Performance Analysis of Reliable MAC-Layer Multicast for IEEE 802.11 Wireless LANs
Chong-Wei Bao and Wanjiun Liao
Department of Electrical Engineering
National Taiwan University
Taipei, Taiwan
Email: wjliao@ ntu.edu.tw
Abstract- In this paper, we study reliable multicast at the MAC
layer for IEEE 802.11 Wireless LANs. In IEEE 802.11, multicast transmissions are unreliable in the sense that multicast frames are transmitted from the Access Point (AP) without an ACK being returned from each receiver as in unicast transmissions. As a result, transmitted multicast frames may be lost due to collisions or errors. There are two types of reliable multicast at the MAC layer proposed for 802.11 in the literature: one is ACK-based and the other is a leader-based mechanism. For the ACK-based mechanism, the AP monitors the frame reception progress of all receivers and retransmits frames whenever no ACK is received from any receiver; for leader-based mechanism, the AP retransmits frames only when no ACK frame is received from the selected leader. We analyze their performance in terms of frame holding time at the AP, and conduct simulation to validate our analytical model. We also propose a new channel acquisition and multicast notification mechanism called RTS/CTS/SEQ to improve the performance of existing work for reliable multicast in IEEE 802.11 WLANs.
Keywords: reliable multicast, IEEE 802.11 WLANs
I. INTRODUCTION
In this paper, we analyze the performance of two reliable MAC-layer multicast mechanisms for IEEE 802.11 Wireless LANs. In IEEE 802.11 [1], multicast transmissions are unreliable in the sense that multicast frames are transmitted from the Access Point without an ACK being returned from each receiver as in unicast transmissions. As a result, transmitted multicast frames may be lost due to collisions or errors. While reliable multicast in the transport layer has been an active research topic, this issue in the MAC layer for IEEE 802.11, has drawn much less attention. Currently, very few protocols, such as Leader-Based Protocol (LBP) [2], have been proposed for IEEE 802.11-based Wireless LANs.
LBP works as follows. A receiver is selected as the leader for the multicast group. The AP then sends a multicast RTS (denoted as m-RTS) frame to all receivers, and only the leader transmits a multicast CTS (denoted as m-CTS) frame in reply to the AP. The AP is then assured that the channel is granted and starts the transmission of a multicast data frame. The leader sends an ACK in reply if the data is received correctly, or sends a NAK otherwise. If any other receiver detects a
transmission error, a NAK is sent. This NAK frame will collide with the ACK, if any, sent by the leader. This leads to the AP not hearing any ACK, and thus retransmitting the lost frame.
Applying LBP to IEEE 802.11 suffers from two problems. One is the hidden terminal problem due to the m-RTS in LBP serving both roles of channel acquisition and multicast notification. The other is the poor performance when the channel error rate is high. This is because the receivers in LBP cannot access the frame sequence number before the frame is received, as there is no such field in the structure of RTS/CTS frames for multicast. As a result, the performance of the error recovery scheme for LBP degrades, particularly for lossy channels.
In this paper, we analyze two types of reliable multicast mechanisms at the MAC layer for IEEE 802.11 WLANs: ACK-based (e.g., [3]) and leader-based (e.g., LBP in [2]). For the ACK-based mechanism, the AP monitors the frame reception progress of all receivers and retransmits frames whenever no ACK is received from any receiver; for leader-based mechanism, the AP retransmits frames only when no ACK frame is received from the selected leader. Thus, the ACK-based mechanism can be regarded as a centralized scheme, and the leader-based mechanism, a distributed one. Since LBP suffers from the hidden terminal problem, and has poor performance when the channel error rate is high, we will enhance LBP to solve these problems in this paper and called the enhanced version of LBP as ELBP. Note that since the work in [3] is designed for ad hoc networks, we will also modify it for IEEE 802.11 WLAN with APs, and called the modified version as “ACK-based Multicast Protocol (AMP).” We will then analyze both types of reliable multicast mechanisms based on AMP and ELBP, and verify the analytical model via simulations.
The rest of the paper is organized as follows. In Sec. II, the two reliable multicast mechanisms to be analyzed are described. In Sec. III, the performance of AMP and ELBP with respect to frame holding time is analyzed. In Sec. IV, the analytical model is verified via simulation. Finally, the paper is concluded in Sec. V.
