Transactions Papers
Credit Pre-Reservation Mechanism for
UMTS Prepaid Service
Hsin-Yi Lee and Yi-Bing Lin, Fellow, IEEE
Abstract—Online Charging System (OCS) supports multiple
prepaid and postpaid sessions simultaneously. Through credit reservation, the OCS assigns some credit units to a session. These credit units are decremented based on the traffic volume or the duration time. If the assigned credit units are consumed before the session is completed, an reserve units (RU) operation is executed to obtain more credit units from the OCS. If the credit at the OCS is depleted, the prepaid session is forced to terminate. During the RU operation, packet delivery is suspended until extra credit units are granted from the OCS. To avoid session suspension during credit reservation, we propose the credit
pre-reservation mechanism (CPM) that reserves credit earlier
before the credit at the GGSN is actually depleted. Analysis and simulation experiments are conducted to investigate the performance of the mechanism. Our study indicates that the CPM can significantly improve the performance of the OCS prepaid mechanism.
Index Terms—Credit reservation, diameter protocol, online
charging, prepaid service, Universal Mobile Telecommunications System (UMTS).
I. INTRODUCTION
P
RICING, charging and billing are important activities in telecommunications [1], [2], [3]. Advanced mobile telecommunications operation incorporates data applications (specifically, mobile Internet applications [4], [5]) with real-time control and management, which can be archived by a convergent and flexible Online Charging System (OCS) [6], [7], [8]. Such convergence is essential to mitigate fraud and credit risks, and provide more personalized advice to users about charges and credit limit controls. The OCS allows simultaneous prepaid and postpaid sessions to be charged in real-time. This feature is important for a telecom operator to deliver multiple sessions simultaneously. Through online charging, the operator can ensure that credit limits are enforced and resources are authorized on a per-transaction basis.Manuscript received March 8, 2008; accepted May 14, 2008. The associate editor coordinating the review of this paper and approving it for publication was M. Guizani.
The authors are with the Department of Computer Science, Na-tional Chiao-Tung University, Hsinchu, Taiwan, R.O.C. (e-mail: hsinyi, liny@csie.nctu.edu.tw).
This work was supported in part by NSC 97-2221-E-009-143-MY3, NSC 98-2221-E-009-059-MY2, NSC 98-2219-E-009-016-, Intel, Chunghwa Tele-com, IBM, ITRI and NCTU joint research center, and MoE ATU plan.
Digital Object Identifier 10.1109/TWC.2010.06.080342
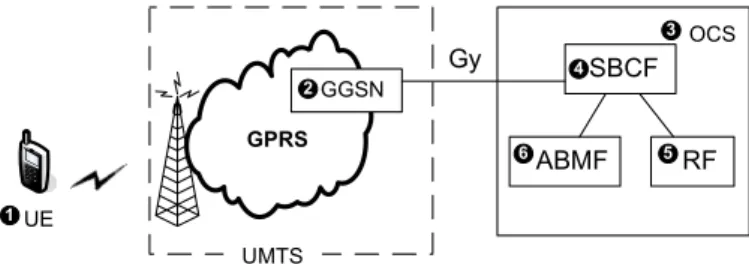
GPRS GGSN 2 UE UMTS SBCF ABMF RF Gy OCS 1 3 4 5 6
Fig. 1. OCS architecture for mobile telecommunications services.
By merging the prepaid and postpaid methods, the OCS proposed in Universal Mobile Telecommunications System (UMTS) provides two-way communications between network nodes and the OCS to transfer information about rating, billing and accounting. Fig. 1 illustrates how UMTS integrates with the OCS [9]. When a User Equipment (UE; Fig. 1 (1)) originates a prepaid session through the General Packet Radio Service (GPRS), the Gateway GPRS Support Node (GGSN; Fig. 1 (2)) requests the prepaid credit from the OCS (Fig. 1 (3)) through the Gy interface.
In the OCS, the Session Based Charging Function (SBCF; Fig. 1 (4)) module is responsible for online charging of user sessions. The SBCF interacts with the Rating Function (Fig. 1 (5)) to determine the tariff of the requested session. The rating function handles a wide variety of ratable instances, such as data volume, session connection time, and event service (e.g., for web content charging). The SBCF also interacts with the Account Balance Management Function (ABMF; Fig. 1 (6)) for credit control. The ABMF maintains user balances and other account data to check if the users have enough credit. The SBCF assigns some prepaid credit units to the GGSN for a user session. These credit units are decremented at the GGSN in real-time based on either the traffic volume or the duration time. After the assigned credit units are consumed, the GGSN may execute a reserve units (RU) operation to ask for more credit from the OCS. If the credit of the user account at the OCS is depleted, the prepaid session is forced to terminate. During the RU operation, packet delivery is suspended until extra credit units are granted from the OCS. To avoid suspension of packet delivery, we propose the credit pre-reservation mechanism (CPM) that reserves extra credit earlier 1536-1276/10$25.00 c⃝ 2010 IEEE
OCS 1. CCR (INITIAL_REQUEST) 2.CCA (INITIAL_REQUEST) GGSN 6. CCR (TERMINATE_REQUEST) 7. CCA (TERMINATE_REQUEST) 4. CCR (UPDATE_REQUEST) 5. CCA (UPDATE_REQUEST) 3. User Packet Delivery until c = 0
User Packet Delivery until the Last Packet of the Session Is Processed Service Suspension Service Resumption RU Oper at io n
Fig. 2. Message flow of the diameter credit control mechanism.
before the credit units at the GGSN are actually depleted. The paper is organized as follows. Section 2 describes the Diameter credit control mechanism exercised at the Gy interface. Section 3 proposes the CPM. Section 4 develops an analytical model for the CPM. Section 5 uses numerical examples to investigate the performance of the CPM. Section 6 gives our conclusions.
