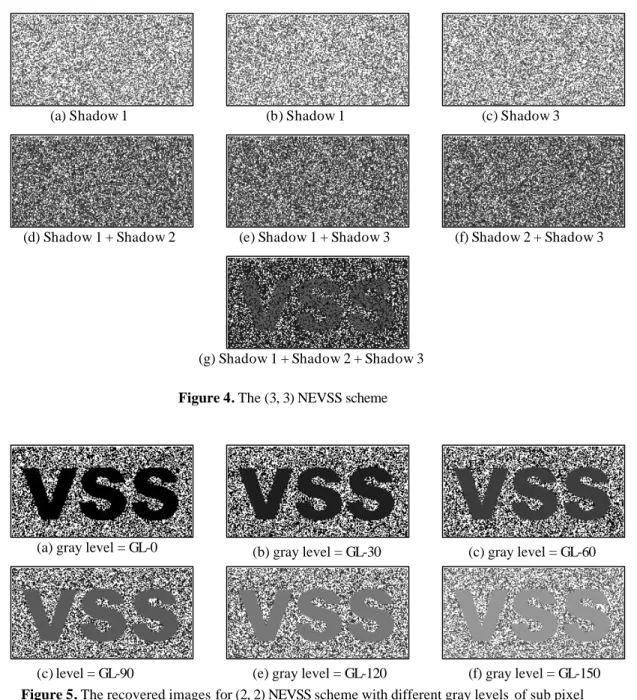
(6) (k, k). NEVSS. scheme.. Then,. for. even. k. so the third condition is satisfied.. C0 = {µ0 ,0 , µ2 , 0 ,..., µk −1, 0 }. £. get the similar result.. Example 4 : For a (3, 3) NEVSS scheme and. Theorem 3: The scheme from Construction 3 is a (k, k) NEVSS scheme with non-expansible shadow size.. k,. For odd n, using the same approach, we can. ,. C1 = {µ1 ,1 , µ3 ,1 ,..., µk ,1 } .. even. i: odd. ,. C1 = {µ1,1 , µ3 ,1 ,..., µk −1 ,1 } , and for odd k,. For. C qj × ( ∑ Cik−−jq ) = C qj × ( ∑ Cik−−jq ) , i: even. C0 = {µ0 ,0 , µ2 , 0 ,..., µk , 0 }. Proof:. k-q. Since. since. the. collections. C0 = {µ0 ,0 , µ2 , 0 ,..., µk , 0 }. 0 1 1 0 C0 = {µ0 ,0 , µ2 , 0 } = {0 1 0 1 } 0 0 1 1 . ,. 0 0 1 1 C1 = {µ1,1 , µ3 ,1 } = { 0 1 0 1} 1 0 0 1. .. and. 0 1 1 0 λ= {G ( 0 ), G ( 1 ), G ( 0 ), G ( 1 )} ={0, 2, 2, C1 = {µ1,1 , µ3 ,1 ,..., µk −1 ,1 } so λ={ 0,K ,0 , 0 0 1 1 n2 n4 nk 678 678 678 2, K,2 , 4, K,4 , …, k ,K, k }, where n 0 = 2}, and γ = n0 67 8. C0k , n 2 = C 2k , n 4 = C 4k , …, n k = C kk , and n. 18 67 γ={ 1, K,1 ,. n. n. 38 67 3, K,3 ,. 58 67 5, K,5 ,. …,. 0 0 1 1 {G( 0 ), G( 1 ), G( 0 ), G( 1 )} ={1, 1, 1, 3} 1 0 0 1. nk −1 when stacking these three shadows. Pλ=1/2(3-1)=1/4, 64 47 44 8 k k k − 1,K, k − 1 }, where n 1 = C1 , n 3 = C3 , n 5 = Pγ=0, thus the difference Pλ-Pγ=1/4. Fig.4(a)~(c). C5k , …, n k-1 = C kk−1 . Since “0” is the dominant k. color among “0”~”k”, and Pλ= C0 /2k-1 =1/2k-1 , Pγ=0. The difference Pλ-Pγ=1/2k-1 holds the second. are shadow 1, shadow2, shadow 3. Fig.4(d)~(f) show that we can not get any information when stacking any two shadows. Fig.4(g) is the recovered image. We can observe that the shadow size is not expansible from the following figures.. condition. For a proof of the third condition “security”, for. Example 5 : For a (4, 4) NEVSS scheme, the two. even n, when q(<k) shadows are stacked, the. white and black collections C0 and C1 of 4×1. r. number of G( v )=j in C0 is. C qj × ( ∑ Cik−−jq ) , Boolean i: even. r and the number of G( v )=j in C1 is C qj × ( ∑ Cik−−jq ) , where j=0, 1, …, q , and i ≦ i: odd. matrices. are. shown. below.
