A Novel Low-Complexity Near-ML Multiuser Detector for DS-CDMA and MC-
CDMA Systems
Yi-Lin Li
Yumin
Lee
Graduate Institute of Comm. Eng. And Dept. of Electrical Eng., National Taiwan University
Taipei 10617, Taiwan
TEL +886-2-2362658 F A X +886-2-23683824 E-mail: yuminlee@cc.ee.ntu.edu.tw Absrraa-In this paper, we propose a novel lowsomplexity
multi-user detection algorithm based on tree search for a unified signal model that applies to both direct sequence code-division mdtiple access (DSCDMA) and multi-carrier CDMA (MC- CDMA) systems. Simulstion results show that the proposed algorithm outperforms most previously proposed multi-user detection schemes, and can achieve aeardptimal (maximum likelihood) performance with very low complexity.
I.
IWRODUCTION
Recently, direct sequence code division multiple access (DS-CDMA) for wireless communications has been given very much attention. It is well known that the performance of conventional (single-user) DS-CDMA detectors is severely limited by multiple access interference (MAI). One way to combat MA1 is by multi-user detection (MUD) [I]. As shown in [I], the optimal (maximum likelihood) MUD achieves the lowest possible symbol error probability, but is too complex to be practical. Many sub-optimal multi-user detectors have therefore been proposed in the literature [1,3,4,5].
As the wireless users demand higher data rates, conventional DS-CDMA system begins to face many difficulties caused by delay-spread multipath propagation. h e promising solution for these difiiculties is multi-canier CDMA (MC-CDMA). MC-CDMA combines the advantages of multi-camier modulation and CDMA to mitigate effects of multipath propagation and provide multiple access capabilities at the same time. Instead of path diversity, MC- CDMA makes use of the inherent frequency diversity in a frequency-selective channel, and is thus less sensitive to the effects of multipath propagation [7]. However, just as in DS- CDMA, MC-CDMA also suffers from MAI, and may require MUD in the receiver in order to be useful.
In this paper, we first establish a unified signal model for DS-CDMA and MC-CDMA. We next propose a novel low- complexity MUD based on tree search for the general signal model. Since both DS-CDMA and MC-CDMA can be accommodated using the general signal model, the proposed low-complexity MUD can be used for both DS-CDMA an MC-CDMA. Simulation results show that the proposed
scheme outperforms most previously proposed sub-optimal MUD, and can achieve near-optimal (maximum likelihood) performance.
11. GENF,RALDISCRETE-TMhIE SIGNALMODEL OFCDMA AND ML DETECTOR STRUCTURE
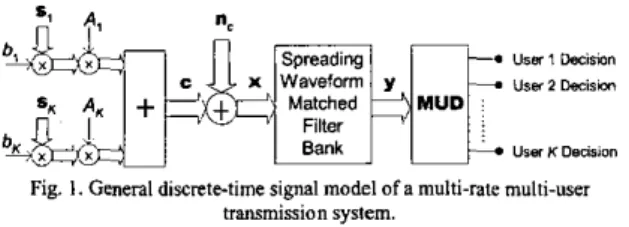
Consider the discrete-time baseband signal model of a multi-rate multi-user transmission system shown in Fig. 1, in which a total of
K
active users transmit one information symbol simultaneously. The received signal is modeled as an N x 1 vector x, where N i s the spreading factor, given by= S A b + n ,
where si, is the signature vector of the i-th user, A,, and b, are, respectively, the channel gain and information symbol of i-th user, and n, is a zero mean, circularly symmetric white Gaussian noise vector with autocorrelation matrix given by E[n,n/]= NoI. In (I), S, A, and b are N x K ,
K
x K , and KXlmatrices whose definitions are clear from the equation. It can be shown that the maximum likelihood (ML) receiver for the system in Fig. 1 consists of a bank of K filters, each being matched to one active users’ signature vector weighted by the corresponding channel gain, followed by some decision logic (denoted as multi-user detector [MUD] in Fig. 1) for detecting the transmitted symbols of all active users [I]. The output of the matched filter bank (MFB) can be expressed in matrix-vector form as
where
Fig. I. General dimete-time signal model of a multi-rate multi-user tlmmisbion system.