II. DIAMETERCREDITCONTROLMECHANISM In online charging services, credit control is achieved by ex-changing Diameter Credit Control Request (CCR) and Credit Control Answer (CCA) messages through the Gy interface defined between the GGSN and the OCS [10]. The message flow of the online charging is illustrated in Fig. 2 with the following Steps:
Step 1. To initiate the service session, the GGSN sends a CCR message with type INITIAL REQUEST to the OCS.
Step 2. Through the interactions among the SBCF, the ABMF and the RF, the OCS determines the tariff of the requested service session and then reserves the amount𝜃 of credit units for the service session if the credit balance 𝐶𝑟 at
the OCS is no less than 𝜃 (i.e., 𝐶𝑟≥ 𝜃). Then the OCS
returns a CCA message with type INITIAL REQUEST to the GGSN. This message indicates the amount 𝜃 of granted credit to the session.
Step 3. After receiving the CCA message, the GGSN starts to deliver the user packets. Let 𝑐 be the amount of the remaining credit of the service session. This credit is decremented at the GGSN. At the beginning of this Step, 𝑐 = 𝜃. During the session, the granted credit units may be depleted (i.e., 𝑐 = 0). If so, the session is suspended and Step 4 is executed.
Step 4. The GGSN sends a CCR message with type UP-DATE REQUEST to the OCS to report the used credit units and request for additional credit units. Packet
Steps 6 and 7
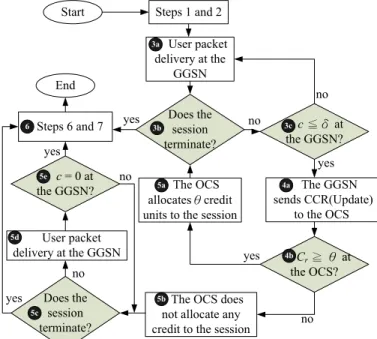
The OCS does not allocate any credit to the session yes End Does the session terminate? c = 0 at the GGSN? yes yes no no The OCS allocatesθcredit units to the session User packet delivery at the GGSN Start User packet delivery at the GGSN Does the session terminate? c≦δ at the GGSN? no yes yes The GGSN sends CCR(Update) to the OCS Cr≧ θ at the OCS? no no Steps 1 and 2 6 3a 3b 3c 4a 4b 5a 5b 5c 5d 5e
Fig. 3. Flowchart of the CPM (steps 1, 2, 6, and 7 are the same as those in the diameter credit control mechanism).
livery is suspended, and any newly arriving packets are buffered at the GGSN.
Step 5. The OCS deducts the amount of used credit from the user account and reserves extra amount 𝜃 of credit units for the session. Then the OCS acknowledges the GGSN with a CCA message to indicate that𝜃 credit units have been reserved. The session is resumed at the GGSN and the buffered packets are delivered. Note that Steps 3 - 5 may repeat many times before the service session is complete. At Steps 2 and 4, if 𝐶𝑟 < 𝜃 at the OCS,
then the session is forced to terminate. For the discussion purpose, Steps 4 and 5 are called an RU operation. Step 6. When the session is completed, the GGSN sends
a CCR message with type TERMINATE REQUEST to terminate the session and report the amount of used credit.
Step 7. The OCS deducts the amount of the used credit from the account. Then the OCS acknowledges the reception of the CCR message by sending a CCA message with type TERMINATE REQUEST.
In the above procedure, when the credit units are depleted at the GGSN, an RU operation is executed to request for addi-tional credit units. The session must be suspended until extra credit units are granted from the OCS. Delayed processing of user packets at the GGSN may seriously degrade the quality of service. To resolve this issue, we propose the credit pre-reservation mechanism in the next section.
III. CREDITPRE-RESERVATIONMECHANISM In the credit pre-reservation mechanism (CPM), we define a threshold𝛿. When the amount 𝑐 of the remaining credit for the session is not larger than𝛿 (i.e., 𝑐 ≤ 𝛿), the GGSN conducts an RU operation to request extra credit from the OCS. During the RU operation, the GGSN continues to process the user packets. Hopefully, the GGSN will receive the extra amount𝜃 of credit
units before𝑐 = 0, and therefore the user packets need not be buffered (i.e., they are not suspended for processing) at the GGSN. Fig. 3 illustrates the flowchart of CPM, which modifies Steps 3-5 in Fig. 2 as follows:
Step 3a. The GGSN delivers the user packets and deducts the reserved credit units.
Step 3b. If the processed packet is the last one of the service session, then Step 6 is executed to terminate the session (the session is successfully completed). Otherwise, the execution proceeds to Step 3c.
