Resource and Performance Management
in Wireless Communication Networks
Chih-Hao Lin and Frank Yeong-Sung Lin
Department of Information Management
National Taiwan University
Taipei, Taiwan, R.O.C.
Email: d5725001@im.ntu.edu.tw
Abstract
In this paper, we study the problems of resource and performance management in channelized wireless networks. For identifying research issues systematically, we propose a research framework consists of two modules: performance optimization and network servicing modules. For an in-service communication network, performance optimization module manages radio resources to ensure communication quality of service and optimize system performance. For channelized wireless system, the realtime issues of performance optimization are admission control, channel assignment, power control, and homing. Network servicing module is event-driven or periodically resource augmentation plan, which alleviates the performance exceptions and optimizes long-term system revenue by using corrective mechanisms consist of resource augmentation, channel reassignment, cell rearrangement, and rehoming issues. Under the consideration of generic sectorization and interference effects, we introduce several mathematical models for both modules and formulate the associated issues as combinatorial integer programming problems. By using Lagrangean relaxation method, several efficient and effective algorithms are developed to deal with these NP-hard problems.
1. Introduction
Due to the rapid growth of wireless communication systems in the world, the scarcity of spectrum resource necessitates efficient management and optimization mechanisms. In order to efficiently utilize the spectrum resource, frequency resource management is becoming one of the most important issues for channelized wireless networks. Whether channel sharing is based upon given cell configuration, there exists a fundamental limitation on the number of users sharing the same frequency simultaneously. Since higher resource utilization can achieve higher revenues, how to assign channel resources and reorganize cell configuration to optimize resource utilization become critical issues in wireless networks.
To deal with these problems, we propose a research framework to identify associated research issues for
wireless resource and performance management purposes. According to the characteristics and objectives of operational problems, this research framework consists of two parts: performance optimization module and network servicing module. The objectives of performance optimization module are to ensure quality of service (QoS) and optimize realtime system performance. In an in-service channelized wireless network, performance optimization will be achieved by realtime admission control, channel assignment, power control, and/or homing mechanisms subject to carrier-to-interference ratio (CIR), QoS, configuration, and capacity constraints. As the traffic demands exceed the traffic load threshold, network servicing mechanisms must be applied to expand network capacity. The objectives of network servicing module are to maximize long-term revenue by using channel augmentation, channel reassignment, configuration re-arrangement, and rehoming mechanisms.
In this paper, we develop several mathematic formulations to model these mechanisms. Although various resource management approaches have been proposed to increase the channel utilization, the proposed generic sectorization model is more suitable to model real world network than traditional approaches. This model can construct irregular cell location, arbitrary transmission power, reasonable height, and any kind of sector architectures.
The major communication QoS for channelized wireless systems is downlink CIR constraint [7]. Under the consideration of generic sectorization networks, we propose three kinds of interference estimation methods to accumulate interferences from all of interfering cells to approximate real interference strength.
Although channel filters in both base stations (BSs) and mobile terminal (MTs) significantly attenuate signal from adjacent channels, severe interference may occur when the power level of adjacent interfering channels greatly exceeds that of the desired channel. In this paper, we together accumulate co-channel interference (CCI) and adjacent channel interference (ACI) in our generic interference model to estimate the total interferences received by MTs [1].
State 2: Necessary Augmentation Transition 1: Admission control Transition 2: Channel assignment Transition 4: Homing Transition 6: Channel augmentation Transition 7: Channel reassignment Transition 8: Configuration Rearrangement Transition 5: Starvation Transition 10: Abundance
Performance optimization module Network servicing module The characteristics and issues of resource and performance management problems
Transition 3: Power control State 1: Realtime Arrangement Transition 9: Re-homing
Fig. 1. The research framework of generic resource and performance management These combinatorial optimization problems described
in this paper are NP-complete. Based upon Lagrangean relaxation method, we formulate these problems as integer programming problems subject to configuration, capacity, QoS, and CIR constraints. The configuration and capacity constraints require that the transmission power and the assigned channels for each antenna must be admissible with hardware equipment limitations. Whereas, the QoS constraints require that the call blocking probability and call-dropping rate constraints are satisfied. The CIR constraint ensures that received CIR is larger than the sensitivity of MTs. To take into account computation time constraints, instead of attempting to solve the problem optimally we introduce several Lagrangean-based algorithms to solve these problems efficient and effective.
