Provably Secure ID-based Mutual Authentication
and Key Agreement for Multi-server Environment
Yun-Hsin Chuang
Department of Mathematics, National Changhua University of Education, Jin-De Campus, Chang-Hua 500, Taiwan
mathbaby@gmail.com
Yuh-Min Tseng
Department of Mathematics, National Changhua University of Education, Jin-De Campus, Chang-Hua 500, Taiwan
ymtseng@cc.ncue.edu.tw
Abstract― With the popularity of Internet and wireless
networks, more and more network architectures are used in multi-server environment, in which mobile users re-motely access servers through open networks. In the past, many schemes that have been proposed to solve the issue of mutual authentication and key agreement for multi -server environment and low-power mobile devices. How-ever, most of these schemes have suffered from many at-tacks after these schemes were proposed since these de-signers did not provide the formal proofs. In this paper, we first give a security model for multi-server environ-ment. We then propose two ID-based mutual authentica-tion and key agreement (MAKA) schemes from bilinear maps, one is used for general users with a long validity period, and the other one is used for anonymous users. Under the presented security model, we also give the for-mal proofs of the proposed schemes, and demonstrate that the proposed schemes are well suitable for low-power mo-bile devices.
Index Terms― ID-based, authentication, multi-server,
key agreement, bilinear map.
I. INTRODUCTION
Since Internet and wireless networks have gained popularity around the world, there are many situations that mobile users need to remote access the systems. The issue of remote user authentica-tion for single server environment has already been solved by a variety of schemes [6, 8, 19].
The system which provides resources to be ac-cessed over the open network often consists of many different servers around the world, called the multi-server environment. However, a traditional remote user authentication is only suitable for the single server architecture environment. The tradi-tional remote user authentication may suffer from several attacks if it is used for the multi-server en-vironment, such as server impersonating and user impersonating. Thus, users and servers need to au-thenticate each other mutually in a multi-server en-vironment. Therefore, the design of a secure mutual authentication and key agreement (MAKA) scheme
for multi-server environment has received much attention from many cryptographers.
Generally, there are three types of MAKA schemes for multi-server environment, namely password-based, public-key based, and ID-based schemes. In the password-based schemes, servers must generally maintain the password tables. For the public-key based schemes, the management for users’ certificates is a load for system authorities. ID-based schemes may simplify the certificate management as compared with the traditional pub-lic-key based schemes. Here, we concern with the design of ID-based MAKA schemes for multi -server environment.
Let’s review the evolution of the MAKA schemes for multi-server environment. In 2001, Li et al. [11] proposed a multi-server authentication scheme using neural networks. The main defect of this scheme is that it spends too much time on training neural networks. At the same time, Tsaur et al. [20] proposed a remote user authentication scheme based on RSA cryptosystem. However, Kim et al. [10] pointed out that Tsaur's scheme can-not be secure against the off-line guessing attack in 2002. Furthermore, Tsaur et al. [21] also showed another weakness on Tsaur's scheme, and give an improvement to withstand the above two weak-nesses. In 2003, Lin et al. [14] proposed a remote authentication scheme for multi-server architecture that it is based on the ElGamal digital signature scheme and the simple geometric properties on the Euclidean plane. However, this scheme has security flaw [2].
In 2005, Choi et al. [3] proposed an ID-based authenticated key agreement for low-power mobile devices. They did not concern with multi-server environment. Indeed, their scheme is suitable for multi-server environment, but it does not provide
full forward secrecy. In 2008, Tsai [18] proposed a multi-server authentication scheme based on one-way hash function without verification tables. However, in Tsai’s scheme, servers need to com-municate with the registration center for each user’s login phase, it is quite inconvenient and the regis-tration center will be a communication bottleneck. Furthermore, in some situations, users want to access the systems anonymously. Therefore, to de-velop an anonymous (or dynamic) MAKA scheme becomes a new issue. An anonymous MAKA scheme provides users to use anonymous identity to login the servers and thus it can achieve user’s anonymity. In fact, a general ID-based MAKA scheme cannot provide user’s anonymity, because it has to change user’s identity in a short-term period. Several dynamic ID-based remote user authentica-tion schemes [5, 12, 22] have been proposed to achieve user’s anonymity in the single server envi-ronment. However, these papers are not suitable for multi-server environment. Recently, several anonymous ID-based MAKA schemes for multi- server environment have been proposed. In 2008,
Geng and Zhang [7] proposed a dynamic ID-based user authentication and key agreement scheme for multi-server environment using bilinear pairings. In 2009, Liao and Wang [13] proposed a dynamic ID-based remote user authentication scheme for multi-server environment. However, Hsiang and Shih [9] showed that Liao and Wang’s scheme has security flaws and they furthermore proposed an improvement on Liao and Wang’s scheme. Unfor-tunately, we have pointed out that both schemes [7, 9] suffered from several attacks [4].
Most of dynamic ID-based MAKA schemes for multi-server environment have suffered from many attacks because the designers of these schemes did not give the formal proofs of their schemes. In order to demonstrate that the proposed scheme is indeed secure under several given hy-pothesis, we present a security model for multi-server environment in this paper. Based on the concept of Choi et al.’s scheme [3], we propose two ID-based MAKA schemes using bilinear maps and both schemes achieve full forward secrecy. One is used for general users with a long validity period, and the other one is used for anonymous users. Under the presented security model, we also
give the formal proofs of the proposed schemes. For performance analysis, we demonstrate that the proposed schemes are well suitable for low-power mobile devices.
