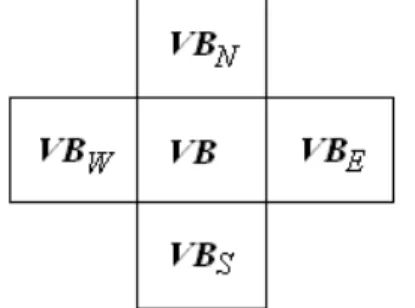1
An ROI-Based Medical Image Tamper Detection and
Recovery Scheme
SHU-CHIEN HUANG(黃樹乾) Department of Computer Science National Pingtung University of Education
Pingtung City, Taiwan schuang@mail.npue.edu.tw
ABSTRACT
In this paper, a tamper detection and recovery scheme for medical images is proposed. First we choose the region of interest (ROI). An ROI is an important region for diagnosis in medical images, and it needs to be protected especially. Then, the authentication and recovery data are embedded into the pixels of some blocks outside the ROI in order to obtain the watermarked image. By authentication extraction, we can determine whether or not the watermarked image has been tampered with. When the ROI has been tampered with, we can automatically localize the altered region, and recover the original ROI image with distortion that is imperceptible to the human eye. Moreover, watermarked images based on our proposed method have high visual quality. Experimental results are given to show the effectiveness of the proposed scheme.
Keywords: tamper detection, tamper recovery, fragile watermarking, ROI protection,
medical image authentication
1. Introduction
2
Watermarked-based methods embed invisible information into the media. The embedded watermark can be extracted and used for verification.
Several watermarked-based image authentication schemes have been proposed. In general, those schemes can be divided into two types: fragile authentication and semi-fragile authentication. Fragile authentication schemes are developed to identify any changes to the image pixels. However, semi-fragile authentication can tolerate non-noticeable modifications caused by digital image processing, such as undergoing lossy compression. In this paper, we focus on fragile authentication techniques.
A1-Qershi et al. [16] presented a hybrid watermarking scheme for DICOM images. In their method, a patient’s data are embedded into the region of interest using a reversible technique based on difference expansions, while tamper detection and recovery data are embedded into the region of non-interest using a robust technique based on discrete wavelet transformation. However, the size of the image must be at least 512×512 pixels in order to allow tamper localization and recovery capabilities in their method. For smaller images, their algorithm can be applied but without the recovery facility as there will not be enough space to embed the compressed form of the region of interest.
In this paper, we propose a fragile authentication scheme for medical images. The physician specifies the ROI before embedding information. A data hiding scheme is proposed to protect the ROI. The details of the proposed method are explained in Section 2. Section 3 demonstrates the experimental results. Finally, we conclude this paper in Section 4.
2. Proposed Method
For a medical image, divide it into many non-overlapping blocks. A block size is 8×8. Assume the image size is 512×512. A total of (512×512)/(8×8)=4096 blocks, denoted by B0, B1,…,B4095, are generated.
2.1. Region of interest (ROI). A physician could choose the ROI in the image. In this
proposed scheme, the ROI consists of one rectangular area, and the gray-level value of each pixel inside the ROI is kept unchanged during the watermarked image generation.
3
FIGURE 1. The image with the ROI selection.
2.2. Generating authentication data. For an 8×8 block Bi, the 2-tuple-watermark
(MV, NI) is computed as follows for the authentication data.
First, compute the mean value ME and the variance value VA using only the six most significant bits (MSBs) of all pixels within the block and generate the 8-bit authentication watermark MV by the following equation:
MV= floor(ME+VA) mod 28 . (1) The value of MV is between 0 and 255, and it takes 8 bits to store this value.
Then, the total number of 1s, denoted by N1, in the six MSBs of all pixels within the block is computed. The 8-bit authentication watermark NI is generated as in Eq. (2) below
NI=(i+N1) mod 28. (2) The value of NI is also between 0 and 255, and it takes 8 bits to store this value.
The authentication data of each block are the 2-tuple-watermark (MV, NI). It is obvious that 16 bits are required to store the authentication data.
2.3. Generating recovery data. For each block in the first block group, we further
divide it into 16 sub-blocks of 2×2 pixels. Figure 2 shows the block Bi and a
sub_block I. Compute the average intensity of sub-block I and denote it avg_I=floor((I1+I2+I3+I4)/4). The recovery intensity of sub_block I is obtained by
truncating the two LSBs in avg_I. Therefore, it takes 6 bits to store the recovery data of each sub_block. For the 16 sub-blocks, it takes 96 bits to store the recovery data of the block Bi.
(a) (b)
4
2.4. Watermarked image generation. In this section, we describe the embedding
method for the watermarked image generation.
For each bock in the second block group, the 16-bit authentication data (MV, NI) are embedded into the pixels within the current block, as shown in Fig. 3.
FIGURE 3. The 16-bit authentication data (MV, NI) are embedded.
