Maria
C,
Yuang and /en C. Liu, National Chiao Tung Universityh e user community's
propose
a
new
Dual Bus (FQDB) [8], DQDB [2],demand for network band- DrOtOCOl.
~r;Or;~;Zed
AdaDtive
Cyclic-Reservation Multiple-AccessThe
width continues to expand as net- (CRMA) [9]? Multislot Reservation
works become more nervasive and
'
insertion
fpAcc/)r
Alternating. Cvcle Control (MRAC) new applications with stringentthat espec;al/y suifab/e for
[lo], S++"[li, and Adapt&e Cycl;requirements emerge. New applica- Cell Insertion (ACCI) [ l l ] . Among
tions with diverse service reauire-
clkna-sen/er-based gigabit
these protocols, the ACCI mecha- nism is considered the most promis-LANS
and
MANS_
ing protocol with respect t o ments and traffic characteristicsinclude the visualization of comput-
er-generated images, massive file achieving. t h e aforementioned
transfers, and high-quality video.
Moreover, the increase in the performance of desktop work- stations and the development of optical fiber hardware have been driving network speeds into data rates of 1 Gbis. Unlike existing local area networks (LANs) and metropolitan area networks (MANs), gigabit LANs and MANS exhibit high bandwidth-delay product. Moreover, forthcoming networks are required to support diverse nodes demanding different amounts of bandwidth. Examples are networks with multime- dia workstations and with client-server configurations. These facts render traditional medium access control (MAC) proto- cols unviable.
A viable M A C protocol for gigabit LANs a n d MANs should satisfy the following four requirements. First of all, it should guarantee low mean and variance of the access delay [ 11. Second, maximum utilization should be achieved; better design leads to greater accommodation of packets on a link at any time. Third, the protocol should be delay-invulnerable in the sense that equivalent performance should be offered to homogeneous stations regardless of the network size (propa- gation delay). An example of a protocol that fails to meet this requirement is the Distributed Queue Dual Bus (DQDB) Queue Arbitrated (QA) protocol [ 2 ] , in which unfairness is exhibited as the propagation delay increases [ 3 ] . Finally, a protocol should also allow both fair and prioritized access for client-server-based networks. That is, the p r o t o c o l s h o u l d offer fair access to homogeneous stations (e.g., clients) and prioritized access to a special class of stations (e.g., gateways, servers). Notice that the prioritized access referred to here is different from the priority transmissions supported by most existing LANs and MANs. The former is provided o n a sta- tion basis, whereas the latter is offered on a packet basis. Another motive requiring prioritized access is the prolifera- tion of multimedia workstations, which mostly generate real- time traffic to the network and require stringent quality of service (QoS) guarantees.
The article initially assesses several existing MAC proto- cols, including Fasnet [4], Expressnet [ 5 ] , Manufacturing Automation Protocol (MAP) [6], Buzznet [7], Fair Queue
v
requirements. However, owing to
the lack of the prioritized access consideration, ACCI fails to provide QoS for client-server-based networks.
The goal of this article is to propose a new protocol, called Prioritized Adaptive Cycle Cell Insertion (PACCI), especially advantageous to client-server-based gigabit LANs and MANS. PACCI achieves bounded delay and high utilization regardless of the network size and load. In addition to providing fair access for regular nodes (e.g., clients) through regular cycles, PACCI offers prioritized access t o privileged nodes (e.g., servers) through restricted cycles. The bandwidth allocation of the regular and restricted cycles is then based on an analytic model in an effort to provide QoS guarantees in terms of throughput under diverse traffic loads. This article also pre- sents simulation results that demonstrate the accuracy of the analysis and the superior performance of PACCI.
The remainder of this article is organized as follows. The next section gives an assessment of several existing high-per- formance MAC protocols operating on bus-based networks. T h e third section gives an overview of the ACCI protocol. The PACCI protocol is then proposed in the fourth section. T h e fifth section presents the analytic model on which the bandwidth allocation of regular and restricted cycles is based. The sixth section presents simulation results that demonstrate the superiority of PACCI and confirm the accuracy of the analytic model. Finally, concluding r e m a r k s are given.