The remainder of this paper is organized as follows. We briefly review some mathematical as-sumptions in Section II and establish a security model for ID-based MAKA scheme for multi-server environment in Section III. The pro-posed two ID-based MAKA schemes for multi -server environment are shown in Section IV. Sec-tion V presents the security analysis of the pro-posed schemes. Section VI shows the performance analysis and comparisons. Then, we draw our con-clusions in Section VII.
II. PRELIMINARY
In this section, we briefly describe the concept
of bilinear pairings and several important security assumptions.
A. Parameters and bilinear map
Let G1 be an additive cyclic group with a prime order q and G2 be a multiplicative group with the same order q. G1 is a subgroup of points on an elliptic curve over a finite field E(Fp) and P is the
generator of G1. G2 is a subgroup of the multiplica-tive group over a finite field. A bilinear pairing is a map eˆ:G1×G1→G2 which satisfies the following requirements:
(i) Bilinear:eˆ(aP, bQ)=eˆ(P, Q)ab for all P, Q ∈ G1 and a, b ∈ *
q
Z .
(ii) Non-degenerate: there exist P, Q∈ G1 such that eˆ(P, Q) ≠1.
(iii) Computability: there exists an efficient algo-rithm to compute eˆ(P, Q) for all P, Q∈ G1.
B. Mathematical problems and assumptions
Here, we present several mathematical prob-lems and assumptions as follows:
• Decision Diffie-Hellman (DDH) Problem:
Given P, xP, yP, zP ∈ G1 for some x, y, z ∈ * q
Z , it is easy to verify eˆ(xP, yP)=eˆ(P, zP). That is, DDH in G1 is easy.
• Computational Diffie-Hellman (CDH) Problem: Given P, xP, yP ∈ G1 for some x, y ∈ *
q
xyP .
• Collusion Attack Algorithm with k traitor
(k-CAA) problem: Given P, sP, h1, h2,..., hk∈Z*q,
P h s 1 1 + ,s h2 P 1 + ,…, and s+hk P 1 , finding P h s+ 1 for some h ∈ * q Z .
• Modified BIDH with k values (k-mBIDH)
prob-lem: Given P, sP, tP, h, h1, h2,..., hk∈Z*q, P h s 1 1 + ,s h2 P 1 + ,…, and s+hk P 1 , finding t h s P,P e + 1 ) ( ˆ .
We call the pair (G1, G2) of groups as a Gap Diffie-Hellman group if the DDH problem can be solved in polynomial time but no probabilistic al-gorithm with non-negligible advantage within polynomial time can solve CDH problem. The general bilinear map eˆ: G1×G1→G2 is operated
under the Gap Diffie-Hellman group. As noted in [1], the gap Diffie-Hellman (GDH) parameter gen-erators which satisfy the GDH assumptions are be-lieved to be constructed from the Weil and Tate pairings associated with super-singular elliptic curves or abelian varieties.
Additionally, the k-mBIDH problem is a bi-linear variant of the k-CAA problem. We assume that there is no polynomial time algorithm solving the CDH, k-CAA and k-mBIDH problems with non-negligible probability.
III. THE SECURITY MODEL FOR ID-BASED
MAKA SCHEME
In this section, we establish the security model and define the security for ID-based remote mutual authenticated key agreement for multi-server envi-ronment.
A. Security Model
In this subsection, we define the attack model for an ID-based MAKA scheme for multi-server environment. Assume that the multi-server envi-ronment contains three types of participants, the registration center (RC), the n users U ={Ui | for
i=1,…,n} and the m service providers S ={Sj | for
j=1,…,m}; RC is a trusted party . Each user Ui and
each server Sj has unique identity ID and Ui IDSj
from {0,1}l, respectively. In the model we allow each user Ui to execute a scheme repeatedly with
each server Sj. Instances of Ui (resp. Sj) model
dis-tinct executions of the scheme. We denote s-th
in-stance of Ui (resp. Sj), called an oracle, by ΠUsi
(resp. s Sj
Π ) for an integer s∈N. The public parame-ters params and identities ID= {ID ,Ui IDSj | for
Ui∈U, Sj ∈S} are known by every participant
(in-cluding the RC, users, servers and adversaries).
Adversarial model The model is used to formalize the scheme and the adversary’s capabilities. Allow a probabilistic polynomial time (PPT) adversary A to potentially control all communications in the network via accessing to a set of oracles as defined below. We consider the following types of queries for ID-based MAKA scheme. Let α∈{U, S }. - Extract (ID): Give A the long-term secret key of
ID which is chosen by A, where ID∉ ID.
- Execute (Ui, Sj): Give A the complete transcripts
of an honest execution between Ui and Sj. This
query models the passive attack. - Send (Πs
α, M): A sends a message M to in-stanceΠs
α. When Παs receives M, Παs responds to A according to the ID-based MAKA scheme. This query models the active attack.
- Reveal (Πs
α): Give A the session key for the in-stanceΠs
α.
- Corrupt (IDα): Give A the long-term secret key
held by IDα. This query models the forward
se-crecy. - Test (Πs
α): This query is used to define the ad-vantage of A. When A asks this query to an in-stance Πs
α for α∈{U, S }, the oracle chooses a random bit b∈{0,1}. Return the session key if b = 1, return a random value if b = 0. A is allowed to make a single Test query at any time during the game.
