Security Enhancement for Robust Password Authenticated Key Agreement Using Smart Cards
全文
(2) The login protocol When user i wants to login the server, he must insert his smart card into a card reader and inputs his password PWi . Then, the smart card computes a random number r and sends bi , EV (r) to the server. i. After receiving bi , EV ( r ) , the server decrypts bi by i. the. secret. key. s. and obtains h ( PW i || b) || ID i || CI i || h ( ID i || CI i || h ( PW i || b)) , and then the server can compute Vi = h ( ID , s, CI i ) . Therefore, the server will use Vi to decrypt EV (r ) to obtain the random number r. i. However, we find a drawback of Juang et al.’s scheme, that is, the scheme cannot perfectly prevent the offline dictionary attack with the smart card. In our proposed attack, there are two assumptions as follows. First, the smart card has stolen by an attacker and the attacker can obtain the secret data from the smart card. Second, The attacker should intercept communicated messages between the client and the server before. By the above two assumptions, the attacker can get {bi ,Vi , IDi , CI i , b} from the smart card, and bi , EV ( r ), x = r ⊕ u i , y = h( r || u ), L = h(h(( PWi || b) | Vi || r || i. from the communication channel. Then the attack is shown as follows. u). Step 1: The attacker uses Vi to decrypt EV (r ) to get r. i. Then the server checks if 1. after decrypting bi , the authentication tag h ( ID i || CI i || h ( PW i , b )) is valid, 2. IDi is in the registration table in the server, and 3. CI i is stored in the registration table. If any of the above verifications is false, the server revokes the login request and the phase stops. If all of the above verifications are true, the server generates a random number u and computes x = r ⊕ u and y = h ( r || u ) . Then, the server sends (x,y) to user i. After user i receives (x,y), he computes x ⊕ r to obtain u and checks if y is equal to h( r || u) . If no, user i revokes the login protocol. Otherwise user i computes L = h(h( PWi || b) ||Vi || r || u ) and a session key S k = h(Vi , r, u ) , and then sends L to the server. Now, the server is authenticated by user i. After receiving L, the server checks if L is equal to h( h( PWi || b) ||Vi || r || u) , If no, the server revokes the login request and the login protocol stops. Otherwise the server computes a session key S k = h (Vi , r , u ) and accepts the login request. Now, user i and the server authenticate each other and can use the session key S k = h(Vi , r, u ) in secure communication soon.. Step 2: The attacker uses r to get u from x. Step 3: The attacker uses {Vi , r, u, b} to make an off-line password guessing attack on L. Then the attacker can use the offline dictionary attack with the smart card to attack Juang et al.’s scheme successfully.. 4. Our proposed scheme In this section, we propose a new scheme based on elliptic curve cryptosystems to remedy the weakness of Juang et al.’s scheme. Our proposed scheme consists of five phases: the parameter generation phase, the registration phase, the precomputation phase, the login phase and the password changing phase. Except of notations of Juang et al.’s scheme, we define additional notations in our proposed scheme, and the remainder notations are the same with Juang et al.’s scheme. Note that the proper encryption mode needs to be used, such as the Cipher Block Chaining (CBC) mode. We show our proposed additional notations as the following.. Notations P:. The changing password protocol. A large prime.. E P : The elliptic curve equation over Z P .. When user i needs to change his password, he must agree a session key with the server through the login protocol in advance. Then the user can uses the session key to encrypt the changing password message {IDi , h( PWi * || b* )} and sends E S ( IDi , h( PWi * || b* )) to the server. Then the. x : The server’s private key based on elliptic curve cryptosystems. PS : The server’s public key based on elliptic curve cryptosystems. G : The generator point of a large order.. server. The parameter generation phase. k. computes. the. new. secret. information after the server receiving the message, and sends E S (bi * ) to *. * * * bi = E s (h( PWi || b * ) || IDi || CI i || h( IDi || CI i || h ( PWi || b ))) k. user i. User i then decrypts the message by the session key and stores b and b* in his smart card. *. i. 3. Weakness of Juang et al.’s scheme. In this phase, the server needs to generate some parameters as the following. 1. The server chooses a large prime P and selects two field elements a ∈ Z P and b ∈ Z P , where a and b must satisfy 4a 3 + 27b 2 ( mob P) ≠ 0 . The elliptic curve equation E P : y 2 = x 3 + ax + b over Z P is defined.. - 899 -.