The authentication and recovery data of the x-th block in the first block group are embedded into the pixels of the y-th block in the second block group, as shown in Fig. 4, where x∈[0, NB1-1] and y∈[0, NB2-1]. The total size of the authentication and recovery data is 112 bits. In the proposed scheme, a 1-D transformation [4] as shown in Eq. (3) is used to obtain a one-to-one mapping sequence.
y=(x × K) mod NB1, (3) where K is a prime and K∈Z-{NB1’s factors}. Note that the criteria NB2≥ NB1 must be satisfied in the proposed scheme.
5
2.5. Tamper detection.
For the y-th block in the second group (i.e., the block Bi in the image), the
procedure of our detection scheme is described as follows.
Step 1. Extract the corresponding 16 bits from the pixels within the current block, and obtain the authentication data (MV, NI).
Step 2. Only the six MSBs of each pixel within the block are used to compute the mean value ME, the variance value VA, and the total number of 1s N1.
Step 3. If (MV==(floor(ME+VA) mod 28)) and (NI==((i+N1) mod 28)), mark the block valid, otherwise mark it invalid.
After the tamper detection for each block in the second block group is finished, then determine whether the x-th block in the first block group (i.e., the block Bj in the
image) is tampered with or not. A 2-level hierarchical tamper detection algorithm is applied in our method.
Level-1 detection:
Step 1. Compute y=(x × K) mod NB1, if the y-th block in the second block group is valid, then go to Step 2; else go to Step 5.
Step 2. Extract the corresponding 16 bits from the pixels within the y-th block in the second block group in order to obtain the authentication data (MV, NI) of the x-th block in the first block group.
Step 3. Only the six MSBs of each pixel within the block are used to compute the mean value ME, the variance value VA, and the total number of 1s N1.
Step 4. If (MV==(floor(ME+VA) mod 28)) and (NI==((j+N1) mod 28)), mark the block valid, otherwise mark the block invalid. Go to Step 1 to detect whether the next block is tampered with or not.
Step 5. The method cannot determine whether the x-th block is tampered with or not, mark it with a specified color. Go to Step 1 to detect whether the next block is tampered with or not.
Level-2 detection: For each valid block VB, mark this block invalid if its four neighboring blocks VBE, VBW, VBS, and VBN, shown in Fig. 5, are all invalid.
FIGURE 5. The valid block VB and its four neighboring blocks VBE, VBW, VBS, and
6
2.6. Image recovery. If the x-th block in the first block group is invalid, perform the
following steps for recovery:
Step 1. Compute y=(x × K) mod NB1, if the y-th block in the second block group is valid, then go to Step 2.
Step 2. Extract the corresponding 96 bits from the pixels within the y-th block in the second block group in order to obtain the recovery data of the x-th block in the first block group. The 96 bits are then divided into 16 parts, and each part has 6-bit representative information.
Step 3. Pad two 0’s to the end of each 6-bit representative information to form a new 8-bit intensity. Replace each pixel in the corresponding 2×2 sub-block with the new 8-bit intensity.
Step 4. Go to Step 1 to recover the next invalid block.
3. Experimental Results
The proposed algorithm is implemented in C language on a Pentium IV PC using the operating system Microsoft Windows XP. The grayscale medical image, as shown in Fig. 6, is used for testing the ability of the tamper detection and recovery.
The experimental results are discussed in two aspects. One is the measurement of the watermarked image quality and the other is the ability to recover the ROI. In the experiment,the peak signal-to-noise ratio (PSNR) is employed to measure the image quality. The PSNR of the original image O relative to watermarked image (or recovery image) G is defined as
∑∑
= = − × = × = M i N j j i j i G O N M MSE dB MSE PSNR 1 1 2 , , 2 10 , ) ( 1 , ) 255 ( log 10 (4)where the size of the original image is M×N.
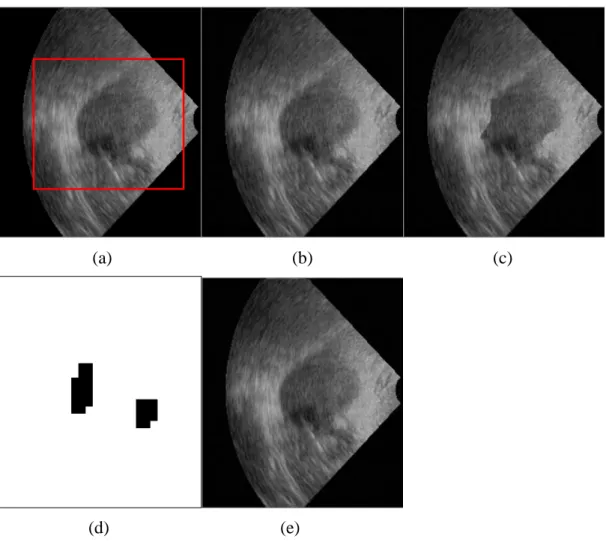
Figure 7(a) is an ultrasound image with the ROI selection. The image is 256×224 (8 bits/pixel) in size. The ROI consists of one rectangular area. The values of NB1 and NB2 are 418 and 478, respectively. The watermarked image is shown in Fig. 7(b). The PSNR value of this watermarked image is 44.72 dB. The tampered image, as shown in Fig. 7(c), is obtained from the watermarked image by adding a tumor-like feature.
