A
New Method
to Improve the Performance of
-
TCP
SACK
over Wireless Links
Jeng-Ji
Huang
Department of Electrical Engineering National Taiwan University
Taipei 106, Taiwan
E-mail: hjj@santos.ee.ntu.edu.tw
Abstract-In this paper, a new method to improve TCP SACK’S performance over wireless links is presented. T h e
proposed method attempts to differentiate congestion and corruption loss by the use of tagged segments. Whenever
a congestion loss OCCUPS at a router, a tagged segment is dropped at the router and a notiflcation is generated. Loss
of the tagged segment is eventually detected by the TCP t o serve an indication of congestion. When the tagged seg-
ment is not lost due t o congestion, its survival then further seryes as a trial signal for the TCP t o detect corruption loss. Contrasting to most existing approaches employing explicit notification, our method is attractive in that it re- quires no modiflcation to the receiving end. Simulation results show that our method signifleantly improves the performance of TCP SACK over both low and long delay noisy links.
I. INTRODUCTION
Extending the T C P (Transmission Control Protocol) into the wireless segments has attracted enormous re- search attention in recent years [1]-[18]. One major effort
treats the performance degradation problem of wireless T C P which is caused mainly by TCP’s unable t o discern between network congestion and (wireless) link corrup- tion losses, and the predominant assumption tha t TC P segment loss is a sign of network congestion.
Among the many approaches t o cure this problem, one category falls into providing a robust wireless link using more powerful link-layer protocols, e.g., FEC (Forward Error Correction) or ARQ (Automatic Repeat request)
[l], [Z], or using a performance enhancing proxy ( PE P) a t the boundary of the Internet, e.g., the snoop protocol [3]
or the split-connection protocol [4]. Another category is
t o change T C P to let it become capable of distinguishing these two kinds of loss [7]-[ll]. In this category, side in- formation must be supplied and should be firm and clear enough t o let a sender correctly tell if a loss is due t o corruption and t o avoid triggering unnecessary conges- tion avoidance mechanism. But, if side information has ambiguity, the sender should be rather conservative in preventing network from congestion collapse 1191.
There have been several previous works 191-1111 on pro-
viding clear side information. Their design is t o incorpo-
The vmrk reported in this paper is supported by the National Science Council, Taiwan (NSC 91-2219-E-260-001).
Jin-Fu Chang
Department of Electrical Engineering National Chi Nan University
Puli, Nantou 545, Taiwan
E-mail: jfcbang@ncnu.edn.tw
rate an explicit notification signal into the congestion de- tection mechanism. However, most of them require mod- ifications at both the sender and receiver TCP, and
at
routers or base stations as well. Other approaches, e.g.,
[5]-[7], although affect only TCP implementation at the
sender, the information provided is less clear.
In this paper, a new method to differentiate these two types of segment loss is proposed. When a router is in congestion, a notification is generated by forcefully drop- ping a pretagged segment. Based on whether a congestion notification is detected, the T C P is able to differentiate congestion losses from corruption losses. The proposed congestion notification involves changes at the sender and routers only, no modification is required a t the receiving end.
The rest of this paper is organized as follows. Section I1 gives relevant backgrounds, including related works that use side information for differentiation, and an overview of T C P SACK (TCP with Selective Acknowledgement). We introduce the proposed method in Section 111, and
compare its performance with T C P SACK through sim- ulations in Section IV. Finally, concluding remarks are given in Section V.
11. B A C K G R O U N D S
A . Related Snde-hformatzon Based Works
Side information appears in one of the following forms. RTT (round trip time) [5], (61: The sender deduces that a router may currently encounter congestion from the observation of an increasing RTT. Segment losses are then assumed t o he due t o congestion in this case.
ECN (explicit congestion notification)
[ZO]:
For a T C P connection that is ECN-capable, if a sender receives three duplicateACKs
with the C E (Congestion Experienced) bit set, the sender infers that a segment loss due t o con- gestion has occurred (71.ELN (explicit loss notification) [SI: An ELN bit in a
new form of acknowledgement called ACKELN is judged at the base station, and is used t o explicitly tell that a segment has been lost before it comes t o the base station. Lhack (last hop acknowledgement) 191: A lhack is r e turned to the source for every message received at the
base station, and is used bo indicate to the source that the corresponding message must have been lost due to corruption if the sender does not receive an ACK from the receiving end for this message.
