評估產業之雲端準備度 - 政大學術集成
全文
(2) 謝辭 論文的研究與撰寫,對我來說是學生時期的里程碑也是最後一個大關卡,當 初選擇就讀研究所也是希望能透過研究來擴展自己對於資管的認識,也讓自己在 論文研究的階段能更充實自己的能力。 回首兩年研究所時光,從一開始對於論文的撰寫徬徨、到進一步確定目標、 擬定流程,與最後的執行階段,每一個階段都遇到了許多困難與能力的不足,因 此在此要感謝指導教授張欣綠教授,張教授時常指點論文上的方向,也常常給予 我許多學習的建議,讓我能在研究上更加的順遂,進而完成了一開始認為難以完 成的目標。也因為張教授的指導,我過去兩年的研究所時光所學習到的也更加的 充實。真的很感謝張教授兩年來的指導,本研究如果少了張教授的指導是無法完 成的。 另外要感謝研究所同學的鼓勵與陪伴,論文撰寫的過程中,時常會有不確定 與迷惘的時候,此時有好同學的陪伴,一起討論目前的進度與所遇到的困難,時 時會有豁然開朗的感覺,也更加篤定自己研究的進行,論文的完成才能如期。 最後要感謝家人與其他朋友的支持,尤其是家人在我進行問卷研究時,透過 多方的介紹,得到了許多與現存使用雲端運算的公司的聯絡方式。家人也時常給. 立. 政 治 大. ‧. ‧ 國. 學. n. al. er. io. sit. y. Nat. 我鼓勵與關心我目前的論文進度,讓我的研究更加的順利。 兩年的時光一下就飛逝,現在回過頭來想,真的覺得一路上很充實也非常地 順利,真的要感謝許多人一路的幫忙,我相信經歷過研究的磨練以後,未來我也 可以對於自己的所學更加得心應手,進而回饋給社會。. Ch. engchi. I. i n U. v.
(3) 摘要 近年來雲端運算逐漸盛行且其已被許多企業採用,雲端運算所帶來的好處包 含提供更好的連結、企業不同廠的無間隙合作,進而提高生產效率。透過現存論 文的研究,我們發現企業導入雲端運算與使其和企業內企業流程成功結合為兩大 企業成功的因素。然而,要如何導入與對雲端運算加以控制卻很少在現存論文中 談及,更遑論企業在導入雲端前該做哪些準備等議題。本研究也透過文獻的探討 提出兩個研究面向(管理面與科技面),文獻探討也發現,此兩面向為企業選擇 導入公有雲或是私有雲的主因。再者,本研究提出兩個討論面向的同時,也與現 存的雲端服務供應商討論此兩面向,希望能讓兩面向更加符合現存雲端狀況。根 據這兩面向的基礎,本研究在此兩大面向下提出許多因素來探討企業導入雲端的 準備度。本研究也進一步透過問卷的方式訪問現存有採用或是導入雲端的企業, 問卷內容涵蓋上述提到的兩面向,進而透過所收集的資料之分析來探討真正影響 雲端導入成功與否的因素是否與研究所提出的假設符合。研究結果發現,虛擬化 與 IT 建設的有無與完善程度對於私有雲的導入成功與否有正向關係。而研究結 果也指出,公有雲與私有雲兩種型態的雲端也有相互的關係。. 立. 政 治 大. ‧. ‧ 國. 學. 關鍵詞:雲端運算、雲端準備度、公有雲、私有雲. n. er. io. sit. y. Nat. al. Ch. engchi. II. i n U. v.
(4) Abstract Cloud computing has been dedicated to providing several benefits, such as better connectivity and seemingly seamless cooperation between different plants, that improve firm performance. Previous research maintains that introducing cloud computing and combining it with companies’ processes are two of the prime factors that lead companies to success; however, the manner of implementing this technology and exerting control over it are rarely discussed, especially with regard to the preparation before a company’s official launch of cloud computing. A literature review enables us to propose two dimensions—technological and managerial concerns—of factors driving companies to introduce cloud computing through both private and public clouds. Moreover, after proposing the two dimensions, we examine them by conducting interviews with several companies in the hopes of making these dimensions more applicable and pragmatic in business. Because the purpose of this research is to prepare companies to implement cloud computing, we design a questionnaire based on the dimensions and undertake a survey with several companies that have implemented cloud computing to determine the underlying factors influencing the performance of cloud computing. The results of this research show. 立. 政 治 大. ‧. ‧ 國. 學. n. al. er. io. sit. y. Nat. that both of the virtualization and IT infrastructure readiness factors have positive impacts on private clouds, and the results also indicate a relationship between public and private clouds, which means companies that have adopted public clouds are more likely to succeed in adopting private clouds.. Ch. i n U. v. Keyword: Cloud computing, Cloud readiness, Private cloud, Public cloud. engchi. III.
(5) Contents Chapter One: Introduction..................................................................................................... 1 Chapter Two: Literature Review ........................................................................................... 3 2.1. Cloud computing .......................................................................................................... 3. 2.2. Readiness for Cloud Computing .................................................................................. 7. Chapter Three: Research Model...........................................................................................12 3.1. Technological Readiness ............................................................................................ 12. 3.2. Managerial Readiness ................................................................................................. 14. 政 治 大 Chapter Four: Research Methodology .................................................................................17 立 The adoption Public and Private Clouds .................................................................... 16. 4.1. Pilot Test..................................................................................................................... 17. 4.2. Data Collection ........................................................................................................... 18. 4.3. Measurements ............................................................................................................. 19. 4.4. Instrument Validation ................................................................................................. 20. ‧. ‧ 國. 學. 3.3. y. Nat. io. sit. Chapter Five: Analysis and Results ......................................................................................26 Mean Value Analysis ................................................................................................. 26. 5.2. Results ........................................................................................................................ 27. 5.3. Findings and Discussion ............................................................................................. 29. n. al. er. 5.1. Ch. engchi. i n U. v. Chapter six: Conclusion .........................................................................................................37 6.1. Summary .................................................................................................................... 37. 6.2. Contributions .............................................................................................................. 37. 6.3. Limitations and Future Research ................................................................................ 38. References ...............................................................................................................................39 Appendix A. Questionnaire (English Version) ....................................................................46 Appendix B. Questionnaire (Mandarin Version) ................................................................52 Appendix C. Participant List ................................................................................................57 IV.
(6) Table Contents Table 2-1 Features of Cloud Computing ....................................................................... 5 Table 4-1 Characteristics of the Study Sample ........................................................... 18 Table 4-2 Item Measures of Cloud Computing Readiness ......................................... 19 Table 4-3 The Initial Results of Factor Analysis ........................................................ 20 Table 4-4 Summary of Factor Analysis ...................................................................... 21 Table 4-5 Measurement of Constructs ........................................................................ 22 Table 4-6 Correlation Matrix ...................................................................................... 24. 治 政 Table 5-1 Mean Value Analysis of Public Cloud Adoption 大 ....................................... 26 立 Table 5-2 Mean Value Analysis of Private Cloud Adoption ...................................... 26 Table 4-7 Summary of K-count for Discriminant Validity ......................................... 25. ‧ 國. 學. Table 5-3 Summary of PLS Analysis.......................................................................... 28 Table 5-4 Mean Values of Cloud Familiarity of Different Groups ............................ 31. ‧. Table 5-5 Test of Normality ........................................................................................ 32. y. Nat. sit. Table 5-6 Results of Descriptive Statistics ................................................................. 33. n. al. er. io. Table 5-7 Scores for Public Clouds ............................................................................ 35. i n U. v. Table 5-8 Scores for Private Clouds ........................................................................... 36. Ch. engchi. V.
(7) Figure Contents Figure 3-1 Research Framework ................................................................................. 12 Figure 5-1 PLS Analysis (Calculated Using SmartPLS) ............................................ 27 Figure 5-2 Scatter Diagram for Public Clouds ........................................................... 36 Figure 5-3 Scatter Diagram for Private Clouds .......................................................... 36. 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. VI. i n U. v.
(8) 1. Chapter One: Introduction Due to the ever-growing use of services in business, cloud technology has reached an important critical point that affects corporate strategy and changes business models. Organizations that are aware of trends and manage themselves effectively using cloud technology will gain a competitive advantage (Goodburn and Hill, 2010). Therefore, cloud technology plays an important role for companies attending to a great amount of information and gaining profits. Cloud technology may facilitate the functionality of an IT infrastructure, IT platform or IT product and be applied as a set of services in a seamlessly scalable model. Due to this feature, companies may choose what cloud services they need and pay as they operate (Dargha, 2011). Generally speaking, the architecture of cloud technology is divided into three broad categories based on user access and ownership. The first category is public clouds, which include the management of a third party and are often characterized by the hosting of pay-per-use, virtualized servers by service providers. The second category is private clouds, a virtualized IT infrastructure that hosts services for employees and is managed by an organization’s IT staff. The last category is hybrid clouds, which have elements of the former two and enable an. 立. 政 治 大. ‧ 國. 學. ‧. enterprise to serve as its own cloud provider as well as a host for outside applications (Emerson, 2010). Considering the emphasis placed on the merits of cloud technology, a company may choose between implementing private or public clouds. Introducing public clouds provides a company more convenience by simply outsourcing cloud technology to a third party. In contrast, a company is able to take better control of its own data and services when using private clouds. The choice depends on the company’s readiness to implement cloud technology. Some existing cloud providers maintain that people and organization as well as processes and technology must be addressed in developing a cloud strategy and that all relevant factors must be considered over the course of the engagement in this strategy (IBM, 2009). The fact that cloud coverage within a company includes managerial and technological issues may be deduced from the providers’ suggestions. In addition, some researchers suggest that selecting the wrong IT services for the cloud may be operationally costly and can potentially harm a business strategy. Companies thus require a sufficiently specific yet applicable method to assess the cloud’s readiness when applying it. This. n. er. io. sit. y. Nat. al. Ch. engchi. i n U. v. method should also be capable of being applied in parallel with ongoing business activities (Loebbecke, Thomas, and Ullrich, 2012). Accordingly, it is essential for companies to equip themselves with a means of assessing their readiness for cloud technology. 1.