In the model we consider two types of adver-saries according to their attack types that simulated
by the queries issued by an adversary. A passive
adversary is allowed to issue the Execute, Reveal,
Corrupt, and Test queries; an active adversary is additionally allowed to issue the Sendand Extract queries.
B. Definitions of Security
To demonstrate the security of the ID-based MAKA scheme for multi-server environment, we give some definitions of security in this subsection.
Definition 1 Πs
α and Πtβ, where α∈U and β∈S, are said to be partners if they authenticate mutually and establish the session key.
Definition 2 An oracle Πs
α with its partner Πβt is said fresh (or holds a fresh key SK) if the follows two conditions hold:
1.Πs
α accepted a session key SK ≠ NULL with Πβt and neither Πs
α nor Πtβ has been asked for the Reveal query.
2. There is no Corrupt query has been asked before the query Send(Πs
α, M) or Send (Πtβ, M) has been asked.
Definition 3 An ID-based MAKA for multi-server environment offers existential unforgeability and maintains secrecy session key secrecy against adaptive chosen ID attacks if no probabilistic polynomial-time adversary A has a non-negligible advantage in the following game played between an adversary A and infinite set of oracles Πs
α for
IDα∈ID and s∈N.
1. A long-term key is assigned to each user and server through the initialization phase related to the security parameter.
2. The adversary A may ask several queries and get back the results from the corresponding oracles. 3. There is no Reveal (Πs
α) query or Corrupt (IDα)
query have been asked before the Test (Πs
α)
query has been asked.
4. The adversary A may ask other queries during asking the Test (Πs
α) query where Παs is fresh.
A outputs its guess b’ for the bit b which is cho-sen in the Test (Πs
α) query eventually and the
game is terminated.
The advantage of the adversary A is measured by the ability of distinguishing a session key from a random value, i.e., its ability is guessing b. We de-fine Succ to be the event that A correctly guesses the bit b which is chosen in the Test query. The advan-tage of the adversary A in the attacked scheme P is defined asAdvA,P
( )
k = 2⋅Pr[
Succ]
-1.IV. THE PROPOSED SCHEMES
This section presents two ID-based MAKA schemes for multi-server environment. The nota-tions used in the system are summarized in the fol-lowing.
• RC : The registration center. • Ui : The i-th user.
• Sj : The j-th server.
•IDα: The identity of the participant α. • DIDα: The secret key of the participant α.
• AIDi : The anonymous identity of Ui that
gener-ated by RC.
• SIDij : The session identity between the user Ui
and the server Sj.
• Ppub : The public key of RC.
• ⊕: The exclusive-or operation. • ||: The concatenation operation.
A multi-server environment contains three types of participants, the registration center (RC), the n users {Ui | for i=1,…,n} and the m servers {Sj
| for j=1,…,m}. Assume that RC is a trusted party that verifies users’ and servers’ validities, and dis-tributes participants’ private secret keys.
When a user wants to access the resources of the servers, he/she has to register first. There are two scenarios of user’s validity period as follows: Scenario 1. Long validity period: such as visa,
credit card, access control, membership card...etc.
Scenario 2. Anonymous and short validity period: in some situations, users want to access the resources of the service providers anony-mously such as prepaid mobile phone cards, online service prepaid cards, guest temporary security cards ...etc.
We propose two schemes (Scheme I and Scheme II) which are suitable for Scenario 1 and
Scenario 2, respectively.
A. Scheme I
The Scheme I is composed of three phases: setup phase, registration phase, and mutual authen-tication & session key agreement phase.
[Setup Phase]
Let G1 be an additive cyclic group of prime or-der q generated by P and let G2 be a multiplicative cyclic group of the same order as G1. Registration center RC selects two one way collision-resistance cryptographic hash functions H : {0,1}∗→Z
q* and H1:{0,1}∗ →{0,1}l. 2 1 1 G G : G eˆ × → is a bilin-ear mapping from the additive group G1 to the multiplicative group G2.
RC selects a secret key s in Zq*, RC computes
g=eˆ(P,P) and its public key Ppub = sP. Then, RC
publishes the system parameters <G1,G2, P, eˆ, H, >
,g,q ,P
H1 pub [Extract Phase]
When a user Ui (resp. a server Sj) with identity
i
U
ID (resp.
j
S
ID ) wants to register and obtain the secret key, RC computes Ui’s (resp. Sj’s) secret key
P q s DID i Ui = + 1 (resp. P q s DID j Sj = + 1 ), where
qi =H(IDUi ) (resp. qj =H(IDSj)). And RC then
sends i U DID (resp. j S
DID ) to the user Ui (resp.
the server Sj) via a secure channel. The extract
phase is as shown in Figure 1.
RC User Ui P q s DID ID H q Z choose r i U U i * q R i i i + = = ∈ 1 ) ( > < DIDUi Card Smart > <IDUi
Fig.1. Extract phase of Scheme I
[Mutual Authentication & Key Agreement Phase] If a user Ui wants to access the resources of a
server Sj and establish a session key, they execute
the following steps as shown in Figure 2:
1. The user Ui computes qj =H(IDSj) and randomly
chooses ai in Zq*. Ui computes ti =gai, hi=H1(ti),
vi=H1(hi), Qj=Ppub+qjP, Xi=ai⋅Qj, and Yi=
(ai+hi)⋅DIDUi , and then sends <IDUi, Xi, Yi, vi >
to the server Sj.