.
W-ECN (wireless-ECN) [lo]: The W-ECN is used asa prompt notification to retransmit lost segments when- ever congestion loss occurs. Thus, it can be used as an indicative signal of congestion.
HACK (HeAder ChecKsum) [ll]: The HACK proposes
to add a separate checksum for the header portion of a T C P segment so that T C P receiver is able to check the integrity of header. The receiver is able t o return a signal ACK back to the sender indicating corruption.
In comparison, RTT or ECN provides less clear infor- mation than the other four. But, implementation of ELN, W-ECN, or HACK requires changes at both sender and receiver, and a t routers or base stations as well; while implementation of RTT or ECN affects the software a t sender only. Lhack though is able to provide a clear sig- nal and requires no change a t the receiver, the signal is subject to loss as it travels hack t o the sender.
B. T C P S A C K
The SACK option of T C P has been standardized and widely deployed in the Internet [12], [21]. In T C P SACK,
the SACK option should he included in duplicate ACKs
[22]. When three consecutive duplicate ACKs are col-
lected a t the sender, fast recovery is triggered and trans- mit window is halved.
Using SACK, a sender can he informed
of
up to three noncontiguous blocks of data that have been received and queued a t the receiver. With this information, the sender is able t o retransmit the segments that comprise the holes in the sequence space, whenever the number of flying seg- ments in the pipe is less than the congestion window. If there are no holes, new data is sent. When an ACK ac- knowledges everything sent before fast recovery was en- tered, the T C P leaves fast recovery.Due to the ability to recover from multiple lost seg- ments in one RTT, it has been shown t h a t T C P SACK provides a better performance than other versions of T C P [4], [14]. In addition, experiment results also show
that T C P SACK is more efficient on noisy large BDP (bandwidth-delay-product) connections [15].
111. THE PROPOSED METHOD
The proposed method is a variant of T C P SACK. It attempts to differentiate losses by the use of tagged seg- ments. Differentiation is facilitated by a new conges- tion detection mechanism, whereas segment losses are no longer directly interpreted as congestion warning unless a tagged segment is declared lost.
A . Tugged Segments
Tagged segments are equivalent t o normal T C P seg- ments except that the priority bit in their I P header is set
low. Like normal segments, payload information is also carried by tagged segments; thus, they must be recovered if they are lost. To T C P receiver, a tagged segment looks exactly the same as a normal segment, since its IP header would have been removed.
Use of low-priority segments can also he found in 1131,
[E], and [23]. They are used as probing packets to mea-
sure the available bandwidth in the network [13], [23], or
are used t o carry information to the receiver more rapidly without harming other flows [16]. In this paper, tagged
(low-priority) segments are used to provide the sender with the information of network congestion.
In the proposed method, one segment is tagged at the source per every window worth of segments. When an ACK returns t o acknowledge successful reception of the previously tagged segment, a next segment is tagged, even when the T C P is undergoing a fast recovery.
B. Droppzng Polacy ut Routers
The proposed method requires the support of a new dropping policy at routers. Under this new dropping pol- icy, whenever congestion loss occurs a t a router, a n e tification is generated by forcefully dropping one tagged segment a t the router. If no such tagged segment is avail- able, the next arriving tagged segment will be dropped, even though the router may become not congested as it arrives. Dropping a tagged segment serves as a notifica- tion to cover congestion losses that have occurred since the drop of the last tagged segment. Loss of a tagged seg- ment will be eventually detected at the sender via SACKS t o serve as a signal indicative of congestion.
It should be noted th at a tagged segment may he force- fully dropped when th e buffer is actually not full. The impact of such extra drop can be either of the following two. One is that this extra drop may lead the T C P t o reenter fast recovery. We shall later in Sec. IILD.1 illus- trate that fast recovery reentering is vital for the proposed method. The other is th at T C P may take more time to recover losses. It is because that, although T C P SACK is able to retransmit multiple losses in one RTT, it in no way says that no matter how many segments are lost all can be retransmitted in one RTT. Thus, the T C P may take an additional RTT to continue t o recover losses due t o the extra drop [24]. We have performed simulations t o
examine its impact on Performance in Sec. N.B; as will be seen, degradation turns out t o he very light.