(9) The main purpose of this research is to develop a model for assessing companies’ readiness for implementing cloud technology. The study focuses on readiness for private clouds and public clouds and the difference between the two types of clouds. In addition, the model considers factors regarding both technological and managerial aspects. The research questions are as follows: (1) What are the readiness factors for public clouds? (2) What are the readiness factors for private clouds? (3) What readiness factors differentiate public from private clouds? (4) Are private clouds more adoptable for companies that have introduced public clouds?. 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. 2. i n U. v.
(10) 2. Chapter Two: Literature Review To better understand what readiness factors for different types of cloud computing are and how to measure them, the literature review focuses on two parts. The first part consists of the introduction of cloud computing and features of cloud computing. The second part reviews the literature relating to the readiness of cloud computing.. 2.1. Cloud computing. 2.1.1 Introduction of Cloud Computing Cloud computing has become a prominent battleground among major IT vendors because there is an increasingly pervasive trend where IT vendors make most of their products online – whether it be hardware, software or network infrastructure (Hunter, 2009). As a matter of fact, cloud implementation is now a business imperative. In addition to virtualized technology, cloud computing is the culmination of several years of technology innovations and on-demand access to a shared pool of virtual computing resources stemming from years of technological development (Goodburn and Hill, 2010).. 立. 政 治 大. ‧. ‧ 國. 學. n. al. er. io. sit. y. Nat. On the whole, cloud computing may be considered as having four layers of structure and three types of applications. In many cases, organizations will put one or more service structures and types of application into practice (IBM, 2010). According to Mell and Grance (2010), the common cloud service structures are as follows: (1) IaaS (Infrastructure as a Service) This structure consists of the use of the most fundamental computing structures, which is often rendered by cloud providers. The capability provided to the consumer is provision processing, storage, networks, and other fundamental computing resources, and the consumer is able to deploy and run arbitrary software. (2) PaaS (Platform as a Service) PaaS is based on IaaS. The capability provided by PaaS is to deploy onto the cloud infrastructure consumer-created or acquired applications created using programming languages and tools supported by the IaaS layer. (3) SaaS (Software as a Service) SaaS, the most accessible layer, provides users with the cloud providers’. Ch. engchi. i n U. v. applications running on a cloud infrastructure. The services offered by providers are accessible from various client devices via the Internet. Consumers do not manage or control the underlying cloud infrastructure, including the network, servers, operating systems, and storage. Among cloud applications, there are private clouds, public clouds and hybrid 3.
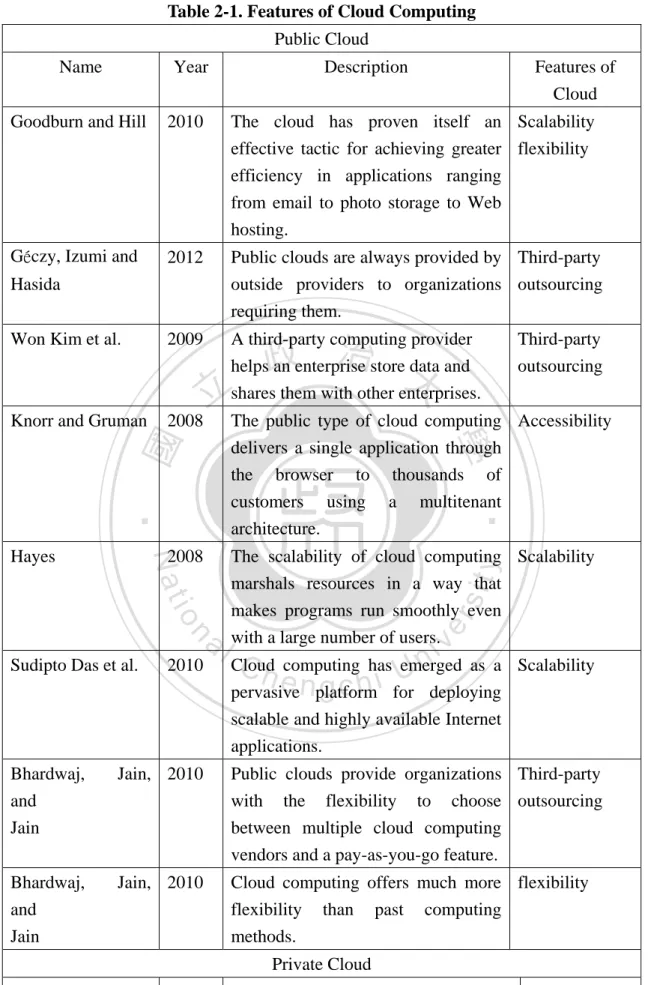
(11) clouds, each defined by the relationship between cloud providers and cloud users. The most common three types of application are as follows (Harris, 2011) (1) Private Cloud Private clouds are often owned and operated exclusively by one corporation. With all their infrastructure and structure built behind an organization’s firewall, these clouds provide services for the organization’s employees and sometimes users outside the scope of the organization. (2) Public cloud Public clouds often refer to computing and IT infrastructure that is owned by an organization but that provides computing and information services to external users or subscribers. (3) Hybrid cloud These clouds are a mixture of public clouds and private clouds. They may be useful for some well-established corporations that already have their own computing and IT infrastructure but require additional computing and IT services or vice-versa. However, this study focuses solely on the readiness for public and private clouds. We define companies that self-own the IaaS layer of cloud computing as private cloud users even if these companies outsource the rest of the three layers to other cloud providers.. 立. 政 治 大. ‧. ‧ 國. 學. 2.1.2 Features of Cloud Computing. y. Nat. sit. n. al. er. io. Considering the convenience and benefits brought by cloud computing, companies are leaning toward adopting it. However, to what extent may a company be considered a fully cloud-adopting one? The answer varies according to their initial goals and purposes (Reynolds and Bess, 2009). Generally speaking, the adoption of innovations consists of a sequence of stages in which an individual or decision-making unit gains initial knowledge about an innovation, forms an attitude toward the innovation, and makes a decision to adopt or reject it (Rogers, 2003). As the adoption sequence proceeds, it will be gradual as the organization obtains a better understanding about cloud computing and as cloud computing technologies become more mature, which result in more benefits gained from cloud computing (Simalango, Kang, and Oh, 2010). On the whole, companies must know the features of cloud computing before adoption (Emerson, 2010). We summarize the characteristics in the following table.. Ch. engchi. 4. i n U. v.
(12) Table 2-1. Features of Cloud Computing Public Cloud Name. Year. Description. Features of Cloud. Goodburn and Hill. 2010. The cloud has proven itself an Scalability effective tactic for achieving greater flexibility efficiency in applications ranging from email to photo storage to Web hosting.. Géczy, Izumi and. 2012. Public clouds are always provided by Third-party outside providers to organizations outsourcing requiring them.. Won Kim et al.. 2009. A third-party computing provider helps an enterprise store data and shares them with other enterprises.. Knorr and Gruman. 2008. Hasida. 立. multitenant. sit. y. The scalability of cloud computing Scalability marshals resources in a way that makes programs run smoothly even with a large number of users.. n. al. er. io 2010. a. ‧. ‧ 國. 學. customers using architecture.. 2008. Sudipto Das et al.. Third-party outsourcing. The public type of cloud computing Accessibility delivers a single application through the browser to thousands of. Nat. Hayes. 政 治 大. v i n Cloud emerged as a C h computing has U i e h n g c for deploying pervasive platform. Scalability. scalable and highly available Internet applications. Bhardwaj, and Jain. Jain, 2010. Public clouds provide organizations Third-party with the flexibility to choose outsourcing between multiple cloud computing vendors and a pay-as-you-go feature.. Bhardwaj, and. Jain, 2010. Cloud computing offers much more flexibility flexibility than past computing. Jain. methods. Private Cloud. Sotomayor et al.. 2009. Private cloud deployments provide Self-owned local users with a flexible and agile infrastructure 5.
(13) private infrastructure to operate service workloads within their administrative domain. Chow et al.. 2009. Traditional security, availability, and Self-owned third-party data control are prompting infrastructure some companies to build private clouds to avoid these issues by building a self-owned infrastructure.. Doelitzscher et al.. 2011. The main objective of building a Self-owned private cloud is to create on-demand infrastructure infrastructures in the company.. Sultan. 2009. A private cloud requires a team of network, database, and system management experts to maintain the system.. 政 治 大. 立Cloud. 2010. computing provides added Cloud service value for organizations, saving costs in sustainability operations, resources and staff, as well. ‧ 國. 學. ‧. as providing new business opportunities for service-oriented models. Achieving long-term sustainability is an important success factor for organizations.. io. sit. y. Nat. er. Chang, Wills, and Roure. Cloud service sustainability. al. n. v i n The previous literature review that there are three features C hallows us to conclude U i e h n gc of public clouds: (1) Third-party outsourcing – Cloud-implementing companies must outsource the implementation to a third-party company due to a relative lack of knowledge regarding cloud implementation. (2) Accessibility – The concept of accessibility may be provided via the Internet, which is also critical to cloud computing, as cloud computing services should be accessible to all those qualified to access it. (3) Scalability and flexibility – Business fluctuates according to high and low seasons. During high seasons, companies ought to meet a large amount of need coming from its customers, and it is superfluous to own a massive quantity of software and hardware simply to meet that need. Therefore, cloud computing should allow companies to scale up and down computing capacity and to be flexible in switching between different services when necessary. 6.
