基於智慧卡之使用者身分辨識之設計與應用 - 政大學術集成
全文
(2) 摘 要 隨著網際網路的普及化,使用者在遠端即可存取系統資料或是使用系統所提 供之資源,為了防止非法入侵電腦系統以及保護系統的安全,所以身份驗證是一 件很重要的工作。近來,隨著目前科技進步,IC 智慧卡已是一個攜帶方便且具 備安全性及計算能力的儲存載具, 其應用範圍相當廣泛,因此,透過 IC 智慧卡 作為身分辨識的通行驗證的協定技術,以確保個人存取資料之安全,也是現今許 多學者愈來愈重要之考量。然而目前大部份已被提出之智慧卡作為身分辨識之安 全通行協定,系統與使用者端都須事先建立公開金鑰系統 這可能對智慧卡造成 計算量與記憶體之負擔。於 2013,Guo 和 Chang 學者基於混沌對應( chaotic maps) 之原理,且不須使用公開金鑰系統,提出一個適用於智慧卡且具使用者匿名(user anonymity) 性質的身分辨識,防止被追蹤與保護使用者的資訊安全。但是,我 們發現他們所提之方法並不具有匿名(user anonymity) 性質,且無法提供使用者 自行可任意更改其密碼,需透過遠端系統之運算才行。因此,本研究提出了一個 身分辨識驗證的改進方式,適用於智慧卡且具匿名(user anonymity) 性質,即使 當智慧卡內之儲存內容遭讀取時,我們之協定仍然能確保使用者與遠端系統的安 全性,且所提之研究方法更適於智慧卡與行動裝置之使用者。 另一方面,由於科技之進步,讓社會大眾得以透過網路於各個不同之伺服器 端來存取資源,使得遠端使用者身份辨識於多重伺服器存取資源的安全越來越重 要。然而,目前被提出的單一註冊之遠端身份辨識於多重伺服器存取的安全協 定,大部份易遭受非法攻擊,例如:內部攻擊,密碼猜測攻擊,與偽造攻擊等。 因此,本研究基於混沌對應( chaotic maps)亦提出一個新的認證協定於多重伺服 器存取安全之研究,以利不同環境之使用,所提之方法除了能提高驗證階段的效 率且能符合各種不同之安全性質,以確保使用者與遠端系統之安全。 關鍵詞: 匿名性,身份辨識,混沌對應(chaotic maps),多重伺服器. 1.
(3) Abstract User authentication is an important technology to guarantee that only the legal users can access resources from the remote server. Recently, the smart card based password authentication scheme became more and more important and functional. There are many mutual authentication protocols with user anonymity proposed in literature for preventing unauthorized parties from accessing resources through insecure environment. However, most of them are based on smart cards have to establish public key cryptosystems in advance. To solve the problem, in 2013, based on chaotic maps, Guo and Chang proposed an efficient mutual authentication protocol with user anonymity for the smart card. Unfortunately, this study will demonstrate their scheme could not achieve the user anonymity property, and do not allow changing password freely for the user. Then, we proposed a new method to remedy the weaknesses. The proposed method is secure even if the secret information stored in the smart card is compromised. Only one-way hash function and simple polynomial computations are involved in our protocol. It is more suitable for practice implementation.. In addition, ubiquitous computing has become very popular where multiple servers are involved in authenticating their users. Single registration and user authentication are important issues for multi-server environments. However, most of them are still vulnerable to various security problems. In this study, based on the Chebyshev chaotic maps, we will propose a new user authentication protocol for multi-server networks. Our protocol not only could withstand various attacks but also provide much better performance when compared to other related protocols.. Keywords: anonymity; user authentication; chaotic map, multi-server. 2.
(4) 誌謝 首先誠摯的感謝指導教授左瑞麟老師這兩年來的指導,讓我得以一窺資訊安全 領域的深澳,謝謝老師適時的指點我研究的方向,讓我在學習時獲益良多。學生 在此也特別感謝蒞臨指導的口試委員:楊中皇教授、李南逸教授、范俊逸教授與 王智弘教授,對於我的碩論提供許多寶貴的意見,讓我的這篇論文更趨完整。. 在這兩年的日子裡,感謝實驗室的學長姐們給我的協助與諮詢,讓我的研究能 更順利,也謝謝同屆的同學們給我的鼓勵與各種幫助,讓我在遇到困難時,能不 畏縮、正面的思考總能迎刃而解,也因為有妳們的陪伴,讓我這兩年的研究生活 精彩充實、積極愉快。. 最後我要感謝我最愛的家人,感謝父母養育我、包容我、關心我,總是給我鼓 勵與溫暖的支持,讓我得以完成我的研究與這篇論文。感謝家人時時刻刻的陪 伴,陪我度過各種難關。謝謝你們的關懷與幫助,才能讓我的研究論文得以順利 完成。. 3.
(5) Contents 摘要.............................................................................................................................. 1 Abstract ..................................................................................................................... 2 Chapter 1 Introduction...................................................................................... 6 1.1 Research Motivation and Background .....................................................6 1.2 Dissertation Organization ................................................................................8 Chapter 2 Related Works ............................................................................... 10 2.1 Preliminary ............................................................................................................10 2.2 Review of Guo and Chang’s Scheme .....................................................11 2.3 Security analysis of Guo and Chang’s Scheme .................................14 Chapter 3 A Secure and Efficient Password Authentication with Smart Card Based on Chaotic Maps ........................................................ 16 3.1 The Proposed Scheme .....................................................................................16 3.2 Discussions ............................................................................................................19 3.2.1 Security Analysis .......................................................................................19 3.2.2 Performance ..................................................................................................23 3.3 Summary .................................................................................................................24 Chapter 4 An Efficient User Authentication with Smart Card for Multi-Server Networks ............................................................................ 26 4.1 Preliminary ............................................................................................................27 4.1.1 Review of Li et al.’s Protocol .............................................................27 4.1.2 Security analysis of Li et al.’s Protocol .........................................30 4.2 The Proposed Scheme .....................................................................................32 4.3 Discussions ............................................................................................................36 4.3.1 Security Analysis .......................................................................................36 4.3.2 Performance ..................................................................................................39 4.
(6) 4.4 Summary .................................................................................................................41 Chapter 5 Conclusions and Future Researches .................................. 42 Reference ................................................................................................................ 44. 5.
(7) Chapter 1 Introduction . Recently, more and more people have relied on computer networks to access information, exchange knowledge, and process data in distributed network environments, and then the network security has been becoming important. User authentication is an important technology to guarantee that only the legal users can access resources from the remote server. To achieve simplicity, efficiency and low-communications, the techniques of user authentication based on smart cards are becoming more and more important in today’s network environment.. 1.1 Research Motivation and Background With rapid development of the network technology, password based authentication has been widely used in many areas, such as the remote access control systems, medical systems, banking and payment systems and so on [1]. Currently, due to the cryptographic capacity, low cost, and the portability, the smart card-based authentication scheme is becoming more and more important and functional [2,3,5,7]. There are many remote user authentication protocols with smart card have been proposed to improve security, efficiency, and functionality extensively by many scholars in recent years [2-14]. Moreover, the compromise of user’s identity would lead to the tracing of the previous network communications for the same user. To protect from the risk of ID-theft, the user anonymity property is required for the privacy protection user [9,10]. In 2008, Juang et al.’s [12] proposed a new password-authenticated key agreement protocol based on elliptic curve cryptosystems. Their scheme not only could provide identity protection but also construct the session key agreement and enhance efficiency by using elliptic curve cryptosystems. Unfortunately, Sun et al.’s proposed an improved scheme to overcome the weakness of Juang et al.’s, including inability of the password-changing and the session key problem. 6.
(8) [13]. Later, there are many password based authentications with smart card have been proposed to achieve the user anonymity [9,10,11,16,17,20]. Due to the smart card usually does not support powerful computation capability, new secure authentication protocols with less calculation in the smart cards are required[12,13,16,17,20]. In 2013, based on Chebyshev chaotic maps, Guo and Chang firstly proposed password-authenticated key agreement protocol using smart card [20].Their scheme is efficient since no time-consuming modular exponential computing and scalar multiplication on elliptic curve cryptosystem are involved in the authentication processes. They claimed that their protocol is able to provide user anonymity even though the adversary could extract the data stored in the smart card. However, we will show that Guo and Chang’s scheme is still vulnerable to the impersonation attack by using data extracted from his own smart card, and do not allow changing password freely for the user. Moreover, their scheme cannot provide the user anonymity. Then, in this study, we will propose improved method to overcome Guo and Chang’s security weaknesses. And our improved scheme needs not to create public key cryptosystems in advance. Nowadays, ubiquitous computing has become very popular where multiple servers are involved in authenticating their users. Namely, a user can login different servers through mobile networks to obtain diversified services. In traditional remote login methods for a multi-server architecture, a user not only has to log into various remote servers with repetitive registration, but also needs to remember the various user identities and passwords. This will make password authentication extremely inconvenient. In 2004, Lee and Chang proposed a user identification and key distribution scheme for multi-server networks [29]. In their scheme, the user registered at the registration center once and can use all the designated servers for the services. Later, many convenient authentication schemes with smart cards have subsequently been proposed for the multi-server environments [30-34]. In multi-server environments, single registration to a trusted registration center is the most 7.
