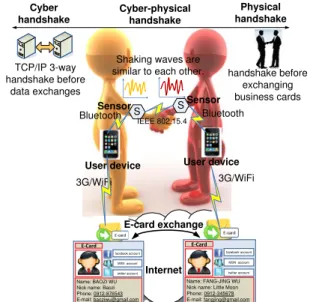
Cyber-Physical Handshake
Fang-Jing Wu
Department of Computer Science, National Chiao Tung
University, Hsin-Chu, Taiwan
fangjing@cs.nctu.edu.tw
Feng-I Chu
Department of Computer Science, National Chiao Tung
University, Hsin-Chu, Taiwan
fychu@cs.nctu.edu.tw
Yu-Chee Tseng
∗Department of Computer Science, National Chiao Tung
University, Hsin-Chu, Taiwan
yctseng@cs.nctu.edu.tw
ABSTRACT
While sensor-enabled devices have greatly enriched human interactions in our daily life, discovering the essential knowl-edge behind sensing data is a critical issue to connect the cyber world and the physical world. This motivates us to design an innovative sensor-aided social network system, termed cyber-physical handshake. It allows two users to nat-urally exchange personal information with each other after detecting and authenticating the handshaking patterns be-tween them. This work describes our design of detection and authentication mechanisms to achieve this purpose and our prototype system to facilitate handshake social behavior.
Categories and Subject Descriptors: C.2.1 [Network
Architecture and Design]: Wireless communication
General Terms: Algorithms, Design, Experimentation Keywords: cyber-physical system, participatory sensing,
pervasive computing, social network, wireless sensor network
1.
INTRODUCTION
Recently, sensor-enabled mobile phones have become es-sential tools in the study of cyber-physical systems (CPSs) [1]. CPSs enrich the interactions between the virtual and the physical worlds and sensor-aided social networking has been recognized as one of the main CPS applications [2, 3]. This work designs an innovative sensor-aided social net-work system, termed cyber-physical handshake, to enable natural information exchange after detecting and authenti-cating the handshaking patterns between two persons. In the physical world, the handshake behavior between two people implies that a social link will be authenticated be-tween them before they exchange personal information (e.g., exchanges of business cards). On the other hand, in the cy-ber world, a handshake procedure is adopted by two nodes to authenticate each other before they start data exchanges. The work follows the concept of “handshakes” to design an authentication mechanism based on sensing patterns to fa-cilitate automatic data exchanges between two users after they have a handshake, as shown in Fig. 1. Instead of gen-erating and authenticating shared keys [4, 5], our system is ∗Y.-C. Tseng’s research is co-sponsored by MoE ATU Plan, by NSC grants 97-3114-E-009-001, 97-2221-E-009-142-MY3, 98-2219-E-009-019, and 98-2219-E-009-005, 99-2218-E-009-005, by ITRI, Taiwan, by III, Taiwan, by D-Link, and by Intel.
Copyright is held by the author/owner(s).
SIGCOMM’11, August 15–19, 2011, Toronto, Ontario, Canada. ACM 978-1-4503-0797-0/11/08. S S Sensor User device Bluetooth IEEE 802.15.4 3G/WiFi 3G/WiFi Bluetooth Internet Sensor User device E-card exchange
Shaking waves are similar to each other.
Cyber-physical handshake Physical handshake Cyber handshake TCP/IP 3-way handshake before data exchanges handshake before exchanging business cards Name: BAOZI WU Nick name: Baozi Phone: 0912-876543 E-mail: baoziwu@gmail.com EͲCard facebook account MSN account twitter account Name: FANG-JING WU Nick name: Little Moon Phone: 0912-345678 E-mail: fangjing@gmail.com EͲCard facebook account MSN account twitter account
Figure 1: Architecture of our cyber-physical hand-shake system.
a light-weight approach which incurs less computation over-head and is more suitable for simple sensor devices (e.g., a watch).