The tamper detection result is shown in Fig. 7(d). The experiment reveals that the ability of the proposed method to detect tampering is adequate. Fig. 7(e) shows the recovered image. The value of PSNR is 41.33 dB.
7 unchanged.
FIGURE 6. the ovarian ultrasound image, size 256×224.
(a) (b) (c)
(d) (e)
FIGURE 7. (a) Original image with the ROI selection, (b) watermarked image, (c) tampered image, (d) tamper detection result, (e) recovered image.
4. Conclusion
8
watermarking scheme for medical image tamper detection and recovery has been proposed. First, the ROI is selected, and the authentication and recovery data of each block inside the ROI are embedded into the blocks outside the ROI for tamper detection and recovery usage. When each block inside the ROI is tampered with, the approximate image can be recovered from the information embedded in other blocks. The quality of every watermarked image is high, in that it is greater than 44 dB for every original image. The experimental results show that the positions of the tampered areas are marked correctly and the recovered image is visually indistinguishable from the original image. In conclusion, the proposed scheme is simple and effective for medical image authentication and recovery.
REFERENCES
[1] F. Cao, H. K. Huang and X. Q. Zhou, Medical image security in a HIPAA mandated PACS environment, Computerized medical imaging and graphics, vol.27, no.2-3, pp.185-196, 2003.
[2] N. A. Memon and S. A. M. Gilani, Watermarking of chest CT scan medical images for content authentication, International Journal of Computer Mathematics, vol.88, no.2, pp.265-280, 2011.
[3] C. Y. Lien, T. Kao, C. H. Hsiao and C. I. Keng, A software-embedded method of security protection applied in indirect imaging in dentistry, Journal of Medical and Biological Engineering, vol.30, no.4, pp.203-207, 2010.
[4] P. L. Lin, C. K. Hsieh and P. W. Huang, A hierarchical digital watermarking method for image tamper detection and recovery, Pattern Recognition, vol.38, no.12, pp.2519-2529, 2005.
[5] C. C. Chang, Y. S. Hu and T. C. Lu, A watermarking-based image ownership and tampering authentication scheme, Pattern Recognition Letters, vol.27, no.5, pp.439-446, 2006.
[6] W. C. Chen and M. S. Wang, A fuzzy c-means clustering-based fragile watermarking scheme for image authentication, Expert Systems with Applications, vol.36, no.2, pp.1300-1307, 2009.
[7] M. U. Celik, G. Sharma, E. Saber and A. M. Tekalp, Hierarchical watermarking for secure image authentication with localization, IEEE Transactions on Image Processing, vol.11, no.6, pp.585-594, 2002.
[8] T. Y. Lee and S. D. Lin, Dual watermark for image tamper detection and recovery, Pattern Recognition, vol.41, no.11, pp.3497-3506, 2008.
[9] C. S. Chan and C. C. Chang, An efficient image authentication method based on hamming code, Pattern Recognition, vol.40, no.2, pp.681-690, 2007.
9
medical images with tamper localization, Journal of digital imaging, vol.22, no.6, pp.620-628, 2009.
[11] C. H. Lin, Y. C. Li, H. F. Chien and S. L. Chien, Multipurpose image authentication method based on vector quantization, International Journal of Innovative Computing, Information and Control, vol.6, no.3(B), pp.1435-1446, 2010.
[12] S. S. Wang and S. L. Tsai, Automatic image authentication and recovery using fractal code embedding and image inpainting, Pattern Recognition, vol.41, no.2, pp.701-712, 2008.
[13] P. W. Wong and N. Memon, Secret and public key image watermarking schemes for image authentication and ownership verification, IEEE Transactions on Image Processing, vol.10, no.10, pp.1593-1601, 2001.
[14] M. U. Celik, G. Sharma and A. M. Tekalp, Lossless watermarking for image authentication: a new framework and an implementation, IEEE Transactions on Image Processing, vol.15, no.4, pp.1042-1049, 2006.
[15] R. Chamlawi, A. Khan and I. Usman, Authentication and recovery of images using multiple watermarks, Computers and Electrical Engineering, vol.36, no.3, pp.578-584, 2010.
[16] O. M. A1-Qershi and B. E. Khoo, Authentication and data hiding using a hybrid ROI-based watermarking scheme for DICOM images, Journal of digital imaging, vol.24, no.1, pp.114-126, 2011.
[17] S. Han, M. Fujiyoshi and H. Kiya, An efficient reversible image authentication method, IEICE Transactions on Fundamentals, vol.E91-A, no.8, pp.1907-1914, 2008.