The remainder of this paper is organized as follows. In Section 2, we provide the research framework for resource and performance management problems. Section 3 describes several generic mathematic models that are the key components of our formulations. Based on these models, we develop a sequential homing algorithm to deal with performance optimization problem in Section 4 and several algorithms for network servicing problems in Section 5. Our computational experiments are discussed in Section 6. Finally, the summary of this paper is described in Section 7.
2. Research Framework
By using classification approaches, generic research framework decomposes complexity problems to systematic research issues and usually guides to solution policies. In this section, we propose a research framework for the resource and performance management problems. Due to different performance objectives, there are two kinds of problems: one is performance optimization module (arranges wireless resource to optimize realtime system performance) and the other is network servicing module (periodically considers resource augmentation and
configuration rearrangement to maximize system long-term revenue). We depict the relationship of these two modules by finite-state-mechanism in Fig. 1.
In this research framework, we use two system states to differentiate realtime and long-term operational objectives. There are ten transitions in the framework to perform possible treatments for the corresponding system state. A system stays at State 1 means that great majority of traffic requirements can be serviced by this system and all of the in-service requirements must satisfy QoS constraints. In this state, there are four operational treatments can optimize realtime system performances. These treatments consist of admission control, channel assignment, power control, and homing policies.
If applying all of these mechanisms on wireless system still violates the call blocking probability constraints, it means that current system resource becomes insufficient, which may cause by the growth of traffic demands or the change of traffic distributions. The starvation transition will be triggered and it will transfer the system state to necessary augmentation state, denoted as State 2. At State 2, system operator can adopt four treatments to rearrange and/or augment system resource to expand system capacity. These mechanisms consist of channel augmentation, channel reassignment, configuration rearrangement, and rehoming. After the amendment of network servicing module, wireless networks will transfer to State 1 again. We describe these mechanisms as follows.
Admission control: Whenever a new traffic demand arrives, admission control mechanism must be applied immediately to decide whether system can grant this new requirement or not. The new grant decision must not violate the QoS requirements of existing users and still satisfy all of system constraints.
Channel assignment and re-assignment: Considering CCI/ACI and configuration constraints, channel assignment mechanism will assign enough feasible
channels to each cell to optimize resource utilization. Channel reassignment may be required in a wireless network when channel interference or new channels become available to optimize resource utilization. Power control and configuration re-arrangement: If the
distribution of traffic demand changes due to populations shift, power control and/or configuration rearrangement mechanisms are indispensable even though channel reassignment may solve some kinds of performance exceptions. Power control changes transmission power level of each antenna. Furthermore, configuration re-arrangement can periodically amend antenna coverage by tuning both sector radian and power level for each antenna.
Homing and re-homing: For satisfying call blocking constraint purpose, load balance policy prefers to home a new traffic demand or rehome an existing one to the lowest utilization cell in order to minimize the total amount of system required channels.
Channel augmentation: When the traffic demand exceeds a critical point and the current network capacity becomes insufficient, channel augmentation is required to expansion network capacity. The objective of this mechanism is to minimize the long-term channel license fee subjects to the call blocking constraint and coverage constraint.
Using this research framework, we introduce several generic mathematic models for research issues in Section 3 and develop several algorithms for both research modules in the Section 4 and 5.
3. Generic Mathematical Formulations
3.1. Generic Configuration Specification
We adopt the most widely quoted macro-cell model as our propagation prediction model, which divides the prediction area into open, suburban, urban, and small city areas [2]. We construct wireless system by specifying the carrier frequency, the heights of BSs and MTs, and the distances from BSs to MTs. This empirical propagation prediction model can be applied in built-up quasi-smooth areas for distances between 1 and 20 km and for frequencies in the range of 150 MHz to 1 GHz (It had be extended to cover up to 100 km and 2 GHz). The existing and augmentation frequencies are labeled as continuous integer numbers. Using this naming scheme, we can describe the neighboring relationship and calculate the frequency separation.
