行政院國家科學委員會專題研究計畫 成果報告
混合式排程機制應用於 IEEE802.16 OFDMA 網狀網路之研究 研究成果報告(精簡版)
計 畫 類 別 : 個別型
計 畫 編 號 : NSC 97-2221-E-011-055-
執 行 期 間 : 97 年 08 月 01 日至 98 年 07 月 31 日 執 行 單 位 : 國立臺灣科技大學電機工程系
計 畫 主 持 人 : 黎碧煌
計畫參與人員: 碩士班研究生-兼任助理人員:李俊霖 碩士班研究生-兼任助理人員:林裕培 碩士班研究生-兼任助理人員:吳欣祐 博士班研究生-兼任助理人員:簡鴻吉
報 告 附 件 : 出席國際會議研究心得報告及發表論文
處 理 方 式 : 本計畫涉及專利或其他智慧財產權,1 年後可公開查詢
中 華 民 國 98 年 10 月 16 日
行政院國家科學委員會補助專題研究計畫成果報告
混合式排程機制應用於 IEEE 802.16 OFDMA 網狀網路之研究
計畫類別: 個別型計畫 □ 整合型計畫 計畫編號:NSC97-2221-E011-055
執行期間: 97 年 8 月 1 日至 98 年 7 月 31 日
計畫主持人:黎碧煌 共同主持人:
計畫參與人員:簡鴻吉、李俊霖、林裕培、吳欣祐
成果報告類型(依經費核定清單規定繳交): 精簡報告 □完整報告
本成果報告包括以下應繳交之附件:
□赴國外出差或研習心得報告一份
□赴大陸地區出差或研習心得報告一份
出席國際學術會議心得報告及發表之論文各一份
□國際合作研究計畫國外研究報告書一份
處理方式:除產學合作研究計畫、提升產業技術及人才培育研究計畫、列 管計畫及下列情形者外,得立即公開查詢
□涉及專利或其他智慧財產權, 一年□二年後可公開查詢
執行單位:國立台灣科技大學電機工程系
中 華 民 國 98 年 9 月 12 日
行政院國家科學委員會專題研究計畫成果報告
混合式排程機制應用於 IEEE 802.16 OFDMA 網狀網路之研究
計 畫 編 號:NSC-97-2221-E-011-055
執 行 期 間:97 年 8 月 1 日 至 98 年 7 月 31 日
主 持 人:黎碧煌 國立台灣科技大學電機工程系
計畫參與人員:簡鴻吉、李俊霖、林裕培、吳欣祐 國立台灣科技大學電機工程系
This study provided four different link selection strategies for the centralized scheduling mechanisms and evaluated them with simulations to find out a better solution. For distributed scheduling mechanisms, we also proposed hashing selection scheme (HSS) to schedule packets using unique scheduling data for each node. This algorithm will further improve the request invalid problem existing in FIFO and random selection. After then, we conclude a hybrid scheduling mechanism which switches their scheduling mechanism based on the type of requested connection. Based on simulation results, such the hybrid scheduling mechanism can properly achieve spatial reuse ability of mesh network and enhance the network performance.
一、中文摘要
IEEE 802.16 標 準 中 定 義 了 點 對 多 點 (point-to-multipoint; PMP)與網狀(mesh)網路兩 種模式,其中網狀網路所提供的服務無論在服 務覆蓋率、傳輸效率、布建成本與系統可靠度 都要比傳統蜂巢網路來得好。在相關研究中,
並沒有針對網狀網路在正交分頻多工存取的 環境下,進行網路繞徑與封包排程以及服務品 質保證,提出適當的解決方案。因此,本研究 之目的即在尋求一個合適的網路架構及排程 方法,以應用於這樣的網路上。
本研究針對集中式排程選用四種鏈結選 擇策略進行評估以找出較適當的排程機制。在 分散式排程中,我們也提出了: “雜湊時槽選擇 機制”(hashing selection scheme; HSS),每個節 點透過不同的依據做資料排程,以降低在一般 選擇機制或是隨機選擇機制上的頻寬要求失 效的問題。我們根據先前得到的結論提出混合 式排程針對不同的傳輸需求適當的選擇集中 式或分散式方法來傳送資料。根據模擬結果,
此混合式機制的確能妥善利用網狀網路空間 再利用的特性並提升網路效能。
Keywords: Mesh Networks, IEEE 802.16, WiMAX, Centralized Scheduling, Distributed Scheduling
二、計畫緣由與目的
隨著電腦和通訊技術的快速發展,全球網 路正在快速的往下一代網路演進。由於未來個 人通訊上對多媒體及無線網路頻寬的需求日 益增加,無線宽頻網路技術的重要性亦日漸增 長。運用無線宽頻網路能夠將數據網路、語 音、視訊、多媒體及 Internet 的應用簡單方便 的 普 及 至 家 庭 及 企 業 用 戶 ; 其 中 由 IEEE 802.16 標準中所定義的無線寬頻都會型區域 網 路 (wireless metropolitan area networks;
WMAN)因能夠提供高速的無線傳輸並滿足行 動用戶的多媒體應用而成為下一代無線通訊 的重要技術。
關鍵詞:網狀網路、IEEE 802.16、WiMAX、
集中式排程、分散式排程
Abstract:
The IEEE 802.16 standard specifies two modes for sharing the medium: point-to-multipoint (PMP) and mesh modes. The wireless service in the Mesh mode is much better than the one in the traditional cellular network on service coverage, system capacity, construction cost, and even system availability. To the best of our knowledge, there is no proper solution to do packet routing and scheduling with QoS guarantee in an OFDMA mesh network.
Therefore, the purpose of this study is to get a suitable network architecture and to do routing and scheduling on such networks.
