Performance Analysis for Voice/Data Integration on a
Finite-Buffer Mobile System
Yieh-Ran Haung, Yi-Bing Lin, Senior Member, IEEE, and Jan-Ming Ho
Abstract—Personal communication service (PCS) networks
offer mobile users diverse telecommunication applications, such as voice, data, and image, with different bandwidth and quality-of-service (QoS) requirements. This paper proposes an analytical model to investigate the performance of an integrated voice/data mobile network with finite data buffer in terms of voice-call blocking probability, data loss probability, and mean data delay. The model is based on the movable-boundary scheme that dynamically adjusts the number of channels for voice and data traffic. With the movable-boundary scheme, the bandwidth can be utilized efficiently while satisfying the QoS requirements for voice and data traffic. Using our model, the impact of hot-spot traffic in the heterogeneous PCS networks, in which the param-eters (e.g., number of channels, voice, and data arrival rates) of cells can be varied, can be effectively analyzed. In addition, an iterative algorithm based on our model is proposed to determine the handoff traffic, which computes the system performance in polynomial-bounded time. The analytical model is validated by simulation.
Index Terms—Handoff, hot-spot, movable-boundary, personal
communication service, quality-of-service.
I. INTRODUCTION
A
PERSONAL communication service (PCS) [1]–[4]network offers integrated services where mobile users communicate via wireless links in the radio coverage of base stations. PCS networks are expected to support diverse applica-tions, such as voice, data, and image, etc., demanding different quality-of-service (QoS) and bandwidth. The bandwidth of the wireless links is inherently limited and is generally much smaller than that in its wireline counterpart. Particularly, for integrated voice/data mobile networks, voice traffic results in call losses and data traffic suffers from longer delays should networks have insufficient bandwidth. Thus, it is essential to design mobile networks that furnish effective and dynamic al-location of the bandwidth to satisfy different services demands. In integrated voice/data mobile networks, several proposed bandwidth allocation schemes [5]–[8] attempt to achieve im-proved system performance (e.g., voice-call blocking proba-bility and data delay, etc.). Generally, these schemes are based on movable-boundary strategy with or without reservation for voice or data traffic. Although these schemes were evaluated Manuscript received June 13, 1997; revised November 2, 1998. The work of Y.-B. Lin was supported in part by the National Science Council under Contract NSC88-2213-E009-079.
Y.-R. Haung and J.-M. Ho are with the Institute of Information Science, Academia Sinica, Taipei, Taiwan, R.O.C.
Y.-B. Lin is with the Department of Computer Science and Information En-gineering, National Chiao Tung University, Hsinchu, Taiwan, R.O.C. (e-mail: liny@csie.nctu.edu.tw).
Publisher Item Identifier S 0018-9545(00)02546-9.
extensively, the effect of handoff [1]–[4], [9] traffic due to the movement of portables was not taken into account. Handoff de-notes the procedure of changing channels associated with cur-rent connection to maintain acceptable service quality. It is ini-tiated by cell boundary crossing. When the cell size of PCS net-works is relatively small [1]–[4], the handoff traffic has an im-portant effect on the system performance.
This paper proposes an analytical model to study the system performance of an integrated voice/data mobile network with finite data buffer in terms of voice-call blocking probability, data loss probability, and mean data delay. Our model is based on the movable-boundary scheme, which considers both voice and data traffic with the handoff effects.
With the movable-boundary scheme, the available band-width (i.e., radio channels) of each cell is partitioned into three compartments, namely, designated voice channels, designated data channels, and shared channels. Designated voice and data channels are dedicated for voice and data traffic transmissions, respectively. The shared channels can be used by either type of traffic. The boundary between compartments is dynamically moved such that the bandwidth can be utilized efficiently while satisfying the QoS requirements for voice and data traffic.
Previous handoff studies [1], [3], [9], [10] assumed a homo-geneous PCS network where all cells have the same number of channels and experience the same new and handoff call ar-rival rates. Our model accommodates the heterogeneity of a PCS network by relaxing the restrictions in those previously pro-posed models. With our model, the parameters (e.g., number of channels, voice, and data arrival rates) of cells can be varied, and hence the impact of hot-spot traffic can be effectively an-alyzed. Our model utilizes an iterative algorithm to determine the handoff traffic, which computes the system performance in polynomial-bounded time. Simulation experiments are con-ducted to validate the accuracy of the analytical model.