where "H" denotes Hermitian transposition, R=(SA)H(SA), and n=(SA)%, is a zero-mean circularly symmetric complex Gaussian noise vector with covariance matrix NOR. The output of MUD in the ML receiver is equal to
b = argmin[(y
-
Rb)"R-'(y-
Rb)] (3)in which the minimization is over all
M K
possible choices of b, where M is the cardinality of the signal constellation'. Assuming that R is positive-definite, there exists a unique KxK lower triangular matrix L with positive diagonal elements such thatR = L ~ L , (4)
thus
b
= argmin)l(L-Hy-
Lbf = a r g y l [ ( r - Lbf ( 5 ) where r = L-Hy is the whitened received signal vector. The ML receiver structure obtained according to (5) is shown in Fig. 2.Since L is lower triangular, the minimization in ( 5 ) can be performed using a perfect
M-ary
tree shown in Fig. 3. Specifically, consider a particular (k-1)-th parent node with associated candidate subsequence b,,,, =(i,
,&,
..
.,ik.,)
and node metric DPoreL. The parent node has Mchildren at the k-th level corresponding to each one of the M signal constellation points. The associated node metric of the child node corresponding to the signal constellation point
ik
is given byD&,d =
D
,
,
,
+Jz*-
L A q ,
(6)
user 1 oeusionUser 2 Decision
MFB
Fig. 2. The MLreceiversrructure.
I We assume that every user has the same signal constellation.
in
which l, is the (k, n)-th entry of L. In addition, the candidate subsequence associated with this child node is given byb*,d = ( b p y m t d (8)
The algorithm is initialized by setting the metric and candidate subsequence associated with the root (0-th level) node to 0 and the null sequence, respectively. The above procedure is performed from the root to the leaf (K-th level) nodes of the tree, resulting in a total of bf candidate (sub)sequences and associated metrics
.
The output of the ML MUD is the candidate (sub)sequence at the K-th level with the smallest associated metric. In general, the number of additions and multiplications of the tree-search algorithm is proportional toe.
The model described in (1) is a well-known signal model for the conventional synchronous DS-CDMA operating in a flat-fading environment [I], It can be shown that (1) can also be used to model MC-CDMA signals, which combines frequency-division multiplexing (OFDM) and CDMA techniques to combat severe multipath fading effects and provide multiple access capability at the same time
[7].
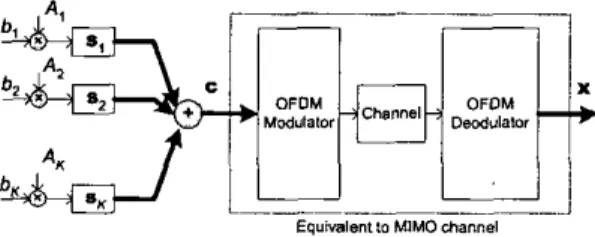
The baseband-equivalent signal model of down-link (DL) synchronous MC-CDMA system is shown in Fig. 4. The OFDM transceiver in MC-CDMA can be viewed as an equivalent multi-input multi-output (MIMO) channel characterized by the channel matrix H. The received signal xis thus given by x = H c + n ,
= H(s,,s,
,...,
s,)Ab+
nc (9)= S' A b
+
nc,where E = SAb
.
It can be seen that (9) can be obtained by replacing S with S' in ( I ) .On
the other hand, the baseband equivalent signal model of up-link(UL)
quasi-synchronous MC-CDMA system is shown in Fig. 5, where "quasi- synchronous" means that the MC-CDMA signals from all active users are roughly alignedin
time. Viewing the OFDM,_,
%I r m n d ,ea, mdesl e d l0vd c m 1-1
modulators as equivalent MlMO channels characterized by channel matrices
A,,
A>,
._.,
Hx,
we can express the received signal x aswhere c, = si x (b, x A . ) . It is then clear that (IO) can also be obtained from
(I).
Since DS-CDMA, DL MC-CDMA, andUL
quasi-synchronous MC-CDMA signals all fit the general model in (I), all MUD techniques discussed in this paper apply equally well to each one of them.111. PRLWHITENED TREE-PRLNMG FOR COMPLEXrrY REDUCTION
Although the performance of the ML detector is very appealing [I], it is too complex to be practical. The prohibitively high complexity arises From keeping track of all possible paths from the root to the
&f
leaf nodes. Therefore, one method for complexity reduction is by tree-pruning. Some simple breadth-first methods have previously been proposed. In [ 6 ] , for example, conventional tree-pruning algorithms such as the M-, T-, and MT-algorithms arc applied to synchronous CDMA. In the M-algorithm, for example, only B survivors are retained at each level. In this paper, we propose an improved tree-pruning algorithm, referred to as pre-whitened tree-pruning (PW-TP), that is efficient and flex-Equivalent lo MlMO channel
Fig. 4. Baseband equivalent signal model for DL MC-CDMA system
b w .