(3) 2. The server finds a generator point G of the order n, where n is a large divisor, and n × G = 0 . 3. The server selects a random number x as his private key and safely keeps it in his secret storage. 4. The server computes the public key PS = ( x × G) and publishes the parameters ( PS , P, EP , G, n) .. The registration phase When user i needs to register in the server, he performs the following phase with the server. First, the server verifies user i by using a secure identification scheme. Then user i sends {IDi , h( PWi || b)} to the server via a secure channel, where b is a random number chosen by user i and PWi is a password chosen by user i. After receiving {IDi , h( PWi || b)} , the server creates the card identifier CI i , which is the number of cards that the server has issued to user i. If ID i is a new user, then the server will set CI i = 1 and store {IDi , CI i } in the registration table in the server. If the server issues a new card to user i that registered before, the server can get {IDi , CI i } from the registration table. Then the server computes CI i = CI i + 1 and stores {IDi , CI i = CI i + 1} in the registration table in the server. The server generates bi = E s (h( PWi || b) || IDi || CI i || h( IDi || CI i || h( PWi || b))) and Vi = h( IDi ,s, CI i ) . The server then issues the smart card to user i that contains {bi ,Vi , IDi , CI i } . When getting this smart card, the user then stores b into the smart card. The memory of smart card contains {bi , V i , ID i , CI i , b} . User i then keeps the smart card and PW i for the login phase.. The precomputation phase. decrypt EV (e) to obtain e = ( r × G ) . Then the server i. checks if 1. decrypting. bi can get the authentication tag ( IDi || CI i || h( PWi , b)) ,. 2. IDi is in the registration, and 3. CI i is stored in the registration table. If any of the above verifications is false, the server revokes the login request. If all of the above verifications are true, the server selects a random number u and computes c = ( e × x ) = ( r × x × G ) and M S = h(c || u || Vi ) . Then the server sends u, M s to the smart card. After the smart card receiving u,M s , it computes M S and check if M S is equal to h(c || u || Vi ) . If no, the smart card revokes the login phase. Otherwise the smart card computes M U = h(h( PWi || b) ||Vi || c || u) and a session key S k = h(Vi , c, u) , then sends M U to the server. At this time, the server is authenticated by the smart card. When receiving M U , the server checks if M U is equal to h(h( PWi || b) ||Vi || c || u) , If no, the server revokes the login request. Otherwise the server accepts the login request and computes a session key S k = h(Vi , c, u) . Then the smart card and the server authenticate each other and can use the session key S k = h(Vi , c, u) in secure communication soon.. The changing password protocol When user i needs to change his password, he needs to agree a session key with the server through the login phase in advance. Then the smart card can uses the session key to encrypt the changing password message * {IDi , h( PWi || b* )} and sends E S ( IDi , h( PWi * || b* )) to the k. The smart card selects a random number r, and computes e = ( r × G ) and c = ( r × Ps ) = ( r × x × G ) as a point over E P before the start of the login phase. Then it stores (c,e) into it’s memory for use in the login phase.. The login phase When user i wants to login the server, he must inserts his smart card into a card reader and inputs his password PWi . In our proposed scheme, the smart card will complete the precomputation phase before the login phase. After user i has inputted the password and the smart card has finished the precomputation phase, the smart card sends bi , EV ( e) to the server, where i. Vi = h( IDi , s, CI i ) .. After receiving bi , EV (e) , the server decrypts bi by i. the secret key s and obtains h( PWi || b) || IDi || CI i || h( IDi || CI i || h( PWi || b)) , and then the server computes Vi = h( IDi , s, CI i ) . Therefore, the server will use Vi to. server. The server computes the new secret information bi = E s ( h( PWi || b * ) || IDi || CI i || h( IDi || CI i || h ( PWi || b * ))) *. *. *. after the server receiving the message, and sends E S (bi * ) k. to the smart card. The smart card then decrypts the message by the session key and stores bi * and b* in its memory.. 5. Security analysis In this section, we will analyze the security of our proposed scheme.. (1) Mutual authentication In our proposed scheme, the goal of mutual authentication is to establish an agreed session key Sk between the user and the server [5]. Let A mean the user, B mean the server and A ←⎯S⎯k → B denote that the user and the server share the common session key Sk. If there is an Sk such that A believes A ←⎯S⎯k → B and B believes A ←⎯S⎯k → B for the transaction, we can say the mutual authentication. - 900 -.
