Chiu, W.-Y., Tao, Y.-H., Hong, T. and Lin, W.-Y., A Unified Web Transaction Mining
with fuzzy Intentional Browsing Data, International Conference of Information
Management,Taipei, Taiwan, May 29, 2004.
A Unified Transaction Mining with Fuzzy Intentional Browsing Data
Yu-Hui Tao1 Tzung-Pei Hong1 Wen-Yuan Chiu2 Wen-Yang Lin11National University of Kaohsiung 2Lin Chin-Hsing Hospital
Abstract
Intentional browsing data (IBD) is a new data component proposed by Tao et al. (2002) to improve Web usage mining that uses Web log files as the primary data sources. As an illustration, Yun and Chen’s (2000) Web transaction mining (WTM) algorithm was used to demonstrate how IBD enhanced WTM on pages with item purchase by IWTMp (Intentional-based WTM with purchase) and complemented WTM on pages without item purchase by IWTMnp(IWTM with no purchase). Although IWTMpand IWTMnp satisfactorily illustrated the benefits of IBD on the WTM algorithm, potential practical improvements remains to be addressed. Two most obvious issues are: First, why separates the source data into purchased-item and not-purchased-item segments to be processed by two IWTM algorithms? Second, numeric IBD counts are not user friendly for decision-making purpose in practice. Accordingly, we propose a unified IWTMualgorithm that processes all pages with and without item purchase simultaneously. In addition, we transform IBD occurrence values into linguistic items using the fuzzy set concept. The comparative implications of IWTMpand IWTMnpvs. IWTMuand IWTMuf are also discussed.
Keywords: Web usage mining, Intentional Browsing Data, Web Transaction Mining, Fuzzy
1. Introduction
Web mining is defined as applying data mining techniques to Web data [2], which is further classified into Web usage mining (WUM), Web content mining and Web structure mining [1]. WUM adopts mainly the Web log records that typically include host name or IP address, remote user name, login name, date stamp, retrieval method, HTTP completion code, and number of bytes in a file retrieved (http://www.w3.org/TR/WD-logfile). The log file content has shown to be valuable, but it does not include all user interactions WUM algorithm can utilize. As a result, intentional browsing data (IBD)[3], such as scroll-bar, select, or save-as user interactions, is formally defined as a new data ingredient to be used in WUM. The benefits of IBD has been shown in estimating browsing time [4] and illustrated in Web transaction mining (WTM) algorithm [6] that explored the relationship of traveling and purchasing behavior. Specifically in the WTM case, one intentional-based WTM (IWTM) algorithm focusing on the purchased items (IWTMp) and another one on the not-purchased items (IWTMnp) were used to demonstrate the potential benefits of enhancement and complement, respectively. These modified algorithms meet their intended purpose satisfactorily, but technically why separated the data sources into purchased and not-purchased segments for two algorithms? It would be more efficient to have one unified IWTM algorithm (IWTMu) to process the whole data set at one time in practice. Moreover, IBD count is not user friendly in practical decision-making processes. Consequently, this paper addresses these two practical issues by proposing a unified IWTMuwith fuzzy
treatment on IBD (IWTMuf) and discusses the comparative implications between IWTMp, IWTMnp, IWTMu, and IWTMuf.
2. Preliminaries
The original WTM algorithm assumed one merchandise item on one Web page, which was represented as B{i1} meaning Web page B with item i1. The purpose of IWTMpis to show that a user’s interest level on an item can be represented as the occurrence of a certain IBD, which can then enhance the predicting power of the original WTM association rules. For example, an IWTMpassociation rule on the browsing path of Web pages A-B-F-G, i.e., <ABFG: B{i1, b14}. G{i6, b61}>, indicates additional information on Web page B with 4 occurrences of b1-type IBD, and on Web page G with 1 occurrence of b6-type IBD. One implication is that among users who have purchased i1on page B, the ones with higher b1-type IBD are more likely to purchase i6on page G, especially if accompanied with any b6-type IBD. Therefore, more resources and promotion strategies can be applied to those users with higher occurrences of corresponding b1and b6. On the other hand, IWTMnpis used to probe those Web pages without any purchase by IBDs. For example, <ABFG: F{0, b55}.G{0, b61}> implies that a user with browsing path A-B-F-G may not purchase anything on Web pages F and G, but has a strong potential interest on page F with 5 occurrences of b5-type IBD and some interest on page G with 1 occurrence of b6-type IBD. Therefore, a proper promotion effort may stimulate the users who have purchased neither on page F nor on G but with higher occurrences of corresponding b6and b7.
