國立交通大學
電機資訊國際學位學程
碩士論文
異質網絡中的一個新的換手必要性估計方法
A new handover necessity estimation approach
in heterogeneous networks
Student: Maxence Gorde
Advisor: Ching-Yao Huang
異質網絡中的一個新的換手必要性估計方法
A new handover necessity estimation approach
in heterogeneous networks
研究生:高旻頌
Student: Maxence Gorde
指導教授:黃經堯
Advisor: Ching-Yao Huang
國 立 交 通 大 學
電機資訊國際學位學程
碩士論文
A Thesis
Submitted to EECS International Program
National Chiao Tung University
In partial fulfillment of the Requirements
For the degree of
Master
November 2013
Hsinchu, Taiwan, Republic of China
中華民國一百二年十一月
異質網絡中的一個新的換手必要性估計方法
學生: 高旻頌
指導教授: 黃經堯 教授
國立交通大學 電子研究所
摘要
由於在過去幾年間,移動寬頻接取的需求猛增,異質網路已被視為未來數年的領導 網路設計結構。用戶使用移動服務的方式發生了巨大變化,在人口密集的城市地區, 現有的室外網絡可能不足以處理所有的流量需求。對應這些新的市場需求,異質網 路似乎是一個聰明的部署策略,尤其是在人口密集的城市地區。它們包括在同一個 網路結構中,使用不同的無線接入技術和無線區域網路,並要滿足品質,彈性和精 確度的要求。 然而,異質網路中,在同一時間有眾多的無線電發送信號。此特性導出了一個議題, 即行動裝置在不同特性的蜂巢之間進行換手。許多換手協定已實現,使行動裝置始 終連接到目前提供最好的服務質量的蜂巢。 反之,在這篇論文中,我們提出研究換手的必要性評估的協議,這意味著能夠藉由 實時量測網路參數,來評估換手的必要性。 我們的換手必要性評估演算法,需要知 道行動裝置已滯留在候選網路覆蓋範圍內時間。我們的貢獻是對於滯留時間的估計, 這可能會導致許多優點。透過模擬,我們已量化這個解決方案的性能,了解其潛在 的影響或潛在部署。 關鍵詞:異質網路、資料市場、寬頻接取、換手必要性評估A new handover necessity estimation approach
in heterogeneous networks
Student: Maxence Gorde
Advisor: Pr. Ching-Yao Huang
EECS International Graduate Program
National Chiao Tung University
ABSTRACT
Heterogeneous networks (HetNets) are bound to become the leading network design structure for the coming years, since the demand for mobile broadband access started to explode a few years ago, and will continue to do so within the next few years. In addition, the way users consume those mobile services has drastically changed. As a result, the existing outdoor networks that rely on macro cells might not be sufficient to deal with all the traffic demand, especially in dense urban areas. In response to these new market needs, heterogeneous network appear to be a clever deployment strategy. They consist in using Radio Access Technologies (RATs) and Wi-Fi in the same network structure, in order to meet quality, flexibility and precision requirements.
However, HetNets generate numerous radio transmission signals at the same time. This disparity creates issues regarding the handovering process of a mobile device among cells that do not share the same characteristics. Numerous handover protocols have been implemented in order to make the device be always connected to the cell that is currently providing the best Quality of Service (QoS).
Instead, we propose in this thesis to study handover necessity estimation (HNE) protocols, which means being able of measuring the need for a handover by evaluating network parameters in real time. The algorithms we performed for HNE need to use the time the mobile device has been spending within the candidate network coverage. Our contribution has been to use an estimation of this time, which may lead to numerous advantages. Simulations have been made to quantify the performance of this solution and see their potential impacts and deployment potential.
Table of contents
Table of contents ... iii
Tables ... v
Figures ... v
List of acronyms ... vi
I. Introduction ... 1
1.1 Background ... 1
1.2 Problem statement ... 2
1.3 Aim of the thesis ... 3
1.4 Structure of the thesis ... 3
II. Mobile broadband evolution ... 4
2.1 Mobile data traffic growth ... 4
2.2 Behavior evolution in data consumption ... 10
III. Heterogeneous networks ... 11
3.1 Presentation ... 11
3.2 Benefits ... 14
3.2.1 Mobile operator benefits ... 14
3.2.2 User benefits ... 16
3.3 Architecture ... 16
3.4 Wi-‐Fi ... 18
3.4.1 Presentation ... 18
3.4.2 Spectrum management ... 19
3.4.3 Advantages and limitations ... 19
3.4.4 Security ... 19
3.5 Femtocells ... 20
3.5.1 Presentation ... 20
3.5.2 Access management ... 20
3.5.3 Interference management ... 21
3.5.4 Advantages and limitations ... 22
3.6 Handover issue ... 23
IV. Handover protocols ... 24
4.1 Presentation ... 24
4.2 Vertical handovers ... 25
4.3 Vertical handover classification ... 26
4.6 Handover failure protocol ... 31
4.7 Unnecessary handover protocol ... 33
4.8 Simulations ... 34
4.9 Results ... 36
V. Conclusion ... 39
References ... 40
Tables
Table 1 – Global Internet traffic growth from 1997 to 2001 -‐ 5 -‐ Table 2 – Global mobile data traffic growth from 2008 to 2012 -‐ 5 -‐ Table 3 – Vertical handover groups’ assets and liabilities -‐ 28 -‐
Figures
Figure 1 – Global mobile data traffic forecasts from 2012 to 2017 -‐ 6 -‐ Figure 2 – Mobile data traffic distribution over different kind of devices -‐ 7 -‐ Figure 3 – Global mobile devices and connections growth -‐ 8 -‐ Figure 4 – Mobile cloud traffic growth from 2012 to 2017 -‐ 9 -‐ Figure 5 – Alternatives to improve current networks performances -‐ 12 -‐ Figure 6 – Heterogeneous network diagram -‐ 14 -‐ Figure 7 – Main reasons leading to churn (customers moving from one operator to another one) -‐ 15 -‐ Figure 8 – Wi-‐Fi channel allocation and channel overlap -‐ 19 -‐ Figure 9 – Vertical and horizontal handover protocols -‐ 24 -‐ Figure 10 – Handover necessity estimation system architecture -‐ 29 -‐ Figure 11 – WLAN to cellular network HNE scheme -‐ 35 -‐ Figure 12 – Number of handover failures of fixed RSS, hysteresis based, and HNE methods regarding the velocity of the mobile device -‐ 37 -‐ Figure 13 – Number of unnecessary handovers of fixed RSS, hysteresis based, and HNE methods regarding the velocity of the mobile device -‐ 37 -‐
List of acronyms
2G 2nd Generation
3G 3rd Generation
3GPP 3rd Generation Partnership Project
4G 4th Generation
ABC Always Best Connected
ARPU Average Revenue per User
BPSK Binary Phase Shift Keying
CAGR Compound Annual Growth Rate
CAPEX Capital Expenditure
COMP Base Station Cooperative Multipoint
CSG Closed Subscriber Group
DSL Digital Subscriber Line
DSP Digital Processing Schemes
GSM Global System for Mobile Communications
HetNet Heterogeneous Network
HNE Handover necessity Estimation
HSPA High Speed Packet Access
HTTPs Hypertext Transfer Protocol Secure
IEEE Institute of Electrical and Electronics Engineers
LTE Long Term Evolution
M2M Machine to Machine
MAC Medium Access Control
MIMO Multiple Input Multiple Output
MMS Multimedia Messaging Service
MNO Mobile Network Operators
OFDM Orthogonal Frequency Division Multiplexing
OPEX Operational Expenditure
OSG Open Subscriber Group
PHY Physical Layer
QAM Quadrature Amplitude Modulation
QoS Quality of Service
QPSK Quadrature Phase Shift Keying
RSS Received Signal Strength
SIM Subscriber Identity Module
SMS Short Message Service
TLS Transport Layer Security
UMTS Universal Mobile Telecommunications System
VPN Virtual Private Network
WEP Wired Equivalent Privacy
WLAN Wireless Local Area Network
I. Introduction
1.1 BackgroundMobile communication networks are currently faced to new challenges since the demand for mobile broadband access and data traffic exploded over the last few years. This situation is mainly due to data consumer devices, such as smartphones, that were first released in 2007.
