On Synchronized Channel Sensing and Accessing for
Cognitive Radio Users in IEEE 802.11 Wireless
Networks
TakChon Lou
1, Hsi-Lu Chao
1, and Tzu-Jane Tsai
21
Department of Computer Science, National Chiao Tung University, Hsinchu, Taiwan
2
Information & Communications Research Laboratories, Industrial Technology Research Institute, Hsinchu, Taiwan
Email: hlchao@cs.nctu.edu.tw
Abstract-One of the most challenging issues in cognitive radio systems is channel sensing and channel accessing. In this paper, a synchronized channel-sensing and accessing for cognitive radio users in IEEE 802.11 wireless networks is proposed. The mechanism consists of two phases: fast channel sensing and proactive channel vacating. Fast channel sensing is for a pair of cognitive radio users to search an available channel time-efficiently; proactive channel vacating is for the pair of cognitive radio users to be aware of the presence of primary users and vacate the occupied channel as quick as possible. We utilize the concept of channel hopping to reduce the average channel sensing time of cognitive radio users. Besides, through the designed interruption mechanism, cognitive radio users can create opportunities for primary users to claim the spectrum and thus minimize the caused interference to primary users. From the simulation results, our proposed protocol can efficiently balance the tradeoff between throughput performance of a cognitive radio network and waiting time of primary users to claim channels.
Keywords-Cognitive radio, channel sensing, channel accessing, synchronized channel hopping, channel vacating
I. INTRODUCTION
As more and more versatile multimedia services emerge in the market, it becomes obvious that the spectrum is much scarcer and thus the current frequency allocation schemes cannot accommodate the needs of all services. Cognitive radio [1] is a promising technique to alleviate the problem of spectrum shortage. The concept of cognitive radio is that unlicensed users (referred to as cognitive radio users, CR users) can access the spectrum owned by licensed users (referred as primary users, PUs), while they cannot interfere with primary users when exploiting the spectrum. Thus to realize the technique of cognitive radio, a cognitive radio user must have the ability to measure, to sense, and to learn channel characteristics and availabilities [2]. In addition, primary users can claim the spectrum anytime when they have data to send, thus cognitive radio users should be able to identify the presence of primary users in time and vacate the occupied bands immediately to prevent/reduce the interference to primary users.
The focus of this paper is to design a spectrum sensing and accessing mechanism for cognitive radio users in 802.11-based networks. Spectrum sensing is the task for cognitive radio users to collect information about spectrum
usage and existence of primary users; while spectrum accessing is the task for cognitive radio users to transmit data packets efficiently and vacate the occupied data channel to primary users as quick as possible.
The rest of this paper is organized as follows. Related work is discussed in Section II. System model and assumptions is presented in Section III. The detailed protocol design of out mechanism is described in Section IV. Section V presents and discusses the simulation results, while Section VI concludes the paper.
II. RELATED WORK
Based on the way a CR user searches for free channels, existing spectrum sensing schemes can be classified into two categories: proactive and reactive. The former is periodic basis, and a CR user continuously searches for unoccupied channels, and maintains a table to record the characteristics of sensed channels (such as signal-to-noise value, and occupancy), even if it has no data to send currently; the latter, contrarily, is on-demand basis and a CR user searches for unoccupied channels only when it has data frames to transmit.
A. Proactive approaches
Proactive schemes mainly mean that a CR user needs to sense all channels continuously regardless of having data to transmit or not. In particular, in [3], a statistical channel allocation MAC protocol, named SCA-MAC, is proposed. In SCA-MAC, it reduces the total transmission time efficiently and improves the successful delivery rate. However, the disadvantages include (i) data channel selection is based on the recorded statistics of the CR receiver, and the designated spectrum hole may not be idle for the CR sender; (ii) to sense multiple continuous available channels is time consuming; and (iii) how to achieve synchronization is not addressed.
Instead of dedicating the control channel to control message exchanges, [4] utilizes two radios to do channel sensing (named listening radio) and data transmission (named data radio). This protocol can well exploit available channel resources, its implementation is complicated and hardware-constrained because each CR user needs to be equipped two transceivers and globally synchronized, which means that all CR users achieve time synchronization. Besides, CR users would exchange massive packets which are bandwidth consuming.
