Proceedings of the 2004 IEEE
Taipci, Taiwan. March 21-23, 2004
International Conference on Networking. Sensing Control
Survivability and Performance Optimization of Cellular
DS-CDMA Networks Considering Recovery Decision of
Base Stations
Kuo-Chung Chu' and
Frank
Yeong-Sung LintDepartment
of
Information Management
National Taiwan University, Taipei,
Taiwan
'd5725003@im.ntu.edu.tw
tyslm@m.ntu.edu.tw
Abstract
-
In this paper, we analyze the networksurvivabiliry in
CDMA
networks considering that base stations may fail. A survivable network is modeled as mathematical optimization problem. The objective is to minimize the total blocking traflc. We apply Lagrangean relaxation as a solution approach and analyze results on call blocking rate, service rate, as well as CPU time. Experiments illustrate that the recovery of base stations is a key factor to reducing call blocking rate for the smaller base station number and f o r the system in the heavy loading. Time consumed for increasing the base station number is mare significant than it for increasing the mobile user number.Keywords: Base station recovery, Lagrangean relaxation, mathematical modeling, network survivability, performance evaluation, quality of service.
1
Introduction
Theoretically, CDMA provides no upper l i t of available channels, but its capacity is bound with quality of service (QoS) constraint. Chahers and Solman [l] identify three impacts of mobility on QoS, including link
type, movement, and mobile devices impacts. A typical infkstmcmre of cellular network consists of a number of components, including base stations ( B S ) , base station controllers (BSC), mobile switching centers (MSC), home location registers ( E R ) and visiting location registers
(VLR), signaling system 7 (SS7), public switched telephone networks (PSTN), high-capacity
trunks,
etc. In the entire system, the base station which directly communicates with mobileusers
is a critical
facility.If
more base stations are deployed, there is a greater possibility of failure. A number of issues related to reliability and survivability of wireless and mobile networks are identified 121.To
analyze the impact of inhsmcture component failures, a scalable approach to modeling and simulating the reliability and Survivability of wireless networks is presented [3]. Even though thatspare part is an alternative to tackle the problem of components failure, some natural disasters such as floods
and earthquakes as well as some human factors, may crash the base station. Thus, part of the users may he out of
service so that overall QoS will degrade. In terms of operation, if =me base stations can be properly recovered,
it enhances QoS and provides survivable service. Accordingly, base station recovery is one of the most important approaches to minimizing total system call
blocking rate.
To
the best of our howledge, intensive researches have been conducted on planning of cost minimization both for general wireless survivable networks (41, and for DS-CDMA networks [SI, but they focus on long-term planning problem. Actually, network monitoring/servicing to identify and to alleviate potential failures in state of system operation is more important. Although performance comparison of FH-CDMA and DS-CDMA for wireless survivable networks is discussed [6], relatively little work has been attempted to tackle the overallcall blocking problem in conjunction with recovery decision of base station. The remainder of this paper is organized as follows. In Section 2, a mathematical problem formulation of survivable networks is proposed. Section 3 presents a solution approach to the problem based on Lagrangean relaxation. Section 4 illustrates the computational experiments. Finally, Section 5 concludesthis paper.
2 Network
Survivability
and
2.1 Problem description
Performance Modeling
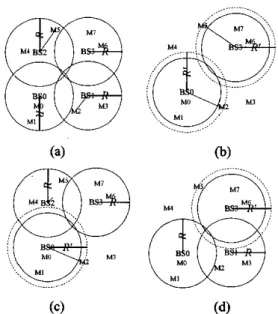
A basic approach to provisioning survivability and to reducing the impact of base station failures is recovery by redundant resources or mobile base stations. An alternative is overlaying architecture by adjusting transmission power of all availabldworkable base stations. Figure 1 illustrates an example which consists of four base stations (BSO-BS3) and eight mobile users (MO-M7). There are two mobile users covered by each base station. In Figure l(a), all base stations work normally (no failure) in power radius R. M 2 and MS is served by BSl and BS2,
respectively. Figure 1@) is a case of both BSI and BS2 failures. Thus, BSO and BS3 adjust power with R ' to serving M 2 and MS, respectively. However, if some of
failed base stations are to be recovered, it must be a complicated decisions. Figure l(c) and (d) is alternative to recovering one of failed base stations BS2 and BS3,
respectively. Also, power of available base stations BSO and BS3 is adjusted. Network survivability considering recovery decision of failed base stations, e.g. recovering N
of M failed base statons C(M,N), is a combinational optimization problem. A number of assumptions, including perfect power control, reverse link perfectly separated fbm the forward link, without considering fading and forward link, are given. In terms of call blocking analysis, some complicated scenarios lie new, re-homing, outbound, handover calls are not dealt with.