2.
SYSTEM ARCHITECTURE
The basic idea of the cyber-physical handshake system is to allow two users to exchange data if they have a handshake with each other. When two users make friends with a hand-shake in the physical world, the shaking waves perceived by the two users’ sensor nodes will have high degree of similar-ity in both frequency and time domains. We then use the similarities to authenticate a handshake behavior. Fig. 1 shows our system architecture. Each user is equipped with a smart phone and wears a watch-like sensor node with an accelerometer on his/her wrists. Sensor nodes follow IEEE 802.15.4 to communicate with each other. Each sensor node is associated with its user’s smart phone through bluetooth. Each sensor node is responsible for detecting and reporting handshaking samples to its user’s smart phone. The smart phone will compute a value of similarity between the two users’ samples. If the value of similarity is greater than a predefined threshold, it will exchange the user’s E-card with the other user over the Internet.
2.1
Software Design
Our software design is composed of four phases, as shown in Fig. 2.
Compute similarity Wf in frequency domain
Compute similarity Wt in time domain
WfTf Tf-Wf<įf Wt>Tt Y Y N N Phase 1: Handshake Detection
Sensor node Detect shaking event? Y Log N samples Receive a confirm_shaking message? Exchange N samples
Report samples to the user device
User device
N
Phase 2: Handshake Capture Y
Send a confirm_shaking message N
Phase 3: Pattern Authentication Y
Inform its sensor node to exchange email addresses Phase 4: E-card Exchange
Get email addresses from its sensor node Send E-card to the specified email address
Frequency-domain authentication Time-domain authentication Y N
Figure 2: Software design of our system. Phase 1: handshake detection. In this phase, we use
each sensor node to detect shaking events. We sample data at a rate of Rs. For each sample ν, we check if the shaking condition|ν − 1g| > τsholds, where g is the gravity and τs is a predefined threshold. If the number of shaking samples per second detected is greater than Rs/2, the sensor node will broadcast a confirm shaking message and enter the next phase.
Phase 2: handshake capture. In this phase, the
sen-sor node logs the upcoming N samples and checks if it has received a confirm shaking message recently. If so, it ex-changes these N samples with that sensor node and then reports all these samples to its smart phone.
Phase 3: pattern authentication. In this phase, each
smart phone will compute the values of similarity in both frequency and time domains to decide whether the two sam-ples are resulted from the same handshake in the physical world. First, we compute the value of similarity in the fre-quency domain between two samples, say a and b, by Wf =
1 5 ∫5 f =0Cab(f ), where Cab(f ) = |Pab(f )|2 Paa(f )×Pbb(f ) is the
magni-tude squared coherence of the two samples. Here, we only
consider the coherence between 0∼ 5 Hz because the hand-shake frequency of a human can hardly exceed this range. If Wf ≥ Tf, we have a handshake match and enter the next phase, where Tfis a predefined threshold. Otherwise, if Tf− Wf < δf, where δf is a small value, then the value of sim-ilarity in the time domain will be computed by the Pearson’s correlation coefficient Wt=|(N1−1)Σ
N
i=1(Ai−A)×(Bi−B)
σa×σb |, where
σa and σb are the standard deviations of a and b, respec-tively. Here, Ai(resp., Bi) and A (resp., B) denote the i-th reading and the mean of the a’s (resp., b’s) samples. Here,
δf is a guard parameter to involve the time-domain hand-shake detection. If Wt > Tt, a handshake is detected and we enter phase 4, where Ttis a predefined threshold.
Phase 4: E-card exchange. In this phase, the user
device will inform its sensor node to exchange user’s email address with the other sensor. Then it sends a personal E-card to that address over the Internet for further social networking behaviors.