ASSESSMENT
OFMAC
PROTOCOLS everal existing high-performance MAC protocols operating o n bus-based networks are assessed based o n cyclicity, access mode, delay invulnerability, and prioritized access. Each criterion will be described in detail. Notice that provid- ing an exhaustive survey is not the intention of this article. These protocol examples are selected for the purpose of showing the protocol evolution and making distinct perfor- mance comparisons.First of all, it is preferable to access the bandwidth on a cyclic basis owing to the easy achievement of fairness. T h e
time period during which the access is prohibited between two consecu- tive cycles is referred to as the cycle g a p . Unquestionably, a minimal cycle gap yields maximal utilization. Furthermore, due to the increasing bandwidth-delay product in gigabit LANs and MANs, cycle gaps become more unbearable. ACCI is the only protocol incurring no cycle gap and achieving maximum uti- lization.
Second, LANs and MANS often operate under one of thrlee access modes. random access fF.A). con-
Based on an analytic model,
PACCI
offers prioritized access
t o achieve multiple levels
of
delaykh ro ugh pu
t
requirements while still
retaining the superior
performance of the
ACCI protocol.
trolled access (CA), i n d hybridaccess (HA) (the combination of RA and CA). Researchers have revealed that MAC protocols employing the H A mode achieve maximal utilization under a variety of traffic loads. Moreover, the HA mode can be further classified as either explicit or implicit. The explicit HA mode entails explicit mode switches (e.g., from R A to CA) as the traffic pattern in the network alters. Examples of protocols adopting this mode are MAP [6] and Buzznet [7]. The major drawbacks of this mode type are twofold. First, the determination of the mode change is not a trivial problem. Second, much bandwidth waste is incurred during the mode change. As opposed to the explicit HA mode, the implicit one allows the network to automatical- ly adapt to different traffic patterns without any mode switch. The network behaves as an RA system under light loads and as a CA system under heavier loads. Examples are MRAC 1101 and ACCI [ l l ] . The advantage of this mode type is the reduction of bandwidth walste by eliminating the mode switch.
Third, a MAC protocol should be invulnerable to the size of a network (i.e., delay.invulnerable). Gigabit LANs and MANs employing delay-vulnerable MAC protocols may waste immense amounts of bandwidth and present unfairness prob- lems. An example is the DQDB QA protocol [2], in which an unfairness problem is exhibited as the propagation delay increases. By contrast, ACCI was shown to provide equivalent performance to homogeneous nodes regardless of the network size.
Finally, as was previously stated, a protocol should offer both fair and prioritized access for networks with client-server configurations. Examples of protocols satisfying this require- ment are FQDB [8] and Si+
+
[1], in which prioritized access is provided by assigning different window sizes to clients and servers. However, this behavior may produce large amounts of high bursty traffic to the network and result in large delay jit- ters. These protocols are thus not suitable for supporting real- time applications.The goal of this article is to present the design of a MAC protocol which allows flexible prioritized access to ensure guaranteed delay bounds and delay jitters for privileged nodes while incurring minimal performance degradation for regular nodes. Our newly designed MAC protocol is a variant of ACCI, called Prioritized Adaptive Cycle Cell Insertion (PACCI). Based on an analytic model, PACCI offers priori- tized access to achieve multiple levels of delayithroughput requirements while still retaining the superior performance of the ACCI protocol.
OVERVIEW OF THE
ACCl
PROTOCOLor ease of explanation, we briefly describe the ACCI pro-
F
tocol and its network interface. The interface of ACCI consists of two buffers : the forwarding buffer (F-BUFF) andtransmitting buffer (T-BUFF). The F - B U F F is used to temporarily store traffic cells passing from upstream nodes, and the T-BUFF is used to store local cells. The head- end continuously generates a series of cycles, each of which is initially o n e cell in length. Each cycle ensures one access opportunity to each node without the utilization of an explicit token passing scheme.