II. RELIABLE MAC-LAYER MULTICAST The issues of reliable MAC-layer multicast can be decomposed into two problems: (1) channel acquisition, and (2) error-recovery strategy. In what follows, we propose a channel acquisition mechanism, and enhance the two types of error-recovery schemes (i.e., ACK-based and LBP), which together will provide reliable multicast transmissions for IEEE 802.11 WLANs.
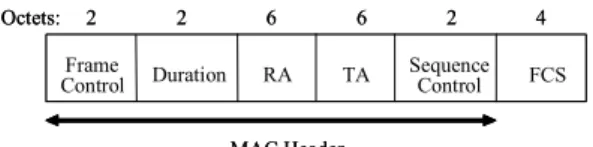
A. Channel Acquisition and Multicast Notification In this paper, we propose a channel acquisition mechanism called RTS/CTS/SEQ for IEEE 802.11. In RTS/CTS/SEQ, the structures of both RTS and CTS frames remain intact. The SEQ is a new control frame defined as in Fig. 1, where TA represents the Transmitter Address, and Sequence Control shows the sequence number and the fragment number of the frame to be transmitted.
Figure 1. The format of an SEQ frame
The RTS/CTS/SEQ exchange works as follows. A receiver, say host X, is randomly selected to respond to the RTS/CTS exchange. The AP sends a unicast RTS frame to host X, and host X sends a unicast CTS frame in reply after an SIFS period. The AP multicasts an SEQ frame after an SIFS if the CTS frame is received correctly. No one needs to respond to this multicast SEQ. If the channel has been acquired after the previous u-RTS/u-CTS exchange, the m-SEQ will not collide and will thus achieve multicast notification. After another SIFS, a data frame is multicast by the AP. Error recovery described in Sec II. B then follows.
Figure 2. The RTS/CTS/SEQ exchange
B. Error Recovery
Two protocols are proposed for error recovery: (1) an ACK-based scheme called ACK-based Multicast Protocol (AMP), and (2) an enhanced LBP scheme called ELBP. Both protocols are based on the RTS/CTS/SEQ exchange for channel acquisition and multicast notification.
1) AMP
After the RTS/CTS/SEQ exchange and data multicast, the RAK/ACK exchange follows. The AP polls each multicast receiver in turn via a Request for ACK frame (denoted as RAK) and each receiver sends an ACK in reply after an SIFS. If no ACK is heard for a RAK, the AP records the unsuccessful receiver, say host Y, and contends the channel for frame retransmission. After the frame is retransmitted in multicast, the AP resumes the polling, starting from host Y. This process repeats until all multicast receivers have completed a RAK/ACK exchange.
2) ELBP
After the RTS/CTS/SEQ exchange and data multicast, the AP waits for an ACK from the leader selected by a leader election procedure as in [2]. As in LBP, if no ACK is heard from the leader within a period of time, the data is retransmitted in multicast.
However, the operation of non-leader hosts is different from LBP, in which non-leader hosts send a NAK to collide with the leader’s ACK whenever the received frame is in error, regardless of whether this erroneous frame has been received successfully before or not, due to the unknown sequence number. In ELBP, because of the announcement from SEQ frames, non-leader hosts send a NAK only when the following multicast frame has not been received correctly yet, and stay quiet for any retransmitted frame which has been received successfully before. As a result, ELBP can effectively eliminate the redundant retransmissions caused by LBP.
Note that together with the RTS/CTS/SEQ exchange, ELBP can further eliminate the hidden terminal problem suffered by LBP. For LBP, a u-RTS from a hidden terminal of the leader, say H1, may collide with the AP’s m-RTS, which may destroy the functionality of multicast notification between the area covered by the AP and H1. However, the multicast notification in ELBP is provided by SEQ frames, instead of m-RTS frames. Therefore ELBP and AMP are free from the hidden terminal problem thanks to the RTS/CTS/SEQ exchange.
III. FRAME HOLDING TIME AT AP
In this section, the performance of both AMP and ELBP with respect to frame holding time at the AP is analyzed. The frame holding time is defined as “the time period from the start of an AP sending a certain multicast frame to the end of the successful reception by all members.”