Step 3c. Let 𝛿 be the CPM threshold. If 𝑐 ≤ 𝛿, Step 4a is
executed. Otherwise, the execution proceeds to Step 3a. Step 4a. The GGSN sends a CCR message with type
UP-DATE REQUEST to request for additional credit. During the RU operation, if𝑐 > 0, the user packets are continu-ously delivered at the GGSN. When𝑐 = 0, the session is suspended and the newly arriving packets are buffered. Step 4b. If the OCS does not have enough credit units (i.e.,
𝐶𝑟 < 𝜃), Step 5b is executed. Otherwise, Step 5a is
executed.
Step 5a. The OCS sends the CCA message to the GGSN to indicate that extra amount 𝜃 of credit units have been reserved for the session. Then the execution proceeds to Step 3b. If the last packet arrives during the RU operation, the termination operation (Steps 3b and 6) is executed after the GGSN has received the CCA message. (This is called delayed termination) In this case, the session is successfully completed.
Step 5b. The OCS sends the CCA message to the GGSN. This message indicates that no credit is reserved for the session.
Step 5c. If the previously processed packet is the last one of the session, then the session is successfully completed. Step 6 is executed.
Step 5d. The GGSN continues to deliver the user packets. Step 5e. If𝑐 = 0, then the session is forced to terminate, and
Step 6 is executed. Otherwise, the execution proceeds to Step 5c.
Step 6. The session terminates by executing Steps 6 and 7 in Fig. 2.
In the CPM, if 𝛿 is set too small, then the credit units for a session are likely to be depleted and the session must be suspended during the RU operation. On the other hand, if𝛿 is set too large, many credit units are reserved in the active sessions, and the credit in the OCS is consumed fast. In this case, an incoming session has less chance to be served, and an in-progress session is likely to be force-terminated. Therefore, it is important to select an appropriate𝛿 value to “optimize” the CPM performance.
IV. ANALYTICMODEL FOR THECPM
We describe an analytic model to investigate the CPM performance. We assume that the prepaid session arrivals for a user form a Poisson process with rate𝛾. The inter-arrival time between two packet arrivals has the mean 1/𝜆. The round-trip transmission delay for the RU operation (i.e., the round-trip message delay for the CCR and CCA message pair) has the mean 1/𝜇. An arrival packet is the last one of the session
with probability 𝛼; in other words, the session continues with probability1 − 𝛼, and the expected number of packets delivered in a session is 1/𝛼.
Initially, a user has 𝐶 credit units at the prepaid account in the OCS. Without loss of generality, we assume that each user packet consumes one credit unit. Define a low credit (LC) period as an interval such that during this interval,𝑐 ≤ 𝛿 for a session. At the beginning of an LC period, the session initiates an RU operation. If more than𝜃 packets arrive during this RU operation, then𝜃 − 𝛿 packets will be buffered at the GGSN. Consequently, at the end of the RU operation, another RU operation must be issued to obtain more credit units to absorb the buffered packets and to ensure that 𝑐 > 𝛿 after the buffer is empty. Before an LC period ends, the RU operation may be executed for several times until the session has reserved more than 𝛿 credit units. The output measures investigated in our study are listed below.
𝐵: the average number of packets buffered during an RU operation
𝑊 : the average packet waiting time
𝑃𝑟: the probability that during an LC period, two or more RU
operations are executed
𝑃𝑛𝑐: the probability that a session is not completely served;
i.e., the probability that a new session request is blocked or an in-progress session is forced to terminate
𝑋𝑠: the average number of the RU operations performed in
a session
To derive 𝑃𝑟 and 𝐵, we first consider the case where 𝛼 =
0; i.e., a session is never terminated. Let 𝐾 be the number of packets arriving in one RU operation (excluding the first packet arrival that triggers the RU operation). It is clear that
𝑃𝑟= Pr[𝐾 ≥ 𝜃] (1)
We assume that an RU operation delay has the Erlang density function 𝑓(𝑡) with the shape parameter 𝑏 = 2 and the scale parameter ℎ = 1/𝜇. (I.e., 𝑡 is the summation of two Exponential delays. This assumption will be relaxed, and more general distributions will be considered in the simulation model.) Therefore the Laplace-Stieltjes Transform𝑓∗(𝑠) of the
RU operation delay is 𝑓∗(𝑠) = ( 𝜇 𝜇 + 𝑠 )2 (2) For 𝛼 = 0, the probability that 𝐾 = 𝑘 can be calculated as follows: Pr[𝐾 = 𝑘, 𝛼 = 0] = ∫ ∞ 𝑡=0 [ (𝜆𝑡)𝑘 𝑘! ] 𝑒−𝜆𝑡𝑓(𝑡)𝑑𝑡 (3) = ( 𝜆𝑘 𝑘! ) ∫ ∞ 𝑡=0𝑡 𝑘𝑒−𝜆𝑡𝑓(𝑡)𝑑𝑡 (4) = ( 𝜆𝑘 𝑘! ) (−1)𝑘 [ 𝑑𝑘𝑓∗(𝑠) 𝑑𝑠𝑘 ] 𝑠=𝜆 (5) = ( 𝜆𝑘 𝑘! ) (−1)𝑘 [ 𝑑𝑘 𝑑𝑠𝑘 ( 𝜇 𝜇 + 𝑠 )2] 𝑠=𝜆 (6) = 𝜆𝑘(𝑘 + 1)𝜇2 (𝜆 + 𝜇)𝑘+2 (7)
In (3), the RU operation delay is 𝑡 with the probability 𝑓(𝑡)𝑑𝑡. During period 𝑡, there are 𝑘 packet arrivals following the Poisson distribution with the rate𝜆. Eq. (5) is derived from (4) using Rule P.1.1.9 in [11]. Substitute (2) in (5), we obtain (7).