WiMax(world interoperability for microwave access)原是由生產 IEEE 802.16 標 準相關的廠商所成立的一個非營利性團體,主 要為推廣 IEEE 802.16 這個新的無線通訊標 準,之後也成為了 IEEE 802.16 標準的代名
詞。第一版的 IEEE 802.16 是在 2001 年的 12 月提出,透過 10~66GHz 頻帶之寬頻無線傳 輸,僅有視線所及(line of sight; LOS)傳輸的能 力,並使用單載波(single carrier)的實體層標 準。2003 年一月提出的 IEEE 802.16a 在傳輸 頻帶加入了 2~11GHz 的部份並支援非視距 (NLOS) 傳 輸 的 能 力 。 2004 年 定案的 IEEE 802.16d(現稱為 IEEE 802.16-2004)則是 IEEE 802.16a 的更新版,主要針對上傳通道(uplink) 引入了一些改善效能的措施[1]。到了 2005 年 所公布的 IEEE 802.16e 標準[2],則是一個可 以在 11GHz 以下的頻帶對固定或移動式的使 用者提供無線寬頻服務的擴充協定;相對於 IEEE 802.16d 系統主 要 是以正交 分 頻多工 (orthogonal frequency division multiplexing;
OFDM)做為無線傳輸介面,IEEE 802.16e 則是 以 正 交 分 頻 多 工 存 取 (orthogonal frequency division multiple access; OFDMA)為主在頻域 上提供多使用者的存取。
IEEE 802.16 標準中定義了兩種主要的運 作模式,分別是點對多點(point-to-multipoint;
PMP)與網狀(mesh)模式。在點對多點的模式 中,所有的用戶台(subscriber station)都與基地 台(base station)直接連線;相對地在網狀模式 中,網路中的用戶台並不需要與基地台直接連 線,而可以允許用戶台透過鄰接用戶將傳輸的 資料轉傳到基地台,如此一來便形成了多跳點 (multi-hop)的聯繫,並且隨著網路節點的增 加,網路的覆蓋範圍以及靈活性也會隨之提 升。當某一個連線中斷時,可選擇其他連線繞 路傳送而不必擔心斷線問題[3]。[4]指出在複 雜的地面環境下,利用 IEEE 802.16d 所規範 的網狀網路來提供的無線資料服務無論在服 務覆蓋率、傳輸效率、布建成本與系統可靠度 都明顯的比傳統蜂巢網路要來的好。然 而 IEEE 802.16d 的網狀網路僅定義在正交分頻 多工的環境中,對於如何於正交分頻多工存取 的環境下提供網狀網路服務的說明卻付之闕 如。因此,[5]針對如何在 IEEE 802.16e 的正 交分頻多工存取環境下支援網狀網路拓樸提 出了訊框架構方面的修正。
為了能夠妥善的分配在網狀模式下基地 台與用戶台之間的交通與各用戶台頻寬的分 配,IEEE 802.16 提出了兩種不同的排程機 制 : 集 中 式 排 程 (coordinated centralized scheduling; CSCH) 與 分 散 式 排 程 (distributed scheduling; DSCH)機制。集中式排程機制就是 網路內各節點的頻寬需求及路徑選擇都會由 基地台來做決定,各節點依據基地台所給于的
資料來傳送或接收封包。[6]指出對於以基地 台為起訖點的傳送,集中式排程機制在效能方 面要比分散式來得好,然而集中式排程機制卻 並不適合臨時性的頻寬需求。在集中式排程機 制中,基地台不但要決定網路繞徑的構成同時 也要處理各網路節點頻寬分配的問題。[7]提 出利用適當的繞徑方法可以大幅度的提高空 間再使用率(spatial reuse ratio)進而提升系統 的整體輸出。[8~14]進一步地提出以各種不同 的繞徑與封包排程方式來增進系統效能。
分散式排程則採用了 EBTT(election based transmission timing)來傳送分散式排程控制封 包 。 EBTT 使 用 二 跳 點 鄰 接 區 (two-hop neighborhood)所流通的資訊,來決定控制封包 傳送的位置以避免與其他節點碰撞(collision) 的情形。網路內的各節點則利用分散式排程控 制封包做三向交握(three-way handshaking)以 決定資料時槽(data timeslots)分配的方式。[15]
修正了 EBTT 以更即時完整地更新二跳點鄰 接點(two-hop neighbor)的訊息。另外,[16][17]
則對 EBTT 的效能做了完整的分析與模擬,[18]
則針對 EBTT 在高密度網狀網路效率不彰的 問 題 提 出 了 動 態 指 數 後 退 演 算 法 (dynamic backoff exponent)以增進分散式排程的可調性 (scalability),[19]則提出 FEBA/DRR 以解決資 料時槽分配的問題。
目前所提出的方法多是針對正交分頻多 工環境所做,對於如何在正交分頻多工存取應 用網狀網路的拓樸並不多見。[20]提出跨層 (cross-layer)最佳化的排程方法,利用實體層所 回饋的信號強度決定最適當的網路繞徑與頻 道選擇(channel selection)以達到最大的網路輸 出。然而,這樣的方式由於排程演算的複雜度 實際上並沒有辦法使用,而且也沒有考量到分 時 多 工 存 取 (time division multiple access;
TDMA)的環境,同時也並未妥善利用網狀網 路最大的特性—空間再利用。[21]提出以雙維 度對映(two-dimensional mapping)的方式來處 理時域和頻域上雙重多工存取的情形,但卻仍 僅能處理單一跳點(single hop)的傳輸模式。因 此,如何在正交分頻分時多工存取的環境下 [22],充分地利用空間再利用的特性來決定網 路繞徑、頻寬分配來達成系統效能的最佳化就 成了一個重要且有趣的課題。因此,本研究之 目的在於提出一個實現於 IEEE 802.16 上的網 狀網路排程演算法以妥善利用網狀網路空間 再利用的特性,來達成網路效能的增進。
三、混合式排程演算法機制
為 了 完 整 利 用 正 交 分 頻 多 工 存 取 的 特 性,我們採用[5]所提出一個新的框頁架構來 支援以下的排程工作。如圖 1(a)所示,控制子 框頁(control subframe)利用正交分頻多工/分 時多工存取技術,而資料子框頁(data subframe) 才利用正交分頻分時多工存取的技術;圖 1(b) 說明了控制子框頁與資料子框頁實際的內容。
control subframe
subframe data
subchannel
(a)
(b)
圖1 正交分頻多工存取的網狀網路訊框架構
3.1 集中式排程演算法
在 IEEE 802.16 網 狀 網 路 集 中 式 排 程 中,為了讓每個用戶台都能夠直接或間接與基 地台溝通,使用了排程樹(scheduling tree)架 構。本研究對於排程樹的建立,採用廣度優先 搜尋演算法(breadth first search; BFS),因為此 種演算法具有讓排程樹的高度盡可能達到最 小的優點,也就是說當有一個新節點欲加入網 狀網路時,則會選擇離基地台最近且在它通訊 範圍的節點做為父節點,如果同時有多個節點 可以選擇,則選擇其 Node ID 最小的節點做為 父節點,其流程圖如圖 2 所示。
由於集中式排程並無實際的時槽配置資 訊,因此本研究利用 MSH-CSCF 與 MSH- CSCH-Grant 訊息並參考[23][24],選用四種鏈 結選擇策略,分別為︰
1. Nearest_to_BS_first︰優先選擇與基地台 跳躍數最少的鏈結。
2. Farthest_to_BS_first︰優先選擇與基地台 跳躍數最多的鏈結。
3. Lowest_load_first︰優先選擇整個網路頻 寬需求最少的鏈結。
4. Highest_load_first︰優先選擇整個網路頻
寬需求最多的鏈結。
以上四種鏈結選擇策略若遇到條件相等時,則 選擇鏈結傳送端Node ID最小者優先排程。本 研究同時加入允入控制機制,在頻寬不足時依 過去頻寬分配紀錄,依序減少每個鏈結分配的 時槽數,因此並不會造成嚴重不公平現象。
BS
Tree Level 0
Node[i]
? i=1
Node[i]
Tree_Level
?
node ID Node[i]
i++
i ?
