A General Privacy Preserving Auction Mechanism for Secondary Spectrum Markets
Qianyi Huang, Yang Gui, Fan Wu, Member, IEEE, Guihai Chen, Member, IEEE and Qian Zhang, Fellow, IEEE
Abstract—Auctions are among the best-known market-based tools to solve the problem of dynamic spectrum redistribution.
In recent years, a good number of strategy-proof auction mech- anisms have been proposed to improve spectrum utilization and to prevent market manipulation. However, the issue of privacy preservation in spectrum auctions remains open. On the one hand, truthful bidding reveals bidders’ private valuations of the spectrum. On the other hand, coverage/interference areas of the bidders may be revealed to determine conflicts.
In this paper, we present PISA, which is a PrIvacy preserving and Strategy-proof Auction mechanism for spectrum allocation.
PISA provides protection for both bid privacy and cover- age/interference area privacy leveraging a privacy preserving integer comparison protocol, which is well applicable in other contexts. We not only theoretically prove the privacy preserving properties of PISA, but also extensively evaluate its performance.
Evaluation results show that PISA achieves good spectrum allocation efficiency with light computation and communication overheads.
I. INTRODUCTION
I
NDUSTRY experts indicate that the fast growing wireless technology is being stalled by the scarcity of radio spec- trum [10]. This scarcity is often considered to be a result of the static and rigid spectrum allocation by the government. The spectrum may be idle when the primary users are not engaged in data transmission, while at the same time many unlicensed users are starving for radio spectrum. Such a static allocation mechanism can not fully utilize the limited spectrum. In order to improve spectrum utilization, secondary spectrum markets have emerged, where auctions are used to dynamically redistribute channels (e.g., [2, 8, 9, 12, 13, 33, 36, 37, 46]).Different from the auctions held by the government, auctions
Q. Huang is with the Department of Computer Science and Engineering, Hong Kong University of Science and Technology and Shanghai Key Labo- ratory of Scalable Computing and Systems, Department of Computer Science and Engineering, Shanghai Jiao Tong University (email: qhuangaa@ust.hk).
G. Yang, F. Wu, and G. Chen are with Shanghai Key Laboratory of Scalable Computing and Systems, the Department of Computer Science and Engi- neering, Shanghai Jiao Tong University (e-mail: yanggui1989@gmail.com;
fwu@cs.sjtu.edu.cn; gchen@cs.sjtu.edu.cn). Q. Zhang is with the Department of Computer Science and Engineering, Hong Kong University of Science and Technology (email: qianzh@cse.ust.hk).
F. Wu is the corresponding author.
This work was supported in part by grants from 973 project 2012CB316201, 2013CB329006, China NSF grant 61173156, 61422208, 61472252, 61272443 and 61133006, CCF-Intel Young Faculty Researcher Program and CCF- Tencent Open Fund, the Scientific Research Foundation for the Returned Overseas Chinese Scholars, Jiangsu Future Network Research Project No.
BY2013095-1-10, RGC under the contracts CERG 622613, 16212714, HKUST6/CRF/12R, and M-HKUST609/13, as well as the grant from Huawei- HKUST joint lab. The opinions, findings, conclusions, and recommendations expressed in this paper are those of the authors and do not necessarily reflect the views of the funding agencies or the government.
in secondary spectrum markets occur dynamically and more frequently. The auctioneers may be primary users who tend to lease their channels in order to receive proper payoff during their idle time. The bidders may be secondary wireless service providers that need spectrum to serve their subscribers, or a mobile device that needs spectrum to transmit data.
In spectrum auctions, strategy-proofness (defined in Section II) is the topic of major research efforts, which stimulates bidders to bid their true valuations of the spectrum. It e- liminates the overhead of gaming over each other and the auctioneer can allocate the channels to who value it the most.
However, different from the primary spectrum auctions where all bids are open and auction results are posted on FCC web pages, there are privacy concerns in secondary spectrum auctions. Truthful bidding divulges the bidder’s true valuations towards the spectrum, which are closely related to the profits of winning the spectrum. Bidders are not willing to share such information with other bidders or the auctioneer. Let us consider that the auctioneer is a cellular network provider, named A, and another cellular network provider B participates in the auction as a bidder to request for channels to transmit data. The bid may imply B’s economic situation, which is highly sensitive information. B is reluctant to disclose it to the auctioneer (i.e. A), who is a competitor in some sense.
Furthermore, corrupt auctioneers may exploit such knowledge to their advantage. For instance, the auctioneers/sellers may set the reserve price accordingly in future auctions to increase their own revenue. Unfortunately, most existing works fail to protect bid privacy in auction design.
Moreover, spectrum allocation may disclose the bidders’
coverage/interference areas. Spectrum is spatially reusable.
Two bidders distanced by space can simultaneously use the same channel for transmission. In auctions, bidders may be required to reveal their coverage/interference areas to the auc- tioneer to determine conflict. However, coverage/interference areas may divulge the location information of the bidders, especially when the bidders are mobile devices. It may also disclose other sensitive information, such as their business models and subscriber distribution. Thus, bidders are reluc- tant to share their coverage/interference information with the auctioneer.
Therefore, privacy preservation and strategy-proofness are both important factors in designing spectrum auctions. How- ever, there are several challenges. First, due to the spatial reusability of spectrum, well-separated bidders can share the same channel. Existing privacy preserving auctions (e.g., [4, 28]) are designed for traditional goods (e.g., paintings, jewelry), where each commodity can only be allocated to one
Auctioneer Agent
Bidders
Fig. 1. System Architecture
bidder. When it comes to spectrum auctions, they may either fail or lead to significant degradation of spectrum utilization.