Now we consider the case when 𝛼 ≥ 0. If a session is terminated during an RU operation,Pr[𝐾 = 𝑘] is derived by considering the following cases:
(I) When𝑘 = 0, we have Pr[𝐾 = 0] = Pr[𝐾 = 0, 𝛼 = 0]
(II) When𝑘 > 0, there are two subcases:
(IIa) There are exactly 𝑘 packet arrivals during an RU
operation (with probability Pr[𝐾 = 𝑘, 𝛼 = 0]) and the session is not terminated by any of the first𝑘 − 1 packets (with the probability (1 − 𝛼)𝑘−1). Note that the 𝑘-th packet can be the last one of the session.
(IIb) There are more than 𝑘 packet arrivals during an
RU operation if the session is never terminated (with probability ∑∞𝑖=𝑘+1Pr[𝐾 = 𝑖, 𝛼 = 0]), and the ses-sion is actually terminated at the 𝑘-th packet arrival (with probability(1 − 𝛼)𝑘−1𝛼).
Based on the above cases,Pr[𝐾 = 𝑘] is derived as Pr[𝐾 = 𝑘] = Pr[𝐾 = 0, 𝛼 = 0] , k=0 (8) ⎧ ⎨ ⎩Pr[𝐾 = 𝑘, 𝛼 = 0] (1 − 𝛼)𝑘−1 + ∞ ∑ 𝑖=𝑘+1 Pr[𝐾 = 𝑖, 𝛼 = 0] (1 − 𝛼)𝑘−1𝛼, k>0 (9) From (7), (8) can be derived as
Pr[𝐾 = 0] = ( 𝜇 𝜆 + 𝜇 )2 (10) For𝑘 > 0, Eq. (9) is simplified as
Pr[𝐾 = 𝑘] = [ 𝜆𝑘(𝑘 + 1)𝜇2 (𝜆 + 𝜇)𝑘+2 ] (1 − 𝛼)𝑘−1 + ∞ ∑ 𝑖=𝑘+1 [ 𝜆𝑖(𝑖 + 1)𝜇2 (𝜆 + 𝜇)𝑖+2 ] (1 − 𝛼)𝑘−1𝛼 = [ (1 − 𝛼)𝑘−1𝜆𝑘 (𝜆 + 𝜇)𝑘+2 ] { (𝑘 + 1)𝜇2+ 𝛼𝜆 [(𝑘 + 2)𝜇 + 𝜆]} (11) When𝜃 > 0, from (1) and (11), 𝑃𝑟 is derived as
𝑃𝑟= Pr[𝐾 ≥ 𝜃] = ∞ ∑ 𝑘=𝜃 [ (1 − 𝛼)𝑘−1𝜆𝑘 (𝜆 + 𝜇)𝑘+2 ] { (𝑘 + 1)𝜇2+ 𝛼𝜆 [(𝑘 + 2)𝜇 + 𝜆]} = [ 𝜆𝜃(1 − 𝛼)𝜃−1 (𝜆 + 𝜇)𝜃+1 ] [𝜇(𝜃 + 1) + 𝜆] (12) When𝜃 = 0, 𝑃𝑟= Pr[𝐾 ≥ 0] = ( 𝜇 𝜇 + 𝜆 )2 +∑∞ 𝑘=1 Pr[𝐾 ≥ 𝑘] = 1 (13) The expected number 𝐵 of buffered packets is derived as follows: When the number𝑘 (of packet arrivals during an RU
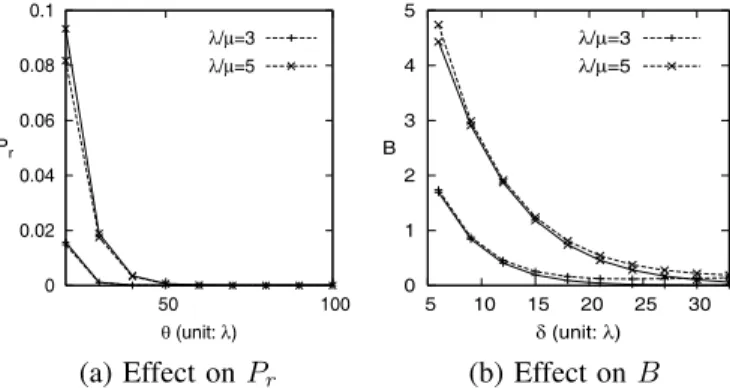
0 0.02 0.04 0.06 0.08 0.1 50 100 θ (unit: λ) Pr λ/μ=3 λ/μ=5 0 1 2 3 4 5 5 10 15 20 25 30 δ (unit: λ) B λ/μ=3 λ/μ=5
(a) Effect on 𝑃𝑟 (b) Effect on𝐵
Fig. 4. Validation of simulation and analytical results on𝑃𝑟and𝐵 (𝛼 = 0.01, 𝛾/𝜇 = 1/20, and 𝛿 = 0.3𝜃; solid curves: analytic results; dashed curves: simulation results).