B. Reactive approaches
In [5], there is a dedicated channel which is always available for CR users to exchange control information. Each beacon interval is divided into three phases: “channel selection”, “sensing”, and “data transmission”. One characteristic of [5] is that CR users can transmit packets on not only data channels, but also the control channel, and thus it achieves high channel utilization. However, [5] has the same disadvantage as [4] that all CR users achieve global synchronization. Another drawback of [5] is massive exchanges of control messages in channel selection phase.
A hardware-constraint cognitive MAC (HC-MAC) was proposed in [6]. Considering limitations of sensing constraint and transmission constraint, the authors formulate an optimal stopping problem by considering sensing overhead and transmission limitation. However, the drawback of HC-MAC is only one CR pair can do transmissions at a time.
A channel-hopping based cognitive radio MAC mechanism was proposed in [7]. Each CR user has its own channel hopping sequence, which is determined by its unique ID (e.g., MAC address). All CR users share the same hopping sequence generation function, and thus a potential CR sender can easily obtain the hopping sequence of its intended CR receiver. The advantage of this approach is it does not need a dedicated control channel. However, for a potential CR sender, how to meet its intended CR receiver on a specific channel efficiently is not elaborated in [7].
Through sensing the whole spectrum and exchanging massive control messages with each other to determine a best and available channel is a time-inefficient way for cognitive radio users. The reason is that the traffic behavior of primary users is unpredictable. Therefore, it may occur that primary users come back to claim the spectrum when CR users are sensing channels and exchanging control messages and are not yet transmitting data. However, detailed detection/interruption mechanisms were not proposed in literature. Therefore, we employ an interruption mechanism for primary users to be able to claim channels.
III. SYSTEM MODEL AND ASSUMPTIONS
The adopted system architecture in this paper is shown in Fig. 1. Here we consider an IEEE 802.11-based service network, which consists of an access point (AP) and multiple primary users (PUs), as the primary network. On the other hand, CR users operate in an ad hoc mode, and thus these CR users form a distributed cognitive radio network (CRN). In this CRN, we do not consider routing issue and thus all are single-hop transmissions, i.e., a pair of CR users can communicate only when they are one-hop neighbors. Besides, we make some assumptions:
1. Similar to [8, 9], each CR user equips only one transceiver, and it has the capability of sensing the presence of PUs on the channel switching to.
2. There is a dedicated channel for CR users to exchange control messages, and N data channels.
3. When a CR user is idle, it always listens to the control channel.
4. A pair of CR users can start to transmit data packets when they find a channel which is not currently occupied by PUs and other CR users.
5. CR users utilize CSMA/CA protocol to resolve collisions on the control channel.
IV.THE PROPOSED SYNCHRONIZED CHANNEL SENSING AND ACCESSING MECHANISM
In this section, we introduce our proposed synchronized channel sensing and accessing mechanism. Through the proposed mechanism, a pair of CR users can find and sense an unoccupied channel efficiently, and then transmit data frames on that channel. In our approach, we define three control frames and four parameters. In the following, we use 802.11 MAC frames as an example to elaborate our protocol. However, the proposed mechanism can be applied to other contention-based wireless primary networks.
A. New Control Messages
1. RTSCR: this control frame is utilized by a potential CR
sender to inform the CR receiver its transmission intention. Besides, two parameters are included in the frame: initial selected data channel ID, and increment-per-hop, both are introduced soon. RTSCR is sent at the
control channel only.
2. CTSCR: this control frame is utilized for a CR receiver to
reply its CR sender that it is idle and ready to sense the specified initial data channel. Similarly it is sent at the control channel only.
3. Ready-To-be-Interrupted (RTI): this control frame is sent by a CR sender after receiving a data ACK from the CR receiver and is for one-hop neighboring primary users to claim the data channel, if they have data to send.