2.2 Performance indicators
About the performance issues of wireless conunnnications, Snow et al. [ 2 ] identify outage index taking into account both m a g n i t u d d e number of customers being influenced, and duratiow-the amount of time that service being impacted. Besides, the index focuses on two service components: registration blocking (I& when the customer is unable to initially register with the wireless network system; and call blocking (IcR). failures to call setup from registered customers. Based upon both
IRB
and ICB, the following induces two performance indicators to be analyzed in this research, say service rate and call blocking rate. The detailed description of the two performance indicators is as follows,( 1 ) Service rate (RS): No matter what causes the base stations to fail, power adjustment of availabldworkable base stations (inkgating partial fixed base stations) is conducted. Some mobile users originally covered by the base stations are probably still out of service.
This
out-of- service results in registration blocking,( 2 ) Call blocking rare (Rd: The call blocking
probability (PB) of mobile users is expressed by Erlang's
B formulaP, = B ( g , c ) , where g is aggregate traffic, c is available channel resources. Thus, call blocking rate is R, = g
.
P,
= g . B(g, c ) . Actually, in the survivable environmenfPB
can be M e r decomposed into two cases, a) PB = B ( g , c ) , where g is aggregate flow of total users covered by workable base stations, and c is overall available channels; b)P,
= B(g',c') = 1, where g' is aggregate flow of lost traffic (out of service), and c' is zero since the system does not allocate any channels.2.3 Performance modeling
= (1- I=).
The network survivability is formulated as a following mathematical optimization problem
(IP)
that the objective is to minimize the total call blocking rate of overall system, wbicb is the sum of average blocking in the coverage and lost traffic (9'). Notations used to modeling the problem are listed in the Table 1. Even though the call blocking probability, B, of Erlang's B formula, is nondifferentiable with respect to e, and nonconvex with respect tog, but the(C) (d)
Figure 1. An example of network survivability ; (a) normal case;
(b) BSl and BS2 failures with BSO and BS3 power adjushnent ; (c) BS2 recovery with BSO power adjustment ; (d) BS1 recovery
with BS3 power adjustment
call blocking rate, Le. g J . B,, is a convex function of g,
rather than B, alone [7].
5
= M i n x g,B,(g,,c,)+g'(W
,sa. subject to:s
c, 5 M , O S r s R , B , k , , c , ) sP,
z,, = 0 or 1 f , = O o r l cJ Ez'
V j € B" V j e B"(1) V j e B " ( 2 ) Vjjs B",fjs T(3) V t € T(4) 'Vje B , f e T ( 5 ) Vjje B(6)(7)
V j c B" ( 8 ) Vr, E U,, j € B"(9) V j c B"(10) V j E B " , f € T(11) V j E B(12) (13)Constraint ( I ) ensures that each traffic demand is
served by a base station in the required QoS. Constraint (2) checks aggregate flow of each base station jeB". Constraint (3) requires that a mobile user must be in the
coverage of a base station before it is to be served by that base station. Constraint (4) is to guarantee that each mobile user can be homed to no more than one base station. Constraint ( 5 ) ensures that h , = l only if
4
63 si =1 in each of two cases, a) base station j is failed (s,=l) and to be fixed ~ = l ) ; b) base station j is good (s,=O) and no fix is needed ~ = O ) . Constraint (6) ensures that the decision variable of S i n g base stations is set to 1 only if s,=l.Constraint (7) guarantees that total number of k e d base stations is less than predefined threshold U. Constraint (8) is to ensure that the number of users who can be active at the same time in a base station is no greater than upper bound
Mp
Constraint (9) is to ensure that transmission power radius of each base station j e B " is between 0 and Rp Constraint (10) requires that a base station serves its slave mobile users under pdefined threshold of call blocking probability. Constraints (11) and (12) are to enforce the binary property of the decision variables. Finally, constraint (13) denotes the integer property of decision variables for channel allocation.3 Solution
Approach
3.1
Lagrangean relaxation
The approach to solving the problem
(IP)
is Lagmngean relaxation[SI
[9], which includes the procedures that relax complicating com+~aints, multiply the relaxed constraints by corresponding Lagrangean multipliers, and add them to the primal objective function. Based on above procedures, we transform the primal optimization problem @) into the following Lagrangean relaxation problem(LR)
where Constraints (l), (2), (3),(5). (6) are relaxed. Furthermore, LR can be decomposed into three independent subproblems: 1) channel assignment, power control subproblem and capacity management subproblem; 2) admission control subproblem; 3) base station recovery subproblem.