3. The Unified IWTM Algorithm with Fuzzy IBDs (IWTM
uf)
From a practical viewpoint, the purpose of a unified IWTMualgorithm is to process the whole intended data set at once by only one algorithm, while IWTMufis to add fuzzy treatment on IBDs to IWTMu. We modify and enhance the original notations, definitions and implication rules of IWTM [3] as follows. Let N = {n1, n2, ..., np-1, np} be a set of Web pages of a Web site; I = {i1, i2, ..., im-1, im} be the merchandise items listed in the Web site assuming one Web page can have only one merchandise item for sale; B = {b1
o
1,b2o
2,..., bx-1o
x1,bxo
x} be the IBDs assuming each Web page x has only one bx-type IBD associated with a number of occurrences ox, where p, m, and x are none-zero positiveintegers and need not be the same values.
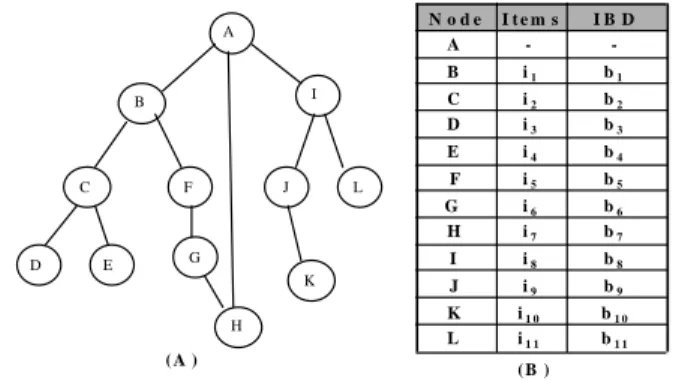
b1 0 i1 0 K b1 1 i1 1 L b9 i9 J b8 i8 I b7 i7 H b6 i6 G b5 i5 F b4 i4 E b3 i3 D b2 i2 C b1 i1 B -A I B D I t e m s N o d e ( B ) A B C D E F G H I J K L ( A )
Figure 1. A Web transaction tree and corresponding transaction data
Figure 1 illustrates a Web transaction tree with associated IBDs, where A, B, ..., L represent the Web page names and A is the entry page that usually contains no merchandise item.
Definition 1: Let {s1, s2, ..., sy} be a path sequence, where {s1, s2, ..., sy}N y
.
mx. A transaction pattern is represented as <s1, s2, ..., sy: n1{i1, b1
r
1 }, n2{i2,b1
r
1 }, …, nx{ix, b1r
1 }>, wherer
f is the fuzzy region of the f-th IBD with 1fz, and {n1, n2, ..., nx}{s1, s2, ..., sx}N y
.
Definition 3: Let <sy: X Y> be an association rule, where X and Y are both subsets of (I, B) and X∩Y =ψ.
The detailed definitions and notations of fuzzy treatment can be referred to Wang et al. [5]. Similar to either IWTMpor IWTMnp, the unified IWTMufalgorithm mines transaction patterns but with fuzzy IBDs, in which the occurrence values of IBDs are transformed into fuzzy regions for linguistic terms by the given membership functions. The procedure of IWTMufis first summarized here and an example is given in next Section:
Step 1: Sort all transaction records in ascending order of ID.
Step 2: Generate a set of 1-transaction candidate patterns C1 from Step 1 with Fuzzy IBDs.
Step 2-1: First calculate the occurrences of purchased items in each Web page without repetition. For each user, count only one for repeated purchases of the same items, but the exact occurrences of IBDs. When a user has the same IBDs in different patterns, take the minimum value as a conservative estimate for IBD potential that has yet to be realized. Then take the maximum value among all users having the same IBD occurrences. Repeat the same procedure for the counterpart of Web pages without item purchases.
Step 2-2: For each item in C1, convert the occurrence values of IBDs for each Web page into the membership values in all of the fuzzy regions according to the given membership function. An example of membership functions is shown is in Figure 2.
