Imbalanced Wireless Networks
Chien-Lung Hsu*, Wen-Te Lin, and Yen-Chun Chou
Department of Information Management Chang Gung University, Tao-Yuan 333, Taiwan, ROC Taiwan Information Security Center (TWISC),
Taipei 106, Taiwan, ROC
*
clhsu@mail.cgu.edu.tw {b9244203, b9244118}@stmail.cgu.edu.tw
Received 29 March 2007; Revised 20 April 2007 ; Accepted 22 May 2007
Abstract. Yeh et al. recently proposed a password-based authenticated key exchange protocol based on RSA for imbalanced wireless networks. However, several scholars pointed out that Yeh et al.’s protocol is insecure against off-line password guessing attacks and inefficient enough for mobile devices in terms of the computa-tional load. This paper will propose a new efficient and secure password authenticated key exchange protocol. Both security and performance of the proposed protocol are better than previously proposed protocols. Keywords: Authentication, Key Exchange, Password, Wireless, Imbalanced, Password Guessing
1 Introduction
In a wireless network environment, information is transmitted in electromagnetic media through the air, rather than traditional wired or other physical conduits. All wireless signals traveling through the air without any protec-tion are susceptible to analysis. This means proprietary informaprotec-tion, healthcare records, user’s identity, financial messages, or any other types of sensitive information might be compromised by malicious persons. Hence, secure communication in such an environment is a very important issue.
Password authenticated key exchange protocols allow two entities to authenticate each other with a human memorable password and agree on a secret common key shared between them. The session key is used to secure their communication channel for confidentiality. Such protocols have been widely used in wired network for their simplicity and convenience, since users can choose easy-to-remember passwords without any assistant device. Major challenges in designing password authenticated key exchange protocols in wireless networks are perform-ance and security considerations. A wireless network is generally an imbalperform-anced one in which computational capabilities and storage capacities of the servers are powerful and those of the mobile devices (e.g., handset, PDA, and so forth) are limited. It is difficult to implement security techniques used in wired network on mobile devices for their limited CPUs, memory, bandwidth, and storage abilities from a performance perspective. From security considerations, a password authenticated key exchange protocol must be secure against password guess-ing or dictionary attacks since passwords are generally drawn from a small and enumerable space. Password guessing attacks can be generally divided into three types [11]:
(i) Detectable on-line password guessing attacks: An adversary attempts to use his guessed password to perform an on-line transaction. If the transaction is accepted by the correspondent, the adversary is convinced of this password. Otherwise, the failed guess will be detected (and logged). Such an attack is generally unavoidable, but it can be handled appropriately. For instance, invalid trials must be controlled under appropriate intervals. (ii) Undetectable on-line password guessing attacks: An adversary attempts to use his guessed password to
per-form an on-line transaction. Correctness of the guessed password must be verified by the responses sent from the correspondent. New transaction with the same correspondent will be initiated, provided that his guess fails. Failed guess is undetectable by the correspondent.
(iii) Off-line password guessing attacks: An adversary can guess user’s password with eavesdropped or collected authentication messages in off-line manner. The adversary can freely guess user’s password and check its correctness without being detected.
In 1992, Bellovin and Merritt [1] combined a symmetric and a asymmetric cryptographic techniques to pro-pose a well-known encrypted key exchange (EKE) protocol against off-line password guessing attack. Since then, much research on EKE using different types of public key cryptosystems (e.g. RSA, ElGamal, and Diffie-Hellman key exchange) has been investigated [3, 4, 5]. It can be seen that these schemes are unsuitable for im-balanced wireless network from above performance perspective. In 2002, Zhu et al. [14] proposed a password based authenticated key exchange protocol based on RSA [9]. They claimed that their protocol can be imple-mented efficiently on most of the lightweight devices in wireless networks. However, Yeh et al. [11] latter dem-onstrated an undetectable on-line password guessing attacks on Zhu et al.’s protocol and proposed an improve-ment to eliminate this security flaw. Yeh et al. claimed that their protocol not only withstands undetectable on-line password guessing attack, but also provides explicit key authentication. Recently, Yoon and Yoo [12], Yang and Wang [10], and Zhang [13] demonstrated an off-line password guessing attack on Yeh et al.’s protocol to show the claimed requirement is violated. This paper will propose a new efficient password authenticated key exchange protocol for imbalanced wireless networks to eliminate the security flaw and gain better performance in terms of computational complexities, communication overheads, transmission number, and required storage.