Voice traffic used to dominate mobile network traffic volume until data traffic overtook voice in around 2010. The consumer habits in terms of mobile services use changed drastically as smartphones became more and more popular. The capabilities of those devices in addition to mobile applications and laptops connected to mobile networks create huge amounts of transmitted data, and traffic forecasts predict that this traffic explosion will keep on increasing. Also, the way users consume mobile services has also been considerably modified, as the majority of smartphones are used while people are at the office or at home [1]. Therefore, more than 60% of the mobile data traffic is now generated within “private” areas [2]. Mobile operators have noticed that in dense urban areas, the existing outdoor networks might not be sufficient to deal with all the traffic demand. So, they are now faced to new challenges for achieving sufficient coverage, capacity and quality targets.
The current mobile networks that we are used to rely on do not suit with the change of habits in mobile data consumption. Networks need nowadays to be more accurate on where are located the data transmission needs, which keep on increasing. Large network coverage might not meet requirements in terms of quality in the future, as people consume more and more mobile data in restricted areas. Network coverage might have to focus on providing high data transmission rates in specific places where people tend to gather and demand mobile access.
In response to the growing demand for affordable mobile broadband connectivity, a very interesting solution for the evolution of radio access networks is heterogeneous networks (HetNets). As a deployment strategy, especially in dense urban areas, they might be a
clever choice for mobile operators. It consists in using all at once different Radio Access Technologies (RATs) and Wi-Fi in the same network structure.
Customer satisfaction depends on good coverage and capacity in a lower churn rate [3]. If mobile operators reduce the load of data in indoors areas, they will be able to keep on offer quality services, no matter the ever-increasing traffic. Moreover, operators could provide value-added services and applications using this solution. Indeed, they can improve user’s utility and thus the average revenue per user (ARPU). The mobile operator benefits also rely on capital expenditure (CAPEX) and operational expenditures (OPEX) reduction, which may have impact on pricing. So, HetNets appear to be a win-win solution if used in a deployment strategy.
Many technologies are available for HetNets deployment. Operators already provide wide-area GSM coverage and HSPA in densely populated urban wide-areas. They now want to deploy small cells to support the macro layer and increase network capacity when required. Many networks will include an overlay of cells of different sizes. For instance, outdoor terminals may be served by a combination of macro, micro and pico cells. All together, they will complement the fixed wide area networks and support traffic.
1.2 Problem statement
One critical issue that has to be dealt with in HetNets is handover. Indeed, HetNets consist of multiple cells which might have different characteristics. As a result, they generate at the same time numerous radio transmission signals relying on different transmission protocols, transmitted power, and cell coverage, both for uplink and down link. As a result, they create a radio mist where different radio signals representing different. The handover of a wireless mobile device among this radio mist need to be sensitive to all types of connection powers and be able to choose in real time the most efficient one. Numerous handover protocols have been implemented and tested for allowing the device to be always connected to the cell currently providing the best QoS.
However, even if handovers protocols are nowadays quite effective, there is still some liabilities regarding the fact of being able to know whereas or not some handovers are really needed or should be avoided regarding various network parameters. There is
wide-measuring the need for a handover by evaluating network parameters in real time. Indeed, unnecessary handovers or handovers that are bound to fail when performed are the cause of a waste of time, energy, money, and has an impact on the provided QoS. Thus, reducing the amount of failed and unnecessary handovers may lead to a better throughput and improve the user experience by estimating of the need of a handover between cellular networks and WLANs.
1.3 Aim of the thesis
The aim of this thesis is to carry out a qualitative analysis of heterogeneous networks in order to have a better understanding of this innovative and on the rise network solution. Firstly we will see the evolution of the mobile broadband market and highlight some trends in the market thanks to technology comparisons and real case examples. Then we will have a detailed presentation of heterogeneous networks, their structure, their technologies, strengths and weaknesses. Following that, we will focus the handover issue and how performing handover in heterogeneous networks might be improved using handover necessity estimation patterns.
To sum up in one question, the aim of the thesis may be explained as follows: Considering the even increasing heterogeneous networks deployments to make up for the ongoing growth of mobile data traffic, how the handover operation of a mobile device connected to such networks might be improved using handover necessity estimation protocols that rely on a real time network parameters analysis?
1.4 Structure of the thesis
The chapter 2 of the thesis is an analysis of mobile broadband traffic evolution over the last decade. It aims to understand how mobile traffic has so far changed, and also to try to make some forecasts about mobile traffic evolution within the next few years. Following that, chapter 3 introduces us with the notion of heterogeneous networks and how it represents an interesting alternative to make up for current macro cells networks liabilities. Chapter 3 also analyses in more detail heterogonous networks architecture and some of its most popular used technologies. Then it tackles the handover issue created by the co-existence of current networks with heterogeneous ones. To deal with this issue, chapter 4 explains the importance of avoiding unnecessary or failed handovers that would result in a waste of time, energy, money and damage the consumer perception about the quality of service. Following that, chapter 4 presents some handover failure or necessity estimation
protocols. The new feature of this thesis is to use the estimated travelling time of a mobile device through a given cell and use it in such handover necessity estimation protocols. It aims to give these protocols more flexibility, time-responsiveness, and reduce latency. Then chapter 4 goes through some simulations of these handover necessity estimation protocols using estimated travelling time to determine how these methods might improve the network quality of service and performance by eliminate unnecessary handovers. The results of those simulations are then analyzed and interpreted to compare the handover efficiency with and without such protocols. It leads to a clear assessment of the handover necessity estimation protocols overall performances and helps to figure out their deployment potential.
II. Mobile broadband evolution
2.1 Mobile data traffic growthMobile traffic is globally soaring, and its rate of growth is accelerating, due to the ever-increasing number of data consumer devices, such as smartphones and tablets. The average data use of those mobile users is also rising. Average smartphone usage grew 81 percent in 2012. The average amount of traffic per smartphone in 2012 was 342 MB per month, up from 189 MB per month in 2011, according to the Cisco Visual Networking Index, 2013 (VNI). The heavy investments in new technologies – 4G (fourth generation), LTE (Long Term Evolution) – will not provide immediate network capacity, since the terminal market is still dominated by 3G devices.
We can see on the two tables below the global Internet traffic growth from 1997 to 2001 and the global mobile data traffic growth from 2008 to 2012. We observe that the growth figures are close, so the analysts might use this pattern to make some reliable forecasts for the coming years.
Table 1: Global Internet traffic growth from 1997 to 2001 1997 178% 1998 124% 1999 128% 2000 195% 2001 133%
Source: Cisco, VNI mobile, 2013.
Table 2: Global mobile data traffic growth from 2008 to 2012
2008 156%
2009 140%
2010 159%
2011 115%
2012 70%
Source: Cisco, VNI mobile, 2013.
The number of powerful smartphones and tablets will increase exponentially, resulting in more mobile data consumption. This will require a major development in mobile cloud computing, as most of the traffic will result in cloud-based services. In the Cisco VNI: Global Mobile Data Traffic Forecast Update 2012-2017, there are clear indications of an explosion in mobile data traffic:
- Global mobile data traffic will increase 13 fold between 2012 and 2017. Mobile data traffic will grow at a compound annual growth rate (CAGR) of 66 percent from 2012 to 2017, reaching 11.2 exabytes per month by 2017.