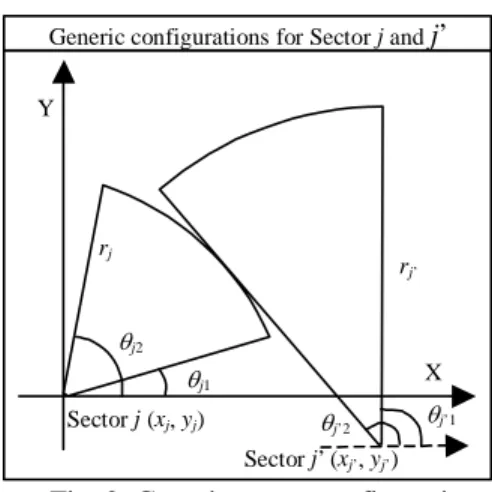
In this paper, generic sectorization model allows irregular BS locations, selective radiuses or transmission power of antennas, and any kind of sectorization radians. Therefore, this model can specify several kinds of real wireless networks, such as omni-direction antenna, regular sectorization, and irregular smart antenna structures. We depict the generic configuration in Fig. 2.
θj1 θj2 Sector j (xj, yj) Sector j’ (xj’, yj’) rj rj’ X Y θj’1 θj’2
Generic configurations for Sector j and j’
Fig. 2. Generic sector configurations
3.2. Generic Interference Models
To satisfy the CIR constraints in channelized wireless systems, CCI usually be considered as one of the most important issues. Due to ACI may cause channel impairments such as cross-talk effects, premature handoffs, and dropped calls, ACI is become another significant QoS degradation factor in channelized wireless network. Most of literatures mainly focus on CCI but ignores the possibility of CIR constraint violation due to the aggregate effect from both CCI and ACI excess the interference upper bound.
In this paper, we jointly consider CCI and ACI in our generic interference model. If the transmitter and receiver are matched, we can use to denote the filter characteristic. A ratio called as net filter discrimination (NFD) describes the discrimination of ACI over CCI due to channel separation and modulation spectrum shape. This NFD ratio can be defined as a function of channel separation normalized to the bit-rate and formulated as [8]
) ( f S
∫
∫
∞ ∞ − ∞ ∞ − ∆ + ⋅ = ∆f S f S f f df S f df NFD( ) ( ) ( ) 2( ) .We assume that the interfering power is considered uncorrelated with each others and the desired signal, thus all signals are “power-added” at the receiver. We simply accumulate both CCI and ACI to estimate the total inferences received by MTs. We can formulate the CIR constraint by accumulate all interferences received by each MT to satisfy the receiver sensitivity of each MT. For different kinds of applications, we propose three kinds of interference estimation models.
3.2.1. MT-based Interference Model. This exact
approach estimates the received interferences for each MT by using radio propagation prediction methods or exactly power measurement techniques. This exact approach is advantage on its higher precision at interference power level but disadvantage on its time complexity depends on the number of MTs and BSs. In performance optimization module, we can enforce the CIR requirement for MT t,
which are homed to Sector j, by formulating the CIR constraint as ji j j H h j Ci F i j tj tj hj y i i G G y a a t ) 1 1 ( |) ' (| ' ' ' ' ' − ≤ + + −
∑
∑ ∑
∈ ∈ ∈ γ θ δ ∀i∈F,j∈C,t∈T (1) where j A F i ji N y ≤∑
∪ ∈ ∀j∈C (2) 1 or 0 = ji y ∀j∈C,i∈F . (3)Notations C/T F/ /A denote the sets of sectors/MTs/ existing channels/augmentative channels in the system, respectively. denotes the candidate homes for MT t. Notation is indicator function, which is 1 if Sector j
belongs to homing policy and 0 otherwise. The received power of MT t H hj δ t H h∈
t from the downlink signal of Sector j denotes as . Function is the NFD ratio that is a function of the channel separation. Decision variable is channel assignment, which is 1 if Channel i is assigned to Sector j and 0 otherwise. Threshold of acceptable CIR is
tj
a θ
( )
∆iji y
γ . Because Inequality (1) will violate whenever =0, we introduce an arbitrarily large number to avoid the violation possibility. Inequality (2) is configuration constraint of each sector.