?
Tree Level 1 N
N
Y
Y Y
Y
N
N
圖2 排程樹廣度優先搜尋法流程圖
首先利用廣度優先搜尋演算法建立排程 樹。之後,每個節點檢查各自佇列中的封包 數,各節點再按照各自在排程樹出現的順序送 出 MSH-CSCH-Request 到父節點,透過父節 點的轉發訊息跟基地台要求頻寬,等到基地台 收到排程樹上所有節點的頻寬要求後,則去檢 查是否有新進的連線要求。若有新進連線要 求,則隨機選擇一個新進連線,然後透過允入 控制機制,去決定頻寬是否足夠分配給選擇的 新進連線。若有足夠的頻寬分配則接受所選擇
的新進連線;若沒有足夠的頻寬分配則拒絕所 選擇的新進連線,然後再去檢查是否還有其他 新進連線要求;如果沒有新進連線要求,則收 集所有已接受的連線所需的鏈結以及時 槽 數,然後按照鏈結選擇策略配置每個鏈結所需 要的時槽;假使系統沒有足夠的時槽分配給所 有鏈結所要求時槽數,則按照過去頻寬分配的 紀錄依序減少每個鏈結分配到的時槽數,直到 系統頻寬足夠分配為止,之後基地台再透過廣 播 MSH-CSCH-Grant 訊息通知所有節點最新 的排程資訊,當所有節點收到之後推算出自己 的傳輸時間,並在適當的時間傳輸。
3.2 分散式排程演算法
在沒有設計時槽選擇的機制之下,是在資 料子訊框中由最左上開始,以由上到下由左至 右的方式選擇時槽。因為每個節點都是用相同 的選擇方式來選擇時槽,導致時槽會被大量的 重複選取,產生大量的 Request 失效的問題。
本 研 究 提 出 了 雜 湊 選 擇 機 制 (hashing selection scheme; HSS)的方式來取代隨機選擇 機制,每個節點針對相同頻寬的要求者所做的 排程區塊會不相同。圖 3 為隨機選擇機制和 HSS 的不同,圖 3(a)為隨機選擇機制的示意 圖,在排程的時候是由第一個區塊開始以隨機 的方式來做安排,直到第一個區塊已經沒有時 槽能夠做安排,才跳到下一個區塊繼續做安 排,而圖 3(b)則是 HSS 的選擇方式,針對每 個節點所要求的頻寬,會依照演算法以單一性 的方式選擇時槽來分配,直到這個區塊沒有剩 餘空間給該節點後,才會繼續透過演算法來選 擇新的區塊來做排程。
(a)
(b)
For the neighbor 1
For the neighbor 2
For the neighbor 3
圖3 隨機選擇機制及HSS概念比較
每 次 排 程 時 , 會 依 照 節 點 的 編 號 (identifier; ID)以及要做排程的訊框編號當做
鍵值(key value),並透過以下公式來計算出針 對不同節點的頻寬要求之排程的區塊為何:
k n D
n
Hk( ) ( )* % (1) 2
_
_ _
DURATION DATA
duration dataslot
Total
D (2)
D ID Granter_ %
(3)
% _ 2
*2 1 )(k k HASH FACTOR
(4)
此處
k表示所要做排程的訊框編號 n表示計算第幾次移動的雜湊值
) (n
Hk 表示在第k個資料子訊框中第n次移動 的雜湊值,如此便可算出每次排程的區塊。
3.3 混合式排程演算法
由於集中式排程需要基地台的涉入,因此 如果只是相鄰節點之間資料的傳送將會多出 許多不必要的頻寬浪費;而跨節點的傳送又無 法只由相鄰節點彼此溝通就能夠成功傳送。本 研究針對這樣的問題提出混合式排程演 算 法,在相鄰節點之間的資料傳輸以前述之分散 式排程演算法來決定資料子訊框排程位置,而 非相鄰節點的傳送則以集中式排程演算法來 達成。
四、系統模擬及結果分析
本節將針對我們所提出的排程演算法,在 不同網路環境下之情形進行模擬及比較。在集 中式排程中我們假設網路為格狀拓樸之 型 態,如圖4所示。圖5為該網路拓樸於集中式排 程下之排程樹。
圖4 總節點數為25的網路拓樸
圖5 總節點數為25的排程樹
圖6為四種鏈結選擇策略之傳輸效能比 較,由圖中可見傳輸效能隨著連線到達 率 (connection arrival rate) 增 加 呈 現 穩 定 的 增 加 , 直 到 連 線 到 達 率 達 到 100 connections/
minute以後,Lowest_load_first的傳輸效能逐漸 呈 現 飽 和 狀 態 , 而 當 連 線 到 達 率 到 了 120 connections/minute 以 後 , Farthest_to_BS_first 的傳輸效能也逐漸開始呈現飽和狀態,連線到 達率繼續增加達到180 connections/minute以 後,Nearest_to_BS_first、Highest_load_first兩 種鏈結選擇策略的傳輸效能也漸漸趨向飽和 狀態,由於在本研究中每個連線的路由路徑都 必須經由基地台,因此離基地台越近的鏈結其 頻 寬 需 求 通 常 也 會 較 大 , 所 以 才 會 造 成 Nearest_to_BS_first與Highest_load_first的傳輸 效能極為相近,不過從圖中兩條曲線比較仍可 看 出 Highest_load_first 的 傳 輸 效 能 略 高 於 Nearest_to_BS_first。
圖7為四種鏈結選擇策略之連線拒絕率比 較,由圖中可發現連線拒絕率隨著連線到達率 增加而逐漸趨向線性增加,當連線到達率達到 60 connections/minute 以 後 , 我 們 可 以 發 現 Lowest_load_first與Farthest_to_BS_first兩種鏈 結選擇策略的連線拒絕率開始大於零,亦即整 個網路頻寬資源逐漸呈現略為不足現象,開始 拒絕新進的連線要求。當連線到達率到了120 connections/minute以後,Nearest_to_BS_first、
Highest_load_first兩種鏈結選擇策略的連線拒 絕 率 才 開 始 大 於 零 , 不 過 仍 可 發 現 Highest_load_first 的 連 線 拒 絕 率 低 於 Nearest_to_BS_first。因此四種鏈結選擇策略 連 線 拒 絕 率 由 小 到 大 依 序 為 Highest_load_first 、 Nearest_to_BS_first 、 Farthest_to_BS_first、Lowest_load_first,至於 造成這中間差異的原因可能是因為需求頻寬 較大的鏈結在頻寬的配置比較缺乏彈性,所以
當系統優先配置需求頻寬較小的鏈結之後造 成系統沒有足夠的頻寬提供給需求頻寬較大 的鏈結,因此造成連線拒絕率上升相對傳輸效 能就較差。
圖8為四種鏈結選擇策略的平均存取延遲 比較,由圖中可見四種鏈結選擇策略在網路輕 載時其平均存取延遲都在142 ms上下,相差範 圍都在一個訊框時間範圍內,這主要是由於排 程順序造成封包傳送到目的端時間上的 差 距 , 但 隨 著 系 統 服 務 連 線 數 上 升 , Lowest_load_first 、 Farthest_to_BS_first 、 Nearest_to_BS_first、 Highest_load_first四種鏈 結選擇策略分別在系統服務連線數為 90、
110、130、150開始呈現緩緩上升,主要是因 為系統能接受的連線數已經逐漸達到飽和,所 以系統才會產生較高的平均存取延遲,但由於 系統的允入控制機制讓系統維持在一定的服 務連線數,才使得平均存取延遲不至於因為網 路負載的增加而大幅上升。
分散式排程則以隨機拓樸來進行模擬。在 隨機拓樸中,透過期望鄰近節點的機制,來產 生整個網路拓樸。舉例來說,假設設定鄰近節 點個數為3,因此在產生網路拓樸時,每個節 點會產生約在三個左右的鄰近節點。在本研究 中,隨機拓樸中設定的鄰近節點數為3。