U
ModulslcrK
Fig. 5. Bawband equivalsnl signal modcl for UL quasi-synchronous MC- CDMA ~ y ~ t c m .
ible especially for large constellation
size.
PW-TP is a new M-algorithm with a different .number of survivors for each level and incorporates set partitioning [SI for further complexity reduction. Simulation results and a rough complexity analysis show that the inherent properties of L allow the proposed algorithm to efficiently reduce computational complexity while causing only. very little performance degradation.The proposed algorithm is
as
follows. Assuming that after pruning only Mk.l nodes are retained in the (k-1)-th level, and consider a particular retained node with node metric D,,,and associated candidate subsequence
bpm, = ( i , , i 2 , . . , , i k - l ) . The signal constellation is first partitioned into Nk disjoint cosets Y d l ) , Yd2),
...,
YANk)), which can be obtained using well-hown set partitioning techniques [8] commonly used in trellis-coded modulation. We then construct Nk children for this node, each child corresponding to a signal constellation coset as shown in Fig.6 . For the child node corresponding to the j-th coset, the associated node metric is given by
:
where zkis given in (7). Furthermore, the associated candidate subsequence for this child node is as given in (S), but
Lk
is redefined asThe above procedure is repeated for every retained node at the (k-1)-th level, therefore a total of NkMk.l children at the k- th level arc obtained. The node metrics of these children arc next sorted in ascending order, and only the first Mh nodes arc retained. The entire procedure is then repeated using these
M k retained nodes as parents until the height of the tree reaches
K.
The candidate (sub)sequence associated with the leaf node with the smallest node metric is the output of the proposed multi-user detector. Note that the root node is always retained and is assigned the zero metric and null candidate subsequence.The proposed algorithm can be justified as follows. First, for the tree shown in Fig. 3, a node at the (k-1)-th level of the tree has M children, therefore a total of MMk., metrics, where
Mk.1 is the number of nodes at the (k-1)-th level, need to be computed and sorted to determine the survivors o f the k-th level. This number can he lowered by discarding some of the
M children of each parent node based on tentative decisions. In the proposed algorithm, the signal constellation is partitioned into cosets, and tentative decisions are formed by
slicing the decision variable zk onto each coset appropriately weighted by lu as in
(12).
The number of children for each parent is therefore reduced to the number of cosets. Since retaining the path corresponding to the correct transmitted sequence after pruning is a necessary condition for correct detection in any tree-pruning algorithm, it is important that the correct path should not he eliminated prematurely when some child nodes are discarded. Intuitively, the probability of erroneously eliminating the correct path decreases with increasing minimum distance within each weighted coset, which in turn increases with the number of cosets and 1,. Thereforeas
1, increases the number of cosets can he reduced without increasing the probability of prematurely eliminating the correct path. It has been observed that luincreases with k
on
average, therefore it is sensible to use a different number of cosets, Nk, at every level, and make Nk a decreasing function of k.On the other hand, the complexity of the kee search algorithm can he significantly reduced by limiting the number of survivors at each level as in the conventional M- algorithm I6]. AS mentioned earlier, it is important that the correct path should not be eliminated prematurely due to pruning. The probability of losing the currect path at level k depends on the number of retained survivors and the squared minimum distance between the candidate subsequences at the k-th level. defined as
(13)
^ ^
where
6,
=(6,,,6,2,...,6,,k)
and6 ,
=(b21,b22,...,62,k) arc two different members of the3
possible candidate subsequences at the k-th level. Obviously, as d L ( k ) increases, more survivors can he discarded without increasing the probability of losing the correct path. Since in general 2-(k) is different for every k, it is also sensible to retain different numbers of survivors at different levels as proposed in this paper, rather than retaining a fixed number of survivors at all levels as in the conventional M-algorithm. Furthermore, it can he shown thatd&(k) B min{di,(k- I),/*'d&)
(14)
Fig. 6. Determinnim of the children far a particular parent node. M=4 N*=2.
where d- is the signal constellation minimum distance. Since
lu
increases with k as mentioned earlier, d L ( k ) also increases withk
in general. Hence, the number of retained survivors at the k-th level,Mk,
should decrease with k i n order to lower complexity. As will be shown later by simulation, such choice combined with a variable number of signal cosets indeed achieves near-optimal performance with significantly reduced complexity.IV. SLMULATION RESULTS
The performance of the proposed PW-Tp algorithm is evaluated by computer simulation for an LJL quasi- synchronous wireless MC-CDMA transmission system with 32 subcamers. All users in the system are assumed to have equal power and the signature vector of each user is a Walsh code with N=32 chips. The signal constellation for each user is 8-level phase-shift keying (BPSK), therefore
M
=8.
