Luor, T., Lu, H.-P., Tao, Y.-H.,
Lin, T. M. Y. and Tung, C.-H., Determinants of client
intention of software outsourcing vendors - A model from Taiwan's financial industry ,
Journal of Academy of Business and Economics (Selected paper of IABE 2008), Vol.8, No. 2,
159-165, 2008.
DETERMINANTS OF CLIENT INTENTION OF SOFTWARE OUTSOURCING VENDORS: A MODEL FROM TAIWAN’S FINANCIAL INDUSTRY
Ted Tainyi Luor, National Taiwan University of Science and Technology, Taiwan, ROC Hsi-Peng Lu, National Taiwan University of Science and Technology, Taiwan, ROC
Yu-Hui Tao, National University of Kaohsiung, Taiwan, ROC
Tom M. Y. Lin, National Taiwan University of Science and Technology, Taiwan, ROC Chi-Hsiang Tung, International Bills Finance Corporation, Taiwan, ROC
ABSTRACT
While many studies have focused on information software (IS) outsourcing, little is known about the determinants influencing clients’ decision on IS outsourcing vendors. This article explores the relationships among client beliefs, factors, and intention, which determine their associations with IS outsourcing vendors in the financial industry—a relatively conventional industry with a preference for rule-regulated and structured activities. Ten factors influencing the decision of outsourcing vendors are first classified into four belief groups; then a simple model explaining client intention and preferences with respect to outsourcing is presented using the Correlation Analysis. Interviews with participants are also conducted to collate information during the classification process. By systematically discussing factors and attempting to bridge the gap between theory and practice, this article presents certain useful findings to theorize the association between IS clients and vendors for Taiwan’s financial industry.
Keywords: information system, outsourcing, security, belief, trust
1. INTRODUCTION
The volume and range of services being outsourced have notably increased in recent years (Gonzalez, Gasco, and Llopis, 2006). In fact, the study of outsourcing has progressively increased since its early start in the 1960s (Gonzalez et al., 2006). In practice, many companies have been choosing IS outsourcing in response to complicated information systems (IS) and various internal requirements. In literature, many studies focused on IS or Information Technology (IT) outsourcing provide fruitful references for suppliers to formulate their methodologies and strategies for successful IS implementations (Yusufa et al., 2004). A successful IS outsourcing relationship can help outsourcing clients to achieve benefits such as cost-savings, increased flexibility, better quality services, and acquisition of new technology. However, there is little theoretically sound and formal knowledge about the determinants that influence a clients’ decision on IS outsourcing vendors. Therefore, it would be a perfect supplement to the existing literature and IS outsourcing suppliers for providing a formal model uncovering the determinants influencing the client’s intention to use an IS outsourcing vendor.
The banking and thrift industries are undergoing a technological metamorphosis (Zhu, Scheuermann, and Babineaux, 2004). This venture has attracted considerable attention and speculation in both the financial and IT communities. In addition, in 2003, expenditures for outsourcing information services totaled USD$500 million, a 14% increase over the previous year. In terms of the types of outsourcing jobs, the services engaged were still mainly software development and maintenance, which accounted for 55.03% of all services (Taylor and Todd, 1995). This paper studies the IS outsourcing factors in the
The financial industry is an information-intensive industry in which information technology (IT) is becoming increasingly important. Take Taiwan for example. The financial institutions are facing dual competitive pressure in the areas of service quality and administrative efficiency (DGBAS, 2007). Taiwan has also been rated as having a high-performance orientation—the degree to which a society encourages and rewards group members for performance improvement and excellence (Javidan and House, 2001). In 2003, a total of USD$4.2 billion was expended on ITs in the nation, indicating a 25.33% increase over the previous year and accounting for 1.3% of the GDP. In terms of the ratio of information expenditure to total capital, the financial industry, including the banking and insurance industry, ranked as the second largest buyer of ITs (accounting for 16.57% of the total amount), after the manufacturing industry (20.51%). The function and role of IT in an organization are assisting in streamlining business processes via IT, creating a competitive edge through strategic developments, underpinning/enhancing strategic business goals, and maximizing operational efficiencies (Peppard and Ward, 1999). Therefore, Taiwan’s financial industry is an ideal place to investigate the relationships among the variables of IS outsourcing and develop a model for impacting clients’ decision on IS outsourcing vendors.
