Cheng-Min Lin1,*, Chyi-Ren Dow2, Khong-Ho Chen2 and Tsen-Fen Lai2
1 Department of Computer and Communication Engineering, Nan Kai Institute of Technology, Nantou 542, Taiwan, ROC
lcm@nkc.edu.tw
2 Department of Information Engineering and Computer Science, Feng Chia University, Taichung 407, Taiwan, ROC
{crdow@fcu.edu.tw, cyne@pluto.iecs.fcu.edu.tw, M9431035@fcu.edu.tw}
Received 13 January 2007; Revised 5 March 2007; Accepted 26 March 2007
Abstract. Although Internet use is increasing, older adults have still difficulties to use computers. This study presents three assistant agent models, a local model, mobile model, and pocket model, to assist older adults in using the Internet easily. This study analyzes scenarios for the three models, and compares their total system delay time when used by older adults. The goal is to identify the best model of an assistant agent to decrease difficulty when accessing information on the Internet. In terms of performance error, the local model is more suitable than the other models for use by older adults.However, in terms of mobility, the mobile and pocket models are more suitable than the local model. Additionally, this study presents three mathematical models of agents and assesses their respective advantages and disadvantages.
Keywords: older adults, models, portable, mobile agent, preference data, personal web.
1 Introduction
The Internet offers the possibility for individuals to access information and interact with each other via computer and telecommunication equipments. However, despite the growing proportion of senior citizens, the population of elderly Internet users is relatively very small, perhaps because aging is generally associated with decreased functional ability [1]. Some areas of reduced functional ability significantly affect the ability of older adults to utilize the Internet [2][3].
Older adults typically have problems operating computers, searching the Internet, and designing of web sites [1][4][5][6]. Although numerous web assistant agents have been developed, these problems continue to exist. In solving these problems, it is important to first generate personal information, including bookmark, site histories, identification (ID) and password logs, cookies and other personal information. This personal information can assist older adults in accessing the Internet easily and eliminate the need to memorize excessive amount of information. The second task is to simplify web page layout to assist older adults in reading web page easily. When older adults use computers at home, popular browsers can meet their needs. However, older adults face a significant problem. In today’s world of broadband network connectivity, computer users are more mobile than ever. Users typically use computers at home, school and work. A problem encountered by mobile users is that they lack a static environment as they from place to place. That is, computers in different environments are typically configured differently from home computers. Thus, when a user moves between computers, data, which is specific to web browsers, does not move with a user. In such situations, older adults must perform the following tasks. First, they need to reset text size. Second, they need to search again for their favorite websites. Third, they lose their record of web site already accessed. Fourth, they maybe forget their IDs and passwords for particular web sites. To assist older adults and avoid these problems, this study presents an agent system that assists older adults in overcoming these problems. This agent is called a Preference Agent. The Preference Agent has two principal functions—personal information portability and web page simplification. The agent constructs a personal environment for accessing the Internet.
There are many studies investigating agent system models. This study analyzes three models—the local agent model, mobile agent model, and pocket agent model. Based on the characteristics of older adults, this study examines the different effects when old adults use these three agent models. This study then analyzed how older adult behaviors influence the efficiency of operating, and examines the efficiency when using these three models
* Correspondence author
mathematically. The primary purpose is to identify the advantages and disadvantages associated with each agent model. The principal goal is to increase the efficiency of browsing through a network.
The remainder of this paper is organized as follows. Section 2 describes related work in agent technologies and limitations of older adults. Next, three web agents and the preference agent are introduced in Sections 3 and 4, respectively. Then, the advantages and disadvantages of three models are discussed in Section 5. Finally, conclusions are given in Section 6.
2 Related Work
Agents are utilized to assist older adults when browsing web sites in terms of agency, autonomy, proactivity, reactivity and mobility. Agent has a fair degree of control over its actions and does not always need to wait for commands. Agent can make decisions and function independently. Agents typically filter information, some of which is filtered autonomously, and only presents users with information considered of interest. In the past several years, various agent models have been proposed. Although many studies have investigated software agents, little is known about agent models for assisting older adults. Hence, based on the use of proposed agents, this study divides agent models into three categories—local agent model, mobile agent model and pocket agent model—for client-server, mobile computing, and ubiquitous computing paradigms, respectively.
First, the local agent model uses an agent installed on a client personal computer and provides services to users, ex., [7][8]. Decreased mobility, vision, and working memory affect older adults’ interactions with computers, and reduce the accuracy with which older adults position a cursor on a computer screen [3] [4][5][6] [9][10][11] [12]. Consequently, text size, word links, redundant navigational cues, and terminology affect the performance of older adults surfing the Internet [11]. Junji [12] and Arnott [13] proposed an assistive device to improve performance for older adults accessing the Internet. Older adults can install web assistant agents on their own PCs based on need. These agents provide a personal web service for older adults based on personal requirements.