I \ \
subject to: (4), (7)-(13),
Table 1. Description of notation
...
B
F
The set of base s t a t i m
The set of failed base stations. Fc B
Predefined &hold of total
fixed
base stations Thesetoffixed basestatom, F k F, I F + U Tbe set of available base stations, B kB-FThesetofworkablebasestations, B'=BCIF'
The amificial base station to carry the rejected d when decides to reject the call
Tbe set of mobile usm
Call blacking probability in base staton j , j E B
Upper bound on the number of usm that can active at the same time at base station j, j E B
Upper bound on the m - i o n p o w radius of base statan j, jt R
lhreshold of call blocking probability for each base station
i P R
,,,--
T h e number of users who can be active at the same time in
the base station j, js R
Transmission power radius of base station j, j € B
The set of hansmission radius of base station j A m g a t e flow at base shtion j, je E"
q
6
g,
The p " ~
ihat
a base Stanon received h m a mobile user that IS homed to the base smon wth perfect power controlIhe energy that BS received
Asmallnumber
E6
Nmd Total nose
G Thepmcessmggnm NO The background nom
a vo~uactlv~tyfactor
7 Attenuationfaclor
1,
D,,
The M cr e q m e n t of mobile statlon r(m Erlang), I 1
D a m bchvcen bare &on land moblle user I
0, Distanccbetwgnbasestationjandj'
'I'
'''
Coverage indicator function which ir 1 ifmabile user ,can be served by base station jand 0 oth&,p B
Granting decision -able which is 1 if mobile w rI is serviced by base station J and 0 othawlse, p B
Initial indicator function of base station s, 4 which is 1 if base station is failure and 0 othawise
Decision vsnable of fixlns failed base station je R m not, which is 1 if broken base station is fixed and 0 otkrwix
Exclusive-or ofJand sj expressed by ( l - m l - s,)
A
s,
(I) channel assignment, power control, and capacity
management subproblem related to c,
,
r,,
and g , IE
- d g +"'((") ---(- ~ ,"'I d N o N,,,,
i , i
subject to: (8) (9) (IO) (13)
Problem (SUBI) can be decomposed into lB'1
subproblems since the value of
5
and e, is discrete and limited. To get an optimal solution, we just exhaustively search for all possible combinations ofc,, 5
and g,.
(2) admission control subproblem: related to z,,
subject to: (4) and (11).
In (SUBZ), tlie second term &&TIxAt is a constant, total aggregate traffic in the system, which can be dropped and added back to the optimal value. Then (SUBZ) can be decomposed into IB'Ixl TI independent subproblems for each I,, = (v;,D,, +(v: -l)A,) where j t B " and teT. To get the minimal value of problem (SUBZ), we assign either z,, = 1 for the minimal value of I,, , or zJ, = O otherwise.
(3) base sfafion recovery subproblem: related to f,
z
,
,
,
=mince
(- (1 -r,N
- s,) -r,
. s,)IST 1'"
subject to: (7), (12).