The wireless channel is modeled as a frequency selective fading channel cormpted by AWGN. The channel gains at the suhcarrier frequencies are assumed to be independent and identically distributed circularly symmetric complex Gaussian random variables with unity variance.In
addition to the PW-TP, the conventional M-algorithm as well as several conventional single- and multi-user detectors, including the single-user matched filter (MF) receiver[I],
linear decorrelating receiver [
1,4,5],
and zero-forcing decision-feedback detector (ZF-DF) (31, are also simulated to provide baselines for comparison. The MF receiver directly slices the outputs of MFB to make decisions. The linear decorrelating receiver multiplies the received signal vector y by R-' and slices the components of the resulting vector to obtain the symbol decisions. The zero-forcing decision- feedback detector (ZF-DF) was proposed in [ 3 J , and can be viewedas
the conventional M-algorithm with the number ofretained survivors B set to I . The proposed receiver uses combinations of four sets of
M I
and two sets of Nk given below:Variable number of survivors:
{Mkset 1)={16,16,16,16,16,16,16,16, 16,16,16,16,8,8,8,8,
8,8,8,8,4,4,4,4,2,2,2,2,1,1,I,l)
{Mkset2)={64,64.64.64,32,32,32,32,l6,16,l6,l6,8,8,E,E,
8.8.8.8.4.4.4.4.2.2.2.2.1.1.1.1
1
{Mk set 3)={64,64,64,64,64,64,32,32,32,32,32,32,
16,16,16,16,8,8,8,8,4,4,4,4,2,2,2,2,l,l,l,l){Mk
set4)=(8,8,8,8,8,8,8,8,8,8,8,8,4,4,4,4,4,4,4,4,2,2,2,2)
Variable number of cosets:
{Nh set I ) ={8,8,8,8,4,4,4,4,4,4,4,4,2,2,2,2,2,2,2,2,2,2,2,2,
2.2.2.2.2.2.2.2)
Note that {Mk set 4 ) and {Nk set 2 ) are defined only for
k-I.
..24 because they are used only for the cases in which K= 24. The simulation results are given in Figs. 7, 8, and 9. The bit error rate
@ER)
of the simulated receivers are in Fig. 7 as functions of K at EdNpIZdFi, where Eb is the energy per bit and NO is variance of the AWGN on each subcarrier. Here{Mk
set I ) and ( N I set I } are used for the proposed receiver. As can be seen from Fig. 7 , both the conventional M-algorithm and the proposed receiver significantly outperform the conventional single- and multi- user detectors. TheBER
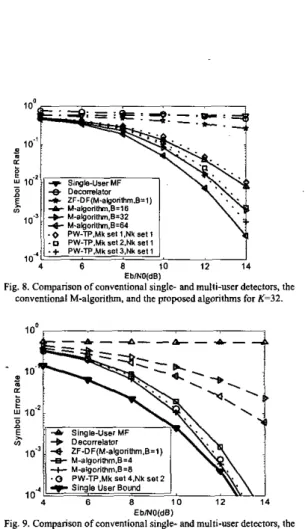
of the proposed receiver is roughly the same as the conventional M-algorithm with B = 16. However, the computational complexity of the proposed receiver with ( M i set I } and {Nk set 1 } is obviously lower when K >4.Fig. 8 compares the performance of the PW-TP and conventional M-algorithm for fully loaded system, i.e. K=N=32. Performance of the conventional single- and multi- user detectors are also plotted for comparison. It can be seen that PW-TP with (Mh set I ) and {Nk set 1 ) achieves roughly the same performance as the conventional M-algorithm with
B = 16. However, a rough complexity analysis shows that PW-TP requires 70% fewer arithmetic operations (required for metric computation and sorting) than the conventional M- algorithm. Similarly, PW-TP with
{Mk
set 2) and {Nb set I } achieves roughly the same performanceas
the M-algorithm with B = 32, but requires 62% fewer operations. Finally, the performance of PW-TP with{Mh
set 3 ) and (Nk set I } and the M-algorithm with B = 64 are comparable, but PW-TP only requires 15% of the computations in the M-algorithm. It can also be observed from this figure that PW-TP does not exhibitBER
floor, which indicates that PW-TP has good asymptotic multiuser efficiency ( M E ) [I]. Finally, it is interesting to note that{Mi
set I ) ,{Mh
set 2 ) , and{Mk
set 3 ) differ only in k 1 . . . 1 6 . Since, when combined with { N k setI } , {Mi set 2 ) and {idb set 3) significantly outperform
( M k
set I}, one can conclude that the performance of the proposed
Fig. 7. Comparison of conventional single- and multi-~ser detectors, the
conventional M-algorithm, and ths proposed algorithm$ for EdNo=12dB.