The paper is organized as follows. Section II presents the analysis of an integrated voice/data mobile network with finite data buffer. In Section III, extensive performance results are pre-sented. In addition, the accuracy of analytical results are con-firmed by simulation results. Finally, Section IV concludes the paper. The notation used in this paper is in Appendix I.
II. PERFORMANCEANALYSIS
In this section, we analyze the system performance in terms of voice-call blocking probability, data loss probability, and mean data delay in each cell. The system under consideration is an integrated voice/data mobile network, in which the users move along an arbitrary topology of cells according to the routing 0018–9545/00$10.00 © 2000 IEEE
Fig. 1. Base station architecture.
probability (from cell to cell In each cell the arrivals of new voice calls, handoff voice calls, new data packets, and handoff data packets are Poisson distributed with rates
and respectively. In addition, we assume that the system uses the nonprioritized handoff scheme [1]–[4] where the channel assignment to the new and the handoff voice calls/data packets are not distinguishable.
It is assumed that voice and data traffic have exponential ser-vice-time (call holding time) distribution with means and respectively. Moreover, the residence times in a cell for voice and data portable are assumed to follow exponential dis-tribution with means and respectively. Although the cell residence times are typically nonexponential in a particular mobile system, the analysis based on the simplified exponen-tial assumption has been widely used [1], [3], [9]–[12] and does provide useful mean value information for the output measures. To relax the exponential assumptions, performance of the mov-able-boundary scheme can be investigated by the simulation ex-periments conducted in this paper.
A. The Model
For each cell the base station architecture is illustrated in Fig. 1. There are three types of traffic channels. Designated voice and data channels are dedicated for voice and data traffic transmissions, respectively. The shared channels can be used by either type of traffic. Voice traffic is balked from the system if legitimate channels are all in use upon its arrival. On the con-trary, data traffic would be queued in a buffer should legitimate channels be busy.
In our study, the base station architecture (see Fig. 1) is modeled by a continuous-time model with heterogeneous
arrivals (voice and data), multiple designated channels (voice,
data, and shared channels), and finite data buffer. For analytical tractability, we assume that the buffer size is infinite and then compute the tail probability to approximate the data loss probability under finite buffer size. Starting with a guess of handoff rates and we assume that voice and data traffic in each cell are Poisson distributed with arrival rates
and
respectively. Moreover, the channel occupancy times for voice and data traffic are assumed to have exponential distribution
with means and
respectively. Note that and will be determined
by an iterative algorithm (to be elaborated later). Each base station has finite buffer size Let be the total number of channels in cell and and be the number of channels
designated for voice and data traffic, respectively (see Fig. 1).
Thus, there are shared channels that can be
used by either type of traffic. All channels are employed in a first-come first-serve (FCFS) manner.
B. The Analysis
The queueing system shown in Fig. 1 is ergodic [13] if
Let be the
steady-state probability that simultaneously there are voice calls and data packets in cell ; the corresponding balance equations are shown as follows.
Case I: If the number of voice calls in cell is less than
i.e., then
.. .
..
. (1)
Case II: If the number of voice calls in cell is equal to
i.e., then
.. .
..
Case III: If the number of voice calls in cell exceeds but is less than the total number of channels eligible for voice
traffic, i.e., then
.. .
..
. (3)
Case IV: If the number of voice calls in cell is equal to
i.e., then
.. .
..
. (4)
Define the probability generating function of the occupancy dis-tribution of data traffic as
(5)
where and By using (1)–(4), we derive
in four cases.