Second, strategy-proofness and bid privacy are somewhat con- tradictory objectives. Strategy-proofness encourages bidders to reveal their true valuations of the spectrum, while bid privacy tends to prevent the auctioneer and other participants from learning the bidders’ true valuations. Third, different from conventional auctions, spectrum allocation is constrained by geographic conditions. The allocation process should satisfy the geographic constraints while preserving bidders’ cover- age/interference area privacy.
In this paper, we consider the problem of privacy preser- vation in spectrum auctions, and propose PISA, which is a PrIvacy preserving and Strategy-proof Auction mechanism for secondary spectrum markets. As shown in Figure 1, we introduce a third party (e.g., [21, 22, 32]), namely an agent, who acts as an intermediary between the bidders and the auctioneer. The agent should be non-profit and we require the agent to be a well-established organization. Therefore, some trustworthy non-profit organizations are suitable to play the role of the agent, such as Spectrum Bridge [26]. Although the agent may be a well-established party, bidders are still reluctant to share private information with any party, the agent being no exception. Thus, in PISA, the agent and the auctioneer cooperate to perform the auction, but neither of them can infer any sensitive information about the bidders without collusion. The essence of PISA lies in our privacy preserving bid comparison protocol, and we further extend the protocol to privately determine geographic conflict.
We summarize our contributions as follows:
1) To the best of our knowledge, PISA is the first strategy- proof spectrum auction mechanism that protects both bid privacy and coverage/interference area privacy without sacrificing social welfare.
2) We present a protocol to perform efficient comparison between integers without revealing their actual values.
Our protocol can compare arbitrary large integers and is well applicable in other contexts.
3) We implement PISA and extensively evaluate its perfor- mance. The evaluation results show that PISA achieves good channel utilization, with low computation and communication overhead.
The rest of the paper is organized as follows. In Section II, we review technical preliminaries. In Section III, we present the detailed design of basic PISA, which preserves bid privacy of the winners. In Section IV, we enhance PISA to provide stronger privacy protection (i.e., coverage/interference area
privacy and k-anonymous bid privacy for all bidders). We present our evaluation results in Section V. In Section VI, we briefly review related works. Finally, we conclude and point out future research directions in Section VII.
II. PRELIMINARIES
In this section, we first briefly review some solution con- cepts and present our auction model. Then, we define a generic strategy-proof spectrum auction mechanism. Finally, we introduce a useful homomorphic cryptosystem.
A. Solution Concepts
We recall the solution concepts used in our study. Let si
denote player i’s preference strategy and s−idenote the strat- egy profile of all the players except for player i. ui(si, s−i) is the utility of player i when the strategy of player i is si and the strategies of all other players are s−i.
Definition 1 (Incentive Compatible [23]). A mechanism is incentive compatible if for any strategy s′i ̸= si and any other players’ strategy profile s−i, the utility ui of the player i always satisfies the following condition:
ui(si, s−i)≥ ui(s′i, s−i).
Intuitively, in an incentive compatible mechanism, players can maximize their utilities by reporting truthful preference information, regardless of other players’ strategy profiles.
Next, we introduce another related concept.
Definition 2 (Individual Rational [23]). For any strategy si
and any other players’ strategy profile s−i, the utility ui of the player i always satisfies the following condition:
ui(si, s−i)≥ 0.
A mechanism is individually rational if each player always gets a non-negative utility, which means that each player can gain no less utility from faithful participation than non- participation. We now give the formal definition of strategy- proof mechanism.
Definition 3 (Strategy-Proof Mechanism [19][30]). A mech- anism is strategy-proof when it satisfies both incentive- compatibility and individual-rationality.
In a strategy-proof mechanism, misbehavior cannot result in any extra profit. Each player can maximize her utility by truthful participation.
In the field of privacy preservation, k-anonymity [29] is widely used to quantify the degree of privacy preservation (e.g., [39]). A scheme provides k-anonymous protection when a person cannot be distinguished from at least k− 1 other individuals.
Definition 4(k-anonymity [29]). A privacy preserving scheme satisfies k-anonymity, if a participant cannot be identified by the sensitive information with probability higher than 1/k.
B. Auction Model
We model the procedure of spectrum allocation as a sealed- bid auction, involving an auctioneer, an agent, and a number of bidders. For clarity, we assume that there is a single channel to be shared among the bidders1.
The auctioneer may be a primary user who tends to lease her idle channel to a group of conflict-free secondary users, in order to receive proper payoff during her idle time. The auctioneer may also be a specialized third-party platform for spectrum management, such as Spectrum Bridge [26]. Bidders simultaneously submit their encrypted bidding tuples via the agent to the auctioneer. The auctioneer decides the winners and their charges.
We consider that there is a setB = {1, 2, · · · , z} of bidders.
Let ⃗v = (v1, v2,· · · , vz) denote the valuation profiles of the bidders, which is their private information. Accordingly, the bidders’ bidding profile is denoted by ⃗b = (b1, b2,· · · , bz).
Let ⃗x = (x1, x2,· · · , xz) and ⃗y = (y1, y2,· · · , yz) denote the vector of bidders’ latitudes and longitudes, respectively.
Bidder i can share the channel with bidder j, if their cover- age/interference areas do not overlap.