The remainder of this paper is organized as follows. In Section 2, we give a brief review of Yeh et al.’s proto-col [11] and discuss its security. In Section 3, we will propose our password authenticated key exchange protoproto-col. In Section 4, we give security analyses and performance evaluations. Finally, we give the conclusions.
2 Brief Review of Yeh et al.’s Protocol
In this section, we will give a brief review of Yeh et al.’s protocol [11] and an off-line password guessing attack on Yeh et al.’s protocol.
2.1 Yeh et al.’s Protocol
There are two participants involved in Yeh et al.’s protocol [11]: a client B and a server A. The client B is a low-power device (e.g. PDA, handset, etc.) and the server is low-powerful in the imbalanced wireless networks. A and B share a password pw in advance. Let h1, h2, h3, and h4 be distinct cryptographic one-way hash functions and Ek(M)/Dk(C) be a symmetric encryption/decryption of the plaintext M/the ciphertext C under the secret key k. A and B cooperatively perform the following steps for entity mutual authentication with key exchange:
Step 1. The client B sends a service request to server A.
Step 2. The server A generates a RSA public key (n, e) and private key d by using a public key generator, where n is the product of two large secret primes and ed = 1 (mod φ(n)).
Step 3. A randomly chooses an integer rA ∈ R{0, 1}l and sends (rA, n, e) to the client B, where l is a set of all length l bits binary string.
Step 4. Upon receiving (rA, n, e) from A, B performs an interactive protocol to verify the validity of A’s public key (n, e). If the public key is invalid, B terminates this protocol. Otherwise, B chooses a random integer rB ∈R Z n, computes
π = Epw(IDA, IDB, rA, rB) (1)
z = πe mod n (2)
and sends z back to the server A. Step 5. A computes π = zd mod n (3) (IDA, IDB, rA, rB) = Dpw(π) (4) Step 6. A computes cB = h2 (rB) (5) K = h3 (rA, cB, IDA, IDB) (6)
σ = EK(IDB) (7)
and sends σ to the client B. Note that K is regarded as the secret session key shared between A and B. Step 7. B uses his chosen random integer rB to compute cB' and K' by Eqs. (5) and (6), respectively. B decrypts
the received σ to obtain IDB' with the session key K'. If IDB' ≠ IDB, B terminates this protocol. Other-wise, B computes δ = h4(K) and sends it back to the server A.
Step 8. A computes δ' = h4(K) and checks if δ' is equal to the received δ. If it does not hold, A terminates this protocol. Otherwise, A accepts the connection.
Client B Server A Request (n, e, rA) rA ∈ R{0, 1}l {mi ∈ R Zn}1≤i≤N Check if h1(mi') = h1(mi) {mie mod n}1≤i≤N {h1(mi')} 1≤i≤N rB ∈R Z n π = Epw(IDA, IDB, rA, rB) z = πe mod n z σ π = zd mod n (IDA, IDB, rA, rB) = Dpw(π) cB = h2 (rB) K = h3 (rA, cB, IDA, IDB) σ = EK (IDB) cB' = h2 (rB) K' = h3 (rA, cB', IDA, IDB) IDB' = DK'(σ) Check if IDB' = IDB δ = h4(K) δ δ' = h4(K) Check if δ' = δ
Fig. 1. Yeh et al.’s Protocol [11]
2.2 Discussions on Yeh et al.’s Protocol
In 2005, several scholars proposed an off-line password guessing attack on Yeh et al.’s protocol [11]. That is, an adversary can masquerade as a server A to obtain some authentication messages from the client, and then freely guess the client’s password. Details of this attack are described below.
Step 1. The client B sends a service request to server A.
Step 2. The adversary F generates RSA private and public keys as d and (n, e) such that ed = 1(mod φ(n)), re-spectively.
Step 3. The adversary F randomly chooses an integer rF ∈ R{0, 1}l and sends (rF, n, e) to the client B.