In(SUB3),thesecondtenn c ( ( c v : , - v i ) s , - c v : , )
is a constant that can be calculated easily. Then, let k, = C v : , ( l - Z s , ) + v : so . that
(SUB3)
can be decomposed into IBI independent subproblems for eachk,
. To get a minimal value of problem (SUB3), we assigneither f, = 1 for first
14
minimal value of k, (for constraint(7))
at most, or f , = 0 otherwise.,'a n T - 7
I F T
3.2 Lagrangean
dual
problem
and
subgradient method
According to the weak Lagrangean duality theorem [IO], for any (v:,v:,,v;,,v:)20 and v:
,
the objective value of Z,(v,,v,, v,,, v,,, vi) is a lower bound on Z,. Based on Problem (LR), the following dual problem @) is constructed to calculate the tightest lower bound.1 1 1 4 1
Table 2. Given parameters
No(atlon Value YNo 7 db EboVtao, 6 db
4
1 20 T 4 G 15625 0. i n Z , = m az,(.I,,
(, <,,
v:,,@)
subject to: (d,,
{,,
v:,, <) 2 0 and4
.Then, a suhbgadient method is applied to solving the dual problem. Let the vector S be a subgradient of
Z D ( ( , $ , < , , v ; , , $ ) at($,(,$,,v;,,<). In iteration k of subgradient optimization procedure, the multiplier vector
II is updated byz"' = n * + t ' S ' , in which 'f is a step s u e dete&ed by = 6 (Zip - Z,
(='))/I1
s'
112
,
wherez',
is an upper bound on the primal objective function value after iteration k, and 6 is a constant where0 S 6<
2 .3 3 Getting primal feasible solutions
This
research applies both Lagrangean relaxation and subgradient method to solving the problem of network survivability and performance modeling. The procedure is to get a better primal feasible solution in the process of iteratively solving dual problem. We developan
algorithm A to geaing primal feasible solutions, it needs to be checked if solutions satisfy all constraints relaxed before.[Algorifhm A ]
Step 1.Check QoS constraint (1) for each base station j. Adjust the transmission power radius r j down if the QoS constraint is still violated, or go to Step 2 otherwise.
Step 2. Compute the aggregate traffic flow g, of each base station j based on the transmission power radius r j
determined in Step I .
Step 3.Check. the call blocking constraint B, (g, , c,) 5
P,
. Assign the available channel e, up to meet the call blocking requirements4
if the call blocking constraint is still violated, or go to Step 4 otherwise.Step 4. Adjust the transmission power radius r j to the extent for just far enough to cover all mobile users in each base station j.
Step 5. Calculate the whole blocking h;lffic in the system that is based upon the decision variables, including e , , 5 , g,
,
and z,, , solved in previoussteps. Step 6 . End algorithm.
4 Computational Experiments
4.1 Experimental
environment
Parameters are given in Table 2. Algorithm implementation and platform running on is coded in C and is PC with INTELm P4-1.6GHZ CPU, respectively. We evaluate the algorithm for 5 cases of base station number
