Wavelet based multipurpose color image watermarking by using dual watermarks with Human Vision System models
全文
(2) TSAI. and LIN:. WAVELET. BASED. MULTIPURPOSE. COLOR. IMAGE. WATERMARKING. BY USING. DUAL. WATERMARKS. 1427. 2. Related Works 2.1 Visible Watermarking Visible watermarking techniques are used to protect copyright of digital multimedia (audio, image or video) that have to be delivered for certain purpose, such as digital multimedia used in exhibition, digital library, advertisement or distant learning web, while illegal duplicate is forbidden. From the literature survey, the visible watermarking has captured significant attention [3] since there are not only different visible watermarking approaches either in spatial or transform domain but also varrrrousvisible watermark removal schemes. Braudaway et al. [4] proposed one of the early approaches for visible watermarking by formulating the nonlinear equation to accomplish the luminance alteration in spatial domain. Meng and Chang [5] applied the stochastic approximation for Braudaway's method in the discrete cosine transform (DCT) domain by adding visible watermarks in video sequences. Mohanty et al. [6] proposed a watermarking technique called dual watermarking by combining of a visible watermark and an invisible watermark in the spatial domain. The visible watermark adopted to establish the owner's right to the image and invisible watermark to check the intentional and unintentional tampering of the image. Chen [7] has proposed a visible watermarking mechanism to embed a gray level watermark into the host image based on the statistic approach by the standard deviation of blocks. Hu and Kwong [8], [9] implemented an adaptive visible watermarking in the wavelet domain by using the truncated Gaussian function to approximate the effect of luminance masking for the image fusion. Based on image features, they first classify the host and watermark image pixels into different perceptual classes. Then, they use the classification information to guide pixel-wise watermark embedding. In high-pass subbands, they focus on image features, while in the low-pass subband, they use truncated Gaussian function to approximate the effect of luminance masking. Yong et al. [10] also proposed a translucent digital watermark in the DWT domain and use error-correct code to improve the ability to anti-attack. Each of above schemes wasn't devoted to better feature-based classification and the use of sophisticated visual masking models. Recently, Huang and Tang [3] presented a contrast sensitive visible watermarking scheme with the assistance of HVS. They first compute the CSF mask of the discrete wavelet transform domain. They later use square function to determine the mask weights for each subband. At last, they adjust the scaling and embedding factors based on the block classification with the texture sensitivity of the HVS for watermark embedding. However, their scheme doesn't consider the following issues: 1. The basis function of the wavelet transform plays an. important role during the application of CSF for the HVS in the wavelet transform domain. 2. The embedding factors emphasize more weights in the low frequency domain instead of the medium-to-high frequency domain. 3. The interrelationship of block classification and the characteristics of the embedding location. For the first issues, the direct application of CSF for the HVS in the wavelet transform domain needs to be further studied [11]-[13] while the basis function of the wavelet transform is a critical factor to affect the visibility of the noise in the DWT domain. For the second issue, the watermark embedding in the low frequency components results high degradation of the image fidelity. In addition, the high frequency components of the watermarked image easily suffer common image signal processing attacks with low robustness. For the third issue, the plane, edge and texture block classification in [3] is a genuine approach should the local and global characteristics of wavelet coefficients be further considered. 2.2. Image Authentication and Temper Detection. Semi-fragile watermarking schemes have been proposed to verify the integrity of digital contents and tolerate some degree of mild modifications such as JPEG compression and channel AWGN. Interested readers could refer [14], [15] for latest development in this topic. Regarding the watermark embedding approach, the fragile (semi-fragile) watermarks can be embedded in the spatial domain or the transformed domain while the schemes embedding watermarks in the transformed domain offer a higher degree of robustness [2]. Recently, many semi-fragile methods are based on wavelet transform domain since it can resist a certain degree of attacks and have the spatial and frequency localization of digital data by the nature of multiresolution discrete wavelet decomposition. Kundur and Hatzinakos [16] proposed one of the first approaches to semi-fragile watermarking called telltale tamper proofing. They embed a watermark in the discrete wavelet domain of the image by quantizing the corresponding coefficients. They also use a statistics-based tamper assessment function as measurement for tamper proofing and authentication. H.P. Alexandre et al. [17] proposed a novel technique for content authentication of digital images by quantizing wavelet packet coefficients and adopting characteristics of the human visual system to maximize the embedding weights for improving good imperceptibility of watermarked image. Hua Yuan and Xiao-Ping Zhang [18] proposed a semi-fragile watermarking method based on image modeling using the Gaussian mixture model (GMM) in the wavelet domain. They modify selected wavelet coefficients according to the GMM parameters obtained through an EM algorithm. Ding et al. [19] proposed a wavelet-based chaotic semi-fragile watermarking scheme based on chaotic map and odd-even quantization. Their scheme can detect and.
