台灣臉書使用者的隱私權管理 - 政大學術集成
全文
(2) 台灣臉書使用者的隱私權管理 Facebook users’ privacy management in Taiwan. 研究生:林宜萱 指導教授:劉幼琍教授. 立. Student: Yi-Hsuan Lin Advisor: Professor Yu-li Liu. 政 治 大. 國立政治大學. ‧ 國. 學. 國際傳播英語碩士學位學程. Nat. er. io. sit. y. ‧. 碩士論文. al. n. A Thesis v i Submitted to International Master’s Program in n Ch U e n g c h i Studies International Communication National Chengchi University In partial fulfillment of the Requirement For the degree of Master of Arts. 中華民國 103 年 7 月 July 2014. i.
(3) ACKNOLWEDGEMENT My two years as a graduate student went by like a whirlwind. Producing this thesis was by far one of the most challenging tasks in my academic career. I felt like I had to exhaust all of my knowledge and skill sets to actually make this happen. There were a lot of hiccups, or so-called “rough patches” throughout this process. But luckily I had some amazing people to walk with me along the way. First and foremost, I would like to thank my advisor, Professor Yu-li Liu for her continuous support from the start to finish. I was truly thankful for all the time she put into working with me. It was the numerous meetings and revisions we went. 政 治 大 members, Professor TJ Shih and Professor Wen-yi Hsu for their guidance during my thesis 立 through together that helped me polish my work. I would like to thank my committee. writing process. I really appreciated the commitment and constructive feedback from them.. ‧ 國. 學. Also, I would like to offer my special thanks to Abby Moreno, Esther Lu and Ruby Liu. ‧. from IMICS ’14. While thesis writing could be such a demanding job both physically and. sit. y. Nat. mentally, having a support group so that we could have someone to whine to, panic with and. io. er. eventually find a way out together was utterly important. The long hours in the study room, the spontaneous phone calls to vent about our misery (with thesis), and the weekend-long trip. al. n. v i n Cschedules we took to an island amid our busy endless thesis meetings were all parts of U h e n gand i h c the package. I was glad to come to know these amazingly positive individuals. At one point, thesis writing wasn’t so bad anymore. Last but not least, I would like to thank my family and my pet bunny for putting up with me throughout my crazy moments while writing my thesis. Needless to say, they had always been my strongest support group. I felt extremely blessed.. ii.
(4) ABSTRACT Given the high penetration rate of Facebook and more than 10 million daily active users in Taiwan, the subject of Facebook became an important focus of study. This thesis attempted to examine how factors such as gender and gender, time spent on Facebook, personal privacy orientation, knowledge, negative experiences and privacy concerns would predict users’ profile privacy settings and their use of privacy protection strategies. By utilizing the Communication Privacy Management theory (CPM), individuals and collectives would develop the rules, known as boundary. In the process of managing one’s privacy, they would coordinate the boundary and also mitigate the disruption to the rules established, known as boundary turbulence. A survey of 1,102 Facebook users in Taiwan through an online questionnaire was conducted over a two-week period from April 29 – May12, 2014, and yielded a confidence level of 95% and a 3% confidence interval. Results showed that 48.6% of respondents were males, while 51.4% were females. Respondents that fell between the age group 25-34 also made up the biggest group among users. Respondents had spent an average of 4.71 years on Facebook at the time of the study, and reported that they spent an average of 3.06 hours on Facebook per day. Facebook users in Taiwan were privacy-oriented, had partial knowledge to. 立. 政 治 大. ‧ 國. 學. ‧. Facebook’s privacy policy, and were concerned about their privacy on Facebook, particularly. er. io. sit. y. Nat. how Facebook utilized their personal user information. As for negative experiences users had on Facebook, over three quarters of them reported the negative experience of being invited into the spammed shopping groups. Respondents also utilized different privacy settings based on the nature of the information on their profiles.. al. n. v i n C h regression analyses, Through performing linear hierarchical e n g c h i U results showed that gender, time spent on Facebook, users’ personal privacy orientation, knowledge toward Facebook’s privacy policy and negative experiences served as predictors to the strictness of users’ profile privacy settings. On the other hand, gender, age, knowledge toward Facebook’s privacy policy, negative experiences and privacy concerns served as predictors for users’ privacy protection strategies. This thesis contributed to the current research pool in the following ways. First of all, the sample in this thesis was representative of the population of daily active users in Taiwan. Secondly, while numerous previous studies have focused on predicting users' privacy management via privacy settings or the frequency of updating their privacy settings as dependent variables, this thesis also considered privacy protection strategies, such as deleting Facebook friends, un-tagging photos, and turning off cookies on computers. Thirdly, this thesis also considered users' negative experience on Facebook, and confirmed that it was a significant predictor to both users’ privacy settings on profiles, and privacy protection strategies. iii.
(5) Keywords: Communication Privacy Management theory (CPM), Facebook, privacy, boundary management, Taiwan. 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. iv. i n U. v.