圖 10 是 隨 著 系 統 封 包 到 達 率 (system packet arrival rate)的增加來比較其節點產能的 結果,可以發現HSS機制相較於其他兩種機 制,具有較高的節點產能,但隨著系統封包到 達率的增高,HSS機制的產能漸漸和一般選擇 或隨機選擇機制的結果相同,這是因為資料子 訊框的空閒時槽已經不能滿足節點的頻寬要 求,因此不管使用什麼機制,其節點產能會漸 漸相同。
圖11為隨著系統封包到達率的增加來比 較其延遲時間的結果。可以發現HSS機制和另 外兩種機制的延遲時間較高,是因為HSS機制 並不是由資料子訊框的最前面開始做排程,而 是依照每個節點的雜湊值不同,會被排程到較 後面的時槽,所以HSS機制才會有較高的延遲 時間,但隨著系統封包到達率的增高,其HSS 機制的延遲時間也會漸漸與另外兩種機制相 同,這是因為時槽漸漸的開始排程到中間之 後,因此三種機制的排程結果會漸漸相同。
圖12為系統封包到達率與Request失效的 比較,在這張圖中,HSS機制在Request失效率 的表現一樣和另外兩種機制來的好,因為HSS 機制可以同時降低主要干擾以及二次干擾狀 況下Request失效問題的產生。
五、結論
由於IEEE 802.16中對於頻寬分配的排程 演算法並沒有明確規範。為了解決這個問題,
本研究分別對集中式與分散式排程進行分析 並提出可行之方案。在集中式排程中,選用四 種鏈結選擇策略,並針對此四種不同的鏈結選 擇策略對整個網路效能的影響做一個評估,找 出一個較好的排程機制以提升網路效能。由模 擬結果可以發現,在四種鏈結選擇策略之中,
由於需求頻寬較大的鏈結在時槽配置上較不 具 彈 性 , 因 此 Nearest_to_BS_first 與 Highest_load_first所呈現的傳輸效能較其他兩 者佳。
在分散式排程方面,本研究提出了“雜湊 時槽選擇機制”,透過每個節點都是以不同的 依據做資料排程,來降低在一般選擇機制或是 隨機選擇機制上的頻寬要求失效的問題,使得 原本因為隱藏節點所造成的頻寬要求失效的 問題有大量的改善。根據模擬結果的確能改善 並提升其結果,但在重載時由於資料子訊框的 時槽有限,因此並沒有辦法完全改善其問題。
本研究同時提出了結合此兩者方法之混 合式排程機制以進一步針對不同型態之傳輸 需求提供解決方案。未來可加入對多媒體服務 類型QoS的探討,提出更好的管理機制以因應 目前多媒體的傳輸需求。
參考文獻
[1] IEEE 802.16-2004, “IEEE standard for Local and Metropolitan Area Networks — Part 16: Air Interface for Fixed Broadband Wireless Access Systems,” Oct. 1, 2004.
[2] IEEE 802.16e-2005, “IEEE Standard for Local and Metropolitan Area Networks – Part 16: Air Interface for Fixed and Mobile Broadband Wireless Access Systems – Amendment for Physical and Medium Access Control Layers for Combined Fixed and Mobile Operation in Licensed Bands,” Dec. 7, 2005.
[3] Raffaele Bruno, Marco Conti, and Enrico Gregori, “Mesh Networks: Commodity Multihop Ad Hoc Networks,” IEEE Communications Magazine, Vol.43, Issue 3, pp.123-131, Mar. 2005.
[4] Roberto Hincapie, Javier Sierra, and Roberto Bustamante, “Remote Locations Coverage Analysis with Wireless Mesh Networks based on IEEE 802.16 Standard,” IEEE Communications Magazine, Vol. 45, Issue 1, pp.120-127, Jan. 2007.
[5] Yann Lebrun, Francois Horlin, Andre Bourdoux, and Liesbet Van der Perre, “Feasibility Study of the Mesh Extension for the IEEE 802.16e
Communication System,” Symposium on Communications and Vehicular Technology, pp.93-96, Nov. 2006.
[6] Simone Redana and Matthias Lott,
“Performance Analysis of IEEE 802.16a in Mesh Operation Mode,” in Proc. of IST SUMMIT 2004, June 2004.
[7] Liqun Fu, Zhigang Cao, and Pingyi Fan,
“Spatial Reuse in IEEE 802.16 Based Wireless Mesh Networks,” IEEE International Symposium on Communications and Information Technology, Vol. 2, pp. 1358-1361, Oct. 2005.
[8] Hung-Yu Wei, Samrat Ganguly, Rauf Izmailov, and Zygmunt J. Haas, “Interference-Aware IEEE 802.16 WiMax Mesh Networks,” IEEE 61st Vehicular Technology Conference, Vol. 5, pp. 3102-3106, May 2005.
[9] Yang Cao, Zhimin Liu, and Yi Yang, “A Centralized Scheduling Algorithm based on Multi-path Routing in WiMAX Mesh Network,”
International Conference on Wireless Communications, Networking and Mobile Computing, pp. 1-4, Sep. 2006.
[10] Jian Tao, Fuqiang Liu, Zhihui Zeng, and Zhangxi Lin, “Throughput Enhancement in WiMAX Mesh Networks Using Concurrent Transmission,” International Conference on Wireless Communications, Networking and Mobile Computing, Vol. 2, pp. 871-874, Sep.
2005.
[11] Daehyon Kim and Aura Ganz, “Fair and Efficient Multihop Scheduling Algorithm for IEEE 802.16 BWA Systems,” 2nd International Conference on Broadband Networks, Vol. 2, pp.
833-839, Oct. 2005.