(3) IEICE. TRANS.. FUNDAMENTALS,. VOL.E91-A,. NO.6. JUNE. 2008. in. cy-. 1428. localize malicious attacks with high peak signal-to-noise ratio (PSNR), while allowing more JPEG compression and channel additive white Gaussian noise (AWGN) tolerance. Since [19] is superior in resisting JPEG and AWGN attacks among other semi-fragile approaches, we further modify the scheme and integrate it into the proposed dual watermark approach which will be explained in the next section. 3.. The Proposed Approach. The most important requirements in the visible watermarking scheme are the robustness and translucence, but unfortunately these are in confliction with each other. If we increase the energy of watermark to improve its robustness, the problem we get is perceptual translucence decreasing with less image fidelity and vice versa. Therefore, we have to decrease the energy of the watermark to get good perceptual translucence and the embedded watermark will still be robust to intentional or unintentional signal processing attacks. HVS (Human Visual System) is the key factor we have found in providing the good translucence of the watermarked image and a better robustness [3]. A lot of works have been devoted to understanding HVS and offering mathematical models of how humans see the world [12], [20]. Psychovisual studies have shown that human vision has different sensitivity from various spatial frequencies (frequency subbands). Common HVS models are com-. Fig. 1. posed of image dependent or independent Just Noticeable Difference (JND) thresholds, so the HVS by using the contrast sensitive function (CSF) and noise visibility function. Fig.2. Luminance. sensitivity. βλ,θin different. curve. DWT. level. the. spatial. of CSF.. and. orientation.. (NVF) is integrated in this study and will be explained in brief as following. where. 3.1. CSF (Contrast Sensitive Function). cles/degree. For watermarked images, there has been a need for good metrics for image quality that incorporates properties of the HVS. The visibility thresholds of visual signals are studied by psychovisual measurements to determine the thresholds. These measurements were performed on sinusoidal gratings with various spatial frequencies and orientations by given viewing conditions. The purpose of such study was to determine the contrast thresholds of gratings by the given frequency and orientation. Contrast as a measure of relative variation of luminance for periodic pattern such as a sinusoidal grating is given by the equation C=(Lmax-Lmin)/(Lmax+Lmin). f=•ãfx2+fy2. (1). where Lmaxand Lminare maximal and minimal luminance of a grating. Reciprocal values of contrast thresholds express the contrast sensitivity (CS), and Mannos and Sakrison [20] originally presented a model of the contrast sensitive function (CSF) for luminance (or grayscale) images is given as follows:. cies. in. (2). of visual the. Figure. the. the. cies. between. high. HVS. be. and [3].. used. to. are. which. the. spatial. to. the. characterizes. CSF. of. and. less this. a simple. luminormalized. curve,. to normalized. 0.125. frequen-. respectively).. a function. Therefore,. develop. frequency. directions,. as. sensitive. 0.025. fy. curve HVS. According. is most. frequencies. can. the. and. vertical. CSF. of. frequency.. that. (fx. and. sensitivity. spatial. angle. horizontal. 1 depicts. nance. we. spatial sensitive. see. to low. knowledge. image. can frequen-. from. independent. and CSF HVS. model. CSF in. the. the to. masking. discrete. method their. masks. use. is. one. wavelet. five-level DWT. CSF. are. to. led. wavelet. in. to. mask. with. studies. have. Fig.. 11-weight. the. CSF to. according. in [11].. transform.. CSF. the refers. well-designed. curve. presented. method. apply. masking. coefficients. Some. the. same. in the. way CSF. importance.. weight. the. CSF 2 into. per-. Huang DWT. and CSF. Figure. 3 illustrates. weights. shown. for. subband. Psychovisual. midal. the. transforms. 11-weight. each. [12]. domain.. weighting. importance [3]. mask the. of perceptual. ceptual Tang. [11], wavelet. which. general. H(f)=2.6*(0.0192+0.114*f)*e-(0.114*f)i.i. is. band-pass DWT. characteristic. decomposition,. shown [3].. the. HVS. that For is. the. HVS. a five-level most. sensitive. has. a. pyrato.
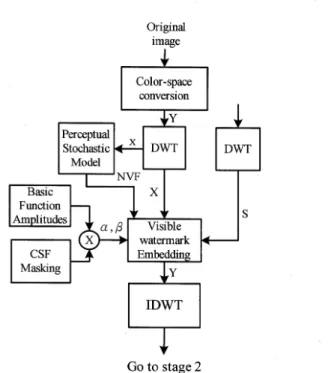
(4) TSAI. and LIN:. WAVELET. BASED. MULTIPURPOSE. COLOR. IMAGE. WATERMARKING. BY. USING. DUAL. WATERMARKS. 1429. Table 1. Basis function amplitudes for a five-level 9/7 DWT .. (4) where w(i,j)=γ[η(γ)]γ1/||γ(i,j)||2 -γ and variance of host image. ∫∞ 0 e-uut-1 du(gamma function) Fig.3. A five-level. DWT. structure.. rλ(βλ)values. for. each. level. λ are. indicated at the center of each band.. is the. shape. mean. and. shape. parameter. the the. distortion. off. as. the. function CSF. in mid-frequency frequency. (3). in. masking.. subband. value [3]. is. The. regions drifts. applied adequate. is determined. on to. and. both. sensitivity. sides.. approximate. modulation. falls. The the. for. denotes. of. by:. subband. are. smallest. rate. the. shown for. decomposed in. Fig.. level. 2. modulation.. where In. and ƒÀƒÉs the. level. addition,. as. coefficient. shown. values 5 in. 3.2. in at level. Fig.. CSF. Fig.. 3.. 3 and. It is the. of the. perceptual. for 3. rƒÉ represents. apparent values. importance. that falls. off. rƒÉs have for. level. each. has. 3.3. 0.3≦. parameter. for. of. by. real. γ ≦1.. the. local. images,. the. In our. γ=0.65. scheme,. and. width. of. Detection Thresholds for DTW Coefficients. the. In order to further improve the HVS model for better image quality, the knowledge of detection thresholds for DWT coefficients should be also studied. A.B. Watson, et al. [13] proposed a mathematical model for DWT noise detection thresholds which is a function of level, orientation, and display visual resolution. The model is given by. the ,θ=loga+k(logfλ-loggθf0)2. weight the. range. most. γ. is 1.. logYλ wavelet. shape. is determined. For. Г(t)=. r(i,j)=x(i,j)-x(i,j)/σx.. each. (3) where ƒÉ. is in the. estimated. window. r (i,j). variance.. global. Г(3/γ)/Г(1/γ), and. and. local. the. square effect. rate ƒÀƒÉ. parameter the. η(γ)=√. σ2x is. highest. 1, 2, 4 and. 3.. NVF (Noise Visibility Function). where. a. is. putation of a NVF (Noise Visibility Function) that characterizes the local image properties and identifies texture and edge regions. Accordingly, when the local variance is small, the image is flat, and a large enough variance indicates the presence of edges or highly texture areas. Because human eyes are sensitive to changes in flat than edges regions of the image, ones can increase the energy of watermark in the edges and high textured areas of the image, and reducing it in smooth regions in similar peak-signal noise rate (PSNR). This allows us to determine the optimal watermark locations and strength for the watermark embedding stage. Therefore, this concept from NVF can be used to develop a simple image dependent HVS model. They developed three such NVF Functions and we adopt the NVF Function with Stationary GG (Generalized Gaussian) Model in this study. The formula is as following:. minimum. quency. gƒÆf0, fƒÉ is. level ƒÉ,. and. gƒÆ shifts. function. of. orientation.. amplitudes. for. dicating. Many schemes embedded the watermark as random noise in the whole host image with the same strength regardless of the local properties of the host image, so the visible artifacts are easy taken placed at flat regions. S. Voloshynovskiy et al. [11] presented a stochastic approach based on the com-. the. the. the. threshold spatial. the. occurs. frequency. minimum Table. a 5-level. basis. (5). DWT.. function. of. by 1. In. at. an. shows this. fre-. decomposition amount. the study,. amplitudes, ƒÉ. spatial. that. basis we. use. as DWT. is. a. function AƒÉ,ƒÆin-. level,. and. ƒÆ as orientation.. 3.4. The is. Visible. complete. design. summarized. Fig.. 4:. (1). The. By. as. host. main (2). Watermarking. using. (3). Modify the. filter. the. following. Yi ,j=α. from of. grayscale. be. watermarking. is converted. is not. the. flow. algorithm. chart. in the. [13],. is. color. same. coefficients. compute. Y component. watermark the. proportionally DWT. Algorithm. shown. space. in. do-. to YCrCb.. coefficients. and. visible. image. Bi9/7. watermark it should. the. and. RGB. D wavelet image. of following. color. from. Embedding. as. image. the. one. scaled. If of. to the. of the. the from. host. the. 5-level. 2-. host the. width. host. host image. color of. image,. image. by. using. equation. λ,θ×Xi,j+(1-NVFi,j)×Si,j×. βλ,θ. (6). Note: (i,j) indicates the spatial location. X and S are the decomposed wavelet coefficients of the host image.