The organization of the remaining paper is as follows: Research Model depicts the variables and the model, Research Method profiles the 12 CIOs and briefly describes the process of conducting this study, Measure and Results examines the summarized results, Discussion presents the interpretation of the results, and Conclusions summarizes this study with limitations and future work.
2. RESEARCH MODEL
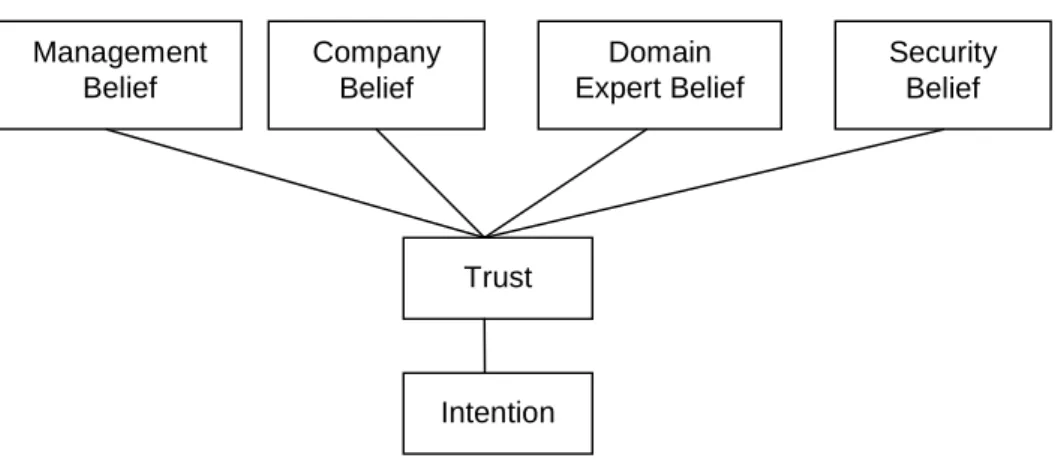
The formulation of the proposed research model is presented. With additional companies outsourcing their software-related operations, issues associated with the management of outsourcing relationships have attracted significant research attention. Many studies have identified numerous outsourcing variables. However, no consistent groups have been found. Our literature analysis resulted in ten external variables with regard to the theoretical research model. These variables, including project management (PM), capability maturity model integration(CMMI), client satisfaction (SAT), quality (QUL), image/reputation (IR), stable financially and managerially (SFM), business size (BS), industry expertise (IE), experience (EXP), and security of confidential data or protection valuable software asset (SPS), have been posited or demonstrated as being associated with outsourcing in previous researches.
Moreover, ten variables found to affect the outsourcing decision in previous studies are categorized into four belief groups, including management belief (MB), company belief (CB), domain expert belief (DEB), and security belief (SB), based on the opinion of twelve chief information officers (CIOs). The 12 CIOs all have over 10 years experience of software industry, are currently working in the companies with capital of greater than 100 $USD million, and mostly agree or strongly agree with the 4 belief categories suggested by this study. A simple guideline for assigning the variable to the belief is based on the number of votes by the 12 CIOs. For example, since Project Management has 11 votes on Management belief and 1 vote on the Company belief, it is classified into Management belief. Accordingly, PM, CMMI, SAT and QUL belong to Management belief, IR, SFM, and BS belong to Company belief, IE and EXP belong to Domain Expert belief, and SPS alone belongs to Security. Another noteworthy variable is trust. In their case study of outsourcing relationships, Zviran et al. (2001) found that the gradual development of trust can lead companies from merely being committed to a contract to becoming long-term strategic partners. There are also many studies on the effect of trust as an important outsourcing factor (Kishore et al., 2003; Sabherwal, 1999; Lander et al., 2004; Kern and Willcocks, 2000; 2002). Thus, it is reasonable to introduce trust into the uncertain model of clients when they choose an IS outsourcing vendor. Based on the above derivation, we propose a conceptual model as shown in Figure 1.