[12] Yingjie Wang, Zhenhua Wu, Mugen Peng, and Wenbo Wang, “Performance of Wireless Mesh Networks with Centralized Multihop Scheduling for Intelligent Transportation Systems,” 6th International Conference on ITS Telecommunications Proceedings, pp. 777-781, June 2006.
[13] Peng Du, Weijia Jia, Liusheng Huang, and Wenyan Lu, “Centralized Scheduling and Channel Assignment in Multi-Channel Single-Transceiver WiMax Mesh Network,”
IEEE Wireless Communications and Networking Conference, pp. 1734-1739, Mar.
2007.
[14] Harish Shetiya and Vinod Sharma, “Algorithms for Routing and Centralized Scheduling in IEEE 802.16 Mesh Networks,” IEEE Wireless Communications and Networking Conference, Vol. 1, pp. 147-152, Apr. 2006.
[15] Nico Bayer, Dmitry Sivchenko, Bangnan Xu, Veselin Rakocevic, and Joachim Habermann,
“Transmission timing of signaling messages in IEEE 802.16 based Mesh Networks,” in Proc.
European Wireless Conference 2006 (EW ’06), Apr. 2006.
[16] Min Cao, Wenchao Ma, Qian Zhang, and Xiaodong Wang, “Analysis of IEEE 802.16 Mesh Mode Scheduler Performance,” IEEE Transactions on Wireless Communications, Vol.
6, Issue 4, pp. 1455-1464, Apr. 2007.
connection arrival rate(connections/minute)
60 80 100 120 140 160 180 200 220
system throughput(Mbps)
10 15 20 25 30 35
Farthest to BS first Nearest to BS first Highest load first Lowest load first
[17] Claudio Cicconetti, Alessandro Erta, and Luciano Lenzini, “Performance Evaluation of the Mesh Election Procedure of IEEE 802.16/WiMAX,” Proceedings of the 10th ACM Symposium on Modeling, analysis, and simulation of wireless and mobile systems, pp.
323-327, Oct. 2007.
[18] Nico Bayer, Bangnan Xu, Veselin Rakocevic, and Joachim Habermann, “Improving the Performance of the Distributed Scheduler in IEEE 802.16 Mesh Networks,” IEEE 65th Vehicular Technology Conference, pp.
1193-1197, Apr. 2007.
圖6 四種鏈結選擇策略的傳輸效能比較
connection arrival rate(connections/minute)
60 80 100 120 140 160 180 200 220
connection blocking ratio
0.0 0.1 0.2 0.3 0.4 0.5 0.6
Farthest to BS first Nearest to BS first Highest load first Lowest load first
[19] Claudio Cicconetti, Ian F. Akyildiz, and Luciano Lenzini, “Bandwidth Balancing in Multi-Channel IEEE 802.16 Wireless Mesh networks,” 26th IEEE International Conference on Computer Communications, pp. 2108-2116, May 2007.
[20] Kemal Karakayali, Joseph H. Kang, Murali Kodialam, and Krishna Balachandran,
“Cross-Layer Optimization for OFDMA-Based Wireless Mesh Backhaul Networks,” IEEE Wireless Communications and Networking Conference, pp. 276-281, Mar. 2007.
圖7 四種鏈結選擇策略的連線拒絕率比較
mean served connection(connections)
60 80 100 120 140 160
avg access delay(ms)
141 142 143 144 145 146 147 148 149
Farthest to BS first Nearest to BS first Highest load first Lowest load first
[21] Yehuda Ben-Shimol, Itzik Kitroser, and Yefim Dinitz, “Two-Dimensional Mapping for Wireless OFDMA Systems,” IEEE Transactions on Broadcasting, Vol. 52, Issue. 3, pp. 388-396, Sep. 2006.
[22] IEEE 802.16.4c-01/35.
[23] Bo Han, Fung Po Tso, Lidong Lin, and Weijia Jia, “Performance evaluation of scheduling in IEEE 802.16 based wireless mesh network,”
IEEE International Conference on Mobile Adhoc and Sensor Systems, pp.789-794, Oct.
2006.
[24] Qing Xiong, Weijia Jia, and Chanle Wu, “Packet Scheduling Using Bidirectional Concurrent Transmission in WiMax Mesh Networks,”
International Conference on Wireless Communications, Networking and Mobile Computing, pp. 2037-2040, Sep. 2007.
圖8 四種鏈結選擇策略的平均存取延遲比較
Random topology Arrival rate v.s. Throughput Node = 20 Neighbor = 3 Exp = 3 Retry = 0
Arrival rate (103 arrival/sec)
0 50 100 150 200 250
Node throughput (Mbps)
0 2 4 6 8 10 12 14 16 18
Percentage of improvement (%)
-10 0 10 20 30 40
Regular HSS Random Improvement
圖9 流量與產能的關係及改善效益
Random topology Arrival rate v.s. Delay Node = 20 Neighbor = 3 Exp = 3 Retry = 0
Arrival rate (103arrival/sec)
0 50 100 150 200 250
Hop delay (ms)
20 40 60 80 100 120
Regular HSS Random
圖10 流量與延遲時間的關係
Random topology Arrival rate v.s. Invalidation ratio Node = 20 Neighbor = 3 Exp = 3 Retry = 0
Arrival rate (103 arrival/sec)
0 20 40 60 80 100 120 140 160 180 200 220
Invalidation ratio
0.00 0.05 0.10 0.15 0.20 0.25 0.30 0.35
Regular HSS Random
圖 11 流量與 Request 失效率的關係
出席國際學術會議報告
第14屆亞太通訊研討會(The 14th Asia-Pacific Conference on Communications, APCC-2008) 於2008/10/14~2008/10/16於日本東京舉行,這是一個結合新一代通訊與網路系統的國際學術 會議。會中除了一般的論文發表外,還包含了精彩的Keynote Speech。會議的主題包含以下 領域:
* 4G Mobile Network Architecture
* Ad Hoc and Sensor Networks
* Antennas and Propagations
* Broadband Wireless Access
* Broadcasting Technologies
* Coding and Modulations
* Control Plane Technologies
* Convergence Networks
* DSP for Communications
* Emerging Wireless Technologies
* Experimental System and Field Trial
* Flow-based Traffic Management
* Higher Speed Ethernet
* High-speed Switching and Routing
* Information and Communication Theory
* Information Security
* Media Streaming
* Mobile Wireless Systems
* Multimedia Communications
* Network and Service Management
* Network Coding
* Network Security
* Networked Applications and Multicasting
* New Generation Networks
* Next Generation Mobile Networks
* Optical Communications
* Overlay Network and P2P Networking
* Parallel Processing on Multi-Core Systems
* Photonic Networks
* QoS and Resource Management
* RF Technologies
* Satellite and Space Communications
* Speech and Video Signal Processing
* VPNs and Traffic Engineering
* Wireless LANs
會中發表論文題目為“An Enhanced Election-Based Transmission Timing Mechanism in IEEE 802.16 Mesh Networks”,並於發表完畢後,與主持人及現場學者有相關的討論,對本
研究有相當的幫助。
在研討會上吸收相關學者之經驗,以擴展自身的國際觀且對相關領域有更進一步的瞭 解。在此次研討會中,經由和相關學者專家之討論,確實對於相關領域之發展方向及未來之 研究趨勢有更進一步的瞭解。發表的論文如下:
An Enhanced Election-Based Transmission Timing Mechanism in IEEE 802.16 Mesh Networks
Bih-Hwang Lee Chun-Ming Chen
lee@ccg.ee.ntust.edu.tw bhlee@mail.ntust.edu.tw Department of Electrical Engineering
National Taiwan University of Science and Technology
AbstractIEEE 802.16 is also known as the worldwide interoperability for microwave access (WiMAX), which defines point-to-multipoint (PMP) and mesh modes to support wireless medium access. The mesh mode provides an easy and cheap way to construct the last-mile connection. The multi-hop environment which supports spatial reuse can use the radio resource more efficiently.