The auctioneer determines the charging profile
⃗
p = (p1, p2,· · · , pz) and the allocation profile
⃗a = (a1, a2,· · · , az), where ai= 1 indicates that bidder i is allocated the channel, while ai = 0 indicates not. The utility of bidder i can be defined as
ui= (vi− pi)ai.
The goal of all bidders is to maximize their own utilities. Here, we assume that the bidders do not collude with each other.
In contrast to the bidders, the overall objective of the auction is to guarantee strategy-proofness, and to maximize channel allocation efficiency subject to the conflicting conditions.
C. A Generic Spectrum Auction Scheme
As pointed out in [40], the spatial interference constraints make the problem of finding the optimal allocation in the above auction model NP-complete. A practical solution is to resort to monotonic allocation in order to improve computation efficiency, and to apply critical charging to guarantee strategy- proofness. In this subsection, we present a representative auction scheme that achieves both strategy-proofness and computational efficiency.
We model the geographic conflicts of the bidders as a con- flict graphG. On the conflict graph, each bidder is represented by a vertex. Two bidders (vertices) are connected if their coverage/interference areas overlap. Two important concepts are critical neighbor and critical value.
Definition 5 (Critical Neighbor [40]). Given G \ {i}, the critical neighbor CN (i) of bidder i is a neighbor of i where if i bids lower than CN (i), i will not be allocated, and if i bids higher than CN (i), i will be allocated.
1For multi-channel case, we can change the monotonic allocation algorithm and the critical charging algorithm according to [40], and apply our privacy preserving bid comparison protocol.
Definition 6(Critical Value [40]). The critical value of bidder i is defined as the bid of CN (i); if CN (i) does not exist, the critical value of i is 0.
Algorithm 1 describes the monotonic allocation procedure, whereA denotes the set of available bidders and N(i) denotes the set of neighbors of bidder i in G. Lines 2-6 iteratively allocate the channel to the highest bidder i inA, and eliminate i and her neighbors from further consideration. The algorithm stops when there is no bidder left inA.
Algorithm 1 Monotonic Allocation Algorithm
Input:Conflict graphG, bidder set B, and bidding profile
⃗b.
Output: Allocation profile ⃗a.
1: A ← B; ⃗a ← 0z.
2: while A ̸= ∅ do
3: i← argmax
j∈A (bj).
4: ai← 1.
5: A ← A \ (N(i) ∪ {i}).
6: end while Return ⃗a.
Algorithm 2 shows the critical charging procedure. Lines 5-11 determine the critical value of bidder i. Each winner is charged with his/her critical value. In the case of a tie, we may break the tie either randomly or by the bidders’ identifiers.
Algorithm 2 Critical Charging Algorithm
Input: Conflict graphG, bidder set B, bidding profile ⃗b, allocation profile ⃗a, and bidder i.
Output: Payment pi.
1: if ai= 0 then
2: Return 0.
3: end if
4: A ← B \ {i}.
5: while A ̸= ∅ do
6: k← argmax
j∈A (bj).
7: if k∈ N(i) then ◃ CN (i) = k.
8: Return bk.
9: end if
10: A ← A \ (N(k) ∪ {k}).
11: end while Return 0.
Here we have the first theorem. Please refer to [40] for the proof.
Theorem 1. The generic spectrum auction mechanism is strategy-proof.
We note that the generic spectrum auction mechanism may reveal the bidders’ private information to the auctioneer.
We present our approaches to protect bidders’ privacy in Section III and Section IV.
D. Boneh-Goh-Nissim (BGN) cryptosystem
Homomorphic encryption is a form of encryption that enables specific types of computations to be carried out
on ciphertexts, and obtain a new ciphertext, which can be decrypted to match the result of computations applied directly to the original plaintexts.
In this work, we adopt Boneh-Goh-Nissim (BGN) cryp- tosystem [3]. It supports computations of unlimited number of additions with at most one multiplication. Thus it can evaluate quadratic multi-variate polynomials on ciphertexts.
Before introducing the BGN cryptosystem, we recall bilin- ear map and bilinear group, which are the bases of the BGN cryptosystem.
Definition 7(Bilinear Map [3]). LetG1andG2be two cyclic groups of order n, for some large n. A map e :G1×G1→ G2
is said to be bilinear if
e(Pa, Qb) = e(P, Q)ab, for all P, Q∈ G1 and a, b∈ Z.
Definition 8 (Bilinear Group [3]). G1 is a bilinear group if there exists a group G2and a bilinear map e, s.t.,
1) G1 andG2are two multiplicative cyclic groups of finite order n.
2) g is a generator ofG1.
3) e : G1× G1 → G2 is a bilinear map and e(g, g) is a generator ofG2.
Given n, [3] presents an approach to constructing a bilinear group of order n. Due to limitations in space, we do not elaborate on it here. Next, we describe the three algorithms making up the BGN cryptosystem.
KeyGen(τ ):Given a security parameter τ∈ Z+, generate two random τ -bit primes q1, q2, and set n = q1q2∈ Z. Generate a bilinear group G1 of order n as described in [3]. Let e : G1× G1→ G2 be the bilinear map.
Randomly pick two generators g, u from G1 and set h = uq2. Then h is a random generator of a q1-order subgroup of G1. The public key isPK = (n, G1,G2, e, g, h). The private key is SK = q1.
Encrypt(PK, m): We assume that the message space consists of integers from {0, 1, · · · , T } with T < q2. To encrypt a message m with the public keyPK, pick a random integer r from Zn, and compute
C = gmhr∈ G1. Here, C is the ciphertext of m.