3. RESEARCH METHOD
This section describes the research method used to test the research model and hypotheses. Based on the proposed model for IS outsourcing relationships, both data collection methods of personal interview and survey are adopted. The research model required a great deal of information to be gathered from the survey participants. As CIOs and survey participants often do not have the time for in-depth interviews, we decided to administer both questionnaires and short interviews.
In the first stage, as seen in the previous section, we conducted the short interviews with twelve CIOs and classified 10 variables into MB, CB, DEB, and SB. To assess the research model in the second stage, we conducted a questionnaire-based survey to collect data from IT managers or staff employees of Taiwan’s financial industry. Participants were asked to fill out the questionnaire, based on their experiences of working with one particular IS outsourcing vendor.
The preliminary instrument was initially reviewed for comprehensiveness and unambiguity by some faculties, doctoral candidates, and Executive Master of business administration (EMBA) students who had also worked in the financial industry. The measurement sufficiency of the proposed measures was also examined in a realistic context by some IT experts in the financial market in order to verify the suitability of the written expressions, the clarity of the information, and the response formats. It was concluded that no particular problems existed in the survey instrument.
Invitation e-mails were sent out to more than 300 people, including IT managers and employees working in Taiwan’s financial industry. The e-mail explained the purpose of the study and requested peoples’ participation. The investors were asked to click on the URL link provided in the e-mail message, which was linked to the Web-based online survey instrument. A coupon valued at 100 Taiwanese dollars (about USD$3) was offered to encourage participation.
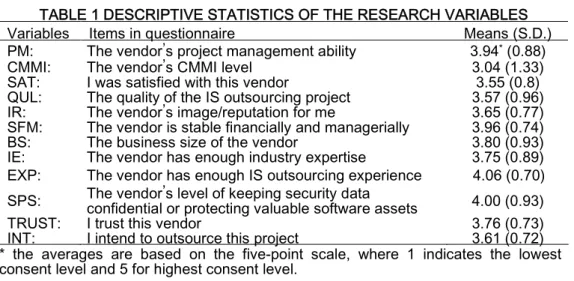
Each participant was asked to complete a questionnaire that included the measures of the ten variables, attitude, trust, and three types of intentions. All items had five-point scales anchored with “lowest consent level” (1), “highest consent level” (5), and “neutral level of consent” (3). The questionnaire items can be seen in Table 1 in the next section. Overall, 102 experts with work experience in IS outsourcing responded to our survey.
4. MEASURES AND RESULTS
Management Belief Company Belief Domain Expert Belief Security Belief Trust Intention
profile roughly matches the stereotype of Taiwan IT professions based on our assessment.
The descriptive statistics of the mean and standard deviation (S.D.) for the ten variables are summarized in the last column of Table 5. Among them, all but one have averages above 3.5, which is on the somewhat consent level of the five-point scale used in this study. In particular, EXP and SPS are above 4.0 and PM and SFM are close to 4.0, which indicate a pretty strong level of consent. On the other hand, CMMI is just a little bit over the neutral level of 3.0, which is an indication of it being a relatively less dependent variable. As mentioned in the above section, the descriptions of the questionnaire items are shown in the second column of Table 1.
Since security has only one item, its reliability is unavailable. Among the other three beliefs, only Management belief has a reliability coefficient higher than 0.8, which is considered adequate. As for the other two beliefs, namely Company belief and Domain Expert belief, their reliability coefficients are less adequate since they are 0.6454 and 0.5671. Therefore they will be marked as limitations of this study in the Conclusion section.