Frame
Control Duration RA TA SequenceControl FCS
Octets: 2 2 6 6 2 4
MAC Header Frame
Control Duration RA TA SequenceControl FCS
Octets: 2 2 6 6 2 4
MAC Header
u-RTS SIFS u-CTS SIFS m -SEQ SIFS m -DATA
u-RTS / u-CTS : unicast RTS / CTS m-SEQ / m-DATA : multicast SEQ / DATA
u-RTS SIFS u-CTS SIFS m -SEQ SIFS m -DATA
u-RTS / u-CTS : unicast RTS / CTS m-SEQ / m-DATA : multicast SEQ / DATA
A. System Model and Assumptions
Table I. Notations used in the analysis
Consider a system consisting of N stations, including the AP, forming a single subnet. There are R receivers belonging to the multicast group, i.e., R<N, and the multicast flow is transmitted from the AP to each multicast receiver. In our model, all stations are located in the transmission range of the AP. The error probability of each link from the AP to a receiver is assumed independent and identical, and denoted as pe. Thus, a station experiencing an error state does not imply the links of any other stations are also in error.
We assume that all the stations operate synchronously. The propagation time is assumed negligible in the analysis. To simplify the analysis, we further assume that all hosts transmit data based on the RTS/CTS exchange, and RTS, CTS, SEQ, ACK and NAK frames will not be lost or received in errors. Thus, the performance results may be thought of as the upper bounds of the real-world performance.
All stations are assumed backlogged. In other words, the outgoing queue of each station always has at least one frame to send, and each station always tries to access the channel to send out the frame. In this analysis, we do not consider the hidden terminal problem and the
capture effect of the CSMA/CA protocol. The notations used in the analysis are summarized in Table I.
B. Number of Transmissions
Let M denote the number of transmissions for an m-data (i.e., multicast data frame) to be received correctly by all R receivers. In [4], the pdf and the expectation of transmissions for R receivers to receive a frame correctly are expressed as follows.
( )
1 ( 1) , 1,2," ) ( 0 ) 1 ( = − − = =∑
= − p m p i R m M P R i i e m i e i∑
∑
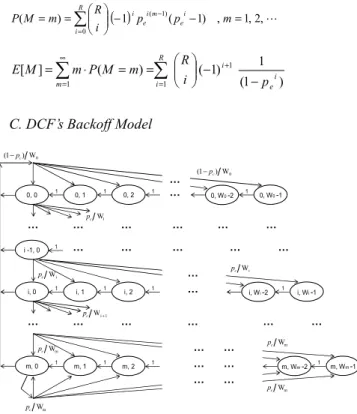
= + ∞ = − − = = ⋅ = R i ei i m i p R m M P m M E 1 1 1 (1 ) 1 ) 1 ( ) ( ] [ C. DCF’s Backoff ModelIn [5], the exponential backoff mechanism of an IEEE 802.11 station can be modeled as a two-state Markov chain shown in Fig. 3. The state of the Markov chain is defined as {s(t), b(t)}, where s(t) is the backoff stage of the station at time t, and b(t) is the backoff count for a given station at time t.
Let Pc denote the probability of a collision for a
frame being transmitted on the channel. Thus,
1 ) 1 ( 1− − − = N c P τ
(1) ) ) 2 ( 1 ( ) 1 )( 2 1 ( ) 2 1 ( 2 0 0 c c m c c P W P W P P − + + − − = τ
.
(2) Inverting (1), we obtain 1 1 ) 1 ( 1− − − = N c P τ(3)
Together with (2) and (3), Pc and
τ
can be solved byusing numerical techniques.