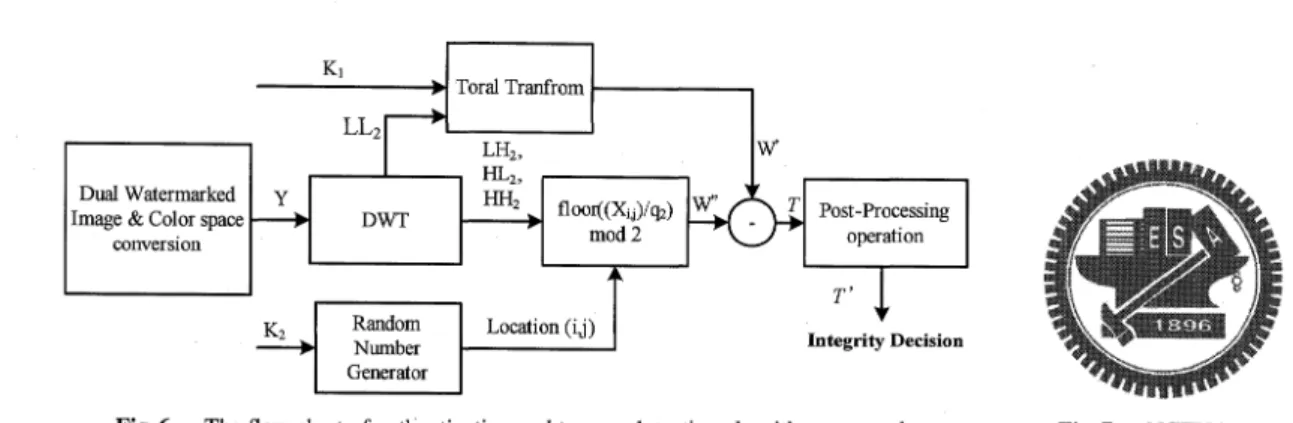
(5) IEICE. TRANS.. FUNDAMENTALS,. VOL.E91-A,. NO.6. JUNE. 2008. 1430. Fig. 5 Fig. 4. The flow chart. and. the. (4). and. of the proposed. watermark the. visible. image.. relationship. watermarking. NVF. is. defined. in. of ƒ¿ƒÉ, ƒÆand ƒÀƒÉ, ƒÆis. The flow chart. of the proposed. visible. watermarking. approach.. approach.. formula. defined. in. (3). where ƒ¿ƒÉ, ƒÆ=1-ƒÀƒÉ, ƒÆ. (4). Inverse age. transform. to obtain. the. DWT. coefficients. a watermarked. image. of (Y. the. host. W(i,j)=(x'+y'). im-. (4). We. use. K2. as. random. pseudo-random 3.5. Semi-Fragile. Watermark. Generation. and. Embedding. r,. Algorithm. is. difficult. that. can. to. develop. avoid. pecially. any. while. verify. In. the. modified. the. expensive. detect. the. visible. into. the. the. host. kind. of. labors, image. is. tampering. watermarked. images,. (semi-fragile. watermark). proposed. watermarking. algorithm. human. of such. authentication. [19]. a dual. watermarking. content. to of. image. from as. by. texture. order. integrity. algorithm image. attack. the. complicated.. a visible. visible. scheme. for. semi-fragile. as following is. (1). shown. and. Select. q1 the. termarked. In order. Y. K1. obtain 1•…j•…c.. and. of it, to. get we. as the. are. the. (Luminance). r•~. high refer. automorphisms and. q2. image. number),. chart. K1 and. and. coefficients (3). flow. embedding of. (8). define. not. (9),. (10),. and. (6).. is. the. ar-. procedures. are. the. visible. X. is. (13). performs. (i,j). decomposed. as controlling binary. K2. the. private. compute. the. security. size. chaotic. y(i,j)=f(x(i,j),W,q2). 2-level. map.. Note: •u•E•vdenotes. visible 2-D. wa-. wavelet. (pseudo system. Map. random called. toral. Qnum=•uLL2/q1•v. Using W (i,j)•¸{0,1},. Eqs.. (7),. (8),. 1•…i•…r,. we. the. function on. in f. wavelet. forStep. X (i,j). watermark indicates. in. into W.. the coefficients. q2. spatial of. image.. (9). of the. of LL2.. chaotic. parameter. watermark. from. watermark. [22]'s. keys. parameter.. component. c is the. to. are. visible waquantiza-. function. the. binary. watermarking. quantization. into the odd-even. quantization the. parameter. the. as. 1•…i•…. embedding. HH2}.. quantization. (12),. watermarked. 2, 3},. HL2,. is embedded using simple. according. quantization. two-dimensional. watermark. {LH2,. odd-even. formula region. location.. complete. semi-fragile. The. odd-even. the. to. (11),. create (i,j)•¸{1,. determine. watermark image by. We. to. 5.. parameters:. scheme. (2). the. in Fig.. Select. watermark. The binary termarked. mula. we. seed location. corresponding. tion.. chitecture. The. to. es-. watermarked. our. array. 1•…j•…c. location (5). It. mod 2. component).. floor. function..