Figure 2. The membership function for IBDs
S
tep 2-3: The scalar cardinality of each fuzzy region in all of users is calculated as the count value.Step 2-4: The fuzzy region with the highest IBD count among all of the possible regions for each Web page is selected. A set of 1-transaction candidate patterns C1 is then completed with the semantic information of IBDs.
Step 3: Set two minimum support values, one for the patterns with item purchases and the other one without. Save all C1 items whose sums of occurrences are greater than or equal to the minimum support value into large 1-transaction patterns T1, which represents possible browsing paths for purchasing or not purchasing an item over a hurdle value.
Step 4: Generate a set of candidate 2-transaction patterns C2 by joining items in T1.
Step 4-1: According to the Web browsing sequential paths, generate a set of candidate 2-transaction patterns C2 by joining items in T1.
Step 4-2: Calculate the fuzzy membership values of all C2 patterns for all user IDs. For each C2 pattern, first take the minimum value of pattern components within the same user ID as a conservative estimate similar to Step 2-1, and then sum them up across user IDs. Repeat the same process for all C2 patterns.
Step4-3: Calculate the scalar cardinality (count) in C2 for all user IDs.
than or equal to the minimum support value into large 2-transaction patterns T2. Step 6: Repeat steps 4 and 5 until no large k-transaction sets can be generated.
IWTMuf differs from IWTMp or IWTMnp mainly on three aspects. First, all records enter into IWTMuin Step 1 and are processed differently in Step 2 for records with purchases and for records without purchases as they were in IWTMpand IWTMnp, respectively. Second, items with purchases and without purchase are joined in a mixed way after Step 3. Therefore, minimum support values can be set differently as in IWTMpor IWTMnpin Steps 3 and 5 so that IWTMuis guaranteed to cover whatever outcomes IWTMpand IWTMnphave. Third, the IBD counts in IWTMp and IWTMnpare transformed into a linguistic representation in IWTMufso that the association rules are much user friendly during business implementation in practice.
4. An Example of IWTM
ufWe illustrate IWTMufusing the example depicted in Figure 1 as follows:
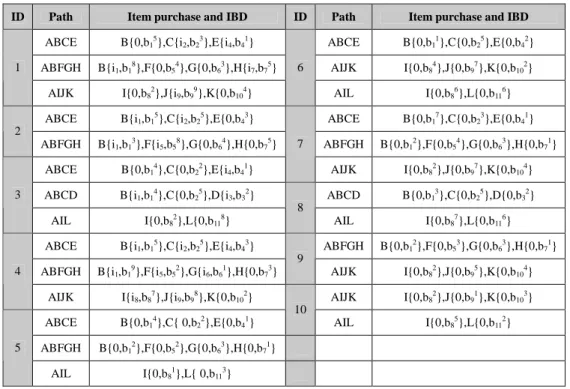
Step 1: Order user Web browsing transaction records in ascending order of ID. Table 1 lists the user IDs, Web sequential browsing paths, and sets of (item, IBD) which represent purchase states and corresponding IBD occurrences. Notice that every path contains both items with purchase and without purchase, such as B{0,b15}, C{i2,b23}, E{i4,b41} exists in ABCE path for user ID 1, where item 0 represents no purchase.
Table 1. The list of general transaction patterns by user ID
ID Path Item purchase and IBD ID Path Item purchase and IBD ABCE B{0,b15},C{i2,b23},E{i4,b41} ABCE B{0,b11},C{0,b25},E{0,b42}
ABFGH B{i1,b18},F{0,b54},G{0,b63},H{i7,b75} AIJK I{0,b84},J{0,b97},K{0,b102}
1
AIJK I{0,b82},J{i9,b99},K{0,b104}
6
AIL I{0,b86},L{0,b116}
ABCE B{i1,b15},C{i2,b25},E{0,b43} ABCE B{0,b17},C{0,b23},E{0,b41}
2
ABFGH B{i1,b13},F{i5,b58},G{0,b64},H{0,b75} ABFGH B{0,b12},F{0,b54},G{0,b63},H{0,b71}
ABCE B{0,b14},C{0,b22},E{i4,b41}
7
AIJK I{0,b82},J{0,b97},K{0,b104}
ABCD B{i1,b14},C{0,b25},D{i3,b32} ABCD B{0,b13},C{0,b25},D{0,b32}
3
AIL I{0,b82},L{0,b118}
8
AIL I{0,b87},L{0,b116}
ABCE B{i1,b15},C{i2,b25},E{i4,b43} ABFGH B{0,b12},F{0,b53},G{0,b63},H{0,b71}
ABFGH B{i1,b19},F{i5,b52},G{i6,b61},H{0,b73}
9
AIJK I{0,b82},J{0,b95},K{0,b104}
4
AIJK I{i8,b87},J{i9,b98},K{0,b102} AIJK I{0,b82},J{0,b91},K{0,b103}
ABCE B{0,b14},C{ 0,b22},E{0,b41} 10 AIL I{0,b85},L{0,b112} ABFGH B{0,b12},F{0,b52},G{0,b63},H{0,b71} 5 AIL I{0,b81},L{ 0,b113}
Step 2: Generate the candidate set C1 from all the pages with or without item purchases.