The network interface first stores the incoming cell into the F-BUFF. Each node then repeatedly per- forms four tasks:
*Transmits a cell stored in the T-BUFF upon detecting the start of a new cycle
Accepts the incoming cell addressed to it
Forwards the incoming cell from the F-BUFF if the T- BUFF is empty or access is prohibited during the current cycle
Initiates overload control if the F-BUFF overflows. As a result, each cycle expands as it travels toward the end of the bus. The creation and expansion of access cycles take place in a completely distributed manner. Finally, the access cycle duration is variable, adapting itself to the load of the network.
PACCI PROTOCOL
CC[ operates on the same network topology and inter-
p"
face as does ACCI. The PACCI protocol is now presented in this section.CELL FORMAT
Data are carried in fixed-length time slots, called cells. Each cell contains a one-byte access control field (ACF) and a 52- byte information field (IF). Basically, the first three subfields in the ACF indicate the status of a cell. The congestion con- trol (CC) bit is used for congestion control 1111. It is activated on the opposite bus as the cell occupancy of the F-BUFF exceeds the congestion threshold. The last three fields are used for the dynamic designation of nodes (regular or privi- leged nodes). Each subfield in the ACF is further described, in order and in detail, as follows:
Cycle {vpe (CT): identifies the type of the cycle, restricted B u s y ( B ) : indicates whether the slot is used (= 1) or Start of cycle (CS): indicates whether the slot is the head
of a new cycle (= 1)
CC: indicates that this node is overloaded and the near- est upijtream node will be forced to emit an empty slot Prioritized status request (PR): indicates that a request has
been made by a node for ranking itself as a privileged node
Prioritized status confirmed (PC): indicates that a node has been confirmed as a privileged node
Prioritized status termination (PT): indicates that a termi- nation request has been made by a node for ranking itself back as a regular node
(= 1) or regular (= 0) empty (= 0)
PACCI OPERATIONS
Initially, the headend of the PACCI network statistically and alternately generates a number of regular and restricted cycles based 011 the analysis described in the next section. Regular cycles can be accessed by any nodes, whereas restricted cycles
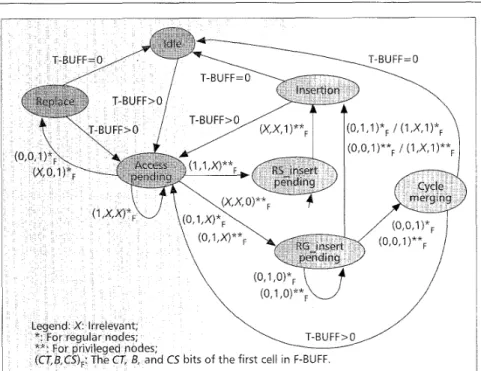
Figure 1 . State transition diagram for PACCI.
can only be accessed by privileged nodes. Essentially, nodes can be dynamically designated as either regular or privileged nodes according to the following procedure.
Adopting the similar distributed queue and counter mecha- nism employed in D Q D B [ 2 ] , PACCI uses three bits in the ACF: PR, PC, and PT. A node wishing to become a privileged node first makes a request by setting “PR = 1” in a slot on the reverse bus, then enters the countdown state. Upon receiving the request, the headend sets “PC = 1” in a slot on the forwarding bus to implicitly accept the request. The count- down counter of the node is decremented by one when a slot with activated PC (PC = 1) is sensed. The request for privi- leged node status is granted as the countdown counter reach- es zero. As the node desires no extra bandwidth, it issues a termination request (PT = 1) to withdraw itself from the priv- ileged node set.