B. New Parameters
1. Initial selected data channel ID (denoted as Ch(1)): it is randomly selected by a CR sender, and is the first data channel that the pair of CR users will switch to do channel sensing. Ch(1) is a positive integer, and
( )
N Ch ≤≤ 1
1 .
2. Increment-per-hop (h): it is randomly generated by a CR sender to derive the ID of next-try data channel. h must satisfy: (i) h is less or equal to the number of data channels (i.e., N), and (ii) h and N are relative primes. For example, when N=8, h could be 1, 3, 5, and 7. The reason of N and h being relative primes is to avoid many CR pairs sensing the same subset of data channels. 3. TXOPCR: the bounded time interval during which a CR
user can send as many frames as possible. The impact of a large TXOPCR value is long sensing time of finding an
Figure 1. The adopted system architecture consisting of primary users and CR users
available idle channel for a CR user. In this paper, the unit of TXOPCR is frames. For example, TXOPCR is m frames indicates a CR sender can transmit at most m frames on a data channel.
4. SIFSCR: the small time gap between a RTI and the next data frame. This short time interval is providing opportunities for PUs to claim channels. When a PU wants to send data at a channel, and hears a RTI control frame, it replies with a RTS and then the CR sender vacates the channel immediately. If there are multiple RTSs sent within SIFSCR and collisions occur, the CR sender detects the presence of PUs and still returns the occupied data channel. SIFSCR is long enough for a PU to send a RTS (i.e., SIFSCR >tRTS). In this paper, we set
SIFSCR=10×SIFS. However, it is adjustable to improve throughput performance.
C. The proposed channel sensing and accessing algorithm
The proposed channel sensing and accessing algorithm for CR users consists of two phases: fast channel sensing and proactive channel vacating.
C.1 Fast channel sensing
When a CR sender, say CRA, intends to transmit data to a CR receiver CRB, it first checks the availability of CRB by sending a RTSCR on the control channel. Both the randomly
generated Ch(1) and h are encapsulated in the RTSCR. The
control channel access and collision resolution are based on the CSMA/CA mechanism. If CRB is listening to the control channel and successfully receives the RTSCR, it replies CRA a CTSCR. At this moment, CRA and CRB achieve synchronization and switch to channel Ch(1) for channel sensing purpose.
When hopping to Ch(1), both CRA and CRR listen to Ch(1) for t time interval to avoid interfering on-going transmissions of PUs or CR users. Here we set t be 2ms. If Ch(1) is still idle after t time, CRA and CRB exchange RTS and CTS as usual. Otherwise, CRA and CRB hop to the next data channel and then sense again. The reason that CRA and CRB exchange RTS and CTS at the data channel is to avoid collisions when more than two pairs of CR users sensing the same data channel. The next sensed data channel is determined by (1).
( )
i+1 =(
Ch( )
i +h)
modN,i≥1Ch , (1)
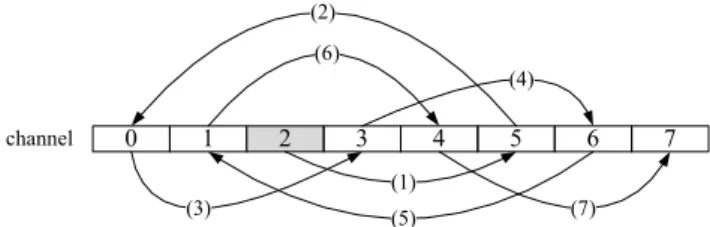
where i indicates the ith channel hopping, and N is the number of data channels. Using Fig. 2 as an example, the number of data channel N is 8 (numbered 0-7); Ch(1) and h are 2 and 3, respectively. Therefore, the pair of CR users will first sense channel 2. If channel 2 is busy, they will further sense channel 6 (because [(2+3) mod 8]=5). The complete hopping sequence is [2, 5, 0, 3, 6, 1, 4, 7, 2, 5, 0, 3, 6, …]. We observed that the hopping sequence is repeated and each channel is sensed once per run. We also observed that different hopping generation functions have no impact on a CRN’s system performance through simulations. Due to limited papers, we do not show this result in this paper.