(14) We also summarize two features of private clouds: (1) Self-owned infrastructure – Private clouds enable companies to have more control of the technology, which stems from the increased possession of cloud software and hardware. Companies may either build their own infrastructure maintained by their staff or own a private computing site external to their organization that is used solely by them. (2) Cloud service sustainability – Due to the nature of private clouds, companies adopting this type of cloud service must maintain its operation and even have a group of IT maintainers responsible for providing services in order and in use. This research concludes several features of both public and private clouds. To ensure that these features will result in positive effects and benefits, companies should be aware of their readiness to implement cloud computing.. 2.2 Readiness for Cloud政 Computing 治 2.2.1. 立 Cloud Readiness. 大. ‧. ‧ 國. 學. Moving IT services to cloud computing reorganizes a company’s IT landscape and makes the company subject to the impact on its IT strategy and performance. Selecting the wrong IT services for the cloud may thus be operationally costly and. n. al. er. io. sit. y. Nat. cause pains in business strategy (Loebbecke, Thomas, and Ullrich, 2012). Therefore, it is critical for a company to devise a fully developed strategy and choose a type of cloud computing that best suits it before implementing cloud computing. For example, a particular service may be applicable for an organization when a company is in its startup stage. As the organization grows in size, the same service that was previously applicable may be out of date and soon require replacement (Dargha, 2011). Based on the literature review, cloud readiness may be categorized into two major readiness concerns: (1) Technological readiness Successful cloud implementation requires careful attention to technological issues, such as bandwidth needs and virtualization, to render flexible and scalable hardware services (Wang and Laszewski, 2010). In addition, Emerson (2010) states that recognizing technological vulnerabilities in existing facilities before embarking on the deployment of cloud computing offers an opportunity for potential cloud computing adopters to fortify their critical systems. Therefore, we reason that all the. Ch. engchi. i n U. v. cloud-related techniques, including an organization’s infrastructure and employees’ knowledge about operating this technology, should be considered. (2) Managerial readiness In addition to technological concerns, managerial concerns surrounding training 7.
(15) and security are also important. For example, IT staff will need to learn new skills to manage functions such as group multi-tenancy and application mobility, and cloud computing usually comes with an isolated security breach that has a greater impact on an enterprise (Emerson, 2010; VMware, 2011). Selecting the wrong IT services for the cloud may thus be operationally costly and potentially harm a business strategy, so both types of concerns should be taken equally seriously. In addition, due to the disparate adoption effects of public and private clouds, companies adopting cloud computing should prepare for adoption according to their choice of cloud computing. We discuss the different types of readiness for public and private clouds.. 2.2.2. Readiness for Public Clouds. In accordance with previous chapters in which we elaborate on cloud adoption and decompose readiness into managerial and technological concerns, here we discuss several readiness issues for public clouds. Categorizing some companies as “likely cloud ready” certainly requires a common understanding of cloud computing. The delivery of computing as a service rather than a product, whereby shared resources, software and information are provided to computers and other devices as a utility (such as the electricity grid) over a network (Loebbecke, Thomas, Ullrich, 2012).. 政 治 大. 立. ‧. ‧ 國. 學. n. al. er. io. sit. y. Nat. There is no doubt that companies adopting cloud computing may obtain several benefits. For instance, the scale economies of public cloud companies lead to substantial cost decreases over time (Mcafee, 2011). To obtain a foothold in cloud computing technology, one must be ready for it. Therefore, in this research, we derive three major concerns for public clouds mentioned below from previous research.. Ch. i n U. v. Technological readiness (1) Internet connection Generally speaking, public clouds are built and connected via the Internet, which suggests that cloud services should always come with connectivity. In addition, cloud computing is a recent trend in IT that moves computing and data away from desktop and portable PCs to large data centers. Cloud computing refers to applications delivered as services over the Internet as well as to the actual cloud infrastructure — namely, the hardware and systems software in data centers that provide these services (Dikaiakos et al., 2009). The use of a public cloud increases speed to market, reducing or eliminating information latency, a devilish issue common to conventional value. engchi. chains, and cloud computing features accessibility and flexibility as two main criteria regarding connectivity (Goodburn and Hill, 2010). Managerial readiness (2) Contract management 8.
(16) Cloud computing is a form of outsourcing; as such, it shares the essential risk profile of all outsourcing contracts concerning opportunistic behavior, shirking, poaching, and opportunistic renegotiation (Clemons and Chen 2011). As the importance of cloud computing grows, an increasing number of companies are riding this wave to provide public cloud computing services, such as Amazon, Google, Microsoft, Rackspace, and GoGrid. These cloud providers offer a variety of options in terms of pricing, performance, and feature set (Li et al., 2010). In addition being ready, adopting companies should be mindful of some contract issues, such as performance, security (including data citizenship and data residence), and legal recourse (Clemons and Chen, 2011). (3) IT staff training The strategic importance of IT has been established, and progress has been made in understanding how to introduce IT effectively. Much research, especially in the MIS discipline, has been undertaken to develop a better understanding of IT implementation and to assess the contribution of IT to the improvement of organizational efficiency and effectiveness (Lai and Mahapatra, 1997). By the same token, the adoption of cloud computing should be taken seriously as well. The adopting company must address not only technological issues, such as software and. 立. 政 治 大. ‧ 國. 學. ‧. hardware, but also staffing issues, including training operations staff to implement the. n. al. er. io. sit. y. Nat. technology (Subashini and Kavitha, 2011). Compared to private clouds, public clouds are far less complicated in several ways. Because a company does not need to own its own data center or computing site when adopting public clouds, all the company should do is equip its staff that uses the cloud technology with some skills or knowledge of the technology as opposed to fully understanding how to develop or help the company deliver new services.. 2.2.3. Ch. engchi. i n U. v. Readiness for Private Clouds. Companies that desire the benefits of cloud computing services without the risks are looking to create cloud-like environments in their own data centers. Private clouds represent a convergence of tech trends holding great promise for enterprise computing and are a powerful combination of modular commodity hardware that may be sliced and diced into many small pieces, with networking and storage that may be dynamically allocated through preset policies (Babcock, 2009). As one steps into the field of private clouds, one should be more aware of the complex nature of private clouds, which involve a greater amount of preparatory legwork. Therefore, in this research, we derive four major concerns for private clouds mentioned below from previous research. Technological readiness 9.
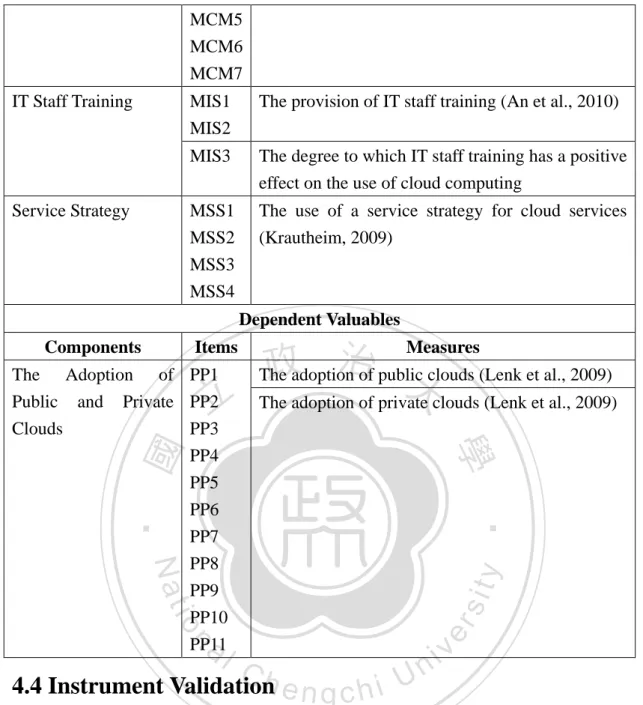
(17) (1) Virtualization Because cloud computing will be a multitenant environment for running virtual systems, it will provide access to virtual CPUs, memory, storage networks, IP addresses, firewalls and catalog capabilities. To implement virtualization, companies encounter with various changes that result from virtualizing current equipment and facilitating inner processes (Preimesberger, 2011). There are several typical aspects of virtualized data centers. These aspects include setting up new tenants, backing up the databases, managing the customizations and configurations of tenants, and obtaining patches and newer versions of the software, with which we may understand that several issues of virtualization are influential and require preparation when introducing private clouds (Rochwerger et al., 2009). (2) IT infrastructure The private cloud infrastructure is often operated solely within a single organization and managed by the organization or a third party regardless of whether it is located on- or off-premises (Dillon, Wu, and Chang, 2010). Therefore, self-owned IT will be necessary and require some “headroom” to manage normal peaks in demand. Infrastructure systems that are able to operate efficiently at reduced loads reduce the cost of designing in this headroom (Emerson, 2010). In addition, this research defines an organization owning IaaS as a private cloud user, so companies. 立. 政 治 大. ‧. ‧ 國. 學. must construct their own IaaS infrastructure and maintain it.. sit. y. Nat. Managerial readiness (1) Service strategy. n. al. er. io. For public cloud users, to implement cloud computing, organizations generally simply must set up a secure account with a provider. Normally, some products offer Internet-based services—such as storage, middleware, collaboration, and database capabilities—directly to users. Providers charge users using a range of methods, such as by bandwidth consumed, data transferred, or storage space filled (Leavitt, 2009). However, being a private cloud user entails being a cloud service provider. Some research suggests cloud computing pricing strategy may be considered more of a “business” issue, which gives rise to company issues, for example, how to provide customers with the services they need and how much the service provider should charge its customers (Marston et al., 2010). To provide services, pricing strategy is important to private cloud users, as is customers’ knowledge about how to use the services.. Ch. engchi. i n U. v. (2) IT staff training Compared to public clouds, training IT staff for private clouds is more complicated in several ways. When private clouds are used within a company, IT staff carry greater responsibility for operating and maintaining the IT. IT staff must learn 10.