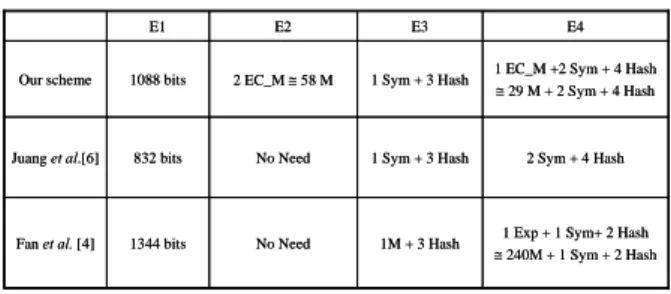
(4) is finished between A and B [5]. If a scheme can deduce the following statement [5]: A believes B believes A ←⎯S⎯k → B and B believes A believes A ←⎯S⎯k → B, we can say that it satisfies strong mutual authentication. In step 2 of the login phase of our proposed scheme, after A receives the message u, M s from B, he will compute M s and verify if M s = h(c || u || Vi ) . A can compute the session key S k = h(Vi , c, u) and will believe A ←⎯S⎯k → B. Since the random number r is chosen by A, e = ( r × G ) is computed by A in the precomputation phase, A believes that e is fresh and can only be decrypted by B using the shared secret key Vi , and only B can use the secret key x to compute c = ( e × x ) , then A believes B believes A ←⎯S⎯k → B. In step 3, after B receives the message M U from A, he first checks if the authenticator M U = h(h( PWi || b) || Vi || c || u ) is valid. If yes, he will compute the session key S k = h(Vi , c, u) and then believes A ←⎯S⎯k → B. Since the random number u is selected by B, B believes that the random number u is fresh. On receiving the authenticator M U from A, B can verify u is embedded in M U by A and then B believes A believes A. Sk ←⎯ ⎯→. B.. (2) Preventing the replay attack The replay attack is that an attacker tries to imitate the user to login the server by resending the messages transmitted between the user and the server. In our scheme, we use the nonces to prevent this kind of attacks. In our proposed scheme, the smart card chooses a nonce r and compute e = ( r × G ) in the precomputation phase, and then he sends it to the server in the login phase. The second nonce u is selected by the server.. password he guesses is correct or not through the tapped messages. Therefore, if the messages have not enough information to verify the guessed password, the scheme can prevent this attack. The first message that between the user and the server is {bi , EV (e)} . The attacker i. cannot verify the password PWi from this message. If the attacker intercept the message M U = h(h( PWi || b) || Vi || c || u) , the attacker also can not guess the password successfully since the entropy of Vi , c and u are all very large.. (5) Preventing the offline dictionary attack with the smart card This attack is the same with the offline dictionary attack without the smart card, except that in this case, the attacker can obtain the secret information stored in the smart card. In order to prevent this attack, the password stored in a smart card must be encrypted by the server’s secret key. Even if the attacker obtains the secret information from the smart card, the attacker also can not obtain the right password. In our scheme, the password stored in the smart card is included in bi . Only the server can use the secret key s to decrypt bi and obtain h( PWi || b) . Since the attacker can not get the hashed password, he can not generate a valid message M U = h(h( PWi || b) ||Vi || c || u) which is used in step 3 of the login phase. Therefore, the attacker cannot obtain the right password and cannot create the message M U .. 6. Performance consideration (1) Low communication and computation cost. (3) Preventing the insider attack The insider attack is that the user’s password is obtained by the server in the registration phase [8]. Therefore, the user must conceal his password from the server to prevent the insider attack. In our proposed scheme, the smart card of the user in the registration phase will generate a random number b and compute h( PWi || b) . Then, the smart card sends h( PWi || b) to the server for registration. Hence the server can not get the correct password.. (4) Preventing the offline dictionary attack without the smart card. We suppose that n in the scheme [4] is of 1024 bits in order to make the discrete logarithm and factoring problems infeasible. We suppose that the block size of secure symmetric cryptosystems is 128 bits and the output size of secure one-way hashing function [10] is 128 bits. We also assume that the modulo number in an elliptic curve is of 163 bits. So it needs 163*2 = 326 bits