(9) important feature and any user could receive desired services from various service providers without repeating registration. Due to the limitation of computational power, a smart card may not be able to afford heavy computations. In 2008, for enhancing the system performance, Tsai suggested lightweight computations such as one-way hash function during multi-server authentication processes using smart cards [28]. Recently, there are many hash-based authentication schemes with smart card have been proposed in multi-server environments. Unfortunately, most of them are vulnerable to masquerade attack, insider attack, and the server or the registration center spoofing attack [21,27,35-36]. For enhancing the security of multi-server networks, in 2011, Chang and Cheng proposed a secure and lightweight user authentication method for multi-server architecture [35]. Unfortunately, Li et al. pointed out that Chang and Cheng’s scheme still suffers from insider attack, smart card lost attack, and session key disclosure attack, and then they also proposed an improvement to overcome Chang and Cheng’s problems [36]. Furthermore, we will find that Li et al.’s scheme is still vulnerable the off-line password guessing attack. Moreover, in Li et al.’s scheme, it is required registration center to join the authentication and construct the common session key for user and the remote service providers. It will make the registration center to be another security and performance bottleneck, which will bring more communication and computing overlay. Therefore, based on the Chebyshev chaotic maps [15,19], we will propose a new efficient user authentication protocol for multi-server networks in this dissertation.. 1.2 Organization The remainder of this study is organized as follows. In the next chapter, we give some related works that will allow us to discuss the security in this dissertation. Based on chaotic maps, we will present a new user authentication with smart card in chapter 3. In chapter 4,. 8.
(10) we will design an efficient user authentication with smart cards for the multi-server environment. Finally, some conclusions and future researches are stated in the last chapter.. 9.
(11) Chapter 2 Related Works Based on the Chebyshev chaotic maps, we propose the applications of user authentication with smart card in this dissertation. Therefore, in Subsection 2.1, we introduce the properties of Chebyshev chaotic maps [15]. Guo and Chang’s chaotic maps-based password-authenticated key agreement using smart cards is reviewed in Subsection 2.2, and the security analysis of Guo and Chang’s scheme is described in Subsection 2.3.. 2.1 Preliminary Before a new improvement password-authenticated key agreement protocol based on chaotic maps is proposed, this session first introduces the properties of Chebyshev chaotic maps that will allow us to discuss the security of the proposed methods in Chapter 3 and 4 [15,16,19,20]. Definition and properties of Chebyshev chaotic maps: Let n be an integer number and x be a variable with the interval [1,1] ; Chebyshev polynomial map Tn : R R of degree n is defined by the following recurrent relation:. Tn ( x) 2 xTn1 ( x) Tn2 ( x) , where n 2 , T0 ( x) 1 , and T1 ( x) x . For example: the first some Chebyshev polynomials are T2 ( x) 2 x 2 1, T3(x) = 4x3 - 3x , T4 ( x) 8x 4 8x 2 1 .. One of the most important properties is that Chebyshev polynomials establishes that Tr(Ts(x))=Trs(x). and. the. consequence. property. is. the. computation. under. composition Tr (Ts ( x)) Ts (Tr ( x)) . In order to enhance the security, Zhang proved that property holds for Chebyshev polynomials defined on interval (, ) [19]. In this article, we use the enhanced Chebyshev polynomials: Tn ( x) 2 xTn1 ( x) Tn2 ( x) mod N , where 10.
(12) n 2 , x (, ) , and N is a large prime number. And it is obvious that. Tr (Ts ( x)) Ts (Tr ( x)) Trs ( x) . Key agreement protocol based on Chebyshev chaotic maps: In 2007, under the Diffie-Hellman protocol concept, Xiao et al. [15] proposed a key agreement protocol based on Chebyshev chaotic maps: (1) User A and B choose a random number x (1,1) together. (2) A selects a random larger integer r and computes X Tr ( x) , and then sends X to B. (3) B randomly selects a larger integer s and computes Y Ts ( x) , and then sends Y to A. (4) A and B could compute the secret key k Tr (Y ) Ts ( X ) Trs ( x) . Owing to the property Tr (Ts ( x)) Ts (Tr ( x)) Trs ( x) , A and B could construct the common secret key for the secure communication.. 2.2 Review of Guo and Chang’s scheme This subsection briefly reviews Guo and Chang’s chaotic maps-based password authenticated key agreement protocol [20]. Their protocol consists of four phases: (1) the parameter generation phase; (2) the registration phase; (3) the authentication phase; and (4) the password change phase. Parameter generation phase: In this phase, the server S needs to choose some parameters as follows: (1) The server chooses a public key scheme based on Chebyshev chaotic maps, and its public key is ( x, Ts ( x)) and its private key is s. (2) The server S selects a secure one-way hash function h( ). (3) The server S selects a symmetric key cryptosystem with encryption Ek ( ) and decryption Dk ( ) , where k is the corresponding of symmetric key. Registration phase: If the user U with identity ID would like to register or reregister with the server S, U and 11.
(13) S will perform the following steps: Step 1. The user U selects a password pw and a random number b and computes. h( pw b) , where “. ” is string concatenation operator. Then, the user U submits his/her. identity ID and the value h( pw b) to the server S for registration over a secure channel. Step 2. If the ID is valid, the server S computes IM EKS ( ID h( pw b)) , where KS is the master key of the server S. Step 3. S stores the data {IM, h( ), Ek ( ) , x, Ts ( x) } into a new smart card, and issues this smart card to the user U through a secure channel. Step 4. U stores the random number b into the smart card. Authentication phase: After completing this phase, the user U and the server S can achieve the mutual authentication and establish a common session key used in communication. If U wants to log into the server S, then U and the server S will perform the following steps: Step 1. The user U first inserts his/her smart card into a card reader and inputs the password pw. Step 2. The smart card selects a random number u and computes KA Tu (Ts ( x)) . The smart card further computes EKA (hpw IM T1 ) , where hpw h( ID h( pw b)) . Then the smart card sends the message {IM , Tu ( x), EKA (hpw IM T1 )} to the server S, where T1 is the current timestamp of the smart card. Step 3. Upon receiving the message {IM , Tu ( x), EKA (hpw IM T1 )} , the server S computes. KA Ts (Tu ( x)) Tu (Ts ( x)) using his/her private. key s, and. further decrypts. EKA (hpw IM T1 ) with the key KA. Then, the server S checks whether T * T1 T , where T * is the time of receiving the login message and T is the time threshold.. 12.
(14) Step 4. The server S decrypts IM using his/her master key KS and obtains ID and h( ID h( pw b)) and checks whether h( pw b) . Then, the server S computes hpw. hpw . If the verification is false, the server S terminates this session. If the hpw. verification is successful, the server S believes that the user U is valid. Step 5. The server S selects a random number s and computes Ts ( x) . Then, the server S computes EKA (Ts ( x) h( ID T2 ) T2 ) and sends this message to the smart card, where T2 is the server S’s current timestamp of the system. Step 6. After receiving the message EKA (Ts ( x) h( ID T2 ) T2 ) , the smart card decrypts this message using KA and obtains T2 . Then it compares whether the delay time is acceptable. The. smart. card. further. computes h( ID T2 ) ,. and. compares. whether. h( ID T2 ) h( ID T2 ) . If the equation holds, the server is authenticated by the smart card. Step 7. The user U and the server S could compute the common session key SK Tu (Ts ( x)) Ts (Tu ( x)) , respectively. Password change phase: In Guo and Chang’s scheme, if the user U wants to change his/her password, he/she performs the following steps: Step 1. The user U inserts his/her smart card into a card reader, enters the old password pw, and requests to change the password. Then, the user U enters the new password pw * . Step 2. The smart card first computes the h( pw b) and the new h( pw * b) . Then. the smart card selects a random number u and computes EKA (h( pw b), h( pw * b), IM ) , where. KA Tu (Ts ( x)). .. Next,. the. smart. {EKA (h( pw b), h( pw * b), IM ), Tu ( x)} to the server. 13. card. sends. the. message.