Case I: If , then
(6)
where
and
Case II: If , then
(7)
where
and
Case III: If , then
(8)
where
Case IV: If , then
where
From (6) to (9), we obtain
(10) After rearrangement, (10) is rewritten as
(11) Consider the voice-call blocking probability and the handoff voice-call arrival rate in cell Since the nonprioritized handoff scheme is adopted, the voice-call blocking probability is equal to the voice-call forced termination probability, which is given by
(12)
Note that By setting in (6)–(8) and
after manipulations, can be expressed as
(13) Since the probability that an accepted voice call will attempt to hand off is the rate of the handoff voice calls moving out of cell is given by
(14) By using (14), the rate of handoff voice calls moving into cell
is expressed as
(15) After the voice-call blocking probability in each cell
is determined, can be calculated using (15).
To evaluate the data loss probability in cell we follow the approach described in [15]. Let be the tail probability of the number of data packets when there are voice calls in cell i.e., The generating function for is expressed as
(16)
where and After some manipulations,
we have
(17)
where is given in (11). Based on the algorithm
proposed in [15], the data loss probability in cell can be expressed as
(18) where is the real part of the complex number To limit
the error within we let Following the same
reasoning for the handoff voice calls, the rate of handoff data packets moving into cell is related to by
(19) Differentiating (10) with respect to and setting the mean number of data packets in cell can thus be derived as
(20) Using (20) and applying Little’s Formula, we obtain the mean data delay, in cell as
(21) where and are given in (18) and (19), respectively.
Consequently, as shown in (13), (18), and (21), to compute and we have to calculate
and the steady-state
probabilities and
The reader is referred to [14] for the details of these calculations. We will, however, provide the major computational steps in Appendix II. It is worth noting that, since these calculations are polynomial bounded, the performance measures of the mobile system can be computed in polynomial-bounded time.
C. The Iterative Algorithm
In this section, we propose an iterative algorithm to compute the voice-call blocking probability, the data loss probability, and the mean data delay in cell using the equations derived in Sec-tion II-B. Recall that the voice-call blocking probability is derived based on the amount of traffic contending for the available channels. is changed if some data packets are lost, resulting in a reduction in the contending traffic.
Beginning with an initial data arrival rate, with no loss, we first derive and Based on arrival rate new data loss probability and voice-call blocking probability [ and
respectively] can then be obtained. We iterate this procedure until and converge and use these two quantities as estimates for the data loss probability and the voice-call blocking probability, respectively. After and are determined, the handoff data and voice-call arrival rates
[ and respectively] can then be calculated
by using (19) and (15), respectively. To obtain the convergent
values of and we follow an iterative technique
proposed in [1].
Assume that there are cells in the mobile system, and a mobile user moves from cell to cell with the routing proba-bility The iterative algorithm is shown as follows:
D. The Iterative Algorithm
Input Parameters: (routing matrix), (new voice-call arrival rate to cell (new data arrival rate to cell (mean voice-call service time), (mean data service time), (mean voice-portable residence time), (mean data-portable residence time), (number of chan-nels of cell (number of channels designated for voice traffic), (number of channels designated for data traffic), and
(buffer size for cell
Output Measures: (handoff voice-call arrival rate to cell (handoff data arrival rate to cell
(voice-call blocking probability in cell (data loss probability in cell and (mean data delay in cell
Step 1): and
Step 2): For select initial values for and
and perform the following steps.
Step 3): and
Step 4): Compute by using (11).
Step 5): Compute by using (17).
Step 6): Compute and by using (13) and (18),
respectively. Step 7):
Step 8): Iterate steps 4)–7) until and converge.
Step 9): Compute and by using (15) and (19),
respectively.
Step 10): Iterate steps 3)–9) until and converge. Step 11): Compute by using (21).
For all cases studied in this paper, the iterative procedure con-verges within ten iterations of steps 3)–9), where each itera-tion of steps 3)–9) converges within 13 iteraitera-tions of steps 4)–7). Moreover, we observe that numbers of iterations required for homogeneous systems are smaller than heterogeneous systems, but the difference is not significant. Since the run time com-plexity of steps 4)–7) is polynomial bounded, the iterative al-gorithm is a polynomial-bounded alal-gorithm. Accordingly, the recomputation of the system performance due to the bandwidth reallocation can be performed in polynomial-bounded time.