- Smartphones represented only 18 percent of total global handsets in use in 2012, but represented 92 percent of total global handset traffic
- In 2012, the number of mobile-connected tablets increased 2.5 fold to 36 million, and each tablet generated 2.4 times more traffic than the average smartphone. - IPhone and Android platforms generate most of the smartphone data use, but
Android is now higher than iPhone.
- We expect mobile data traffic to increase by 13 times between 2012 and 2017. - Two-thirds of the world's mobile data traffic will be video by 2017.
- The second largest segment is mobile Web/Data. These two sources will be responsible for almost 90% of the total mobile data traffic.
- There will be 788 million mobile-only Internet users by 2015.
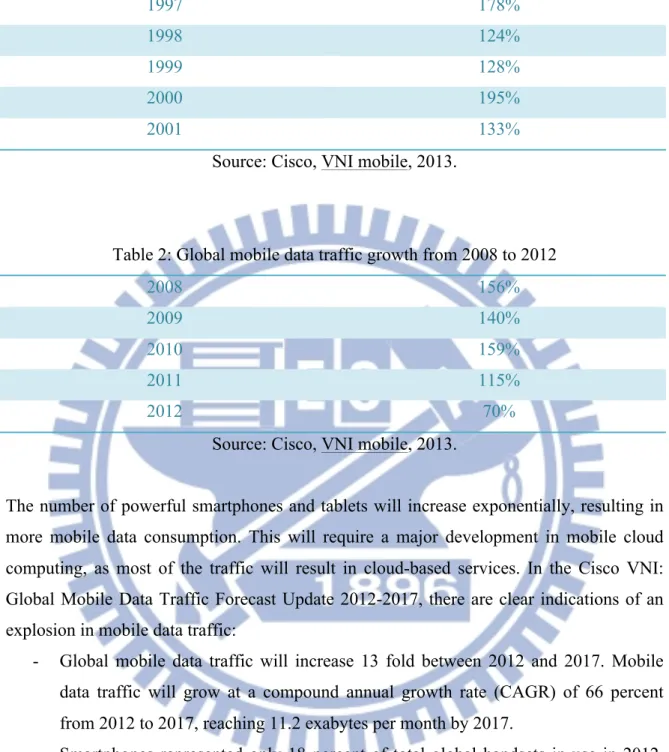
On the graph below, we can see the expectation of mobile data traffic within 2017.
Figure 1: Global mobile data traffic forecasts from 2012 to 2017 Source: Cisco, VNI mobile, 2013.
These figures highlight the fact that users have changed their way to use mobile services, and that the use of the Internet tends to be more and more a mobile use rather than a fixed one. Also, new powerful devices and new services will continue to push users to consume more and more data with their mobile devices. As we said it before, data consumption through mobile networks started when smartphones were released. These new devices provided a new generation interface and the access to mobile services and features that used to be available only at home. However, it is important to say that the nature of a device is deeply related to its data consumption. For example, the smart tablets have a screen resolution much higher than usual smart phones, so they need to receive much more data from the network in order to make up for this additional information need.
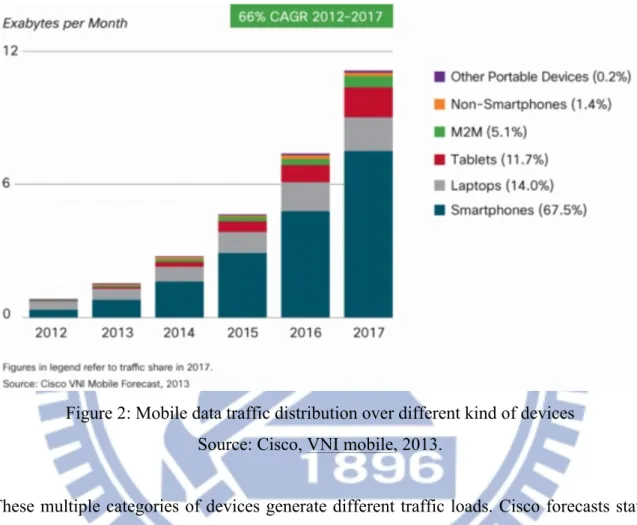
The devices responsible for this traffic are widely diversifying. Traffic from smartphones is going to exceed traffic from laptops, which have been by far the main driver of mobile data traffic for years. The following graph gives some estimation about how data traffic data traffic will be distributed among devices within 2017.
Figure 2: Mobile data traffic distribution over different kind of devices Source: Cisco, VNI mobile, 2013.
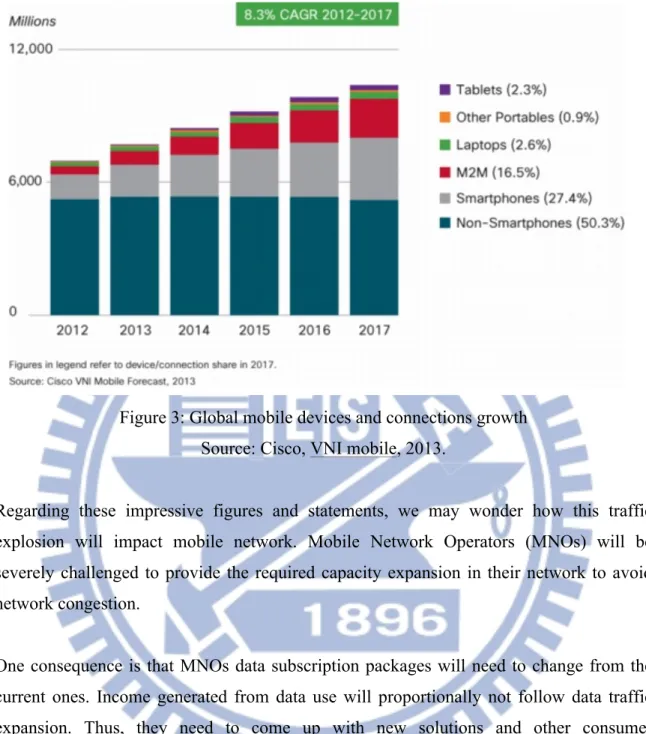
These multiple categories of devices generate different traffic loads. Cisco forecasts state that smartphones will be responsible for just over 67% of all global mobile data traffic in 2017. Laptops will have dropped to 14% of the traffic in 2017, as they generated 45% of the data traffic in 2012. Tablets will have risen to almost 12%. And even if non-smartphones will be by far the most numerous existing devices, they will generate just 1.4% of all mobile traffic in five years. Indeed, if we compare the mobile data traffic distribution over different kind of devices to the number of devices connected (see on the following figure), we notice that the most numerous connected devices are not the ones responsible for the majority of traffic loads.
Figure 3: Global mobile devices and connections growth Source: Cisco, VNI mobile, 2013.
Regarding these impressive figures and statements, we may wonder how this traffic explosion will impact mobile network. Mobile Network Operators (MNOs) will be severely challenged to provide the required capacity expansion in their network to avoid network congestion.
One consequence is that MNOs data subscription packages will need to change from the current ones. Income generated from data use will proportionally not follow data traffic expansion. Thus, they need to come up with new solutions and other consumer subscription offers. According to ABI Research, data revenues will only grow at a CAGR of about 15 to 18 percent until 2015, while data traffic is expected to have a 42 percent CAGR rate. This may lead to the end of “Unlimited” data packages.