(18) new skills to manage functions such as group multi-tenancy and application mobility. Ideally, they will be able to streamline processes to manage availability, reliability, scalability, security and service-level agreements using the same tools for both internal and external virtualized cloud environments (VMware, 2011). A private-cloud-adopting company should both recruit a group of employees and develop a formal system to train these employees in preparation for providing cloud services.. 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. 11. i n U. v.
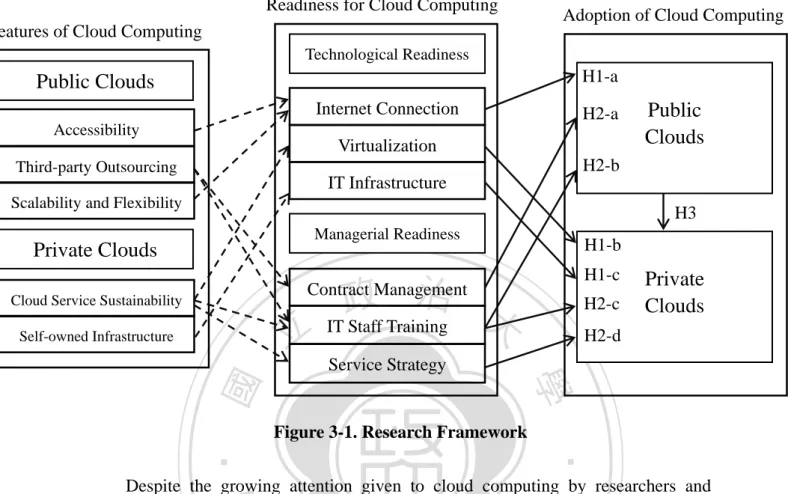
(19) 3. Chapter Three: Research Model Readiness for Cloud Computing. Adoption of Cloud Computing. Features of Cloud Computing Technological Readiness. H1-a. Public Clouds Internet Connection. H2-a. Accessibility. Virtualization. Public Clouds. H2-b. Third-party Outsourcing. IT Infrastructure Scalability and Flexibility. H3 Managerial Readiness. Private Clouds. H1-b H1-c. 政 治 大 IT Staff Training. Contract Management. Cloud Service Sustainability. 立. Self-owned Infrastructure. H2-c. Private Clouds. H2-d. Service Strategy. ‧ 國. 學 Figure 3-1. Research Framework. ‧. n. al. er. io. sit. y. Nat. Despite the growing attention given to cloud computing by researchers and companies, the understanding of cloud computing remains in its infancy. To change this phenomenon, client companies must know which of their IT services are appropriate for cloud computing. Companies that from time to time wish to seize on cloud computing and make a change fail to develop the specific and applicable means whereby they prepare to implement cloud computing (Loebbecke, Thomas, and Ullrich, 2012). Due to this phenomenon, this work contributes to the research on cloud readiness. The research framework is shown in Figure 3-1. The research incorporates technological and managerial concerns, each of which is illustrated on the top and bottom of Figure 3-1. We propose that the two concerns of readiness have major effects on cloud adoption. As mentioned in the former chapter, different concerns affect either public or private clouds or both of them. As we take a step further, public and private cloud adoption may be decomposed into different factors affecting their. Ch. engchi. i n U. use. The details of this framework are described below.. 3.1 Technological Readiness 3.1.1 Internet Connection 12. v.
(20) Web 2.0 applications use the Web as a platform for delivering end-user applications. Because cloud computing is based on Web 2.0 application with the aim of delivering services in a far-flung way, and because accessibility, scalability, and flexibility are all features afforded by public clouds, cloud computing requires the support of an Internet connection (Raman, 2008). Ercan (2010) notes that the most important feature of the various applications offered by cloud computing is its flexibility and scalability. Scalability is what the cloud provides its services to clients and enables clients to operate and process service requests according to work traffic at any time. Cloud computing also provides the end-users with the flexibility to configure various partitions of resources and access all the given services without being limited to one device (Buyya et al., 2009). In addition, cloud computing entails moving computing and data from one’s desktop and portable devices to data centers and having all the sources controlled at one site. Therefore, all the features of cloud computing make the Internet connection important; if the Internet connection fails, services in the cloud are inclined to be blocked and unavailable (Dikaiakos et al., 2009). Kandukuri et al. (2009) also maintains that cloud computing uses the Internet and all connection devices as communication media. Companies’ success in preparing to implement cloud computing partly demands Internet facilities and the ability to connect and deliver services through these devices; accordingly, we propose the. 立. ‧. ‧ 國. 學. following:. 政 治 大. y. Nat. n. 3.1.2 Virtualizationa l. er. io. sit. Hypothesis 1-a: An Internet connection has a positive impact on public clouds.. Ch. engchi. i n U. v. A cloud computing platform dynamically provisions, configures, reconfigures, and de-provisions servers (physical machines or virtual machines) when needed. In the cloud, the cloud’s virtual infrastructure, invisible to all the users, facilitates services and circulates demands from users on demand (Gurav and Shaikh, 2010). Cloud computing provides the service abstraction necessary to ensure that an application or business service is not directly tied to the underlying hardware infrastructure, such as servers, storage or networks. Within the scope of private clouds we mentioned previously, private cloud adopters are those who possess their own Iaas layer. Self-owned infrastructure forms the basis of private clouds, where virtualization is practiced. Ibrahim et al. (2010) also propose that virtualization enables on-demand access to a pool of virtual computing resources and that cloud owners should modify their computing sources and make them cloud-workable. Therefore, we hypothesize the following: 13.
(21) Hypothesis 1-b: Virtualization has a positive impact on private clouds.. 3.1.3. IT Infrastructure. The operation of private clouds is often executed within and solely under the control of an organization (Dillon, Wu, and Chang, 2010). For this operation to occur, cloud computing requires a cloud-implementing company to construct and own its IT infrastructure, such as a data center, which is not news for today’s major Internet companies that have built massive data centers to power their cloud businesses. One company that serves as a large cloud provider must consider employing a larger site to manage a large amount of work (Weiss, 2007). In a data center such as that employed by Google, each server is fundamentally an independent machine running its own copy of an operating system to meet customers’ needs. Therefore, we hypothesize the following:. 立. 政 治 大. ‧ 國. 學. Hypothesis 1-c: IT infrastructure has a positive impact on private clouds.. ‧. 3.2 Managerial Readiness. Nat. sit. y. 3.2.1 Contract Management. n. al. er. io. Companies using public clouds always rely on a third-party cloud service provider to offer cloud computing instead of building their own clouds. Legal, regulatory and audit issues associated with contracting should be assessed before cloud-based services are used, and companies should not contract for IT services with a vendor that refuses to provide detailed information on continuity management programs. Therefore, cloud computing users should prepare themselves for the incorporation with the cloud provider before implementation. Organizations should define service-level requirements for IT workload, demand service-level agreements from the provider and ensure that the contract contains penalty clauses when service-level agreements are not met (Heiser and Nicolett, 2008). In addition, because cloud users depend on their providers, it is vital to have a proper risk management program that may proactively and routinely identify, monitor, assess, and manage the. Ch. engchi. i n U. v. systems and technology risks to avert their occurrence or mitigate their impacts (Paquette, Jaeger, and Wilson, 2010). Accordingly, we propose the following: Hypothesis 2-a: Contract management has a positive impact on public clouds. 14.
(22) 3.2.2 IT Staff Training Applying public clouds requires cloud users to outsource cloud computing to a third-party provider. Engaging cloud service providers is similar to managing uncertainty, and negotiating under uncertainty represents both the most challenging problem at the outsourcing phase and the most practical problem faced during the actual implementation of cloud computing (An et al., 2010). To manage uncertainty and maintain the cloud services, a group of well-trained employers will be critical in the outsourcing phase. In addition to the questions concerning the construction of service-level requirements and proactive measures mentioned before, the trained group should be able to observe the process of contract fulfillment and maintain the performance of cloud providers, shifting from one provider to another when necessary. Therefore, we propose the following:. 政 治 大. 立. Hypothesis 2-b: IT staff training has a positive impact on public clouds.. ‧ 國. 學. ‧. Private clouds are a rising technology in need of much work. Because private clouds must be maintained and used continuously, IT staff training takes on a more. n. al. er. io. sit. y. Nat. important position among companies using them. Notwithstanding current research and existing cases of successful cloud implementation, companies nonetheless must constantly train their employees to achieve satisfactory performance (Li, Chen, and Wang, 2010). In preparation for running cloud services smoothly and infallibly, IT staff should be provided with proper training and be capable of streamlining processes to manage reliability, availability, scalability, and security, using the same tools for both internal and external virtualized cloud environments (VMware, 2011). It is not easy for a company to manage a cloud, and employees’ knowledge of it may be critical. If the staff fails to maintain or sustain cloud services, the services may be out of order, making a negative impression on the company’s customers or employees in other departments. Therefore, we propose the following:. Ch. engchi. i n U. v. Hypothesis 2-c: IT staff training has a positive impact on private clouds.. 3.2.3 Service Strategy Krautheim (2009) suggests that cloud computing is poised to revolutionize computing as a service and that providers should sustainably maintain the operation of cloud computing. With the ability to provide on-demand computing resources 15.