C. Differentiation Rule
In the proposed method, differentiating losses between congestion and corruption is performed at the end of fast recovery according to whether a tagged segment has been lost in the window upon entering fast recovery. Under our new dropping policy, if loss of a tagged segment
is f o u n d there exists at least one segment loss due to congestion; otherwise, all losses are due to cor-
must slow down its sending rate, even if there is only one segment loss that is due t o congestion. On the contrary, when losses are concluded as due to corruption. the trans- mit window is restored to the value before fast recovery was entered.
Unfortunately, loss of a tagged segment may be due t o not only congestion at a router hut also corruption on the wireless link. Differentiation is conservative by assuming that a congestion event has occurred in this case. However, when a tagged segment is not lost, the survival would provide T C P with a strong indication that no congestion has occurred on the path; thus, all segment losses can he concluded as due to corruption.
Due to that loss of a tagged segment is used as a con- gestion notification, our method involves changes at the sender and routers only. No modification of software is required at the receiver. Furthermore, our congestion no- tification mechanism is robust, since the signal provided is ohviously free from any further damage
as
it loops back to the sender.D. Reliabrlity of the Proposed Method
The proposed method poses two main threats to reli- ability. One is that delayed congestion notification may result from delayed drop of a tagged segment. Another is that route may change.
D . l Delayed Congestion Notification
Under the new dropping policy, as mentioned in Sec. III.B, whenever a congestion loss occurs at a router, one tagged segment needs t o he dropped in order t o generate a notification. If none is available, the next arriving tagged segment is dropped. This results in the following two scenarios.
1. The tagged segment to he dropped is sent before TCP’s entering fast recovery. In this case, the segment would have appeared in the window when fast recovery is entered. Loss of this tagged segment shall be detected at the end of fast recovery, and used t o notify of network congestion.
2. The tagged segment t o he dropped is a new data seg- ment that is sent during fast recovery. This occurs when there are no holes in the window and the number of seg- ments in the pipe is less than the congestion window, as mentioned in Sec. 1I.B. If all losses in the window upon entering fast recovery have h e n recovered, T C P will leave the current fast recovery. In this case, loss of the tagged segment shall be detected in the next
fast
re- covery. According t o our differentiation rule, a sender does not reduce its rate until a congestion is notified. Thus, sender’s response t o a congestion event has to he delayed till when loss of the tagged segment is detected at the end of a later fast recovery. The delay would amount t o ahout one RTT, i.e., the duration of a fast recovery.To solve the above problem, one possible solution is to inject more tagged segments into every window. This
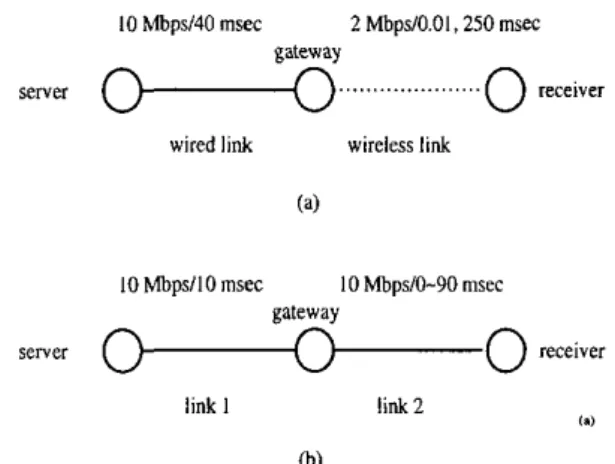
10 MbpsI40 msec 2 Mbpd0.0l ,250 msec gateway
Servel
0
-
0
...0
receive!wired link wireless link (4
IOMbps/lOmsec 10 MbpdO-PO msec
eatewav
1. 1
link 1 link 2
(b)
Fig. 1. The topology in the simulations of (a) a TCP connection over a wireless link and (b) a wired connection.
would force the first scenario to occur more often, and would thus lessen the occurrence of the second. However, the increase would raise the ambiguity or vagueness of our proposed signal, due t o increasing chance that tagged seg- ments are rather corrupted by channel errors. This would as a result reduce the degree of improvement offered by our method.
D.2 Route Changes
In practice, the route of a T C P connection may un- dergo changes during its lifetime, although route changes are normally infrequent 1251. If the ronte has changed
while a congestion event occurs in the old path, conges- tion notification may not be generated by the new path. Without congestion notification, the sender does not r e duce its transfer rate. However, this does no harm to the network since sender has no need t o reduce its rate if no congestion develops along the new path.