Next, the mobile agent model scheme uses an agent server, which is a combination of a web server and mobile agent server [11] [14][15][16][17][18][19][20][21]. A user only needs to submit their service request to the server. The agent server then identifies and launches an agent to execute the requested services based on user identity. The principal characteristic of a mobile agent, as opposed to a local agent, is its mobility. Mobile agents can move through a network of sites and search for, filter, and process information needed to accomplish tasks. Older adults can thus obtain service easily when changing computers.
Finally, the pocket service operates by encapsulating the services on the pocket storage device, for example [22]. Such a service is also called a pocket agent model. Advances in mobile telecommunications and device miniaturization facilitate providing standard and novel location- and context-dependent Internet services to mobile clients. Bellavista et al. [23] developed a ubiquitous provisioning of Internet services to portable devices. Additionally, Rajan and Ma developed a novel scheme to achieve the objective of ubiquitous sessions across mobile cellular and IP domains [24]. Most pocket services make personal preference data portable. Personal preference data is included in Microsoft Internet Explorer settings, favorites, cookies and history, in addition to files, folders and icons, which are indispensable user tools [25][26]. This data allows user to work on different PCs in different locations.
These factors include the interconnection network and the characteristics of older adults [27][28][29]. The following list several essential points that affect computer operation by older adults.
Activity. Reduced motor abilities have the most severe effect on the ability of older users to interact with input devices. Older adults take longer than their younger counterparts when performing the same movement— the movements of older adults are relatively more variable, less smooth, and less coordinated. The loss of fine motor skills makes it difficult for older user to position a cursor on a computer screens. Physical errors when manipulation input devices are called performance errors. Examples of performance errors are missing targeted keys, striking adjacent keys in addition to the targeted key, pressing keys for too long, thereby producing repeat letters, moving the mouse while double clicking, and dropping the mouse button while dragging.
Vision. The aging eye has reduced ability to focus on close objects due to a reduction in lens elasticity. Additionally, a decline in visual acuity affects the ability to see objects clearly. Consequently, reading text on a computer monitor is a difficult task. Not only is it difficult for such users to read characters that are small, the standard white web page background can prevent such users from seeing page contents even when text size is optimal.
Working memory. The memory of older adults is typically degenerating. Skill acquisition literature suggests that older people have more difficulty than their younger counterparts in acquiring new skills, and older adults attain relatively lower levels of performance. Computer tasks involving cognitive skills may prove problematic for older adults. Computer tasks place high demands on working memory. Reduced working memory places older adults at a disadvantage when performing interactive computer tasks. Working memory entails holding and
manipulating information temporarily while engaging in various cognitive tasks. Cognitive tasks include manipulating complex browser settings.
3 System Model
This section describes the three models proposed. This study considers the factors that affect total system delay time for older adults.
3.1 Overview
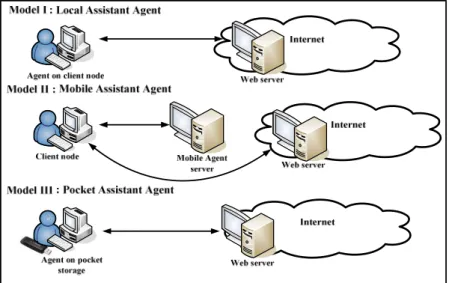
An agent-based system is distributed. Represented by the graph G = (V, C), the agent-based system can be considered as a set V of fail-stop nodes, interconnected via a communication network consisting of a set C of bidirectional communication channels. No shared memory or common clock exists for these nodes; communication between the nodes is only by passing messages. We assume that the messages in channels are FIFO. Additionally, we assume the channels are reliable, and that a node has one or more processes or agents. Agent-based systems for assisting older adults can be classified into three model types (Fig. 1)—local, mobile, and pocket models. An older adult uses a client node, denoted as ci, where 0≤ i ≤ m-1, to access information from
a remote server, denoted by sj, where 0≤ j ≤ n-1, through the Internet. An assistant agent is automatically
activated to assist the user. Specially, the number of servers is not equal to the number of clients; that is, the relationship between clients and servers is many-to-many.
Fig. 1. Overview of assistant web agent approaches
3.2 Model of Assistant Agents
In the local assistant agent scheme, an agent is utilized to assist older adults. The agent is denoted by Al,i where
0≤ i ≤ n. The agent is a fixative agent installed in a client’s node. We assume that the number of agents equals the number of clients; that is, a one-to-one relationship exists between the number of clients and agents. Notably, Al,i
is only executed in a specified client node, ci.