Decrypt(SK, C): To decrypt a ciphertext C using the private key SK = q1, note that
Cq1= (gmhr)q1= (gq1)m.
To recover m, it suffices to compute the discrete log of Cq1 in base gq1. Although it appears inefficient to do decryption, BGN cryptosystem is well suited to our scenario. In our application, we only need to decide whether a ciphertext is an encryption of 0 or not.
Next, we show the homomorphic properties of BGN cryp- tosystem. Given ciphertexts C1 = gm1hr1 ∈ G1 and C2 = gm2hr2 ∈ G1,
C1⊕C2= C1C2hr= gm1hr1gm2hr2·hr= gm1+m2hr1+r2+r
is the ciphertext of m1+ m2 for a random r∈ Zn.
Furthermore, BGN cryptosystem allows one multiplication using the bilinear map. For h is of order q1, we rewrite h = gαq2 for some unknown α ∈ Z. Set ˆg = e(g, g) and ˆh = e(g, h) = ˆgαq2. Hence, ˆg is of order n and ˆh is of order q1. Pick a random r′∈ Zn, then
C1⊗ C2 = e(C1, C2)ˆhr′= e(gm1hr1, gm2hr2)ˆhr′
= e(gm1+αq2r1, gm2+αq2r2)ˆhr′
= e(g, g)(m1+αq2r1)(m2+αq2r2)ˆhr′
= e(g, g)m1m2e(g, g)αq2(m1r2+m2r1+αq2r1r2)ˆhr′
= e(g, g)m1m2e(g, h)m1r2+m2r1+αq2r1r2ˆhr′
= gˆm1m2ˆhr¯∈ G2
is the ciphertext of m1× m2, where ¯r = m1r2+ m2r1+ αq2r1r2 + r′. We note that the system is still additively homomorphic inG2.
III. BASICPISA
In this section, we first introduce our privacy preserving bid comparison protocol. Then we introduce our spectrum auction mechanism, namely PISA, which preserves the win- ners’ bid privacy and achieves strategy-proofness. Here we assume that the auctioneer has full knowledge of bidders’
coverage/interference areas to construct the conflict graph.
In Section IV, we enhance our design to provide stronger privacy protection, that is, coverage/interference area privacy, k-anonymous bid privacy for both winners and losers.
A. Privacy Preserving Bid Comparison
To determine the auction winners, it suffices to let the auctioneer know whether bi is higher than bj, for any i and j from B, without revealing the exact values of bi and bj. This problem is a variant of secure comparison. A generic solution is based on Yao’s garbled circuits [38], which have a predefined number of inputs. However, in spectrum auctions, it is difficult to determine the number of bidders before the bidding phase. Hence Yao’s approach is not practical here.
Therefore, we design a more flexible approach. Our protocol is based on bit-wise comparison, allowing us to compare arbitrary large integers. We describe it separately for clarity, and it is well applicable in other contexts.
We consider two l-bit binary bids bi = (blibli−1· · · b1i)2 and bj = (bljblj−1· · · b1j)2, where b1i and b1j denote the least significant bits, while bli and blj denote the most significant bits. For each integer k∈ [1, l], we define
ωkij= (bki − bkj)2= (bki)2+ (bkj)2− 2bkibkj, (1)
λkij = ζijk[(bki)2− (bkj)2+ 1 +
∑l r=k+1
ωrij], (2)
where ζijk ∈R Z+ is a random positive number. In this subsection, l, k and t are all integers. Then, we get the following lemma.
Lemma 1. For any i, j ∈ B, we have bi < bj, if and only if there exists exactly one k∈ [1, l], where λkij = 0.
Proof. For any t∈ [1, l], we have ζijt > 0 and ωtij = (bti− btj)2≥ 0, (bti)2− (btj)2+ 1≥ 0 − 1 + 1 = 0,
hence λtij ≥ 0. Next, we prove the necessary and sufficient conditions.
• Given bi< bj, there exists k∈ [1, l], such that bki = 0 <
bkj = 1 and bti= btj for any t∈ [k + 1, l]. Consequently, ωijk = (bki − bkj)2= 1,
and
ωtij= (bti− btj)2= 0,∀t ∈ [k + 1, l].
Hence,
λkij = ζijk[02− 12+ 1 + 0] = 0.
We further distinguish two cases.
– For t∈ [1, k − 1], since ωijk = 1, we have
∑l r=t+1
ωrij> 0.
Hence, λtij > 0.
– For t∈ [k + 1, l],
(bti)2− (btj)2+ 1 = 1 > 0.
Hence, λtij > 0.
Therefore, there exists exactly one k∈ [1, l], where λkij= 0.
• Given λkij = 0, for ζijk > 0, we can infer that
(bki)2− (bkj)2+ 1 = 0∧
∑l r=k+1
ωijr = 0.
Hence, bki = 0 < bkj = 1 and bti= btjfor any t∈ [k+1, l].
Therefore, bi< bj. This completes our proof.
We note that both Equation (1) and (2) are quadratic polynomials in bki and bkj. Consequently, we can evaluate them using the BGN cryptosystem. With Lemma 1, we can compare two bids without knowing their exact values.
B. Design Details
In basic PISA, bidders submit their encrypted bidding tuples to the agent who preprocesses them before transferring them to the auctioneer. The auctioneer can decrypt the encrypted tuples and find only the necessary information to run the auction, without inferring any nonessential information. In this subsection, we present the design details of basic PISA, which comprises four phases shown as follows.