Data consumption also depends on the kind of service used by the consumer. Some applications require more high data rate and/or lower latency, such as real-time services. These features are very important to improve user experience as much as possible. So mobile operators are now faced to new challenges, they need to analyze their customers
habits regarding mobile access and use. The aim of this is to meet quality and reliability requirements.
As mentioned before, most of the traffic within the next few years will result in cloud-based services, and two-thirds of the world's mobile data traffic will be video by 2017. Those real-time services are critical issues for operators because they reflect the most the quality of service for the consumer point of view. These services do not accept any data rate insufficiency or latency. Operators will need to come up with innovative solutions to comply with those requirements.
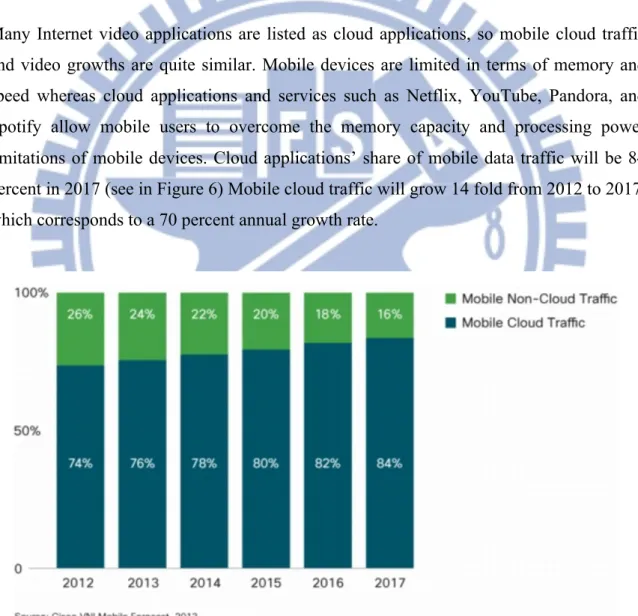
Many Internet video applications are listed as cloud applications, so mobile cloud traffic and video growths are quite similar. Mobile devices are limited in terms of memory and speed whereas cloud applications and services such as Netflix, YouTube, Pandora, and Spotify allow mobile users to overcome the memory capacity and processing power limitations of mobile devices. Cloud applications’ share of mobile data traffic will be 84 percent in 2017 (see in Figure 6) Mobile cloud traffic will grow 14 fold from 2012 to 2017, which corresponds to a 70 percent annual growth rate.
Figure 4: Mobile cloud traffic growth from 2012 to 2017 Source: Cisco, VNI Mobile, 2013.
2.2 Behavior evolution in data consumption
So far we have presented the rise in mobile data consumption over the past decade, and we highlighted that this exponential growth will keep on increasing within the next few years. But this phenomenon of traffic growth has always been present since the very beginning of mobile telecommunications, either due to the augmentation of the number of consumers, the handset devices performances improvement, the ever increasing types of network services… So mobile data traffic soaring is a logical and predictable feature, as it was the case for voice traffic, for example.
However, the consumers’ behavior has been considerably modified since the introduction on the market of smartphones devices combined with mobile data new services. Mobile data access led to a quite unique and new issue that we have not covered yet: the way users consume mobile services.
Right now operators typically already have wide-area GSM coverage and HSPA in densely populated urban areas. The mobile networks consist of macro cells that provide both voice and data transmission. The users are expected to move among those cells and are handover from one cell to another if they move beyond the current cell coverage capacity. This network solution has proven its efficiency for voice transmission. But since the introduction of mobile data services on the market, we have noticed that users tend to consume most of the mobile data in specific areas, in contrast to voice traffic, which occurs anywhere and often when users are highly mobile.
A survey conducted by Cisco’s Internet Business Solutions Group [4] points out that people who are at home are responsible for around 40% of mobile data traffic and 25% when they are at work. So it means that roughly 65% of mobile data is consumed within restricted areas. This highlights how mobile data consumption is different from voice transmission, as it occurs more and more inside buildings among “private” areas.
In most 3G networks today, operators are also seeing capacity demand in some areas growing much more rapidly than in the rest of their networks. These former hotspots have effectively evolved into much larger hot zones, outdoor and indoor areas. So mobile operators need to provide network access among those small areas indoor and in “hot
Meanwhile, consumers are expecting QoS to keep on improving, as it did over the last few years, and prices to keep on decreasing as technology improve. Users are very sensitive to unexpected, unreasonable or charges for data traffic exceeding their monthly limits, which they even consider to be non-justified if they are aware of technology improvements. They will certainly not accept the current MNO pricing plans that don’t seem to support or be favorable to the expected growth in data traffic, as wireless access is nowadays abundant and almost free.
III. Heterogeneous networks
3.1 PresentationNowadays, mobile operators are faced to new challenges: they need to find solutions to deal with this ever-increasing transmission rates and carry large quantities of traffic though radio waves in priority areas where data consumption is much higher than the average data flow in macro cells.
One possible solution could be to improve existing macro cells, by enhancing them with more spectrums, advanced antennas, increased order of diversity on the receiver and/or the transmitter, and greater baseband processing capacity within and between nodes. Today a lot of DSP (Digital Processing Schemes) are proposed to increase efficiency. They rely on using MIMO (Multiple Input Multiple Output) antenna structures, COMP (base station cooperative multipoint) and interference control techniques. Their aim is to eliminate co-channel interference due to frequency reuse. In outside areas with little environmental interference generation, these schemes tend to be very effective. But in indoor environment surrounded by walls, which reflect interferences, the improvement is limited compared to the solution complexity. Another field of study might be MAC (Medium Access Control) layer schemes, such as packet scheduling. But again, in restricted areas where data rates are high, the results are not encouraging enough.
Another field of study would be to densify the macro network by adding strategically located small cells to improve capacity. This approach keeps the total number of sites relatively low, while network performance becomes less sensitive to traffic location. A
from a three-sector site to a six-sector site. These strategic cells could use macro equipment or even micro equipment.
The last resort that mobile operators have left consists in adding small cells, i.e. complementing macro cells with small cells and dedicated indoor solutions based on the 3GPP standard. This approach can include the use of microcells, pico cells, femto cells, as well as Wi-Fi. Thus, there will be numerous base stations in denser spatial configuration, and more efficient directional antennas. Basically, the aim is to improve spatial reuse: architecture deployment will achieve what PHY/MAC layers cannot sustain. This is where heterogeneous networks are interfering. The figure below illustrates the different solutions we just talked about.
Figure 5: Alternatives to improve current networks performances Source: Ericsson white papers, it all comes back to backhaul, 2012.
Heterogeneous networks are networks connecting any devices using different transmission protocols and technologies. They make co-exist a range of different Radio Access Technologies (RATs) and Wi-Fi, where macro cells are complemented by a multitude of
Some mobile operators have already started to deploy heterogeneous networks among their structures, and most of them plan do to so very soon. As mentioned before, mobile data traffic exponential increase will keep going on within the years to come. Thus, wireless and mobile Internet might become a dominant technology. But to maintain its growth, wireless connection must remain stable in terms of running costs, energy consumption and access fees. And the major investments in new telecommunication generations, such as 4G or LTE, will not be able to sustain right away such a growth, as 3G devices are still dominating the market.
Basically, heterogeneous networks consist in implanting small radio nodes to provide the demanded wireless data rates in those strategic hotspots and indoor areas. These home nodes aim to transfer large wireless data flow over a short distance and use fixed networks as backhaul. We can see that the average user data rate will mainly depends on the density of base station deployment, rather than on the peak rate. In this thesis we will study several ways to deploy heterogeneous networks, each of them depending on different strategies and having unique specificities link to the technology they use. In consequence, comparison, analysis and outcomes are related to technological considerations.