(23) dynamically, companies are facing the challenge of changing their IT strategy. As new technology appears, this new approach to doing business comes with its new changes. For example, the cloud characteristic of measured service suggests that any cloud service has a metering capability at an abstraction level appropriate to the service type (such as storage, processing, and active user accounts), which give rise to some issues, such as billing and pricing (Grobauer, Walloschek, and Stocker, 2011). If they do not resolve problems resulting from these issues, companies may fail abysmally in cloud computing. Entering the cloud computing field entails the need for strategic reform. In addition to billing and pricing, companies’ strategy should factor in holistic service-selecting measures to choose the right services to be deployed on cloud and improve the services to satisfy demands from customers so that cloud services may be sustained at a company. Therefore, we propose the following:. 政 治 大. Hypothesis 2-d: Service strategy has a positive impact on private clouds.. 立. ‧ 國. 學. 3.3 The adoption Public and Private Clouds. ‧. Private and public clouds differ primarily in terms of the type of ownership and access rights that they support. Access to private cloud resources is restricted to the. n. al. er. io. sit. y. Nat. users belonging to the organization that owns the cloud (Buyya, Ranjan, and Calheiros, 2010). In this research, the difference we define between public and private cloud users is the ownership of the IaaS layer in cloud computing. However, on the adoption side of cloud computing, when cloud users transform public clouds into private ones, due to the cloud users’ background and knowledge of public clouds, the users will have a better grip on private clouds and a better chance to succeed; accordingly, we propose the following:. Ch. engchi. i n U. v. Hypothesis 3: Public cloud adopters are more likely to succeed in adopting private clouds.. 16.
(24) 4. Chapter Four: Research Methodology 4.1 Pilot Test In preparation for the development of the research model, we conducted interviews with two existing cloud service providers in 2012. Both of these providers play important roles in the national provision of cloud service and consultation. (3) Chunghwa Telecom Founded in 1996 with a capital of $96.48 billion, Chunghwa Telecom began with services ranging from on-site to mobile communication. In recent years, Chunghwa Telecom has become one of the nation’s largest telecommunication companies and has crossed over to cloud services in an effort to improve communication quality and maximize customer satisfaction. (4) ASUS Founded in 1990, ASUS has quality, humanity, and courtesy as business values. Beginning as a computer and hardware manufacturer, the company has recently begun to aid customers in processing massive amounts of information and is embarking on the provision of cloud services. During the interviews, we presented our research model, along with several. 立. 政 治 大. ‧. ‧ 國. 學. n. al. er. io. sit. y. Nat. questions covering managerial and technological issues such as Internet connections and disaster recovery processes. The questions were designed to cause them to bounce their cloud computing implementation experiences off of their companies and consult with them regarding the recent landscape of cloud computing. After the interviews, we altered our research framework and made it more suitable for our research by eliminating several obsolete issues and adding ongoing issues to the framework. For example, given the current cloud computing environment, the introduction of cloud computing to companies is not as much of a barrier as it was in the past, as several cloud providers aid companies with the implementation of cloud computing or even perform the preparatory work for them; at the same time, cloud-introducing companies are only required to outsource cloud computing and focus on how to make the most out of the technology. Therefore, companies should place an emphasis on developing better services and pricing strategies based on cloud computing. The final framework is shown in chapter three.. Ch. engchi. 17. i n U. v.
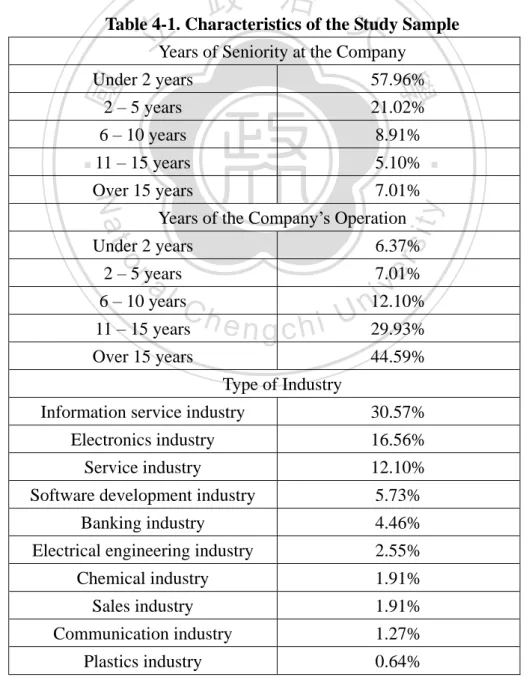
(25) 4.2 Data Collection We conduct the research empirically via online questionnaire. The targets of our questionnaire are both companies that are currently implementing cloud computing and those that are not, and the target respondents are the staff at the companies and do not necessarily work in the IT department. We mail the link to our questionnaire to our target respondents via email. To collect as large a sample as possible, we place our questionnaire on several technology-related web forums. To boost the motivation of our targets to complete the questionnaire, we offer each respondent a coupon that entitles them to $NT100 off any purchase at the Carrefour hypermarket. The questionnaire is available online for a month, and we receive 155 completed questionnaires, of which only 140 are usable. A summary of sample characteristics is provided below in Table 4-1.. 治 政 Table 4-1. Characteristics of the大 Study Sample 立Years of Seniority at the Company 57.96%. 2 – 5 years. 21.02%. 6 – 10 years. 8.91%. 11 – 15 years. 5.10%. Over 15 years. 7.01%. sit. 6.37%. 2 – 5 years. io. Under 2 years. er. Nat. Years of the Company’s Operation. y. ‧. ‧ 國. 學. Under 2 years. 7.01%. n. al. Ch. 6 – 10 years. 11 – 15 years. engchi. iv 12.10% n U. Over 15 years. 29.93% 44.59%. Type of Industry Information service industry. 30.57%. Electronics industry. 16.56%. Service industry. 12.10%. Software development industry. 5.73%. Banking industry. 4.46%. Electrical engineering industry. 2.55%. Chemical industry. 1.91%. Sales industry. 1.91%. Communication industry. 1.27%. Plastics industry. 0.64% 18.
(26) Car manufacturing industry. 0.64%. Others. 21.66%. To determine the current status of cloud computing implementation at each company, we tabulate the data obtained and tallied the number of companies with each status. Based on the previously mentioned taxonomy, which is used to categorize companies on the basis of services implemented within the IAAS layer, we realize that the number of companies that has adopted public clouds alone is 31. However, the number of companies that has adopted private clouds alone is 33. Twenty-three companies have not applied any cloud computing services, whereas the number of companies that has applied both public and private clouds is 53, which is the largest amount.. 4.3 Measurements. 立. 政 治 大. ‧ 國. 學. The constructs of the research model are operationalized using the measures shown in Table 4-2 below. The questionnaire is shown in Appendix A. Table 4-2. Item Measures of Cloud Computing Readiness. io. al. n. TIC2 TIC3. Virtualization. IT Infrastructure. Components. TV1. The possession of an Internet connection (Raman, 2008). sit. TIC1. Measures of Technological Readiness. y. Items. er. Internet Connection. ‧. Nat. Components. Independent Variables. The degree to which the Internet connection reaches and is accessible by users. Ch. engchi. i n U. v. The possession of virtualized assets (Gurav and Shaikh, 2010). TV2. The degree to which employees responsible for cloud services manipulate virtualization well. TII1 TII2. The scope of IT sources owned by a company (Dillon, Wu, and Chang, 2010). TII3 TII4. The degree to which companies’ internal IT property works and helps to solve problems. Items. Measures of Managerial Readiness. Contract Management MCM1 The deployment of people responsible for contract MCM2 management (Heiser and Nicolett, 2008) MCM3 The degree to which contract management MCM4 facilitates cloud service outsourcing 19.
(27) MCM5 MCM6 MCM7 IT Staff Training. Service Strategy. MIS1 MIS2. The provision of IT staff training (An et al., 2010). MIS3. The degree to which IT staff training has a positive effect on the use of cloud computing. MSS1 MSS2 MSS3 MSS4. The use of a service strategy for cloud services (Krautheim, 2009). Dependent Valuables Components. Measures 治 政 The adoption of public clouds (Lenk et al., 2009) 大. Items. The Adoption of PP1 Public and Private PP2 Clouds PP3 PP4 PP5. ‧ sit. n. er. io. al. y. Nat. PP6 PP7 PP8 PP9 PP10 PP11. The adoption of private clouds (Lenk et al., 2009). 學. ‧ 國. 立. C. hengchi 4.4 Instrument Validation. i n U. v. Before we begin to analyze the data, we verify the model we proposed in an earlier chapter and ensure that the model will be more relevant. We conduct factor analysis to assess the validity of each construct. We use the principle component analysis and Varimax rotation method to extract factors. The initial results of factor analysis are shown in Table 4-3. Table 4-3. The Initial Results of Factor Analysis 1. 2. 3. 4. 5. 6. TII1. 0.790. 0.092. 0.300. 0.244. 0.165. 0.030. TII3. 0.783. 0.065. 0.413. 0.197. 0.094. -0.030. TII2. 0.774. 0.180. 0.295. 0.030. 0.181. 0.104. TII4. 0.703. 0.089. 0.433. 0.228. -0.072. 0.269. 20.