operation) is no less than the threshold 𝛿 (i.e., 𝑘 ≥ 𝛿), the session will have𝑘 − 𝛿 buffered packets. Therefore, from (11)
𝐵 =∑∞ 𝑘=𝛿 (𝑘 − 𝛿) Pr[𝐾 = 𝑘] = ∞ ∑ 𝑘=𝛿 (𝑘 − 𝛿) [ (1 − 𝛼)𝑘−1𝜆𝑘 (𝜆 + 𝜇)𝑘+2 ] { (𝑘 + 1)𝜇2+ 𝛼𝜆 [(𝑘 + 2)𝜇 + 𝜆]} = [ (1 − 𝛼) 𝜆 𝜆 + 𝜇 ]𝛿+1 [ 𝛿𝜇2+ 𝛼𝛿𝜆𝜇 + 2𝜇2+ 2𝜆𝜇 + 𝛼𝜆𝜇 + 𝛼𝜆2 (1 − 𝛼) (𝜇 + 𝛼𝜆)2 ] (14) The purpose of the analytic model is two folds: First, it partially verifies that the simulation model is correct. Second, it sheds light on the effects of the input parameters on𝑃𝑟and
𝐵. Our simulation model is based on an event-driven approach widely adopted in mobile network studies [12], and the details are elaborated in [13].
Eqs. (12) and (14) validate against the simulation experi-ments as illustrated in Fig. 4. In this figure, the dashed curves represent the simulation results, and the solid curves represent the analytical results. These curves indicate that the analytic and the simulation results are consistent.
V. NUMERICALEXAMPLES
This section uses numerical examples to investigate the performance of the CPM. For the presentation purpose, we assume that the packet termination probability is𝛼 = 0.01 and the session arrival rate (normalized by the message delivery rate) is 𝛾 = 𝜇/20. For other 𝛼 and 𝛾/𝜇 values, we observe similar results, which are not presented in this paper. In Figs. 4 and 5, the packet arrivals in a session have a Possion distri-bution and the RU operation delay has an Erlang distridistri-bution. These Expontial-like assumptions are relaxed in Figs. 6 and 7 by considering the Pareto and the Gamma distributions. The effects of the input parameters𝜆/𝜇, C, 𝜃 and 𝛿 are described as follows.
Effects on𝑃𝑟. Fig. 4 (a) shows how𝑃𝑟 is affected by𝜃 and
𝜆/𝜇. From (12) and (13), we have lim
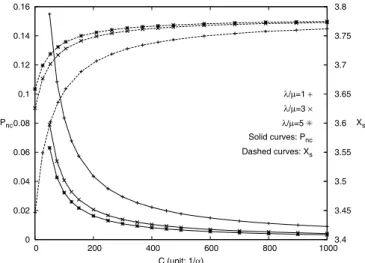
0 0.02 0.04 0.06 0.08 0.1 0.12 0.14 0.16 0 200 400 600 800 1000 3.4 3.45 3.5 3.55 3.6 3.65 3.7 3.75 3.8 C (unit: 1/α) Pnc Xs λ/μ=1 + λ/μ=3 × λ/μ=5 6 Solid curves: Pnc Dashed curves: Xs
Fig. 5. Effects of𝜆/𝜇 and C on 𝑃𝑛𝑐and𝑋𝑠 (𝛼=0.01,𝛾/𝜇=1/20, 𝛿=0.3𝜃, and𝜃=50𝜆).
Therefore, it is obvious that 𝑃𝑟 is a decreasing function
of𝜃.
When𝜆/𝜇 is very small or vary large, we have lim
𝜆/𝜇→0𝑃𝑟= (1 − 𝛼)
𝜃−1 and lim
𝜆/𝜇→∞𝑃𝑟= 0 (16)
When 𝜆/𝜇 increases, more packets arrive during an RU operation. When more than𝜃+𝛿 packets arrive during one RU operation, an extra RU operation will be immediately executed. Consequently,𝑃𝑟increases. Therefore𝑃𝑟is an
increasing function of 𝜆/𝜇.
Effects of𝜆/𝜇. Fig. 4 (b) shows that 𝐵 is increasing
func-tions of𝜆/𝜇. From (14), we have lim
𝜆/𝜇→0𝐵 = 0 and 𝜆/𝜇→∞lim 𝐵 =
(1 − 𝛼)𝛿
𝛼 (17)
When𝜆/𝜇 increases, it is likely that more than 𝛿 packets will arrive during the interval of the RU operation. Note that 𝑊 positively co-relates with 𝐵. Therefore both 𝐵 and𝑊 increase as 𝜆/𝜇 increases.