However, before investing in network structure modifications, operators can still lead users to change the way they consume data. As an example, marketing is an efficient and money-saving way for operators to orient customers to one or another solution in which architecture is already deployed. Thus, it might be interesting to release new offers with block sized pricing or including incentives to convince customers to use network operators Wi-Fi in public areas. We will not go deeper in these considerations but marketer brainstorming might come out with interesting and non-technical solutions.
In this thesis, we focus on heterogeneous networks from mobile operator point of view. Thus, we will first have an overview on what heterogeneous networks can bring to both mobile operators and users.
Figure 6: Heterogeneous network diagram
Source: 4G Americas, Developing and integrating a high performance Het-Net, 2012.
3.2 Benefits
3.2.1 Mobile operator benefits
From the operator point of view, heterogeneous networks present many benefits. Firstly, they do not require heavy investments compared to the conventional macro cells. Heterogeneous networks need to gradually deploy relatively cheap network devices, such as short-range antennas or gateways. They will be connected to the core network, whom costly infrastructure is already paid, used, and do not need any modification. When using these network access solutions for mobile traffic, operators reduce the amount of data flow on their current network. It makes them save money. In comparison, the macro cell deployment strategy, which consists with deploying more dense cellular sites, might be an answer to the technical requirements, but it is also a very costly and energy-wasting solution. The large number of powerful base stations represents large investments and operating costs. Moreover, the end-user part of heterogeneous networks, if deployed in private areas, will depend on users’ electricity provisioning, and so reduce the operator energy bill.
Secondly, it reduces network congestion risks, an issue that we widely covered before. Congestion leads to QoS deterioration and thus to unsatisfied customers. If customers are unsatisfied with their current operator, they might react either by consuming less or by changing their operator. In both cases, it will be a loss threat for the operator and an opportunity for the other ones.
Also, it will enable operators to increase their revenues. With heterogeneous networks, operators direct a part of data traffic to another network handled by a fixed operator. So they save money on network costs but continue to charge the service regarding pricing method and the technology used. In addition, fixed Internet access allows better QoS than mobile broadband access, which suffer latency and low rate liabilities. Thus consumers who use those access networks enjoy better services thanks to higher bandwidth. The better is the service, the higher is the revenue. So operators might have a rise in their ARPU.
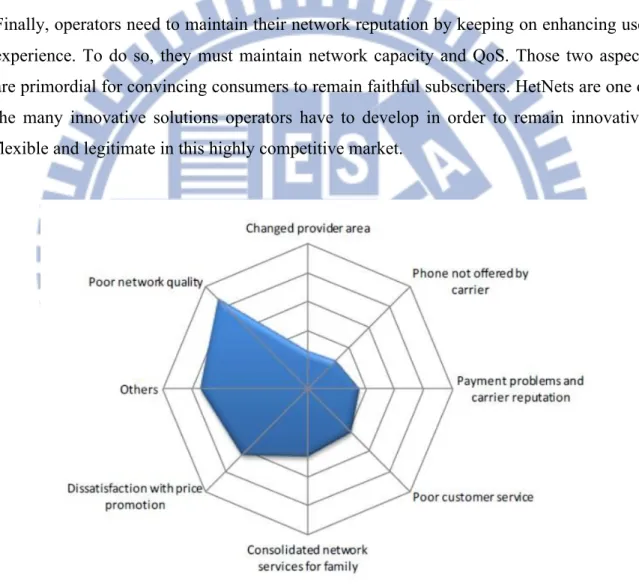
Finally, operators need to maintain their network reputation by keeping on enhancing user experience. To do so, they must maintain network capacity and QoS. Those two aspects are primordial for convincing consumers to remain faithful subscribers. HetNets are one of the many innovative solutions operators have to develop in order to remain innovative, flexible and legitimate in this highly competitive market.
Figure 7: Main Reasons leading to churn (customers moving from one operator to another one) Source: Ubiquisys, The evolution of femto cells, world economic forum, technology pioneer, 2009.
This graph highlights how crucial is network quality for operators if they want to keep their customers. Consequently, as we just saw it, operators have to tackle two priority
issues, congestion and QoS to maintain this network quality. And heterogeneous networks appear to be a very appropriate solution, as we talked about it in the section above.
3.2.2 User benefits
Heterogeneous networks use different Internet access technologies, which are wired, to provide mobile services. The most used technologies are Wi-Fi and femtocells. A femtocell gets Internet access through a gateway, called femto-gateway, this way they have access to the mobile network. Fixed Internet access is better than wireless access in terms of reliability, quality and latency [6]. Wi-Fi access and femtocells are recognized for providing good quality services thanks to their fixed connections structure. Thus, users relying on these technologies enjoy a better user experience.
Moreover, with more efficient indoor coverage, home nodes make mobile devices reduce energy consumption. Indeed, when devices are in indoor areas and want to reach outdoor antennas, they usually need to increase their signal power in indoor areas to make up for building signal absorption. This has an impact on devices’ battery life. Heterogeneous networks will also free resources on macro-cells mobile networks, so they improve service quality for fast moving users who will be using the current networks. The reliability and efficiency of those networks will lead to new services and competitive prices for users.
Finally, we can say that heterogeneous networks are a win-win solution. Operators might not hesitate to deploy and promote this solution among their current users, and maybe get new ones thanks to it.
3.3 Architecture
The usual HetNet architecture scheme is as follows: operators already have wide-area GSM coverage and HSPA in densely populated areas. They’re now deploying alternative coverage in hotspots/ hot zones or in rural areas:
As we mentioned it before, the hotspots are strategic areas where the connectivity demand is much higher than anywhere else among macro cells, so specific access nodes have to be deployed in order to offer dedicated coverage and better data flow. The rural areas are not as profitable as urban areas due to the small number of users and they wide spacing one from each other. So operators want to exploit this digital dividend, but by deploying
Heterogeneous networks use all at once different transmission protocols and technologies, such as LTE, Wi-Fi, in macro, micro, pico and femto cells. HetNets will include an overlay of cells of different sizes.
LTE stands for Long Term Evolution. It is an evolution of the UMTS standardized by the 3GPP. It allows very high speed data rate for mobile devices, and can deal with non-handset-type device. LTE coverage will focus on urban areas to support the exponential growth of mobile broadband traffic using macro cells highly scalable infrastructure.
A microcell is a mobile phone network cell using low power. It uses power to define and modify the range of its coverage area. The average radius of a micro cell is around two kilometers, where macro cells can go up to more than 30 kilometers. Microcells use the 2G technology of macro cells on a shorter range. They are deployed to improve capacity in public areas with high phone use rate, such as train stations, or during events that gather a lot of people. Pico cells are able to provide both outdoor and indoor coverage/capacity increase in hotspots such as shopping malls or offices, with a typical cell radius of up to 200 meters.
Femto cells are used indoors in cells of no more than 10-25m radiuses. While an operator deploys pico cells, femto cells are typically user-deployed: femtocells are ready to use and require no specific facilities or technical knowledge: any user can then install it. They were originally designed for voice coverage but they also have the potential to provide indoor data offload.
Small cells are bound to play a major role in future operators’ networks, as the large majority of small cell deployments will support the macro layer to add capacity when and where required. The cellular standards already mentioned will continue to exist and to improve (3GPP, LTE, 4G) along with local area technologies such as femtocells or Wi-Fi. In fact, offloading data traffic from cellular networks to femtocell or Wi-Fi might be decisive for indoor data offload uses. It appears to be highly attractive for operators from a cost point of view, making them reduce traffic in their HSPA and LTE networks. According to Cisco, 33% of total mobile data traffic went by femtocell or Wi-Fi hotspot in
3.4 Wi-‐Fi
3.4.1 Presentation
Wi-Fi is a Wi-Fi Alliance trademark, which provides the certification. It aims to connect through a wireless link any personal device, such as personal computer or smartphone, to the Internet. The covering area radius of an access point is about 10 to 30 meters. However, by using relays and many access points, the covering area can be expanded to fit the size of a university or even a city. The first use of Wi-Fi remains within a private or home access point. Nowadays, it is possible to turn some smartphones into a Wi-Fi access point, but only if the device is connected to a mobile network through 3G.