(6) TABLE OF CONTENT Chapter One: Introduction-------------------------------------------------------------------------------1 1.1 Facebook users abroad and in Taiwan------------------------------------------------------2 1.2 Purpose of research---------------------------------------------------------------------------5 1.3 Chapter organization--------------------------------------------------------------------------6 Chapter Two: Literature review-------------------------------------------------------------------------8 2.1 Nature of social networking sites and privacy paradox phenomenon-----------8 2.2 Definition of privacy------------------------------------------------------------------10 2.3. Theoretical framework: Communications Privacy Management (CPM)------------14. 2.4. Previous research on users’ privacy management on Facebook----------------------19. 政 治 大. Chapter Three: Methodology--------------------------------------------------------------------------26. 立. 3.1 Survey questionnaire design---------------------------------------------------------------27. ‧ 國. 學. 3.2 Measurement --------------------------------------------------------------------------------29 3.3 Sampling plan--------------------------------------------------------------------------------32. ‧. 3.4 Statistical analysis---------------------------------------------------------------------------35. y. Nat. Chapter Four: Facebook’s development in Taiwan and privacy policy evolvement------------37. io. sit. Chapter Five: Data analysis on the survey questionnaire------------------------------------------46. n. al. er. 5.1 Correlation between independent variables and dependent variables---------------58. i n U. v. 5.2 Predicting users’ profile privacy settings on Facebook--------------------------------60 5.3. Ch. engchi. Predicting users’ use of privacy protection strategies on Facebook---------61. Chapter Six: Discussion--------------------------------------------------------------------------------65 Chapter Seven: Conclusion-----------------------------------------------------------------------------75 Notes------------------------------------------------------------------------------------------------------82 References------------------------------------------------------------------------------------------------83 Appendix I: Survey questionnaire (Chinese version)---------------------------------------------90 Appendix II: Survey questionnaire (English version)---------------------------------------------95 Appendix III: Construct intercorrelation------------------------------------------------------------101 Appendix IV: Results of research question and hypotheses-------------------------------------103. v.
(7) LIST OF TABLES Table 1.1. Top 10 websites with the most unique viewers in Taiwan---------------------5. Table 3.1. Descriptive statistics of constructs-------------------------------------------------32. Table 3.2. Sample demographics----------------------------------------------------------------33. Table 5.1 Years of using Facebook----------------------------------------------------------------46 Table 5.2. Average hours spent using Facebook per day------------------------------------47. Table 5.3. Respondents’ personal privacy orientation--------------------------------------47. Table 5.4. Respondents’ knowledge regarding Facebook’s privacy policy-----------50. Table 5.5. 政 治 大 Respondents’ privacy concerns----------------------------------------------------53 立. Table 5.6. Respondents’ previous negative experience on Facebook------------------51. Respondents’ profile privacy settings for less sensitive information-------55. Table 5.8. Respondents’ profile privacy settings for more sensitive information-----56. Table 5.9. Respondents’ privacy protection strategies-------------------------------------57. Table 5.10. Zero-order correlation--------------------------------------------------------------59. ‧. ‧ 國. 學. Table 5.7. y. Nat. er. io. sit. Table 5.11 Hierarchical linear regression on Facebook users’ privacy settings on profiles and privacy protection strategies in Taiwan (Final standardized regression. al. n. v i n Ch coefficients)--------------------------------------------------------------------------64 engchi U. vi.
(8) LIST OF FIGURES Figure 2.1. Communications Privacy Management by Petronio (2002, 2007)--------15. Figure 3.1. Research model-----------------------------------------------------------------------28. Figure 4.1. Facebook users and feature launch dates over the years (2004-2014)----39. Figure 4.2. Number of Facebook users in Taiwan (2009-2013)-------------------------41. Figure 6.1. Predictors of users’ privacy settings---------------------------------------------73. Figure 6.2. Predictors of users’ privacy protection strategies--------------------------74. 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. vii. i n U. v.
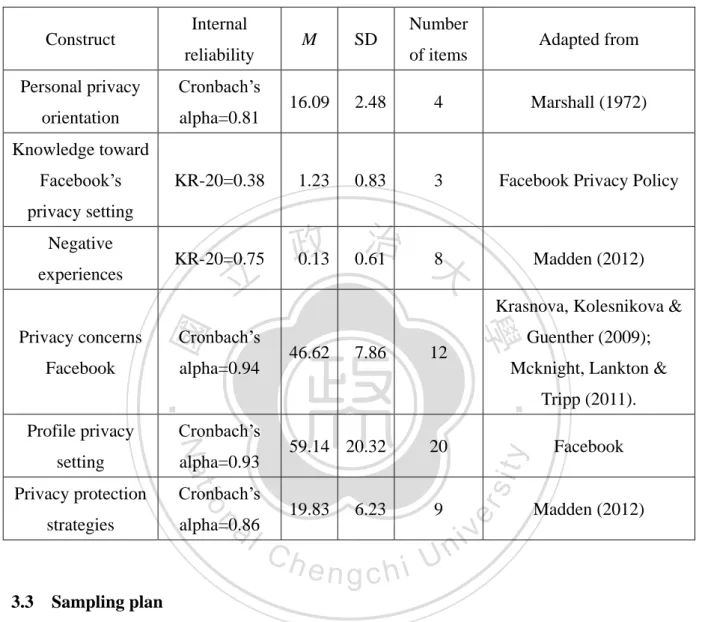