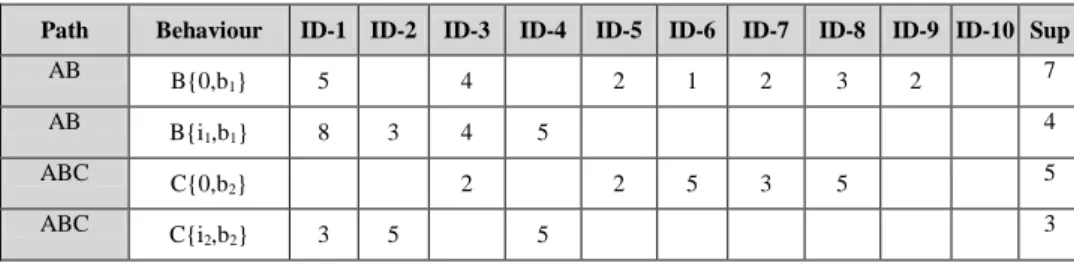
Step 2-1: For the with-purchase illustration, user ID 2 in Table 1 has purchased i1on page B twice, namely B{i1,b15} and B{i1,b13}, which is only counted once. Among the ten users of IDs, only 1-4 had purchased i1on page B, which leads to a support value of 4 for i1purchase on page B. Similar process On the IBD, the frequency of b1is calculated first as the minimum value for each user. For the with-purchase illustration, user ID 2 in Table 1 has purchased i1on page B twice, namely B{i1,b15} and B{i1,b13}, which is calculated as min(b15, b13) = b13. That is, the IBD
occurrence value is 3 for user ID 2 on page B. On the other hand, B{0, b15} of path AB, the counterpart of B{i1, b1
8
}, is obtained similarly with 0 item purchase and max{b15, b14, b12, b11, b12, b13, b12}= b15 from IDs 1, 3, 5, 6, 7, 8 and 9.This calculation is repeated for all users with purchase items and without purchase items as seen in Table 2. Due to the length of the tabulation, only partial results were listed in Table 2.
Step 2-2: The occurrences values of IBDs for each user on Web page from Table 2 are converted into the fuzzy sets by the given membership function in Figure 2. For instance, the IBD value of B{0,b1} for user ID-3 is 4, which is converted into the fuzzy set (0.25/Low+0.75/middle +0/High). The complete result of items in Table 2 can be seen in Table 3, in which each item has their values in the regions of Low, Middle, and High.
Step 2-3: The scalar cardinality of each fuzzy region in all of users is calculated as the count value. Take the Low fuzzy region for Web page B without purchase, B{0,b1L} as an example, its scalar cardinality equals to (0.0+0.0+0.25+0.0+0.75+1.0+0.75+0.5+0.75 +0.0)=4 as indicated in the last column of Table 3. This step is repeated for all other regions, and for all behavior items.