2. Upon receiving the login request message <
i
U
ID , Xi, Yi, vi >, the server Sj checks whether
i
U
ID exists in the Certificate Revocation List (CRL) or not. If yes, Sj rejects the login request.
Otherwise, Sj continues the following process. Sj
computes ti =eˆ(Xi, DIDSj) and hi=H1(ti), and
then checks if vi=H1(hi). If it does not hold, Sj
rejects the login request. Otherwise, Sj continues
the following process. Sj computes
) ( Ui
i H ID
q = and Qi =Ppub+qiP. And then Sj
checks if eˆ
(
Yi, Qi)
equals to hii g
t ⋅ . If not, Sj
reject the login request. Otherwise, Sj randomly
chooses *
q R
j Z
b ∈ and computes Xj =bj⋅Qj
and zj =H1
(
ti||Xi||Xj||Yi||SIDij)
. And then the server Sj sends <zj, Xj> to the user Ui.3. Upon receiving <zj, Xj>, the user Ui checks
whether zj equals toH1
(
ti||Xi||Xj||Yi||SIDij)
ornot. If not, Ui outputs FAIL and aborts it.
Oth-erwise, the user Ui and the server Sj may
com-pute the common session key ) (
1 i i j i j j ij ij H t||a X ||X||Y||z||SID
SK = ⋅ and ) ( 1 i j i i j j ij ij H t||b X||X||Y||z||SID SK = ⋅
, respectively. It is clear that two session keys are identical by the following equations:
) (
1 ti||ai Xj||Xi||Yj||zj||SIDij
H ⋅
= H1(ti||aibj⋅Qj||Xi||Yj||zj||SIDij) =H1(ti||bj⋅Xi||Xi||Yj||zj||SIDij).
The proposed Scheme I is used for general users with a long validity period, so the server Sj
must check whether
i
U
ID exists in the Certificate Revocation List (CRL) or not. The verification of
i
U
User Ui Server Sj
(
)
i i j U i i i j i i j pub j i i i i a i * q R i S j DID h a Y Q a X P q P Q h H v t H h g t Z choose a ID H q ⋅ + = ⋅ = + = = = = ∈ = ) ( ) ( ) ( 1 1 > <IDUi, Xi, Yi,vi > <zj, Xj ) ( 1 i i j i ij j H t||X||X||Y||SID z check if =( )
(
)
(
i i j i ij)
j j j j * q R j h i i i i pub i U i i i i i S i i U ||SID ||Y ||X ||X t H z Q b X Z b g t , Q Y e P q P Q ID H q h H v t H h , DID X e t ID i i j i 1 1 1 choose ˆ if check ) ( ) ( if check ) ( ˆ CRL if check = ⋅ = ∈ ⋅ = ⋅ + = = = = = ∉ ) || ( 1 i i j i j i j ij ij H t a X ||X||X||Y||z||SID SK = ⋅ SKij =H1(ti||bj⋅Xi||Xi||Xj||Yi||zj||SIDij)Fig.2. Mutual Authentication & Key Agreement Phase of Scheme I
B. Scheme II
Different to the Scheme I, Scheme II uses anonymous identity AIDi and adds user’s valid
pe-riod to achieve user’s anonymity and solve the revocation problem.
The Scheme II is also composed of three phases as Scheme I: setup phase, extract phase, and mutual authentication & session key agreement phase. The setup phase is the same as Scheme I. [Extract Phase]
If there is a user, said Ui, wants to register to
RC. Ui submits the application to RC. Then, RC
randomly chooses * q
i Z
r in and computes Ui’s
anonymous identityAIDi =H(ri), qi=H(AIDi||valid
period), and Ui’s secret key P
q s DID i Ui = + 1 , and sends <AIDi, DIDUi , valid period> to the user Ui
via a secure channel with a smart card. The server
register case is the same as Scheme I. The extract phase is shown in Figure 3.
RC User Ui P q s DID AID H q r H AID Z choose r i U i i i i * q R i i = + = = ∈ 1 period) valid || ( ) ( > < ,validperiod i U i, DID AID Card Smart application
Fig.3. Extract phase of Scheme II
[Mutual Authentication & Key Agreement Phase] If a user Ui wants to access the resources of a
server Sj and establish a session key, they execute
the following steps:
1. The user Ui computes qj =H(IDSj) and randomly
chooses ai in Zq*. Ui computes ti, hi, vi, Qj, Xi,
and Yi as the same way in Scheme I, and sends
<AIDi, Xi, Yi, vi, valid period > to the server Sj.
Xi, Yi, vi, valid period>, the server Sj checks
whether it is overdue or not. If yes, Sj rejects the
login request. Otherwise, Sj computes )
( i Sj
i eˆ X , DID
t = and hi=H1(ti), and then
checks if vi=H1(hi). If it holds, Sj computes qi
=H(AIDi|| valid period). Otherwise, Sj rejects the
login request. Note that the following steps are the same as ones of the mutual authentication & session key agreement phase in Scheme I.
V. SECURITY ANALYSIS
The security of the proposed schemes is based on the CDH, k-CAA and k-mBIDH problems in the random oracle model. In Lemma 1(resp. Lemma 2), we demonstrate that the proposed schemes resist the user (resp. server) impersonating attack. Note that we use the replaying concept of Forking Lemma [16] to prove Lemma 1. We then summa-rize the security of the proposed schemes in Theo-rem 1, and the proof of TheoTheo-rem 1 demonstrates that the proposed schemes provide full forward se-crecy. In conclusion, we formally prove that the proposed two schemes with full forward secrecy can resist user impersonating and server imperson-ating attacks. For convenience, we denote the maximum advantages of the adversary with run-ning time T by the following notations.