IEEE 802.16 defines three kinds of scheduling algorithms without specifying the detail. In this paper, we propose a new enhanced election-based transmission timing mechanism to solve the problem currently on the coordinated distributed scheduling algorithm.
According to the simulation results by using the network simulator ns2, the new mechanism can prevent the unexpected collision of MSH-DSCH messages and can get better performance on time-sensitive traffic.
Key words: IEEE 802.16, WiMAX, wireless medium access , scheduling algorithms
1. Introduction
The demand of broadband access is highly increased by the rapid growth of new services, such as voice over IP (VoIP), video on demand (VoD), online gaming, and peer-to-peer. It is a challenge to provide broadband access everywhere, hence wireless access technologies have become attractive solutions.
Compared with the wired technologies such as HFC (hybrid fiber/coaxial) and DSL (digital subscriber line), the broadband wireless access (BWA) can be deployed easily with low cost regardless of the terrain layouts, and it is simple to add users by providing additional radio interface and capable link conditions. IEEE 802.16 is also known as the worldwide interoperability for microwave access (WiMAX) [1][2], which defines point-to-multipoint (PMP) and mesh modes to support wireless medium access[3]. In the PMP mode, the wireless link operates with a central base station (BS) to serve a group of subscriber stations (SSs) within the same antenna sector by broadcasting. All SSs receive the same transmission signal from BS within a given frequency channel, while BS coordinates all the transmissions from SSs to BS. On the other hand, SSs can communicate with each other directly without BS involved in the mesh mode.
The IEEE 802.16 standard defines three kinds of scheduling schemes for the mesh mode: the centralized scheduling, the coordinated distributed scheduling, and the uncoordinated distributed scheduling. In the centralized scheduling, BS determines flow assignments on the channel by the requests of SSs; SSs then use the information from BS to decide how to share the channel in different time slots. The connection setup time is extremely long, because all control and data packets have to go through BS from source to destination; therefore the centralized scheduling is not suitable to occasional traffics. In both coordinated and uncoordinated distributed schedulings, the IEEE 802.16 standard defines a three-way handshake mechanism to allocate the channel
resources among SSs. The coordinated distributed scheduling algorithm uses the control portion of each frame to transmit its own scheduling. By contrast, the uncoordinated distributed scheduling is established by direct requests and grants in the data subframes without colliding with the scheduled data by the coordinated scheduling methods.
To compete the transmission opportunities in the control subframes, the IEEE 802.16 standard proposes a pseudo-random election algorithm based on the scheduling information within the two-hop neighborhood. The coordinated distributed scheduling transmits its signaling packet via this election algorithm. However, IEEE 802.16 standard does not specify the detail of the competing method.
[4] provides an extension of original election algorithm to solve the problem that information from 2 hop far neighbor is not correct. But the extension does not really fix the situation.
This paper proposed a modification on the extension to overcome the problem and examine its performance on ns2.
The rest of this paper is organized as follows. Sec. 2 describes the overview of the distributed scheduling algorithm in the IEEE 802.16 mesh mode. Sec. 3 states the problem on current election-based transmission timing (EBTT) mechanism and provides our enhancement on EBTT mechanism. We show our simulation results in Section 4.
Finally conclusions are made in Section 5.
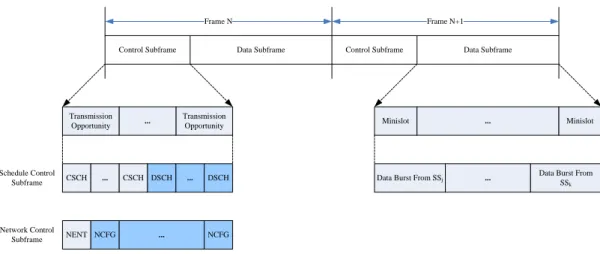
2. The Coordinated Distributed Scheduling Algorithm In the IEEE 802.16 scheduling algorithm, the control messages and data packets are allocated in different timeslots as Figure 1. The description of different control messages and the related scheduling parameters are shown in Table 1. The control subframe provides two functions: one is for network construction and maintenance, known as network control subframe, and the other is for resource scheduling, known as schedule control subframe. In network control subframe, the MSH-NENT message is used for the new node to send network entry request, while the MSH-NCFG message obtains network parameters. In schedule control subframe, the MSH-CSCH message stores the centralized scheduling information, while the MSH-DSCH message stores the coordinated distributed scheduling information. Frames with the network control subframe happen periodically every Scheduling_Frames, assigned in the MSH-NCFG, frames; and all the other frames contain the schedule control subframes.
Every control subframe consists of MSH-CTRL-LEN transmission opportunities. Each transmission opportunity has seven OFDM symbols to carry one control message. The value of MSH_DSCH_NUM defines how many MSH-DSCH messages in one schedule control subframe. Therefore, the length of the MSH-CSCH parts is equal to MSH-CTRL-LEN MSH_DSCH_NUM.
Control Subframe Data Subframe Control Subframe Data Subframe
Frame N Frame N+1
Transmission Opportunity
Transmission Opportunity
... Minislot ... Minislot
CSCH ... CSCH DSCH ... DSCH Schedule Control
Subframe
NENT NCFG ... NCFG
Network Control Subframe
Data Burst From SSj
Data Burst From SSk
...
Fig. 1 The IEEE 802.16 frame structure for the mesh mode
Table 1 IEEE 802.16 mesh mode control messages and parameters Requester Granter
Time
Request
Grant
Confirm Message/Parameter Description
MSH-NENT Mesh network entry message MSH-NCFG Mesh network configuration message MSH-DSCH Mesh distributed schedule message MSH-CSCF Mesh centralized schedule configuration
message
MSH-CSCH Mesh centralized schedule message MSH-CTRL-LEN Control subframe length
MSH_DSCH_NUM Number of MSH-DSCH opportunities in schedule control subframe
Scheduling_Frames
Defines how many frames have a schedule control subframe between two frames with network control subframe
NextXmtMx A configuration parameter used to calculate NextXmtTimeInterval
NextXmtTime
Dictates the next MSH-NCFG or MSH-DSCH message transmission opportunity
NextXmtTimeInterval
Dictates the next MSH-NCFG or MSH-DSCH message eligibility interval for neighbors
XmtHoldoffTime
Dictates the number of MSH-NCFG.