(6) TSAI and LIN: WAVELET BASED MULTIPURPOSE. COLOR IMAGE WATERMARKING. BY USING DUAL WATERMARKS 1431. Fig. 6. The flow chart. xr=sgn(x(i,j))(•bx(i,j)•b. (6). Perform. to. FORj=1. wavelet. coefficients. as. location. 2:. W(i,j),. q2). CASE. 3: HH2(i,j)=f(HH2(i,j),. LH2(i,j)=f(LH2(i,j),. Inverse. transform The. the. W(i,j),. DWT. with. is converted. q2). coefficients. Y component. to. of. visible. in the. the. and. color. Y. com-. semi-fragile. space. domain. from. RGB.. Semi-Fragile. Watermark. Detection. 6. Authentication. and. Tamper. Algorithm. shows. the. which. is. flow. chart. similar. to. The. tamper. embedding.. of. the. watermark. part. of. detection. semi-fragile. detection. water-. procedure. as. fol-. lows: (1). Select. parameters:. scheme.. (2). q1. value. of. and. extraction. The. obtained. the. and. K1,. color. Select. K1. and. are. the. q2. K2,. q1. and. matrix. NCTU. indicates. logo.. the pixels. that were. (15). K2. are. the. private. quantization q2. are. keys. of the. parameter.. the. same. in. (7) Since the algorithm is designed to be semi-fragile watermarking scheme which would want to be robust to mild modifications in all cases, it is inevitable that we can not detect all malicious attack in pixel-wise. However, for practical cases such as removal visible watermark using neighbor pixels and image cropping which crops objects from a source and pastes them onto a target, the malicious attacks always be applied in a certain region in the watermarked image. That is to say, we assume tamper pixels are always continues. Therefore, for a certain tamper detection matrix element T(i,j), if the number of tampered neighboring element for T(i,j) is greater than a given threshold, we regard T(i, j) as a tampered one. The summary of such post-processing operation of tamper detection matrix is shown as following formula (16):. The. embedding. processes. visible. space the. 2-level. Fig. 7. tamper detection tampered.. watermarked. domain. from. image RGB. is converted. in. to YCrCb. Note:. (3). .. follows. (i, j). CASE. scheme,. approach. T=│W'-W"|. q2). Figure. algorithm. r. W(i,j),. YCrCB. detection. (13). 1: HL2(i,j)=f(HL2(i,j),. watermark. mark. 2). CASE. ponent.. 3.6. on. and tamper. to c. SWITCH. (7). mod. quantization. FORi=1. of authentication. Y. 2-D. (Luminance) wavelet. component. coefficients. and. of it,. compute. r•~c. is the. L as. width. of. window, ƒÀ. as threshold.. the size. of. (8). According. to. marked. the. image,. DWT. the. decomposition. size. of. of. tamper. the. detection. water-. matrix. is. LL2. r•~c, (4). Use. K1. and. random and (5). location. According the. K2. arrays;. to W'. create. (i,j)∈{1,2,3}, to the. quantized. two-dimensional. (i,j)∈{0,1},. 1≦i≦r,. location. (i,j),. coefficient,. pseudo-. 1≦i≦r,. we. defined. as. Thus. 1≦j≦c. 1≦j≦c.. find. the. sub-band. u (i,j).. The. which. and. one. ing. 4•~4. we. rescale. size. of. may. be. obtained. by. the. following. about. element. in. block the the. in. 1/16 the the. tamper. of. matrix. watermarked. indicates. watermarking. detection. watermarked. the. a correspondimage.. matrix. image. image.. and. Finally,. to have obtain. the the. same. tamper. extract detection. watermark. is. image.. formula. (14): W"(i,j)=(•u(u(i,j)/q2)•v). (6). Having the. obtained. tamper. W",. then. was. not. two. mod. watermarks. detection T=0. tampered.. matrix. It means. the. Otherwise,. 2. W' as visible. (14). and. formula. W", (15),. watermarked the •e1•f. element. we If. 4.. define. The. W'=. dual. Experiments. proposed. image. tested. by. USC. image. Discussion. multipurpose. watermarks. in. the. and. using. has the. database. watermarking been. commonly [23].. implemented available Because. the. algorithm and color evaluation. using. intensively images. from. standards.
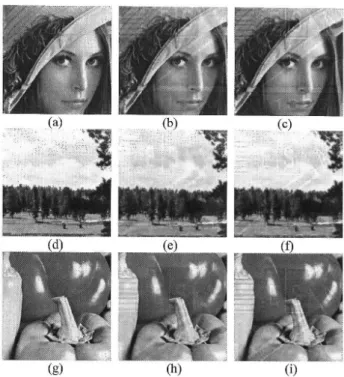
(7) IEICE TRANS. FUNDAMENTALS,. VOL.E91-A,. NO.6 JUNE 2008. 1432. Table. 2. PSNR. summary. of watermarked. color images.. Fig. 9 The visual comparison of close-ups for images from Fig. 8. (a), (d), (e) are close-ups of the original images. (b), (e), (h) are close-ups of the watermarked images by the method of [3]. (c), (f), (i) are close-ups of the watermarked images by the proposed algorithm.. 4.1. Fig. 8 Original images of (a) Lena (d) Lake (g) Peppers. (b), (e), (h) are watermarked images by the method of [3]. (c), (f), (i) are watermarked images by the proposed algorithm.. for. visible. pare. watermarking. our. the. algorithm. fair. ering. comparison. HVS,. has. [11] pared. AiS. Watermark. the. results. [3],. used. we. T1=1. in. choose [3]. during One. for. formance Table inal. host. by. [3]. proposed gorized. blocks. [24],. the. the. to match. the. com-. and. the. Huang. value. each. from we. approach. of. from. methods. In. describe. the. T2=350. of. 7 NCTU. 512•~512. logo. logo. and of. two. subband, PSNR. purpose. and. 8(c),. approach. as following.. (e), (f), The. (h) (i). so values. embedded. the. 8 shows. per-. analysis. the. in orig-. respec-. watermarked. watermarked. performance. The. is tabulated. and •gPeppers•h. are are. Fig.. is logo).. images. of •gLena,•h •gLake•h 8(b),. image. (school. experimental. comparison. Figs.. didn't. watermark. images. and. the. comparison.. in Fig.. Figures. images.. here.. technique. Protector proposed. consid-. addressed. than. the. com-. To make. watermarking. colors. classify and. the. of 2 for. tively.. they. to. grayscale. illustration. with. would. ones.. watermark. Pictures. [3]. we. is highly. visible. 512•~512. method. thresholds. [3]. performance. by. of. absent, proposed. visible. of. based. better. performance Tang's. CSF. shown. and. other. simulation. the. are. previously. with. the. Since [3]. system with. images. images can. by be. the. cate-. Visual Quality. From Figs. 8(b) (c), (e) (f) and (h) (i) image pairs, the proposed method has the closest luminance and chrominance maintenance compared with the original ones which are shown clearly from the photos even the difference is sometimes identified subjectively. The watermarked images by using [3] have more bright effect in the unmarked areas. On the other hand, translucence effect is one of requirements for an effective visible watermarking algorithm. The results from our proposed method have better translucence effect than the method of [3] to make photos look more natural since the watermarked images by using [3] affect the details of the host (original) image more, especially in Figs. 8(b), (e), (h). To further compare the details from the watermarked images, Fig. 9 demonstrates some of close-ups for comparison. Figures 9(a), (d), (g) are the close-ups from original images in Fig. 8. Figures 9(b), (e), (h) are the close-ups from the watermarked images by using [3]'s method. Figures 9(c), (f), (i) are the close-ups from the watermarked images by using the proposed technique. It is very clear that the watermark's edges and thin lines are blurred in those images by using the method of [3]. In addition, the watermark patterns in our proposed method still have sharp edge and the logo watermark is evidently embedded. For the text pattern, the text of character A in our results is with sharper edge than the ones in Figs. 9(b), (h). Besides, the outlines in our results are clearer than those from method of [3]..