TABLE 1 DESCRIPTIVE STATISTICS OF THE RESEARCH VARIABLES
Variables Items in questionnaire Means (S.D.)
PM: The vendor’s project management ability 3.94*(0.88)
CMMI: The vendor’s CMMI level 3.04 (1.33)
SAT: I was satisfied with this vendor 3.55 (0.8)
QUL: The quality of the IS outsourcing project 3.57 (0.96) IR: The vendor’s image/reputation for me 3.65 (0.77) SFM: The vendor is stable financially and managerially 3.96 (0.74)
BS: The business size of the vendor 3.80 (0.93)
IE: The vendor has enough industry expertise 3.75 (0.89) EXP: The vendor has enough IS outsourcing experience 4.06 (0.70) SPS: The vendor’s level of keeping security dataconfidential or protecting valuable software assets 4.00 (0.93)
TRUST: I trust this vendor 3.76 (0.73)
INT: I intend to outsource this project 3.61 (0.72) * the averages are based on the five-point scale, where 1 indicates the lowest consent level and 5 for highest consent level.
Using our research model, the ten variables were categorized into four beliefs. MB, CB, and DEB consisted of more than one variable; only one variable was categorized under SB. Therefore, we assumed that the values of MB, CB, and DEB could be equal to the average of the associated variables and be calculated by MB = (PM + CMMI + SAT + QUL ) / 4, CB = (IR + SFM + BS ) / 3, and DEB = (IE + EXP ) / 2. Table 2 summarizes the correlation coefficients among the four beliefs, trust, attitude, and the responses to the three types of intentions. For the 102 participants, all the beliefs with trust are at least significant at the 0.05 levels. In other words, the conceptual model is fully supported by the data collected in this study.
TABLE 2 CORRELATION MATRIXES
Variable Securit
y DomainExpert Company Management Trust Intention
Security 1.000 .071 .385(**) .217(*) .343(**) .087 Domain Expert 1.000 .206(**) .550(**) .458(**) .455(**) Company 1.000 .729(**) .574(**) .574 Management 1.000 .712(**) .752(**) Trust 1.000 .686(**) Intentions 1.000
** and * denote that correlation is significant at the 0.01 and 0.05 levels, respectively. Note: The means (standard deviations) are shown on the diagonal
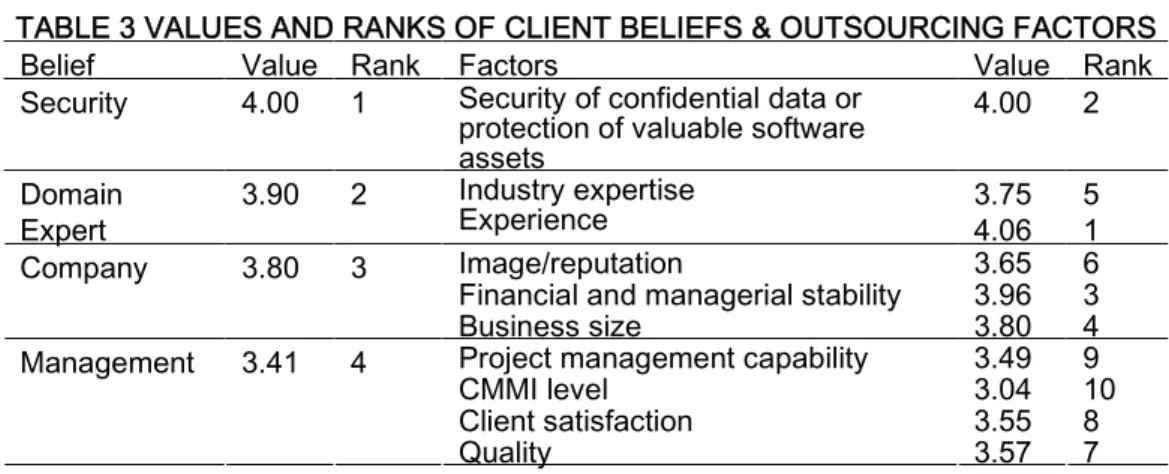
order: SB, DEB, CB, and MB, as shown in the third column of Table 3. The results imply that in the financial industry where employees are considered to be conventional and prefer rule-regulated and structured activities, SB is considered more seriously than the other three beliefs in IS outsourcing.