(15) Step 3. Upon receiving this message {EKA (h( pw b), h( pw * b), IM ), Tu ( x)} , the server. KA Ts (Tu ( x)) and. computes. decrypts. EKA (h( pw b), h( pw * b), IM ) and. IM. using KA and KS, respectively. Then the server checks whether h( pw b) h( pw b) . If the equation holds, the server computes IM * EKS ( ID h( pw * b) , and then replaces IM with IM * for the smart card.. 2.3 Security analysis of Guo and Chang’s scheme Based. on. Chebyshev. password-authenticated. key. chaotic. maps,. agreement. Guo. protocol.. and In. Chang the. proposed. enhanced. a. new. Chebyshev. polynomials: Tn ( x) 2 xTn1 ( x) Tn2 ( x) mod N , where n 2 , T0 ( x) 1 , T1 ( x) x , x (, ) , and N is a larger prime number. It is obvious that if given x and s, it is easy to. compute Ts ( x) y ; however, given y, it is very hard to find the exact parameters x and s such that y Ts ( x) . There are many pairs x and s such that y Ts ( x) .The probability of obtaining the exact x and s are equivalent to performing an exhaustive search on y Ts ( x) . Therefore, without the knowledge of x and s, it is very difficult for someone to impersonate the server to compute. Ts ( x). .. On. the. other. hand,. from. the. recurrent. relation. Tn ( x) 2 xTn1 ( x) Tn2 ( x) mod N , given y and x, it is computationally tractable to obtain s such that y Ts ( x) when s is not large enough. In Guo and Chang’s scheme [20], they claimed that their scheme could achieve user identity anonymity property. It means that the adversary cannot find out the true user’s ID by intercepting the communication message {IM , Tu ( x), EKA (hpw IM T1 )} in their authentication phase, where IM EKS ( ID h( pw b)) . The user’s ID information is encrypted by using the server’s master KS and common session key KA. Even though the secret data {IM, h( ), Ek ( ) , x, Ts ( x) }stored in the smart card are compromised, the adversary also cannot obtain any 14.
(16) information about the user’s ID from IM. Since the user’s ID combined with a random number b is encrypted by server’s master key KS. The corresponding message IM EKS ( ID h( pw b)) is stored in the smart card.. However,. in. their. scheme,. when. U. sends. the. login. request. message. {IM , Tu ( x), EKA (hpw IM T1 )} to remote server S, IM is always kept the same parameter from U.. The attacker can use IM to distinguish each user and to be seen as user’s identification. Then, the adversary is able to find any relation between any readings of the same user. Therefore, their scheme uses IM as an identity (ID), it cannot actually provide the advantage of the user’s anonymity property. In the registration phase of Guo and Chang’s scheme [20], the server S stores the data {IM, h( ), Ek ( ) , x, Ts ( x) } into a new smart card, and issues this smart card to the user U, where s is server’s private key. Now suppose that the adversary (someone U a ) could extract the data x and Ts ( x) which stored on U a s smart card. With the message communication , then it is computationally to find u from given the values x and Tu ( x) when u is not large enough. With the communication message {IM , Tu ( x), EKA (hpw IM T1 )} , then the adversary could compute KA Tu (Ts ( x)) and decrypt EKA (hpw IM T1 ) with the key KA when u is not large enough. Thus, the adversary could obtain hpw and impersonate the user U for the future communication. Hence, the adversary U a could attack and access the system. In this situation, Guo and Chang could not provide secure password-authenticated key agreement protocol based on Chebyshev chaotic maps. Therefore, Guo and Chang’s protocol also relies on the hard problem of high-degree polynomials when the smart card’s data x and Ts ( x) are extracted. Moreover, in Guo and Chang’s scheme, the user cannot freely change his/her password without the remote server joining this password change phase.. 15.
(17) Chapter 3 A Secure and Efficient Password Authentication with Smart Card Based on Chaotic Maps There are many mutual authentication protocols with user anonymity proposed in literature for preventing unauthorized parties from accessing resources through insecure environment. However, most of them are based on smart cards have to establish public key cryptosystems in advance. To solve the problem, in 2013, based on chaotic maps, Guo and Chang proposed an efficient mutual authentication protocol with user anonymity for the smart card. Unfortunately, in subsection 2.3, we have demonstrated that their scheme could not achieve the user anonymity property, and do not allow changing password freely for the user. In this chapter, we will propose improved method to overcome Guo and Chang’s security weaknesses. Only one-way hash function and simple polynomial operations are required in our protocol. And our improved scheme needs not to create public key cryptosystems in advance. Contrary to the traditional public key cryptosystem based mutual authentication key agreement protocols [13,14,17,18], our scheme is more secure and efficient for applications. In section 3.1, we will propose a more secure user authentication protocol based on Chebyshev chaotic maps. The discussions of the securities and the performances of the proposed protocol are described in section 3.2. Finally, a brief of summary is presented in the last section.. 3.1 The Proposed Scheme To illustrate the protocol clearly, the Chebyshev chaotic maps Tn ( x) used in our protocol are the same as Guo and Chang’s scheme [20]. In the initialization, the server S chooses two secret keys s and d, where s and d are large numbers. And h( ) is a secure one-way hash function with fixed-length output. Our scheme consists of three phases: the registration, the authentication, and the updated password. The details of these phases will 16.
(18) be described as follows. Registration phase: If the user U i with identity IDi would like to register or reregister with the server S, U i and S will perform the following steps: Step 1. The user U i selects a password pwi and a random number bi and computes. h( pwi bi ) . Then, the user U i submits his/her identity IDi and h( pwi bi ) to the server S for registration over a secure channel. Step 2. If the IDi is valid, the server S computes xi h( IDi || d ) , Ts ( xi ) , and. Vi h( IDi || d ) h( pwi bi ) . Step 3. S stores the data {h( ), Vi , Ts ( xi ) } into a new smart card, and issues this smart card to the user U i through a secure channel. Step 4. U i stores the random number bi into the smart card. Authentication phase: If U i wants to log into the server S, then U i and the server S will perform the following steps: Step 1. The user U i first inserts his/her smart card into a card reader and inputs the IDi and password pwi . Then, the smart card selects a random number u and computes. h( IDi || d ) Vi h( pwi bi ) , KAi Tu (Ts ( xi )) , CIDi IDi KAi , Tu (h( IDi || d )) , and Yi h(h( IDi || d ) || Tu (h( IDi || d )) || T1 ) .. Next,. the. smart. card. sends. the. message {CIDi , Tu (h( IDi || d )), Yi , T1} to the server S, where T1 is the current timestamp of the smart card. Step 2. Upon receiving the message {CIDi , Tu (h( IDi || d )), Yi , T1} , the server S checks whether T * T1 T , where T * is the time of receiving the login message and T is the time threshold. Then, the server S computes KAi Ts (Tu (h( IDi || d )) , IDi CIDi KAi ,. 17.
(19) and xi h( IDi || d ) using server’s secret keys s and d. Next, the server S computes. Yi h( xi || Tu (h( IDi || d )) || T1 ) and checks whether Yi Yi . If the verification is false, the server S terminates this login request for a period of time. If the verification is successful, the server S believes that the user U i is valid. Step 3. The server S selects a random number v and computes Tv ( xi ) ,. KSi Tv (Tu (h( IDi || d )) and Ri h( IDi || xi || KSi || T2 ) , where xi h( IDi || d ) . Then, S sends the message T2 , Tv ( xi ) , and Ri to the user U i , where T2 is the server S’s current timestamp of the system. Step 4. After receiving T2 , Tv ( xi ) , and Ri , the smart card compares whether the time T2 is. acceptable.. Then,. it. further. computes. K. i. S (. u. T(. v. Tand ) i )x. Ri h( IDi || h( IDi || d ) || KSi || T2 ) , and compares whether Ri Ri . If the equation holds, the server is authenticated by the user U i . From the above authentication phase, the user U i and the server S could compute the common session key KSi Tv (Tu (h( IDi || d )) Tu (Tv ( xi )) , where xi h( IDi || d ) . This authentication process is briefly illustrated in Figure 1 Updated password phase: In our method, if a user wants to arbitrarily update his/her password pwi , he/she does not need to register with the server S. It is very convenient for the user to change his password. Now suppose user U i would like to change his/her password, he/she only requires to perform the following steps. Step 1: U i inserts the smart card into the smart card reader and then inputs IDi and his/her old pwi . Then, the smart card computes Vi Vi h( pwi bi ) h( pwi bi ) . Step 2: Replace Vi with Vi on the memory of the smart card. It is accepted because. 18.