(8) TSAI and LIN: WAVELET BASED MULTIPURPOSE. COLOR IMAGE WATERMARKING. BY USING DUAL WATERMARKS 1433. Table JPEG. 3 PSNR summary 2000 compression.. 4.2. PSNR. Since. (Peak. we. data. need. in [3] (peak. many. common. ues. to. for. do. fidelity.. larity. with. host. and after. below. for. the PSNRs. The. also. have. for val-. listed. truly. for. repre-. watermark. correlation. do. images.. 30dB. don't. visible. positive. the with. PSNR. are. values. quality. with. generally. images,. approach. PSNR. have. Higher. the. values. proposed. visual. values. are. colour. Even. before. comparison images. ratio). the. subjective. the. image. complete. 512•~512. purpose.. the. ages,. the. watermarked. used. comparison. sent. make the. images. Ratios). signal-to-noise. comparison. color. Signal-to-Noise. where. PSNR. of watermarked. imwith. better. the. image. definition. of. simi-. PSNR. is. as. following: PNSR(dB)=10log10(2552/MSE) where. MSE. image. and. of. color. is the. make. it is better image. then. sults. from. Table. the by. of. our. proposed. high. image. PSNR of. method. JPEG. The. robustness. should. be. of. The. PSNR. sion. are. labeled •gafter.•h. proposed. [25]. the re-. scheme. method. the. only. in. PSNR. This. could. achieve. values less. than. means. that. as. but. [3].. is better. 0.2-0.3dB. images.. visible. good. also. in Table. The. image. and. the. those. PSNR. as. with. ex-. image find. The. compared. and the. the. is 100:3. means. after(wn) between. image.. both. PSNR. watermarked column the image.. are. methods. those. compressed. values. tool. compres-. ratio. for. watermarked. PSNR. 2000. compressed. values. the. image.. that. and. compres-. compression. jpeg. column. between. are. the. technique. 2000. compression. PSNR. pure •gafter•h. original values. after. image of. JPEG. as the. 3. The. columns. watermark. For. and. uncompressed. compared. can. addition,. is adopted. before. are. watermarked. make. watermarks.. comparison.. from. two. to. tabulated. method. watermarking. for. values. are. In. only. of the. tested. the. 3, we. the. cover. available.. watermarking. our. are. 7. The. than. [3].. is not. Fig.. [3],. same. Compression. tabulated. between. our. design. invisible. software. from. from. the. [3]. from. of visible. 2000. in. values. watermark. of. method for. images. images. quality. the. used. that. multipurpose. 4.3. ble. watermarked Y component. comparison.. fidelity. visible. function. values. the the. watermark. watermarked. those. There. watermark. 2 disclose. higher. those dual. sion,. of for. watermark. performance. denotes. tra. error pixel. with. same. a logo. for. achieve. than. per. comparison the. the. embed. effort. of. a fair. However,. This. square image. to embed. best. can. mean. original. Fig. 10 The visual quality comparison of close-ups of watermarked image after jpeg 2000 compression ratio of 100:3. (a), (d), (e) are close-ups of the original images. (b), (e), (h) are close-ups of the watermarked images by the method of [3]. (c), (f), (i) are close-ups of the watermarked images by the proposed algorithm.. image.. To. We. the. (17). almost. means. compressed From the. Tasame. for both methods while the compressed watermarked images are compared with the watermarked images (after(wn) column). However, the PSNR values are higher while the compressed watermarked images are compared with the original images by the proposed approach than by the method of [3] (after column). Therefore, this statistic indicates that the image quality of watermarked image before and after compressed is higher by the proposed approach than the method of [3]. To further investigate the effect of compression, the visual difference can be illustrated by the close-up comparison. Figure 10 shows the close-ups of original images. Figures 10(b), (e), (h) are the close-ups of watermarked images by the method of [3]. Figures 10(c), (f), (i) are the close-ups of watermarked images by our proposed method. By comparing Figs. 10(b), (c), (e), (f), (h), (i), the compressed images maintain the details of the logo pattern but the characters E, S, A of watermarked images by our proposed method are more apparent than those of watermarked images by the method of [3]. This observation is consistent with the claim of our discussion in Sect. 2 that the embedding factors in [3] emphasize more weights in the low frequency domain instead of the medium-to-high frequency domain while the high frequency components of the watermarked image easily suffer common image signal processing attacks like compression. Therefore, we can conclude that our proposed method is more robust than Huang and Tang's method by JPEG 2000 compression attack from above observation where the visibility of watermark is surely higher by the proposed approach..