Wi-Fi is built on IEEE 802.11 standards. This set of standards is used to implement wireless local area networks (WLAN) in the 2.4, 3.6 and 5 GHz bands. Today, the two most common norms today are 802.11g and 802.11n. 802.11g works in the 2.4 GHz band. It relies on an OFDM transmission scheme which was already used in a former norm 820.11b. The maximum physical layer bit rate that might be achieved is about 54 Mbit/s but the average throughput is more 22 Mbit/s. Due to its spectral characteristics, 802.11g is vulnerable to interferences from other devices signals which also occur in the 2.4GHz band.
802.11n is an improvement of 802.11 standards by using multiple-input multiple-output antennas. It is able to deal with both 2.4GHz and 5 GHz bands. It allows a significant increase of the bit rate compared to the earlier 802.11g. Throughput goes from 54 Mbit/s up to 600 Mbit/s with four spatial streams at a channel width of 40 MHz. To achieve the maximum data rate, 64-QAM coding (Quadrature Amplitude Modulation) is needed but other encodings might also be used: n-QAM, QPSK, BPSK.
3.4.2 Spectrum management
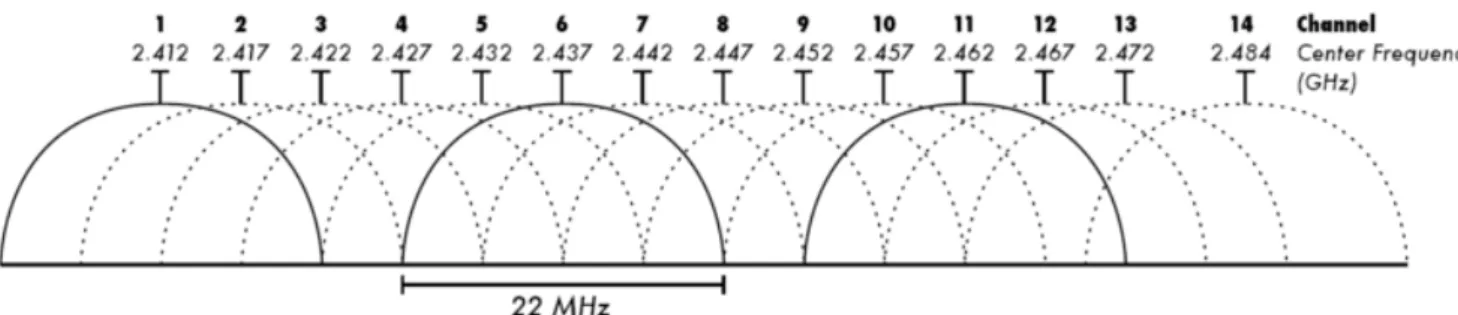
Figure 8: Wi-Fi channel allocation and channel overlap
Source: IEEE, 802.11™ specific requirements: wireless LAN medium access control (MAC) and physical layer (PHY) specifications, 2012.
As we can see on the above graphic, in 802.11 bands are divided into channels. As an example, the 2.4000 – 2.4835 GHz band is spited into 13 channels. Each of it has a width of 22MHz, and they are separated by a 5MHz border. Channel is centered on 2.412 GHz and 13 on 2.472GHz. Consequently, only every fourth or fifth channel can be used without overlap.
3.4.3 Advantages and limitations
The first advantage of Wi-Fi is its easy deployment, which saves time and money. Wi-Fi uses 5 channels in the 2.4 GHz band. No overlapping occurs when two channels use channel numbers which differ by five or more. The fastest norm (802.11n) needs double the radio spectrum compared to other norms like 802.11a or 802.11g. The expected next norm of Wi-Fi is 802.11ac. It will be impossible to use it with any other norms on the same band.
3.4.4 Security
To secure Wi-Fi networks access, several encryptions are currently used. The most used one was WEP but it has been shown that its code may be easily breakable even if well-configured. Some alternatives are available, such as Wi-Fi Protected Access encryption (WPA and WPA2).
Open Wi-Fi networks do not often benefit from any protection, which means that all the traffic from connected devices is visible to anyone located in the given area. However, other ways might be used to secure traffic and protect personal data, like VPN or secure Hypertext Transfer Protocol (HTTPs) on Transport Layer Security (TLS).
In some areas with numerous access points, “Wi-Fi pollution” might occur, and result in interference between signals, due to overlapping in the 802.11b/g spectrum. This situation is likely to happen in dense-population areas like offices, shopping malls or any shared building. However, it is important to know that many devices are also using the 2.4GHz band, such as cordless phones, microwave ovens, security cameras…
3.5 Femtocells
3.5.1 Presentation
Definition: “Femtocells are low-power wireless access points that operate in a licensed spectrum to connect standard mobile devices to a mobile operator’s network using residential DSL or cable broadband connections.” [7] Femtocells are deployed in homes or company buildings where they deal with from 2 to 4 active mobile phones in private houses, and up to 16 in business offices.
Femtocells have been developed to comply with some criteria: - Low-power access points
- Using mobile technology - In licensed spectrum
- Generating coverage and capacity - Over internet-grade backhaul - At low prices
- With full operator management - Self-organizing / self-managing
Femtocells rely on small device that any mobile customer can buy from his operator. It consists in a reduced size antenna which uses operator-licensed spectrum and is connected to the mobile network through a secured link over the Internet. From the customer point of view, there is no difference from a femtocell and a normal macro cell. They both provide all the mobile services (voice call, sms, mms…), and mobile phones deal with the handover from one to another.
3.5.2 Access management
provide better capacity and coverage. Restriction access solutions are needed to manage access rights.
The different restricted areas may be divided into three main categories [8]
- Open Subscriber Group (OSG). This pattern allows any user who subscribed a contract with the femtocell provider (the mobile operator) to have access to the femtocell. However, this may disturb the personal DSL access because of high data consumption of neighboring handsets. It might lead to some trouble with the DSL subscriber unless the femtocell provider offers discounts to share DSL access price.
This solution is however the most effective because it allows numerous mobile users to be connected to femtocells inside buildings in case of an advanced femtocell deployment.
- Close Subscriber Group (CSG). This management allows only authorized handsets to connect to the femtocell, which is the most common access restriction. This way, the femtocell is used as a way to improve capacity and coverage in the customer’s private area. But it remains poor in terms of traffic offloading, because only users who are at home can use it.
- The Hybrid Access Restriction uses both OSG and CSG solutions features. In this case, all the customers of the femtocell provider are allowed to connect to the femtocell but only if none of the authorized handsets want to use it. This way it gives benefits to the DSL subscribers and also enables the mobile operator to offload traffic when the femtocell is not in use.
3.5.3 Interference management
One of the most critical issues to deal with during femtocells deployment is interference management. Adding femtocells in the current mobile networks may lead to interference, as femtocells’ spectrum band is the same one as macro cells. Interferences commonly create coverage and capacity drops, and thus a waste of money. [11]
Here is some usual radio frequency interference issues related to bad femtocell deployment:
- Desensitized femtocell or handset: Handsets and base stations are calibrated to operate in a given dynamic range. However, if femtocells antenna and handsets are too close to each other, it creates high signal levels beyond the sensitivity range of the receiver [12]. On the download link, the handset receiver can be saturated and degrade demodulation performance. On the upload link, a high noise can be detected at the femtocell make the system unstable.