The mobile assistant agent scheme uses an agent server si, which is a combination of a web server and
mobile agent server. This agent is denoted as Am,j, where 0≤ j ≤ n-1. When an older adult needs connect to si and
input her ID and password, and then si dispatches Am,j to cj and activates the application program. Thus, Am,j
enables the application on cj and transfers the personal information of an older adult to cj. An older adult can
obtain service and personal information from si. Then the older adults will download a personal browser
configuration allowing the user to access their favorite web server easily. When the configuration of the older adult be modified, Am,j will upload their information to si automatically—all personal information is stored in si.
The pocket assistant agent scheme utilizes a pocket storage device. The agent program and personal information are both stored in the pocket storage device [25][26]. When an older user wants to start the assistant agent denoted as Ap,i, they just plug the pocket storage device into the computer, ci. The agent then assists the
user actively. An older user will not need to be authenticated and she also achieves mobile functionality.
The service type and information is essential for older adults when accessing Internet information. The web assistant agent, in local, mobile, and pocket assistant agents, provides such information anytime and anywhere. Particularly, these software agents provide information, including Bookmarks, History log, Text size, Cookies, and Password. The Bookmark information is utilized to allow an older user to connect to her favorite website easily. Which website she accesses is stored in the History log. Text size records the optimal text size for reading. Additionally, some web services need Cookies and Passwords.
3.3 Model of System Delay
This subsection introduces the proposed system delay model. The model can be divided into four parts, working model, channel model, transmitting node model and a receiving node model, based on the model proposed by Knudsen and Maden in 1999 [30]. Their model, which focused on a single computer, included a software driver, channel, and hardware driver. Additionally, their communication delay model introduced a Protocol Control Information (PCI) and Universal Serial Bus (USB). This study extends their model to the Internet. Hence, a channel in the proposed model may be a local bus in a computer or a connection in a network between two nodes—a transmitting node and receiving node. Notably, a node is a driver when the delay model works on a single computer.
The working model is utilized to indicate the exception of communication delay. This study defines this model to represent the interactivity between an adult user and a computer. Additionally, the working model in a different model of web agents can be represented to different things. The local and mobile agent models consist of time when identification is checked and time when an address is typed into a web site. The pocket model is primarily the time a USB device is plugged in is utilized to identify a user. The other three models that are incorporated into the communication delay model are same as those proposed by Peter and Jan. Hence, these models are described in detail elsewhere.
We assume that the proposed system can be executed in parallel in a pipeline fashion. In other words, the four parts in the proposed models can be executed individually. The total system delay consists of a delay time of the working model, twt, and delay time of communication, tct; Total system delay is denoted by tst. Total system
delay is calculated as
ct wt
st
t
t
t
=
+
, (1)where tct is proposed by Knudsen and Maden [13]
(
)
+ × = d rd cd td ct n t t t t max , , 1 2 , (2)where ttd, tcd, and trd are the time of transmitting, channel, and receiving, respectively, and nd is the number of
data words. Although Knudsen and Maden proposed three equations, one each for ttd, tcd, and trd, this study
summarizes these equations into the following general form.
(
xs xc x)
xxd c c n f
t = + /
,
(3)where x is t, c, or r, txd is ttd, tcd, or trd, and cxs is the total number of synchronization cycles.It is either ctx, ccs, or
crs, where cts, ccs, and crs are the total number of transmissions, channels, and receiving synchronization cycles,
respectively. Additionally, cxc is the number of words, including those transmitted, channel, and received.
The other element affecting system total delay is the work model of older adults (twd). According to [7][12],
this study can identify those with physical disabilities who have difficulty accurately manipulating the computer input device. Consequently, this study has designed three assistant agents (Figs. 2, 3, and. 4). Physical errors generated while manipulating input devices are referred to as performance error (PE). Several factors affect the work model for older adults. This study calculates PE as
(
)
∑
∈ × × + = } , , , { 1 t p w m y y y y wt PE T C t , (4)where y is m, w, p or t , Ty is the average time of operations, and Cy is the counter of operations when users call
the assistant agent. Hence, Tm, Tw, Tp and Tt are the average time of operating the mouse, working memory,
plug-in, and typing, respectively; Cm,Cw, Cp, andCt are the counter of operations when operating the mouse, working
3.4 Function of assistant agent
We infer that it is beneficial to increase accessibility for older users by reducing the number of steps required to operate a computer and providing portable personal information. The following are scenarios in the proposed system; total system delay time for the three models is compared.
3.4.1 Local assistant agent model
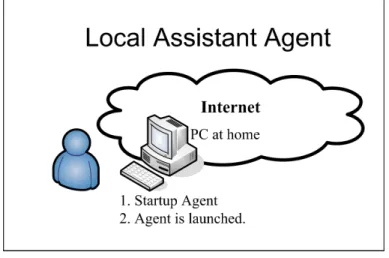
A local agent model is a one-to-one model. The agent is installed on a personal computer operated by an older adult who does not gain assistance from a network; all user information is stored on the personal computer.Fig. 2 presents the steps in the local model agent’s scenario. This study considers two cases according to whether an installation of agent is required. The two cases are as follows.