EbINOLB)
Fig. 8. Comparison ofconventional single- and multi-user detectors, the
~onventionsl M-algorithm, and the proposed algorithms far K=32.
EbMO(dB1
Fig. 9. Conpansan of Conventional single- and multi-wCr detectors, the eonvFntiona1 M-algorithm, and the proposed algorithms for K=24.
algorithm is more sensitive to the number of survivors retained in the first few levels of the tree. This observation corroborates the claim of &,,(k) being an increasing function of k made earlier in this paper.
Fig.
9 shows theBER
of
the various receivers as functions of EdNo forK
= 24. Here the proposed PW-TP algorithm uses{MI
set 4 ) and ( N h set 2 ) . It can be seen that it performs roughly the same as the M-algorithm with B = 8. However, a complexity reduction of roughly 60% is achieved. Furthermore, the proposed receiver significantly outperforms the M-algorithm with B = 4, which has comparable yet slightly higher complexity. It should also be noted that PW- TP almost achieves the single-user bound at highEdNo
even though ( N b set 2) uses smaller number of cosets compared to { N k set I}. In fact, it can be shown that the mean 'square value of Ill is a decreasing function of K , thus fewer cosets are requiredfor
smaller K . Therefore as K decreases, the complexity of PW-TP can he reduced even further by reducingNk.
v.
CONCLUSIONS REFERENCESMC-CDMA is
an
amactive scheme for high data rate [I] S . Verdu, MullilrrerDefrcrion. Cambndgeunivenitypress. 1998.[21 I. M. Wozeneraff. 1. M. lacobs. Principles of Communicolion wireless transmission because it mitigates the effects of
multipath propagation and provides multiple access (31 A. D U ~ I - H E I I ~ ~ , J. H O I " ~ , zoran zvonar, "Multiuser Detection for ,965,
capabilities at the same time. CDMA Systms,"lEEE Personal Communicatiom, A p d 1995.
MC-CDMA also s u ~ m s from MAI and may require MUD in I41 Shimon Moshavi, "Multi-User Detection for DS-CDMA
Communications:' IEEE Communicotiom Magazine. Oct. 1996.
signal model for DS-CDMA and MC-CDMA. We next simulation Compacisan of Multiuer Receivers for Cellular CDMA,"
propose a novel low-complexity MUD scheme based on tree IEEE Trans. On Vehicular Technology, Vol. 49. No.4, July Z W O search for the unified signal model, Since the unified signal Lei Seareh Detection Schemes wei. Lars K. R a m m " Richad WYnVm. 'wear @ti" Tree-
for Bit-Synchronous Multiuser CDMA
models applies to both DS-CDMA and MC-CDMA, the systems over eunsian and
proposed scheme is equally applicable to both. Simulation IEEE T~ORS. on communicotiom, vol. 45. N ~ . 6, lune 1997.
results that the proposed algorithm outperforms most [71 Shinsultc Hara, Ramjee b a d , ''Overview of Multicmier CDMA"
previously proposed sub-optimal MUD, and can in fact IEEE Cammunicntion Magazine,
[SI G. Ungcrboeck. "Chamel e d n g with MultilcveVPha~e Signals." IEEE
achieve near-optimal (maximum likelihood) performam
rranr
fnform. mea,,,, with very low computational complexity.However, as in DS-CDMA,
order to be useful. In this paper, we first establish a unified [51 R, M, N. S. Coml.Mcndola, and B. D. wwmc,, ..A
[61
~ ~ ~ ~ ~ i g h . ~ ~ d i ~ ~ channelL-
1997. r.28, pp.55.67, la. 1982.