MSH-DSCH transmission opportunities an SS can not transmit such messages after NextXmtTime
XmtHoldoffExponent A configuration parameter used to calculate XmtHoldoffTime
TempNextXmtTime
The temporary next transmission opportunity used in election-based transmission timing algorithm to compete with competing neighbors
EarliestSubsequentXm tTime
Estimates the earliest transmission opportunity an SS is eligible to transmit MSH-NCFG or MSH-DSCH message after NextXmtTime
Fig. 2 Three way handshaking procedure
3. The Enhanced Election-Based Transmission Timing (EEBTT) Mechanism
3.1 IEEE 802.16 Election-Based Transmission Timing (EBTT) Mechanism
IEEE 802.16 EBTT mechanism is used to schedule the MSH-NCFG and coordinated MSH-DSCH messages in control subframe, which supports the scheduling of regular broadcast transmissions in a multihop, mesh network without explicit schedule negotiations [5]. This mechanism is supposed to be collision-free within each node’s extended neighborhood. Moreover, it is completely distributed and need no central control from BS. Besides, it is also fair and robust due to the pseudo-random nature. To avoid the collision of MSH-DSCH messages in the schedule control subframe, every node needs to broadcast its next MSH-DSCH transmission time to its neighbors. The next MSH-DSCH transmission time of each node is described by two parameters, NextXmtMx and XmtHoldoffExponent, in IEEE 802.16 instead of broadcasting exact NextXmtTime. These two parameters are included in every MSH-DSCH message to form NextXmtTimeInterval which the exact NextXmtTime located in. The length of NextXmtTimeInterval is 2XmtHoldoffExponent , also known as The coordinated distributed scheduling algorithm
employs a three way handshaking to setup the transmission as shown in Fig. 2. The requester first sends a request with or without availability information of possible minislots assignment via its MSH-DSCH message to the granter. The granter then verifies if the request can be fulfilled. If so, it feedbacks a grant message with the assigned minislot information to the requester. The requester sends confirm message back to the granter once it accepts the grant message.
eligibility interval. Besides broadcasting own parameters via MSH-DSCH, every node also includes its all one-hop neighbors’ parameters. By doing so, every node is able to calculate the NextXmtTimeInterval of all nodes in the two-hop-neighborhood. After successful transmission of MSH-DSCH, a node must wait at least XmtHoldoffTime transmission opportunities to start its election procedure again.
NextXmtTimeInterval can be expressed by
and .
1
2
2XmtHoldoffExponentNextXmtMxNextXmtTime XmtHoldoffExponent NextXmtMx
2 4
XmtHoldoffExponent Time
XmtHoldoff
k
k L
Time XmtHoldoff 16
Time XmtHoldoff e
NextTmxTim tTime
bsequentXm
EarliestSu
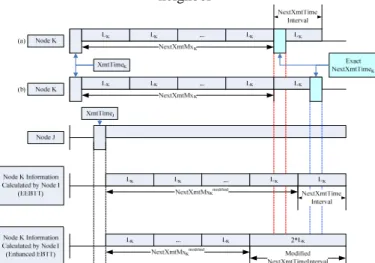
Every node calculates its NextXmtTime during the current transmission time using the distributed election algorithm defined in the standard. A node chooses the first transmission opportunity after the holdoff time as the temporary next transmission time, TempNextXmtTime, and competes at this opportunity with all possible competing nodes in the two-hop-neighborhood as shown in Fig. 3. Lk denotes the
length of NextTmxTimeInterval so
that . There are three types of
competing nodes: (1) node whose NextTmxTimeInterval includes the TempNextXmtTime (Node B); (2) node whose EarliestSubsequentXmtTime is the same as or before the
TempNextXmtTime, where
(Node C); and (3) node whose schedule information is unknown (Node D). Once the competing nodes are found, a pseudo-random election function is used to decide the winner.
If the node wins, it sets the TempNextXmtTime as its NextXmtTime and computes the related NextXmtMx by its XmtHoldoffExponent. Then the node broadcast the information to the neighbors via MSH-DSCH message. If the nodes looses, it chooses the next transmission opportunity and repeats the competing procedures until it wins.
Fig. 3 Competing Node Decision
3.2 Problem Statements of IEEE 802.16 EBTT Mechanism Since the calculation of NextXmtTimeInterval is based on NextXmtMx, XmtHoldoffExponent and the transmission opportunity when the MSH-DSCH message is received, the scheduling information of two-hop neighbors would be miscalculated as shown in Fig. 4. Node K is the neighbor of node J. Node I is the neighbor of node J; and node K is a two-hop neighbor of node I. Once node I receives MSH-DSCH message from Node J, it will calculate NextXmtTimeInterval of Node K based on XmtTimej instead of XmtTimek. Because XmtTimek is different from XmtTimej,
NextXmtTime of Node K has the chance to be miscalculated to cause the unexpected collision. Since there is no way for Node I to know the exact XmtTimek, the scheduling information of Node K should be modified before Node J broadcasting. [4]
proposes an extension to IEEE 802.16 EBTT (EEBTT) which modifies NextXmtMx using Eq. (1). However, this extension does not entirely solve the problem. Figure 5 shows the possible problem that EEBTT might experience. Node I, J and K have the same relationship as the previous case. Since the exact NextXmtTime is included in NextXmtTimeInterval, it might happen at the very first or last opportunity of NextXmtTimeInterval. Case a shows the situation that NextXmtTime occurs at the first transmission opportunity of NextXmtTimeInterval. On the other hand, case b represents an opposite situation that NextXmtTime occurs at the last transmission opportunity of NextXmtTimeInterval to case a.
Apparently, in case a, Node I still get wrong NextXmtTimeInterval estimation.