(9) CHAPTER ONE: INTRODUCTION While the year 2014 marks the 10th anniversary for Facebook, it has gone from the college dorm in Harvard to 1.23 billion monthly active users worldwide (Kiss, 2014). With a vast audience base, the company has over 1 million active advertisers worldwide by June 2013 (Stampler, 2013). Like many other social networking sites, Facebook relies heavily on selling advertising spots for its revenue. Facebook has gradually established itself as a major advertising venue. However, a survey carried out by Socialbakers in April 2013 depicted a loss of 9 million monthly users for Facebook in U.S.A., and 2 million in U.K. In a study by. 政 治 大 for quitting Facebook include privacy concerns (48.3%), general dissatisfaction (13.5 %), 立 University of Vienna by surveying 600 Facebook users in Europe, some of their top reasons. shallow conversations (12.6 %) and fear of becoming addicted (6 %). According to Brenda. ‧ 國. 學. Wiederhold, Editor of the journal Cyberpsychology, Behaviour and Social Networking which. ‧. published the findings,. sit. y. Nat. given high profile stories such as WikiLeaks and the recent NSA surveillance. io. er. reports, individual citizens [were] becoming increasingly more wary of cyber-related privacy concerns.. al. n. v i n C hconcerns was leading Apparently, users’ increasing privacy them into decreasing the use of engchi U Facebook, or committing “virtual identity suicide”1 to delete their Facebook accounts entirely (Woollaston, 2013). Aside from the decreasing number of users in some countries, there was also an increasing number of law suits regarding Facebook’s privacy breach by actions such as tracking users’ cookie that records web browsing history after the user logged off from Facebook (Protalinski, 2012), using "Sponsored Stories" program to share user's "likes" with certain advertisers without paying users or allowing them to opt out (Levine, 2013), and more recently, scanning users’ "private" messages for links and other information that can be sold to advertisers, marketers and data aggregators (Riley, 2014). 1.
(10) In fact, since 2011, Facebook had faced a series of allegations and lawsuits regarding how the social networking guru handled users’ data. For one, Facebook was facing a class action nationwide in the U.S.A. for tracking users’ cookies after they logged out of the service and using “Sponsored Stories” program to share users’ “likes” with certain advertisers. According to court filings, Facebook charged advertisers nearly $234 million for Sponsored Stories between January 2011 and August 2012; however, Facebook did not pay users or allow them to opt out of sharing their “likes” with advertisers (Levine, 2013). Facebook continued to track users’ cookie and receive data for user’s browser service instead. More. 政 治 大 website with Facebook’s social plug-ins. Eventually, the lawsuits snowballed and became a 立. importantly, the data recorded on cookies was found to be used by a third party, such as a. nation-wide class action. However, while the case was still pending, Facebook made changes. ‧ 國. 學. to the logout process in response to the class action, and ensured the cookies no longer sent. ‧. back personally-identifiable information after users log out (Protalinski, 2012).. sit. y. Nat. On the other hand, Facebook was also facing another class action for its violation of the. io. er. Federal Wiretap Laws. Basically, the case concerned allegations that when advertisements on Facebook games such as Farmville were clicked on the social network, identifiable. al. n. v i n C h page addressesUand Facebook IDs were collected, information of the user like the Facebook engchi. and disclosed to advertisers without users’ permission. But in May 2014, the San Francisco-based Ninth U.S. Circuit Court of Appeals ruled that Facebook did not violate the wiretap laws for disclosing identifiable information to the user. Hence Facebook has subsequently defeated this particular class action (Kravets, 2014).. 1.1. Facebook users abroad and in Taiwan With regard to Facebook’s global audience, Global Web Index released its quarterly. report, GWI Social from 2013 Q4 and found that users between 25 to 34 years old made up the biggest group for its user base, and only 26% of its active users were between ages 16-24 2.
(11) (Mander, 2014). Similarly, according to Socialbakers (2014), a company that offered monitoring and tracking tools for analysis of social networks, the largest age group of Facebook users in May 2014 in Taiwan was between 25 to 34 years old (31.8%), followed by the users between the age of 18 to 24 years old (21.7%). In 2010, after surveying 2,253 American adults whom were 18 and older over a period of one month on the phone, Madden & Smith (2010) concluded in their research report with Pew Internet on “Reputation management and social media” that Americans were increasingly becoming aware of the fact that online reputation did matter, but the full scope. 政 治 大 those between 18-29 years of age more actively restricted access to the information they 立 of its influence was difficult to assess. According to them, young American adults, namely. shared. They were more likely to change their privacy settings, delete unwanted comments or. ‧ 國. 學. remove their names from photos when compared to other age groups. However, the efficacy. ‧. of these limitations by young adults was unknown. And lastly, the researchers pointed out that. y. sit. io. er. control.. Nat. reputation management was a moving target, but with many factors outside of a user’s. In terms of the Facebook users’ profiles, Gibbs & Cho (2010) looked into cross-cultural. al. n. v i n differences in privacy managementC behaviors between American and Korean social network hengchi U. users. Utilizing Petronio's (2002) Communication Privacy Management (CPM) theory, their study explored how the American users on Facebook and Korean users on Cyworld (a social networking site) regulated privacy boundaries in terms of thickness and thinness, size and range of collective privacy boundaries. Results suggested that different national cultures would place different values on privacy. As for Facebook in Taiwan, the traditional Chinese interface was launched in 2008. After the launch of the localized interface, what was significant was the immense popularity Facebook received from the famous game “Farmville” (commonly known as “Happy Farm” in Taiwan). At the time, 23 million people in China and Taiwan tended their digital crops on a 3.