Table 2. The occurrence values of IBD for All user IDs
Path Behaviour ID-1 ID-2 ID-3 ID-4 ID-5 ID-6 ID-7 ID-8 ID-9 ID-10 Sup
AB B{0,b 1} 5 4 2 1 2 3 2 7 AB B{i 1,b1} 8 3 4 5 4 ABC C{0,b 2} 2 2 5 3 5 5 ABC C{i 2,b2} 3 5 5 3
Table 3 The counts of fuzzy regions for candidate sets C1
Behaviour Region ID-1 ID-2 ID-3 ID-4 ID-5 ID-6 ID-7 ID-8 ID-9 ID-10 Count
Low 0.25 0.75 1 0.75 0.5 0.75 4 Middle 1 0.25 0.25 0.25 0.5 0.25 2.5 B{0,b1} High 0 Low 0.5 0.25 0.75 Middle 0.25 0.5 0.75 1 2.5 B{i1,b1} High 0.75 0.75 Low 0.75 0.75 0.5 2.0 Middle 0.25 0.25 1 0.5 1 3 C{0,b2} High 0 Low 0.5 0.5 Middle 0.5 1 1 2.5 C{i2,b2} High 0
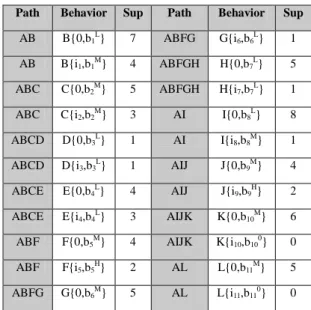
Step 2-4: The fuzzy region with the highest count among the three possible regions for each Web page is selected. Take B{0,b1} as an example, its counts are 4 for Low(L), 2.5 for Middle (M), and 0 for High(H). Since the count for Low is the highest among the three counts, the region Low is thus used to represent the occurrences of IBD for behavior item B{0,b1} in later miming process as shown in the first path AB by B{0,b1L} in Table 4 with support value (Sup) 7. Notice that Sup is
calculated in Step 2-1 as explained earlier. This step is repeated for all other IBDs. Steps 2-2 to 2-4 completed the fuzzy treatment of IBD counts and thus the complete C1 is as shown in Table 4.
Table 4. 1-Transaction pattern candidate set (C1) Path Behavior Sup Path Behavior Sup
AB B{0,b1L} 7 ABFG G{i6,b6L} 1
AB B{i1,b1M} 4 ABFGH H{0,b7L} 5
ABC C{0,b2M} 5 ABFGH H{i7,b7L} 1
ABC C{i2,b2M} 3 AI I{0,b8L} 8
ABCD D{0,b3L} 1 AI I{i8,b8M} 1
ABCD D{i3,b3L} 1 AIJ J{0,b9M} 4
ABCE E{0,b4L} 4 AIJ J{i9,b9H} 2
ABCE E{i4,b4L} 3 AIJK K{0,b10M} 6
ABF F{0,b5M} 4 AIJK K{i10,b100} 0
ABF F{i5,b5H} 2 AL L{0,b11M} 5
ABFG G{0,b6M} 5 AL L{i11,b110} 0
Step 3: Assume the minimum support value for item purchase is 2 and for no item purchase is 6. The rationale for the different minimum support values is because a practical Website would have more no-purchased transactions than purchased transactions among all records. Therefore, a higher initial minimum support value on no-purchase transactions will quickly filter out an insignificant portion of no-purchase items. Save the transaction patterns with purchases whose support values are greater than or equal to 2 in large 1-transaction pattern set T1. Similarly, save the transaction patterns without purchase whose support values are greater than or equal to 6 in large 1-transaction pattern set T1, as seen in Table 5.
Table 5. Large 1-Transaction Pattern Set (T1) Path Behavior Sup Path Behavior Sup
AB B{0,b1L} 7 ABF F{i5,b5H} 2
AB B{i1,b1M} 4 AI I{0,b8L} 8
ABC C{i2,b2M} 3 AIJ J{i9,b9H} 2
ABCE E{i4,b4L} 3 AIJK K{0,b10M} 6
Step 4: Generate a set of candidate 2-transaction patterns C2 by joining items in T1.
Step 4-1: According to the Web sequential browsing paths, generate 2-transaction pattern candidate set C2 from T1 by joining items in T1 as shown in Table 6. Notice that Sup value is determined by the occurrence counts of the behavior items found in Table 1. If the count is 0, then the 2-transaction pattern is not shown in Table 6.