(9) IEICE TRANS. FUNDAMENTALS,. VOL.E91-A,. NO.6 JUNE 2008. 1434. Table 4 PSNR Median Filter.. summary. of watermarked. color. images. before. and after. Table. 5. PSNR. Gaussian. Table 6 PSNR Average Filter.. median the ups. of. ups. of. the. method. 7•~7. 11. tering the. The. visual. quality. of watermarked Huang. and. comparison. image. Tang's. (a). method. of close-ups. original. (c). image. of 7•~7. (b). watermarked. median. watermarked. image. by. fil-. the proposed. al-. By. robustness. and. StirMark. Since ilar as. the. the. logo. and. blurred the. to the. for. the. same. as. values. both. before. pression. are almost. images. while. with. the. the. method. in. are. of. indicates. that. fore. and. after. than. the. method. the. by. the the. further. by. are. PSNR. val-. meaning 2000. is com-. watermarked. are. investigate. than. by. statistic. image. proposed. are. compared. this. watermarked the. im-. values. approach. Therefore, of. attack. filtering. PSNR. images. proposed. higher To. JPEG. 4.5. sim-. that the PSNR values while the filtered wa-. with. quality is. [3].. can find methods. column).. image. filtering. their. of. hard. to. filtering shown. are in. also. Tables. which. indicate. visual like. from. characters. effect. (e),. outperforms. higher. by. [26]. like. preformed. our and. 6 are. and. (i),. S,. A,. consistent. or. 11(c). by. the. the. the but. median visibility. approach. and. av-. experimental with. the. watermarking PSNR. (i). There-. filtering the. the. (f),. 11(b).. proposed. Gaussian. visible higher. E,. [3]. of. It is apparent. where. the. (h),. in Fig. Fig.. the. proposed. 11(c),. (h). of. observation. the. (f),. existed in. closeby. close-ups. Figs.. (e),. recognized. 5 and. are by. but. the. above. is surely. (i). (c),. blurry 11(b),. technique from. attacks. 11(b),. evidently. be. are. image. image. Figs.. (i.e.. (h). by close-. values. reabove scheme. than. other. [3].. ICA (Independent Component covery Attack. Analysis) Image Re-. comparison.. of. and. than. are. attack. are. a stronger the. Figs.. (e),. (f),. watermarked. became. illustrated (g). watermarked. 11(c),. is still. proposed. watermark. schemes. here. this. median. section. the. for. columns. watermarked. (after. of. for. However,. images [3]. 8,. the. tested. filtering. Fig.. two. compared. filtered. original. here. here. after. the. column). the. in. are. also. median. labeled •gafter•h. mentioned. (after(wn). higher. and. There. is. adopted. applied. From Table 4, we the same for both. termarked ages. 4.. attack. 5•~5. shown is. methods. as. and. filtering. in Table. ues. is. 3•~3. illustration. PSNR. tabulated. software of. median. filtering. of. be (d),. 11(b),. of. Figures. 1896). can 11(a),. Figures filtering. [3].. attack. better. difference Figures. pattern. is. fore,. visual. contour. of. findings. Median. [26]. results. 7•~7. The. of. and after. images. characters. sults. The. before. comparing. sharper. has. color images. filtering. filtered. erage. Filtering. of watermarked. the. of. Other. Median. summary. images.. median. gorithm.. 4.4. and after. median. method.. of. before. original 7•~7. filtering. images. color images. comparison.. median. have. Fig.. of watermarked. filtering,. close-up. that. summary. Filter.. be-. approach the. effect. of. Regarding the removal technique, the image recovery method [27] can remove visible watermarking patterns consisting of thin lines and a few human interventions of imageinpainting approach of [28] can deal with patterns of thick lines. However, the iterative process of image-inpainting is costly and time-consuming. The image inpainting attack for the proposed visible watermarking is performed for Lena image only and Fig. 12 shows the watermarked image in Fig. 12(a), the mask used during the image inpainting attack in Fig. 12(b) and the recovered image in Fig. 12(c). From Fig. 12, we have found that the image inpainting based watermark removal approach could not remove the watermark completely since the watermark outline are still existing and the detailed image content can not be fully reconstructed..
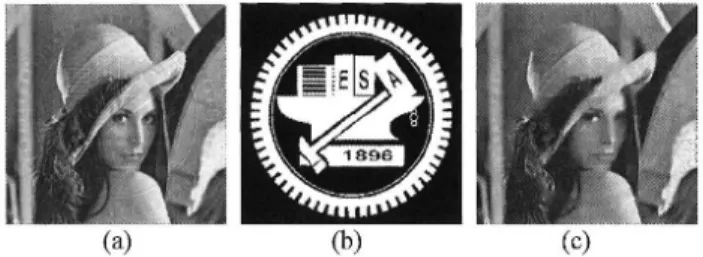
(10) TSAI and LIN: WAVELET BASED MULTIPURPOSE. COLOR IMAGE WATERMARKING. BY USING DUAL WATERMARKS 1435. (a) Fig. 12. Recovering. (b) the watermarked. (c) images by image inpainting. ap-. proach (a) is the watermarked images with NCTU logo by the proposed approach. (b) is the mask used during the watermark removal (c) is the recovered image after the image inpainting attack.. Therefore, a better image recovery attack is needed for further comparison. Pei and Zeng [29] proposed another image recovery algorithm for removing visible watermarks which is simple, fast with less human intervention. The method mainly utilized independent component analysis (ICA) to separate host images from watermarked and reference images. The algorithm included three phases: watermarked area segmentation, reference image generation, and image recovery. In their experiments, five different visible watermarking methods [3]-[7] and three public domain images are tested. The experimental results showed that their algorithm can successfully removed the visible watermarks, and the algorithm itself is independent of both the adopted ICA approach and the visible watermarking method. Interested readers can refer [29] for detailed information. In this study, we have implemented the method of [29] and tested several public images used in [29] for comparison. By applying the method of [29] to our proposed visible watermarking approach, Fig. 13 illustrates the results of the watermark removal attack where the logo patterns slightly disappear but still exist and the contours are recognizable in Figs. 13(b), (d), (f). Besides, the watermark removal scheme in [29] can remove the watermark by the method in [3]-[7] but the proposed approach can resist such attack. We can conclude that the proposed visible scheme certainly outperforms the methods in [3]-[7]. The robustness of a visible watermarking scheme mainly depends on how difficult or impossible it is to remove the embedded visible watermark patterns without exhaustive and costly user interventions. Even the results in Figs. 12 and 13 show that the proposed visible watermarking approach can resist the watermark removal attacks, we fully understand subsequent signal processing operations like equalization, sharpening or background blurring could completely remove the watermark eventually. Even the visible watermark will be removed completely, our dual watermark can still disclose the information about where the attacks occur and the tamper detection simulations are performed next.. Fig. 13. Recovering the watermarked. tion. algorithm. Tamper Detection. CS2. erations.. In. q2=10, and. 15. fragile. our. marked. ble. image,. blue the. In the. we. neighboring. use In. Fig.. Fig.. 14(b) Peppers. of Figs.. and. 15(c),. 14(c) parts. where. of. these For. the. Fig.. AWGN. marked. with. quality. watermarked. 16. Lake. image: Lake. one image.. (QF). image object. 17. and. and. the same. visicom-. are inserted detection. into results. the. 14(b). tam-. and. Fig.. Figs.. operation. JPEG. setting.. (a boat) From. the. water-. watermarked. indicate. show. tampering. Fig.. different ƒÐ2 factor. sym-. remove. points Figs.. object. dual. (the. in. tam-. an. 15(b). correctly. of. and. and. the. of the to. peppers) From the. image. located. combination. modification, after. are. 14 semi-. copyright. of. objects. marked. and. 14(b),. with. part. three. watermarked. parts. A. pixels. and two image. the. Fig.. bottom. shoulder. 15(b),. pany logo of the watermarked. pered. right. op-. Figure. image,. In. Adobe. q1=30,. (visible. tampered. character. into. use. parameters. images. respectively.. of. we. processing. L=1, ƒÀ=3.. image.. watermark.. set. result. embedded),. inserted. Lena. Lena. we. the. image logo. is. images, of image. K2=1234,. demonstrate. company. tampered. experiments,. detection. bol (R)). up. implementation. watermarks. pering (a. make. for. K1=1234, Fig.. Lake. To evaluate the validity of the proposed image authentica-. and. Photoshop. different. 4.6. images from the proposed method. (a), (c), (e) are the watermarked images with NCTU logo. (b), (d), (f) are the recovered image of (a), (c), (e) respectively under image recovery attack.. is. 16(a). shows. inserted. 16(c),. mild. detection. compression. Figure 16(b). and. tamper. (d),. with shows. the into (e),. the. tampered the. we. watercan. see.