Step 4. The client B performs an interactive protocol to verify the validity of A’s public key (n, e). If the public key is invalid, B terminates this protocol. Otherwise, B computes π and z by Eqs. (1) and (2), respec-tively, and then transmits z back to the adversary F.
Step 5. On receiving z, the adversary F computes π by Eq. (3) and terminates this protocol.
Step 6. With the knowledge of π, the adversary guesses the client’s password pw', decrypts π with pw', and checks if (IDA, IDB, rA) can be correctly recovered. The adversary can repeat Step 6 to guess the client’s password until correct identities are recovered. That implies the guessed password is genuine.
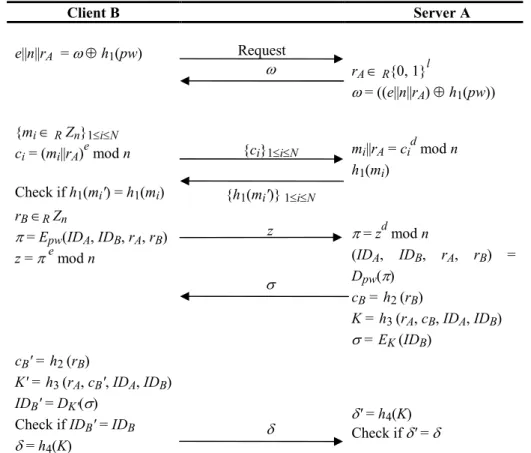
To eliminate above attack, Yang and Wang [10] modify the interactive protocol of Yeh et al.’s protocol [11]. Figure 2 illustrates Yang and Wang’s improvement. Since Steps 5 to 8 of Yang and Wang’s improvement are the same as those of Yeh et al.’s protocol, we only describe the remaining steps below.
Step 1. The client B sends a service request to A.
Step 2. The server A generates a RSA public key (n, e) and private key d.
Step 3. A randomly chooses an integer rA ∈ R{0, 1}l, computes ω = ((e||n||rA)⊕h1(pw)) to the client B, where the symbol “||” denotes the concatenation of binary string.
Step 4. The client B uses his password pw to recover (e, n, rA) by ω ⊕ h1(pw), picks N integers mi in Zn for 1 ≤ i ≤ N, and then cooperates with A to perform the following sub-steps:
Step 4.1 B computes ci = (mi||rA)e mod n (for 1 ≤ i ≤ N) and sends it to A. Step 4.2 A derives mi||rA by computing cid, and sends h1(mi) back to B. Step 4.3 B computes h1(mi) and checks if it is equal to the received h1(mi).
Client B Server A e||n||rA = ω ⊕ h1(pw) Request ω rA ∈ R{0, 1}l ω = ((e||n||rA) ⊕ h1(pw)) {mi ∈ R Zn}1≤i≤N ci = (mi||rA)e mod n Check if h1(mi') = h1(mi) {ci}1≤i≤N {h1(mi')} 1≤i≤N mi||rA = cid mod n h1(mi) rB ∈R Zn π = Epw(IDA, IDB, rA, rB) z = πe mod n z σ π = zd mod n (IDA, IDB, rA, rB) = Dpw(π) cB = h2 (rB) K = h3 (rA, cB, IDA, IDB) σ = EK (IDB) cB' = h2 (rB) K' = h3 (rA, cB', IDA, IDB) IDB' = DK'(σ) Check if IDB' = IDB δ = h4(K) δ δ' = h4(K) Check if δ' = δ
Fig. 2. Yang and Wang’s Improved Protocol [11]
3 The Proposed Protocol
In the proposed protocol, we only use one one-way hash function h instead of four ones in Yeh et al.’s protocol. The symbols Ek(M) and Dk(C) are defined as a symmetric encryption and a decryption algorithms as those men-tioned above. The server A and the client B also share the same password pw in advance. A and B cooperatively perform the following steps for entity authentication with key exchange as shown in Figure 3:
Step 1. The client B sends a service request to server A.
Step 2. The server A generates a RSA public key (n, e) and private key d by using a public key generator, where n is the product of two large secret primes and ed = 1 (mod φ(n)).