For a specific hopped data channel, say Ch(i), there are four possible sensing results:
1. Ch(i) is idle for both CRA and CRB
In this case, CRA sends a RTS frame to CRB immediately and waits for CRA’s reply. Upon successfully receiving the CTS, CRA starts to transmit data frames to CRB. After
successfully transmitting a data frame, CRA broadcasts a RTI to one-hop neighboring PUs and waits for SIFSCR so that PUs can claim the channel. Upon receiving RTS sent by a PU, CRA and CRB vacate the data channel and hop back to the control channel. Besides, CRA can send at most TXOPCR frames at that data channel. If there are still queued frames to send, CRA and
CRB must switch to the control channel, and run the procedure of fast channel sensing again.
2. Ch(i) is idle for CRA but busy for CRB
Similar to case 1, CRA sends a RTS frame to CRB immediately. However, CRB cannot successfully receive the RTS and thus it does not reply a CTS frame. After staying at
Ch(i) for T time interval, both CRA and CRB hop to Ch(i+1) simultaneously. T is the maximum time interval that CRA and
CRB stay at Ch(i), and it can be derived by CRA and CRB independently. It is known that T ≥t+tRTS +2SIFS+tCTS, where
t
RTS, andt
CTS are the transmission time for RTS and CTS frames. We set T =t+tRTS +2SIFSCR+tCTS in this paper.3. Ch(i) is busy for CRA but idle for CRB
Since Ch(i) is busy for CRA, CRB does not transmit a RTS frame. After waiting an amount of T time duration, both CRA and CRB hop to Ch(i+1).
4. Ch(i) is busy for both CRA and CRB
Similar to case 3, CRA and CRB hop to Ch(i+1) after T time interval.
The process of data channel hopping and sensing does not terminate till CRA and CRB find one data channel which is not occupied by PUs and other CR users.
C.2 Proactive channel vacating
There are two situations for a CR pair to vacate the occupied data channel: one is they have accessed the data channel long enough (i.e., it has already transmitted TXOPCR frames at that data channel), and the other is PUs want to claim that data channel. For the former, the CR sender and receiver stop transmitting/receiving data frames and then hop back to the control channel, as described in Sec. III.C.1. Our phase 2 design focuses on the latter. To be aware of the presence of potential primary senders, there must be a mechanism for potential primary senders to interrupt the transmissions of a CR pair. The design challenges of this interruption mechanism are twofold: how does a potential primary sender recognize that the data channel is occupied by a CR pair or other primary users, and how to make a CR pair to automatically return the borrowed data channel. We
(2) 0 1 2 3 4 5 6 7 (1) (3) (4) (5) (6) (7) channel
Figure 2. An illustrative example of data channel hopping sequence: N=8,
elaborate our interruption mechanism in the following. Both challenges are dealt with RTI control frame.
After transmitting a data frame and successfully receiving the ACK, a CR transmitter sends a RTI frame and then waits for SIFSCR long. Within this time duration, potential primary senders are able to send RTS to its intended primary receiver. Upon receiving RTS messages, the CR sender/CR receiver knows the presence of primary users, and they will hop to the control channel. There are three possible actions after a CR sender transmitting a RTI:
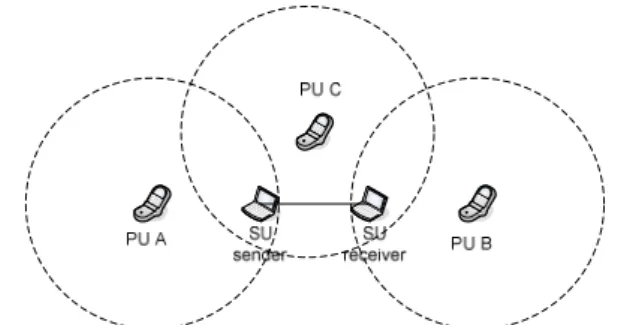
1. Case 1: the potential primary sender is a neighbor of the CR sender, while it is not a neighbor of the CR receiver In Fig. 3, PUA is such a potential primary sender. PUA sends a RTS frame upon receiving RTI frame. The CR sender then stops transmitting data and hops back to the control channel. In the meantime, the CR receiver does not receive further data frames, and thus is aware that the CR sender must be interrupted by a potential primary sender. The CR receiver hops back to the control channel, too. If the CR sender still has data for the CR receiver, it generates a new initial data channel ID and increment-per-hop, and sends communication invitation on the control channel. The corresponding timetable of message exchanges is in Fig. 4(a).