R The number of multicast receivers in the group
N The total number of stations in the WLAN, including the AP
M The number of transmissions for all receivers to receive a frame correctly
D
T The time to transmit an RTS, a CTS, an SEQ and a multicast data frame, i.e.,
SIFS 3 DATA SEQ CTS RTS+ + + + = D T A R
T + The time to transmit a RAK and an ACK, i.e., SIFS 2 ACK RAK+ + = + A R T ACK
T The time to transmit an ACK, i.e.,
SIFS
ACK+
=
ACK T
τ The probability that a station transmits a frame in a slot
S
T The time of a successful transmission slot
C
T The time of a collision slot
slot idle
T _ The duration of an idle slot
slot av
T _ The average slot time observed by the AP in the contention phase for AMP and ELBP 0, W0 -1 i, Wi -1 m, Wm -1 0, 0 i, 0 m, 0 0, 1 0, 2 i, 1 i, 2 m, 1 m, 2 0, W0 -2 i, Wi -2 m, Wm -2 i -1, 0 1 W c p 1 i W+ c p i W c p m W c p m W c p m W c p m W c p i W c p 0 W ) 1 (−pc 0 W ) 1 (−pc 1 1 1 1 1 1 1 1 1 1 1 1 … … … … … … … … … … … … … … … … … … … … … … … … … … 1 …
D. Analysis of Frame Holding Time 1) AMP
Let
X
AMP denote the frame holding time of AMP. Thus, ] ) 1 ( [ ) 1 ] [ ( ) 1 ] [ ( ] [ ] [ _slot av A R D AMP T q q DIFS M E T M E R T M E X E ⋅ − + ⋅ − + ⋅ − + + ⋅ = + (4) where q=τ(1−τ)N−1, and . ] ) 1 ( ) 1 ( 1 [ ) 1 ( ) 1 ( ) 1 ( 1 1 _ _ C N N S N slot idle N slot av T N T N T T ⋅ − − − − + ⋅ − − + ⋅ − = − − τ τ τ τ τ τThe first term in (4) corresponds to the total time from when the AP starts sending a multicast frame until it is successfully received by all receivers. This is equal to the mean number of multicast frame transmissions, each with TD =RTS+CTS+SEQ+DATA+3SIFS . The second term is the total time for the AP inquiring the receivers until an ACK is received from all receivers. This is equal to the mean number of RAK/ACK exchanges for a data frame being received successfully by all receivers. Since the AP should at least inquire R receivers, and poll the failed receiver again after each retransmission, it comes to a total of R+ ME[ ]−1 RAK/ACK exchanges, each with
SIFS ACK
RAK
TR+A = + +2 .
The third term in (4) corresponds to the total time of the AP contending for channel access. Each m-data experiences E[M]-1 retransmissions. For each retransmission, the AP contends the channel after waiting a DIFS. Since the successful transmission probability of a frame sent by the AP is q=τ(1−τ)N−1, the mean
number of time slots between the successful transmissions of two frames, which is a geometric distribution with parameter q, is (1-q)/q, and the mean time of each slot in this period is Tav_slot. Thus, the mean contention time for each retransmission is
slot av T q q)/ ) _ 1
(( − ⋅ , yielding the total time as ] ) 1 ( [ ) 1 ] [ ( Tav_slot q q DIFS M E − ⋅ + − ⋅ . slot av
T _ is calculated as follows. The probability that the AP sees an idle slot during the contention phase is (1−τ)N, which takes time
slot idle
T _ . The probability
that the AP observes a success in transmission caused by any other host is (N−1)τ(1−τ)N−1, which takes time
S
T . The AP detects a collision with a probability of
1 ) 1 ( ) 1 (
1− −τ N−Nτ −τ N− , and a collision slot takes time C T . Thus, . ] ) 1 ( ) 1 ( 1 [ ) 1 ( ) 1 ( ) 1 ( 1 1 _ _ C N N S N slot idle N slot av T N T N T T ⋅ − − − − + ⋅ − − + ⋅ − = − − τ τ τ τ τ τ 2) ELBP
Let XELBP denote the frame holding time of ELBP. Thus,
]
)
1
(
[
)
1
]
[
(
)
(
]
[
]
[
_ slot av ACK D ELBPT
q
q
DIFS
M
E
T
T
M
E
X
E
⋅
−
+
⋅
−
+
+
⋅
=
(5)
The first term in (5) corresponds to the total time from when a multicast frame is sent until the frame is correctly received by all receivers. Again, the mean number of times each frame is transmitted is E[M], and each transmission takes TD+TACK . Thus, it spends
) (
]
[M TD TACK
E ⋅ + in total for an m-data. The second term is the time for the AP contending the channel for successfully sending an m-data.
IV. PERFORMANCE EVALUATION
In this section, we provide simulation results to validate our analytical models. The physical parameters used in the simulation follows the IEEE 802.11a standard: data rate: 54Mbps; an idle slot: 9µs; an SIFS: 16µs; a DIFS: 34µs; an RTS: 20 octets; a CTS: 14 octets; data frames: 2304 octets; an ACK: 14 octets; MAC overhead: 28 octets; CWmin: 16; CWmax: 1024.