Phase 1: Initialization
Before the auction, the auctioneer sets up the parameters for BGN cryptosystem and runs KeyGen(τ ) (as shown in Section II-D). Then, the public keyPK = (n, G1,G2, e, g, h) is announced, while the private key SK = q1 is not revealed.
The auctioneer also sets the possible bidding range of integers R = [bmin, bmax], where bminand bmaxare two l-bit binaries.
Phase 2: Bidding
In the bidding phase, each bidder i decides her bid bi∈ R according to her valuation vi. The bidder i encrypts every bit bki from her bid bi with the auctioneer’s public keyPK:
E(bki) = Encrypt(PK, bki), k∈ [1, l],
where Encrypt() is the encryption function defined in Section II-D. For ease of expression, we denote the series of encrypted bits of bi as
E( ˜bi) = (E(bki))k∈[1,l].
Then, the bidder i sends [i, E( ˜bi)] as her bidding tuple to the agent.
Phase 3: Preprocessing
After receiving all the encrypted bidding tuples from the bidders, the agent preprocesses the ciphertexts.
For each bidder i, the agent appends E(˜i) to the least significant end of E( ˜bi). Here, similar with E( ˜bi), E(˜i) is the series of encrypted bits of bidder i’s binary ID number.
Now the bidding tuple turns out to be:
[i, E( ˜bi)||E(˜i)],
where|| is the concatenation operator. The suffix does not affect the comparison result of the two bids, except the case of tie. With the suffix, the tie can be broken according to the bidders’ ID number.
Then, for any pair of bidders i and j, the agent computes:
E(ωijk) = E((bki)2+ (bkj)2− 2bkibkj)
= e(E(bki), E(bki))× e(E(bkj), E(bkj))
×e(E(bki), E(bkj))−2,
E(λkij) = E((bki)2− (bkj)2+ 1 +
l+⌈log∑2z⌉ r=k+1
ωrij)ζkij
= e(E(bki), E(bki))ζkij× e(E(bkj), E(bkj))−ζkij
×e(g, g)ζijk ×
l+⌈log∏2z⌉ r=k+1
E(ωijr)ζijk, (3)
for each k∈ [1, l + ⌈log2z⌉] and ζijk ∈RZ+. Here, ⌈log2z⌉ is the length of bidders’ binary ID number, since there are z bidders in total.
Finally, the bidder sends the following tuples to the auc- tioneer:
[i, j, E(˜λij)],∀i, j ∈ B ∧ i ̸= j,
where E(˜λij) is the list of E(λkij) for k∈ [1, l+⌈log2z⌉]. We note that the elements in E(˜λij) can be randomly permuted.
Phase 4: Opening
(a) Conflict graph construction:The auctioneer can con- struct the conflict graphG = (V, E) according to bidders’ geo- graphic distribution, where each bidder is represented by a ver- tex. Two vertices are connected if their coverage/interference areas overlap. Here, N (f ) ={h ∈ V|(f, h) ∈ E}.
(b) Monotonic allocation: For each edge (f, h) ∈ E, the auctioneer can decrypt E(˜λf h), and check whether it contains a λkf hthat is equal to 0 for k∈ [1, l+⌈log2z⌉]. If so, bf < bh; otherwise, bf > bh.
We can update Algorithm 1 to protect the bidders’ bidding values. Algorithm 3 shows the privacy preserving winner allocation procedure. We define matrix S = [˜λf h]f,h∈V. In lines 2-6, we iteratively pick bidder f , who does not have 0 in ˜λf h, for any h ∈ A \ {f} (i.e., bidder f has the highest bid in A); and eliminate f and her neighbors from A. When the setA becomes empty, the algorithm outputs the allocation profile ⃗a.
Algorithm 3 Privacy Preserving Allocation Algorithm Input:Conflict graph (V, E) and matrix S = [˜λf h]f,h∈V. Output: Allocation profile ⃗a.
1: A ← V; ⃗a ← 0z.
2: whileA ̸= ∅ do
3: Pick f ∈ A, s.t., @h ∈ A\{f} and k ∈ [1, l+⌈log2z⌉], such that λkf h= 0.
4: af ← 1.
5: A ← A \ (N(f) ∪ {f}).
6: end while Return ⃗a.
(c) Critical charging: Since the auctioneer is not given the encrypted bids from the agent, the charges to the winners cannot be computed directly according to Algorithm 2. How- ever, the auctioneer can determine the critical neighbor of each winner.
Algorithm 4 Privacy Preserving Critical Neighbor Determi- nation Algorithm— CN (f )
Input:Conflict graph (V, E), matrix S = [˜λf h]f,h∈V, and bidder f .
Output: Critical neighbor CN (f ).
1: A ← V \ {f}.
2: whileA ̸= ∅ do
3: Pick f′ ∈ A, s.t., @h ∈ A \ {f′} and k ∈ [1, l +
⌈log2z⌉], such that λkf′h= 0.
4: if f ∈ N(f′) then
5: Return f′.
6: end if
7: A ← A \ (N(f′)∪ {f′}).
8: end while Return N U LL.
Algorithm 4 shows our privacy preserving critical neighbor determination procedure. In lines 2-8, we determine bidder f ’s neighbor f′, who would be allocated the channel if f is absent from the auction. Then, the algorithm outputs f′ as the critical neighbor of f . If no such f′ exists, the algorithm returns N U LL. We note that Algorithm 4 differs from Algorithm 2, because it outputs the bidder f ’s critical neighbor CN (f ), instead of the critical value.