Step 3. A randomly chooses an integer rA ∈R Z n, computes
Step 4. Upon receiving π from A, B decrypts π as
rA||n||e = Dpw(π) (9)
Step 5. A and B cooperatively perform an interactive protocol to verify the validity of A’s public key (n, e). If the public key is invalid, B terminates this protocol.
Step 6. B randomly chooses an integer rB ∈R Z n, computes
z = (rB ⊕ pw ⊕ rA)e mod n (10)
K = rA ⊕ rB ⊕ (IDA||IDB) (11)
σ = h(rA||rB||IDA||IDB||K) (12)
and sends (σ, z) back to the server A. Note that K is the session key shared between A and B. Step 7. A decrypts the received z with his private key d, the password pw, and his chosen number rA by
rB' = (zd mod n) ⊕ pw ⊕ rA (13)
Step 8. A further derives the shared session key K' as
K' = rA ⊕ rB' ⊕ (IDA||IDB) (14) and checks the following equality
σ = h(rA||rB'||IDA||IDB||K') (15)
If it holds, legitimacy of the client B and the authenticity of the established session key K' are verified. Step 9. A computes the following message for key confirmation as
δ = h(K') (16)
and sends it to the client B.
Step 10. On receiving the message δ, B checks its validity by Eq. (16). If above equality holds, B is convinced of the session key K and the legitimacy of the server A.
Client B Server A rA||n||e = Dpw(π) {mi ∈ R Zn}1≤i≤N Request π rA ∈ R{0, 1} l π = Epw(rA||n||e) Check if h(mi') = h(mi) {mie mod n}1≤i≤N {h(mi')} 1≤i≤N rB ∈R Zn z = (rB ⊕ pw ⊕ rA)e mod n K = rA ⊕ rB⊕(IDA||IDB) σ = h(rA||rB||IDA||IDB||K) Check if δ = h(K) σ, z δ rB' = (zd mod n) ⊕ pw ⊕ rA K' = rA⊕rB' ⊕ (IDA||IDB)
Check if σ = h(rA||rB'||IDA||IDB||K')
δ = h(K')
Fig. 3. The Proposed Protocol
4 Security Analyses and Performance Evaluations
In the following, we first analyze the security of our protocol and then give the performance evaluations in Sub-section 4.1 and 4.2, respectively.
4.1 Security Analyses
We analyze the security of the proposed protocol from the following security considerations and show that it is secure against some attacks below.
Considerations to on-line password guessing attack – Consider the scenario that the adversary F attempts to compromise the password pw by interacting with the server A or the client B. First, if the adversary masquerade as the server A, he can guess the password pw', compute π' by Eq. (8), and then send π' to the client B. B can derive (rA', n', e') by Eq. (9) using the genuine password pw. F then cooperates with B to perform an interactive protocol as that in Yeh et al.’s protocol. The adversary F, however, cannot response a valid h(mi) to B without knowing d' such that e'd' = 1 (mod φ(n')) if pw' ≠ pw. Hence, this attack will be detected by the client. Second, if the adversary F masquerades as the client B, then he can guess a password pw' to decrypt π sent from B to obtain (rA', n', e') by Eq. (9). However, the server is able to detect the on-line password guessing attack by checking message mie' mod n' sent from the adversary if pw' ≠ pw. Therefore, the proposed protocol is secure against the on-line password guessing attack.
Considerations to off-line password guessing attack – There are two possible attacks plotted by the adversary F. In the first case, F can first intercept all communication between A and B, and then use it to guess the pass-word pw by himself. It can be seen that π and z are computed from the password pw. With the knowledge of the intercepted π, the adversary cannot guess the password and check its correctness by Eq. (8) since he cannot de-rive the secret random integer rA from other intercepted messages. If the adversary F attempts to guess the pass-word pw by using z, he must derive the random numbers rA and rB in advance. We can see that rB is protected by RSA encryption and rA by the symmetric encryption under the password. The second case is similar to the off-line password guessing attack as mentioned in Subsection 2.2. It can be seen that pw is only known to the server A and client B. This attack will be detected by A or B as shown in the analysis of on-line password guessing attack before the adversary attempts to replace (n', e') with (n, e).