III. NUMERICALRESULTS
To verify the accuracy of the analysis, we carried out an event-driven simulation. In the simulation, we considered the move-ments of users along a one-dimensional (1-D) cellular system [9], [11], [16], which consists of six cells arranged as a ring. We assume that a mobile user moves to its left neighboring cell with the same probability as to its right neighboring cell. To simplify our results, the cellular system is assumed to be homogeneous, although the simulation can accommodate arbitrary heteroge-neous PCS network structure. For a homogeheteroge-neous PCS network, we have
and
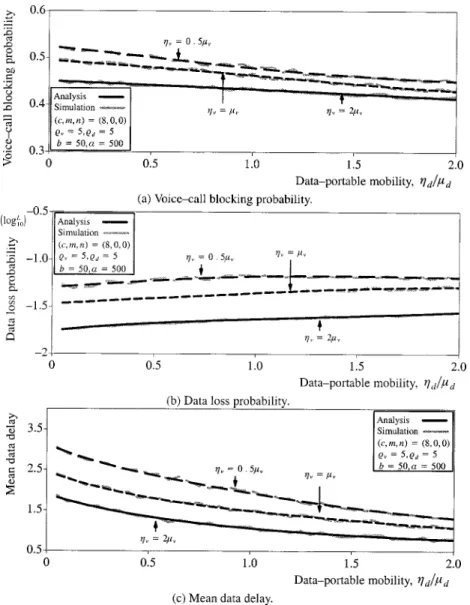
The simulation was run for a relatively long duration, and appro-priate statistics (i.e., voice-call blocking probability, data loss probability, and mean data delay) were obtained after allowing sufficient time to reach a steady state (i.e., all cells experienced almost the same voice-call blocking and data loss probabilities). The effect of voice- and data-portable mobilities on the system performance can be seen in Fig. 2 where
i.e., the ratio of voice service time to data service time). The figure indicates that analytical results agree with simulation results with negligible discrepancy. Moreover, from Fig. 2(a) and (c), we observe that the voice-call blocking probability and the mean data delay decrease as voice- or data-portable mobilities increase. This phenomenon is consis-tent with known results [1], [17] for pure voice system where the nonprioritized handoff scheme is adopted. As or increases, the system experiences larger handoff arrivals and
Fig. 2. System performance versus data-portable mobility.
shorter channel occupancy times where the total offered load (new plus handoff arrivals) is about the same. For the same offered load, and decrease as the service times decrease. Fig. 2(b) shows that the data loss probability decreases as voice-portable mobility increases. As increases the channel occupancy times decrease, resulting in the associated decrease in Moreover, it is seen that is insensitive to under smaller voice-portable mobility, say and slightly increases as increases under larger voice-portable mobility, say
This phenomenon is due to the fact that large values of correspond to large values of resulting in an increase in the data queue length and hence an increase in the data loss prob-ability. Note that as increases the contending voice traffic increases, the effect of on becomes significant.
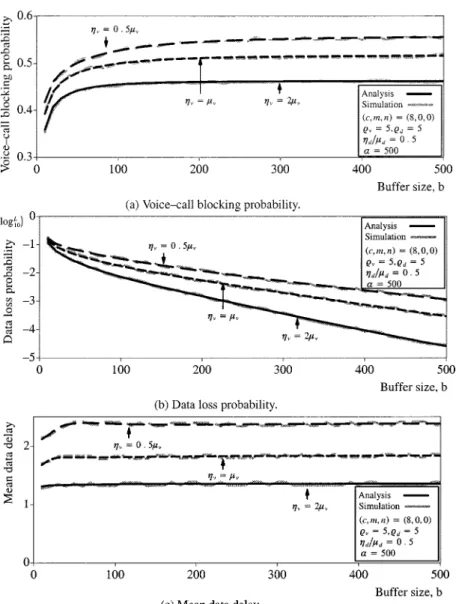
Fig. 3 plots the system performance for different voice-portable mobilities as a function of buffer size. Again, the figure shows that analytical and simulation results are consistent. From Fig. 3(b), it is clear that as the buffer size increases the data loss probability decreases. The tradeoff is the associated increases in the voice-call blocking probability and the mean data delay as shown in Fig. 3(a) and (c). This phenomenon is due to the fact that as the data loss probability decreases the contending
traffic increases, resulting in the associated increases in and In addition, to guarantee a prescribed data loss probability, the buffer size is expected to increase with decreasing Fig. 3(b) shows this quantitatively. On the other hand, as we have seen previously, the data loss probability increases as increases. Thus, as increases, larger buffer size is required to guarantee a prescribed data loss probability.