- Interference between macro and femtocells: Femtocells are deployed inside buildings, where they are likely to interfere with the macro cells outdoor signal, which goes through barriers such as walls and glass. Thus, interferences can be observed on both download and upload links. For the download link, interference may be created outside and damage outdoor signals. On the upload link, the handsets connected to the femtocell may interfere with the handsets connected to the macro network.
- Interference between femtocells is also likely to happen because of unplanned deployment. As an example, a femtocell deployed installed near a wall between to two apartments can cause significant interference to other apartments. In that case, the femtocell with the strongest radio frequency signal may not necessarily be the serving femtocell due to restricted access as explained earlier.
Many solutions have been developed to rule out those issues during femtocells deployment. One of them is the Femtocell Download Link TX Power Self Calibration: “To avoid a femtocell creating coverage holes outside, a solution is to adjust signal power between the femtocell and the macro cell. The above mentioned cell uses an autonomous self-calibration. It means that femtocells make download link measurements from macro cells and other femtocells to calculate the required transmission power level.”
3.5.4 Advantages and limitations
Femtocells allow operators to provide satisfactory coverage in indoor areas that are difficult to cover with outdoor base stations. They also allow operators to provide full services in rural areas, which would be expensive for operators to provide with macro cells. So they enable isolated areas to be as fully connected as an urban city may be. They are able to scan surrounding signals and then to choose by themselves their band
which are sometimes limited for wide-area coverage. In addition, they can use lower frequencies bands in order to reduce power consumption.
They improve the quality of service by providing extended coverage, capacity and service to consumers. Following this idea, a more efficient network will attract more customers and will result in more competition, thus to better prices for customers, innovations and good quality services.
However, femtocells generate an additional electromagnetic radiation in a private area, generating high frequency electromagnetic pollution and interference in the home. They represent risks to the confidentiality of private communications, but still lower than Wi-Fi, as authentication is managed by the SIM card. Also, the antenna device almost cannot be controlled in any way by the user, when it is installed. Finally, even if the power consumption is quite low, yet it has to be paid by the household or company.
3.6 Handover issue
In an ideal wireless environment, a mobile user is capable of using the device while moving from a point to another, thanks to the terminal active connection while migrating from one network coverage to another.
One critical issue that has to be dealt with in HetNets is handover. Indeed, HetNets use multiple cells at the same time, each of them having different size and sometimes different technology. User devices, which rely most of the time on macro cells coverage used to only handover from one macro cell to another relying on the only criteria of the location among the macro cells. With HetNets, they need now to handover among different types of cells and transmission protocols regarding the best achievable QoS. Jumping from one cell to another become much more complicated as it requires now to take in account new criteria such as connection cost, quality coverage, data rate, protocol disparities, received power sensitivity…
The numerous cells melt together in HetNets create a radio mist where different radio signals representing different transmission protocols at different transmitted power are present at the same time, both for uplink and down link. In heterogeneous network the transmitted power of micro cells can be much smaller than for macro, and logically pico
cell power is much smaller than micro, so the handover procedure need to be sensitive to all types of connection powers and be able to choose in real time the most efficient one.
Regarding those issues, handover protocols may be implemented and tested for allowing the device to be always connected to the cell currently providing the best QoS.
IV. Handover protocols
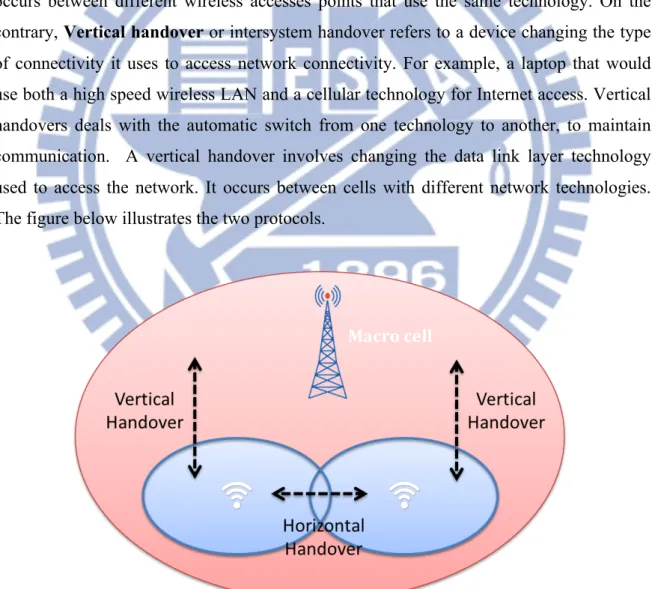
4.1 PresentationHandover protocols might be divided in two categories: Horizontal handover (handoff) or intra-system handover takes place between cells with the same network technology. It occurs between different wireless accesses points that use the same technology. On the contrary, Vertical handover or intersystem handover refers to a device changing the type of connectivity it uses to access network connectivity. For example, a laptop that would use both a high speed wireless LAN and a cellular technology for Internet access. Vertical handovers deals with the automatic switch from one technology to another, to maintain communication. A vertical handover involves changing the data link layer technology used to access the network. It occurs between cells with different network technologies. The figure below illustrates the two protocols.
Figure 9: Vertical and horizontal handover protocols Macro cell
Stages of a Vertical handover
- Network discovery: Mobile needs to determine which networks are usable and what services are available.
- Handover decision: Mobile determines which network it should connect to.
- Handover execution: Connections are necessary to re-route from existing network to new network.
They differ in several aspects such as bandwidth, data rate, and frequency of operation… All these make vertical handovers more challenging to implement.
4.2 Vertical handovers
A handover execution refers to the ABC (Always Best Connected) concept, including the authentication, authorization and transfer of user’s context information. The handover decision is the ability to decide when to perform a handover and to which access network to change. A vertical handover agent might consider network bandwidth, load, coverage, cost, security, QoS, user preferences… Many parameters have been proposed in researches, concerning vertical handover decision algorithms. The following presents some of these parameters.
- RSS
RSS is the most widely used criterion because it is easy to measure and directly related to service quality. There is a close relationship between RSS measurement and distance from the mobile terminal to it point of attachment. RSS is used by the majority of horizontal handover algorithms, and is an important criterion for vertical handover as well.
- Network connection time
Network connection time is the amount of time a terminal remains in a given network coverage. It is important to choose the right moment to trigger a handover so that the service quality is maintained to satisfactory levels. For example, a handover too early performed from WLAN to cellular network will waste network resources, and if done too late would result in handover failure. Also, if the connection time in the target network is potentially too short, handover should be avoided. These are important features for reducing the number of unnecessary handovers. Network connection time is related to a mobile’s location, velocity, and distance to the point of attachment. It affects the mobile
terminal RSS. The RSS variation then determines the time during the mobile terminal stays connected to a network. This aspect is critical for vertical handover because HetNets usually have different sizes of network coverage.
- Available bandwidth
It is the measure of available data communication resources (bit/s). It is a good indicator of traffic conditions in the access network, and is especially important for delay-sensitive applications.
- Power Consumption
Power consumption is a critical issue if the terminal’s battery is low. In such a case, it would be preferable to handover to a point of attachment which could help extend battery life.
- Monetary cost
Charging policies vary among networks and operators. If different networks have different charging policies, the cost of a network service should be considered in some cases in the handover decision.
- Security, integrity and privacy of transmitted data
This parameter might be critical, because for some applications, the integrity of the data is important, hence a more secure network should be chosen over a lower level security one.