(11) IEICE TRANS. FUNDAMENTALS,. VOL.E91-A,. NO.6 JUNE 2008. 1436. (a). (b). (c). (a). (b). (c). (d). (e). (f). (g). (h). (i). Fig. 14 (a) Dual watermarked image of Lena. (b) Tampered dual watermarked image. (c) Tampering detection.. (a). (b). (c). Fig. 15 (a) Dual watermarked image of Peppers. (b) Tampered dual watermarked image. (c) Tampering detection. Fig. 18 Dual watermarked images of (a) Lena (d) Lake (g) Peppers respectively. (b), (e), (h) are tampered dual watermarked images with watermark removal attack. (c), (f), (i) are images after tampering detection.. For more serious attacks like watermark removal, we are also interested in the detection capability by the pro(a) (b). (c) Fig.. 16. Tamper. AWGN. with. image. (d) detection. for. different ƒÐ2.. of Lake. (a). the. (e). combined. tampering. Watermarked. (c) ƒÐ2=6(d) ƒÐ2=12. image. operations. of Lake. (b). and. tampered. (e) ƒÐ2=18.. posed approach. Figure 18 demonstrates the temper detection result. We can clearly see the tampered areas are labeled in Figs. 18(c), (f), (i) and reflected the evidence of tempering. After the intensive performance comparison, the results of different attacks, visual quality analyses and temper detection demonstrate that the proposed multipurpose color image watermarking by using dual watermarks with HVS method is more robust with better image quality. In summary, we are convinced that the proposed complete architecture is a superior scheme among the referred published techniques. 5.. (a). (b). (c). Fig. 17 Tamperdetectionfor the combinedtamperingoperationsand JPEGcompression.(a) QF=100 (b) QF=80 (c) QF=60.. the. detection. rectly (c), is. result. after we. located. quality. AWGN. can. see. the. correctly factor. (QF). of. tampered. with detection after settings.. Lake. different ƒÐ2. result JPEG. image From. of. tampered. compression. is located Figs.. cor-. 17(a), Lake. with. (b),. image different. Conclusion. A novel watermarking-based technique for copyright protection and authentication has been presented in this study. In copyright protection, we propose a new visible watermarking technique where the intensity of the watermark in different regions of the image depends on the underlying content of the image and human sensitivity to spatial frequencies. The collaboration of CSF and NVF for HVS models is leveraged with the noise reduction of the visibility thresholds for HVS in DWT domain. The perceptual weights is fine tuned for watermark embedding which results significant improvement over the watermarked images by CSF only based algorithms regarding the image quality, translucence and robustness of the watermarking. For authentication and verification of the integrity for the.
(12) TSAI. and LIN:. WAVELET. BASED. MULTIPURPOSE. COLOR. IMAGE. WATERMARKING. BY USING. DUAL. WATERMARKS. 1437. dual watermarked images, mark algorithm which can tack effectively yet tolerate compression and channel. we applied a semi-fragile waterdetect and localize malicious atmild modifications such as JPEG additive white Gaussian noise. [16]. [17]. D.. Kundur. tale. tamper. July and. Alexandre for. image,•h. H.. Yuan the. 2004. and. Int.. pp. 413-416, [19]. K.. [20]. J.L.. C.. no.4, [21]. [1]. the encoding. pp. 525-536,. Proc.. Intellectual. Property. Organization. (WIPO),. http://www.. [23]. wipo.int/ [2]. I.J.. Cox,. cess.,. J. Kilian,. J., F.T.. Leighton,. watermarking vol.6,. for. no.12,. B.B.. Huang. ing. scheme,•h. and. and. pp. 1673-1687, S.X.. IEEE. Dec.. Tang, •gA. IEEE. T. Shamoon, •gSecure. multimedia,•h. Image. Pro-. Braudaway,. K.A.. vol.13,. Conf.. SPIE,. and. visible. watermark-. pp. 60-66,. April-June. Mohanty,. K.R.. vol.2,. P.-M.. Chen, •gA. 913, Y. Hu. F.C.. Proc.. and. Y. Hu. image. watermark,•h. Deterrence. visible. ICIP,. for. vol.1, and. image,•h. Oct./Nov.. [28]. Techniques,. 5th. Int.. video. and. Lett.,. L. Yong,. L.Z.. Oct.. in 1998.. Kankanhalli, •gA. 7th. ACM. Int.. mechanism Signal. on. Int'l. pp. fidelity. Theory,. Baumgaertner,. and. digital. cri-. vol.20,. T. Pun, •gA. image. Information. Y.Z.. watermark-. Hiding,. Chen, •gJoint. watermarking,•h. [Online]:. pp. 211-236,. wavelet IEEE. Feb.. Image. and. Trans.. spatial. trans-. Consum.. Elec-. 2000.. Database. [Online]:http://sipi.usc.. adaptive. M.. Bertalmio,. V.. SIGGRAPH. 2000,. Y. Wu,. no.11,. L.R.. Signal. and. Iyer, for. Z.H.. and. Sept.. and. C.-H.. and. Huang. J.-L.. Multimed.,. S.C.. Pei. ible. watermarked. and. A.E.. wavelet. image,•h. vol.1,. no.4,. Processing. Nov.. pp. 25-28,. Workshop,. wa-. Chinese. J. of. 2004. and. compression,•h pp. 88-93,. evaluation. of. Proc.. 10th. IEEE. IEEE. CS. Press,. Tung. University. search. interests. sic, digital. in Taiwan include. watermarking. puting for electronic Eta Kappa Nu.. D.. Levicky. tal. image. and. P. Foris, •gHuman. watermarking,•h. visual. system. Radioengineering,. models. vol.13,. Watson,. of wavelet no.8,. G.Y.. Yang,. quantization. Ekici,. B.. no.4,. in. tronic C. Fei,. Imaging, D.. Forensics. and. B. Colkun,. of. semifragile. vol.13,. Kundur,. watermark-based. and. IEEE. Image. and. Nazi,. no.1,. pp. 209-216,. R.. Kwong, •gAnalysis. authentication Security,. U.. and. watermarking. vol.1,. Process.,. vol.6,. Akcay, •gCompar-. algorithms,•h. J. Elec-. 2004.. systems,•f no.1,. M.. pp. 43-55,. and IEEE. design. Trans. March. novel. image Trans.. pp. 543-550,. Dec.. Feb.. watermarking,•h. IEEE. 2004.. recovery. algorithm. Information. for. Forensics. visand. 