Fig. 2. Local Agent scenario has two cases.
Case 1. An assistant agent is executed. The user must first click on an icon for the service located on the desktop. Hence, a unit of average time of mouse Tm is only included in this step. We assume installation of a local agent is
not required when the desktop computer has an agent service installed.
Case 2. When an adult user needs to use a different computer, she must reinstall the agent service. That requires working memory and positioning the cursor using the mouse.
With the number in above this study finds that
(
)
+ + + + = 2 ), 1 ( ) 1 ( 2 1 , 1 Case for PE T PE T Case for PE T t w w m m m m wt , (5)and total system delay time is
wt st t
t = . (6)
As the assistant is installed in a local client, this study ignores the communication delay time.
3.4.2 Mobile assistant agent model
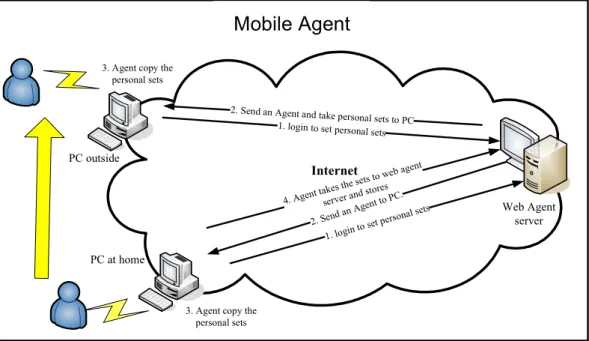
Mobile agents are processes dispatched from a source computer to accomplish a particular task. After its submission, the mobile agent proceeds autonomously, independent of the sending client. Fig. 3 illustrates the steps in the scenario with the mobile agent model. The mobile assistant agent model has four steps. The timing of the four steps is present as follows.
Step 1. Connect to the web agent server. An older user must connect to the web agent server before accessing the Internet. This operation involves typing and working memory.
Step 2. Before using the model, an authentication step is necessary. An older user must input their ID and password. When authentication is correct, the agent server will dispatch the personal assistant agent to the client site. Hence, this operation also requires typing and working memory.
Step 3. Select the service. The assistant agent assists older users in selecting a service, and uploading or downloading personal information. These operations require the user to position the cursors using a mouse.
Internet Web Agent server PC at home PC outside 2. Send a n Agent t o PC.
2. Send an Agent and take personal sets to PC 1. login to set personal sets
1. login t
o set pers
onal sets
3. Agent copy the personal sets 4. Agent ta kes the se ts to web agent server and stores
3. Agent copy the personal sets
Mobile Agent
Fig. 3. Mobile Agent scenario
Step 4. Upload or download personal information. When an older user wants to upload their personal information, the assistant agent collects user information and stores this information in an agent server database. When an older user wants to download information, the assistant agent will restore browser environment from the database.
With the number in above this study finds that
(
m)
w(
w)
t(
t)
m
wt T PE T PE T PE
t =4 1+ +3 1+ +2 1+ (7)
Total system delay time is calculated as
(
m)
w(
w)
t(
t)
m ct
st t T PE T PE T PE
t = +4 1+ +3 1+ +2 1+ (8)
The communication between the assistant agent and node is via the Internet. The connection rate depends on the network communication model. Hence, this study does not discuss the network communication delay.
3.4.3 Pocket assistant agent model
The pocket agent model operates by encapsulating the agent in a pocket storage device. When an older user plugs the pocket storage device into a PC, the agent can act autonomously. The agent provides services based on user needs. Fig. 4 illustrates the scenario with a pocket agent model.
Internet
PC at home PC outside 3. Agent helps user to configure his sets on PC
2. Agent autoruns
1. detect portable storage device 2. Agent autoruns
3. Agent copies his sets to storage device
Pocketable Assistant Agent
1. detect portable storage device
Mobility
Step 1. Plug the pocket storage device into computer. The user plugs the pocket storage device into the computer before accessing information on the Internet.
Step 2. The PC detects the device and starts up automatically the assistant agent.
Step 3. The agent then ascertains whether the computer is the user’s. If it is not the user’s computer, the agent will restore the user’s information automatically.
With the number in above, this study found that
(
p)
p
wt T PE
t = 1+ (9)
Total system delay time is calculated as
(
p)
p ct
st t T PE
t = + 1+ (10)
Communication between the assistant agent and node is via USB protocol. According to Knudsen and Maden, the max channel delay time of various communication models is 2.2s. Consequently, we assume the USB protocol delay time is 2.2s.