(28) TV1. 0.684. 0.379. 0.019. 0.003. 0.338. 0.218. TV2. 0.594. 0.298. 0.251. 0.161. 0.529. 00.194. MSS4. 0.568. 0.147. 0.529. 0.088. 0.344. 0.247. MCM7. 0.062. 0.852. 0.138. 0.260. 0.047. 0.067. MCM6. 0.163. 0.829. 0.100. 0.209. 0.193. 0.097. MCM4. 0.212. 0.779. 0.173. 0.249. 0.039. 0.210. MCM5. 0.146. 0.659. 0.320. 0.396. 0.170. 0.091. MCM2. 0.180. 0.545. 0.239. 0.387. 0.293. 0.527. MSS1. 0.386. 0.238. 0.786. 0.036. 0.148. 0.039. MSS2. 0.458. 0.230. 0.741. 0.010. 0.173. -0.043. MIS3. 0.326. 0.194. 0.729. 0.128. 0.132. 0.312. MIS2. 0.310. 0.151. 0.566. 0.323. 0.455. 0.172. TIC2. 0.129. 0.243. 0.098. 0.094. TIC1. 0.088. 0.152. TIC3. 0.148. 立 0.295. 0.007. -0.002. 0.800. 0.163. 0.099. MIS1. 0.333. 0.276. 0.370. 0.276. 0.652. 0.057. 0.491. 0.116. 0.483. 0.072. 0.566. 0.165. 0.258. 0.529. 0.216. 0.337. 0.103. 0.631. 0.248. 0.483. 0.179. 0.438. 0.200. ‧. MCM1. ‧ 國. MCM3. 學. MSS3. 0.058 0.880 治 政 0.310 0.148 0.831 大. 0.576. n. al. er. io. sit. y. Nat. We attempt to confine ourselves to the major items that are important for these factors. We omit some items that do not fall into the original categories to see if better factors can be generated. By repeating the omission of different items, we finally obtain better factor analysis results, which are shown in Table 4-4.. Ch. engchi. i n U. v. Table 4-4. Summary of Factor Analysis TII. MCM. TIC. MSS. MIS. TV. TII2. 0.821. 0.210. -0.007. 0.128. 0.172. 0.181. TII3. 0.821. 0.059. 0.170. 0.319. 0.095. 0.117. TII4. 0.798. 0.156. 0.186. 0.149. 0.306. -0.022. TII1. 0.761. 0.064. 0.239. 0.309. 0.008. 0.285. MSS4. 0.582. 0.172. 0.087. 0.427. 0.351. 0.327. MCM7. 0.042. 0.854. 0.223. 0.081. 0.068. 0.013. MCM6. 0.139. 0.840. 0.174. 0.055. 0.074. 0.143. MCM4. 0.202. 0.814. 0.231. 0.132. 0.058. 0.069. MCM5. 0.131. 0.657. 0.397. 0.353. 0.096. 0.124. MCM3. 0.236. 0.630. 0.347. 0.037. 0.402. 0.263. MCM2. 0.145. 0.621. 0.412. 0.191. 0.309. 0.339. 21.
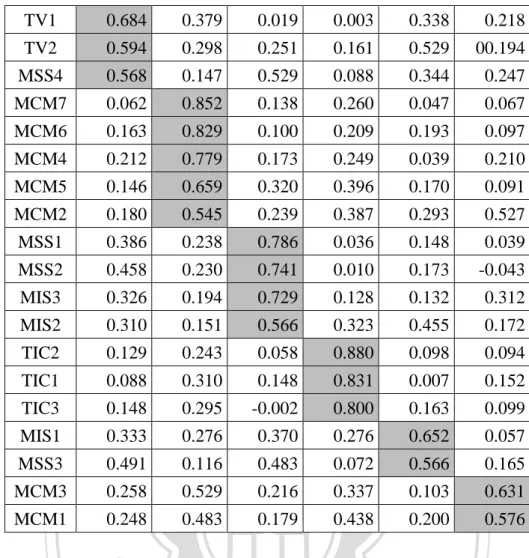
(29) TIC2. 0.136. 0.255. 0.884. 0.032. 0.040. 0.020. TIC1. 0.105. 0.323. 0.820. 0.017. 0.206. -0.026. TIC3. 0.105. 0.293. 0.815. 0.023. 0.019. 0.160. MSS1. 0.422. 0.202. 0.019. 0.770. 0.267. 0.086. MSS2. 0.488. 0.182. -0.008. 0.764. 0.172. 0.101. MIS3. 0.446. 0.257. 0.081. 0.342. 0.716. 0.016. MIS2. 0.349. 0.154. 0.301. 0.337. 0.617. 0.294. TV2. 0.465. 0.268. 0.197. 0.352. 0.149. 0.671. TV1. 0.545. 0.354. 0.005. -0.007. 0.124. 0.609. The final results of the factor analysis are presented in Table 4-4. Initially, there were 23 measurements; after several attempts, 3 measurements, MCM1, MSS3, and MIS1, are removed. The remaining 20 items fall into six categories of final factors. After the process, we recognize that the factor loading of item MSS4 is less than 0.5 in the MSS category. However, to maintain the number of items in a category with more than three items, we place item MSS4 in the MSS category. We will later analyze reliability and validity. To generate consistent results, we use Cronbach’s alpha, which measures the degree to which all items are error-free and is the most widely adopted measure for. 立. 政 治 大. ‧. ‧ 國. 學. sit. y. Nat. reliability assessment (Zhu et al. 2003). Therefore, we assess reliability using Cronbach’s alpha; the values shown in Table 4-5 range from 0.851 to 0.926, suggesting adequate reliability.. al. n. Factor. Contract Management. Measurements. Ch. MCM7. eMCM6 ngchi. er. io. Table 4-5. Measurement of Constructs. Cronbach’s Alpha. i n U. v. 0.926. MCM4 MCM5 MCM3 MCM2 IT Infrastructure. TII3. 0.905. TII2 TII4 TII1 Internet Connection. TIC2. 0.894. TIC1 TIC3 Service Strategy. MSS1 22. 0.900.
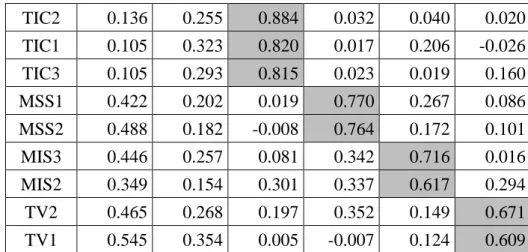
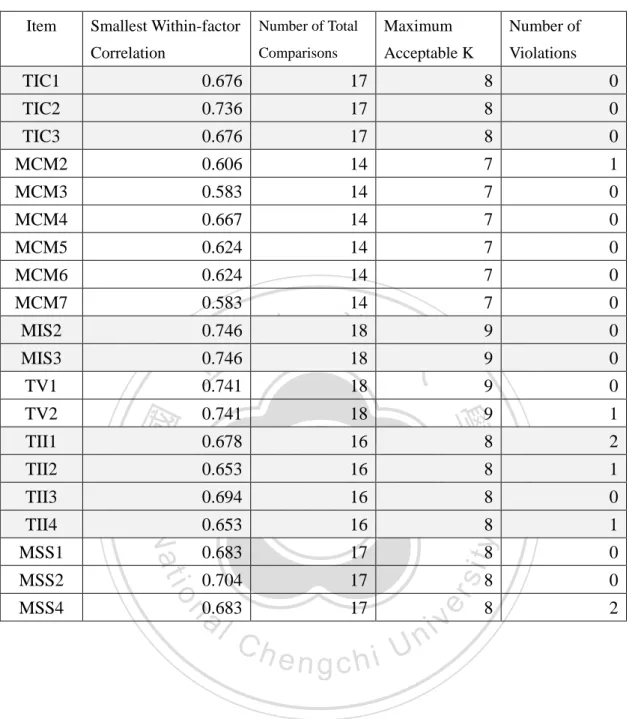
(30) MSS2 MSS4 IT Staff Training. MIS3. 0.854. MIS2 Virtualization. TV2. 0.851. TV1 Construct validity has two aspects: convergent and discriminant validity (Bagozzi et al., 1991). Convergent validity is assessed by scrutinizing the degree to which the correlation of within-factors, items of the same factor, is larger than zero and is therefore sufficient for the test of discriminant validity. The correlation matrix in Table 4-6 shows that the smallest within-factor correlations of Internet connection, Contract management, IT staff training, Virtualization, IT infrastructure, and Service strategy are 0.676, 0.583, 0.746, 0.741, 0.653, and 0.683, respectively. These numbers are significantly higher than zero and thus sufficient for the test of discriminant analysis. Normally, the correlation between different factors ought to be low for a claim of discriminant validity. For each item, we tabulate its smallest within-factor correlation,. 立. 政 治 大. ‧ 國. 學. ‧. with which we compare the correlation number of other items in other factors and count the number (K) of instances in which the smallest within-factor is smaller than the comparable numbers. K should be less than half of the total number of comparisons, which we name maximum acceptable K. The results are shown in Table 4-7 and provide sufficient support for convergent and discriminant validity.. n. er. io. sit. y. Nat. al. Ch. engchi. 23. i n U. v.