to store a point in an elliptic curve [7]. In our proposed scheme, the communication cost of the login phase for cryptographic parameters bi , EV ( e) , u, M s and M U is 384+384+64+128+128=1088 i. bits, where u can be 64 bits and bi , EV ( e) must both be i. encrypted in 3 blocks. In Juang et al.’s scheme [6], that for cryptographic parameters bi , EV ( r ) , x, y and L is i. The offline dictionary attack without the smart card is that the attacker can get the tapped messages and attempts to guess the user’s password from the tapped messages. In some case, the attacker’s offline dictionary attack will be successful, if the user’s password is weak and the attacker has enough information to check if the. 384+128+64+128+128 = 832 bits, where r can be 64 bits and bi must be encrypted in 3 blocks. In Fan et al.’s scheme [4], that for cryptographic parameters ((bi || H ( IDi ) || u ) 2 mod n ) , L2 = {α, β} , and L3 is 1024+64+128+128 = 1344 bits, where u and α can both be 64 bits.. - 901 -.
(5) In the precomputation phase of our proposed scheme, that needs two multiplications of a number over an elliptic curve. In the login phase, our proposed scheme needs one symmetric key operation and three hashing operations for a client, and needs one multiplication of a number over an elliptic curve, two symmetric key operations and four hashing operations for a server. The computation cost of Juang et al.’s scheme [6] in the login protocol requires one symmetric key operation and three hashing operations for a client, and needs two symmetric key operations and four hashing operations for a server. The computation cost of Fan et al.’s scheme [4] in the login protocol requires one modular multiplication and three hashing operations for a client, and needs one exponential operation, one symmetric key operation and two hashing operations for a server. We assume that the multiplication of a number over an elliptic curve is approximant to twenty-nine modular multiplications, and the exponential operation is approximant to two hundred and forty modular multiplications [7]. The efficient comparison between our scheme and related schemes is shown in the Table 1.. (4) No time-synchronization problem In the login phase of our scheme, we use two nonces u and r to prevent the replay attack. No logical time clocks are needed.. (5) Identity protection The user’s identity ID i in our scheme is included in bi , which is sent to the server and encrypted by using the secret key s in the login phase. Only the server can decrypt bi and get IDi . Therefore, our proposed scheme can provide identity protection.. (6) Revoking the lost cards without changing the user’s identity In our proposed scheme, if the user loses his smart card, the server can revoke the lost card. When this user needs to obtain a new smart card, the server will set CI i = CI i + 1 and issues a new smart card to the user.. (7) Session key agreement Table 1. Efficient comparison between our scheme and related schemes E1. E2. E3. E4. Our scheme. 1088 bits. 2 EC_M ≅ 58 M. 1 Sym + 3 Hash. 1 EC_M +2 Sym + 4 Hash ≅ 29 M + 2 Sym + 4 Hash. Juang et al.[6]. 832 bits. No Need. 1 Sym + 3 Hash. 2 Sym + 4 Hash. Fan et al. [4]. 1344 bits. No Need. 1M + 3 Hash. 1 Exp + 1 Sym+ 2 Hash ≅ 240M + 1 Sym + 2 Hash. In our scheme, the user and the server both can agree a session key S k = h(Vi , c, u) after the login phase.. 7. Conclusion. E1: communication cost of the login phase; E2: computation cost of the precomputation phase; E3: computation cost of the login phase for a client; E4: computation cost of the login phase for a server; Exp: exponential operation; Hash: hashing operation; Sym: symmetric encryption or decryption; M: a modular multiplication operation; EC_M: multiplication operation of a number over an elliptic curve.. (2) No password table In order to prevent the server from holding and protecting a large password table, a password or a verification table should not be stored in the server. In our proposed scheme, the hashed password with a random number is encrypted in h( PWi || b) bi = E s (h( PWi || b) || IDi || CI i || h( IDi || CI i || h( PWi || b))) and is sent to the server. The server does not need to keep a password table. In our proposed scheme, the server only needs to keep a registration table to store each card’s identifier. This table is smaller than the password table and does not need to keep secret.. In this paper, we have shown Juang et al.’s scheme’s drawback and proposed a new scheme to remedy this drawback. Our proposed scheme can prevent the offline dictionary attack with the smart card perfectly and the efficiency of our scheme is approximate to that of Juang et al.’s scheme. Acknowledgment. This work was supported in part by the National Science Council of the Republic of China under the Grant NSC 95-2221-E-128-004-MY2, and by the Taiwan Information Security Center (TWISC), National Science Council under the Grants NSC 95-3114-P-001-001-Y02 and NSC 94-3114-P-011-001.. References [1]. [2]. (3) Choosing and changing the password by users. [3]. In our proposed scheme, every user can select his password. Hence the user can easily remember the password. Also, we provide the password changing phase for users to change their passwords.. [4]. - 902 -. M. Burrow, M. Abadi and R. Needham, “A logic of authentication,” ACM Trans. Comput. Syst., Vol. 8, 1990, pp. 18-36. W. Diffie and M. Hellman, “New Directions in Cryptography,” IEEE Trans. Inform. Theory, Vol. 22, pp. 644-654, 1976. J. Don, A. Menezes and S. Vanstone, “The elliptic curve Digital Signature Algorithm (ECDSA),” International Journal of Information Security, Vol. 1, pp. 36-63, 2001. C. Fan, Y. Chan and Z. Zhang, “Robust remote authentication scheme with smart cards,” Computer & Security, Vol. 24, 2005, pp. 619-628..
(6) [5]. [6]. [7]. [8]. [9]. [10]. W. Juang, “Efficient password authenticated key agreement using smart card,” Computer & Security, Vol. 23, 2004, pp. 167-173. W. Juang and S. Chen, "Robust and Efficient Password Authenticated Key Agreement Using Smart Cards," the 16th Information Security Conference, pp. 291-298, Taichung, Taiwan, June 2006. W. Juang and L. Wu, "An Efficient Two-Factor Authenticated Key Exchange Protocol Based on Elliptic Curve Cryptosystems," the 11th Information Management and Implementation Conference (IMI’05), pp. 299~306, Taipei, Taiwan, R.O.C., December 2005. W. Ku and S. Chen, “Weaknesses and improvements of an efficient password based remote user authentication scheme using smart cards,” IEEE Transactions on Consumer Electronics, Vol. 50, No. 1, 2004, pp. 204-207. L. Lamport, “Password authentication with insecure communication,” Communications of ACM, Vol. 24, No. 11, 1981, pp. 770-772. R. Merkle, “One-way hash functions and DES,” Advances in Cryptology - Crypto 89 Proceedings, Lecture Notes in Computer Science, Vol. 435, 1989, pp. 428-446.. - 903 -.
(7)
數據
相關文件
reading scheme, cross-curricular projects and RaC, etc.) in consideration of the pedagogy and connection with the curriculum of English Language from the case study of exemplars
reading scheme, cross-curricular projects and RaC, etc.) in consideration of the pedagogy and connection with the curriculum of English Language from the case study of exemplars
Other than exploring the feasibility of introducing a salary scale for KG teachers, we also reviewed the implementation of the Scheme in different areas including funding
Recommendation 14: Subject to the availability of resources and the proposed parameters, we recommend that the Government should consider extending the Financial Assistance
This is to inform kindergartens and primary schools of the “Library Cards for All School Children” scheme and the arrangement of bulk application for library cards of the
The temperature angular power spectrum of the primary CMB from Planck, showing a precise measurement of seven acoustic peaks, that are well fit by a simple six-parameter
training in goal setting (from general to specific) Task 2: Let’s help our students set better goals with reference to the HKDSE writing marking
According to the problem statement and literature reviews, several functionalities are identified for the proposed CBI-PSP, including: (1) a knowledge classifications scheme