• Advk-mBIDH
( )
T eˆ , ,GG1 2 : solving the k-mBIDH problem
under the Gap Diffie-Hellman group (G1,
G2) and bilinear map eˆ: G1×G1→G2. • AdvForge
( )
TUser : impersonating a user (client).
• AdvForge
( )
TServer : impersonating a server.
• AdvCDH
( )
T : solving the CDH problem.• AdvA
( )
T : attacking the proposed schemes.Lemma 1. Assume that the hash functions H and
H1 are random oracles. Suppose that there exists a
forger A who impersonates the user with running time T0, advantage ε0, and given IDU and IDS.
Suppose that A asks H, H1, Send and Extract
que-ries at most qH, qH1, qS and qE times, respectively. If
/q q q q q AdvForge H S S H
User ≥10 21( +1)( + ) , then there
ex-ists an attacker B that solves the k-CAA problem within expected time T1 ≤ 120686qH1T0/ε0.
Proof. The proof is given in Appendix A.
Lemma 2. Assume that the hash functions H and
H1 are random oracles. Suppose that there exists a
forger A who impersonates the server with running time T, advantage ε, and given IDU and IDS.
Sup-pose that A asks H, H1, Send and Extract queries at
most qH, qH1, qS and qE times, respectively. Then
( )
T qq Adv( )
T Adv k-mBIDH e , ,G G H s Forge Server 2 1 1 2ˆ 1 ≤ .Proof. The proof is given in Appendix B.
Theorem 1. Assume that the hash functions are random oracles. Suppose that there exists an ID-based MAKA adversary A with running time T and given IDU and IDS. Then the ID-based MAKA
is a secure scheme providing full forward secrecy and resists user and server impersonating attacks under the hardness of the k-mBIDH, k-CAA, and CDH problems. Concretely,
( )
( )
T Adv( )
T Adv q q /q q q q q T Adv CDH k-mBIDH eˆ , ,G G H s H S S H + + + + ≤ 2 1 1 1 2 1 ) )( 1 ( 10 2 A, where A makes H, H1, Send and Extract queries at
most qH, qH1, qS and qE times, respectively.
Proof. The proof is given in Appendix C.
VI. PERFORMANCE ANALYSIS AND COMPARISONS
The following is the analysis of the computa-tional complexity of our schemes. For convenience, we denote the computational complexity by the fol-lowing notations:
• TGe: The time of executing a bilinear pairing
op-eration eˆ, eˆ: G1 × G1 → G2.
• TGmul: The time of executing a multiplication
op-eration of points.
• TGadd: The time of executing an addition
opera-tion of points.
• Texp: The time of executing a modular exponential
operation.
• TH: The time of executing a one-way hash
Table 1. Comparisons between previously proposed ID-based schemes and the proposed schemes
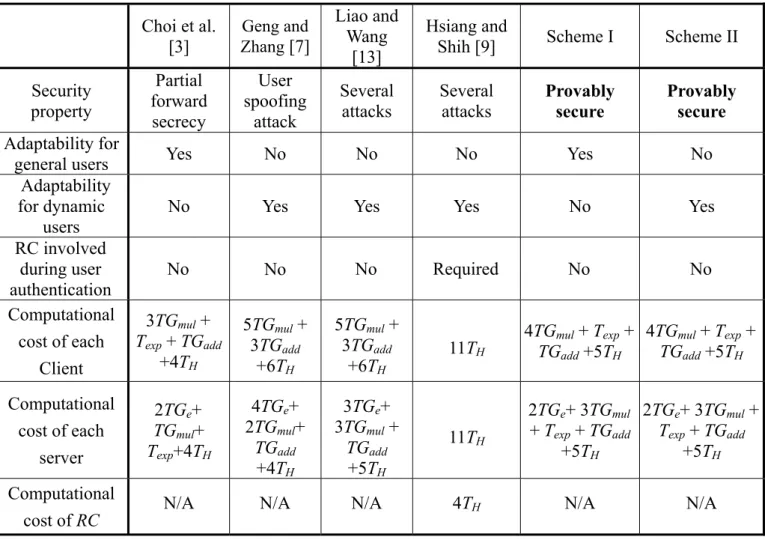
Table 1 the presents comparisons between pre-viously proposed ID-based MAKA schemes for multi-server environment [3, 7, 9, 13] and our schemes in terms of security property, suitable cases and computational complexity.
Adaptability for general users denotes that it is used for general users with a long validity period. On the contrary, adaptability for dynamic users is used for anonymous users. As presented in [3], their scheme provided partial forward secrecy. Hsiang and Shih [9] have shown that Liao and Wang’s scheme [13] suffered from insider attack, masquerade attack, server-spoofing attack, and registration center spoofing attack. In [4], we have presented that Geng and Zhang’s scheme [7] is vulnerable to a user-spoofing attack, i.e., any legal user can create a new user without the registration center RC. Meanwhile, we also demonstrated that Hsiang and Shih’s scheme [9] is vulnerable to an
insider attack and a server-spoofing attack. In which, we have demonstrated that any legal user can compute a system secret value so that anyone who has this system secret can compute any session keys between users and servers, as well as counter-feit the other servers.