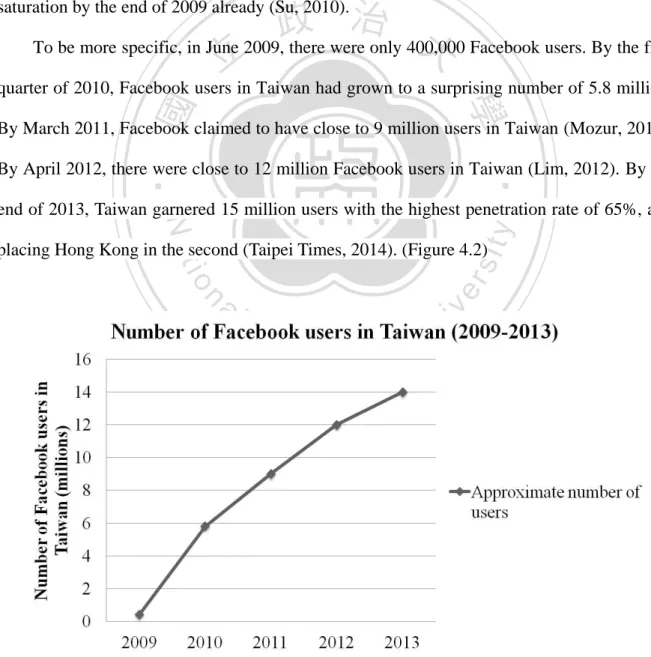
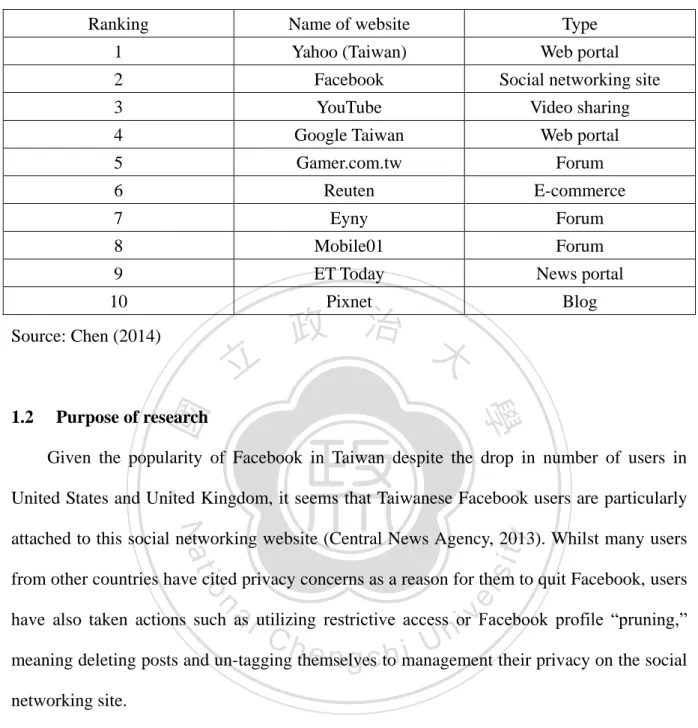
(12) daily basis (Penny, 2010). Up to date, the overall penetration rate in Asia at the end of 2012 was 6.5 percent. The case in Taiwan was even more significant. With a population of 23 million as of date, Taiwan had a 65 percent penetration rate based on the number released in February 2014 (Taipei Times, 2014). It was nearly ten times more than the overall average for Asian countries. While Taiwan already had the highest Facebook penetration rate in Asia, the number of active Facebook users in Taiwan also reached 14 million per month. Among these 14 million Taiwanese users, 10 million were daily users who conducted their social activities through their Facebook pages every day (Central News Agency, 2013). In addition, it was. 政 治 大. released in February 2014 that the penetration rate of Facebook users in Taiwan had gone up to 65% (Taipei Times, 2014).. 立. According to the comScore Media Metrix in April 2013 released by ARO/MMX, a. ‧ 國. 學. marketing research company in Taiwan, there was 118.7 million unique Internet users in. ‧. Taiwan, while Taiwanese users averagely spent 1,411 minutes, or 23.5 hours online per. sit. y. Nat. month. Moreover, at the time of the study, the website with the most visitors was Yahoo!. io. er. (Taiwan), and followed by Google Taiwan. Meanwhile, Facebook came in third (ARO/MMX, 2013). While Facebook had admitted a drop in teen users in U.S.A. (Bercovici, 2013), what. al. n. v i n was interesting was that despite theClawsuits against Facebook h e n g c h i U and a decrease in number of teen users in U.S.A., Facebook remained as one of the top social networking sites in Taiwan. with great popularity. In fact, based on a ranking calculated by Business Next between June to November 2013, Facebook was the second-most popular website in Taiwan, only second to the Web portal Yahoo (Taiwan), and followed by YouTube (Chen, 2014). (Table 1.1). 4.