(BS #) - 40,80, 120, 160,200, and 6 cases of mobile user number (MU #) - 500, 1000, 1500, 2000, 2500, 3000. Locations of BS as well as MU are generated in uniform distribution. The number of failed base stations
(14)
is given to onetenth of total base stations. BS recovery ratios (BSRR) are given to 0.00, 0.25, 0.50, 0.75. The limit of iterations for Lagrangean relaxation approach is 1000, and the improvement counter is 25. The parameter 6 adopted in the subgradient method is initialized to be 2 and halved when the dual objective function value does not improve for 25 iterations. Besides, predefined threshold of call blocking probability for each base station is given withP,
=0.03.4.2 Performance
analysis
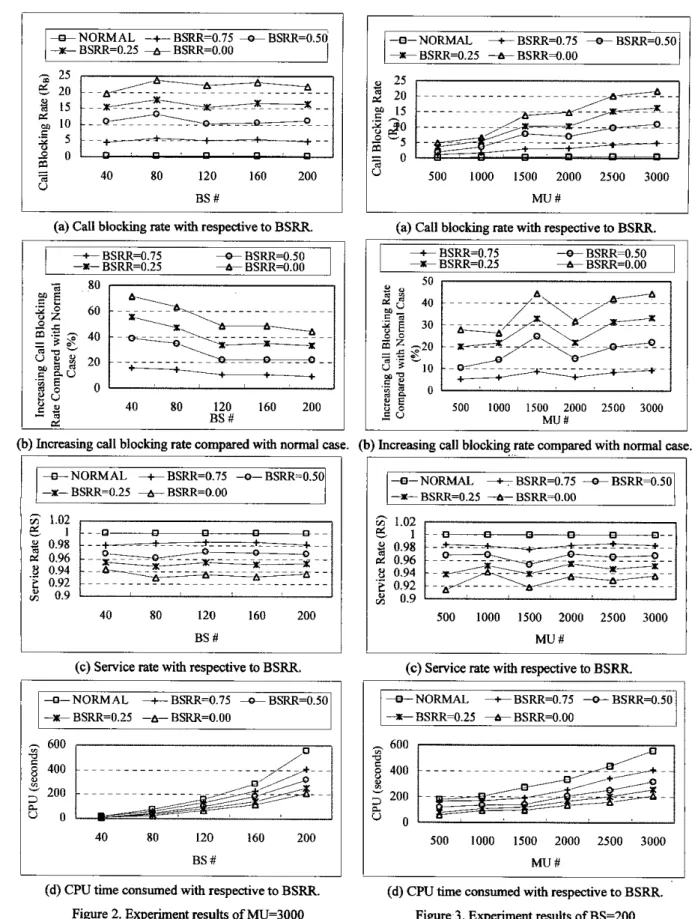
The analysis focuses on Mu # =3000, depicted in Figure 2, and BS # =ZOO, depicted in Figure 3, comparing with a number of BS and MU, respectively. Experiments calculate with all near-optimal solutions in gap less than 0.001%. Experimental results include call blocking rate (upper bound of
Zm),
service rate, and CPU time.( I ) Call blocking rate(RB): In case of MU # 3000,
RB
is insignificant difference among a number of BS, Figure 2(a). In case of BS # 200, Figure 3(a), it is a montonically increasing function of MU #. The number of MU significantly affectsb.
To analyze the impact of BSRR on RB, for each of increasingRB
calculated is compared with normal case (noBS
failure). In Figure 2@), the case of MU # 3000, increasingRs
is varied from 15% to 71% in case of BS # 40, while it is in the range from 10% to44% in case of BS # 200. BSRR is a key factor lo reducing
Rs
f o r small number of BS. In Figure 3@), the case of BS # 200, the maximum of increasing RB is up to 27% in case of MU # 500, while the increasing is varied from Yh to44%
in case of both MU # 1500 and MU # 3000. BSRR is the more important factor to reducing RB when the system is in the heavy loading.(2) Service rate&): Obviously,
&
is a montonically increasing function of BSRR. However, it is insignificant impacts of BSRR on & in all cases of BS # and MU # in Figure 2(c) and Figure 3(c), respectively. No matter which case is calculated,&
is in the range from 0.92 to 0.98.(3) CPU time: Time consumed is to run Lagrangean relaxation procedure up to 1000 iterations. All experiments are converged in less than 1000 iterations. Since the survivability analysis focues on avaible base stations, the more
BSRR
is required, the more CPU is consumed. Also, it is a increasing function of MU # and BS #. In case of Mu # 3000, Figure 2(d), CPU consumed is from 8 to 16 seconds in the smallest BS # 40, while itcalculates with 209 to 556 seconds in the largest BS # 200.