2. Case 2: the potential primary sender is a neighbor of the CR receiver, but it is not a neighbor of the CR sender Again in Fig. 3, PUB is such a potential primary sender. When the CR sender sends a RTI frame, the CR receiver is idle for SIFSCR long. Since tSIFSCR is longer than tDIFS, thus
PUB can send a RTS frame to its receiver. At this time, the CR receiver is aware of the presence of a primary sender. The CR receiver hops back to the control channel. Though the CR sender keeps sending data frames, it does not receive any ACKs from the CR receiver. Therefore, the CR sender vacates the occupied data channel and hops back to the control channel, too. The corresponding timetable of message exchanges is in Fig. 4(b).
3. Case 3: the potential primary sender is a neighbor of the CR sender and the CR receiver
PUC is such a potential primary sender shown in Fig. 3. Both the CR sender and the CR receiver receive the RTS frame sent by PUC, and then hop back to the control channel. The corresponding timetable of message exchanges is in Fig. 4(c).
V. PERFORMANCE EVALUATION
To evaluate the performance of the designed channel sensing and accessing algorithm presented in Sec. IV, we develop a simulation program to discover the system throughput of a cognitive radio network, and the impact on primary users. We compared our approach with [5], i.e., OSA-MAC. Again, we only consider single-hop flows of cognitive radio users.
We compare the performance of our mechanism and OSA-MAC. In this experiment, there are six channels: one is control channel, and the others are data channel. Each data channel is occupied by primary users with Poisson arrival distribution. Cognitive radio users are always backlogged. Settings of simulation parameters are the same as in Table I. The throughput of a considered CRN is shown in Fig. 5. We
observed that our proposed mechanism outperforms OSA-MAC. The reason is, in our approach, a CR sender can transmit multiple frames (the maximum is TXOPCR frames) when an available data channel is sensed. Contrarily, in OSA- MAC, a CR sender only transmits one frame at a time. Note that our approach still performs better than OSA-MAC upon TXOPCR=1. The reason is that the sensing time our approach is shorter than that of OSA-MAC. We further investigate the impact of TXOPCR on primary users. We found that it has no impact on the throughput performance of primary users, shown in Fig. 6. Thanks to the designed interruption mechanism so that primary users can claim borrowed data channels in time.
(a) Timetable of case 1: PUA is a neighbor of CR sender
(b) Timetable of case 2: PUB is a neighbor of CR receiver
(c) Timetable of case 3: PUC is a neighbor of CR sender and CR receiver Figure 4. Explanation of message exchanges for proactive channel vacating
phase
Followed, we investigate the impact of primary users’ traffic load on CR users’ throughput, and the result is shown in Fig. 7. Here we set the number of CR pairs be 15, and vary primary users’ traffic load from 0.1 to 1. For example, 0.2 traffic load indicates that primary users generate packets to utilize 20% bandwidth in total. Our proposed mechanism achieves a higher throughput than OSA-MAC, except when primary users’ traffic load is larger than 0.85. Specifically, the CRN throughput of our algorithm is zero when PUs utilize all bandwidth; contrarily, OSA-MAC still has 0.77 Mbps throughput. The reason is in OSA-MAC, CR users are able to send data frames on not only data channels, but also the control channel. Thus CR users can send frames on the control channel, even if they cannot borrow data channels from PUs.