When 𝜆/𝜇 → ∞, we found that the 𝐵 value in (17) is higher than the simulation result (not shown in this Figure), which is explained as follows: When𝜆/𝜇 → ∞, all packets for a session will arrive before the end of the first RU operation, and therefore the 𝐵 value in (17) is determined by 𝛼. In simulation, the session is always in the “low-credit” status (in the LC period), and every time an RU operation is performed, the number of buffered packets at the end of the operation is reduced. Therefore the expected value𝐵 is smaller than that shown in (17). To avoid buffer overflow, the 𝐵 value in (17) should be considered in system setup.
Fig. 5 shows that𝑃𝑛𝑐increases as 𝜆/𝜇 decreases. Since
𝛼 is fixed, when 𝜆/𝜇 decreases, the session holding times become longer, and it is likely that more new sessions will arrive during the holding time of an existing session. Therefore, when 𝜆/𝜇 decreases, more sessions will exist at the same time. Suppose that the credit in the OCS suffices to support these sessions if they are sequentially delivered. It is clearly that the OCS may not
be able to support these sessions if they are delivered simultaneously. In this case, a newly incoming session is rejected because the credit in the OCS is depleted (while there are unused credit units held in the multiple in-progress sessions). Therefore, 𝑃𝑛𝑐 increases as 𝜆/𝜇
decreases.
In Fig. 5,𝑋𝑠is a decreasing function of𝑃𝑛𝑐because the
number of RU operations performed in a force-terminated session is less than that in a complete session. Therefore, 𝑋𝑠 increases as 𝜆/𝜇 increases.
Effects of C. Fig. 5 shows that the output measures (𝑃𝑛𝑐and
𝑋𝑠) are only affected by the “end effect” of 𝐶. As 𝐶
increases, it is more likely that the remaining credit units in the OCS suffice to support one RU operation and such end effect becomes insignificant. Similar to the𝜆/𝜇 impact,𝑃𝑛𝑐 is a decreasing function of C, and𝑋𝑠 is an
increasing function of C. Fig. 5 indicates that when C is sufficiently large (e.g. 𝐶 ≥ 600/𝛼), the end effect of 𝐶 can be ignored. Same phenomenon is observed for 𝐵 and𝑊 , and the results are not shown.
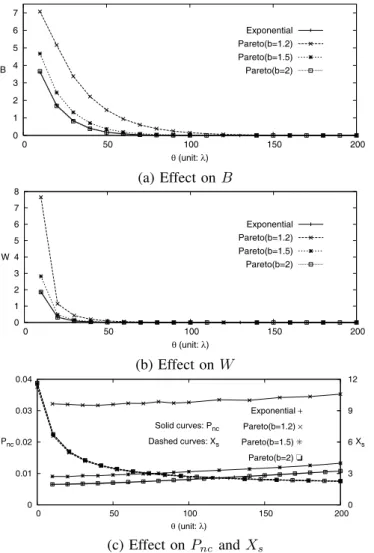
Effects of 𝜃. Fig. 6 intuitively shows that 𝐵, 𝑊 , and 𝑋𝑠are
decreasing functions of 𝜃. Since 𝛿 = 0.3𝜃 in Fig. 6 (b), from (13) and (14), we have
lim 𝜃→∞𝐵 = lim𝛿→∞𝐵 = 0 and lim 𝜃→0𝐵 = lim𝛿→0𝐵 = 𝜆 (2𝜇 + 𝛼𝜆) (1 − 𝛼) (𝜇 + 𝛼𝜆)2 (18) The non-trivial result is that there is a threshold𝜃 value (𝜃 ≈ 100𝜆 in Fig. 6) such that beyond this threshold value, increasing 𝜃 does not improve the performance. On the other hand, Fig. 6 (c) shows that 𝑃𝑛𝑐 linearly
increases as 𝜃 increases. When 𝜃 increases, more credit units are reserved in an RU operation, and the credit in the OCS is consumed fast. Therefore, a newly incoming session has less chance to be served, and an in-progress session is likely to be force-terminated.
Effects of packet interarrival time distribution. Fig. 6
considers the packet arrival times with the Exponential and the Pareto distributions with mean 1/𝜆. In the Pareto distribution, the shape parameter𝑏 describes the “heaviness” of the tail of the distribution. It has been shown that the Pareto distribution with 1 ≤ 𝑏 ≤ 2 can approximate the packet traffic very well [14], [15]. Fig. 6 shows that𝐵, 𝑊 and 𝑃𝑛𝑐are decreasing functions
of 𝑏. When 𝑏 decreases, the tail of the distribution becomes longer, and more long packet interarrival times are observed. Since the mean value1/𝜆 is fixed for the Pareto distribution in Fig. 6, more long packet interarrival times also imply more short packet interarrival times. The number of short interarrival times must be larger than that of long interarrival times because the minimum of the interarrival time is fixed but the maximum of the interarrival time is infinite. Thus, it is likely that more packets will arrive during an RU operation, and𝐵 and 𝑊 increase. With a small𝑏, it is likely that the last session for a user accommodated by the OCS is a very long session. Before the session is completed, new sessions continue to arrive, and are rejected by the OCS, which
0 1 2 3 4 5 6 7 0 50 100 150 200 θ (unit: λ) B Exponential Pareto(b=1.2) Pareto(b=1.5) Pareto(b=2) (a) Effect on 𝐵 0 1 2 3 4 5 6 7 8 0 50 100 150 200 θ (unit: λ) W Exponential Pareto(b=1.2) Pareto(b=1.5) Pareto(b=2) (b) Effect on𝑊 0 0.01 0.02 0.03 0.04 0 50 100 150 200 0 3 6 9 12 θ (unit: λ) Pnc Xs Exponential + Pareto(b=1.2) × Pareto(b=1.5) 6 Pareto(b=2) R Solid curves: Pnc Dashed curves: Xs (c) Effect on 𝑃𝑛𝑐 and𝑋𝑠
Fig. 6. Effects of𝜃 and the packet interarrival time distribution (𝛼=0.01, 𝛾/𝜇=1/20, 𝛿=0.3𝜃, 𝐶 = 600/𝛼, and 𝜆/𝜇=3).
