Chaotic Maps-Based Password-Authenticated Key Agreement
Using Smart Cards
Cheng Guo1, Chin-Chen Chang2,3 1Department of Computer Science,
National Tsing-Hua University, Hsinchu, 30013 Taiwan E-mail: guo8016@gmail.com
2Department of Information Engineering and Computer Science, Feng Chia University, Taichung 40724, Taiwan
E-mail: alan3c@gmail.com
3Department of Biomedical Imaging and Radiological Science, Chinese Medical University, 40402, Taiwan
E-mail: alan3c@gmail.com
Correspondence address: Professor Chin-Chen Chang
Department of Information Engineering and Computer Science, Feng Chia University,
No. 100 Wenhwa Rd., Seatwen, Taichung 40724, Taiwan, R.O.C. Email: alan3c@gmail.com TEL: 886-4-24517250 ext. 3790 FAX: 886-4-27066495
Chaotic Maps-Based Password-Authenticated Key Agreement
Using Smart Cards
Cheng Guo1, Chin-Chen Chang2,3 Abstract
Password-based authenticated key agreement using smart cards has been widely and intensively researched. Inspired by the semi-group property of Chebyshev maps and key agreement protocols based on chaotic maps, we proposed a novel chaotic maps-based password-authenticated key agreement protocol with smart cards. In our protocol, we avoid modular exponential computing or scalar multiplication on elliptic curve used in traditional authenticated key agreement protocols using smart cards. Our analysis shows that our protocol has comprehensive characteristics and can withstand attacks, including the insider attack, replay attack, and others, satisfying essential security requirements. Performance analysis shows that our protocol can refrain from consuming modular exponential computing and scalar multiplication on an elliptic curve. The computational cost of our protocol compared with related protocols is acceptable.
Keywords: Chaotic map, authentication, key agreement, smart card 1. Introduction
With the rapid growth of network technology [1-3] and its growing popularity, user authentication has become increasingly important. The goal of user authentication is to provide the confirmation of two communication entities’ true identities in an open network environment. Meanwhile, in the process of identity authentication, two parties also agree with a common session key used to encrypt their communications over an insecure channel. Many password-based authenticated key agreement protocols [4-6] have been proposed in recent years, where a user can achieve the purpose of identity authentication by submitting his/her identity and password to the server.
Currently, smart card-based user authentication schemes [5, 7-18] have been widely and intensively researched due to their low computational cost, convenient portability, and cryptographic properties. In 2000, Hwang and Li [7] utilized public-key cryptography to propose a remote user authentication scheme with smart cards. In 2005, Fan, Chan, and Zhang [12] proposed a robust remote authentication scheme
using smart cards. Their scheme required neither any password table for verification nor clock synchronization between the user and the server. Meanwhile, their scheme can resist a series of attacks. Juang, Chen, and Liaw [13] proposed in 2008 a new password-authenticated key agreement protocol based on elliptic curve cryptosystems. Their scheme not only satisfied all the criteria of Fan et al.’s scheme but also provided identity protection and session key agreement, and enhanced efficiency by using elliptic curve cryptosystems. In 2009, Sun et al. [14] proposed an improved scheme to overcome the weakness of Juang et al.’s protocol, including inability of the password-changing operation, the session-key problem, and inefficiency of the double secret keys. In 2010, Li et al. [17] also proposed an anonymous password- authenticated key agreement to strengthen the securities of Juang et al.’s protocol by providing initiator untraceability, as well as identity protection property.
With the rapid development of theory and application of chaos, more and more public key cryptosystems [19, 20] based on chaos theory have been studied widely. In 2007, Xiao, Liao, and Deng [21] proposed a novel key agreement protocol based on chaotic maps. In their scheme, following the original Diffie-Hellan key agreement protocol, they utilized the semi-group property of Chebyshev chaotic maps to establish a key agreement protocol. In 2008, Xiao, Liao, and Deng [22] used timestamps to improve the security of original chaotic maps-based key agreement protocols.
Since the smart cards usually do not support powerful computation capability, and cryptographic protocols based on chaotic maps are suitable for environments where processing power, storage space, or power consumption is constrained, it is worthwhile to develop chaotic maps-based authentication and key-agreement protocols with smart cards instead of using modular exponential computing or scalar multiplication on elliptic curves.