IV. SIMULATION RESULTS A N D DISCUSSIONS
In this section, throughput performances of the pro- posed method and T C P SACK are compared via simula- tions. The simulations are conducted using the T C P ns-2 simulator of LBNL (Lawrence Berkeley National Lahora- tory) [26]. The traffic is assumed to he F T P transfers.
The size of each transferred file is 1 Mhytes, and the length of a segment is 1,000 bytes.
A . TCP
Connections over Wireless linksIn this section, performance of the proposed method is examined over a wireless link. The topology in the sim- ulations is depicted in Fig. 1 (a). It consists of a server, a gateway, and a receiver. The wired link between the server and the gateway can he viewed as a path through routers in the Internet. Its bandwidth is assumed to he 10 Mhps [6], [17], and its delay is assumed to be 40 msec [14], (171. The bandwidth of the wireless link between the
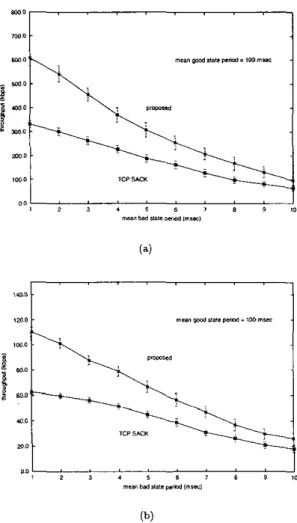
mo, I I 1 2 3 1 I 6 7 B 'i lo m e a DdY.I...rd,mt(r, 0 0 (b)
Fig. 2. Comparison of throughput performance over (a) a low delay
noivy link and (b) a long delay noisy link.
gateway and the receiver is 2 Mbps [7], [17]. But its delay
is taken t o be either 0.01 [ 6 ] , [7] or 250 msec. The for- mer may correspond to a low delay link such as a wireless LAN or cellular system; while the latter may represent a long delay link such as a satellite link.
Correlated channel errors are applied to the wireless link, and are modeled as a two-state, a good state and a bad state, Markov process [IS]. The residual time in either state is exponentially distributed. The mean good state period is fixed at 100 msec; while the mean bad
state period is varied from 1 to 10 msec t o reflect various channel conditions. Segment transmissions are assumed to be successful in a good state and corrupted in a bad state, with probability both equal t o one. After 100 inde- pendent runs, the results are used t o calculate the mean T C P throughput with a 95% confidence interval.
A . l Low Delay Noisy Links
In this section, the throughput performance of the pro- posed method is compared with T C P SACK over low de- lay noisy links. In Fig. 2 (a), our method significantly
outperforms T C P S.4CK, especially for short mean bad state period. The throughput is improved hy 83% for mean bad period equal to 1 msec, 63% for 5 msec, and
47% for 10 msec. The substantial improvement is mainly due to the fact that the proposed method avoids unneces- sary activation of congestion avoidance mechanism, when segment losses are due to corruption and when they are correctly identified.
The advantage of our method becomes less substan- tial for long bad state. It is because that burst length is proportional t o the duration of the bad state. As burst
length increases, the chance of a tagged segment being hit by channel errors increases. Once a tagged segment is lost, even though the loss may be due t o corruption, con- gestion is assumed according to our differentiation rule. This results in unnecessary window reduction, a conse- quence equivalent t o what the original T C P SACK would have; thus, no improvement is seen in this case.
It is clear that improvement offered by our method relies heavily on the survival of tagged segments when channel errors occur on wireless links. In our proposed method, if more protection can be placed on tagged seg- ments a t the link level, further improvement is antici- pated. Ideally, if tagged segments can be completely shielded from channel errors, the proposed method should perform exactly the same as those employing explicit n& tification.
.4.2 Long Delay Noisy Links
Channel errors are shown to have more severe effect on T C P performance over long delay links [13]-1151. It is due to that slow growing of window size after the congestion
window is halved in reaction to a segment loss.
In this section, the performance improvement achieved using our method over long delay noisy links is examined.
As shown in Fig. 2 (b), our method still performs better than T C P SACK by 77% for mean bad state period equal
t o 1 msec, 48% for 5 msec, and 44% for 10 msec. Compare with the previous section, as expected both methods drop dramatically in throughput over long delay noisy links by about 80%. However, loss in improvement of our method
over T C P SACK is light, by less than an average of 10%.