The access of restricted and regular cycles is now described. The state transition diagram is depicted in Fig. 1. Since the access for regular nodes is similar to that for privileged nodes, we only describe the access for privileged nodes. Initially, the node is in the IDLE state. As a local cell arrives at the T- BUFF, the node progresses to the ACCESS PENDING state. At this moment, the detection of an empty slot ( B = 0) trig- gers the node to move to the REPLACE state in which the first cell in the T-BUFF will be forwarded. Otherwise, the node enters the RS-INSERT PENDING or RG-INSERT PENDING state should the cycle detected be a restricted or regular one, respectively.
The node then repeatedly senses the start of a new cycle in an attempt to append the cell in the T-BUFF to the end of the previous cycle. In the first case, upon detecting the start
of a new regular cycle (CS = 1) while being in t h e RG-INSERT PENDING state, the node progresses to the INSERTION or CYCLE MERGING state if the B bit is 1 or 0, respectively. The node in the INSERTION state appends
a cell in its T-BUFF to the end of the previous cycle. The node in the CYCLE MERGING state not only performs the INSERTION operation, but also reduces unused regular- cycle bandwidth by merging an empty regular cycle into the previous busy cycle. In the second case, upon detecting the start of a new cycle while being at the RS-INSERT PEND-
ING state, the node progresses to the INSERTION state. In this state, the node only needs to perform the INSERTION operation. This is because the merging operation is not applied to restricted cycles due to the fact that the restricted-cycle bandwidth has already been allocated for privi- leged nodes.
Notice that the occupancy of the F-BUFF is incremented by one dur- ing t h e I N S E R T I O N s t a t e and is decremented by one when T-BUFF is empty and an empty regular cycle arrives. Due to the finite size of the F-BUFF, congestion control must be activated when t h e F - B U F F over- flows. Moreover, if the F - B U F F is empty and no T - B U F F emission occurs, t h e propagating cells from upstream nodes would suffer from a transit delay equal to the latency of the node. This illustrates that PACCI and ACCI guarantee minimal delay under light load conditions.
BANDWIDTH
ALLOCATION
he bandwidth allocator (in the headend) performs dynam-
T
ic allocation o f regular and restricted cycles based on the queuing analysis presented in this section.SOURCE TRAFFIC MODEL
Our source traffic is modeled by an interrupted Poisson pro- cess (IPP) [12] alternating between 0 (OFF) and 1 ( O N ) states. U defines the probability of switching from state 1 to state 0, and
p
defines the opposite probability. Moreover, in any time slot the node produces one cell in state 1, and no cell in state 0. The steady-state probability of each state, denoted as 111 andno,
can be computed byFI
=ILP,
whereII
=
[nl,n,]
andP
is the probability transition matrix. Accord-ingly,
B
a
n,
=-( a +
pj
’ and “0 =i..p)
Notice that the traffic load created by a node is thus equal to II,. The density function, v(i, x, y ) , which is the probability that node i produces y cells during x time slots, becomes
v(i, x,
Y)
=9
(n,y
(nor
- y > x 2 y . (2) ANALYSISFirst of all, RS:RG (a ratio of the restricted cycles to the reg- ular cycles) denotes the repeated generation of RS restricted cycles followed by R G regular cycles. For example, all cycles with index “p(RS
+
RG)+
q , p E integer union; 0 5 q < RS” are restricted cycles and others are regular cycles. At the beginning of a cycle, say r, the queue length of node i in its T-BUFF is
QL.