TABLE 3 VALUES AND RANKS OF CLIENT BELIEFS & OUTSOURCING FACTORS
Belief Value Rank Factors Value Rank
Security 4.00 1 Security of confidential data or protection of valuable software assets
4.00 2 Domain
Expert 3.90 2 Industry expertiseExperience 3.754.06 51
Image/reputation 3.65 6
Financial and managerial stability 3.96 3
Company 3.80 3
Business size 3.80 4
Project management capability 3.49 9
CMMI level 3.04 10
Client satisfaction 3.55 8
Management 3.41 4
Quality 3.57 7
5. DISCUSSION
According to the statistical analyses and CIO interview data, three implications can be derived as described next.
Implication 1: Security—the most important concern
The findings of our survey indicated security was the most important among the four beliefs, and 2nd
important variable among the ten variables in Table 8. One outsourcing vendor in our survey stated that most of his customers considered security issues when choosing an IS outsourcing vendor, although it was not the most important factor when compared with the other factors. However, security of data or physical assets is one of the most frequently cited concerns in many IS outsourcing studies; in addition, poor security, whether a breach that causes customer distrust or a catastrophic event that affects data or processes (Hayes, 2003; Jones, 1994), has been known to cost companies their money and reputation.
Therefore, while considering IS outsourcing services, companies in the financial industry request vendors to provide information on security issues and base their expectations of IS management and control on this information. Herein, we suggest that an information security standard that specifies high-level security requirements should be focused on and provided by vendors when clients issue their outsourcing requirements. While outsourcing IS services in the financial industry, it is essential that security issues, including roles, responsibilities, and accountability, are clearly defined and well understood by both clients and vendors. Specific security aspects must be included in both service level agreements (SLAs) and the security requirements of contracts. In our survey, some interviewees also mentioned their opinions on confidential data. For example, one CIO stated, “We provide all the stuff related to the outsourcing project; therefore, all the tasks related to IS outsourcing including program coding or document editing should be done on-site.”
Implication 2: Trust as a bridge between beliefs and intentions
Many studies have ascertained variables that influence trust. In this regard, trust could be differentiated into two parts (Oza, 2006): achieving trust in outsourcing relationships and maintaining trust in ongoing outsourcing relationships. Trust is also considered to be an extremely delicate issue in outsourcing relationships. Our study demonstrated that the four beliefs—SB, CB, DM, and MB—can serve as trust-achieving variables. This is consistent with other recent works on outsourcing relationships (Oza, 2006; Zviran et. al, 2001). Therefore, trust can serve as an intermediary connecting belief with intentions. From a practical perspective, our study shows that the combination of the four
with client intentions, we propose a model, which can chart the vendor’s path and help increase the client’s intention in it. Our study categorizes client beliefs pertaining to outsourcing into four types, wherein catering to each type constitutes a step toward attracting client intentions for vendors. However, each step rests on factors that need to be adequately strong to bear the weight of the client-vendor association and allow vendors to advance.
Addressing SB is the first step for vendors toward garnering client intentions. SB comprises only one factor, and this factor is of paramount importance because clients will not outsource work to vendors who cannot guarantee protection of their security assets.
The second step for vendors is catering to DEB, which comprises two factors: industry expertise and experience. A capable expertise provides adequate support to handle all applications. By recruiting, training, retraining, and retaining qualified staff in order to offer specialized services for clients’ company-specific problems, outsourcing vendors can positively affect the trust and intentions of clients. Further, vendors should also possess expertise in client industries and software. In cases where outsourcing vendors serve the direct competitors of their clients, ensuring adequate confidentiality is imperative for the vendors. Herein, experience and resources of vendors facilitate the implementation of solutions (Grupe, 1997). Critical variables in realizing trust in an outsourcing relationship include previous clients’ references and vendors’ experience in outsourcing engagements. If these criteria are met, information provided by the vendors can be considered as highly reliable.