(d) Outcome announcement:We denote the vector of crit- ical neighbors by −−→
CN = (CN (f ))f∈V:af=1. The auctioneer
needs to resort to the agent for the encrypted bids of the critical neighbors. Next, the agent replies with a vector of encrypted bids of the critical neighbors
−
→C = (E(˜bi))i∈−−→CN.
Finally, the auctioneer can decrypt the encrypted critical bids in−→
C , and announce the winners together with their charges.
C. Analysis
We consider the computational complexity for the bidders, the agent and the auctioneer, respectively: bidders have to carry out BGN encryption for each bit in their bids. Thus, each bidder has to carry out encryption l times, where l is the number of bits in the bid; the agent has to carry out pre-processing for each pair of bidders, so the computational complexity of the agent is O(
z2l)
. Here, z is the number of bidders; both the allocation algorithm and charging algorithm run at O(
z2l)
, thus the computational complexity of the auctioneer is O(
z2l) .
The strategy-proofness of PISA is inherited from the generic auction mechanism. We omit the proof here, and directly draw the following conclusion.
Theorem 2. PISA satisfies strategy-proofness.
Besides privacy preservation and strategy-proofness, PISA also achieves the following nice properties.
1) Compared with the generic spectrum auction scheme, PISA protects bidders’ privacy without sacrificing spec- trum allocation efficiency.
2) In PISA, bidders are allowed to choose their bids from a contiguous integer range. Compared with existing mechanisms (e.g., [15]), in which bids are limited to a small set of predefined values, PISA provides bidders with more bidding flexibility.
3) PISA preserves the communication pattern of an auction protocol. In PISA, bidders are not required to communi- cate with each other. After submitting the bidding tuples to the agent, they are free from burdensome computation and communication.
Basic PISA is based on our privacy preserving bid com- parison protocol, hence the auctioneer can compare two bids without knowing their values. As an intermediary, the agent can not decrypt the encrypted bidding tuples to learn the bids.
Therefore, we protect the bid privacy of winners against both the auctioneer and the agent. However, the bids of critical neighbors are revealed as the charges of the winners. In the next section, we enhance our design to thwart such privacy breaches and provide protection for coverage/interference area privacy.
IV. EXTENDEDPISA
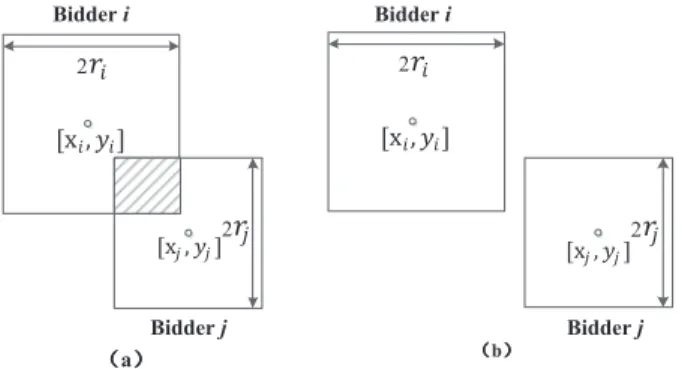
In this section, we intend to provide k-anonymous bid privacy for both winners and losers, together with protec- tion for coverage/interference area privacy. To preserve cov- erage/interference area privacy, we generalize each bidder’s coverage/interference area to a square with side length 2ri.
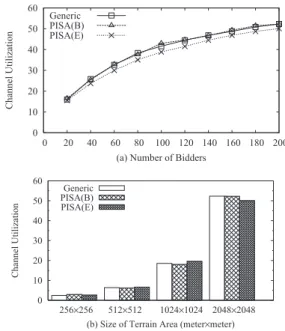
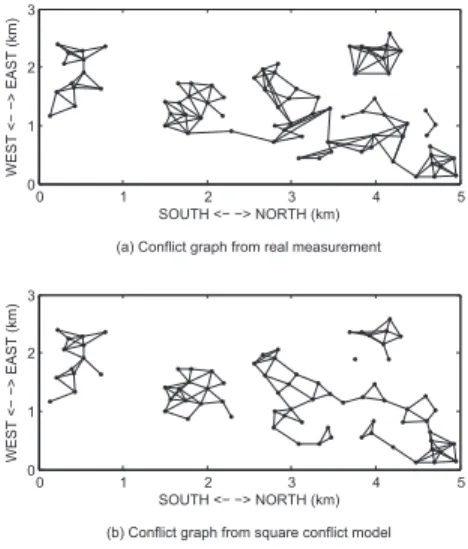
As shown in Figure 2, bidder i and j are conflicting bidders in case (a), while they can share the same channel in case (b). Compare with the commonly used circular conflict areas, this assumption may overestimate interference. To evaluate the impact of this assumption on channel allocation, in Section V, we compare our square conflict model with a conflict graph obtained from a real measurement.
˄a˅ ˄b˅
ሾ݅ǡ ݕ݅ሿ ሾ݆ǡ ݕ݆ሿ
Bidder i Bidder i
Bidder j Bidder j
ݎ݅ 2
ݎ݆ 2
ሾ݅ǡ ݕ݅ሿ ݎ݅ 2
ሾ݆ǡ ݕ݆ሿ 2ݎ݆
Fig. 2. Square coverage/interference area examples. In case (a), bidder i and j have conflict. In case (b), the two bidders do not have conflict.