During the cycle, A: local cells have arrived and the queue length becomes0;
at the end of cycle Y. At the end of cycle r, node i appends a cell to the end of this cycle. Con- sequently, the length of the cycle (C,’) becomes Cy+
1 (or Cl:,) and the queue length of node i is Q‘; for the next cycle, r+
1. In the following subsections, the queue lengths of the privileged and regular nodes are separately discussed, after which the allocation of cycles is analyzed.Analysis for Privileged Nodes - Assuming
e,"
= Q: = A: = O and c i = 0, according to the definitions of random variables given above, we simply get-
Qk = min ( Q i
+
A [ , K+
I), ( 3 ) where K is the size of the 'T-BUFF. Notice that (7: =QL
and A i = 0, for a node in the IDLE and REPLACE states. Mor- ever, since&:
is equal to Qrb+'
+
1 if there exists at least one cell in the T-BUFF,Q J + ~ = max
(?j[
- I, 0). (4) Let qby (i, j ) andq;
(i, j ) be the density functions of Qby andQ
:
,
respectively. That is qby (i J ) = Prob[M = i, Qby = f andq:
(i, j ) = Prob [M = i, =: j ] , where M denotes the index of nodes. In addition, let a r ( i J ) be the density function of A:.
That is d ( i , j ) = Prob[M := i, Ai = j ] . Thus, the distributions are given, according to Eqs. (3) and (4), by
$
(i,j) = nK + (qJ(i,j)i" d(i, j ) ) , I< j S K+
I,q b
(5) (6)
r + l . .
( I , ] ) = xo(&(i,j +I)), I < j K
+
1,where * denotes the convolution operation, and z K + l(.) and
no(.) are operators representing the minimum and maximum functions of probability distribution [ 121. Moreover, the densi- ty function ar(i, j ) can be reformed, by Eq. (2), as
i-1
k=O
d ( i , j ) = x c r ( i , k ) v ( i , k , j ) , j
<
k , (7) where cr(i, k ) is the density function of C;, i.e., cr(i, k ) = ProbSince the probability tlhat a node has a cell to append to the end of a cycle is just the probability of having a nonempty T-BUFF, the density functions for the node to emit no cell and one cell to the cycle are
sr (i, 0) =
qL
(i, 0), and [M =i,
ci'
= k ] .sr (i, 1) = 1 -
q:
(i, O), r'espectively. (8) Next, the cycle lengths regarded by nodes i and i+
1 are related by the following equation:cr(i
+
1, j ) = sr(i, 1) er (i, j - 1)+
sr (i, 0 ) er(& j ) , 1<
j .Analysis for Regular Noldes - If the cycle sensed is a reg- ular one, the preceding analysis for privileged nodes can be applied directly. However, since regular nodes can only access regular cycles, if the cycle sensed is a restricted one, the analy- sis shown below will be applied.
During a restricted cycle, local traffic cells arrive at the node as usual. Equationis (3) and (5) can still be applied. However, since the node is not allowed to emit any cell into this restricted cycle, the queue length of this node remains the same at the end of the cycle. Equations (4) and (6) can be reformed as
(9)
er;
=&I
and(10)
r + l . .
b ( i , ~ ) =
ql
( i , j ) ,respectively. Consequently, the transmission cell probabilities of this node are
sr (i, 0) = 1 and
f ( i , 1) = 0.
Next, the cycle lengths regarded by nodes i and i
+
1 are related by the following equation:cyi, k ) = c y (i
+
1, k ) . (12)Throughput Analysis -- The throughput can be derived as
a function of the cycle ration. The steady state probabilities that node i emits a cell into the restricted and regular cycles, denoted as sRS(i, j ) and sRG(i, j ) , become
sRS(i: j ) = lim sr(i, j ) if r is a restricted cycle, and
s R C ( i , j ) = lim s r ( i , j ) , ifr is a regular cycle. (13)
r+=
r+=
The steady state probabilities of the length of the restricted and regular cycles seen by node N (at the end of the bus), denoted as cRS(N, j ) and cRG(N, j ) , can be expressed as
cRS(IV', j ) = lim c'(N, j ) , if r is a restricted cycle, and cRG
( ~ v ,
j ) = lim cr ( N , j ) , if r is a regular cycle. (14)r + -
r+=
Thus, the mean number of cells emitted by a node i is
1
E[sI:~:)I = ~ [ R s . j . s R S ( i , ~ ) + R G . j . s R G ( i , j ) l . (15) j=O
The meail length of an iteration including RS cycles and RG cycles can be given as
N - l
E [ C ] : = [RS.j.cRS(N,j)+RG.j.cRG(N,j)]. (16)
j=O
Finally, the throughput, T, for node i can be expressed as
]=0
Consequently, in an attempt t o ensure a given QoS in terms o F i.hroughput T , a number of consecutive restricted and regular cycles to be generated can be accurately determined based on Eq. (17).