To the best of our knowledge, no smart card-based password-authenticated protocols utilize chaotic maps to meet the requirement for key agreement in the literature to date. Enlightened by key agreement [21-27] based on Chebyshev chaotic maps, we propose a novel chaotic maps-based password-authenticated key agreement protocol using smart cards that satisfies almost all the benefits of existing authentication protocols with smart cards, including the following characteristics: 1) The computational cost of the smart card is low;
2) The server does not need to keep the table containing IDs and passwords of users; 3) Our protocol can withstand a series of attacks;
4) The user’s identity can be well-protected; 5) The common session key can be established;
6) The user has the ability to choose and change his/her password.
The remainder of the paper is organized as follows: In the next section, we introduce some preliminaries. In Section 3, we demonstrate our proposed protocol. Section 4 presents some evaluations including functionality, security, and performance of the proposed protocol. Finally, we present our conclusions in Section 5.
2. Preliminaries
In this section, we briefly introduce Chebyshev chaotic maps [21] and an original key agreement protocol [21] based on Chebyshev chaotic maps, which are the major building blocks of our protocol.
2.1 Definition and properties of Chebyshev chaotic maps
Let n be an integer and let x be a variable with the interval [-1,1]. Chebyshev polynomial map T Rn: R of degree n is defined using the following recurrent relation: 1 2 ( ) 2 ( ) ( ), n n n T x xT x T x (1) where n2, T x0( ) 1 , and T x1( )x.
The first few Chebyshev polynomials are: 2 2 3 3 4 2 4 ( ) 2 1, ( ) 4 3 , ( ) 8 8 1. T x x T x x x T x x x
One of the most important properties is that Chebyshev polynomials are the so-called semi-group property which establishes that
( ( )) ( ).
r s r s
T T x T x (2)
An immediate consequence of this property is that Chebyshev polynomials commute under composition
( ( )) ( ( )).
r s s r
T T x T T x (3)
In order to enhance the security, Zhang [19] proved that semi-group property holds for Chebyshev polynomials defined on interval ( , ). In our proposed protocol, we utilize the enhanced Chebyshev polynomials:
1 2
( ) (2 ( ) ( ))(mod ),
n n n
T x xT x T x N (4)
where n2, x ( , ), and N is a large prime number. Obviously,
( ) ( ( )) ( ( )).
r s r s s r
T x T T x T T x (5)
2.2 Key agreement protocol based on Chebyshev chaotic maps
agreement protocol based on Chebyshev maps:
1) A and B chooses a random number x [ 1,1] together, and x needs not to be kept secret;
2) A chooses a random large integer r and computes X=Tr(x), and then sends X to B; 3) B chooses a random large integer s and computes Y=Ts(x), and then sends Y to A; 4) A can compute the secret key k T Y r( )T T xr( ( ))s , and B can compute the secret
key k T Xs( )T T xs( ( ))r .
Due to the semi-group property, k k T xrs( ), A and B can achieve the common secret session key used to encrypt the communications between A and B.
3. Our proposed protocol
In this section, we propose a novel password-authenticated key agreement protocol based on chaotic maps. Our proposed protocol contains four phases: 1) the parameter generation phase; 2) the registration phase; 3) the authentication phase; 4) the password change phase.
The notations utilized in this paper are listed as follows.
U user
S server
ID user’s identity
PW identity of the conference member Ui 1
T the user U’s timestamp 2
T the server S’s timestamp *
T the time of receiving the login message
T
the time threshold
|| string concatenation operator
h(.) public collision-free one-way hash function
(.)
k
E secure symmetric encryption algorithm with the secret key
k
(.)
k
D secure symmetric decryption algorithm with the secret key
k
SK the common session key 3.1 Parameter generation phase
In this phase, the server S needs to choose some parameters as follows:
1) The server chooses a public key scheme based on Chebyshev chaotic maps, and its public key is ( , ( ))x T xs and its private key is s;
3) The server selects a symmetric key cryptosystem with encryption Ek(.) and decryption Dk(.), where k is the symmetric key.