B. TCP Connections ouer Wireline Links
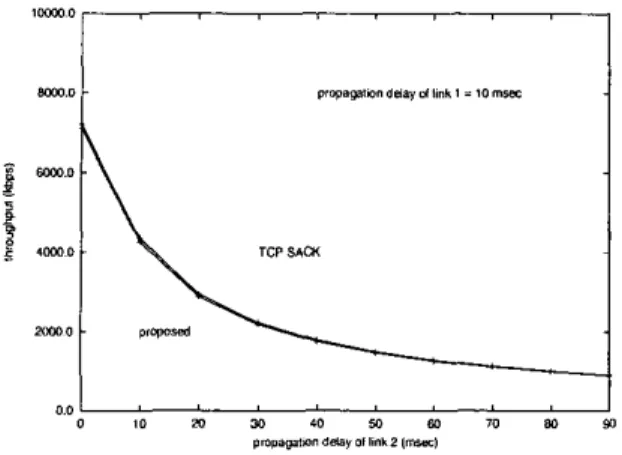
In this section, performance of our method is examined on a connection that consists of wireline links only. The topology in the simulations is depicted in Fig. 1 (b). It consists of a server, a router, and a receiver. The link '1' between the server and the router and the link '2' between the router and the receiver are both wireline of 10 Mbps. The delay of link 1 is fixed at 10 msec; while the delay of
1-0
I 151 P;. K . G. Samaraweera, “Non-congestion Packet Loss Detection for T C P Error Recovery Using Wireless Links,” IEE Pm.-
Commun., vol. 146, no. 4, pp. 222-230, Aug. 1999.
C. Parsa and J. J . Garciil-Luna-Aceves, “Differentiating Con- gestion YS. Random Loss: A Method for Improving T C P Per- formance over Wireless Links,” IEEE W C N C 2000, vol. 1, pp.
[GI
..
90-93, 2000.
R. Ramani and A. Karandikar, “Explicit Congestion Notifi- cation ( E C h l in T C P over Wirelevs Network.” IEEE Inter-
[7]
, ,
e
4 u a o nationol Conference on Personal Wireless CommunicationsW. Ding and A. Jamalipour, “A New Explicit Loss Notifica- tion with Acknowledgement for Wireless TCP,” IEEE Inter-
national Symposium on Personal, Indoor and Mobile Radio
Communications, 2001, vol. 1, pp. 6SG9, Sept. 2001.
J. A. Cobb and P. Agrawal, “Congestion or Corruption? A Strategy for Efficient Wireless T C P Sessions,” IEEE Sympo-
sium on Computers and Communications, pp. 262-268, 1995. 1101 F. P e w , S. Chew., and J . Ma. “An Effective Way to
2000, pp. 495-499, 2000. [8] - 0 191 0 10 20 24 re 50 fa 70 em $3 .mp*sa,londda~ollm** (W, 0.0
. .
Fig. 3. Comparison of throughput performance on a wired connec- Improv; T C P Per6rmance in W/reless/Mobile Netwokks,”
IEEE/AFCEA EUROCOMM 2000. DD. 250-255. 2000.
.:--
L I Y I I .l i l l R. K.‘Balan. B. P. Lee. K. R. R. Knmar. L. Jacob. W. K. 6. link 2 is varied from 0 t o 90 msec t o reflect various RTT
values of a T C P connection.
3, performance of the proposed method is almost equivalent t o that of T C P SACK on a wired connection, with a very slight average degrada- tion of only 2.2%. In the simulations, performance loss of the proposed method is mainly due to the additional time taken for T C P to recover a possible extra drop (of a, tagged segment) as discussed in Sec. 1II.B.
As shown in Fig.
V. CONCLUSIONS
In this paper, we have proposed a method t o improve the performance of T C P SACK over wireless links. The proposed method is made possible by the use of tagged segments accompanied by a new dropping policy. In the proposed method, a sender is able to discern congestion from corruption in large likelihood. In contrast t o most other existing approaches employing explicit notification, our method is attractive in that it requires no modifica- tion a t the receiver. However, a support is required at the routers t o generate congestion notification signals by dropping tagged segments. Through simulations we have compared the performance of our proposed method with T C P SACK over both low and long delay noisy links. The results show that our method significantly improves T C P SACK over a wide range of channel conditions in both environments.
REFERENCES
[l]
[2]
G. Huston, “ T C P in a Wireless Word,” IEEE lntemet Com-
puting, pp. 82-84, MarchIApril 2001.