IqNALYTIC AND SIMULATION
RESULTS
or t h e analytic result computation, t h e network was
F
assuined to have 10 privileged nodes and 20 regular nodes. The size of the T-BUFF, K, was 1000 cells long. The traffic of each node followed the two-state IPP model wherea
= 0.95 andp
=: 0.05. As for the simulation, the network was assumed to have 30 nodes in which 10 nodes (5, 6, 7, 13, 14, 17, 18, 24, 25, 26) were privileged nodes and the rest were regular nodes. The lengths of both F-BUFF and T-BUFF were set as 1000 cells long. Finally, the channel capacity was 1 Gbis and the internodal delay was 5 time slots.Figure 2 shows the throughput as a function of the cycle ratio (F.5bIRG) under an aggregate load of 0.75. For instance, to achieve a throughput of 50 Mbls for privileged nodes, the network has to adopt the minimum cycle ratio (KSIRG) of 113. In addition, t h e figure shows that as t h e cycle ratio (RS/RG) decreases (i.e., fewer restricted cycles), the through- put difference between privileged and regular nodes declines.
Figure 3 shows the significant impact on throughput and delay for privileged nodes due to the introduction of restrict- ed cycles. Figures 3a-3c demonstrate that the more restricted cycles the network generates, the better performance (in terms of the throughput, end-to-end delay, and access delay) privileged nodes achieve. Notice that the access delay is defined a s the duration from the time the cell arrives at the node to the time the cell departs from the node. The trans-
- -
Aggregate load=O 7 5 1
2
8 0 -1 0 1 .A-regular n_odcs .-. regular nodcs
1
Cycle ratio 1 /I 1 /2 113 1 i4 1 /5 1 i6
. -
E Figure 2. Throughput vs. cycle ratio (RSIRG).
5 5 ... .. . ...
VI 50 .
I
RSiRG=lilG(PACCI) ! RS/RG=O/I (ACCI) N e t w o r k load=0.6I
h 8 4 5 : , II
RS/RG: I/X(PACCI) -..L-,-, I ,I--, -. 20 -- I 3 5 7 9 11 13 I S 17 1 9 21 23 25 27 29 Node i n w x 1 3 5 7 3 11 13 1 5 1'7 1 9 21 23 25 27 2 9 Nodc index 2 0 -- L I I d.L A - , - E! I 3 5 7 - 9 11 13 15 17 19 21 23 25 27 29 k -. -. - - - - Node index -W Figure 3. Simulation results with respect to node index:
u)throughput results; b) end-to-end delay results; c)access delay results; d ) transmission delay results.
mission delay is defined as the sum of the cell transmission time and the propagation delay until the cell reaches the end
of the bus. The access delay and transmission delay together constitute the end-to-end delay. As shown in Fig. 3d, t h e transmission delay is not dependent on the cycle ratio, but on the size of the bus; the longer the distance, the higher the transmission delay.
As shown in Fig. 4a, the throughput is independent of the cycle ratio under light load conditions. However, as the net- work load increases, throughput becomes sensitive to t h e cycle ratio. As shown in Figs. 4b and c under light load condi- tions PACCI performs as well as ACCI, and the performance is irrelevant to the cycle ratio. However, as the network load increases, the benefit of introducing restricted cycles becomes obvious. Figure 4b shows that as the network load increases
to 0.6, the access delay profoundly affects t h e end-to-end delay, and that the delay incurred for privileged nodes in
PACCI is much lower than that in ACCI. This demonstrates
that PACCI ensures minimal delay to privileged nodes while
5:- - ~ -- req&r n o d e s 0 2 0 4 0 5 0 6 0 7 5 0 9 a ) N e t w o r k load 1 0 0 0 0 0 - - -- _- -~ h RSiRG - 1 ,'4 for rcguldr node.; \
RS,'RC-IilGfor
,/Gfi
~ ~ ACC!-regular nodes ,,/' ,,
:
5ocoo- >vz
t 60000 b) Network load I 4000 - 2000-
0 0 0 0 I 8000 6000i
4 0 0 0i
O%-- 0 4 -~ -. -. RS:RG=1/16for - - ; 2 RSiRG-1/4 f o r,."