contribute to𝑃𝑛𝑐. Therefore𝑃𝑛𝑐increases as𝑏 decreases.
Effects of𝛿. Similar to the effect of 𝜃, Fig. 7 shows that
𝐵 and 𝑊 are decreasing functions of 𝛿 (see (18)), and 𝑃𝑛𝑐 is a linearly increasing function of 𝛿. A non-trivial
observation is that when 𝛿 ≥ 0.6𝜃, 𝐵 and 𝑊 approach to zero. It implies that selecting𝛿 value larger than 0.6𝜃 will not improve the performance. Fig. 7 (c) shows that 𝑋𝑠 is an increasing function of𝛿. When the amount of
the credit in a session is less than 𝛿, a CCR message is sent to the OCS. Therefore, for a fixed 𝜃, when 𝛿 is increased, 𝑋𝑠 increases.
Effects of RU operation delay distribution. Fig. 7 consid-ers the Erlang with𝑏 = 2 (which is a Gamma distribution with variance 𝑉 = 18/𝜆2) and Gamma distributed RU operation delays with variances 𝑉 = 0.01/𝜆2, 1/𝜆2, and 100/𝜆2, respectively.
The figure indicates that𝑃𝑛𝑐and𝑋𝑠are not significantly
affected by the RU operation delay distribution. On the other hand, 𝐵 and 𝑊 increase as 𝑉 increases. As 𝑉 increases, more long and short RU operation delays are observed. In long RU operation delays, it is likely that more than 𝛿 packets arrive. Therefore the packets are more likely to be buffered and delayed processed.
0 1 2 3 4 5 6 0 0.2 0.4 0.6 0.8 1 δ (unit: θ) B Erlang(2) Gamma(V=0.01/λ2) Gamma(V=1/λ2) Gamma(V=100/λ2) (a) Effect on𝐵 0 0.05 0.1 0.15 0.2 0.25 0.3 0 0.2 0.4 0.6 0.8 1 δ (unit: θ) W Erlang(2) Gamma(V=0.01/λ2) Gamma(V=1/λ2) Gamma(V=100/λ2) (b) Effect on𝑊 0 0.002 0.004 0.006 0.008 0.01 0.012 0 0.2 0.4 0.6 0.8 1 δ (unit: θ) Pnc Erlang(2) + Xs Gamma(V=0.01/λ2) × Gamma(V=1/λ2) 6 Gamma(V=100/λ2) R Solid curves: Pnc Dashed curves: Xs (c) Effect on𝑃𝑛𝑐 and𝑋𝑠
Fig. 7. Effects of 𝛿 and the RU opeartion delay distribution (𝛼=0.01, 𝛾/𝜇=1/20, 𝜃=100𝜆, 𝐶 = 600/𝛼, 𝜆/𝜇=3, and the packet arrival times have
the Pareto distribution with the mean1/𝜆 and 𝑏 = 2).
VI. CONCLUSIONS
This paper investigated the prepaid services for the UMTS network where multiple prepaid and postpaid sessions are simultaneously supported for a user. We described the prepaid network architecture based on UMTS, and proposed the credit pre-reservation mechanism (CPM) that reserves extra credit earlier before the credit at the GGSN is actually depleted.
An analytic model was developed to compute the average number 𝐵 of packets buffered during an reserve units (RU) operation and the probability𝑃𝑟that more than one RU
oper-ation is executed during a low credit (LC) period. Simuloper-ation experiments are conducted to investigate the performance of CPM. We have the following observations:
∙ 𝐵 and 𝑊 increase as 𝜆/𝜇 increases. The probability
𝑃𝑛𝑐 that a session is not completely served decreases as
𝜆/𝜇 increases. The avarage number 𝑋𝑠of RU operations
performed in a session is an increasing function of𝜆/𝜇.
∙ 𝐵, 𝑊, 𝑋𝑠and𝑃𝑛𝑐 are only affected by the end effect of
𝐶. When 𝐶 is sufficiently large (e.g., 𝐶 ≥ 600/𝛼, where 𝛼 is the probability that an arrival packet is the last one of the session), the end effect can be ignored.
∙ 𝐵, 𝑊 and 𝑋𝑠decrease but𝑃𝑛𝑐increases as𝜃 increases.
that beyond this threshold value, increasing 𝜃 does not improve the CPM performance.