Fig. 4 Mismatch of the NextXmtTimeInterval from two-hop neighbor
Fig. 5 Comparison of EEBTT and Enhanced EBTT
3.3 The enhanced EBTT mechanism
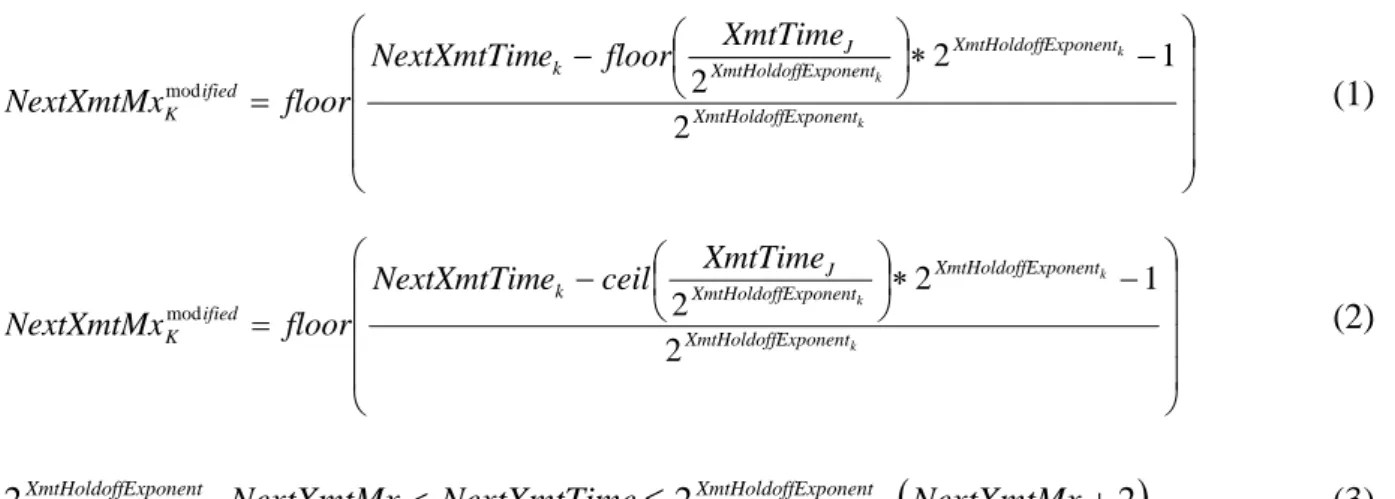
As the description of Section 3.2, both original IEEE 802.16 EBTT and EEBTT can not completely avoid the possible collision to MSH-DSCH messages of two-hop neighbors. We make two modified on the original IEEE 802.16 EBTT mechanism to solve the problem. First at all, NextXmtMx also has to be modified to adapt the difference between Node K and Node J (using the same notations as previous scenario) as Eq. (2).
k
k k
Exponent XmtHoldoff
Exponent XmtHoldoff Exponent
XmtHoldoff J k
ified K
XmtTime floor
e NextXmtTim floor
NextXmtMx
2
1 2 2
mod (1)
k
k k
Exponent XmtHoldoff
Exponent XmtHoldoff Exponent
XmtHoldoff J k
ified K
XmtTime ceil
e NextXmtTim floor
NextXmtMx
2
1 2 2
mod (2)
2
2
2XmtHoldoffExponentNextXmtMx NextXmtTime XmtHoldoffExponent NextXmtMx (3)
Since the difference between XmtTimeK and XmtTimeJ might be less than the length of NextXmtTimeInterval, which equals to , the inside floor function has to be replaced by the ceil function to prevent from missing while NextXmtTime happens on the early part of NextXmtTimeInterval. By doing so, the modified NextXmtMx might be negative if XmtTimeJ is close enough to NextXmtTimeK. To overcome this problem, if modified NextXmtMx is negative, it should be set to zero. However, the limited length of NextXmtTimeInterval still does not allow including all the possibilities of NextXmtTime from two-hop neighbors shown as Fig. 5. Due to this limitation, we propose Eq. (3) to modify NextXmtTimeInterval to include all the possibilities. The modification does not apply to the NextXmtTimeInterval calculations of all nodes but only the NextXmtTimeInterval calculations of two-hop neighbors.
Fortunately, we can get the hop information in the MSH-NCFG messages so there is no frame format changed.
Exponent XmtHoldoff
2
4. Simulation Results
In order to realize the performance of our enhancements on EBTT, the network simulator ns2 [6] is used. Thus we have developed a WiMAX mesh module for ns2 based on the IEEE 802.16 standard. The module is modified from the open resource of [7]. This module can support four kinds of transmission timing algorithms. The first one is the original IEEE 802.16 EBTT but it treats all two-hop neighbors as unknown nodes, denotes as unaware. With the second one, all exact NextXmtTime within the two-hop-neighborhood are known, denotes as aware. This one should be the best condition compared with others since it has the least competing nodes. The third one is EEBTT; and the last one is our proposed enhanced EBTT. All scenarios are based on an equilateral grid network consists of 36 nodes shown as Fig. 6.
The distance between neighboring nodes is 275m, and the transmission range is 280m. The other simulation parameters are listed in Table 2.
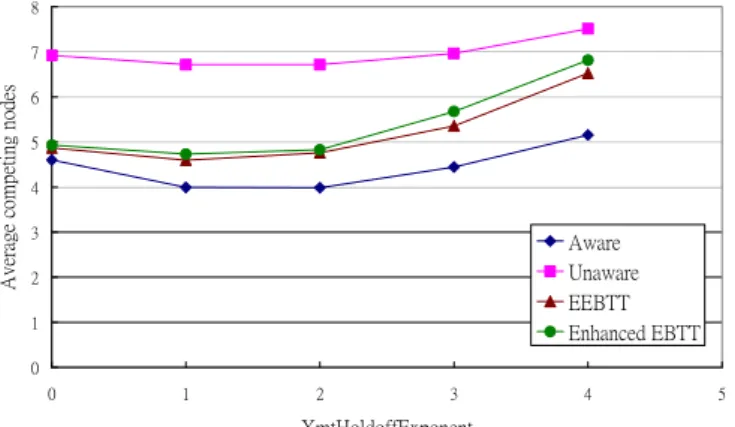
Fig. 7 shows the average competing nodes of four mechanisms with different XmtHoldoffExponent. Aware mechanism plays the best role, and unaware mechanism performs the worst. Our proposed enhanced EBTT is a little worse than EEBTT, because the enhanced EBTT extends regular NextXmtTimeInterval twice. Also, it is interesting that
no matter which mechanisms is chosen, all get the best results as XmtHoldoffExponet equals to 1~2; because the environment with zero XmtHoldoffExponent does not have enough space to spare MSH-DSCH messages within the short XmtHoldoffTime.
Once XmtHoldoffExponent is greater than 2, the large NextXmtTimeInterval makes the possibility of neighboring nodes overlapping their NextXmtTimeInterval higher, thus the number of average competing nodes increases.
Fig. 8 is the results of the average DSCH messages interval with different XmtHoldoffExponent. In this figure, XmtHoldoffTime dominates the results. Since XmtHoldoffTime increases exponentially by XmtHoldoffExponet, the average DSCH messages interval follows the same trend to increase.
Fig. 9 is the DSCH error ratio. All mechanisms except EEBTT experience no error during the simulation. Although the error ratio of EEBTT is less than 0.5%, it still has the impact on time-sensitive traffic.
Fig. 6 The simulated topology
Table 2 Simulation Parameters
Parameter Value Frame length 4ms
MSH_CTRL_LEN 4 MSH_DSCH_NUM 4 Scheduling Frames 4 Bandwidth 10MHz Simulation duration 100s