As we all know, the time of executing a bilinear pairing operation TGe is more time-consuming than
other operations, TGadd, and TH are trivial in
com-parison with TGe, TGmul, and Texp. Table 1. The
computational complexity of Scheme I is the same as Scheme II. Recently, some implementations [15, 17] of elliptic curve cryptographic primitives and pairings on microprocessors have been proposed. Especially, these implementations focus on the re-lated pairing-based operations for low-power com-puting devices (i.e., smartcards). According to the presented experimental data of related pairing op-erations on microcontrollers [15, 17], it is obvious Choi et al. [3] Geng and Zhang [7] Liao and Wang [13] Hsiang and
Shih [9] Scheme I Scheme II Security property Partial forward secrecy User spoofing attack Several attacks Several attacks Provably secure Provably secure Adaptability for
general users Yes No No No Yes No
Adaptability for dynamic
users
No Yes Yes Yes No Yes
RC involved during user authentication No No No Required No No Computational cost of each Client 3TGmul + Texp + TGadd +4TH 5TGmul + 3TGadd +6TH 5TGmul + 3TGadd +6TH 11TH 4TGmul + Texp + TGadd +5TH 4TGmul + Texp + TGadd +5TH Computational cost of each server 2TGe+ TGmul+ Texp+4TH 4TGe+ 2TGmul+ TGadd +4TH 3TGe+ 3TGmul + TGadd +5TH 11TH 2TGe+ 3TGmul + Texp + TGadd +5TH 2TGe+ 3TGmul + Texp + TGadd +5TH Computational
that our proposed schemes are well suitable for low-power mobile devices.
Note that even though our schemes increase lit-tle computational cost than the previously proposed schemes, our schemes provide complete security properties. Since these schemes [7, 9, 13] suffered from some attacks, they are not suitable for practi-cal applications.
VII. CONCLUSIONS
To develop a secure ID-based mutual authen-tication and key agreement (MAKA) for multi-server environment and low-power mobile devices is an important issue. In this paper, we have proposed two secure and efficient ID-based MAKA schemes providing full forward secrecy for multi-server environment and low-power mobile devices. We have formally proved that our two schemes are secure MAKA schemes in the random oracle model and under the CDH, k-CAA,
k-mBIDH problem assumptions.
ACKNOWLEDGEMENTS
This research is partially supported by Na-tional Science Council, Taiwan, R.O.C., under contract no. NSC97-2221-E-018-010-MY3.
REFERENCES
[1] D. Boneh and M. Franklin, “Identity-based en-cryption from the Weil pairing”, Proc. of Crypto ’01, LNCS 2139, pp.213-229, 2001. [2] X. Cao and S. Zhong, “Breaking a remote user
authentication scheme for multi-server archi-tecture”, IEEE Communications Letters, Vol. 10, No. 8, pp.580-581, 2006.
[3] K.Y. Choi, J.Y. Hwang, D.H. Lee, and I.S. Seo, “ID-based authenticated key agreement for low-power mobile devices”, Springer Lecture Notes in Computer Science, pp.494-505, 2005. [4] Y.H. Chuang and Y.M. Tseng, “Security
weak-nesses of two dynamic ID-based user authenti-cation and key agreement schemes for multi -server environment”, Accepted, 2009.
[5] M.L. Das, A. Saxena, and V.P. Gulati, “A dy-namic ID-based remote user authentication scheme”, IEEE Transactions on Consumer
Electronics, Vol. 50, No. 2, pp.629-631, 2004. [6] M.L. Das, A. Saxena, V.P. Gulati, and D.B.
Phatak, “A novel remote user authentication scheme using bilinear pairings”, Computers & Security, Vol. 25, No. 3, pp.184–189, 2006. [7] J. Geng and L. Zhang, “A dynamic ID-based
user authentication and key agreement scheme for multi-server environment using bilinear pairings”, Power Electronics and Intelligent Transportation System, pp.33-37, 2008.
[8] T. Goriparthi, M.L. Das, A. Saxena, “An im-proved bilinear pairing based remote user au-thentication scheme”, Computer Standard & Interfaces, Vol.31, No. 1, pp. 181-185, 2009. [9] H.C. Hsiang and W.K. Shih, “Improvement of
the secure dynamic ID based remote user au-thentication scheme for multi-server environ-ment”, Computer Standards & Interfaces, Available online 16 December 2008, in press. [10] S. Kim, S. Lim, and D. Won, “Cryptanalysis of
flexible remote password authentication scheme of ICN'01”, Electronics Letters, Vol. 38, No. 24, pp.1519-1520, 2002.
[11] L.H. Li, I.C. Lin, and M.S. Hwang, “A remote password authentication scheme for multi-server architecture using neural net-works”, IEEE Trans. Neural Network, Vol. 12, No. 6, pp.1498-1504, 2001.
[12] J. Li and L.L. Hu, “Improved Dynamic ID-Based Remote User Authentication Scheme Using Smart cards”, WiCOM '08 Wireless Communications, Networking and Mobile Computing, pp.1-4, 2008.
[13] Y.P. Liao and S.S. Wang, “A secure dynamic ID based remote user authentication scheme for multi-server environment”, Computer Stan-dards & Interfaces, Vol. 31, pp.24–29, 2009. [14] I.C. Lin, M.S. Hwang, and L.H. Li, “A new
re-mote user authentication scheme for multi-server architecture”, Future Generation Computer Systems, Vol. 19, No. 1, pp.13-22, 2003.