ji
y
j
G
3.2.2. BS-based Interference Model. For pure channel
assignment or augmentation problems without considering power control or configuration rearrangement, the inter-BSs interfering relationships are static. That is, we can construct compatibility matrix for BSs by using BS-based interference model. Each element of compatibility matrix is a function of distance and can be pre-calculated by Φjj'∝
(
rj' Djj')
α. Element ' is the inverse CIR of interested Sector j interfered by Sector j.jj
Φ
α is the mean path loss exponent that is usually chosen between 2 and 6 depending on the geography. is the shortest distance between the interfering BS j’ and the coverage of interested BS j. That is a reference distance for estimating the maximum interference between j and j’. Notation is the radius of interfering BS j’. We can formulate the CIR constraint as
' jj D ' j r ji j j C j i F i j jjy i i G 1 G )y 1 ( |) ' (| ' ' ' ' ' − ≤ + + − Φ
∑ ∑
∈ ∈ γ θ ∀j∈C,i∈F∪A. (4)3.2.3. Over-estimation Interference Model. Due to the
radius of each sector is one decision variable during adopting power control or configuration re-arrangement mechanisms, transmission power of each sector is uncertain until optimizing the system. For QoS assurance
purpose, we suggest that using the maximum candidate radius of interested sector to substitute uncertain one. Under adopting over-estimation approach, we can assure that any mobile terminal homing to interested cell must not violate CIR constraint. We formulate this approach as
ji j j C j i F i j j jj j y G G i i y r D r ) 1 1 ( |) ' (| ) ( ' ' ' ' ' ' − ≤ + + −
∑ ∑
∈ ∈ θ γ α ∀j∈C,i∈F∪A (5) where 0≤rj≤Rj ∀j∈C. (6)Reference distance Djj'
( )
rj is the minimum distance between interested Sector j and interfering Sector j’ that is a function of the transmission radius of Sector j. is the upper bound of transmission radius for Sector j.j R
3.3. Communication QoS Models
3.3.1. Call-Blocking Probability Constraint. For
communication networks, call-blocking probability is one of the important QoS for service provider to satisfy customers’ requirements. Considering average performance of resource management, we aggregate MTs to become statistic location-based clusters, denoted as for mobile cluster t. The aggregate traffic of Sector j is denoted as . The homing decision variable for MT t on Sector j is denoted as . Its value is set to 1 if MT t is homed to Sector j and 0 otherwise. We use Erlang-B formula t λ j g ( jt z ) ,
∑
∑
∪A F ji y ∈ i jt tz λ ∈T tB to denote the blocking
probability when
∑
∈T t
λtzjt Erlangs of traffic is offered to
∑
∪ ∈F A i
ji
y trunks on Sector j. We can also derive the minimum trunk required function ( , j)
T t jt tz T
∑
λ β ∈ with the condition of call blocking probability threshold βj due to the integer property of trunk numbers. We can formulate two kinds of call-blocking probability constraints as follows: j A F i ji j y g B∑
≤β ∪ ∈ ) , ( ∀j∈C (7)∑
∪ ∈ ≤ A F i ji j j y g T( ,β ) ∀j∈C (8) where j T t jt tz =g∑
∈ λ ∀j∈C. (9)3.3.2. Call-Dropping Rate Constraint. For existing users, call drop means the communication is interrupted and disconnected. Both frequency hopping and handover mechanisms may cause call drop, which will degrade service quality and lose revenue. We introduce two cost-probability functions and . is loss of revenue due to channel reassignment on Channel i and
F i ∆ H t ∆ F i ∆
H t
∆ is loss of revenue due to the decision of re-homing MT
t. The call-dropping constraint can be formulated as
F i
∑
∈∑
∈C j jt z Z j b j T t jt jt H t ji ji F i × y − f + ∆ × z −h ≤M ∆∑
∈ C j∈ ∀ (10) where 1 = jt z ∀t∈T (11) 1 or 0 = ∀j∈C,t∈T . (12)Indicator function denotes whether existing Channel i is used on Sector j or not. denotes the original homing decision. Notation is the call-dropping loss revenue limitation. Equations (11) and (12) enforce that one mobile terminal can only home to one sector. Using this formulation, we can describe the reassignment sequence according to channels’ usage status and differentiate the reliability priority of MTs due to different pricing policies.
ji
f
jt
h Mj
4. Performance Optimization Module
Performance optimization module handles realtime or quasi-dynamic resource management problems. The objective of performance optimization problems is to maximize the number of admitted calls to optimize total system revenue.