Considerations to session key compromising – If the adversary F attempts to compromise K by using the in-tercepted σ or δ, he will face the intractability of reversing the one-way hash function h. On the other hand, it can seen that the session key is derived as K = rA ⊕ rB ⊕ (IDA||IDB) from Eq. (11). If the adversary F attempts to compromise K directly by Eq. (11), he must obtain two secret random number rA and rB in advance. However, rA and rB will not be revealed to F, and the session key K will not be compromised.
Considerations to replay attacks – Suppose all random numbers cannot be used twice in our protocol. Con-sider the scenario that the adversary F attempts to plot the impersonation attack by replaying his intercepted mes-sages. If the adversary F replays the intercepted π to B, he will receive mie mod n from B where mi is randomly chosen by B. The adversary cannot response a valid h(mi') to B without knowing the private key d. Moreover, the adversary F cannot plot a replay attack by masquerading as the client B due to the random number rA chosen by the server A.
Considerations to mutual authentication – In the proposed protocol, the authentication is performed twice. The first one is considered in the steps 1 to 5 of our protocol, the server A and the client B will be authenticated to each other by the shared password. The second one is considered in the steps 6 to 10. The client B randomly chooses a number rB and generates a valid (σ, z) by using (rB, rA, pw, e, n) to the server A. If A can derive cor-rect rB and K to pass Eq. (15), he will be convinced of B’s legitimacy. If A can response a valid δ to B to pass Eq. (16), B is convinced of A’s legitimacy. Hence, the proposed protocol achieves mutual authentication.
Considerations to key establishment and confirmation – We can see that the random number rA and rB are only known to A and B. If mutual authentication is achieved as mentioned above, rA and rB are verified. Hence, both A and B establish a secret session key shared between them by Eqs. (11) and (14). Moreover, if the message (σ, z) passes the verification Eq. (15), A is convinced of that B knows the key K. B is also convinced of that A knows the session K if Eq. (16) holds. Hence, the proposed protocol achieves key establishment and confirmation.
4.2 Performance Evaluations
Let Th, TE, and Texp be the time for executing a one-way hash function, a symmetric encryption/decryption, and a modular exponentiation, respectively. Since the time for executing an exclusive OR operation is negligible for the comparison, we ignore it here. Let |ε|, |n|, and |h| be the bit-length of a ciphertext, a modular n, and an output of a one-way hash function, respectively.
From Tables 1, 2, and 3, it is easy to see the performance of the proposed protocol is better than that of the other protocols [10, 11, 14]. In addition, the proposed protocol uses only one one-way hash function, instead of four ones. Required storage of the proposed protocol is less than that of others and hence suitable for resource-limited mobile devices.
Table 1. Comparisons of Computational Complexities
Protocol Client Server Total
Zhu et al.’s
Protocol [14] (N+5)Th + TE + (N+1)Texp (N+5)Th + TE + (N+1)Texp
(2N+10)Th + 2TE + (2N+2)Texp
Yeh et al.’s
Protocol [11] (N+3)Th +2TE+ (N+1)Texp (N+3)Th + 2TE + (N+1)Texp (2N+6)Th + 4TE + (2N+2)Texp Yang-Wang Protocol [10] (N+4)Th + 2TE + (N+1)Texp (N+4)Th + 2TE + (N+1)Texp (2N+8)Th + 4TE + (2N+2)Texp The Proposed
Protocol (N+2)Th + TE + (N+1)Texp (N+2)Th + TE + (N+1)Texp (2N+4)Th + 2TE + (2N+2)Texp
Table 2. Comparisons of Communication Costs
Protocol Communication Costs
Zhu et al.’s Protocol [14] |ε| + (N+5)|n| + (N+1)|h|
Yeh et al.’s Protocol [11] |ε| + (N+5)|n| + (N+1)|h|
Yang-Wang Protocol [10] |ε| + (N+5)|n| + (N+1)|h|
The Proposed Protocol |ε| + (N+1)|n| + (N+2)|h|
Table 3. Comparisons of the Number of Transmissions
Protocol Client Server Total
Zhu et al.’s Protocol [14] 3 3 6
Yeh et al.’s Protocol [11] 3 3 6
Yang-Wang Protocol [10] 3 3 6
The Proposed Protocol 2 3 5
Notice: The request transmission is excluded in the comparisons.