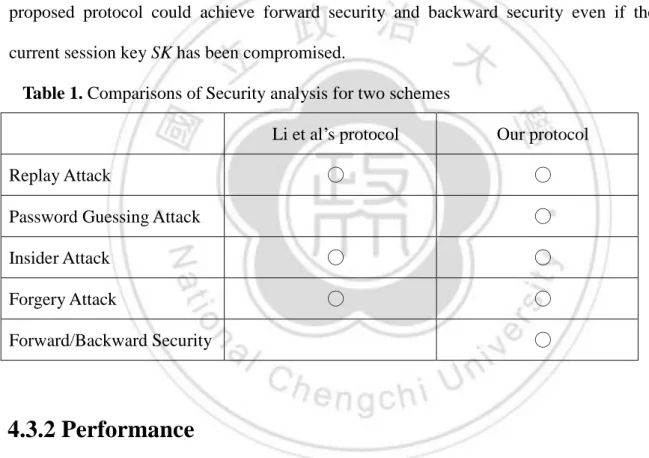
(20) Vi Vi h( pwi bi ) h( pwi bi ) h( IDi || d ) h( pwi bi ) h( pwi bi ) h( pwi bi ) h( IDi || d ) h( pwi bi ). Figure 1. The proposed of Authentication phase Ui (1). Server. timestampT1. xi =Vi h(pwi bi ) Tu ( xi ), KAi Tu (Ts ( xi )) CIDi IDi KAi Yi h( xi || Tu ( xi ) || T1 ). CIDi , Tu ( xi ), Yi , T1 . (2) timestamp. T * ,(T * T1 ) T. KAi =Ts (Tu ( xi ) IDi =CIDi KAi ,xi =h( IDi ||d ). Yi h (h ( IDi || d ) || Tu (h IDi || d || T1 ) check Yi Yi {Tv ( xi )), Ri , T2 } . (3)check timestampT2 KSi Tu (Tv ( xi )). Tv ( xi ), KSi =Tv (Tu ( xi )) Ri =h(IDi || h ( IDi || d ) || KSi || T2 ). Ri h( IDi || xi || KSi || T2 ) check Ri=Ri ____________________________________________________________________________. .. 3.2 Discussions In this section, we are going to explore the securities and the performances of the improved protocol.. 3.2.1 Security Analysis . In this section, we analyze the security of the improved method as follows. Based on Guo and Chang’s scheme [20], our scheme can overcome the weaknesses indicated above of Section 2.3. We summarize the comparisons of the proposed scheme with Guo and Chang’s in Table 1.The security of the proposed scheme can be shown as follows: (1) Mutual authentication At the beginning of authentication phase, the user U i selects a random number u and sends. the. message. {CIDi , Tu (h( IDi || d )), Yi , T1} 19. to. the. server. S,. where.
(21) h( IDi || d ) Vi h( pwi bi ). ,. KAi Tu (Ts ( xi )). ,. CIDi IDi KAi. ,. and. Yi h(h( IDi || d ) || Tu (h( IDi || d )) || T1 ) . From the value Tu (h( IDi || d )) , it is very difficult for the adversary to find the exact u and h( IDi , d ) . The probability of obtaining the exact u and. h( IDi || d ) are equivalent to performing an exhaustive search on Tn ( x) . Without the knowledge h( IDi || d ) or the password pwi of U i , the adversary could not generate the legal messages CIDi and Yi . Therefore, the server could authenticate the user U i through checks the validity of Yi . With the message {CIDi , Tu (h( IDi || d )), Yi , T1} , the server generate a random number v and computes Tv ( xi ) ,. KSi Tv (Tu (h( IDi || d )) and. Ri h( IDi || xi || KSi || T2 ) , where. xi h( IDi || d ) . Then, S sends the messages T2 , Tv ( xi ) , and Ri to the user U i . Without the server’s secret keys s and d, the adversary cannot obtain the exact IDi and. h( IDi || d ) from CIDi , where KAi Ts (Tu (h( IDi || d )) and IDi CIDi KAi . Then, the user U i could authenticate the server S by checking the validity of Ri . Hence, the proposed scheme could provide mutual authentication. (2) User anonymity In the authentication process, the user U i ’s identity IDi is included in the message CIDi IDi KAi , where KAi Tu (Ts ( xi )) and u is a fresh random number. However, without the server’s secret key s, the adversary cannot obtain the exact IDi from CIDi . Since KAi is different for each session, then, the adversary cannot trace the same user Ui from the information CIDi. It can protect the user from tracing over network. Even if the secret information. Vi h( IDi || d ) h( pwi bi ). and. Ts ( xi ) stored in. U i 's. smart card are. compromised, the adversary could not easily obtain any information about the user’s IDi . Therefore, the proposed scheme can achieve user anonymity property. (3) Replay attack The adversary may intercept the message {CIDi , Tu (h( IDi || d )), Yi , T1} and replay it to the 20.
(22) server. However, the server could find the attack through checks the validity of timestamp T1 . Similarly, the adversary may intercept the message { T2 , Tv ( xi ) , Ri }and replay it to U i . The user U i could also find the attack through checks the timestamp T2 . Therefore, our method could withstand the replay attack. (4) Off-line password guessing attack The proposed scheme can achieve user anonymity property. For the CIDi is different for each session, the adversary cannot trace the same user Ui from the information CIDi. Therefore, the mutual information of the interactive authentication messages does not reduce the entropy of user’s password and identity. Moreover, suppose that the adversary gets the data Vi h( IDi || d ) h( pwi bi ) and Ts ( xi ) stored in U i 's smart card, where xi h( IDi || d ) . Then, the adversary can guess a password. pwi* and compute. h( IDi || d ) Vi h( pwi* bi ) . However, the adversary could not verify its correctness. from Ts ( xi ) since he/she does not have the server’s secret key s. Therefore, the proposed scheme could against the off-line password guessing attack. (5) Impersonation attack In the proposed protocol, even though the secret information Vi h( IDi || d ) h( pwi bi ) and Ts ( xi ) stored in U i 's smart card are compromised, the adversary could not easily forgery the user U i without knowing h( IDi || d ) or the password pwi of U i . In addition, suppose that U i extracts the data Vi h( IDi || d ) h( pwi bi ) and Ts ( xi ) from his/her smart card. The U i could only obtain his/her h( IDi || d ) Vi h( pwi bi ) xi . However, it is not helpful for U i to impersonate someone U j without knowing the information h( ID j || d ) and Ts ( x j ) of U j , where x j h( ID j , d ) . Therefore, with the messages h( IDi || d ) and Ts ( xi ) , U i still needs to break the hash function and Chebyshev chaotic 21.
(23) map so as to find the system secrets d and s, respectively. In generally, the length of d and s are about 512-1024 bits. The probability of obtaining the exact d and s are equivalent to performing an exhaustive search on h( IDi || d ) and Ts ( xi ) , respectively. Therefore, without the knowledge of d and s, it is very difficult for someone to impersonate the server and users. (6) The insider attack In the registration of our improved method, the user U i sends the hash value. h( pwi bi ) instead of the password pwi to the server, where bi is a random number generated by the user. The privileged insider A (or the server) cannot get the password since it is protected by the secure hash function and random number bi . Therefore, the proposed scheme could against the insider attack. (7) Forward security After a successful mutual authentication, session key KSi Tu (Tv ( xi )) Tv (Tu ( xi )) is generated for legal user U i and the server S. However, without the knowledge of. xi h( IDi || d ) , an adversary cannot easily to obtain the exactly nonce u and v from the transmission Tu ( xi ) and Tv ( xi ) . Therefore, it is computationally intractable for the adversary to derive the session key KSi from Tu ( xi ) and Tv ( xi ) . Even if an intruder obtains the current session key KSi , it is not easy for him to obtain the current value u and v from KSi . Without knowing the random numbers u and v, it is exceedingly difficult for an adversary to create the session key KSi . Moreover, the nonce u and v are used for only one time. Hence, the improvement scheme can provide forward security even if the current session key KSi has been compromised. For KSi is used for one session only, it is not helpful for the intruder to derive from past communication or future transactions.. 22.
(24) Table 1. Comparisons of Security Analysis for two schemes Guo and Chang’s. Our scheme ○. User Anonymity Replay Attack. ○. ○. Password Guessing Attack. ○. ○ ○. Impersonation Attack Insider Attack. ○. ○. Forward Security. ○. ○. 3.2.2 Performance We use the Chebyshev polynomials to achieve the mutual authentication and establish the common session key. For the Chebyshev chaotic map [15.18.19], given y, it is very hard to find the exact parameters x and n such that y Tn ( x) . Thus, without knowing. xi h( IDi || d ) , the adversary is computationally intractable to obtain the exact u and v from Tu ( xi ) and Tv ( xi ) , respectively. The security of the proposed improvement protocol no longer totally relies on the hard problem of high-degree polynomials. Therefore, it is not necessary for the user and server to select larger numbers u and v to compute Tu ( xi ) and Tv ( xi ) in the authentication phase. Even though the secret information Vi h( IDi || d ) h( pwi bi ) and Ts ( xi ) stored in U i 's smart card are compromised, the. adversary could not easily derive the validity xi h( IDi || d ) and pwi from Vi . Hence, no time-consuming modular exponential computing and scalar multiplication on elliptic are required in our authentication processes. Furthermore, the proposed method does not need to construct public/symmetric key cryptosystem in advance. With regard to efficiency, we define related notations to analyze the computational complexity. The notation E means the time for one symmetric encryption or decryption, T 23.