(7) 00110101 The quality of the recovered image in a VSS 00101011 scheme is usually called contrast. Since the original C0 ={µ0,0 , µ2, 0 , µ4,0 } ={ } 01010011 black and white pixels will be expanded to the 01001101 black and white sub pixels, the recovered image is ,. less clear to the human visual system than the. 00 0 1 1 1 1 0 00 1 01 1 0 1 C1 = {µ1,1 , µ3,1} = { } 01 0 01 0 1 1 1 0 0 001 1 1 .. original image. Contrast provides a measurement for the quality of the recovered image; however, there is no consensus on the definition of contrast. First, we introduce the former definitions about contrast. The parameters h. and l are the. “whiteness” of a white and black pixel, and m is the. 4.Experimental Results and Contrast of the NEVSS Scheme 4.1 Experimental Results. Pixel Expansion. Naor and Shamir defined contrast as. αNS =. h −l [1]. Verheul and Van Tilborg m. Example 1, Example 2, and Example 4 show. showed that Naor and Shamir’s definition is. the (2, 2), (2, 3), and (3, 3) NEVSS schemes. In this. inadequate. For example, two schemes with the. section, we use these three NEVSS schemes to. parameters h=2, l=0, m=7, and h =4, l=2, m=7 will. show how to choose the optimal gray level of sub. have the same contrast value. However, these two. pixel such that we can get the clear recovered. schemes have different clearness of the recovered. image. Fig.5~Fig.7 shows the recovered images. images.. using different gray levels of the basic sub pixel for. αVV =. (2, 2), (2, 3), and (3, 3) NEVSS schemes. The gray. They. gave. the. new. contrast. as. h −l [7]. The definition of αVV does m( h + l). levels we use are GL-0, GL-30, GL-60, GL-90,. not show the correctness. Since αVV is always 1/m,. GL-120, GL-150. Here, GL-0 means black and. when l=0, but in fact for larger h the recovered. GL-255 means white.. image will more clear. Eisen and Stinson improved the previous disadvantages and defined their. From the above experimental results, Fig.5(a), contrast as Fig.6(a), Fig.7(a) have the best contrast a. We find. αES =. h −l [6]. m+ l. an interesting observation that the optimal choice. The authors defined their own contrast by the. of the gray level will be the “black”. The reason is. observation of the real results. We also use the. that when the sets λ or γ have the element “0”, the. methodology to define the contrast of the NEVSS. “0” (white) will perceive big contrast relative. scheme such that the definition of contrast is. “black ” color.. consistent with the recovered image. The contrast. According the experiment, we will define the. of NEVSS αNEVSS is defined as the following:. “contrast” of our NEVSS scheme to meet the real αNEVSS = |Pλ - Pγ. situation in next section.. 4.2 Contrast of the NEVSS Scheme. |×. 255 − ( gray level of the sub pixel ) , 255.