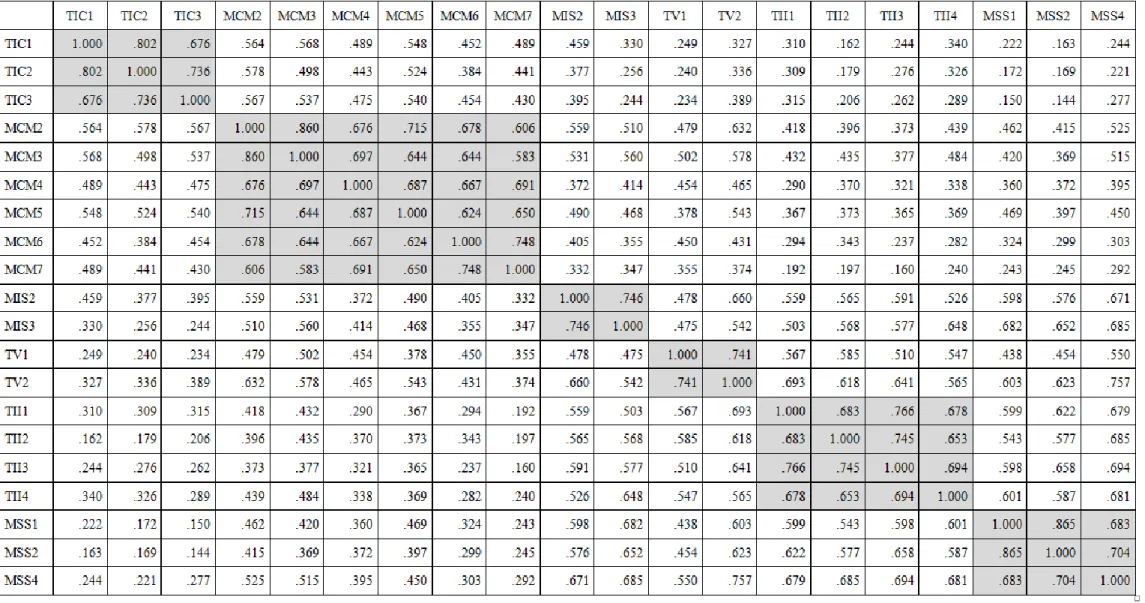
(31) Table 4-6. Correlation Matrix. 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. 24. i n U. v.
(32) Table 4-7. Summary of K-count for Discriminant Validity Item. Smallest Within-factor. Number of Total. Maximum. Number of. Correlation. Comparisons. Acceptable K. Violations. TIC1. 0.676. 17. 8. 0. TIC2. 0.736. 17. 8. 0. TIC3. 0.676. 17. 8. 0. MCM2. 0.606. 14. 7. 1. MCM3. 0.583. 14. 7. 0. MCM4. 0.667. 14. 7. 0. MCM5. 0.624. 14. 7. 0. MCM6. 0.624. 14. 7. 0. MCM7. 0.583. 14. 7. 0. MIS2. 0.746. 9. 0. MIS3. 0.746. 9. 0. 18. 9. 0. 9. 1. 8. 2. TV2. 0.741. 18. 0.678. 16. 0.653. 16. 8. 1. 0.694. 16. 8. 0. 0.653. 16. 8. 1. 0.683. 17. 0.704. 17. al. 17. MSS1. 0.683. n. MSS4. io. MSS2. Nat. TII4. Ch. engchi U. 25. y. TII3. 8. 0. 8. 0. 8. 2. sit. TII2. er. TII1. ‧ 國. 立 0.741. 學. TV1. ‧. 18 政 治 大 18. v ni.
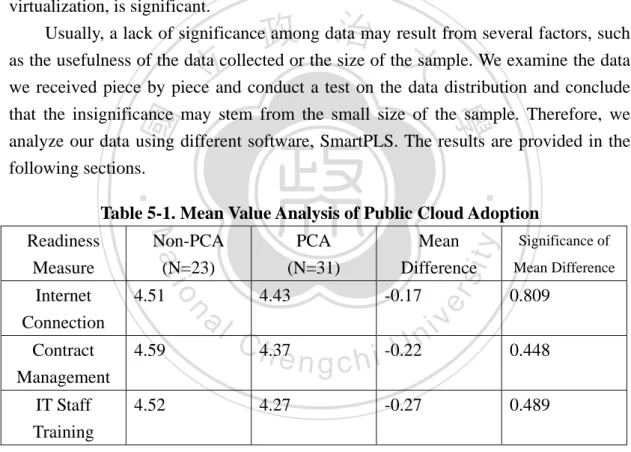
(33) 5. Chapter Five: Analysis and Results 5.1 Mean Value Analysis We divide all of the data collected into four categories and denote companies that have adopted public clouds PCAs and those that have adopted private clouds PrCAs. We name companies that have not adopted cloud computing of any type Non-PCAs and Non-PrCAs, as in tables 5-1 and 5-2, respectively. Tables 5-1 and 5-2 provide a summary of the mean value analysis of public and private cloud adoption. In table 5-1, the comparison of mean values for public cloud adoption indicates that none of the measure comparisons are significant. In the meantime, we perform an analysis of private cloud adoption, and only one of the measure comparisons in Table 5-2, virtualization, is significant. Usually, a lack of significance among data may result from several factors, such as the usefulness of the data collected or the size of the sample. We examine the data we received piece by piece and conduct a test on the data distribution and conclude that the insignificance may stem from the small size of the sample. Therefore, we analyze our data using different software, SmartPLS. The results are provided in the following sections.. 立. 政 治 大. ‧. ‧ 國. 學. Table 5-1. Mean Value Analysis of Public Cloud Adoption. io. 4.51. Contract Management. 4.59. IT Staff Training. 4.52. al. 4.43. y. Mean Difference -0.17. n. Internet Connection. PCA (N=31). sit. Non-PCA (N=23). C h4.37 engchi 4.27. er. Nat. Readiness Measure. i n -0.22 U. v. -0.27. Significance of Mean Difference. 0.809 0.448 0.489. Table 5-2. Mean Value Analysis of Private Cloud Adoption Readiness Measure. Non-PrCA (N=23). PrCA (N=33). Mean Difference. Significance of Mean Difference. Virtualization. 4.50. 5.03. 0.53. 0.086. IT. 4.20. 4.64. 0.44. 0.160. 4.52. 4.47. -0.07. 0.856. Infrastructure IT Staff Training. 26.
(34) Service Strategy. 5.00. 5.26. 0.26. 0.353. 5.2 Results The research model and hypotheses are analyzed using the SmartPLS software. Partial least squares path modeling (PLS) is a component-based estimation method and involves the comparison and testing of corresponding path coefficients among different groups, typically by means of t-statistics. In addition, with a small sample size and normally distributed data, the component-based approach is more likely to detect between-group differences (Qureshi and Compeau, 2009). The graphical results and summary of PLS analysis are shown in Figure 5-1 and Table 5-3, respectively.. 政 治 大. Figure 5-1. PLS Analysis (Calculated Using SmartPLS). 立. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. 27. i n U. v.
(35) Table 5-3. Summary of PLS Analysis. Contract Management. Original. Sample. T Statistics. Significance. Sample (O). Mean (M). 0.068. 0.032. 0.432. 0.333. 0.014. 0.039. 0.162. 0.436. -0.021. -0.015. 0.194. 0.423. -0.270. -0.231. 2.196. 0.014. 0.060. 0.076. 0.561. 0.287. 治 政 0.127 0.166 大1.479. 0.069. 0.124. 0.123. 1.729. 0.042. 0.550. 0.547. 10.408. → Public Clouds IT Staff Training. → Public Clouds IT Staff Training. → Private Clouds Service Strategy. → Private Clouds Internet Connection. → Public Clouds IT Infrastructure. 立. → Private Clouds. 學. ‧ 國. Virtualization. → Private Clouds Public Clouds. ‧. → Private Clouds. 0.000. Nat. y. sit. n. al. er. io. Figure 5-1 shows several connected factors in accordance with our research model, mentioned in chapter 3. The number on each path is measured using t-statistics. Table 5-3 provides a summary of our analysis and includes original sample, sample mean, t statistics, and significance. The original sample number in Table 5-3 indicates the path coefficient of the route, shown in the first column, and is either a positive or a negative figure. The negative or positive sign indicates whether the factor on the left side of a path (to the left of the arrow) is in positive or negative relation to the factor on the right. Additionally, the greater the absolute number of a path coefficient, the stronger the path relation is. For instance, the path coefficient of the service-strategy-to-private-clouds path is -0.270, which means that service strategy is negatively related to private clouds. The significance numbers shown in Table 5-3 are the means we use to assess whether the path coefficients have a low degree of error. A significance number less than 0.1 suggests that the result is calculated on at least a 90% confidence level and. Ch. engchi. i n U. v. that the result is significant in estimating or explaining the research phenomena. By contrast, significance numbers greater than 0.1 are helpful in explaining phenomena. Therefore, we deem three factors ─ contract management, IT staff training, and Internet connection ─ not effective and helpful in the assessment of cloud readiness. 28.
(36) The results in Table 5-3 indicate that there are three path coefficients ─ IT infrastructure, virtualization, and the relation between public and private clouds ─ with significance and having a positive relation to private cloud adoption, which supports our three hypotheses (H1-b, H1-c, H3). As for the path coefficient between service strategy and private clouds, the number 0.014 indicates significance, but it has a negative relation to private clouds. The reason behind the reverse relation may be the recent emergence of cloud computing: it is still a new concept, and most existing cloud-computing-adopted companies still adopt public and private clouds for internal use only, which causes service strategy, the concept of providing cloud services as products, to be considered less critical to readiness issues. The results calculated using PLS support three hypotheses and reject the remainder. These results will be discussed in the follow-up section.. 政 5.3 Findings and Discussion. 治. 立. 大. ‧. ‧ 國. 學. We propose cloud readiness for both public and private clouds and empirically test our research model. Our analysis results assure us of some of our hypotheses but reject three of the readiness factors that we put forward. Accordingly, we summarize our findings and discussion as follows.. er. io. sit. y. Nat. Finding 1: virtualization and IT infrastructure are two factors that produce positive readiness for the adoption of private clouds. In table 5-3, the path coefficients of virtualization and IT infrastructure are significant and positive, which means that the two factors contribute to private cloud readiness when a company shifts from the absence of private cloud adoption to private cloud adoption. Regarding virtualization readiness, cloud computing involves a multitenant environment for meeting various demands from various users, which raises the issue of changing current company equipment status. Therefore, companies that are about to introduce private clouds must consider virtualization. Regarding the IT infrastructure factor, because private clouds are often defined as operating within a single organization or range, IT infrastructure built on-premise is necessary for those contemplating a move to private clouds. The results of our analysis are consistent with our hypotheses.. n. al. Ch. engchi. i n U. v. Finding 2: A relationship exists between public clouds and private clouds, and companies that have adopted public clouds are more likely to succeed in the adoption of private clouds. 29.