3.2 Registration phase
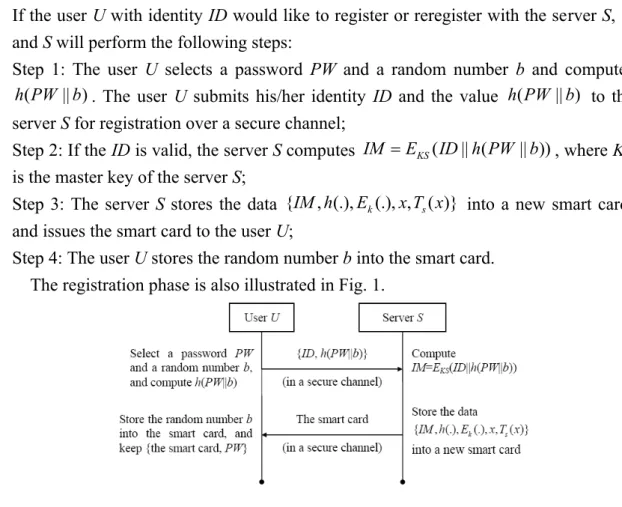
If the user U with identity ID would like to register or reregister with the server S, U and S will perform the following steps:
Step 1: The user U selects a password PW and a random number b and computes
( || )
h PW b . The user U submits his/her identity ID and the value h PW b( || ) to the server S for registration over a secure channel;
Step 2: If the ID is valid, the server S computes IM EKS(ID h PW b|| ( || )), where KS is the master key of the server S;
Step 3: The server S stores the data {IM h, (.),Ek(.), , ( )}x T xs into a new smart card, and issues the smart card to the user U;
Step 4: The user U stores the random number b into the smart card. The registration phase is also illustrated in Fig. 1.
Figure 1 The registration phase.
3.3 Authentication phase
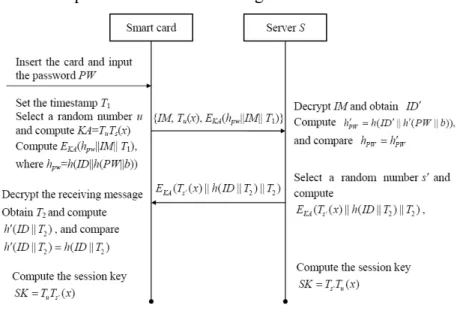
After completing this phase, the user U and the server S can achieve the goal of mutual authentication and establish an agreed-upon session key used in subsequent communication. If user U wants to log in to the server S, the user U and the server S will perform the following steps:
Step 1: The user U first inserts his/her smart card into a card reader and inputs the password PW;
Step 2: The smart card sets the current system time T1 as the timestamp. Then, the smart card selects a random number u and computes KA T T x u s( ). The smart card further computes EKA(hPW ||IM T|| )1 , where hPW h ID h PW b( || ( || )). Then the smart card sends the message {IM T x E, ( ),u KA(hPW ||IM T|| )}1 to the server S;
Step 3: After receiving the message {IM T x E, ( ),u KA(hPW ||IM T|| )}1 , the server S computes KA T T x u s( )T T xs u( ) using his/her private key s, and further decrypts
1
( || || )
KA PW
E h IM T . Then, the server S check whether * 1
T T T;
Step 4: The server S decrypts IM using his/her master key KS and obtains ID and
( || )
h PW b . Then, the server computes hPW h ID h PW b( || ( || )) and compares whether hPW hPW. If the verification is false, the server S terminates this session. If the verification is successful, the server S believes that the user U is valid;
Step 5: The server S selects a random number s and computes T xs( ). Then, the server S computes EKA( ( ) || (T xs h ID T|| ) || )2 T2 , where T2 is the server S’s current system time, and sends this message to the smart card;
Step 6: Upon receiving the message EKA( ( ) || (T xs h ID T|| ) || )2 T2 , the smart card decrypts this message using KA and obtains T2. Then it compares whether the delay is acceptable. The smart card further computes h ID T( || )2 , and compares whether
2 2
( || ) ( || )
h ID T h ID T . If the equation holds, the server is authenticated;
Step 7: The user U and the server S compute the common session key,
( ) ( )
u s s u
SK T T x T T x , respectively.
The authentication phase is also shown in Fig. 2.