2.1 Admission
Control
Problem
In this paper, realtime distributed admission control does not cooperate with DCA but with sequential homing based FCA mechanism because DCA strategies are less efficient than FCA under high load conditions [3]. We propose a sequential homing algorithm to determine homing sequences and FCA to allocate channel resources more efficient. After we determine the homing sequence for each MT, MT initial the call admission control phase and inspect QoS feasibility of each candidate home sequentially.
Given denotes the set of candidate home sectors for MT t, is integer permutation set,
t
H
S gj
B
is the upper bound of aggregate traffic for Sector j, and is blocking probability function of Sector j. We formulate this fixed sequential homing algorithm as an integer programming problem to determine sequential homing variable and call blocking probability .
j
b
hs
x ts
Objective function (IP1):
(IP1)
∑ ∏
∈ ∈ = T t sS ts t IP min λ Bsubject to: (1), (2), (3), and
ts H h jC tj hj hs b B x t =
∑
∑
∈ ∈ δ ∀t∈T,s∈S (13) tj j F i ji g b y =∑
∈ ) , ( ∀t∈T,j∈C (14) j T t hH sS s k tk hs hj t x B g t = ∑ ∑
∑ ∏
∈ ∈ ∈ − = 1 1 δ λ ∀j∈C (15) 1 =∑
∈Ht h hs x ∀t∈T,s∈S (16) 1 =∑
∈S s hs x ∀t∈T,h∈Ht (17) (18) 1 or 0 = hs x ∀t∈T,h∈Ht,s∈S ts ts B B ≤ ≤ 0 ∀t∈T,s∈S,Bts∈Kts (19) tj tj d d ≤ ≤ 0 ∀t∈T,j∈C (20) j j g g ≤ ≤ 0 ∀j∈C. (21)The objective is to minimize the call blocking rate of total system. Constraint (13) is the call blocking probability of MT on the permutation s. Constraint (14) decomposes the call blocking probability of Sector by introducing one auxiliary variable b . Constraint (15) calculates the aggregate traffic for Sector . Constraint (16) enforce only one candidate homed can be selected for each MT t on each permutation. Constraint (17) enforces the number of candidate path is equal to the number of homing decisions. Constraint (18) enforces the integer property of . Constraints (19), (20) and (21) enforce the feasible regions.
t j tj j hs x
5. Network Servicing Module
To optimize long-term average system revenue is the major objective of network servicing module. Channel reassignment, augmentation, configuration re-arrangement, and rehoming mechanisms are the major treatments of wireless network servicing problems.
5.1. Call Blocking Rate Problem
Given the system architecture, we formulate the call-blocking rate minimization problem as an integer programming problem [4].
Objective function (IP2):
∑
∑
∈ ∈ + = C j i A ji j j j IP g B g f y Z 2 min ( , ) (IP2)subject to: (2), (3), (4), (7), (9), and
1 or 0 0 = j y ∀j∈C (22) 1 or 0 ) 1 ( , A+ = j y ∀j∈C. (23)
The objective function is to minimize the call-blocking rate (loss of revenue) of total system. Constraints (23) and (24) enforce the integer properties. Notation denotes the number of original channels assigned to cell j.
j f
5.2. Combinative Network Servicing Problem
Considering the comprehensive of network servicing module, we combine all of treatments in network servicing module to optimize system revenue. In this
problem, the decision will be how to reassign existing channels, rearrange transmission power, rehoming mobile users, and augment additional channels to alleviate performance problems. We denote the license fee of augmented channel i as . We formulate this problem as the following integer programming problem [6].
A i ∆
Objective function (IP3):
(IP3)
∑
∈ ∆ = A i i A i IP a Z 2 minsubject to: (2), (3), (5) , (6), (8), (9), (10), (11), (12), and
jt j jt jtz r p d ≤ ∀j∈C,t∈T (24)
∑
∪ ∈ ≤ A F i ji jt jt p y z ∀j∈C,t∈T (25) i ji a y ≤ ∀j∈C,i∈A (26) 1 or 0 = i a ∀i∈A. (27)The objective function is to minimize the license fee of augmentation channels. Constraint (24) ensure service coverage constraint. Constraint (25) is a redundant constraint to combine the relationship of zjt and yjt together.