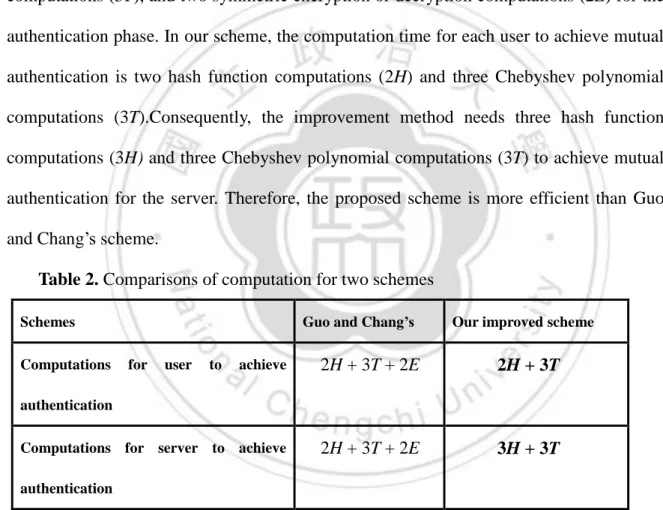
(25) denotes the time for one Chebyshev polynomial computation, and H denotes the time for executing the adopted one-way hash function in one’s scheme. Note that the times for computing modular addition and exclusive-or are ignored, since they are much smaller than E, T, and H. We summarize the comparisons of the proposed scheme with Guo and Chang’s in Table 2. As shown in Table 2, in Guo and Chang’s scheme [20], both the user and the server need to perform two hash function computations (2H), three Chebyshev polynomial computations (3T), and two symmetric encryption or decryption computations (2E) for the authentication phase. In our scheme, the computation time for each user to achieve mutual authentication is two hash function computations (2H) and three Chebyshev polynomial computations (3T).Consequently, the improvement method needs three hash function computations (3H) and three Chebyshev polynomial computations (3T) to achieve mutual authentication for the server. Therefore, the proposed scheme is more efficient than Guo and Chang’s scheme. Table 2. Comparisons of computation for two schemes Schemes. Guo and Chang’s. Our improved scheme. achieve. 2H + 3T + 2E. 2H + 3T. Computations for server to achieve. 2H + 3T + 2E. 3H + 3T. Computations. for. user. to. authentication. authentication. 3.3 Summary In this chapter, we have proposed an improvement to overcome the weaknesses of Guo and Chang’s. The proposed method can provide the following characters: (1) no password table is required for the designated servers; (2) users can freely choose their own. 24.
(26) passwords; (3) users may update their passwords after registration phase; (4) it supplies mutual authentication between the user and the designated server; (5) session key is generated by the user and the remote server for each session; (6) user anonymity property is provided. Without any public/symmetric key cryptosystem included in the proposed scheme, it is more efficient than that of traditional protocols for the practice applications.. 25.
(27) Chapter 4 Efficient User Authentication with Smart Card for Multi-Server Networks The smart card based password authentication is one of the simplest and most adopted method in remote login environments [21-26]. Nowadays, ubiquitous computing has become very popular where multiple servers are involved in authenticating their users. Namely, a user can login different servers through mobile networks to obtain diversified services. In traditional remote login methods for a multi-server architecture, a user not only has to log into various remote servers with repetitive registration, but also needs to remember the various user identities and passwords. This will make password authentication extremely inconvenient. In 2004, Lee and Chang proposed a user identification and key distribution scheme for multi-server networks [29]. In their scheme, the user registered at the registration center once and can use all the designated servers for the services. In multi-server environments, single registration to a trusted registration center is the most important feature and any user could receive desired services from various service providers without repeating registration. Due to the limitation of computational power, a smart card may not be able to afford heavy computations. In 2008, Tsai suggested lightweight computations such as one-way hash function during multi-server authentication processes using smart cards [28]. Recently, there are many hash-based authentication schemes with smart card have been proposed in multi-server environments. Unfortunately, most of them are vulnerable to masquerade attack, insider attack, and the server or the registration center spoofing attack [21,27,35-36]. For enhancing the security of multi-server networks, in 2011, Chang and Cheng proposed a secure and lightweight user authentication method for multi-server architecture [35]. Unfortunately, Li et al. pointed out that Chang and Cheng’s scheme still suffers from. 26.
(28) insider attack, smart card lost attack, and session key disclosure attack, and then they also proposed an improvement to overcome Chang and Cheng’s problems [36]. Furthermore, we will find that Li et al.’s scheme is still vulnerable the off-line password guessing attack. Moreover, in Li et al.’s scheme, it is required registration center to join the authentication and construct the common session key for user and the remote service providers. It will make the registration center to be another security and performance bottleneck, which will bring more communication and computing overlay. Therefore, based on the Chebyshev chaotic maps [15,19], we will propose a new efficient user authentication protocol for multi-server networks. The proposed method not only could resist various attacks but also remedy the weaknesses of Li et al.’s. Compared with other related mechanisms, performance analysis shows that our scheme has much better performance for the real application. The remainder of this chapter is organized as follows. In the 4.1 section, we introduce some related works. The proposed scheme is presented in section 4.2. In section 4.3, the security analyses and performance of the proposed scheme are stated. Finally, a brief of summary will be made in last section.. 4.1 Preliminary In Subsection 4.1.1, we first introduce Li et al.’s [36] authentication protocol for multi-server environments that will allow us to compare with our scheme in Section 4.3. The weakness of Li et al.’s is described in Subsection 4.1.2.. 4.1.1 Review of Li et al.’s Scheme In this subsection, we presented Li et al.’s mutual authentication protocol for multi-server environments using smart card [36].Three entities are included: the user (Ui), the remote server (SPj), and the registration center (RC). RC is responsible for registration 27.
(29) of SPj and Ui. When the server (SPj) registers with RC use the identifier SIDj, RC computes a shared secret key KRS j H (SID j k ) with SPj, where k is a secret key of RC and H( ) is a one-way hash function only known by RC. Li et al.’s protocol consists of five phases: registration, login, authentication and key agreement, password change, and smart card revocation phase. The details are listed in the following. Registration phase: The new user Ui freely chooses an identity idi and a password pwi. Then, he/she sends the registration message to RC. The steps of this phase are as follows: (1) Ui computes h(idi pwi r ) and submits the information idi and h(idi pwi r ) to RC through a secure channel, where r is a random number chosen by Ui and h( ) is a one-way public hash function. (2) RC checks Ui registration information and credit. If it is not valid, RC rejects his/her registration; otherwise RC computes Ui’s account number TIDi Ti idi and stores it in the RC’s database, where TIDi Ti idi and Ti denotes the number of times for a user Ui registering with RC. Note that the value Ti is used to revoke a smart card in case of lost or stolen of smart cards. In addition, Ti 0 if Ui is a new registration user, otherwise RC sets Ti n 1 , n represent the registration times, and updates Ti in Ui’s account database if Ui is re-registering in RC. (3) RC computes i H (TIDi k ) h(idi pwi r ) , and saves ( i , h(TIDi ), h(.), Ti ) into Ui‘s smart card and issues it to Ui over a secure channel. (4) Ui stores r into his/her smart card and Ui needs not to remember r after finishing this phase. Login phase: When Ui wants to login the remote server SPj for asking a service, Ui inserts the smart 28.
(30) card into the card reader and keys his/her identity idi and password pwi. Then, the smart card performs the following steps: (1) The smart card computes TIDi Ti idi and h(idi pwi r ) , then verifies whether. h(TIDi) h(TIDi ) . If it hoes not hold, this phase is terminated by the smart card; otherwise, the smart card transmits {TIDi , 1 , 2 } to SPj, where. NU. is a nonce,. 1 i h(idi pwi r ) NU and 2 h((TIDi SID j ) NU ) . (2) SPj generates a nonce N S and computes 1 KRS j N S , and then sends {TIDi , 1 , 2 , SID j , 1 , 2 } to RC, where 2 h((SID j TIDi ) NS ) .. Authentication and key agreement phase: After receiving the login request {TIDi , 1 , 2 , SID j , 1 , 2 } , RC executes the following steps: (1) RC checks the validity of TIDi and SIDj. If they are not valid, RC rejects this login request; otherwise, RC computes NU 1 h(TIDii k ) . Next, RC verifies the freshness of NU and the validity of h((TIDi SID j ) NU ) 2 . If either one is not correct, RC terminates this request; otherwise, Ui is authenticated by RC. (2) RC computes N S 1 KRS j . Then, RC checks the freshness of N s and the validity of h((SID j TIDi ) N S ) 2 . If either one is not correct, RC terminates this connection; otherwise, SPj is authenticated by RC. (3) RC. generates. a. nonce. NU. computes. h( NU ) NS N R. ,. U h( H (TIDi k ) SK ) , h( NS ) NU N R , and S h( H (SID j k ) SK ) . Then, RC sends { , U , S , } to SPj, where SK h( NU NS N R ) is a common session key.. 29.