5 Conclusion
We have proposed a new efficient password authenticated key exchange protocol for imbalanced wireless net-works. From security perspective, the proposed protocol is secure against on-line/off-line password guessing, replay, impersonation attacks. It is more secure than Zhu et al.’s and Yeh et al.’s protocols [11, 14]. Performance of the proposed protocol is also better than that of Zhu et al.’s, Yeh et al.’s, and Yang and Wang’s protocols [10, 11, 14] in terms of computational complexities, communication costs, transmission number, and required storage.
Acknowledgement
This work was supported in part by Taiwan Information Security Center (TWISC), National Science Council under the grants NSC 95-2218-E-001-001, NSC95-2218-E-011-015, and NSC94-2213-E-182-019.
References
[1] S.M. Bellovin, M. Merrit, "Encrypted key exchange: password-based protocols secure against dictionary attacks," Proceedings of 1992 IEEE Computer Society Symposium on Research in Security and Privacy, pp. 72-84, 1992.
[2] Y. Ding, P. Horster, "Undetectable on-line password guessing attacks," ACM Operating Systems Review, Vol. 29, No. 4, pp. 77-86, 1995.
[3] W. Diffie, M. Hellman, "New directions in cryptography," IEEE Transactions on Information Theory, Vol. IT-22, No. 6, pp. 644-654, 1976.
[4] D. Jablon, "Strong password-only authenticated key exchange," ACM Computer Communications Review, Vol. 20, No. 5, pp. 5-26, 1996.
[5] T. Kwon, J. song, "Efficient key exchange and authentication protocol protecting weak secrets," IEICE Transactions on Fundamental, Vol. E81-A, No. 1, pp. 97-111, 1998.
[6] C.L. Lin, H.M. Sun, T.Hwang, "Three-party encrypted key exchange:attacks and a solution," ACM Operat-ing Systems Review, Vol. 34, No. 4, pp. 12-20, 2000.
[7] C.L. Lin, H.M. Sun, M. Steiner, T. Hwang, "Three-party encrypted key exchange without public-keys," IEEE Communications Letters, Vol. 5, No. 12, pp. 497-499, 2001.
[8] B.C. Neuman, T. Ts’o’, "Kerberos:an authentication service for computer networks," IEEE Communica-tions Magazine, Vol. 32, No. 9, pp. 33-38, 1994.
[9] R.L. Rivest, A. Shamir, L. Adelman, "A method for obtaining digital signature and public key cryptosys-tem," Communications of ACM, Vol. 21, No. 2, pp. 120-126, 1978.
[10] C.C. Yang, R.C. Wang, "Cryptanalysis of improvement of password authenticated key exchange based on RSA for imbalanced wireless networks," IEICE Transactions on Communications, Vol. E88-B, No. 11, pp. 4370-4372, 2005.
[11] H.T. Yeh, H.M. Sun, C.T. Yang, B.C. Chen, S.M. Tseng, "Improvement of password authenticated key exchange based on RSA for imbalanced wireless networks," IEICE Transactions on Communications, Vol. E86-B, No. 11, pp. 3278-3282, 2003.
[12] E.J. Yoon, K.Y. Yoo, "Cryptanalysis of password authenticated key exchange based on RSA for imbalanced wireless networks," IEICE Transactions on Communications, Vol. E88-B, No. 6, pp. 2627-2628, 2005. [13] M. Zhang, "Breaking an improved password authenticated key exchange based on RSA for imbalanced
wire-less networks," IEEE Communications Letters, Vol. 9, No. 3, pp. 276-278, 2005.
[14] F. Zhu, D.S. Wong, A.H. Chan, R. Ye, "Password authenticated key exchange based on RSA for imbalanced wireless networks," Proceedings of ISC 2002, LNCS 2433, pp. 150-161, 2002.
![Fig. 1. Yeh et al.’s Protocol [11]](https://thumb-ap.123doks.com/thumbv2/9libinfo/8816173.230092/3.892.208.724.298.739/fig-yeh-et-al-s-protocol.webp)