We define
x◃i = xi+ ri, x▹i = xi− ri, y△i = yi+ ri, y▽i = yi− ri,
where x◃i, x▹i, y△i, and yi▽ are t-bit binaries. Bidder i and j are out of the coverage/interference range of each other, if the following condition holds:
(x◃i < x▹j∨ x▹i > x◃j)∨ (y△i < yj▽∨ yi▽> y△j) = T RU E. (4) Given Lemma 1, we can evaluate x◃i < x▹j, x▹i > x◃j, y△i < y▽j, and y▽i > y△j privately. Due to limitations of space, we only focus on the differences in phases of bidding, preprocessing, and opening.
A. Design Details
Besides the processing of coverage/interference areas, the key difference lies in the preprocessing phase, where the agent performs a secret permutation to anonymize the bidders.
Phase 1: Initialization
It is similar to the basic PISA in Section III-B.
Phase 2: Bidding
In addition to E(˜bi), each bidder i also calculates E(˜x◃i), E(˜x▹i), E(˜yi△), and E(˜yi▽). Then, the bidder sends
[i, E(˜bi), E(˜x◃i), E(˜x▹i), E(˜yi△), E(˜yi▽)]
to the agent as the bidding tuple.
Phase 3: Preprocessing
For any pair of bidders i and j, the agent computes E(˜λij) as specified in Section III-B. In addition, the agent calculates
E(αkij) = E((x◃ki )2− (x▹kj )2+ 1 +
∑t r=k+1
(x◃ri − x▹rj )2)ξijk,
for each k ∈ [1, t] and ξijk ∈R Z+. Same as before, we let E( ˜αij) = (E(αkij))k∈[1,t]. The agent also carries out the calculations on (x▹i, x◃j), (yi△, yj▽) and (yi▽, y△j), and results in E( ˜βij), E(˜γij), and E(˜δij), respectively.
After finishing the above calculations, the agent carries out a secret permutation π on the results to make them anony- mous to the auctioneer. Then, the agent sends the following anonymous tuples to the auctioneer:
[π(i), π(j), E(˜λij), E( ˜αij), E( ˜βij), E(˜γij), E(˜δij)], for each i, j∈ B and i ̸= j.
Phase 4: Opening
The auctioneer decrypts E( ˜αf h), E( ˜βf h), E(˜γf h), and E(˜δf h), to get ˜αf h, ˜βf h, ˜γf h, and ˜δf h, respectively. We note that bidder f and h cannot share the channel, if the following condition holds:
Ωf h= (
0 /∈ ˜αf h∧ 0 ∈ ˜βf h∧ 0 /∈ ˜γf h∧ 0 ∈ ˜δf h
)
= T RU E.
(5) The auctioneer can construct the conflict graph G = (V, E), where
V = {π(i)|i ∈ B} ,
E = {(f, h)|f, h ∈ V ∧ Ωf h= T RU E} .
Then the auctioneer carries out Algorithm 3 and Algorithm 4 on permuted bidders. Algorithm 3 outputs allocation profile
⃗a′on permuted bidders, while Algorithm 4 returns the permut- ed critical neighbors. Since the auctioneer is unaware of the agent’s perturbation π :B → V, the original identifiers of the bidders remain anonymous. Let−→
W = (f )f∈V:a′
f=1 denote the vector of permuted winners, and−−→
CN = (CN (f ))f∈V:a′f=1de- note the corresponding vector of permuted critical neighbors.
To prevent the agent from finding one-to-one correspondence between the winners and their critical neighbors, the auctioneer permutates−−→
CN to get−−→
CN′. The auctioneer needs to resort to the agent for the winners’ original identifiers and the encrypted bids of the critical neighbors, by sending −→
W and −−→
CN′ to the agent. Next, the agent replies with a vector of winner identifiers
−→
W′= (i)π(i)∈−W→,
and a vector of encrypted bids of the critical neighbors
−
→C′ = (E(˜bi))π(i)
∈−−→CN′.
Finally, the auctioneer can decrypt the encrypted critical bids in −→
C′, map the critical bids to the winners by reversing the permutation done on−−→
CN , and announce the winners together with their charges.
B. Illustrative Example
The following example may help to illustrate how extended PISA works. Suppose there are five bidders 1, 2, 3, 4 and 5, located at (6, 10), (10, 14), (10, 6), (14, 10) and (10, 16) respectively. They are supposed to bid higher than 0, but lower than 16. Each of them has a valuation of the channel in binary form: b1= 00102, b2= 01002, b3 = 10102, b4 = 01012, b5=
01102. For simplicity, we assume r1= r2= r3= r4 = r5= 5.
In the auction, each bidder submits an encrypted bid- ding tuple, which contains his/her encrypted bid and cover- age/interference boundaries. The bidding tuple follows the for- mat of [i, E(˜bi), E(˜x◃i), E(˜x▹i), E(˜yi△), E(˜yi▽)]. For instance, bidder 1 submits
[1, E(]0010), E(]1011), E(]0001), E(]1111), E(]0101)]
to the agent. Here 1 is the identity, b1= 00102,
x◃1= 6 + r1= 10112, x▹1= 6− r1= 00012, y△1 = 10 + r1= 11112, y1▽= 10− r1= 01012. Similarly, bidder 3 submits
[3, E(]1010), E(]1111), E(]0101), E(]1011), E(]0001)].
After collecting all the bids, the agent carries out preprocessing as specified in Phase 3. For simplicity, we omit the suffix.