(31) (4) After receiving the respond message { , U , S , } , SPj computes h( N S ) and SK S h( N S ) , and verifies whether h( H (SID j k ) SK S ) S . If it is not equal, SPj terminates this phase; otherwise RC and Ui are authenticated by SPj and forwards { , U } to Ui. (5) Upon receiving the message { , U } from SPj, Ui computes h( NU ) and. SKU h( NU ) , and verifies whether h( H (TID j k ) SKU ) U . If it is not correct, Ui terminates this phase; otherwise RC and SPj are authenticated by Ui and forwards { , U } to Ui. It is obvious that SK SK S SKU and shared between Ui , SPj, and RC. Password change phase: Now suppose user U i would like to change his/her password, he/she only requires to perform the following steps. (1) U i inserts the smart card into the smart card reader and then inputs id i and his/her old pwi . Then, the smart card computes. TIDi Ti idi and. checks whether. h(TIDi) h(TIDi ) . If it is equal, the user U i chooses a new password PWM and performs the next steps; otherwise, the device terminates the login request for a period of time. (2) Compute i h(idi pwi r ) h(idi pwi r ) (3) Replace i with i on the memory of the smart card. Smart card revocation phase: In case of stolen or lost of smart card, U i can request RC for the revocation. First, RC updates the value of Ti and the value of Ti is incremented by one. Then, U i can register to RC without changing his/her original identity id i .. 4.1.2 Security Analysis of Li et al.’s Scheme 30.
(32) Li et al. proposed a new efficient mutual authentication protocol for multi-server environments with smart card [36]. They claimed that their protocol can withstand the off-line password guessing and smart card lost attacks even if the adversary can eavesdrop all transmitted messages. However, we will explicitly point out that Li et al.’s scheme is still vulnerable the off-line password guessing attack. Now suppose that the adversary (someone U a ) could extract the data ( i , h(TIDi ), h(.), Ti , r ) which stored on U i s smart card, where TIDi Ti idi and i H (TIDi k ) h(idi pwi r ) . In general,. the user only remembers a human-memorable identity number. The detail of the attack is described as follows. (1). The adversary U a. first guesses an identity number. idi* and computes. h(Ti idi* ) .Then, U a checks whether h(Ti idi* ) and h(Ti idi ) is equal. If they are. equal, U a finds the correct identity number idi; otherwise, U a repeats (1) until the correct identity id i is found. (2). U a extracts the transmitted messages {TIDi , 1 , 2 } from TIDi Ti idi , where NU is a nonce,. 1 i h(idi pwi r ) NU , 2 h((TIDi SID j ) NU ) , and. i H (TIDi k ) h(idi pwi r ) . It is obvious that 1 H (TIDi k ) NU . (3). U a guesses a password pwi* and computes h(idi pwi* r ) ; then U a obtains H * (TIDi k ) i h(idi pwi* r ) and NU* 1 H * (TIDi k ) .. (4). Then, U a checks whether h((TIDi SID j ) NU* ) and 2 is equal. If they are equal, the adversary U a finds the correct password pwi for the user U i ; otherwise,. U a repeats steps (3) and (4) until the correct value of pwi is found. Therefore, Li et al.’s method will suffer from the off-password guessing attack when the adversary could extract the data which stored on one’s smart card. Moreover, in Li 31.
(33) et al.’s scheme, it requires RC to join the authentication and construct the common session key for user Ui and the remote server SPj . It will make the RC to be another security and performance bottleneck, which will bring some potential threats to the system. This will bring more delay caused by more communication and computing overlay.. 4.2 The proposed scheme In this section, we use the enhanced Chebyshev polynomials: Tn ( x) 2 xTn1 ( x) Tn2 ( x) mod N , where n 2 , x (, ) , and N is a large prime number [15,19]. Based on the. Chebyshev chaotic maps, we will propose an efficient user authentication protocol for multi-server networks environments. Three entities are included: the user (Ui), the server (SPj), and the registration center (RC). RC is responsible for registration of SPj and Ui. When the server (SPj) registers with RC use the identifier SIDj, RC computes a shared secret key. KRS j h(SID j k ) with SPj, where k is a secret key of RC and h( ) is a secure one-way hash function published by RC. Our protocol contains four phases:. registration, login and. authentication, password change, and smart card revocation phase. The details are listed in the following. The login and the authentication phase is shown in Figure 1. Registration phase: The new user Ui freely chooses an identity idi and a password pwi. Then, he/she sends the registration message to RC. The steps of this phase are as follows: (1) Ui computes h(idi pwi r ) and submits the information idi and h(idi pwi r ) to RC through a secure channel, where r is a random number chosen by Ui. (2) RC checks Ui registration information and credit. If it is not valid, RC rejects his/her registration; otherwise RC computes Ui’s account number TIDi Ti idi and stores it in the RC’s database, where TIDi Ti idi and Ti denotes the number of times for a user Ui registering with RC. Note that the value Ti is used to revoke a smart card in case of lost 32.
(34) or stolen of smart cards. In addition, Ti 0 if Ui is a new registration user, otherwise RC sets Ti n 1 , n represent the registration times, and updates Ti in Ui’s account database if Ui is re-registering in RC. (3) RC computes si h(TIDi k ) h(idi pwi r ) and Ai h(h(TIDi k ) idi ) , then saves (si , Ai , h(.), Ti ) into Ui’s smart card and issues it to Ui over a secure channel. (4) Ui stores r into his/her smart card and Ui needs not to remember r after finishing this phase. Login and authentication phase: When Ui wants to login the remote server SPj for asking a service, Ui inserts the smart card into the card reader and keys his/her identity idi and password pwi. Then, the smart card performs the following steps: (1) The smart card computes TIDi Ti idi , h(idi pwi r ) , and si h(idi pwi r ) , then verifies whether Ai h( idi ) . If it does not hold, this login is terminated by the smart card; otherwise, the smart card calculates the value of Chebyshev polynomial. Tu ( x) , B h( nu SID j ) Tu ( x) , C x Tu ( x) and yi h( Tu ( x) C nu ) . Next, it transmits {TIDi , SID j , B, C, nu , yi } to RC, where nu , x, and u are the nonce selected by the device. (2) After receiving the login request {TIDi , SID j , B, C, nu , yi } , RC checks the validity of TIDi and SIDj. If they are not valid, RC rejects this login request; otherwise, RC computes h(TIDi k ) and derives the value Tu ( x) B h( nu SID j ) . Next, RC verifies the freshness of nu and the validity of yi h( Tu ( x) C nu ) . If either one is not correct, RC terminates this request; otherwise, Ui is authenticated by RC. (3) RC computes p j h( KRS j Tu ( x) C ) and Cij h( KRS j TIDi nu ) Tu ( x) ; then sends 33.
(35) { p j , TIDi , C, nu , Cij } to the remote server SPj. (4) With , Cij, and nu, SPj obtains Tu ( x) Cij h( KRS j TIDi nu ) and checks whether p j h( KRS j Tu ( x) C ) is correct. If it is not held, SPj terminates this phase; otherwise. SPj generates a nonce v and computes x C Tu ( x) , the value of chaotic map Tv ( x) , the session key SK Tv (Tu ( x)) , D Tu ( x) Tv ( x) , and h(TIDi SK nu ) . Then, SPj sends {D, h(TIDi SK nu )} to the user Ui. (5) Upon receiving the message {D, h(TIDi SK nu )} from SPj, Ui computes. Tv ( x) D Tu ( x) and derives the common session key SK Tu (Tv ( x)) with the random number u, and verifies the validity of h(TIDi SK nu ) . If it is not right, Ui terminates this phase; otherwise RC and SPj are authenticated by Ui and forwards. h(SID j SK ) to SPj. (6) After receiving h(SID j SK ) , SPj checks the correctness of h(SID j SK ) . If it is not equal, SPj terminates this phase; otherwise the key SK is shared between Ui and SPj. It is obvious that SK Tu (Tv ( x)) Tv (Tu ( x)) . For the security, the random numbers u, v, x, and nu are used only once. Password change phase: Now suppose user U i would like to change his/her password, he/she only requires to perform the following steps. (1) U i inserts the smart card into the card reader and then inputs id i and his/her old pwi . Then, the smart card computes TIDi Ti idi , h(idi pwi r ) , and si h(idi pwi r ) , then checks whether Ai h( idi ) . If it is equal, the user U i chooses a new password PWi and performs the next steps; otherwise, the device terminates the request. 34.