4 Preference Agent
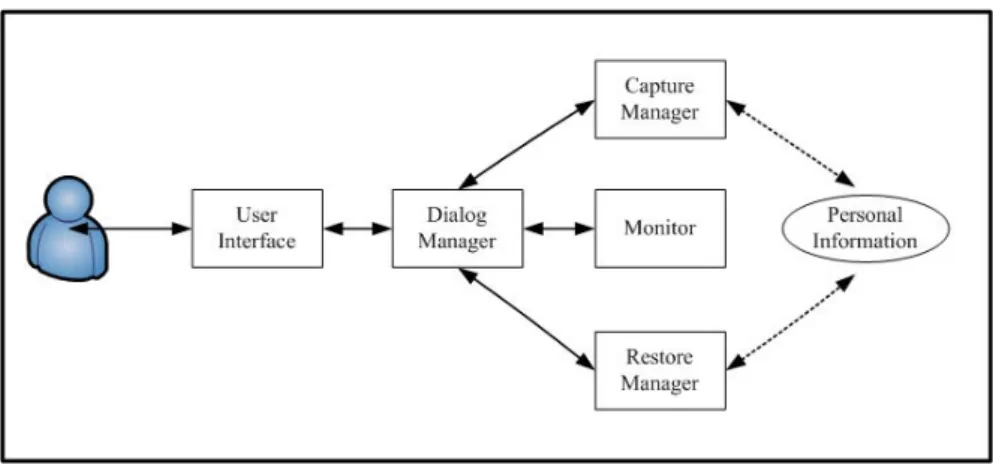
Fig. 5 illustrates the architecture of the preference agent and its modules.
User Interface. This interface interacts with older adults and assists them in operating the assistant agent. The user interface also helps users choose which service they want in a step-by-step manner. This module is designed such that it is easily understood and operated by older adults. There is the bootstrap that assists older users in handling the service step by step.
Dialogue Manager. This module handles logical interactions with users. The main task for this module is to collect messages from a user and the Monitor Agent. This module acknowledges other agents based on messages it receives.
Fig. 5. Architecture of preference agent
Capture Manager. This module responds to obtain user personal sets of Internet Explorer (IE) and then stores these sets in the database. The database may be in the local client, agent server, or a pocket storage device.
Restore Manager. The Restore Manager is responsible for helping users setup up individual browsers like those on their home PC. When the Restore Manager receives a command from the Dialogue Manager, it finds personal sets and download information from the database to the browser.
The personal information stored in a preference agent is presented as follows.
Text size. Due to reduced vision faculty of older adults, older adults cannot read web pages easily when the content of a web page uses text that is very small. Some web sites have considered this problem, and designed web page using bigger text. Increasing readability is important for people with reduced vision; however most of web sites do not meet the readability needs of older adults.
Authentication. Some web sites must authenticate personal ID to provide personal information or services. However, remembering IDs and passwords can prove difficult for older adults due to decreased working memory. Additionally, the typing performance of older adults is typically worse than that of relatively younger users. For instance, when a key adjacent to the intended key is unintentionally struck, the timing between striking the intended key and accidental key can be used to distinguish between separate key strokes. Consequently, reducing typing demands can increase user performance.
Web site ULR. URL influence is the same as that of authentication. Older adults cannot keep remember many URLs, and frequently forget where they found information during previous sessions. Helping users store their favorite web site ULRs can increase user interest in the Internet.
5 Discussion
This study determines which model achieves highest user performance and is most convenient for users. This study then investigates the advantages and disadvantages of these models.
5.1 Comparison of the models
Figs. 6, 7 and 8 present statistical performance graphs for the three models. Based on the statistical graphs, this study determines which model has the smallest delay time. We assume if an older user performs an action that takes 9 seconds, and the fail-step probability is 0.9. This study checks delay time for the three models, and determines which model takes least time to call the assistant agent, thereby minimizing the probability of a fail-step.
5.1.1 Probability of performance error
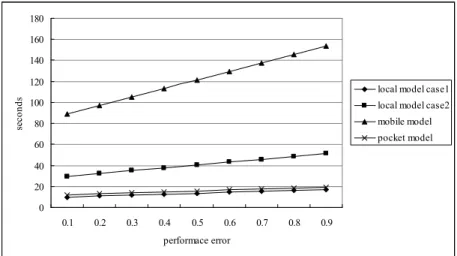
These numberswere calculated based on Eqs.(6), (8) and (10). Fig. 6 shows delay time statistical graph for the local, mobile, and pocket assistant agents. We assume every action in the three models takes 9 seconds. Different models take different amounts of time in different probability of PE (Fig. 5). The local model takes only 17.1 seconds in Case 1 and 51.3 seconds in Case 2. The mobile model needs 153.9 seconds for mobile model. The pocket model needs 19.3 seconds for both cases. It has the shortest delay time for the local model in Case 1. These results confirm that fail-steps, and users will require increased amounts of time to operate the agent.