(13) Table 1.1 The top 10 popular websites in Taiwan2 Ranking. Name of website. Type. 1. Yahoo (Taiwan). Web portal. 2. Facebook. Social networking site. 3. YouTube. Video sharing. 4. Google Taiwan. Web portal. 5. Gamer.com.tw. Forum. 6. Reuten. E-commerce. 7. Eyny. Forum. 8. Mobile01. Forum. 9. ET Today. News portal. 10. Pixnet. Blog. Source: Chen (2014). 立. ‧ 國. 學. 1.2. 政 治 大. Purpose of research. Given the popularity of Facebook in Taiwan despite the drop in number of users in. ‧. United States and United Kingdom, it seems that Taiwanese Facebook users are particularly. y. Nat. sit. attached to this social networking website (Central News Agency, 2013). Whilst many users. n. al. er. io. from other countries have cited privacy concerns as a reason for them to quit Facebook, users. i n U. v. have also taken actions such as utilizing restrictive access or Facebook profile “pruning,”. Ch. engchi. meaning deleting posts and un-tagging themselves to management their privacy on the social networking site. According to the Communications Privacy Management (CPM) theory proposed by Sandra Petronio (2002), privacy is essentially managed through establishing a set of rules, in which an individual or collective have the right to protect their privacy via thin or thick boundaries. The rules, or boundary may also be disturbed in the presence of boundary turbulence (such as the violation of the established rule.) In brief, boundary turbulence referred to something that disrupted the coordination of privacy rules or when the privacy boundary was violated. It could then cause the decrease in trust, and elicit anger and. 5.
(14) uncertainty for users to share private information. In the presence of boundary turbulence, the individual or collective would take actions to restore the boundary coordination (Liu, et al., 2014). Essentially, CPM detailed the process of boundary development, boundary coordination and reaction to boundary turbulence (Altman, 1975; Derlega & Chaikin, 1977; Stutzman & Kramer-Duffield, 2010). While previous studies indicated that factors such as users’ attitudes toward privacy protection (Christofides et al., 2009), awareness of privacy protection (Dey et al., 2012), privacy concerns (Acquisti & Gross, 2006; Stutzman & Kramer-Duffield, 2010; Tufekci,. 政 治 大 privacy violation (Krasnova et al., 2009) will influence users privacy management, this thesis 立 2008), perceived risks and trust (Fogel & Nehmad, 2009), and perceived likelihood of a. included users’ years of using Facebook, average hours per day spent on Facebook and. ‧ 國. 學. previous negative experience on Facebook as additional independent variables.. ‧. By utilizing the theory, this study looked at Taiwanese users’ privacy management on. sit. y. Nat. Facebook via privacy settings on users’ profiles and privacy protection strategies on. io. er. Facebook. Therefore, this thesis investigated into demographics, years of using Facebook, average hours per day spent on Facebook, privacy settings on your Facebook profile page,. n. al. personal privacy orientation,. v i n C h toward Facebook’s knowledge engchi U. privacy settings, privacy. concerns, negative experience on Facebook and privacy protection strategies. In addition, this thesis attempted to see how the variables predicted user’s privacy management in terms of privacy settings on users’ profiles and privacy protection strategies.. 1.3 Chapter organization The chapters were organized as the following. For chapter one, this thesis began with an introduction to the background of study, and a brief overview of the Facebook users abroad and in Taiwan. Then, it moved on to the purpose of research as well as an overall description on the chapters. In chapter two, this thesis covered literature review in the following aspects. 6.
(15) Firstly, it covered relevant literature on nature of social networking sites and the privacy paradox phenomenon. Then, the definition of privacy suitable for the online environment was discussed. The literature also looked at the theoretical framework of this thesis, namely the Communications Privacy Management (CPM) proposed by Sandra Petronio (2002) as the ground of this study. The literature review also covered previous research on users’ privacy management on Facebook. Chapter three covered the methodology for this thesis, in which an online survey questionnaire was used to collect data from Facebook users in Taiwan. This section covered the survey questionnaire design, measurement, sampling plan and statistical. 政 治 大 Chapter four covered the development of Facebook in Taiwan and its privacy policy 立. method for analysis.. evolvement. As for chapter five, the section included both descriptive and statistical analyses.. ‧ 國. 學. The section utilized correlation and linear hierarchical regression analyses to report major. ‧. findings from the data collected. More specifically, this section illustrated how users’. y. Nat. demographics, personal privacy orientation, years of using Facebook and average hours per. er. io. sit. day spent on Facebook, knowledge toward Facebook’s privacy policy, negative experiences on Facebook, privacy concerns correlated and associated with users’ profile privacy settings. al. n. v i n C h six covered theUdiscussion of the results and further and privacy protection strategies. Chapter engchi. implications to the current research pool. Lastly, conclusion, limitation to the study and suggestions for further research were covered in chapter seven.. 7.
(16) CHAPTER TWO: LITERATURE REVIEW Boyd & Ellison (2007, p. 211) has defined social networking sites as web-based services in which individuals were allowed to (1) construct a public or semi-public profile within a bounded system, (2) articulate a list of other users with whom they share a connection, and (3) view and traverse their list of connections and those made by others within the system. Essentially, Facebook is a social networking site that fit the criteria above. Not only that, it is also an array with more than 1 billion of users actively participating on the platform. Therefore, Facebook has become a setting for researchers to observe naturalistic behavior,. 政 治 大 as a subject of study, researchers may accumulate more observable data. In addition, the great 立 test hypotheses and recruit participants for various disciplines of research. By using Facebook. prevalence of Facebook has granted its own right to be a matter worthy of the attention.. ‧ 國. 學. Lastly, with the increasing popularity and dominance of social networking sites, studying. ‧. Facebook may offer insights into the benefits and dangers they may us (Wilson et al., 2012).. sit. y. Nat. io. er. 2.1 Nature of social networking sites and privacy paradox phenomenon First of all, the underlying structure of operation for a social networking site appeared to. al. n. v i n C hnetworking site emphasized be paradoxical in nature. Since a social much on user-generated engchi U content (UGC), the site intentionally kept its security and access controls weak to encourage more information exchange and social interactions. In brief, the main purpose of weak privacy control was to encourage social exchange and to increase popularity of the social networking sites, which in return also made the sites more attractive to advertisers (Burke et al., 2009). However, over the years, users of online networking sites also became more and more concerned with their privacy online. In fact, there was evidence indicating the growing of privacy concern among users throughout the years 2005 to 2009. In 2005, a research showed that participants were oblivious to personal privacy risks on Facebook, given the fact that out 8.