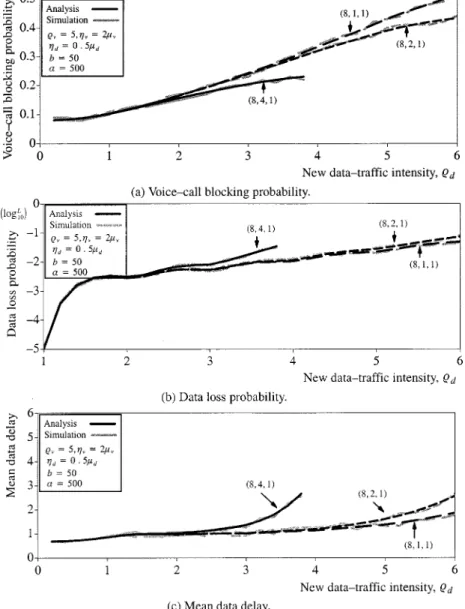
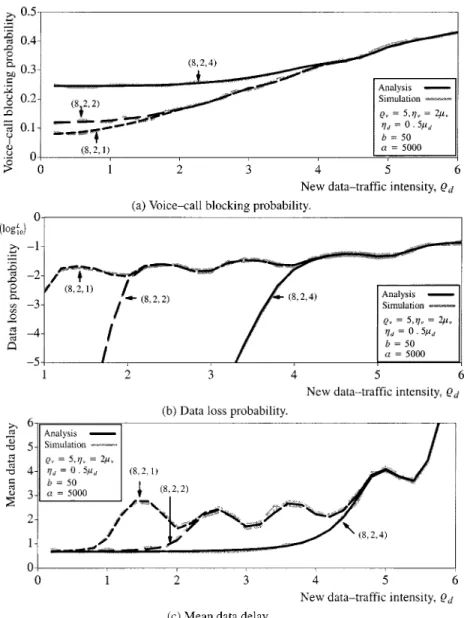
Figs. 4 and 5 depict the system performance for various band-width allocation paradigms as a function of the new data-traffic intensity The figures show that the voice-call blocking probability increases as increases and decreases as increases, while the data loss probability and the mean data delay increase as increases and decrease as increases. An-other observation from Figs. 4(b) and (c) and 5(b) and (c) is that the data loss probability and the mean data delay oscillate as increases. In addition, the figures reveal the high sensitivity of
and to Recall that is the ratio of voice service time
to data service time. For example, with it
is seen that the larger the more and oscillate. This phe-nomenon is also observed in [14]. This salient phephe-nomenon can be inferred from the following fact. Since voice calls often last on the order of minutes, while the duration of data transmission
Fig. 3. System performance versus buffer size.
may elapse only on the order of milliseconds, the termination of voice calls can decrease data losses and delays profoundly. On
the other hand, with from Figs. 4(a) and
5(a), we observe that the voice-call blocking probability is irrel-evant to For more numerical results relating to the readers are referred to [14].
From the point of view of a mobile user, forced termination of an ongoing call is less desirable than blocking a new call. As a result, it needs to impose explicit control on the admis-sion of new calls in order to keep the probability of forced ter-mination at an acceptable level, in addition to allocating band-width dynamically and efficiently. The schedulable region (i.e., the acceptable load region) [18], which has been used for call admission control, can be calculated based on the bandwidth allocation scheme employed, portable mobility, channel occu-pancy time distribution, buffer size, and QoS constraints. For example, with
and Fig. 6 presents the schedulable regions for different voice-portable mobilities under the QoS constraints
and The figure indicates that the larger the larger size of the schedulable region (area under the curve).