regular nodcs ;'4;'
,$- I
RS/RG= 114 for privileged nodes ~/?
2.- . - - 0.5 0.6 0.75 c.9 C) N e t w o r k loadH Figure 4. Simulation results with respect to network load: a ) throughput vs. network loud; b) access delay i ~ . network load; c)
.- . - . - Delay requirement=0.01 s I / L -J
/
I/
0 0 1 5 s 0.8 0.9 1.o
Network load Figure 5 . Cycle ratio vs. network load achieving various QOS (end-to-end delay.)- . - - -
incurring inevitable but reasonable performance degradation for regular nodes.
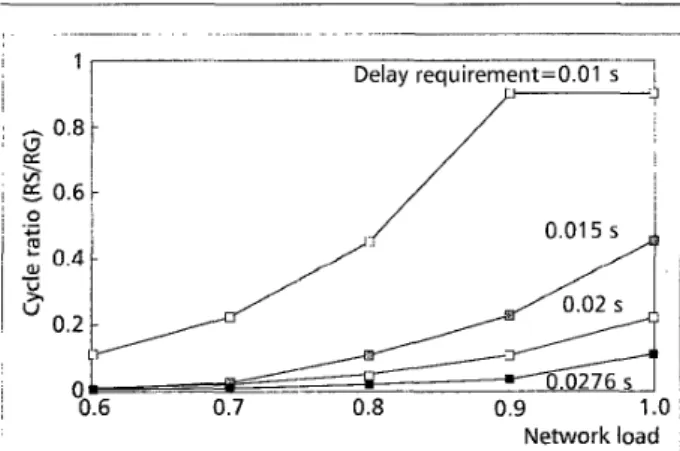
Figure 5 depicts the cycle ratios required in an attempt to satisfy various end-to-end delay requirements (i.e., 0.01, 0.015, 0.02, and 0.0276 s). Simulation results show that no restricted cycle is generated when the network load is below 0.6. In this case, ACCI performs as well as PACCI. However, as the net- work load increases, and as the delay requirement becomes more stringent, higher restricted-to-regular cycle ratios are required in order to ensure any given QoS.
CONCLUSIONS
he article initially presented an assessment of several exist-
T
ing MAC protocols in terms of four criteria: cyclicityicycle gap, access mode, delay invulnerability, and prioritized access. From these protocols, we selected the ACCI mechanism as showing the most promise of satisfying these criteria and mod- eled our proposed PACCI protocol on its more desirable fea- tures. PACCI is suitable for client-server-based gigabit LANs and MANs. It provides fair access for regular nodes by means of regular cycles, and offers prioritized access to privileged nodes by means of restricted cycles. PACCI's bandwidth allo- cation for the regular and restricted cycles is then based on an analytic model in an attempt to guarantee QoS by maintaining throughput under diverse traffic loads. Our analysis consid- ered throughput as a functiion of the cycle ratio (RSIRG) and showed that as RS/RG grows, t h e throughput difference between privileged and regular nodes increases. Simulation results confirmed the accuracy of the analysis. We also found that the throughput and end-to-end delay are not dependent on the cycle ratio under light load conditions, but that as thenetwork load increases, the benefit of having restricted cycles becomes evident. Simulation results also showed that PACCI assures rninimal delay for privileged nodes while incurring reasonable performance degradation for regular nodes.