(8) 5. Concluding remarks. where Pλ is the probability of the dominant color in the set λ , and Pγ is the probability of the dominant color in the set γ .. In this paper, we have presented new (2, 2), (2, n), and (k, k) NEVSS schemes with non-expansible shadow size based on the new infrastructure and. The first term in αNEVSS is the difference of. operation of the sub pixel. In fact, we can also. the probability for the dominant color, and the. construct (k, n) NEVSS schemes by choosing the. second term is the background color. The dominant. suitable sets λ and γ. Here, we give the white and. color means the biggest contrast relative other. black collections C0 , C1 for (3, 4) NEVSS scheme to. colors in the set λ and γ mentioned in the early. show. section. For example, for (2, 2), (2, 3), and (3, 3). the. schemes.. NEVSS schemes, the dominant color is “0” (white).. feasibility. of. (k,. n). NEVSS. C0 = {µ0 ,0 , µ3, 0 } , C1 = {µ1,1 , µ4 ,1 } ,. The contrast of the recovered images in Fig.5 ~. and λ = {0, 0, 2, 2, 2, 3}, γ = {0, 1, 1, 1, 3, 3}, then. Fig.6 are calculated and shown in Table 1.. Pλ - Pγ =1/3-1/6=1/6. If we use the gray level of sub pixel. From Table 1, and Fig.5~Fig.7, we see that our definition of contrast is consistent with the. =(. =. GL-0,. i.e.,. black,. then. αNEVSS. 2 1 255 − 0 1 − ) ×( ) = . However, the general 6 6 255 6. experimental results.. method for constructing (k, n) NEVSS schemes may. Obviously, the value of αNS , αVV, αES, and αNEVSS will be different for one recovered image due to the different definitions. Here, we make a test to show the relation between clearness and the contrast value for different definitions of contrast. First, we choose five typical recovered images for the conventional (2, 2) VSS scheme and use a score of 5 to 1 as “excellent” to “poor” to represent them. Then, select five recovered images for the (2, 2) NEVSS scheme with the same clear quality of the recovered images compared to the conventional (2, 2) VSS scheme. Calculate each contrast value, and we find every slope of line raises when the clearness increases shown in Fig.8. This shows the truth that these contrast αNS , αVV, αES, and αNEVSS really give a measurement of how clear the recovered image is.. need the further studies.. References [1] M. Naor and A. Shamir, “Visual cryptography,” Advances. in. Cryptology- EUROCRYPT’94,. Lecture Notes in Computer Science, No.950, pp.1-12, Springer-Verlag, 1995. [2]. S.. Droste,. “New. cryptography,”. results. Advances. in. on. visual. Cryptology-. EUROCRYPT’96, Lecture Notes in Computer Science, No.1109, pp.401-415, Springer-Verlag, 1996. [3] T. Katoh and Hideki Imai, “Some visual secret sharing. schemes. and. their. share. size,”. Proceedings of International Conferences on Cryptology and Information Security, pp.41-47, DEC. 1996. [4] G. Ateniese, C. Blundo, A. De Santis, and D.R. Stinson, “Visual cryptography for general access structures,” ECCC, Electronic Colloquium on Computational Complexity (TR96-012), via.
(9) WWW using h ttp://www.eccc.uni-trier.de/eccc/. [5] G. Ateniese, C. Blundo, A. De Santis, and D.R. Stinson, “Constructions and bounds for visual cryptography,”. Proc.. 23rd. International. Colloquium on Automata, Languages, and Progrramming (ICALP’96), Lecture Notes in Computer Science , Springer-Verlag, 1996. [6] P.A. Eisen and D.R. Stinson, “Threshold Visual Cryptography. Schemes. With. Specified. Whiteness”, submitted to Designs, Codes and Cryptography,. available. at. http://cacr.math.uwaterloo.ca/~dstinson/visual.ht ml. [7] E.R. Verheul and H.C.A. Van Tilborg, “Constructions and properties of k out of n visual secret sharing schemes,” Designs, Codes and Cryptography, vol.11, No.2, pp.179-196, May, 1997. [8] C. N. Yang and C.S. Laih, “New colored visual secret sharing schemes,” accepted and to be published, Designs, Codes and Cryptography. [9] G.R. Blakley, “Safeguarding cryptographic keys”, AFIPS conference proceedings, vol.48, pp.313-317, 1979. [10] A. Shamir, “How to share a secret,” Commun. of th ACM, vol.22, pp.612-613, Nov. 1979..