Figure 2 The authentication phase.
3.4 Password change phase
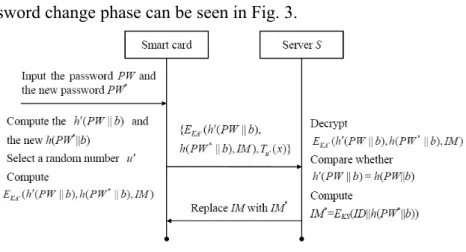
In the proposed scheme, if the user U wants to change his/her password, he/she performs the following steps:
Step 1: The user U inserts his/her smart card into a card reader, enters the old password PW, and requests to change the password. Then, the user U enters the new password PW*;
Step 2: The smart card first computes the h PW b( || ) and the new h PW( *|| )b . Then the smart card selects a random number u and computes
*
( ( || ), ( || ), )
KA
E h PW b h PW b IM , where KA T T xu s( ). Finally, the smart card sends
the message *
{EKA( (h PW b h PW || ), ( || ),b IM T x), u( )} to the server;
Step 3: Receiving this message, the server computes KA T T xu s( )T T xs u( ) and
decrypts *
( ( || ), ( || ), )
KA
E h PW b h PW b IM and IM using KA and KS respectively.
Then the server compares whether h PW b( || )h PW b( || ). If the equation holds, the
server computes * *
( || ( || ))
KS
IM E ID h PW b , and then replaces IM with * IM .
The password change phase can be seen in Fig. 3.
Figure 3 Password change phase.
4. Evaluation of the proposed protocol
In this section, we focus on the functionality, security and performance of the proposed protocol, and make some corresponding comparisons with other related works.
4.1 The analysis of functionality and security
We first argue from the viewpoint of functionality that, compared with related works, the proposed protocol preserves high criteria. We examine our protocol as follows. 1) No password table and verification table.
In a password-based authenticated key agreement protocol, during the registration phase, the user submits his/her identity and password to the server in a secure channel. Then, the server records this message in a password table stored in plain-text or cipher-text form. In the authentication phase, the user inputs his/her identity and password to the server, then the server needs to verify the validity of the user by comparing the message received with the corresponding record. The password table in plain-text form can easily be revealed if the sever is compromised. Therefore, the
password table is usually encrypted into a verification table. In the previous protocols [13, 14, 17], the server required a verification table instead of maintaining a password table. However, the verification table still results in paying for the maintenance cost and suffering from the password-guessing attack.
In our protocol, the server encrypts the verification information using his/her master key and stores it in the smart card. In the authentication phase, the server can derive the verification information from the smart card and decrypt the information. Therefore, the server not only does not need to require a password table, but also does not need to maintain a verification table.
2) Choosing and changing of passwords by users.
In the registration phase, the user can select his/her favorite password and submit it to the server. Furthermore, the proposed scheme provides users the ability to change their passwords. In the password change phase, the user can submit his/her identity, original password, and new password to the server. If the server confirms the true identity of the user, the server can compute IM*, and replace IM with IM* to finish the changing of the password.
3) Identity protection.
The protocol of Juang et al. [13] first proposed the identity protection requirement. In their protocol, the user’s identity is included in parameter bi, which is protected by the symmetric encryption algorithm in the log-in phase. Even though the adversary intercepts the communication between the user and the server, he/she cannot obtain the user’s identity information. However, in Juang et al.’s protocol, the smart card contains the user’s identity information in plain-text form. So, Sun et al. pointed out that if the smart card lost, the user’s identity information will be revealed. Sun et al.’s protocol created more comprehensive identity protection to address this problem.
In the proposed protocol, the user’s identity is contained in the parameter IM, which is encrypted using the server’s master key and stored in the smart card. In the authentication phase, the user’s identity is also transmitted by sending the parameter
IM to the server. Therefore, the user’s identity can be protected even if the smart card
is lost.
Then, we analyze the security of the proposed scheme. Here, we claim that our scheme can satisfy the following security properties: 1) Mutual authentication; 2) Withstanding the insider attack; 3) Withstanding the replay attack; 4) User’s identity anonymity. The comparison of the proposed scheme with others is summarized in Table 1.
1) Mutual authentication.