- User preferences
User’s personal preference influences the selection of network access. If the user has some personal preferences over an access network, it should be taken into consideration during the handover decision.
4.3 Vertical handover classification
We decided to divide the algorithms into four groups, taking into consideration the handover decision criteria and methods implemented to process them.
The main decision criterion in those algorithms is the RSS. Many techniques have been developed to compare the RSS of the current point of attachment with the potential next one. With vertical handover, relative RSS cannot be applied, because of the different technologies involved, the RSS from different types of networks cannot be compared.
- Bandwidth based algorithms
The main criterion considered here is the bandwidth availability. Some algorithms use bandwidth and RSS information to make a decision.
- Cost function based algorithms
This kind of algorithms combines different metrics, such as monetary cost, security, bandwidth, and power consumption to come up with a “cost function”. Then the current network function result is compared to the candidate networks results. The input metrics can be assigned different weights, considering the network conditions as well as the user’s preferences.
- Combination algorithms
These algorithms tend to use much more inputs leading to handover decision. It is usually very difficult to develop analytical formulations when a large number of inputs are used. Thus, machine learning techniques are used to formulate the processes. Fuzzy logic and artificial neural networks based techniques are widely used to deal with these algorithms. The use of continuous and real-time learning processes allows the system to monitor its performance and modify its structure to create highly effective handover decision algorithms.
The following table summarizes the different vertical handover groups’ assets and liabilities.
Table 3: Vertical handover groups’ assets and liabilities
Group Applicable networking technologies Input parameters Handover target selection criteria Complexity Reliability RSS based Usually between macro and micro cellular networks RSS (main input) Network candidate with most stable RSS Simple Reduced because of fluctuation of RSS Bandwidth based Between any two heterogeneous networks Bandwidth and other parameters (RSS) Network candidate with highest bandwidth Simple Reduced because of changing available bandwidth Cost function based Between any two heterogeneous networks Various parameters (cost, bandwidth, security…) Network candidate with highest overall performance Complex Reduced because of difficulty in measuring some parameters Combination algorithms Between any two heterogeneous networks Different input parameters depending on different methods Network candidate with highest overall performance Very complex High because of the training of the system
Each algorithm group has its advantages and disadvantages, especially in the complexity of the same, the more complex they become, the more reliable they are, but also the amount of input that has to be handled is greater, making the algorithms difficult to develop.
4.4 Handover necessity estimation
A wide area open for research is the handover necessity estimation – HNE – that consists in being able to measure in real time the need for a user device to handover or not from one cell to another without the user noticing. This would help reduce the amount of failed or unnecessary handovers, and improve throughput. To perform handover necessity and failure estimation, it is required to develop and use handover need or failure estimation methods, especially between small cells cellular networks and WLANs.
The HNE structure presented in this thesis aims to both reduce handover failures and avoid unnecessary handovers between cellular networks and WLANs. The method proposed in this thesis can be sum up with the following procedure:
Figure 10: Handover necessity estimation system architecture
Instead of trying to improve the currently existing handover algorithms, this method performs handover necessity and failure estimations, and then to decide if a handover should or should not be performed. Thus it allows decreasing the amount of failed and unnecessary handovers between cellular networks and WLANs. The principle is that before triggering a handover, the system makes an assessment of both the handover needs
and failure estimation regarding the current network parameters, mobile device physical parameters and localization. If both the estimation methods give positive results, i.e. the handover appears to be relevant and it has satisfactory chances of success, then the handover is performed.
In this thesis, the parameters that have been used in our HNE protocols are the following ones:
- The handover delay is the time between the start and completion of the handover process. If compared to the time the mobile device is expected to spend within a given cell, it might give an idea of the relevance of performing a handover to the cell or not.
- The total number of handovers allows to make overall statistics about the number of failures, and also gives an idea about the network overall performances. Thus, the number of handovers may be decreased to avoid wasting network resources. - Handover failure probability: in the eventuality of a failed handover process, the
two main reasons for the handover failure are the lack of resources in the target network to complete it, or when the user device moves out of the coverage area of the target network before the handover process is completed. The handover failure probability is an arbitrary selected input parameter that represents our tolerance regarding the proportion of failed handovers that we might accept.
- Throughput: Handover to a network with higher throughput is preferred, so that the data rate delivered to the terminals by the network is higher.
4.5 Estimated travelling time
In addition to the listed parameters above, we added another one to the HNE algorithms that will be presented below. This parameter is the estimated travelling time of the mobile device through the candidate network to handover. The algorithms we performed for HNE need to use the time the mobile device has been spending within the candidate network coverage. Our solution that has not been tried before is to use an estimation of this time.
Indeed, some studies presented methods for estimating the time a mobile device might spend within a given cell when the device cross the border of the cell. However, it was mainly used for RSS based vertical handover algorithms and has never been used for
Instead of waiting for the mobile device to stay within the candidate network for a certain time before being able to actually perform the HNE algorithms and being able to say whereas or not the handover should be performed, we use the estimated travelling time of the device. It is calculated the very moment the mobile enters the network coverage. Thus, we are able to perform the HNE algorithms earlier and then be able to decide to perform or not the handover way sooner.
Some studies developed a formula that calculates the duration during which the mobile terminal is expected to spend within a WLAN cell. This was used only for RSS based vertical handovers, but our method aims to use it with HNE algorithms as explained above. This new approach aims to improve time-responsiveness, efficiency and flexibility.
tWLAN = R 2- l os 2 + V2(t s - tin) 2 V2(t s - tin)
- R is the radius of the WLAN cell
- los is the distance between the access point, and the point where the mobile terminal
takes an RSS sample, estimated by using RSS information and log distance path loss model.
- V is the velocity of the mobile terminal
- ts and tin are respectively the times when an RSS sample is taken and when the
mobile terminal enters WLAN cell coverage.
Now we had an overview of all the parameters used for our HNE method, the following part introduces the two HNE protocols we used in this thesis, the handover failure protocol and the unnecessary handover protocol.
4.6 Handover failure protocol
The purpose of this method is to be able to maintain the number of handover failures below a given and acceptable figure, using a time threshold parameter. For example, if the probability of handover failures needs to be less than 2%, then the time threshold will be adjusted to make the failure ratio (Number of failed handovers / Total number of handovers) remain below 2%.
The time threshold parameter used to make handover decisions is called T1. We compare it
to the estimated traveling time of the mobile device within the WLAN called tWLAN (see in
previous section). If tWLAN is greater than T1, then the mobile terminal will initiate the
handover procedure, on the contrary we consider that the handover will likely result in a failure and so we abort it.
The probability of a handover failure, using the threshold T1 is given by
Pf = 2 π arcsin VTi 2R ! " # $ % & − arcsin VT1 2R ! " # $ % & ( ) * + , -, 0 ≤ T1≤ Ti, 0,Ti< T1. / 0 1 11 2 1 1 1 Where T1= 2R V sin arcsin VTi 2R ! " # $ % & −π 2Pf ! " # $ % &
- R is the radius of the WLAN cell - V is the velocity of the mobile terminal
- Pf is the arbitrary selected handover failure probability that we accept. The
threshold T1 depends on this failure probability tolerance.
- Ti is the handover latency from cellular network to the WLAN.
We assume that V and Ti are already known and can be measured by accelerometers.
In other words, if the travelling time of the device within the WLAN tWLAN is longer than
the handover latency from cellular network to the WLAN (Ti) then the handover will not
fail and so can be initiated. On the contrary if tWLAN<Ti there is a chance that the procedure
might result in a failure, as the Pf expression expresses this failure probability. Then it is
important to find out a balance between avoiding handover failures and trying to handover as many devices as possible to the WLAN to offload traffic load from macro cells. Pf