Then, the agent anonymizes all the tuples, and sends the permuted ones to the auctioneer. For example, the agent sends the following information about bidders 1 and 3 to the auctioneer:
[4′(3), 5′(1), E(2× 2, 4 × 2, 1 × 2, 3 × 2),
E(4× 2, 5 × 3, 3 × 4, 1 × 4), E(3 × 0, 5 × 3, 3 × 2, 2 × 4), E(7× 2, 3 × 1, 2 × 4, 2 × 4), E(3 × 0, 3 × 1, 2 × 2, 2 × 4)].
Here, the numbers inside parentheses in the first two terms are the bidders’ true identifiers, which are hidden from the auctioneer. Furthermore, π(1) = 5′ and π(3) = 4′ are the anonymous identification after the secret permutation π. The numbers in bold are the random numbers generated by the agent (e.g., 2, 4, 1, 3 in the third term correspond to the random number ζij in Equation (3)).
The auctioneer can decrypt the ciphertexts and do the comparison. In this example,
Ω4′5′ = [0 /∈ (4 × 2, 5 × 3, 3 × 4, 1 × 4)]
∧ [0 ∈ (3 × 0, 5 × 3, 3 × 2, 2 × 4)]
∧ [0 /∈ (7 × 2, 3 × 1, 2 × 4, 2 × 4)]
∧ [0 ∈ (3 × 0, 3 × 1, 2 × 2, 2 × 4)]
= T RU E.
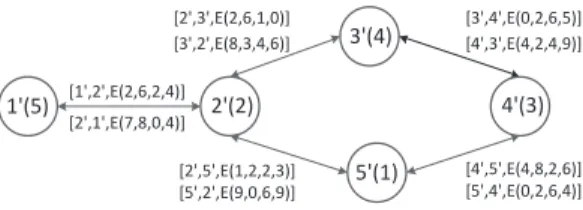
Thus bidder 4′and 5′cannot share the channel. The auctioneer constructs the conflict graph based on the comparison results, as shown in Figure 3. The term by each edge (f, h) ∈ E denotes [f, h, E(˜λf h)] (elements in E(˜λf h) are multiplied with random positive numbers and are randomly perturbed).
From Figure 3, the auctioneer can learn that b1′> b2′,{b1′, b3′} > b2′ > b5′, b4′ > b3′ > b2′, b4′ >{b3′, b5′}, {b2′, b4′} > b5′.
[2',1',E(7,8,0,4)]
1'(5) 2'(2)
3'(4)
4'(3)
5'(1) [1',2',E(2,6,2,4)]
[2',5',E(1,2,2,3)]
[5',2',E(9,0,6,9)]
[2',3',E(2,6,1,0)]
[3',2',E(8,3,4,6)]
[3',4',E(0,2,6,5)]
[4',3',E(4,2,4,9)]
[4',5',E(4,8,2,6)]
[5',4',E(0,2,6,4)]
Fig. 3. Conflict graph constructed by the auctioneer, without revealing actual coverage/interference areas of the bidders.
Then the auctioneer can determine winners and their criti- cal neighbors using Algorithm 3 and Algorithm 4, respec- tively. The winners turn out to be bidder 1′ and 4′, and the corresponding critical neighbors are bidder 2′ and 3′, respectively. The auctioneer permutes −−→
CN = {2′, 3′} to get
−−→CN′ ={3′, 2′}.
Next the auctioneer consults the agent with −→
W = {1′, 4′} and−−→
CN′ ={3′, 2′}, and the agent replies with answer 5, 3, E(˜b4), and E(˜b2). Finally, the auctioneer announces bidder 3 and 5 as winners, with charges 5 and 4, respectively.
C. Analysis
It is evident that extended PISA inherits the nice properties from basic PISA, including strategy-proofness and the three properties listed in Section III-C. To avoid redundancy, we do not elaborate on them again here. In this subsection, we demonstrate some other nice properties of our auction mechanism.
Theorem 3. Extended PISA guarantees k-anonymity for bid privacy, where k =|−−→
CN|.
Proof. We distinguish the following two cases:
Case 1: Bidder i is a critical neighbor, i.e., π(i) ∈ −−→
CN . We consider from the perspectives of both the agent and the auctioneer.
On the one hand, the agent cannot decrypt bidder i’s bidding tuple without the secret key SK, hence the agent cannot find out what the bid is. When the auctioneer consults the agent with −−→
CN′ in the opening phase, the agent learns that bidder i is one of the critical neighbors. However, the order of bidders in −−→
CN′ has been permutated by the auctioneer.
The agent does not know which bidder is which winner’s critical neighbor. When the auctioneer announces the charges for winners, bidder i’s bid is hidden among |−−→
CN| charges.
Thus, the agent cannot identify bidder i’s bid with probability higher than 1/|−−→
CN|.
On the other hand, although the auctioneer can decrypt the bidding tuples, they cannot be linked with the bidders, because all the bidding tuples are anonymized by the agent. The true identifier of a critical neighbor is hidden among z−|−→
W| losers.
Thus, the auctioneer cannot identify bidder i with probability higher than 1/(z− |−→
W|).
For the set of critical neighbors is a subset of losers (z− |−→
W| ≥ |−−→
CN|), both the agent and the auctioneer cannot identify bidder i’s bid with probability higher than 1/|−−→
CN|.
Case 2:Bidder i is not a critical neighbor, i.e., π(i) /∈−−→
CN .