Ensuring CB constitutes the third step for vendors en route to securing client intentions. This step is laid on the foundations of the following three factors: image/reputation, financial and managerial stability, and business size. The reputations of outsourcing vendors affect their chances of receiving outsourcing assignments (Gonzalez et.al, 2005). Initially, reputation is a critical variable for trust in the field of software outsourcing in that it leads to good references and stable relationships. For top managements, reputation is an important determinant of trust when they handpick individuals for outsourcing projects (Lander et. al, 2004). Financial stability and funding can help outsourcing vendors stay competitive in the outsourcing arena (Grupe, 1997; McFarlan and Nolan, 1005). Some small businesses can fall short of providing adequate staff support even when they deploy as wide a variety of systems, software packages, and networks as their bigger counterparts and resolve equally as much related problems. This is because they possess fewer problem-solving resources. Therefore, the larger the business size, the more are the resources available for problem solving.
The fourth step of advancement for vendors is guaranteeing MB, which comprises the following four factors: project management capability, CMMI level, client satisfaction, and quality. Better project management capabilities can translate into better quantitative outsourcing estimation or measurement capabilities, thereby helping vendors achieve better performances than their competitors. Leading vendors generally employ a suite of project management tools, including cost estimation, quality estimation, software planning, and software tracking tools. For example, a firm in the factory quadrant that selects an operationally strong outsourcer may encounter difficulties if it suddenly shifts to the strategic quadrant where its partner lacks the necessary project management and innovation skills to operate. Secondly, CMMI provides a detailed method for assessing the maturity of the software development process. Lastly, Satisfaction in an outsourcing relationship comes about naturally with the meeting of client expectations. The more satisfied a client is with a vendor, the more trust and intention the vendor is guaranteed. High quality of IS outsourcing services by vendors can maintain IS outsourcing customer satisfaction.
After vendors understand and satisfy client beliefs, akin to taking developmental steps, they are led to the bridge of trust that connects them with clients, helping them attract client intentions. Our study ascertains that trust is highly correlated with client intentions. Vendors who satisfy client beliefs and the included factors better their chances of gaining client trust and securing outsourcing assignments.
6. CONCLUSIONS
outsourcing vendor and proposes a theoretical-based model to address this issue in the context of the financial industry. With the analytical approach used in this study, we believe that this study presents useful and practical findings for IS outsourcing vendors to acquire client’s intention to adopt. Despite our careful work, a few limitations need to be noted when using the practical model and implications of this study. First of all, there are only 10 variables and 4 beliefs considered in this study. Some of the CIOs stated that more variables and beliefs may be needed to comprehend the basis on which the clients choose the software outsourcing vendors. Secondly, the reliability coefficients of the four beliefs are not comfortably adequate to analytical standards. More questionnaire items and variables may be needed to improve current measurements. Thirdly, if designed appropriately with the second limitation considered together, the research model can use a more formal method like structured equation method to fit the research model and test the model path. Finally, only the respondents in Taiwan’s financial markets are surveyed in this study. Although the findings may be useful to its scope, they are certainly not representative of the entire Taiwanese financial industry or participants elsewhere. Future research will be necessary to examine these relationships in other financial markets or to compare the results with other industries and demonstrate the managerial implications of these comparisons.
7. REFERENCES
Gonzalez, R., Gasco, J., and Llopis, J., “Information Systems Outsourcing: A Literature Analysis”,
Information & Management, Vol. 43, 2006, 821–834.
Gonzalez, R., Gasco, J., and Llopis, J. (2005), “Information Systems Outsourcing Risks: A Study Of Large Firms”,Industrial Management & Data Systems, Vol. 105(1), 2005, 45–62.