(36) for a period of time. (2) Compute si si h(idi pwi r ) h(idi pwi r ) (3) Replace si with si on the memory of the smart card. Figure 1. The Proposed of Login and Authentication Phase __________________________________________________________________________ Ui (User). SPj (Server). RC (Registration center). TIDi idi Ti , si h(idi pwi r ) A ? h( idi ) choose nu , u, x Tu ( x), C Tu ( x) x, B h( nu SID j ) Tu ( x) yi h( Tu ( x) C nu ). {TIDi , SID j , B, C, yi , nu } Check TIDi and SID j ?. h(TIDi k ) Tu ( x ) B h( nu SID j ) yi ? h( Tu ( x ) C nu ) Compute p j h( KRS j Tu ( x) C ) Cij h( KRS j TIDi nu ) Tu ( x ). {TIDi , p j. }. , Cij C , nu ,. Tu ( x) Cij h( KRS j TIDi nu ) p j =? h( KRS j Tu ( x) C ) x C Tu ( x) Chose v, Compute Tv ( x), SK Tv (Tu ( x)), D Tv ( x) Tu ( x) h(TIDi SK nu ). Tv ( x) D Tu ( x). {D, h(TIDi SK nu )}. SK Tu (Tv ( x)) Check h(TIDi SK nu ) ? Compute h( SID j SK ). h( SID j SK ). C h e chk S I( D j. SK ) ?. ________________________________________________________________________. 35.
(37) Smart card revocation phase: In case of stolen or lost of smart card, U i can request RC for the revocation. First, RC updates the value of Ti and the value of Ti is increased by one. Then, U i can register to RC again without changing his/her original identity id i .. 4.3 Discussions In this section, we are going to explore the securities and the performances of the proposed protocol.. 4.3.1 Security Analyses . In this section, we analyze the security of the improved method as follows. Based on Chebyshev chaotic maps, our scheme can overcome the weaknesses indicated above of Section 4.1.2. The security analysis between the proposed scheme and Li et al. are shown in Table 1. The proposed scheme has several security properties as follows: (1) Security of the system secret In our protocol, only the RC contains the secret k, the users and the remote servers know. nothing. about. it.. For. a. user. Ui,. even. if. he/she. extracts. the. data si h(TIDi k ) h(idi pwi r ) , Ai h(h(TIDi k ) idi ) , and r from his/her smart card , and derives h(TIDi k ) si h(idi pwi r ) with his/her password pwi . The user Ui still needs to solve the hash function problem so as to find the system secret k. Similarly, the server (SPj ) has a secret key KRS j h(SID j k ) . The probability of obtaining the exact k is equivalent to performing an exhaustive search on h(TIDi k ) or KRS j h(SID j k ) . Therefore, without the knowledge of k, it is very difficult. for someone to impersonate the registration center RC. (2) Replay attack In Step 1 of login and authentication phase of the proposed protocol, a random number nu is generated by Ui which makes all login messages dynamic and valid for that session only. Therefore, the proposed method could withstand the replay attacks from the random nonce in different sessions. 36.
(38) (3) On-line and off-line password guessing attacks Now assume that the malicious user has a smart card-lost of some user Ui. From the above proposed scheme, the malicious user uses this card and inputs idi and guessing the password pwi to perform the login and authentication with RC. Accordingly, in Step1 of login and authentication phase, the device calculates. TIDi Ti idi , h(idi pwi r ) , si h(idi pwi r ) , and Ai h( idi) , then checks whether Ai Ai . If it is not equal, the device terminates this login request for a period of time. Therefore, in the on-line password guessing, it is very difficult for the adversary to guess Ui ’s password and identity correctly at the same time, then verify the correction of Ai h( idi ) for h(TIDi k ) . Hence, without knowing the validity of id i and pwi , the on-line password guessing attack will not be arisen by the proposed method. A failed guess could be detected and logged by the device. On the other hand, suppose that the malicious user could extract the information. (si , Ai , h(.), Ti ) which are stored in some Ui ’s smart card. The malicious user may launch an off-line password guessing attack for the proposed scheme. The malicious user guesses some one’s idi and pwi . He/She repeatedly calculates TIDi Ti idi ,. h(idi pwi r ) , si h(idi pwi r ) , and Ai h( idi) , then checks whether Ai Ai . However, without the knowledge of , id i , and pwi ,. the malicious could. not verify if Ai Ai h( idi ) holds or not. The probability of obtaining the exact , id i , and pwi is equivalent to performing an exhaustive search on Ai h( idi ) for. h(TIDi k ) .. Moreover, even if the adversary could eavesdrop all transmitted messages {TIDi , SID j , B, C, nu , yi }. ,. h(SID j SK ) between. Ui ,. { p j , TIDi , C, nu , Cij }. RC,. and. the. server. ,. {D, h (TIDi SK nu )}. SPj.. Without. the. , right. information (si , Ai , h(.), Ti , r ) which is stored in one’s smart card, it is computationally intractable to obtain the same password pwi from the above all transmitted messages. Therefore, the proposed method could resist the off-password guessing attack. (4)The insider attack. 37.
(39) In the registration of our method, the user Ui sends the hash value. h(idi pwi r ) instead of the password pwi to the registration center RC, where r is a random number generated by the user. The privileged insider RC cannot easily obtain the password since it is protected by the secure hash function and random number r. Therefore, the proposed scheme could against the insider attack. (5) The forgery attack In this attack, we suppose that an adversary could get the information. (si , Ai , h(.), Ti ) which are stored in Ui’s smart card. The adversary may select a server provider SPj and choose a trial identity idi and a trial password pwi to perform the login and authentication with RC. Accordingly, in Steps 1 and 2 of login and authentication phase,. without the real identity id i and password pwi correctly at the. same time, it is very difficult for the adversary to derive the right login messa ges and pass the verification process with RC. As a result, the adversary could not easily achieve forgery or impersonation attacks in our proposed method. (6) Provide mutual authentication In Steps 1 and 2 of login and authentication phase, the registration center RC authenticates the login user by checking h(TIDi k ) . Through the shared key. KRS j h(SID j k ) , SPj could verify the RC from the Step 4 of login and authentication phase. Moreover, in Steps 5 and 6 of login and authentication phase, the proposed mechanism could achieve mutual authentication between the login user and the service provider by means of the random number nu and the session key SK. Thus, the mutual authentication property is provided for the proposed protocol. (7) Forward and backward securities After a successful mutual authentication, the session key SK Tu (Tv ( x)) Tv (Tu ( x)) is created for the legal user Ui and the service provider SPj. From the transmission information,. B h( nu SID j ) Tu ( x). ,. C x Tu ( x). ,. D Tv ( x) Tu ( x). ,. Cij h( KRS j TIDi nu ) Tu ( x) , and yi h( Tu ( x) C nu ) , an adversary cannot easily to. obtain the exactly Tu ( x) B h( nu SID j ) Tu ( x). and. and Tv ( x) . It is protected on the hash function Cij h( KRS j TIDi nu ) Tu ( x). 38. .. Therefore,. it. is.
(40) computationally infeasible for the adversary to derive the session key SK from B and Cij. Even if an intruder obtains the current session key SK, it is not easy for him to obtain the current value and KRSj from B and Cij. That is protected under the one-way hash function h() . The probability of obtaining the exactly and KRSj are equivalent to performing an exhaustive search on and KRSj. Moreover, the nonce x, u, v, and nu are used for only once. Therefore, the intruder cannot derive private messages from the past. For SK is used for one time only, even if the intruder obtains the current session key SK, it is not helpful for him to obtain past communication or future transactions. Thus, the proposed protocol could achieve forward security and backward security even if the current session key SK has been compromised. Table 1. Comparisons of Security analysis for two schemes. Replay Attack. Li et al’s protocol. Our protocol. ○. ○ ○. Password Guessing Attack Insider Attack. ○. ○. Forgery Attack. ○. ○ ○. Forward/Backward Security. 4.3.2 Performance To the best of our knowledge, Li et al. proposed a user authentication mechanism for multi-server environments which is more efficient than most of previously proposed schemes [36]. For this reason, we only compare the proposed scheme with Li et al.’s scheme. We use the Chebyshev polynomials to achieve the mutual authentication and establish the common session key. For the Chebyshev chaotic map [15,19], given y, it is very hard to find the exact parameters x and n such that y Tn ( x) . Thus, without knowing 39.