In the proposed protocol, the goal of mutual authentication is to confirm the user’s and the server’s true identities, and establish a common session key between the user
and the server.
In Step 2 of the authentication phase, the smart card first selects a random number
u and computes KA T T x u s( ). Then, the smart card computes
( || ( || ))
PW
h h ID h PW b and further computes EKA(hPW ||IM T|| )1 . The smart card then sends the message {IM T x E, ( ),u KA(hPW ||IM T|| )}1 to the server S. The server S computes KA T T x s u( ) using his/her private key s, and further decrypts
1
( || || )
KA PW
E h IM T and IM using KA and KS, respectively. The server S obtains ID
and h PW b( || ), and computes hPW h ID h PW b( || ( || )). If hPW hPW, then the server can confirm that the user’s identity is valid and the corresponding password is correct.
In Step 5 of the authentication phase, the server S selects a random number s and computes T xs( ). Then, the server S computes EKA( ( ) || (T xs h ID T|| ) || )2 T2 and sends this message to the smart card. The smart card can decrypt this message using KA and computes h ID T( || )2 , and further compares h ID T( || )2 h ID T( || )2 . Since only the server S has the master key KS and the current session key KA, we have reason to believe that if the equation holds, the server is authenticated.
In Step 7 of the authentication phase, the user U and the server S compute the common session key, SK T T x u s( )T T xs u ( ), respectively. Since the random number
u and s are selected by the smart card and the server S, respectively, other entities cannot learn the common session key.
2) Withstanding the insider attack.
An insider attack occurs when a malicious attacker intrudes on the server and steals the user’s password. Therefore, the user needs to conceal the password from the server to prevent the insider attack. In the proposed scheme, in the registration phase, the user selects a random number b and computes h PW b( || ). Then, the user submits
( || )
h PW b to the server for registration. So, the server cannot obtain the password information.
3) Withstanding the replay attack.
A replay attack is a form of network attack. In the authentication phase, a valid data transmission is maliciously or fraudulently repeated or delayed. In order to eliminate the requirements of clock synchronization, the previous authentication key agreement schemes with smart cards [12-14, 17] are based on nonce instead of timestamps. However, in the proposed scheme, the smart card is issued by the server. So, there is reason to believe that all users’ smart cards and the server are clock synchronization. Therefore, we utilize timestamps to withstand the replay attack. In Step 2 of the authentication phase, the smart card selects the timestamp T1, and encrypts the T1 and sends it to the server S. Meanwhile, in Step 5 of the authentication phase, the server S also sets a timestamp T2 and sends it to the smart card. Therefore, the user and the
server can determine whether the delay is within an acceptable range by checking T1 and T2.
4) User’s identity anonymity.
With the rapid development of Internet applications, communication privacy has become an increasingly important security requirement. The user’s ID anonymity property means that in the authentication phase, the adversary cannot find out the true user’s ID by intercepting the communication message. Even though the secret information stored in the smart card is compromised, the adversary also cannot obtain any information about the user’s ID.
In our protocol, the user’s ID combined with a random number b is encrypted by the server S using his/her master key KS. The corresponding message
( || ( || ))
KS
IM E ID h PW b is stored in the smart card. So, the adversary cannot obtain the user’s ID even if the smart card is lost. On the other hand, the adversary can intercept the communication between the user and the server. However, the corresponding user’s ID information is encrypted using the server’s master key KS and the common session key KA. Therefore, the proposed protocol provides the user’s identity anonymity.
Table 1
The comparisons between our protocol and related protocols
P1 P2 P3 S1 S2 S3 S4
Our protocol Yes Yes Full Yes Yes Yes Yes
Fan et al. [12] No Yes No Yes Yes Yes Yes
Juang et al. [13] No Yes Half Yes Yes Yes Yes
Sun et al. [14] No No Full Yes Yes Yes Yes
Li et al. [17] No Yes Half Yes Yes Yes Yes
Song [18] Yes Yes No Yes No Yes No
P1: No password table and verification table; P2: Choosing of passwords by users; P3: Identity protection; S1: Mutual authentication; S2: Withstanding the insider attack; S3: Withstanding the replay attack; S4: User’s identity anonymity.