(17) of those 4,000 participating students, 50% of participates provided their home addresses and 40% provided their phone numbers on the social networking sites (Gross & Acquisti, 2005). But in 2007, there were contrasting findings that that only 10% out of 205 participants provided their home addresses (Fogel & Nehmad, 2009). Aside from the decrease in displaying home addresses, users were also showing proof of altering their privacy settings from open visibility to other options. In 2008, in a study with 1,740 students, an entire third of students had changed their privacy default setting to a more restrictive one (Lewis et al. 2008). These findings suggested that the awareness of privacy and security issues had. 政 治 大 Meanwhile, with the presence of increasingly evident privacy concerns, privacy paradox 立. increased over the years (Dey et al. 2012).. still existed among Facebook users. According to Metzger & Pure (2009), privacy paradox. ‧ 國. 學. referred to the situation when users’ high level of privacy concerns failed to match their low. ‧. level of privacy self-protection behavior. Metzger & Pure (2009) further reinforced in their. sit. y. Nat. study that while privacy issues were of users’ concerns, the tension between users’ desire to. io. er. protect their privacy and the need for social connection must be taken into consideration as well. Studies showed that users claimed to be aware of privacy issues, yet they continued to. al. n. v i n upload or share lots of personal C information (AcquistiU& Gross, 2006; Lee et al. 2008; hengchi. Debatin et al. 2009; Stutzman & Kramer-Duffield, 2010). As suggested by numerous researchers, the risks exposed to users with low privacy control could lead to unintentional disclosure of personal information, damaged reputation due to rumors and gossip, unwanted contact and harassment, vulnerability to stalkers or pedophiles, use of private data by a third party, hacking, and identity theft (Boyd, 2008; Taraszow et al. 2010; Debatin et al. 2009; Wilson et al., 2012). As a result, users had to weigh both risks and benefits of disclosing privacy information. As Acquisti & Gross (2006, p. 37) expressed, the emergence of a social networking site like Facebook had led to “unprecedented phenomenon of information revelation.” In simple terms, the nature of social networking sites intensified the privacy 9.
(18) paradox, also known as the information disclosure and privacy dilemma among users (Wilson et al., 2012).. 2.2 Definition of privacy According to a survey on Internet users from the website msnbc.com in 2006, privacy meant various things from fear of being watched, fear of government intrusion, worriess over companies tracking purchases, and advanced technology such as the ability for GPS to track their physical movements. Among the numerous responses, the most common definition of. 政 治 大 in 1890. As Sullivan (2011) suggested, the lack of clear definitions of privacy has caused 立 privacy was "the right to be left alone," originated from Samuel Warren and Louis Brandeis. much confusion in the discussion pertaining to this topic. In addition, privacy should be. ‧ 國. 學. considered in its context. The legal, classical definitions of privacy may be different from that. ‧. of the online environment. Therefore the following section sought to offer a review on. sit. y. Nat. privacy in order to define the term fittingly to the situation on a social networking site.. io. er. Privacy in the traditional perspective. In United States, four types of invasion to one’s privacy were commonly known. The. al. n. v i n C h false light, appropriation four torts included intrusion of solitude, and public disclosure of engchi U private facts that could lead to embarrassment. According to Prosser (1960), intrusion of. solitude referred to the physical or electronic intrusion into one's private quarters, whereas false light referred to the publication of facts which placed a person in defamation, even though the facts themselves may not be defamatory. Appropriation referred to the unauthorized use of a person's name or likeness to obtain benefits, whereas public disclosure of private facts meant the dissemination of truthful but private information, such as one’s illness. Oftentimes, the revelation of such private fact could lead to embarrassment on the subject. However, the legal perspective of privacy was not the fittest for the online environment. 10.