0 20 40 60 80 100 120 140 160 180 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 performace error se c o n d
s local model case1
local model case2 mobile model pocket model
Fig. 6. The time of three models with difference performance error
5.1.2 Probability of move
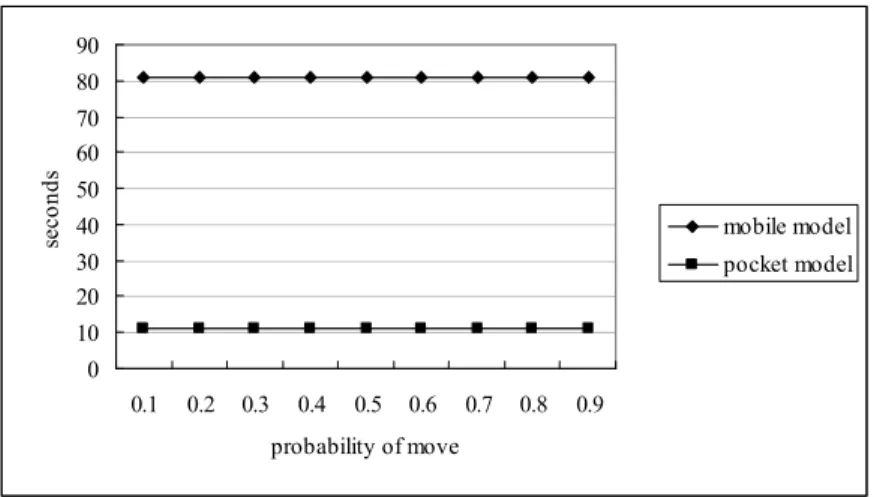
This study performed computations with the probability of a user moving, and the assumed PE does not occur. The time it takes to trigger an agent will be different when a user changes computer. When older users leave home and require assistance from a web agent, they must re-trigger the agent. According to Section 3.4, the local agent is not suited to users moving from home; hence, this study does not consider the local agent here. If probability of a move is high, the delay time of the mobile agent model is longer than that of the pocket agent model (Fig. 7). The shortest delay time is for the pocket model when the probability of mobility is highest. Consequently, we conclude that the proposed pocket model is fitted best for highly mobile users.
5.1.3 Probability of network congestion
Here, this study performs computations based on the probability of network congestion. The effects of network congestion on different models are compared. We assume performance error does not occur. Fig. 8 presents calculation results. The delay time of the mobile model increases with network congestion. Additionally, agents in the local and pocket models are trigged on the Internet. Consequently, their delay time is not affected by
0 10 20 30 40 50 60 70 80 90 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 probability of move se c o n d s mobile model pocket model
Fig. 7. The time of two models with difference probability of move
0 20 40 60 80 100 120 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8 0.9 probability of network congestion
se
c
o
n
d
s local model case1
local model case2 mobile model pocket model
Fig. 8. The time of three models with difference probability of network congestion
network congestion. The shortest delay time is for the local model (Fig. 8). The second short time is for the pocket model.
This study compared the three models with different factors. Integrating the above results shows that pocket model does not always have the shortest delay time; however, it is better than others overall. To compare the local assistant agent, mobile assistant agent, and pocket assistant agent, this study collates the advantages and disadvantages associated with those three approaches. The purpose of this work is to identify the best method to assist older adults in accessing the Internet and assist them in avoiding the difficulties discussed.
5.2 Advantages and disadvantages
This study gathers statistics for delay time and delay factors for the three models. Advantages and disadvantages of the three models are then analyzed. Table 1 presents comparison results for the three models.
Table 1 Comparison of three models
Performance error Mobility Network congestion
Local agent model better worst normal
Mobile agent model worse normal worse
Pocket agent model normal better better
Local assistant agent
Advantages. The local assistant agent is a fixative agent. The assistant agent is installed in a user’s computer, and does not need to connection to a web server to perform authentication. The agent helps older users at anytime
when they are using their own computer. Furthermore, the agent does not need another device to perform authentication. Thus, it is an easy approach for older users.
Disadvantages. Although the local assistant agent is an easy scheme, it cannot support mobility. The agent is only works on a local computer located in the home. When an older user uses ventures outside the home, the agent cannot assist them while operating other computers. When an older adult uses a public computer, the local assistant agent must be installed this requirement can cause serious problems. This operation is inconvenient for older users, as older users must perform more the steps of operations. These operations may be excessively difficult, causing older users to give up easily. Second, when older adults add new data to their sets, they must copy files from their computer to a storage device. Third, the local assistant agent may result in a user’s personal information being left on a public computer. Security is also a serious problem.