[15] L. Oliveira, M. Scott, J. Lopez, and R. Dahab, “TinyPBC: Pairings for authenticated iden-tity-based non-interactive key distribution in sensor networks”. Proceedings of INSS 08, pp.173-179, 2008.
argu-ments for digital signatures and blind Signa-tures”, J. of Cryptology, Vol. 13, 2000, pp.361-396.
[17] M. Scott, N. Costigan, and W. Abdulwahab, “Implementing cryptographic pairings on smartcards”. Proc. Cryptographic Hardware and Embedded Systems 2006, LNCS 4249, Springer-Verlag, pp. 134-147, 2006.
[18] J.L. Tsai, “Efficient multi-server authentication scheme based on one-way hash function with-out verification table”, Computers & Security, Vol. 27, No. 3-4, pp.115-121, 2008.
[19] Y.M. Tseng, T.Y. Wu, J.D. Wu, “A pairing-based user authentication scheme for wireless clients with smart cards”, Informatica: International Journal, Vol. 19, No. 2, pp. 285-302, 2008. [20] W.J. Tsuar, C.C. Wu, and W.B. Lee, “A flexible
user authentication for multiserver internet ser-vices”, Springer-Verlag Networking JCN2001, LNCS, Vol. 2093, pp.174-183, 2001.
[21] W.J. Tsuar, C.C. Wu, and W.B. Lee, “An en-hanced user authentication scheme for multi -server internet services”, Appl. Math. Comput., Vol. 170, pp.258-266, 2005.
[22] Y.Y. Wang, J.Y Liu, F.X. Xiao, and J. Dan, “A more efficient and secure dynamic ID-based remote user authentication scheme”, Computer Communications, Vol. 32, No. 4, pp. 583-585, 2009.
APPENDIX: SECURITY PROOFS
A. Proof of Lemma 1.
Proof. B is given an instance (P, sP, q0, q1, q2, ..., qk,
P q s 1 1 + ,s q2 P 1 + , ..., s+qk P 1 ) of the k-CAA problem , where k ≥ max{qH, qS}. Then B’s goal is
to compute P q
s 0
1
+ . B runs A as a subroutine and simulates its attack environment. First, B generates GDH parameters <eˆ, G1, G2> and sets the public system parameters <G1,G2, P, eˆ, H, H1,Ppub,g,q> by letting Ppub = sP and g=eˆ(P,P). B gives the
pub-lic parameters to A.
Without loss of generality, we assume that for any identity, A queries H, H1, Send and Extract at most once, and Send and Extract queries are
pceded by an H-hash query. To ensure identical re-sponding and avoid collision of the queries, B maintains lists LH and LH1. The lists are initially
empty. B interacts with A as follows:
H-query. When A makes a H-query for ID , B α
returns q0 if ID = IDα U. Otherwise, B finds (ID , α
qα) in LH and returns qα if (ID , qα α)∈LH, or returns
qα and adds (ID , qα α) to LH if (ID , qα α)∉ LH. H1-query. When A makes an H1-query for m, B
finds (m, h) in LH1 and returns (m, h) if (m, h)∈LH1,
otherwise returns a random number h and adds (m,
h) to LH1.
Send-query. When A makes a Send( s
α
∏ , start to β
ID ) query, if ID = IDα U, then B chooses random
numbers a, h and computes X = a(sP + q0P), Y = hP, and then B returns <IDU, (X, Y)> to A.
Other-wise, B finds (ID , qβ β) and (ID , qα α) in LH,
chooses random numbers a, h, computes X = a(sP +qβP), Y = (a+h) P
q s+ α
1
, and then returns <ID , α
(X, Y)> to A. The simulation works correctly since
A can not distinguish whether the transcript (X, Y)
is valid or not unless A knows the server S’s long-term secret key DIDS.
Extract-query. When A makes an Extract query for IDα∉{IDU, IDS}, B finds (ID , qα α) in LH.
Then B returns P q s+ α
1
to A.
Eventually, A outputs a new valid message tuple <IDU, (X, Y)>, without accessing any oracle
expect Hash oracles. By replaying B with the same tape but different choices of H1, as done in the
forking lemma [19], A outputs two valid message
tuples <IDU, (X = aQS , Y = (a + h) P q s 0 1 + )> and <IDU, (X = aQS , Y’ = (a + h’) P q s 0 1 + )> where
h≠h’. B can compute (Y − Y’)/(h − h’) = P q
s 0
1 + and outputs it.
The probability that B correctly guesses h and
equal to the running time of the forking lemma which is bounded by 120686qH1T0/ε0, as desired. ■
B. Proof of Lemma 2.
Proof. To compute zS =H1
(
tU||XU||XS||YU||SIDUS)
to pass the verification, A has to ask the H1 hash query oracle for
(
tU||XU||XS||YU||SIDUS)
, and henceA needs to compute tU first. Then we can construct
an attacker B to breaks the k-mBIDH problem by using A with non-negligible probability. B is given an instance of the k-mBIDH problem (eˆ, G1, G2, P,
sP, tP, q0, q1, q2, ..., qk, P q s 1 1 + ,s q2 P 1 + , ..., P q s+ k 1
) , where k ≥ qH, qS. Then B’s goal is to
compute eˆ
( )
P,P s q0t1
+ . B runs A as a subroutine and
simulates its attack environment. B generates GDH parameters <eˆ, G1, G2> and sets the public system parameters <G1,G2, P, eˆ, H, H1,Ppub,g,q> by let-ting Ppub = sP and g =eˆ(P, P). B gives the public
parameters to A. B permeates the k-mBIDH prob-lem into the queries, which are asked by A, in the
l-th session. The probability of A asking Test query
in the l-th session is 1/qS.