Table 6. 2-Transaction Pattern Candidate Set (C2)
Path Behavior Sup Path Behavior Sup
ABC B{i1,b1M} C{i2,b2M} 2 AIJ I{0,b8L} J{i9,b9H} 1
ABCE B{0,b1L} E{i4,b4L} 2 AIJK I{0,b8L} K{0,b10M} 5
ABCE B{i1,b1M} E{i4,b4L} 1 AIJK J{i9,b9H} K{0,b10M} 2
ABCE C{i2,b2M} E{i4,b4L} 2
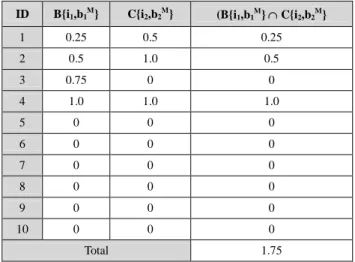
Step 4-2: For each user ID, the fuzzy membership values of each 2-transaction pattern in candidate set C2 is calculated. Here, the minimum operator is used for the intersection. Take <ABC: B{i1,b1M} C{i2,b2M}> as an example, its membership value for ID-1 in Table 3 is calculated as min(0.25, 0.5) = 0.25. The overall membership value for <ABC: B{i1,b1M} C{i2,b2M}> is 1.75 by adding up membership value of IDs 1-10 as show in Table 7.
Table 7 The membership values for <B{i1,b1 M
} C{i2,b2 M
}> of all users.
ID B{i1,b1M} C{i2,b2M} (B{i1,b1M}C{i2,b2M}
1 0.25 0.5 0.25 2 0.5 1.0 0.5 3 0.75 0 0 4 1.0 1.0 1.0 5 0 0 0 6 0 0 0 7 0 0 0 8 0 0 0 9 0 0 0 10 0 0 0 Total 1.75
Step 4-3: The scalar cardinality (count) of each candidate 2-itemset in C2is calculated as can be seen in Table 8.
Step 5: Assuming both minimum support values are set to 2, only those patterns whose support values are greater than or equal to 2 are kept in large 2-transaction pattern set T2 as seen in Table 9. Step 6: According to the Web sequential browsing paths, generate 3-transaction pattern candidate set
C3 by joining itemsets from T2, as seen in Table 10. Because all the support values are less than the minimum support value 2, this algorithm ends here. Accordingly, the final results generate seven association fuzzy rules as suggested by T2 in Table 9.
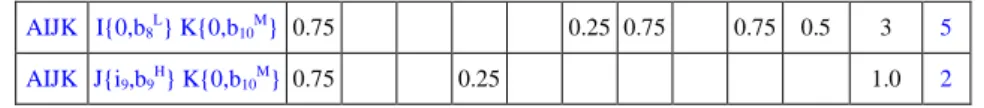
Table 8. 2-transaction pattern candidate set with fuzzy counts Path Behavior ID-1 ID-2 ID-3 ID-4 ID-5 ID-6 ID-7 ID-8 ID-9 ID-10 Count Sup
ABC B{0,b1L} C{i2,b2M} 0 1
ABCE B{0,b1L} E{i4,b4L} 0.25 0.25 2
ABC B{i1,b1M} C{i2,b2M}0.25 0.5 1.0 1.75 2
ABCE B{i1,b1M} E{i4,b4L} 0.25 0.75 0.5 1.5 1
ABCE C{i2,b2M} E{i4,b4L} 0.5 0.5 1.0 2
ABF B{i1,b1M} F{i5,b5H} 0.5 0.5 2
AIJK I{0,b8L} K{0,b10M} 0.75 0.25 0.75 0.75 0.5 3 5
AIJK J{i9,b9H} K{0,b10M}0.75 0.25 1.0 2
Table 9. Large 2-transaction pattern set (T2) Path Behavior Count Sup
ABCE B{0,b1L} E{i4,b4L} 0.25 2
ABC B{i1,b1M} C{i2,b2M} 1.75 2
ABCE C{i2,b2M} E{i4,b4L} 1.0 2
ABF B{i1,b1M} F{i5,b5H} 0.5 2
AIJK I{0,b8L} K{0,b10M} 3 5
AIJK J{i9,b9H} K{0,b10M} 1.0 2
Table 10. 3-transaction pattern candidate set (C3)
Path Behavior Sup
ABCE B{0,b1L} C{i2,b2M} E{i4,b4L} 1
ABCE B{i1,b1M} C{i2,b2M} E{i4,b4L} 1
AIJK I{0,b8L} J{i9,b9H} K{0,b10M} 1
The derived rules from IWTMp, IWTMnp ,IWTMuand IWTMufare listed in Table 11. As we can see, the unified IWTMu algorithm not only covers all the (first four) rules derived from both IWTMpand IWTMnp, but also generates two new rules by rejoining the split data sets. In other words, IWTMucan efficiently obtain the same results as in IWTMpand IWTMnpwhile simultaneously enriching the rule base of previous IWTM algorithms. For instance, the new rule <ABCE: B{0,b15}E{i4,b43}> implies that an average user who did not purchase on page B but with high interest level of b1
5
-type IBD may purchase items on Web pages E with high levels of b15-type or b43-type IBDs, respectively. In practice, we can allocate more resources to promote any user who has presented a high occurrence of b1-type IBD on page B for potential purchase on page E. Furthermore, more dedicated strategies can be deployed based on the interest levels of b15, so that more accurate customer targeting and marketing performance can be achieved.