REFERENCES
[ l ] G. C. 'Watson and S . Tohme, " S f + - A New MAC Protocol for Gb/s Local Area IVetworks," lEE€JSAC, vol. 11, no. 4, May 1993, pp. 531-39. [ 2 ] D r a f t f'roposed Standard, "Distributed Queue Dual Bus (DQDB)
Metropolitan Area Network," P802.6/DI 5, Oct. 1990.
[3] M. C. Yuang and S . Liang, "Assessment and Performance Analysis of DQDE: MAC Protocols," Telecommun. Sys., 1994, pp. 301-1 9. 141 J . 0. I.irnb and C. Flores, "Description of Fasnet, A Unidirectional Local
Area (Communications Network," Bell Sys. Tech. J., vol. 61, part I, Sept. 1982, LIP. 1 4 1 3 4 0 .
[51 L. Fratt,s, F. Borgonovo, and F. A. Tobagi, "Expressnet: A Iiigh-Perfor- mance Integrated-Services Local Area Networks," / € € E JSAC, vol. SAC-
1 , no. 5, Nov. 1983, pp. 898-913.
161 M . A. Marsan and G. Albertengo, "Integrated Voice and Data Net- work," (romp. Commun., vol. 5, no. 3, June 1982, pp. 119-27. [7] M . Ceria, P. Rodrigues, and C. Yeh, "BUZZ-NET: A Hybrid Random
Accessh'irtual Token Local Network," Proc. GLOBECOM '83, San Diego, [8] F. Borgcinovo e t al., "Performance of FQDB, A Fair MAC Protocol for
Dual Bur; Networks," Proc. INFOCOM '92, Florence, Italy, pp. 210-18. 191 M . M . Nassehi, "Cyclic-Reservation Multiple-Access Scheme for Gb/s
LANs and MANs based on Dual-Bus Configuration," Proc. EFOCiLAN
'90. June 1990, pp. 246-51.
[IO] M . C Yuang and 5 . C. Wen, "MRACMAN: A High-Throughput Back- bone IVIIztropolitan Area Network using Simplified Bridges," Proc. /€€€
SUPERCOMMKC '92, Chicago, IL, June 1992, pp. 390-94.
[ I 11 A. Baiocchi e t al., "The ACCI Access Protocol for A Twin Bus ATM Metropolitan Area Network," Proc. lNFOCOM '90, San Francisco, CA, June 1990, pp. 165-74.
[I21 Y. Ohb(3, M. Murata, and H. Miyahara, "Analysis of lnterdepature Pro- cesses for Bursty Traffic i n ATM Networks," /€€€ JSAC, vol. 9, no. 3, Apr. 1'9511, pp. 468-76.
CA, DEC. 1987, pp. 1509-13.
BIOGRAPHY
MARIA C. YUANG received the B.S. degree in applied mathematics from the National Chiao Tung University, Taiwan, in 1978; the M.S. degree in com- puter science from the University of Maryland, College Park, Maryland, in 1981; and the Ph.D. degree in electrical engineering and computer science from the Ikdytechnic University, Brooklyn, New York, in 1989. From 1981 t o 1990, !;he was w i t h AT&T Bell Laboratories and Bell Comrnunications Research (Bellcore), where she was a member of technical staff working on high-speed networking and protocol engineering. She has been an associ- ate professor i n computer science and information engineering at the National Chiao Tung University, Taiwan, since 1990. Her current research interests iiiclude high-speed networking, multimedia communications, per- formance analysis, ATM network management, and protocol engineering.
JEN C. LIU w,as born in Taiwan, Asia, in 1968. He received the B.S. degree in computer science and information engineering from National Chiao Tung University, Taiwan, in 1991, and is currently a Ph.D. candidate in the same department. His doctoral research is focused on high-speed networks, mul- timedia networks, high-performance transport communication systems, and modeling arid performance evaluation of computer communication systems.
-