Without loss of generality, assume that A does not ask queries on a same message more than once, and the hash query is asked before the Send and Corrupt (or Extract) queries. B maintains lists LH
and LH1 to ensure identical responding and avoid
collision of the queries. B simulates the oracle que-ries of A as follows:
H-query. When A makes an H-query for IDα, B
returns q0 if IDα = IDS. Otherwise, B returns qα if
(IDα, qα)∈LH, B returns qα and adds (IDα, qα) to LH
if (IDα, qα)∉LH.
H1-query. When A makes an H1-query for m, B
returns h if (m, h)∈ LH1. Otherwise, B returns a
random number h and adds (m, h) to LH1.
Send-query. For the convenience, classifying Send queries into two types: user-to-server and server -to-user types, denoted by SendUser and SendServer,
respectively.
– When A makes a SendUser(∏ , Start) query, if αs the query is asked in the l-th session, B chooses a random number r and computes X = tP, Y =
rP and returns <IDU, (X, Y)>. Otherwise, B
finds <IDα, qα> in LH, chooses random
num-bers a, h1, vU, and computes QS = sP + q0P, X =
aQS, Y =
(
)
P q s h a α + + 1 , tα = e(P, P)a. Then Badds (tα, h1) and (h1, vα) to LH1 and returns <IDα,
X, Y, vα>.
– When A makes a SendServer(∏ , (IDαs β, X, Y, vβ))
query, B chooses random numbers z and Xα,
returns <z,Xα> and adds <(tβ|| X|| Xα|| Y||SIDβα),
z> to LH1 .
Execute-query. When A asks an Execute(IDU,IDS)
query, then B returns the transcript <(IDU, X, Y, vU ),
(z, XS)> by using above simulation of Send queries. Extract-query. When A asks an Extract query on
IDα∉{ IDU , IDS }, B finds <IDα, qα> in LH and
returns P
q s+ α
1
to A.
Corrupt-query. When A makes a Corrupt query for IDα∈{ IDU , IDS }, B finds < IDα, qα> in LH. Then B returns P q s+ α 1 to A.
Reveal-query. When A makes a Reveal query, B returns a random number.
Test-query. When A makes a Test query, if the query is not asked in the l -th session, B aborts. Otherwise, B randomly chooses a bit b, B returns the session key if b = 1, else returns a random number.
The success probability of B depends on the event that A asks the Test query in the l -th session
and asks a secret value tU
= eˆ
(
XU,DIDS)
= ˆ( 1 ) 0 P q s tP, e + =( )
t q s P,P e 0 1 ˆ + to H1hash oracle. In the above simulation, the probabil-ity that A asks the Test query in the l -th session is 1/qS. If the advantage AdvServerForge of A correctly
guess b in the Test query is ε, then A issues a query for H1(tU) with advantage 2ε. Thus, if A asks the
tU appears in the list LH1 with probability at least 2ε.
Therefore, B solves the k-mBIDH problem with probability at least 2ε/qSqH1 as required, therefore
we have Adv
( )
T q q ε k-mBIDH eˆ , ,G G H s 2 1 1 2 ≤ . Hence, we have Forge ServerAdv = qq Advk-mBIDH
( )
T eˆ , ,G G H s 1 1 2 2 1 ≤ ε .■ C. Proof of Theorem 1.Proof. Let A be an active adversary that gets
ad-vantage in attacking our ID-MAKA. The adversary
A can get the advantage by following cases:
Case1. Forging authentication transcripts and im-personating a user.
Case2. Forging authentication transcripts and im-personating a server.
Case3. Get the session key without altering tran-scripts.
In Case 1, we construct a Forger FU that
gen-erates a valid message pair <ID, (X, Y)> as follows:
FU honestly generates all other public and secret
keys for the system. FU simulates the oracle queries
of A in the natural way. Let ForgeU denotes the
event that A generates a new and valid message pair <ID, (X, Y)>. Then the success probability of
FU satisfiesPrA
[
ForgeU]
≈AdvFForge( )
T ≈ AdvForge( )
T .By Lemma 1, PrA
[
ForgeU]
is negligible, hence( )
TAdvForge is negligible.
In Case 2, Let ForgeS denotes the event that A
impersonates a server. By Lemma 2, we have
[
Forge]
q q Advk-mBIDH( )
T e , ,G G H s S A 2 1 1 2ˆ 1 Pr ≤ . It is obviousthat qq Advk-mBIDH
( )
T e , ,G G H s 1 1 2ˆ 2 1 is negligible since( )
T Advk-mBIDH e , ,GG1 2ˆ is negligible and qS, qH1 are finite.
In Case 3, it is obvious that the problem for getting the session key between IDU and IDS can be
reduces to the Computational Diffie-Hellman (CDH) problem. If A can get the session key with-out altering transcripts, then A can compute
j j i b Q
a ⋅ ⋅ from Xi =ai⋅Qj and Xj =bj⋅Qj
with the advantage AdvCDH
( )
T with running time T.In summary for three cases, we have
( )
T Adv( )
T Adv( )
T Adv( )
TAdv Forge CDH Server Forge User + + ≤ A , and