(41) x, Tu ( x) , and Tv ( x) , the adversary is computationally intractable to obtain the exact u and v from our transmission messages B, C, and D. The security of the proposed protocol no longer totally relies on the hard problem of high-degree polynomials. Therefore, it is not necessary for the user Ui and the server SPj to select larger numbers u and v to compute Tu ( x) and Tv ( x) in the login and authentication phase. Hence, no time-consuming modular exponential computing and scalar multiplication on elliptic are required in our authentication processes. With regard to efficiency, we define related notations to analyze the computational complexity. The notation T means the time for one Chebyshev polynomial computation, and h denotes the time for executing the adopted one-way hash function in one’s scheme. Note that the times for computing modular addition and exclusive-or are ignored, since they are much smaller than T and h. The detail of time complexity comparisons of login and authentication phase between the proposed scheme and Li et al. are shown in Table 2, respectively. As shown in Table 2, the proposed scheme requires six hash functions (6h) and two Chebyshev polynomial computations (2T) for the user side; four hash functions (4h) and two Chebyshev polynomial computations (2T) for the server; and only five hash functions (5h) for the registration center RC. It is obvious that the proposed scheme has better performance than Li et al,’s in the registration center RC. The overhead of computation could be reduced for the RC. It could remedy the weakness of Li et al.’s scheme. Comparing with Li et al.’s, the overhead of few additional hash function and Chebyshev polynomial computations is not significant in the user and remote server sides. In addition, Li et al’s authentication protocol for multi-server environments is still vulnerable the off-line password guessing attack. Therefore, our proposed user authentication method for multi-server networks is more efficient than most of previously proposed schemes.. 40.
(42) Table 2. Comparisons of computation for two schemes Schemes. Li et al.’s scheme. Our proposed scheme. achieve. 6h. 6h + 2T. Computations for the server to achieve. 3h. 4h + 2T. 10h. 5h. Computations. for. user. to. authentication. authentication Computations for the registration center to achieve authentication. 4.4 Summary Remote authentication is important to protect a network server against malicious remote users in distributed systems. Based on the Chebyshev chaotic maps, we propose a secure user authentication protocol for multi-server networks. Only one-way hash function and simple polynomial computations are involved in our protocol. It is very practical for applications. Moreover, the proposed scheme could reduce the overhead of computation for the registration center.. 41.
(43) Chapter 5 Conclusions and Future Researches In this dissertation, we have investigated concerning the secure and efficient user authentication with smart card for wireless networks. We give a brief review of the conclusions as follows. In chapter 3, we have proposed a new efficient password authentication with smart card based on chaotic map. Contrary to the traditional public key cryptosystem based mutual authentication key agreement protocols, our scheme is more secure and efficient for applications. Moreover, the proposed method has the following properties: (1) no password table is required for the designated servers; (2) users can freely choose their own passwords; (3) users may update their passwords after registration phase; (4) it supplies mutual authentication between the user and the designated server; (5) session key is generated by the user and the remote server for each session; (6) user anonymity property is provided. Nowadays, ubiquitous computing has become very popular where multiple servers are involved in authenticating their users. Namely, a user can login different servers through mobile networks to obtain diversified services. Single registration and user authentication are important issues for multi-server environments. In chapter 4, based on the Chebyshev chaotic maps [16-17], we have proposed a new efficient user authentication protocol for multi-server networks. Only one-way hash function and simple polynomial computations are involved in our protocol. It is very practical for applications. In addition, the proposed scheme could reduce the overhead of computation for the registration center. More importantly, in these two scheme, no time-consuming modular exponential computing and scalar multiplication on elliptic are required in our authentication processes. Furthermore, the proposed two schemes need not to construct public key cryptosystem in advance. Therefore, it will be more suitable for smart cards or mobile units in the practice. 42.
(44) applications. Due to most secure cryptosystems are relied on the difficulty of solving hard mathematical problems which require large amounts of computations. It is not practical for the mobile users or smart cards. In order to provide practical, efficiency and low-communications for user authentication based on smart cards, the future researches will plan to develop simple algorithm and fewer parameter requirements for other applications in cryptographic techniques.. 43.
(45) Reference [1]. L.. Lamport,. “Password. authentication. with. insecure. communication,”. Communication of ACM, Vol. 24, pp. 770-772, 1981. [2] H. M. Sun, “An efficient remote user authentication scheme using smart cards,” IEEE Transactions on Consumer Electronics, Vol. 46, pp. 958-961, 2000. [3] H. Y. Chien, J. K. Jan, and Y. M. Tseng, “An efficient and practical solution to remote authentication: Smart Card,” Computer & Security, Vol. 21, pp. 372-375, 2002. [4] J. Y. Liu, A. M. Zhou, and M. X. Gao, “A new mutual authentication scheme based on nonce and smart cards,” Computer Communications, Vol. 31, pp. 2205–2209, June 2008. [5] S. W. Lee, H. S. Kim, and K. Y. Yoo, “Improvement of Chien et al.’s remote user authentication scheme using smart cards,” Computer standards & Interfaces, Vol. 27, No. 2, pp. 181-183, 2005. [6] C. C. Yang and R. C. Wang, “Cryptanalysis of a user friendly remote authentication scheme with smart cards,” Computers & Security, Vol. 23, pp. 425-427, 2004. [7] N. Y. Lee and Y. C. Chiu, “Improved remote authentication scheme with smart card,” Computer Standards & Interfaces, Vol. 27, pp. 177-180, 2005. [8] J. Xu, W. T. Zhu, and D. G. Feng, “ An improved smart card based password authentication scheme with provable security,” Computer Standards & Interfaces, Vol. 31, No. 4, pp. 177-180, 2009. [9] M. L. Das, A. Saxena, and V. P. Gulati, “ A dynamic ID-based remote user authentication scheme,” IEEE Transactions on Consumer Electronics, Vol. 50, No. 2, pp. 629-631, 2004. [10] Y. Wang, J. Liu , F. Xiao, and J. Dan, “A more efficient and secure dynamic ID-based remote user authentication scheme,” Computer Communications, Vol. 32,. 44. No. 4, pp..
(46) 583-585, 2009. [11] D, J. He, M. Ma, Y. Zhang, C. Chen, and J. J. Bu, “ A strong user authentication scheme with smart cards for wireless communications,” Computer Communication,Vol. 34, pp. 367–374, 2011. [12] W. S. Juang, S. T. Chen, and H. T. Liaw, “ Robust and efficient password-authenticated key agreement using smart card,” IEEE Transactions on Industrial Electronics, Vol. 5, pp. 2551–2556, 2008. [13] D. Z. Sun, J. P. Huai, J. Z. Sun, J. X. Li, J. W. Zhang, and Z. Y. Feng, “Improvements of Juang et al’.s password-authenticated key agreement scheme using smart cards,” IEEE Transactions on Industrial Electronics, Vol. 56, pp. 2284–2291, 2009. [14] M. S. Hwang, S, K. Chong, and T. Y. Chen, “DoS resistant ID-based password authentication scheme using smart cards,” Journal of Systems and Software, Vol. 83, pp.163–172, 2010. [15] D. Xiao, X. F. Liao, and S. J. Deng, “A novel key agreement protocol based on chaotic maps,” Information Science, Vol. 177, pp. 1136–1142, 2007. [16] X. X.Li , W. D. Qiu, D. Zheng, K. F. Chen, and J. H. Li, “Anonymity enhancement on robust and efficient password-authenticated key agreement using smart cards,” IEEE Transactions on Industrial Electronics, Vol. 57, pp. 780–793, 2010. [17] R. Song, “Advanced smart card based password authentication protocol,” Computer Standards & Interfaces, Vol. 32, pp. 321–325, 2010. [18] E. J. Yoon , and I. S. Jeon, “An efficient and secure Diffie-Hellman key agreement protocol based on Chebyshev chaotic map,” Communications in Nonlinear Science and Numerical Simulation, Vol. 16, pp. 2383–2389, 2011. [19] L. H. Zhang, “Cryptanalysis of the public key encryption based on multiple chaotic systems,” Chaos Solitons Fract, Vol.37, pp. 669–674, 2008. [20] C. Guo and C. C. Chang, “Chaotic maps-based password-authenticated key agreement 45.
數據



Outline
相關文件
Local, RADIUS, LDAP authentication presents user with a login page. On successful authentication the user is redirected to
However, if the EAP Identity does match a client Identifier and the CredentialState is Accepted the EAP server proceeds with the authentication process and verifies the credential
There is no general formula for counting the number of transitive binary relations on A... The poset A in the above example is not
In this chapter, a dynamic voltage communication scheduling technique (DVC) is proposed to provide efficient schedules and better power consumption for GEN_BLOCK
All necessary information is alive in IRIS, and is contin- uously updated according to agreed procedures (PDCA) to support business processes Data Migration No analysis of
Therefore, a new method, which is based on data mining technique, is proposed to classify driving behavior in multiclass user traffic flow.. In this study, driving behaviors
Service quality, customer satisfaction and customer loyalty are also different while people used Taipei Smart Card in different situation.. We suggest that the Taipei Smart
hands sensory contact with the soil medium high repellency.3 、 In accordance with Based on Welfare benefits Pretest and posttest Checklist of