VI. CONCLUSION AND FUTURE WORK
In this paper, a synchronized channel sensing and accessing mechanism for cognitive radio users has been proposed. This mechanism consists of two phases: fast channel sensing and proactive channel vacating. One unique design in our protocol is interruption mechanism, which is achieved by employing RTI control frames. Through the assistance of RTI, we balance the tradeoff between throughput performance of a CRN and PUs’ channel claiming time. Indeed, primary users may not be able to identify RTI frame due to CR users operating in a dissimilar network system. This problem can be easily solved through adjusting the value of SIFSCR to make primary users “believe” channels are idle and are able to send transmission invitations to intended receivers. Computer simulation was conducted to demonstrate the superior performance of our protocol over that of OSA-MAC.
Our future work is analyzing the proposed mechanism, and extending this mechanism to support multi-hop flows in a cognitive radio network.
ACKNOWLEDGMENT
This work was supported in part by Industrial Technology Research Institute under grant T2-98019-4, in part by National Science Council under grant NSC 97-2219-E-009-002-, and in part by NCTU/MTK Research Center.
REFERENCES
[1] FCC Spectrum Policy Task Force, “Report of the spectrum efficiency working group,” Federal Communications Commission, Technical
Report 02-155, 2002.
[2] T. Yucek and H. Arslan, “A survey of spectrum sensing algorithms for cognitive radio applications,” IEEE Communications Survey and
Tutorials, pp. 116-130, vol. 11, no. 1, 2009.
[3] C.-C. Hsu, S. L. Wei and C.-C. Kuo, “A Cognitive MAC Protocol Using Statistical Channel Allocation for Wireless Ad-hoc Networks,” in Proc.
of IEEE Wireless Communications & Networking Conference, pp.
105-110, 2007.
[4] Y.R. Kondareddy, and P. Agrawal, “Synchronized MAC Protocol For Multi-hop Cognitive Radio Networks,” in Proc. of IEEE International
Conference on Communications, pp. 3198– 3202, 2008.
[5] L. Long, and E. Hossain, “A MAC Protocol for Opportunistic Spectrum Access in Cognitive Radio Networks,” in Proc. IEEE of Wireless
Communications & Networking Conference, pp. 1426– 1430, Las
Vegas, March 2008.
[6] Juncheng Jia and Qian Zhang, “Hardware-constrained Multi-Channel Cognitive MAC” in Proc. IEEE Global Communication Conference, pp. 4653– 4658, 2007.
[7] Hang Su and Xi Zhang, “Channel-Hopping Based Single Transceiver MAC for Cognitive Radio Networks”, in Proc. IEEE Communication
and Information Systems Security, pp. 197– 202, 2008.
[8] D. Cabric, A. Tkachenko, and R. W. Brodersen, “Experimental study of spectrum sensing based on energy detection and network cooperation,” in Proc. of ACM Int. Workshop on Technology and Policy for Accessing
Spectrum (TAPAS), Article No. 12, Aug. 2006.
[9] S. Haykin, “Cognitive Radio: Brain–Empowered Wireless Communications,” in IEEE Journal on Selected Areas in
Communications, vol. 23, no. 2, pp. 201–220, Feb. 2005.
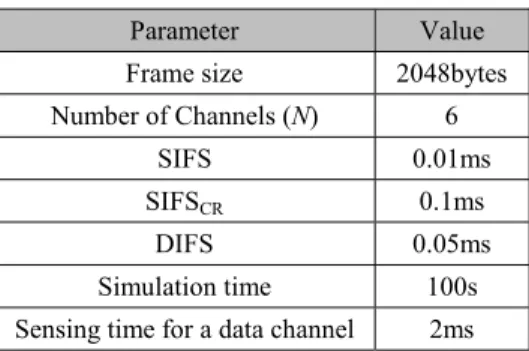
Table 1. Parameter settings of simulation
Parameter Value
Frame size 2048bytes Number of Channels (N) 6
SIFS 0.01ms
SIFSCR 0.1ms
DIFS 0.05ms Simulation time 100s
Sensing time for a data channel 2ms
Figure 5. CRN throughput vs. the number of CU pairs, upon PU utilizing 40% bandwidth
Figure 6. PU throughput vs. the number of CR pairs, upon PUs utilizing 40% bandwidth
Figure 7. The throughput of a CRN vs. PUs’ traffic load, upon 15 CR pairs