In case of BS # 200, Figure 3(d), CPU consumed is from 57 to 117 seconds in the smallest MU # 500, while it calculates with 209 to 556 seconds in the largest MU #
3000. Time consumed is more significant when the number of BS is increasing than Mu is increasing.
5 Conclusions
This
paper investigates the survivability problem of DS-CDMA networks. Network survivability network is modeled as performance optimization problem, failures and recovery decisions of base stations are considered as well. Proposed model in conjunction with developed algorithm recovers some of the failed base stations to guarantee sustainable services as well as to assure quality of service. Experiments illustrate that the recovery of base stations isa
key factor to reducing call blocking rate for the smaller number of BS as well as the system in the heavy loading. Time consumed is more significant when the number of BS is increasing than MU is increasing. Based on the proposed approach, we believe that a more flexible and comprehensive model can further be considered to decide where mobildptable base stations should be allocated in dynamic user requirements.References
D. Chalmers and M. Sohnan, “A survey of quality of service in mobile computing environments,” BEE Communication3 Surveys, ZQuarter, 1999, pp. 2-10. A.P. Snow, U. Varshney, and A.D. Malloy, “Reliability and survivability of wireless and mobile networks,” IEEE Computer, vol. 33, Issue: 7, pp. 49 -55, July 2000.
N. Dimitriou, G. Sfikas, and R. Tafazolli, “Call admission policies for
m,”
in Proc. IEEE VTG vol. 2, pp. 1420-1424,2000.
F. Y . 4 . Lin and C.-Y. LQ “Integrated planning and management of survivable wireless communications networks,” in Proc. APCC/OECC, vol. 1, pp. 541 -544,
1999.
KuoChung’Chu, Frank Yeong-Sung Lin, and Shih-Ha0 Lee, rntergrated planning and capacity management of
survivable DS-CDMA networks”, accepted for publication, IEEE ICNSC, Taipei, Taiwan, March 21-23,2004.
S. Chuprun, C.S. Bergstrom, “Comparison of FWCDMA and DSICDMA for Wireless survivable networks,” in Proc.
IEEE GLOBECOM vol. 3, pp.1823 -1827,1998.
K. R Krihm, ‘The convexity of loss rate in an E r h g
loss system and sojourn in an Erlang delay system with
respect to arrival and service rates,” IEEE Trans on
Communicotiom, 38-9, pp. 1314-1316, Sep. 1990.
A. M. Geoffrion, “Lagrang& relaxation and its use in integer programming”, Math Programming Study, vol. 2,
pp. 82-114, 1974.
M. L. Fisher, “The Lagrangian relaxation method for
solving integer programming problems”, Management
Science, vol. 27, pp.1-18, 1981. ..
[lo] H. Held, P. Wolfe and H. D. Crowder, “Validation of subgradient optimization”, Math. Programming, vol. 6, pp. 62-88. 1974.
6 NORMAL
+
BSRR=0.75 & BSRR=O.50+
BSRR=0.25+
BSRR=O.OOI
(b) Increasing call blocking rate compared with normal case. (a) Call blocking rate with respective to BSRR.
+
BSRR=0.25-+
BSRR=O.OO + BSRR=0.75 4 BSRR=0.50*
BSRR=0.25+
BSRR=O.OO 40 80 120 160 200 BS #I
x u 40 80 120 160 200 -, BS #-
(b) Increasing call blocking rate compared with normal case
-0-NORMA.L +BSRR=0.75 4 BSRR=0.50
t BSRR=0.25 + BSRR=O.OO
500 IO00 1500 2000 2500 3000 M u #
(a) Call blocking rate with respective to BSRR.
t BSRR=0.75 4 BSRR=0.50 t BSRR=0.25 + BSRR=O.OO 50 r
c z
:o 500 1000 I500 2000 2500 3000 2 u MlllY 4- NORMAL if- BSRR=0.25 -h- BSRR=O.OO t BSRR=0.75 4 BSRR=0.50(c) Service rate with respective to BSRR. (c) Service rate with respective to BSRR
(d) CPU time consumed with respective to BSRR. Figure 2. Experiment results of MU=3000
compared with a number of BS
+NORMAL +BSRR=0.75 --ctBSRR=0.50 +BSRR=O.25 +BSRR=O.OO B
-
200 500 1000 1500 2000 2500 3000 M u #(d) CPU time consumed with respective to BSRR. Figure 3. Experiment results of BS=200