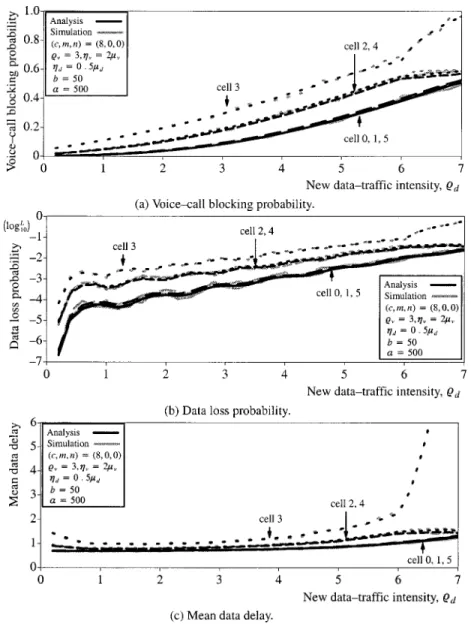
Finally, in order to illustrate the impact of hot-spot traffic on system performance, we carried out a numerical example for a heterogeneous cellular system. We assume that the mobile users move along a ring of six cells according to the routing matrix
For ease of illustrating the effects of hot-spot traffic caused by users’ movements, we assume
and
Fig. 7 shows the system performance for six cells as a function of the new data-traffic intensity Again, the figure indicates
Fig. 4. System performance for various number of designated voice channels.
that analytic results are consistent with simulation results. Moreover, it is observed that the system performance of cell 3 (hot-spot cell) is significantly impaired by hot-spot traffic.
IV. CONCLUSIONS
This paper presented a traffic model for an integrated voice/data mobile system with finite data buffer, and validated its accuracy by simulation. With our model, the system per-formance (i.e., voice-call blocking probability, data loss prob-ability, and mean data delay) based on the movable-boundary scheme and the impact of hot-spot traffic in a heterogeneous PCS network can be effectively analyzed. In addition, we proposed an iterative algorithm to determine the handoff traffic and compute the system performance, and proved that its run time complexity is polynomial bounded. This fact allows the recomputation of the system performance due to the bandwidth reallocation to be performed in polynomial-bounded time. According to the numerical results, we observed the following.
• The voice-call blocking probability and the mean data delay decrease as voice- or data-portable mobilities in-crease, while the data loss probability decreases as voice-portable mobility increases and slightly increases as data-portable mobility increases.
• The data loss probability decreases as the buffer size in-creases. The tradeoff is the associated increases in the voice-call blocking probability and the mean data delay. • The voice-call blocking probability decreases as
increases (i.e., number of channels designated for voice traffic) and increases as increases (i.e., number of channels designated for data traffic), while the data loss probability and the mean data delay decrease as increases and increase as increases.
Recall that the goal of voice/data integration on a mobile system is to share the bandwidth efficiently while keeping the proba-bility of forced termination at an acceptable level. As a result, in addition to allocating bandwidth dynamically and efficiently, it also needs to impose explicit control on the admission of new calls. We have shown an example of the schedulable region
Fig. 5. System performance for various number of designated data channels.
Fig. 6. Schedulable region with QoS guarantees.
which can be used for call admission control. Based on our model, we are developing a scheduling algorithm which com-bines bandwidth allocation scheme and call admission control
in an integrated, efficient, and intelligent manner to satisfy di-verse QoS requirements.
APPENDIX I NOTATION
In this Appendix, we outline the notation used for the anal-ysis. For each cell we define the following notation.
Number of cells in the mobile system.
th cell where .
Routing matrix.
New voice-call arrival rate. New data arrival rate.
Handoff voice-call arrival rate. Handoff data arrival rate.
Mean voice-call service time. Mean data service time.
Fig. 7. System performance for six cells.
Mean voice-portable residence time.
Mean data-portable residence time.
Number of channels.
Number of channels designated for voice traffic.
Number of channels designated for data traffic.
Buffer size.
Steady-state probability of having voice calls and data packets in cell .
Probability generating function
of .
Tail probability of (i.e., .
Probability generating function
of .
Voice-call blocking probability. Data loss probability.
Mean data delay.
APPENDIX II
DERIVATION FOR AND
This Appendix provides the major computational steps for the derivation of
and and
First, setting in (8) and (9), one can derive
recursively. Since from (6) to (8),
By differentiating (8) and (9) with respect to and setting
we obtain recursively.