(37) In table 5-3, the coefficient of the path between public and private clouds is highly significant, and its path coefficient is positive, which indicates positive relations in the shift from public clouds to private clouds. Private and public clouds vary according to the ownership and access rights they support, and the operation of the former is often off-limits to outsiders (Buyya, Ranjan, and Calheiros, 2010). When shifting from public clouds to private clouds, companies must begin to consider how to manage the migration and must introduce several technological changes. However, because of public cloud users’ knowledge, companies will have a better chance of adopting private clouds. The results of our analysis are in favor of our hypothesis. Finding 3: None of the factors we proposed for public cloud readiness is significant, thus providing flimsy evidence in support of our hypotheses.. 政 治 大. In both table 5-1 and table 5-3, the results show that all of the factors we proposed are of no significance, which means that the factors contain a high level of error and are not able to explain our research hypotheses. We summarize the possible reasons for this result below.. 立. ‧ 國. 學. (1) Questionnaire-related Factors. ‧. i.. Small Sample Size. y. Nat. sit. n. al. er. io. We reflect on the number of returned questionnaires and the increase in this number. The questionnaire was made available online for a month initially, but the number of returned questionnaires stopped increasing two and a half weeks into the questionnaire period, and we proceeded with our research. Usually, a research sample size is chosen to maximize the chance of uncovering a specific mean difference and significance among data. A larger sample is more likely to increase the precision of tests of significance between two or more reliability coefficients (Charter, 1999). Statistical significance is a probability statement that tells us how likely it is that the observed difference is the result of chance only. The reason larger samples increase the probability of significance is that they are more likely to reach the prerequisite of significance and reliably reflect the population mean. Accordingly, our small sample size may be a partial cause of the insignificant results regarding our public cloud factors. ii.. Ch. engchi. i n U. v. Questionnaire Design. In addition to the small sample size used in our study, we examine the questionnaire items and attempt to scrutinize all of the item sets. To explain the 30.
(38) phenomenon in which the mean value of PCAs (public cloud companies) are smaller than those for Non-PCAs (non-cloud-computing companies), we examine the public cloud items in particular and review them from a questionnaire recipient’s perspective. We find that items filed under “private clouds” are more generic than those filed under “public clouds,” which indicates that private cloud item sets have greater questionnaire filler friendliness. For example, one of the items on IT infrastructure, filed under “private clouds,” is “The company is equipped with sufficient computer resources.” As for items on contract management filed under “public clouds,” one is worded as follows: “The data security of the company is not threatened by cooperation with a third party.” Because of the possible confusion caused by the item design, questionnaire recipients can be biased, thus generating the unpreferable research results. (2) Participant-related Factors. 立. Questionnaire Recipients’ Familiarity with Cloud Computing. 學. ‧ 國. i.. 政 治 大. ‧. On our questionnaire, we include several filtering items before our research question to reach our real research targets. One of the filtering questions asks recipients whether they are familiar with cloud computing and about the degree to. er. io. sit. y. Nat. which they are exposed to cloud computing. The question is multiple choice, and the answers vary from “I’ve hardly heard of cloud computing” to “I have years of experience with cloud computing and have instructed others in cloud computing.” In addition, we use numbers from one to five to indicate the familiarity of each questionnaire participant. The following table shows the mean value of each group.. al. n. v i n C hof Cloud Familiarity Table 5-4. Mean Values e n g c h i U of Different Groups. Mean. Value. of. Non-cloud Companies (N=23). Public Cloud Companies (N=31). Private Cloud Companies (N=33). 2.87. 2.67. 2.96. Cloud Familiarity We predicted that the mean value of the public cloud group would be greater than that of the non-cloud group. Surprisingly, Table 5-4 indicates that familiarity with cloud computing among non-cloud companies is better than that among public cloud companies, which is unreasonable and unsuspected. Therefore, we suggest that the mean values of group PCA in Table 5-1 are a result of the relative lack of familiarity of the private cloud users among our participants. ii.. Wide Variation In Our Returned Data 31.
(39) We inspect the returned questionnaires and search for anything that might have led to the insignificant results. First, we conduct a test on the normality of the data we retrieved, which is the focus of Table 5-5. Table 5-5. Test of Normality Shapiro-Wilk Statistics Internet Connection. Contract Management. 0.965. 23. 0.568. PCA (n=31). 0.936. 31. 0.065. Non-PCA (n=23). 0.965. 23. 0.561. 治 31 政 0.958 大. 0.257. 立. (n=31). 0.936. 23. 0.148. PCA (n=31). 0.956. 31. 0.231. ‧. Non-PCA (n=23). 學. ‧ 國. Sig.. Non-PCA (n=23). PCA IT Staff Training. Df. n. al. er. io. sit. y. Nat. In Table 5-5, we use Shapiro and Wilk's W test, which is a powerful procedure for detecting normality (Royston, 1983). As a test of the normality of samples, the W statistic may be used to test normality among small samples, and it may be difficult to determine the percentage points of the distribution of a larger sample size (Shapiro and Wilk, 1965). In addition, Shapiro and Wilk’s W test rejects the null hypothesis of normality at the 0.05 level, which means that normal distribution exists when the significance number is larger than 0.05. In table 5-5, we refer to companies not using public clouds as Non-PCAs and using them as PCAs. All of the numbers in the sig. column in Table 5-5 are greater than 0.05, which assures us of the normality of our data. Second, we use the descriptive statistics function in the SPSS software to attempt to discover any abnormalities in our data. The results are shown in Table 5-6, which includes N as the category number, mean value, standard deviation, standard error, and minimum and maximum numbers.. Ch. engchi. 32. i n U. v.
(40) Table 5-6. Results of Descriptive Statistics. N Internet. Mean. Standard. Standard. Deviation. Error. Minimum. Maximum. Non-PCA. 23. 4.507. 1.3100. 0.2731. 1.0. 7.0. PCA. 31. 4.430. 1.0191. 0.1830. 2.0. 6.0. Sum. 54. 4.463. 1.1409. 0.1553. 1.0. 7.0. Non-PCA. 23. 4.594. 1.0210. 0.2129. 2.8. 7.0. PCA. 31. 4.371. 1.0910. 0.1959. 1.8. 6.0. Sum. 54. 4.466. 1.0578. 0.1439. 1.8. 7.0. IT Staff. Non-PCA. 23. 4.522. 2.0. 6.5. Training. PCA. 31. 1.0. 7.0. Sum. 54. 1.0604 0.2211 治 政 1.4367 大0.2580 4.274. 1.0. 7.0. Connection. Contract. 立. 4.380. 1.2847. 0.1748. 學. ‧ 國. Management. By scrutinizing the numbers in Table 5-6, we can observe that all of the mean values are approximately 4 and that the decimal portion of the number fluctuates.. ‧. However, the standard deviation numbers for all factors are higher than 1. In statistics,. n. al. er. io. sit. y. Nat. we usually use the 68-95-99.7 rule to estimate the range of a normally distributed sample. This rule is also known as the three-sigma rule, which suggests that all values of a sample lie within the range of three times the number of its standard deviation from the mean value in a normal distribution. According to this rule, if we multiply a random standard deviation number in Table 5-6 by 3 and add it to its mean value and then designate the calculated number X, we can obtain an X larger than 7. Because we designed our questionnaire using a 7-point Likert Scale, X values larger than 7 are not usual. We can arrive at the conclusion that the variation in our data is considerable, which could be the cause of the insignificance in the results of our analysis.. Ch. engchi. i n U. v. (3) Current User Attitudes toward cloud computing i.. Excessive Reliance of Public Cloud Users. According to a survey regarding cloud computing conducted by TechSoup Global, a nonprofit organization, a lack of training in a company ranks high among the factors that hinder companies’ adoption of cloud computing. In addition to training issues, the willingness of companies to outsource public clouds to a third party is corroborated by other evidence that indicates that additional expenses and unfamiliarity with cloud computing also drive companies to turn to a third party 33.
數據

相關文件
6 《中論·觀因緣品》,《佛藏要籍選刊》第 9 冊,上海古籍出版社 1994 年版,第 1
Then, it is easy to see that there are 9 problems for which the iterative numbers of the algorithm using ψ α,θ,p in the case of θ = 1 and p = 3 are less than the one of the
It is the author’s hope that the Zuting shiyuan may be effectively used as a supplement for understanding Chan texts, and its contributions be fully valued.. Furthermore, the
Continue to serve as statements of curriculum intentions setting out more precisely student achievement as a result of the curriculum.
A Cloud Computing platform supports redundant, self-recovering, highly scalable programming models that allow workloads to highly scalable programming models that allow workloads to
Provide all public sector schools with Wi-Fi coverage to enhance learning through the use of mobile computing devices, in preparation for the launch of the fourth IT in
Provide all public sector schools with Wi-Fi coverage to enhance learning through the use of mobile computing devices, in preparation for the launch of the fourth IT in
• A formal usage policy and procedures should be in place, and appropriate security measures should be adopted to protect against the risks of using mobile computing and