(10) Sub pixel i. j. i+j. Sub pixel. i. j. i+j. “ADD”. =. “OR”. =. “ADD”. =. “OR”. =. “ADD”. =. “OR”. =. (a) “ADD” operation for gray sub pixels. (b) “OR” operation for black and white sub pixels. Figure 1. The sub pixels of the proposed scheme and conventional scheme and their operations.. (a) Shared secret. (b) Shadow 1. (c) Shadow 2 (d) Shadow 1 + Shadow 2 Figure 2. The (2, 2) NEVSS scheme. (a) Shadow 1. (d) Shadow 1 + Shadow 2. (b) Shadow 2. (e) Shadow 2 + Shadow 3 Figure 3. The (2, 3) NEVSS scheme. (c) Shadow 3. (f) Shadow 1 + Shadow 3.
(11) (a) Shadow 1. (d) Shadow 1 + Shadow 2. (b) Shadow 1. (e) Shadow 1 + Shadow 3. (c) Shadow 3. (f) Shadow 2 + Shadow 3. (g) Shadow 1 + Shadow 2 + Shadow 3 Figure 4. The (3, 3) NEVSS scheme. (a) gray level = GL-0. (b) gray level = GL-30. (c) gray level = GL-60. (c) level = GL-90 (e) gray level = GL-120 (f) gray level = GL-150 Figure 5. The recovered images for (2, 2) NEVSS scheme with different gray levels of sub pixel. (a) gray level = GL-0. (b) gray level = GL-30. (c) gray level = GL-60. (d) gray level = GL-90. (e) gray level = GL-120. (f) gray level =GL-150. Figure 6. The recovered images for (2, 3) NEVSS scheme with different gray levels of sub pixel.
(12) (a) gray level = GL-0. (b) gray level = GL-30. (c) gray level = GL-60. (d) gray level = GL-90. (e) gray level = GL-120. (f) gray level = GL-150. Figure 7. The recovered images for (3, 3) NEVSS scheme with different gray levels of sub pixel Table 1. The contrast αNEVSS for different NEVSS schemes Gray level of the sub pixel. Types of NEVSS schemes. GL-0. GL-30. GL-60. GL-90. GL-120 GL-150. (2, 2). 0.50. 0.44. 0.38. 0.32. 0.26. 0.21. (2, 3). 0.33. 0.29. 0. 25. 0.21. 0.17. 0.14. (3, 3). 0.25. 0.22. 0.19. 0.16. 0.13. 0.11. 2. 3. 4. 5. 0.6 Contrast. 0.5 0.4 0.3 0.2 0.1 0 1. clearness Naor-Shamir Contrast. Verheul-Van Tilborg Contrast. Eisen-Stinson Contrast. NEVSS Contrast. Figure 8. The value of αNS , αVV , αES , and αNEVSS.
(13)
數據
相關文件
In Sections 3 and 6 (Theorems 3.1 and 6.1), we prove the following non-vanishing results without assuming the condition (3) in Conjecture 1.1, and the proof presented for the
Department of Computer Science and Information
Department of Computer Science and Information
Department of Computer Science and Information
Department of Mathematics – NTNU Tsung-Min Hwang November 16, 2003... We say that the rate of
In this paper, motivated by Chares’s thesis (Cones and interior-point algorithms for structured convex optimization involving powers and exponentials, 2009), we consider
Department of Mathematics – NTNU Tsung-Min Hwang November 30, 2003... Department of Mathematics – NTNU Tsung-Min Hwang November
Department of Computer Science and Information Engineering, Chaoyang University of