4.2 Performance analysis
In this section, we evaluate some performance issues of the proposed scheme, and make a comparison with the related schemes.
Contrary to the traditional public key cryptosystems based password-authenticated key agreement protocols [13, 14, 17, 18], in the proposed protocol, we utilize the
semi-group property of Chebyshev polynomials to promote the mutual authentication and achieve the common session key. Therefore, no time-consuming modular exponential computing and scalar multiplication on elliptic curves are involved in the authentication phase. Furthermore, we do not need to establish public key cryptosystems in advance.
However, polynomial computation to a very high degree can be involved in the Chebyshev chaotic map. In [21], the authors gave some software implementation issues to decrease the computational costs. Actually, the security of the proposed protocol no longer totally relies on the hard problem of high-degree polynomials. Therefore, it is unnecessary to select very large numbers as r and s. In [23], authors gave several methods to decrease the computation time of T xn( ). For example, the large number s (r is the same) can be written as
1 2 1 1 2 2 i i i k k k s s s s s s s , then 1 1 1 ( ) ( i( i( ))) i s s s s s k k T x T T T T x .
As to compute T xs( ), one needs only k1 k2 ki iterations of the Chebyshev map instead of s iterations.
Using another method [23], the computation of T xn( ) can be reduced from a linear number of steps to a logarithmic number of steps.
And, the authors [23] also established a table that they used to store the most commonly-used expression of Chebyshev polynomials of different degrees. Therefore, the practical application of the proposed protocol is more efficient than that of the traditional protocols. For more details about the software implementation process of chaotic maps, the reader can refer to [21, 23].
Table 2 illustrates the computational cost comparison between our protocol and related protocols.
Table 2
Computation cost comparisons between our protocol and related protocols
C1 C2 C3 C4 C5 C6 Our protocol 1H 1S+sT 2H+2S+ (u+s)T 2H+3S+ (s+s+u)T 2H+1S+uT 3S+sT
Fan et al. [12] 1H 1H+1S 3H 3H+1S+1E Null Null
Sun et al. [14] — 2H+1S 4H+2M 4H+1S+2M 2H — Li et al. [17] 1H 2H+3S 8H+4S 10H+10S+1M 1H+6S 1H+9S
Song [18] — 2H+E 3H+1S 3H+1S+1E Null Null
C1: computation cost of the user in registration phase; C2: computation cost of the server in registration phase; C3: computation cost of the user in authentication phase; C4: computation cost of the server in authentication phase; C5: computation cost of the user in password change phase; C6: computation cost of the server in password change phase;
H: hashing operation; E: modulus exponential operation; S: symmetric encryption or decryption; M: scalar multiplication on elliptic curve; T: Chebyshev maps; Null: can not provide this functionality. 5. Conclusions
In this paper, we have proposed a novel chaotic maps-based password-authenticated key agreement protocol. Our protocol broke through the traditional methods based on public key cryptosystems. In the proposed protocol, we utilized the semi-group property of Chebyshev chaotic maps to establish the session key between the user and the server. Our analysis indicates that our protocol preserves high criteria. Our protocol can withstand a series of attacks and satisfy essential security requirements. The performance analysis shows that the computational cost of our protocol compared with related protocols is acceptable.
In conclusion, our chaotic maps-based password-authenticated key agreement using smart cards overcomes many drawbacks of previous authenticated key agreement protocols with smart cards. The chaotic maps-based password-authenticated key agreement protocol is a new method. We hope that more research will be conducted to further improve the protocol.
References
[1] C. Lee, M. Hwang, I. Liao, Security enhancement on a new authentication scheme with anonymity for wireless environments, IEEE Transactions on Industrial Electronics 53 (2006) 1683-1687. [2] C. Hwang, L. Chang, Y. Yu, Network-based fuzzy decentralized sliding-mode control for car-like
mobile robots, IEEE Transactions on Industrial Electronics 54 (2007) 574-585.
[3] D.J. He, M. Ma, Y. Zhang, C. Chen, J.J. Bu, A strong user authentication scheme with smart cards for wireless communications, Computer Communications 34 (2011) 367-374.
[4] L. Lamport, Password authentication with insecure communication, Communications of ACM 24 (1981) 770-772.