∙ 𝐵 and 𝑊 decrease but 𝑋𝑠increase as𝛿 increases. When
𝛿 is large (e.g., 𝛿 ≥ 0.6𝜃), both 𝐵 and 𝑊 approach to zero.
∙ 𝑃𝑟 increases when 𝜆/𝜇 increases or 𝜃 decreases. ∙ 𝐵, 𝑊 and 𝑃𝑛𝑐 increase as the tail of the packet arrival
time distribution becomes longer.
∙ 𝐵 and 𝑊 increase as the variance of the RU operation
delay increases.
Our study provides guidelines to select the CPM parameters. Specifically, it is appropriate to select𝐶 ≥ 600/𝛼, 𝜃 ≈ 100𝜆, and𝛿 ≈ 0.6𝜃.
REFERENCES
[1] P. Lin, H.-Y. Chen, Y. Fang, J.-Y. Jeng, and F.-S. Lu, “A secure mobile electronic payment architecture platform for wireless mobile networks,”
IEEE Trans. Wireless Commun., vol. 7, no. 7, pp. 2705-2713, 2008.
[2] J. Lau, and B. Liang, “Optimal pricing for selfish users and prefetch-ing in heterogeneous wireless networks,” in Proc. IEEE International
Conference on Communications, June 2007.
[3] Y.-B. Lin and S.-I. Sou, Charging for Mobile All-IP
Telecommunica-tions. Wiley, 2008.
[4] D. Wu, T. Hou, and Y.-Q. Zhang, “Transporting real-time video over the Internet: challenges and approaches,” Proc. IEEE, vol. 88, no. 12, pp. 1855-1875, Dec. 2000.
[5] A.-C. Pang and Y.-K. Chen, “A multicast mechanism for mobile multimedia messaging service,” IEEE Trans. Veh. Technol., vol. 53, no. 6, pp. 1891-1902, Nov. 2004.
[6] S.-T. Sou, H.-N. Hung, Y.-B. Lin, N.-F. Peng, and J.-Y. Jeng, “Modeling credit reservation procedure for UMTS online charging system,” IEEE
Trans. Wireless Commun., vol. 6, no. 11), pp. 4129-4135, Nov. 2007.
[7] S.-I. Sou, Y.-B. Lin, Q. Wu, and J.-Y. Jeng, “Modeling prepaid appli-cation server of VoIP and messaging services for UMTS,” IEEE Trans.
Veh. Technol., vol. 56, no. 3, pp. 1434-1441, May 2007.
[8] S.-I. Sou, Y.-B. Lin, and J.-Y. Jeng, “Reducing credit re-authorization cost in UMTS online charging system,” IEEE Trans. Wireless Commun., vol. 7, no. 9, pp. 3629-3635, 2008.
[9] 3GPP, 3rd Generation Partnership Project; Technical Specification Group Service and System Aspects; Telecommunication management; Charging management; Online Charging System (OCS): Applications and interfaces (Release 10), 3G TS 32.296 version 10.0.0 (2010-03), 2010.
[10] H. Hakala, L. Mattila, J.-P. Koskinen, M. Stura, and J. Loughney, “Diameter credit control application,” IETF RFC 4006, Aug. 2005. [11] E. J. Watson, Laplace Transforms and Applications. Birkhauserk, 1981. [12] P. Lin, Y.-B. Lin, C.-H. Gan, and J.-Y. Jeng, “Credit allocation for UMTS prepaid service,” IEEE Trans. Veh. Technol., vol. 55, no. 1, pp. 306-316, Jan. 2006.
[13] H.-Y. Lee and Y.-B. Lin, “The simulation model for credit pre-reservation mechanism,” Technical Report NCTU-08-01, 2008. [14] M. Cheng and L.-F. Chang, “Wireless dynamic channel assignment
performance under packet data traffic,” IEEE J. Sel. Areas Commun., vol. 17, pp. 7, pp. 1257-1269, July 1999.
[15] S.-R. Yang and Y.-B. Lin, “Performance evaluation of location manage-ment in UMTS,” IEEE Trans. Veh. Technol., vol. 52, no. 6. pp. 1603-1615, Nov. 2003.
Hsin-Yi Lee received her B.S.C.S.I.E degree from
National Chiao-Tung University in 2003. She is currently a Ph.D student of the Department of Com-puter Science, National Chiao-Tung University. Her current research interests include wireless and mo-bile computing systems, and performance modeling.
Yi-Bing Lin (M’95-SM’95-F’03) is Chair Professor
of Computer Science, National Chiao Tung Univer-sity. His current research interests include wireless communications and mobile computing. Lin is the author of the book Wireless and Mobile Network
Architecture (co-authored with Imrich Chlamtac;
published by John Wiley & Sons) and the book
Wireless and Mobile All-IP Networks (co-authored
with Ai-Chun Pang; published by John Wiley & Sons). Lin is an ACM Fellow, an AAAS Fellow, and an IET(IEE) Fellow. He is also an adjunct research fellow of the Institute of Information Science, Academia Sinica, Nankang, Taipei, Taiwan, and consultant professor of Beijing Jiaotong University, Beijing, China.