(19) In order to establish privacy in a different context than the legal perspective, Tavani (2007) stressed that when defining privacy, it must be considered whether privacy was interest-based, or right-based. By definition, the "interests-based" view of privacy referred to a person's desire or intention to have his information protected, and it was mostly for enhancing one's well-being (Tavani, 2007). In terms of the "right-based" view of privacy, it was defined as the utilitarian cost and benefit analysis, where individuals attempted to balance the cost to privacy and the benefits to public safety and crime control (DeCew, 1997, p. 21) As indicated by DeCew (1997), there was a shift to consider privacy in the right-based. 政 治 大 made explicit indication to one’s right to privacy. In Article 12, it was stated that 立. point of view rather than interest-based. The Universal Declaration of Human Rights also. [no] one shall be subjected to arbitrary interference with his privacy, family, home or. ‧ 國. 學. correspondence, nor to attacks upon his honor and reputation. Everyone has the right to. ‧. the protection of the law against such interference or attacks.. sit. y. Nat. According to Tavani (2007), privacy theories could be categorized into four types:. io. er. non-intrusion, seclusion, limitation and control. Though each of the categories brought insight to what privacy was, each of them also had shortcomings in the underlying definitions.. al. n. v i n C has “non-intrusion,”Uin which the definition originated For instance, privacy could be defined engchi. from what Warren & Louis (1890) suggested in their article titled “The Right to Privacy” in Harvard Law Review. According to the authors, privacy was “the right to be let alone” (p.193), or to be free from intrusion of any kind. However, Tavani (2007) found two flaws in this definition. Firstly, “the right to be let alone” sometimes confused the condition or content of privacy with the right to privacy. Furthermore, the non-intrusion theory was also confused with the notion of liberty. Though liberty and non-intrusion were closely related, liberty did not suggest the protection of ones’ rights, whereas non-intrusion did. As for the second type of privacy, seclusion, it referred to privacy as “being alone” (Tavani, 2007, p.6). But the problem again surfaced since some seclusion theories defined 11.
(20) privacy as being inaccessible at all by others, or voluntary and temporary withdrawal from the society. In other words, the seclusion theory of privacy suggested that the more seclusion, the more privacy the individual would enjoy. However, it could easily be confused with the notion of solitude. By all means, the first two types of privacy theories addressed privacy in its physical terms. Hence they were not valid for the privacy in an online environment. The third type of privacy was the control theory. Privacy was thus defined under the condition that “one [had] privacy if and only if one [had] control over information about himself” (Tavani, 2007, p. 7). It emphasized that one must also consider what kind of. 政 治 大 particular information. But the idea of control in terms of what kind of information to control, 立 information one could expect to control, and how much control one could have over that. or how much to control, could be confused with the notion of autonomy.. ‧ 國. 學. The fourth type of privacy was the limitation theory. In the theory of limitation, privacy. ‧. was referred to as the situation when access to one’s information was limited or restricted in a. sit. y. Nat. certain contexts. The merit of this theory was the recognition of “zones” or personal. io. er. boundaries set by individual to restrict or limit access to personal information by others. However, since limitations suggested that the less information others knew about one person,. al. n. v i n Cthis the more privacy the person enjoyed, could be confused with secrecy. Nonetheless, h enotion ngchi U Tavani (2007) found these views of privacy inadequate. According to Tavani (2007, p. 6), the concept of privacy [in U.S.A.] has evolved, initially being associated with intrusion (physical access), then being associated with concerns about interference (in decision making), and, more recently, being associated with concerns about the flow of personal information. In fact, out of the four types of privacy theories discussed above, none of them best suited the type of privacy online. Privacy in the online perspective As suggested by Tavani (2007), a definition of privacy that could be considered for the 12.
(21) online environment was the Restricted Access and Limited Control view of privacy. Under this concept, privacy should be right-based, under an individual’s limited control, and could be protected through restricted access by others. In essence, privacy should be right-based rather than interest-based. What it meant was that an individual would go through the utilitarian cost and benefit analysis in an attempt to balance the cost to privacy and the benefit to public safety and crime control. Privacy online was also under limited control since it was not realistic for an individual to have sole control over every digital footprint or information disclosed in an online environment. Moreover, privacy could be protected by restricted access.. 政 治 大 could restrict others from accessing such information through means of social strategies or 立. Though an individual did not have complete control over his own information online, he. structural strategies. For the purpose of this thesis, online privacy should be deemed as. ‧ 國. 學. right-based, under users’ limited control, and could be protected through restricted access.. ‧. “Right-based” referred to how an individual will analyze the cost and benefits for disclosing. sit. y. Nat. personal information, whereas limited control referred to how an individual did not have. io. er. complete control online; however, one could protect his online privacy through restricting others’ access to such information.. al. n. v i n C h of online privacy, definition Raynes-Goldie engchi U. Having established the. (2010) further. suggested that there were two kinds of online privacy. To be more specific, while users on Facebook cared about protecting their personal information, their concerns about privacy tended to reflect a desire to protect their social privacy rather than their institutional privacy. What it meant was that users were more concerned about controlling who had access to their personal information rather than how advertising companies would make use of their information. In more concrete terms, social privacy referred to users’ concerns about controlling access to personal data that was available to their social contacts. Users may want to keep certain information from some particular contacts among their Facebook friends. Such actions like deleting, editing content or removing tags were thus common measures that 13.