Mobile assistant agent
Advantages. The mobile assistant agent attempts to maximize user mobility. An older user can call a clone agent from an agent server for assistance. All personal information and settings are stored in a database on the agent server. The clone agent monitors user needs and updates modified personal settings in the agent server. Older adults can access the newest and most appropriate person information at all times.
Disadvantages. The mobile agent helps older adults access information on the Internet. However, older users must create a connection to an agent server; the agent server then dispatches the clone agent to the client node operated by the user. There are three problems in this scenario. First, an older user must memorize the URL of the agent server, her ID and password. If she forgets the ULR, ID or password, she cannot launch this service. Second, this process increases the steps required to access the Internet. An older user must key in the ULR, ID and password. Because their mechanical ability degenerates, additional operational steps lead to working efficiency of older adults. Third, and most importantly, mobile agents need an exit in a mobile agent environment. When a client node cannot host specific forms of mobile agents, an older user will not get any service from the mobile agent server. Additionally, the environment required by mobile agents is not universal.
Pocket assistant agent
Advantages. The pocket assistant agent provides mobile capabilities, without needing a mobile agent. This agent is stored in a pocket storage device. Consequently, the pocket agent does not consider the agent environment. By plugging the pocket storage device into a computer and the agent is automatically activated. All personal settings are stored in the device, including favorite web sites, history logs, and cookies. Therefore, an older user can avoid problems associated with connecting to an agent server, and work flow is simplified. Additionally, pocket storage devices are common and inexpensive.
Disadvantages. Older users must prepare a pocket storage device themselves.
Based on the advantages and disadvantages of the agents, older users by must use different triggers to activate agent services. The pocket assistant agent model has the shortest delay time; second is the local assistant agent model. Although delay time of the mobile assistant agent model is longest, it is more convenient than the local model in terms of user mobility. The pocket assistant agent model has the lowest delay time, and has mobile functionality. Pocket storage devices are very common and inexpensive. The pocket assistant agent does not require authentication and maintenance via a server. We conclude that the pocket assistant agent is superior to other models.
6 Conclusion and future work
The purpose of this study is to define a system that can assist older adults in accessing the Internet. The agent system can solve the problems that limit the access of older adults to the Internet. The performance of the three models investigated differed under different circumstances. When an older user is at home and seldom accesses the Internet outside the home, the local agent can meet her needs. However, when older users wants to access the Internet outside the home, the mobile agent and pocket agent can meet their requirements. The pocket agent model meets user needs in various situations. This study presents three web agent models that aim at assisting
older adults, and compares their differences. Comparison results indicates that the packet model is fittest for older adults, as it has less delay time and operates more easily than the other agent models. Future research will investigate agents on the Internet designed for older adults, and design of additional agent system to assist older users accessing the Internet.
Reference
[1] Chadwick-Dias, D. Tedesco, and T. Tullis, “Older Adults and Web Usability: is Web Experience the Same as Web Epertise?” in Proceeding of Conference on Human Factors in Computing Systems, pp. 1391-1394, Apr. 2004.
[2] N. Sukkar, “The Digital Divide and Development,” in Proceeding of Information and Communication Technologies: From Theory to Applications, pp. 27-28, April 2004.
[3] S. Trewin, “A Study of Input Device Manipulation Difficulties,” in Proceedings of the second annual ACM conference on Assistive technologies, April 1996.
[4] V. L. Hanson, “Web Access for Elderly Citizens,” in Proceedings of the 2001 EC/NSF workshop on Universal accessibility of ubiquitous computing, pp. 14-18, May 2001.
[5] S. Kurniawan and P. Zaphiris, “Research-Derived Web Design Guidelines for Older People,” in Proceeding of the 7th international ACM SIGACCESS conference on Computers and accessibility, pp.129-135, Oct. 2005.
[6] D. Maciuszek, J. Aberg, and N. Shahmehri, “What Help do Older People Need? Constructing a Functional Design Space of Electronic Assistive Technology Applications,” in Proceedings of the 7th international ACM SIGACCESS conference on Computers and accessibility Assets '05, pp.4-11, Oct. 2005.
[7] X. Zhou, D. Wu, and J Zhang, “Multi-agents Designed for Web-based Cooperative Tutoring, ” in Proceedings of 2005 IEEE International Conference on Natural Language Processing and Knowledge Engineering, pp. 479-482, 2005.
[8] Z. Zi-ming and M Bo, “An Intelligent Shopping System based on Multi-agent Collaborative Working Model,” in Proceedings of Canadian Conference on Electrical and Computer Engineering, pp. 1562-1565, 2005.