We now calculate the steady-state probabilities from (1)–(4). However, (1)–(4) do not provide enough indepen-dent equations to solve these probabilities. This is because
additional unknowns,
and have to be solved. Thus,
we must discover another additional independent equations. Setting in (10), we obtain one additional equation. Moreover, equating the zeros on both sides of (8) and (9) provides additional equations. Finally, let
(22)
where and From (6), (7), and (22),
we have
(23)
where Notice that has distinct
roots between (0,1). For a rigorous proof, the reader is again re-ferred to [14]. Equating the zeros on both sides of (23) provides the last equations needed.
REFERENCES
[1] Y.-B. Lin et al., “The sub-rating channel assignment strategy for PCS hand-offs,” IEEE Trans. Veh. Technol., vol. 45, no. 1, pp. 122–130, 1996. [2] V. O. K. Li and X. Qiu, “Personal communication systems (PCS),” Proc.
IEEE, vol. 83, no. 9, pp. 1210–1243, 1995.
[3] Y.-B. Lin et al., “Queueing priority channel assignment strategies for handoff and initial access for a PCS network,” IEEE Trans. Veh.
Technol., vol. 43, no. 3, pp. 704–712, 1994.
[4] , “Channel assignment strategies for hand-off and initial access for a PCS network,” IEEE Personal Commun. Mag., vol. 1, no. 3, pp. 47–56, 1994.
[5] H. Qi and R. Wyrwas, “Performance analysis of joint voice-data PRMA over random packet error channels,” IEEE Trans. Veh. Technol., vol. 45, no. 2, pp. 332–345, 1996.
[6] P. Narasimham and R. D. Yates, “A new protocol for the integration of voice and data over PRMA,” IEEE J. Select. Areas Commun., vol. 14, no. 4, pp. 623–631, 1996.
[7] J. E. Wieselthier and A. Ephremides, “Fixed- and movable-boundary channel-access schemes for integrated voice/data wireless networks,”
IEEE Trans. Commun., vol. 43, no. 1, pp. 64–74, 1995.
[8] C. Chang and C. Wu, “Slot allocation for an integrated voice/data TDMA mobile radio system with a finite population of buffered users,” IEEE
Trans. Veh. Technol., vol. 43, no. 1, pp. 21–26, 1994.
[9] F. Pavlidou, “Two-dimensional traffic models for cellular mobile sys-tems,” IEEE Trans. Commun., vol. 42, no. 2/3/4, pp. 1505–1511, 1994.
[10] C. H. Yoon and C. K. Un, “Performance of personal portable radio tele-phone systems with and without guard channels,” IEEE J. Select. Areas
Commun., vol. 11, no. 6, pp. 911–917, 1993.
[11] M. Naghshine and M. Schwartz, “Distributed call admission control in mobile/wireless networks,” IEEE J. Select. Areas Commun., vol. 14, no. 4, pp. 711–717, 1996.
[12] W. C. Wong, “Packet reservation multiple access in a metropolitan mi-crocellular radio environment,” IEEE J. Select. Areas Commun., vol. 11, no. 6, pp. 918–925, 1993.
[13] L. Kleinrock, Queueing Systems, Vol. I: Theory. New York: Wiley, 1975.
[14] M. C. Young and Y.-R. Haung, “Bandwidth assignment paradigms for broadband integrated voice/data networks,” Computer Commun., vol. 21, no. 3, pp. 243–253, 1998.
[15] J. Abate and W. Whitt, “Numerical inversion of probability generating functions,” Operations Res. Lett., vol. 12, pp. 245–251, 1992. [16] Y. Akaiwa and H. Andoh, “Channel segregation—A self-organized
dy-namic channel allocation method: Application to TDMA/FDMA micro-cellular systems,” IEEE J. Select. Areas Commun., vol. 11, no. 6, pp. 949–954, 1993.
[17] Y.-B. Lin et al., “Allocating resources for soft requests—A performance study,” Inform. Sci., vol. 48, no. 1–2, pp. 39–65, 1995.