[5] W. Yang, S. Shieh, Password authentication schemes with smart cards, Computers & Security 18 (1999) 727-733.
[6] W.G. Shieh, J.M. Wang, Efficient remote mutual authentication and key agreement, Computers & Security 25 (2006) 72-77.
[7] M.S. Hwang, L.H. Li, A new remote user authentication scheme using smart cards, IEEE Transactions on Consumer Electronics 46 (2000) 28-30.
[8] H. Sun, An efficient remote user authentication scheme using smart cards, IEEE Transactions on Consumer Electronics 46 (2000) 958-961.
[9] H. Chien, J. Jan, Y. Tseng, An efficient and practical solution to remote authentication: Smart card, Computers & Security 21 (2002) 372-375.
[10] W. Juang, Efficient password authenticated key agreement using smart cards, Computers & Security 23 (2004) 167-173.
[11]W. Ku, S. Chen, Weaknesses and improvements of an efficient password based remote user authentication scheme using smart cards, IEEE Transactions on Consumer Electronics 50 (2004) 204-207.
[12] C.I. Fan, Y.C. Chan, Z.K. Zhang, Robust remote authentication scheme with smart cards, Computers & Security 24 (2005) 619-628.
[13] W.S. Juang, S.T. Chen, H.T. Liaw, Robust and efficient password-authenticated key agreement using smart card, IEEE Transactions on Industrial Electronics 55 (2008) 2551-2556.
[14] D.Z. Sun, J.P. Huai, J.Z. Sun, J.X. Li, J.W. Zhang, Z.Y. Feng, Improvements of Juang et al.’s password-authenticated key agreement scheme using smart cards, IEEE Transactions on Industrial Electronics 56 (2009) 2284-2291.
[15] M.S. Hwang, S.K. Chong, T.Y. Chen, DoS resistant ID-based password authentication scheme using smart cards, Journal of Systems and Software 83 (2010) 163-172.
[16] K.H. Yeh, C. Su, N.W. Lo, Y.J. Li, Y.X. Hung, Two robust remote user authentication protocols using smart cards, Journal of Systems and Software 83 (2010) 2556-2565.
[17] X.X. Li, W.D. Qiu, D. Zheng, K.F. Chen, J.H. Li, Anonymity enhancement on robust and efficient password-authenticated key agreement using smart cards, IEEE Transactions on Industrial Electronics 57 (2010) 793-780.
[18] R.G. Song, Advanced smart card based password authentication protocol, Computer Standards & Interfaces 32 (2010) 321-325.
[19] L.H. Zhang, Cryptanalysis of the public key encryption based on multiple chaotic systems, Chaos, Solitons & Fractals 37 (2008) 669-674.
[20] K. Wang, W. Pei, L. Zhou, Y. Cheung, Z. He, Security of public key encryption technique based on multiple chaotic system, Physics Letters A 360 (2006) 259-262.
[21] D. Xiao, X.F. Liao, S.J. Deng, A novel key agreement protocol based on chaotic maps, Information Sciences 177 (2007) 1136-1142.
[22] D. Xiao, X.F. Liao, S.J. Deng, Using time-stamp to improve the security of a chaotic maps-based key agreement protocol, Information Sciences 178 (2008) 1598-1602.
[23] X.Y. Wang, J.F. Zhao, An improved key agreement protocol based on chaos, Communications in Nonlinear Science and Numerical Simulation 15 (2010) 4052-4057.
[24] X.F. Guo, J.S. Zhang, Secure group key agreement protocol based on chaotic hash, Information Sciences 180 (2010) 4069-4074.
[25] Y.J. Niu, X.Y. Wang, An anonymous key agreement protocol based on chaotic maps, Communications in Nonlinear Science and Numerical Simulation 16 (2011) 1986-1992.
[26] E.J. Yoon, II.S. Jeon, An efficient and secure Diffie-Hellman key agreement protocol based on Chebyshev chaotic map, Communications in Nonlinear Science and Numerical Simulation 16 (2011) 2383-2389.
[27] E.J. Yoon, Efficiency and security problems of anonymous key agreement protocol based on chaotic maps, Communications in Nonlinear Science and Numerical Simulation 17 (2012) 2735-2740.