2.2
Demonstrations
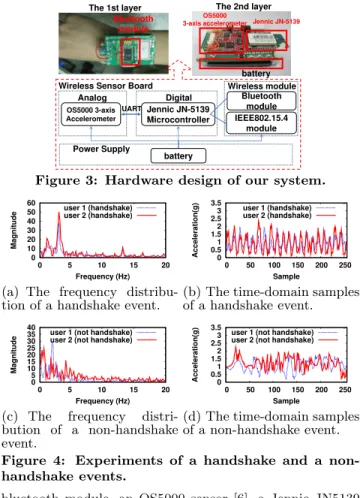
Each sensor node is a two-layer sensor board including a
Analog OS5000 3-axis Accelerometer Digital Jennic JN-5139 Microcontroller UART IEEE802.15.4 module Wireless module Power Supply battery Wireless Sensor Board
Bluetooth module
OS5000
3-axis accelerometer Jennic JN-5139 Bluetooth
module
battery The 1st layer The 2nd layer
Figure 3: Hardware design of our system.
0 10 20 30 40 50 60 20 15 10 5 0 Magnitude Frequency (Hz) user 1 (handshake) user 2 (handshake)
(a) The frequency distribu-tion of a handshake event.
0 0.5 1 1.5 2 2.5 3 3.5 0 50 100 150 200 250 Acceleration(g) Sample user 1 (handshake) user 2 (handshake)
(b) The time-domain samples of a handshake event. 0 5 10 15 20 25 30 35 40 20 15 10 5 0 Magnitude Frequency (Hz) user 1 (not handshake) user 2 (not handshake)
(c) The frequency distri-bution of a non-handshake event. 0 0.5 1 1.5 2 2.5 3 3.5 0 50 100 150 200 250 Acceleration(g) Sample user 1 (not handshake) user 2 (not handshake)
(d) The time-domain samples of a non-handshake event.
Figure 4: Experiments of a handshake and a non-handshake events.
bluetooth module, an OS5000 sensor [6], a Jennic JN5139 [7], and a battery, as shown in Fig. 3. Each OS5000 has a 3-axes accelerometer. We set Rs=40Hz. Jennic JN5139 has a micro-controller and a built-in 2.4GHz/IEEE802.15.4 wire-less module. The user device is a smart phone (HTC Touch 2 [8]) with a bluetooth and a WiFi/3G wireless modules.
We also conduct experiments to log shaking waves of a handshake event and a non-handshake event for 7 seconds. Fig. 4 shows the experimental results, where the two users’ sensing data have high degree of similarity in a handshake event in both frequency distribution and time domain sam-ples.
3.
REFERENCES
[1] F.-J. Wu, Y.-F. Kao, and Y.-C. Tseng, “From wireless sensor networks towards cyber physical systems,” Pervasive and Mobile Computing, to appear.
[2] S. Gaonkar, J. Li, and R. R. Choudhury, “Micro-Blog: Sharing and querying content through mobile phones and social participation,” in Proc. ACM Int’l Conf. on Mobile Systems, Applications, and Services, 2008, pp. 174–186. [3] M.-C. Chiu, S.-P. Chang, Y.-C. Chang, H.-H. Chu, C. C.-H.
Chen, F.-H. Hsiao, and J.-C. Ko, “Playful bottle: a mobile social persuasion system to motivate healthy water intake,” in Int’l Conf. Ubiquitous Computing, 2009, pp. 185–194. [4] R. Mayrhofer and H. Gellersen, “Shake well before use:
Intuitive and secure pairing of mobile devices,” IEEE Trans. Mobile Computing, vol. 8, no. 6, pp. 792–806, 2009. [5] D. Bichler, G. Stromberg, M. Huemer, and M. L¨ow, “Key
generation based on acceleration data of shaking processes,” in Int’l Conf. Ubiquitous Computing, 2007, pp. 304–317. [6] “Os5000,” http://www.ocean-server.com.
[7] “Jennic JN5139,” http://www.jennic.com. [8] “HTC Touch 2,”
http://www.htc.com/tw/product/touch2/overview.html.