On the other hand, rules derived by IWTMufand IWTMuare identical except that the IBD counts in IWTMuare replaced by IBD linguistic terms L/H/M in IWTMuf.As a result, the IBD is expressed in a more natural and understandable way for decision makers to apply the association rules in practice.
Table 11. Comparisons of IWTMu, IWTMp, IWTMnpand IWTMuf
Algorithm Transaction Behavior Rules Implications to WTM IWTMp
(with purchase)
<ABC: B{i1,b18}C{i2,b25}>
<ABF: B{i1,b18}F{i5,b58}>
<ABCE: C{i2,b25}E{i4,b43}>
IWTMnp
(without purchase) <AIJK: I{0,b87}K{0,b104}> Complement
IWTMu
(unified algorithm)
<ABC: B{i1,b18}C{i2,b25}>
<ABF: B{i1,b18}F{i5,b58}>
<ABCE: C{i2,b25}E{i4,b43}>
<AIJK: I{0,b87}K{0,b104}> <ABCE: B{0,b15}E{i4,b43}> <AIJK: J{i9,b99} K{0,b104}> Complete enhancement & complement IWTMuf
(unified algorithm with fuzzy IBD)
<ABC: B{i1,b1M}C{i2,b2M}>
<ABF: B{i1,b1M}F{i5,b5H}>
<AIJK: I{0,b8L}K{0,b10M}>
<ABCE: C{i2,b2M}E{i4,b4L}> <ABCE: B{0,b1L}E{i4,b4L}> <AIJK: J{i9,b9H} K{0,b10M}> Complete Enhancement & Complement with semantic IBD expression
6. Conclusions
This paper focuses on practical improvements that were not addressed in the illustrative work [3] regarding how potential benefits could be brought into the traditional WTM algorithm. We have successfully shown that how a unified IWTMualgorithm could produce the same outcomes of IWTMp and IWTMnpalgorithms as well as derive additional association rules. Moreover, IBD counts in derived association rules were converted to a more readable expression of linguistic terms via the fuzzy set concept. In other words, IWTMufis an efficient replacement of IWTMpand IWTMnpalgorithms and an effective improvement on the volume of useful association rules in practical business applications.
7. References
[1] S.K. Madria, S.S. Bhowmick,W. K. Hg and E. P. Lim, Research issues in Web data mining, The First International Conference on Data Warehousing and knowledge Discover (1999), 303-312.
[2] E. Oren, The World Wide Web: quagmire or gold mine, Communications of the ACM 39 (1996), 65-68.
[3] Y.H.Tao, Y. M. Su, and T.P.Hong, Web transaction mining algorithm with intentional behaviour, The Sixth International Conference on Knowledge-Based Intelligent Engineering Systems & Allied Technologies (2002), Italy.
[4] Y. H. Tao, T.P.Hong and Y.M. Su, Improving browsing time estimation with intentional behavior data, International Journal of Computer Science and Network Security 6(12) (2006), 35-39.
[5] S.L. Wang, W. S. Lo and T. P. Hong, Discovery of fuzzy multiple-level Web browsing patterns, in Proceedings of the International Conference on Fuzzy Systems and Knowledge Discovery (2002), Singapore.
[6] C.H. Yun, and M. S. Chen, Using pattern-join and purchase-combination for mining transaction patterns in an electronic commerce environment, The 24th Annual International Conference on Computer Software and Applications (2000), Taiwan, 99-104.