2006.. and is currently. multimedia. system. and authentication,. commerce.. an associate. professor.. and applications, web services,. Dr. Tsai is a member. His re-. digital. foren-. enterprise. com-. of IEEE,. ACM,. and. pp. 38-43,. J. Villasenor, •gVisibility. Trans.. visible. pp. 16-30,. IEEE. inpainting,•h. 2000.. digi-. 1997.. Sankur,. evaluation. Solomon,. noise,•h. pp. 1164-1175,. ative. J.A.. Ballester, •gImage. Min-Jen Tsai received the B.S. degree in Electrical Engineering from National Taiwan University in 1987, the M.S. degree in Industrial Engineering and Operations Research from University of California at Berkeley in 1991, the Engineer and Ph.D. degrees in Electrical Engineering from University of California at Los Angeles in 1993 and 1996, respectively. From 1996 to 1997, he was a senior researcher at America Online Inc. In 1997, he joined the Institute of Information Management at the National Chiao. 2001.. digital. code,•h. C. Aug.. no.1,. Zeng, •gA. pp. 910-. Systems,. Bell, •gDesign. image. http://www.ece.uvic.ca/. Wu, •gAttacking. vol.6,. Y.C.. and. pp. 417-424,. watermarking. Xu, •gTranslucent. error-correct. pp. 1533-1539, and. http://www.watermarker.com [Online]:. Caselles,. visiblewatermark-. visible. Circuits. Protector:. http://www.petitcolas.net/fabien/software/Stir. a statistic. 2004.. [15]. StirMark,. Security,. 2002.. O.. a visual Inf.. dual. vol.2,. 1219-1220,. fusion-based. Symp.. wavelets. masks. Digital. no.20, image. 2003. vol.27,. perceptual. [14]. Funda-. Multimedia. using. Processing,. domain. vol.37,. Cheng,. based. Beegan,. A.B.. semiTrans.. 2005. of. Trans.. adaptive. compression,. 2003.. Computers,. [13]. and. Pictures. 2000. 1999.. Conf.. S. Kwong, •gAn Proc.. termark. [12]. ,. 1999.. USC-SIPI. Watermark. Trans.. watermarks. pp. 474-477,. M.S.. Proc.. watermarking. S. Kwong, •gWavelet. Press,. A.P.. IEEE. .. MarkBenchmark_4_0_129.zip. Mintzer, •gProtect-. a visible. Ramakrishnan,. visible. Electron.. IEEE. [11]. JPEG. [29]. Proc.. pp. 49-51,. algorithm,•h. [10]. March. N.. content. pp. 241-245,. 2000.. ing,•h [9]. with. Chang, •gEmbedding. technique. Conf.,. and. and Counterfeit. domain,•h. approach,•h. [8]. AiS. [26]. 1996.. S.-F.. watermarking. [7]. Security. pp. 126-132,. J. Meng. S.P.. images. Optical. the compressed [6]. vol.3. 2004.. effects. Workshop. digital no.1,. Proc. Processing,. mdadams/hasper/~. no.2,. Magerlein,. publicly-available. Proc.. [5]. SIPI-The. [25]. [27]. G.W. ing. USC. [24]. 1997.. contrast-sensitive. Multimed.,. spread. Trans.. 2006. [4]. vol.46,. Signal. edu/services/database/Database.html. spectrum. [3]. tron.,. Yu,. and. based. domain,•h. Wang, •gWavelet-based. pp. 787-790,. Sept.. K.Y. for. wavelet. detection,•h IEICE. Herrigel,. to Int.. Com-. 1974.. A.. 3rd. H.X.. tamper. Sakrison, •gThe. July. Germany,. Tsai,. and. and. watermarking. the. May. of images,•h. approach. formation. World. D.J.. S. Voloshynovskiy,. M.J.. Jiang,. no.3,. on. ing,•h. Canada,. with. and. stochastic. [22]. L.G.. watermark-. Electrical. fragile. in. Speech. QC,. vol.E88-A,. Dresden,. References. He,. tellno.7,. 2002.. model. Acoustics,. Mannos. terion. This work was supported by the National Science Council in Taiwan, Republic of China, under NSC95-2416-H009-027 and NSC96-2416-H009-015.. on. on. multiscale. mixture. watermarking. mentals,. Acknowledgments. pp. 879-884,. Montreal,. Ding,. fragile. for , vol.87,. digital. Conference. Zhang, •gA. Conf.. IEEE. Rabab, •gWavelet-based. Canadian. vol.1,. X.P.. Proc.. 1999.. IEEE. Gaussian. watermarking. authentication,•h. K.W.. Engineering,. on. Hatzinakos, •gDigital and. H.P.. puter [18]. D.. pp. 1167-1180,. ing. (AWGN). In addition, the experimental results demonstrate the proposed visible watermarking scheme has achieved high PSNR values with better visual fidelity and robustness to attacks than other schemes and the semi-fragile watermarking scheme has the capability to verify the integrity of the images.. and proofing. of secure Information. 2006.. Chih-Wen Lin has received B.S. degree in Industrial Education from National Taiwan Normal University in 2004, the M.S. degree in Institute of Information Management at the National Chiao Tung University in the year 2007. He currently serves in the Telecommunication Laboratory of Chunghwa Telecom Co. Ltd..
(13)
數據


相關文件
Ss produced the TV programme Strategy and Implementation: MOI Arrangement 2009-2010 Form 2.. T introduced five songs with the
In addition that the training quality is enhanced with the improvement of course materials, the practice program can be strengthened by hiring better instructors and adding
• Paul Debevec, Rendering Synthetic Objects into Real Scenes:. Bridging Traditional and Image-based Graphics with Global Illumination and High Dynamic
• Li-Yi Wei, Marc Levoy, Fast Texture Synthesis Using Tree-Structured Vector Quantization, SIGGRAPH 2000. Jacobs, Nuria Oliver, Brian Curless,
– Camera view plane is parallel to back of volume – Camera up is normal to volume bottom. – Volume bottom
– Any set of parallel lines on the plane define a vanishing point. – The union of all of these vanishing points is the
The stereo matching techniques developed in the computer vision community along with ima ge-based rendering (view interpolation) tech niques from graphics are both essential
According to analysis results, the system satisfaction have nearly 43% variance explained by system quality, information quality, training experience and
![Fig. 8 Original images of (a) Lena (d) Lake (g) Peppers. (b), (e), (h) are watermarked images by the method of [3]](https://thumb-ap.123doks.com/thumbv2/9libinfo/7997284.159810/7.871.78.420.123.648/original-images-lena-lake-peppers-watermarked-images-method.webp)