Grupe, F., “Outsourcing The Help Desk Function”, Information Systems Management, Vol. 14( 2), 1997, 15–22.
Hayes, M., “Precious Connection”,InformationWeek, Vol. 960, 2003, 34–40.
Javidan, M. and House, R.J., “Cultural Acumen for The Global Manager: Lessons From Project GLOBE”,Organizational Dynamics, Vol. 29(4), 2001, 289–305.
Jones, C., “Evaluating Software Outsourcing Options”,Information Systems Management, Vol. 11(4), 1994, 28–33.
Kern, T. and Willcocks, L., “Exploring Information Technology Outsourcing Relationships: Theory And Practice”,Journal of Strategic Information Systems, Vol. 9, 2000, 321–350.
Kern, T. and Willcocks, L., “Exploring Relationships In Information Technology Outsourcing: The Interaction Approach”,European Journal of Information Systems, Vol. 11(1), 2002, 3–19.
Kishore, R., Rao, H.R., Nam, K., Rajagopalan, S., and Chaudhury, A., “A Relationship Perspective On IT Outsourcing”,Communications of the ACM, Vol. 46(12), 2003, 87–92.
Koch, C., “Bursting The CMM Hype”, CIO, Vol. 17(10), 2004,1–6.
Lacity, M.C. and Hirschheim, R., “The Information Systems Outsourcing Bandwagon”, Sloan Management Review, Vol. 35(1), 1993, 73–86.
Lander, M., Purvis, R., McCray, G., and Leigh, W., “Trust-Building Mechanisms Utilized In Outsourced IS DevelopmentProjects: A Case Study”,Information & Management, Vol. 41, 2004, 509–528.
McFarlan, F. and Nolan, R., “How To Manage An IT Outsourcing Alliance”,Sloan Management Review, Vol. 36(2), 1995, 9–23.
Oza, N., Hall, T., Rainer, A., and Grey, S., “Trust In Software Outsourcing Relationships: An Empirical Investigation Of Indian Software Companies”, Information and Software Technology, Vol 48, 2006, 345–354.
Peppard, J. and War, J., “Mind The Gap: Diagnosing The Relationship Between The IT Organization And The Rest Of The Business”,Journal of Strategic Information Systems, Vol. 8, 1999, 29–60. Sabherwal, R., “The Role Of Trust In Outsourced IS Development Projects”,Communications of the ACM, Vol. 42,(2), 1999, 80–86.
Taylor, S. and Todd, P., “Understanding Information Technology Usage: A Test Of Competing Models”,
Information Systems Research, Vol. 6(2), 1995, 144–176.
Yusufa, Y., Gunasekaranb, A. and Abthorpe, M.S., “Enterprise Information Systems Project
Implementation: A Case Study of ERP In Rolls-Royce”,International Journal of Production Economics, Vol. 87, 2004, 251–266.
AUTHOR PROFILES
Dr. Ted Tainyi Luor earned his Ph.D. at the National Taiwan University of Science and Technology, Taiwan, R.O.C. in 2007. Currently he is the manager of information systems department at the International Bills Finance Corporation and a part-time assistant professor at the National Taiwan University of Science and Technology.
Dr. Hsi-Peng Lu earned his Ph.D. at the University of Wisconsin, Madison in 1992. Currently he is a professor and the Dean of Student Affairs at the National Taiwan University of Science and Technology, Taiwan, ROC
Dr. Yu-Hui Tao earned his Ph.D. at the Ohio State University, U.S.A. in 1995. Currently he is a professor and the Directory of Extension Education Center at the National University of Kaohsiung. Dr. Tom M. Y. Lin earned his Ph.D. from Warwick University, U.K. Currently he is an associate professor at the National Taiwan University of Science and Technology, Taiwan, ROC
Mr. Chi-Hsiang Tung currently works in the Information department at the International Bills Finance Corporation, Taiwan, R.O.C.