E Ayanoglu, S. Paul, T. F. LaPorta, K. K. Sabnani, and R. D. Gitlin, “AIRMAIL A Link-layer Protocol for Wireless Net- works,” ACM/Baltzer Wireless Networks, vol. 1, pp. 47-60, Feb. 1995.
[3] H. Halakrishnan, S. Seshan, and R. H. Katz, “Improving T C P j l P Performance over Wireless Networks,” Pmc. 13t
ACM Conf. on Mobile Computing and Networking, pp. 2-11,
Nov. 1995.
C. Partridge, and T. J. Shepard, “ T C P / I P Performance over Satellite Links,” IEEE Network, pp. 4 4 4 9 , Sep./Oct. 1997.
[4]
, , ~~
Seah, and A: L. Ananda, “ T C P HACK: T C P H&r Cheek- s u m Option t o Improve Performance over Lossy Links,“ IEEE
lnjocom 2001, pp. 309-318, 2001.
[I21 S. Floyd, “A Report on Recent Developments in TCP Congen- tion Control,” IEEE Communications Magazine, pp. 84-90, April 2001.
[13] I. F. Akyildiz, G. hlorabito, and S. Palazzo, “TCP-Peach: A New Congestion Control Scheme for Satellite I P Networks,”
IEEE/ACM Pans. on Networking, vol. 9, No. 3, pp. 307-321,
June 2001.
[I41 1. Minei and R. Cohen, “High-Speed Internet Access Through Unidirectional Geostationary Satellite Channels,” IEEE J. Se-
lect. Areas Commun., vol. 17, no. 2, pp. 345-359, Feb. 1999.
[15] C. P. Charalambas, V. S. Frost, and J. B. Evans, “Perfor- mance of T C P Extensions on Noisy High B D P &etworks,”
IEEE Communications Letters, vol. 3 , no. 10, pp. 294-296,
1999.
[IG] V. N. Padmanabhan and R. H. Kats, “TCP Fast Start: A Technique for Speeding up Web Transfers,” Pme. IEEE Globe-
com Internet Mini-GonJerenee, Nov. 1998.
(171 S. hlascolo, C. Casetti, M. Gerla, M. Y. Sanadidi, and R.
W a n g , “ T C P Westwood Bandwidth Estimation for Enhanced Wansport over Wireless Links,” Pmceedings oJACM Mobieom
2001, pp. 287-297, July, 2001.
[I81 M. Zurzi, A. C h o c k a h g u n , and R. R. Rao, “Throughput
Analysis of T C P on Channels with Memory,” IEEE J. Select.
Areas Commun., vol. 18, No. 7, pp. 128%1300, July 2000.
1191 S . Floyd and K . Fall, “Promoting the UseofEnd-to-End Con- gestion Control in the Internet,” IEEE/ACM %an$. on Net-
working, vol. 7, no. 4, pp. 4 5 8 4 7 2 , August, 1999.
[20] K. Ramakrishnan and S. Floyd, “RFC 2481: A Proposal to Add Explicit Congestion Notification (ECN) t o IP,” Jun. 1999. [21] M. Allman, “A Web Server’s View of the Transport Layer,”
ACM Comput. Commun. Rev., vol. 30, no. 5, pp. 10-20, Oct.
2000.
1221 M. Mathis, J. Mahdavi, S. Floyd, and A. Romanow, “ R F C 2018: T C P Selective Acknowledgement Options,” Oct. 1996. 1231 G. Bianchi, A. Capone, and C . Petrioli, “Throughput Analysis
of End-twEnd Measurement-Based Admission Control in IP,”
Fmc. IEEE InJmom, vol. 3 , pp. 1461-1470, March 2000.
[24] R. Goyal, R. Jain, S. Kalyanaraman, S. Fahmy, B. Vandalore, and X. Cai, “Selective Acknowledgements and UBR+ Drop Policies t o Improve T C P j U B R Performance over Terrestrial and Satellite Networks,” ATM Forum/97-0423, April 1997. [25] V. Paxson, “End-to-end Internet Packet Dynamics,” Proceed-
ings of SIGCOMM’97, pp. 139-152, 1997.
[ZG] S . McCanne and S. Floyd, “Ns (network simulator),” [online]. Av&able WWW: http://www-nrg.ee.lbI.gov/ns.