[9] J. Accot and S. Zhai, “Performance Evaluation of Input Devices in Trajectory-Based Tasks: An Application of the Steering Law,” in Proceedings of SIGCHI conference on Human factors in computing systems, pp. 466-472, 1999.
[10] S. Artis, “Effects Of Age And Working Memory On Web-Based Computer Training,” in Proceedings Visual Languages And Human Centric Computing, pp. 269-27, Sept. 2004.
[11] Caglayan and C. Harrison, Agent Sourcebook, John Wiley & Sons, Inc, January 1997.
[12] J. Maeda, K. Fukuda, H. Takagi and C. Asakawa, “WebDigest: Layout-Preserving Visually Enhanced Web Pages,” in Proceeding of Applications And the Internet, pp. 418-421, Jan. 2003.
[13] J.L. Arnott, Z. Khairulla, A. Dickinson, A. Syme, N. Alm, R. Eisma, and P. Gregor systems, "E-mail Interfaces for Older People," in Proceeding of 2004 IEEE International Conference on Man and Cybernetics, Vol.1, pp. 111-117, Oct. 2004.
[14] L. Ardissono, A. Goy, G. Petrone, and M. Degnan, “A Multi-Agent Infrastructure for Developing Personalized Web-Based Systems,” ACM Transactions on Internet Technology, Vol.5, pp. 47-69, Feb. 2005.
[15] D. Chess, B. Grosof, C. Harrison, D. Levine, C. Parris, and G. Tsudik, “Itinerant Agents for Mobile Computing,” IEEE Personal Communications, pp. 34-39, 1995.
[16] W. R. Cockayne and M. Zyda, Mobile Agent, Prentice Hall PTR, Jan. 1998.
[17] Falchuk and A. Karmouch, “AgentSys: a Mobile Agent System for Digital Media Access and Interaction on an Internet,” in Proceedings of IEEE Global Telecommunication Conference (GLOBECOM ‘97), Vol. 3, pp. 1876-1880, 1997.
[18] S. Green, L. Hurst, B. Nangle, P. Cunningham, F. Somers, and R. Evans, Software Agents: A Review, http://www.cs.tcd.ie/research_group/aig/iag/iag.html.
[19] V. A. Pham and A. Karmouch, “Mobile Software Agents: An Overview”, IEEE Communications Magazine, pp. 26-37, July 1998.
[20] T. Sandholm and Q. Huai, “Nomad: Mobile Agent System for an Internet-based Auction House,” IEEE Internet Computing, Vol. 4, No. 2, pp. 80-86, 2000.
[21] B, Thai, S. Wan, and A. Seneviratne, “Executions of Home Applications and Service Customizations in Integrated Personal Mobility Architecture,” in Proceedings of Computers and Communications, 2002. ISCC 2002. Seventh International Symposium, pp. 321-326, Nov. 2002.
[22] G. Itabashi, M. Chiba, K. Tkahashi, and Y. Kato, “A Support System for Home Care Service Based on Multi-agent System, in Proceedings of 2005 Fifth International Conference on Information, Communications and Signal Processing, pp. 1052-1056, 2005.
[23] P. Bellavista, A. Corradi, and C. Stefanelli, “The Ubiquitous Provisioning of Internet Service to Portable Devices,” IEEE Pervasive Computing , Vol. 1, No. 3, pp. 81-87, 2002.
[24] S. Rajan and M. Ma, “Agent Driven Ubiquitous Mobility,” in Proceedings of the 10th IEEE Singapore International Conference on Communication Systems, pp. 1-5, 2006.
[25] DataTraveler II Plus - Migo Edition, http://www.kingston.com/flash/dt_IIplusMigo.asp
[26] S. Potter and J. Nieh, “WebPod: persistent Web Browsing Sessions with Pocketable Storage Devices,” in Proceedings of the 14th International Conference on World Wide Web, pp. 603-612, May 2005.
[27] T. W. Bickmore, L. Caruso, and K. Clough-Gorr, “Acceptance and Usability of a Relational Agent Interface by Urban Older Adults,” in Proceeding of Conference on Human Factors in Computing Systems, pp. 1212-1215, April 2005.
[28] Chadwick-Dias, M. McNulty, and T. Tullis, “Web usability and Age: How Design Changes Can Improve Performance,” in Proceeding of conference on Universal usability, pp. 30-37, Nov. 2003.
[29] Y. Zhao and E. Tyugu, Towards a Personalized Browser for Elderly Users, http://ui4all.ics.forth.gr/UI4ALL-98/zhao.pdf
[30] P. V. Knudsen and J. Maden, “Integrating Communication Protocol Selection with Hardware/Software Codesign,” IEEE Transactions on Computer-Aided Design of Integrated and Systems, Vol.18, No.8, pp. 1077-1095, Aug. 1999.