[18] S. Kumar and D. R. Vaman, “An access protocol for supporting multiple classes of service in a local wireless environment,” IEEE Trans. Veh.
Technol., vol. 45, no. 2, pp. 288–302, 1996.
Yieh-Ran Haung received the B.S. degree in computer science from SooChow University, Taiwan, R.O.C., in 1991 and the M.S. and Ph.D. degrees in com-puter science and information engineering from National Chiao Tung Univer-sity, Hsinchu, Taiwan, in 1993 and 1997, respectively.
Since October 1997, he has been a Post-Doctoral Fellow at the Institute of Information Science, Academia Sinica, Taipei, Taiwan. His research interests include personal communication services networks, integrated services internet, and wireless internet access.
Yi-Bing Lin (S’80–M’96–SM’96) received the B.S.E.E. degree from National Cheng Kung Uni-versity, Taiwan, R.O.C., in 1983 and the Ph.D. degree in computer science from the University of Washington, Seattle, in 1990.
From 1990 to 1995, he was with the Applied Re-search Area, Bell Communications ReRe-search (Bell-core), Morristown, NJ. In 1995, he was appointed as a Professor in the Department of Computer Science and Information Engineering (CSIE), National Chiao Tung University (NCTU), Hsinchu, Taiwan. In 1996, he was appointed as Deputy Director of the Microelectronics and Information Systems Research Center, NCTU. Since 1997, he has been Chairman of CSIE, NCTU. His current research interests include design and analysis of personal communications services network, mobile computing, distributed simulation, and performance modeling. He is an Associate Editor of the IEEE NETWORK. He was a Guest Editor of the IEEE TRANSACTIONS ONCOMPUTERSSpecial Issue on Mobile Computing.
Dr. Lin is an Associate Editor of SIMULATION Magazine, an Area Editor of the ACM Mobile Computing and Communication Review, a Columnist of ACM
Simulation Digest, a member of the editorial board of the International Journal of Communications Systems, a member of the editorial board of ACM/Baltzer Wireless Networks, a member of the editorial board of Computer Simulation Modeling and Analysis, Guest Editor for the ACM/Baltzer MONET Special Issue
on Personal Communications, and an Editor of the Journal of Information
Sci-ence and Engineering. He was the Program Chair for the 8th Workshop on
tributed and Parallel Simulation, General Chair for the 9th Workshop on Dis-tributed and Parallel Simulation, Program Chair for the 2nd International Mobile Computing Conference, and Publicity Chair of ACM Sigmobile. He received the 1997 Outstanding Research Award from the National Science Council, Taiwan, and the Outstanding Youth Electrical Engineer Award from CIEE, Taiwan.
Jan-Ming Ho received the B.S. degree in electrical engineering from National Cheng Kung University in 1978, the M.S. degree from the National Chiao Tung University, Hsinchu, Taiwan, R.O.C., in 1980, and the Ph.D. degree in electrical engineering and computer science from Northwestern University, Evanston, IL, in 1989.
He joined the Institute of Information Science, Academia Sinica, Taipei, Taiwan, as an Associate Research Fellow in 1989 and was promoted to Research Fellow in 1994. He visited the IBM T. J. Watson Research Center in the summers of 1987 and 1988, the Leonardo Fibonacci Institute for the Foundations of Computer Science, Italy, in the summer of 1992, the Dagstuhl-Seminar on “Combinatorial methods for integrated circuit design,” and the IBFI-Geschäftsstelle, Schloβ Dagstuhl, Fachbereich Informatik, Universität des Saarlandes, Germany, in October 1993. He is an Associate Editor of the IEEE TRANSACTIONS ON MULTIMEDIA. His research interests include internet computing, real-time operating systems, real-time networking, real-time multimedia applications, e.g., video conference and video on demand, computational geometry, combinatorial optimization, VLSI design algorithms, and implementation and testing of VLSI algorithms on real designs. He and his team members have developed several system prototypes including a multimedia digital library, ASIS MDL.
Dr. Ho was a Program Cochair of the Workshop on Real-Time and Media Systems from 1995 to 1998 and General Cochair of the International Sympo-sium on Multimedia Information Processing, ISMIP, 1997.