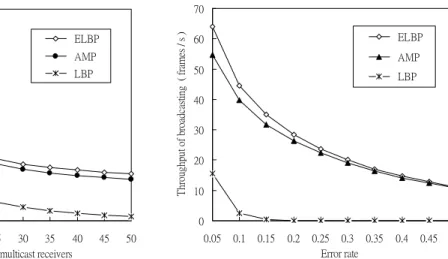
Fig. 4 shows the performance of LBP, AMP, and ELBP. We see that both AMP and ELBP outperform LBP in terms of the AP’s throughput, defined as the inverse of the mean frame holding time at the AP. Note that LBP’s throughput is very poor at high error rates. The performance advantage of our proposed protocols is thanks to the proposed channel acquisition mechanism. Figs. 5 (a) and 5 (b) compare the analytical models of AMP and ELBP with the simulation results. The three pairs of curves in each figure correspond to three different sets of channel error probabilities. The lower the error rates, the lower the frame holding time, matching our expectation. In all cases, all pairs of curves in both figures show that both simulation and analytical results match very well.
V. CONCLUSION
In this paper, we have analyzed the two types of reliable multicast protocols at the MAC layer for IEEE 802.11 WLANs: AMP and ELBP. Both protocols are based on the proposed RTS/CTS/SEQ exchange for IEEE 802.11 WLANs, and are derived from existing works. From the simulation, the performance of AMP and ELBP are both superior to that of LBP, thanks to the channel acquisition mechanism RTS/CTS/SEQ. We have conducted simulations to validate the proposed analytical model. The results show that the simulation and analytical curves match very well, showing that our analytical model is excellent in describing reliable multicast mechanisms for IEEE 802.11 WLANs.
ACKNOWLEDGEMENT
This paper was supported in part by National Science Council (NSC), Taiwan, under a Center Excellence Grant NSC93-2752-E-002-006-PAE, and in part by NSC under Grant NumberNSC93-2213-E-002-132.
REFERENCES
[1] IEEE 802.11 Working Group, Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications, ANSI/IEEE Std 802.11, 1999.
[2] J. Kuri and S. K. Kasera, “Reliable Multicast in Multi-Access Wireless LANs,” ACM/Kluwer Wireless
Networks Journal, vol.7, no.4, pp. 359-369, August 2001. [3] M. T. Sum, L. Huang, A. Arora, and T. H. Lai, “Reliable
MAC Layer Multicast in IEEE 802.11 Wireless Networks,”
Proc. of ICPP, pp. 527-536, Aug. 2002.
[4] D. F. Towsley, J. Kurose and S. Pingali, “A Comparison of Sender-Initiated and Receiver-Initiated Reliable Multicast Protocols,” IEEE Journal on Selected Areas in
Communications, Vol. 15, No.3, April 1997.
[5] G. Bianchi, “Performance Analysis of the IEEE802.11 Distributed Coordination Function,” IEEE Journal on
Selected Areas in Communications, Vol. 18, No. 3, March 2000. 0 20 40 60 80 100 120 140 5 10 15 20 25 30 35 40 45 50
Number of multicast receivers
T hr ough put o f m ul tic as ting ( f ra m es / s ) ELBP AMP LBP
0 10 20 30 40 50 60 70 0.05 0.1 0.15 0.2 0.25 0.3 0.35 0.4 0.45 0.5 Error rate T hro ug hp ut o f b ro ad ca st in g ( fra m es / s ) ELBP AMP LBP
(a) Number of receivers, with error rate = 0.05 (b) Error rates, with no. of receivers = 30 Figure 4. The throughputs of the three protocols
0 20 40 60 80 100 120 140 160 5 10 15 20 25 30 35 40 45 50
Number of multicast receivers
Fr am e hol di ng ti m e (m s) AMP analysis AMP simulation error rate : 0.05 error rate : 0.25 error rate : 0.4 0 20 40 60 80 100 120 140 5 10 15 20 25 30 35 40 45 50
Number of multicast receivers
Fr am e hol di ng ti m e (m s) ELBP analysis ELBP simulation error rate : 0.05 error rate : 0.25 error rate : 0.4
(a) AMP (b) ELBP