Constraint (26) is to count the number of augmentation channels used in this system. Constraint (27) enforces the integer property
6. Computational Experiments
All of the above integer programming formulation problems are NP-complete. Therefore, we use Lagrangean relaxation and subgradient method as our solution approaches. For getting primal feasible solution purpose, Lagrangean relaxation method not only get a theoretical lower bound of primal feasible solution, but also hints us to develop an efficient heuristic algorithm. The detail solution procedures of Algorithm IP1, IP2, and IP3 are described in our paper [4], [5], [6], respectively.
In computational experiments, we randomly generate sectorization network topologies as our experiment environments. In these networks, there are 5 BSs constructed by 15 smart antennas to service 20 MTs under the GSM-like environment that frequency is on 900 MHz, spectrum bandwidth is 12.5 MHz, CIR is 9 dB, average MT height is between 1 m to 10 m above local terrain height, average BS height is between 30 m to 200 m.
After several computational experiments, we compare the computational results of each Lagrangean-based algorithm with associated primal heuristics to evaluate the effective of the proposed algorithm. In admission control problem, when the average traffic requirements increase, Lagrangean-based algorithm can achieve feasible solution but primal heuristic cannot. This proposed algorithm can achieve up to 99% improvement [4]. In channel augmentation problem, the proposed algorithm achieves up to 99.4% improvement of the total call blocking rate under an omni-direction channel assignment scenario and 58.1% improvement under a generic sectorization channel
augmentation scenario [5]. Due to higher complexity of the combinative network servicing problems, we develop several primal heuristics for comparison purpose. In the experiments, whenever we increase the average traffic demands and unbalance the traffic distribution to violate the performance constraints, the network servicing algorithm will adopt mechanisms in the sequence of channel re-assignment, power control, and then channel augmentation automatically [6].
7. Conclusion
In this paper, we study the resource and performance management problems for channelized wireless networks. We propose a research framework and classify the problems into performance optimization and network servicing modules. We clarify the mechanisms for each module and formulate these mechanisms as mathematic models. Base on these models, we develop several integer programming algorithms to model both performance optimization and network servicing problems. All of solution approaches are based on Lagrangean relaxation to decompose NP-hard problems into several solvable subproblems. These algorithms are efficient and effective and worth to be applied on real wireless networks.
References
[1] S. Golestaneh, H.M. Hafez, and S.A. Mahmoud, “The effect of adjacent channel interference on the capacity of FDMA cellular systems,” IEEE Transactions on Vehicular
Technology, vol. 43, no. 4, 1994.
[2] M. Hata, “Empirical formula for propagation loss in land mobile radio services,” IEEE Transactions on Vehicular
Technology, vol. 29, pp. 317-325, 1980.
[3] I. Katzela and M. Naghshineh, “Channel Assignment Schemes for Cellular Mobile Telecommunication Systems: A Comprehensive Survey,” IEEE Personal
Communications, vol. 3, no. 3, pp. 10-31, June 1996.
[4] C-H. Lin and F.Y-S. Lin, “Admission control algorithm for wireless communication networks considering adjustable channel separation,” Proc. IEEE Canadian Conference on
Electrical and Computer Engineering, Canada, 2002.
[5] C-H. Lin and F.Y-S. Lin, “Channel augmentation algorithm for wireless networks considering generic sectorization and channel interference,” Proc. IEEE International Conference
in Mobile and Wireless Communication Networks, Brazil,
2001.
[6] C-H. Lin and F.Y-S. Lin, “Channel reassignment, augmentation and power control algorithm for wireless communications networks considering generic sectorization and channel interference,” Proc. IEEE Emerging
Technologies Symposium on Broadband Communications for the Internet Era, Texas, 2001.
[7] F.Y-S. Lin, “Quasi-static channel assignment algorithms for wireless communications networks,” Proc. ICOIN’98, Japan, January 1998.
[8] P. Malm and T. Maseng, “Adjacent channel separation in mobile cellular systems,” Proc. IEEE Vehicular Technology