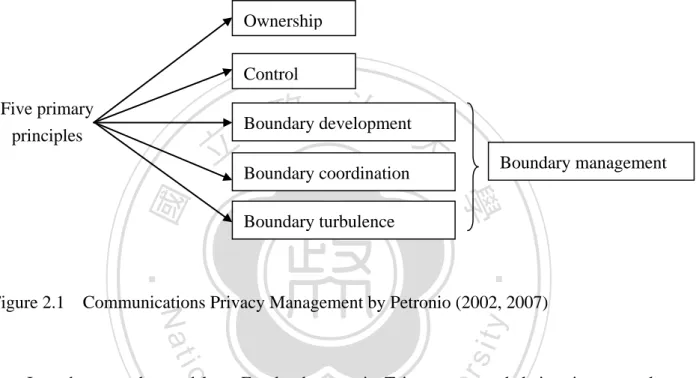
(22) may help to manage one’s social privacy. On the other hand, institutional privacy referred to how companies like Facebook Inc. and its partners and advertisers alike might use users’ personal data for benefits.. 2.3 Theoretical framework: Communications Privacy Management (CPM) Theory Communications Privacy Management (CPM) Theory proposed by Sandra Peteronio (2002) served as a framework to see how individuals or collectives managed their privacy in different situations. More importantly, its goal was “to offer a theoretical perspective that. 政 治 大 information” (Petronio, 2007, p. 218). Given the paradoxical nature of a social networking 立. [suggested] a way to understand the tension between revealing and concealing private. site like Facebook, CPM was a suitable theoretical framework that could be used to look into. ‧ 國. 學. users’ privacy management.. ‧. To begin with, Petronio (2002, p. 6) defined privacy as right-based “the feeling that one [had]. sit. y. Nat. the right to own private information, either personally or collectively.” In other words,. io. er. privacy was right-based. In addition, in order to achieve communication goals, people had to disclose certain private information in the process. The situation was even more so in an. al. n. v i n online environment such as onlineC networking sites. Basically, h e n g c h i U there are five principles for CPM. Firstly, individuals or collectives believed they had the ownership to their private information. Secondly, due to their ownership to the private information, they had the right to control it. In order to strike a balance between revealing and concealing information, the individuals or collectives would set up zones to decide the permissible information flow. CPM thus used the notion of “boundaries” as a metaphor to show the process of utilizing rules and managing one’s privacy. Thirdly, they used privacy rules to decide whether they would open the boundary to reveal information, or close the boundary to conceal information. This was known as the process of boundary development. Fourthly, when individuals or collectives decided to reveal information, the ones they shared the information with were 14.
(23) presumed as co-owners of that information. These co-owners would therefore follow the preexisting rules or negotiate a set of new rules, known as boundary coordination. Lastly, there was a chance that individuals and collectives would encounter boundary turbulence, characterized as a violation to the rules or disruption to the boundary coordination (Petronio, 2007, p.219). The five principles of CPM are illustrated as the following. (Figure 2.1). Ownership Control. 政 治 大. Five primary principles. Boundary development. Boundary turbulence. Boundary management. 學. ‧ 國. 立 Boundary coordination. ‧. er. io. sit. y. Nat. Figure 2.1 Communications Privacy Management by Petronio (2002, 2007). In order to understand how Facebook users in Taiwan managed their privacy on the. al. n. v i n social networking site, this thesis C focused on the three U h e n g c h i latter principles of CPM: boundary development, boundary coordination and boundary turbulence. Altogether, these three tenets. composed the boundary management process. For boundary development, there were some decision criteria that could have an impact on how individuals establish their rules. For instance, gender difference (Stutzman & Kramer-Duffield, 2010), age difference (Madden, 2012), cultural norms (Hsu, 2004), and the risk-benefit ratio for revealing and concealing private information (Krasnova et al., 2009; McKnight et al., 2011) would account for how individuals developed their boundaries to manage privacy. Previous studies have found that gender was indeed a factor that would influence how the individuals set their rules for privacy. To be more specific, females tended to disclose less 15.
(24) personal information when compared to males (Stutzman & Kramer-Duffield, 2010; Stutzman et al., 2011; Madden, 2012), female and younger users were also more likely to remove friends on Facebook (Madden, 2012). As for cultural norms, Hsu (2004) found out that Taiwanese and Chinese users tended to be more worried about improper data sharing and usage, whereas participants from the Netherlands and the U.S. were less concerned. For the risk-benefit ratio, the privacy calculus model was used by various researchers to determine the trade-off between costs and benefits for people in regard to whether or not to disclose personal information. In the privacy calculus model, it assumed that people could. 政 治 大 (Dinev & Hart, 2006). Krasnova et al. (2009) depicted that both perceived concerns and 立. have strong beliefs regarding the costs and benefits in information disclosure at the same time. perceived benefits had significant influences on users’ decision regarding personal. ‧ 國. 學. information disclosure, in which perceived likelihood of damage had a stronger impact on. ‧. perceived concern than perceived damage itself. Meanwhile, Christofides et al. (2009) also. sit. y. Nat. suggested that privacy concerns and personal information disclosure may not be negatively. io. er. correlated since disclosure and control of private information on Facebook may not be as directly related to cost and benefits. Instead, it could be a whole different process, and could. al. n. v i n C h In addition, McKnight be related to the individual’s personality. et al. (2011) proposed a more engchi U elaborated privacy calculus model which included “costs” like privacy concern and. information sensitivity, and “benefits” like perceived usefulness and enjoyment to see how it affected users’ disclosure on personal information. Interestingly, the end results revealed that perceived usefulness and enjoyment did not positively influence information disclosure, while privacy concern did negatively influence information disclosure. In brief, the results of this study suggested that sometimes the reasons for personal information disclosure were not solely because of the fact that perceived benefits outweighed perceived privacy concerns. For boundary coordination, it was when an individual or a collective decided who to share the private information with. People used privacy rules to determine whether to open up 16.
(25) or close their boundaries. Once individuals or collectives chose to reveal their private information, others became co-owners of that private information. In the context of Facebook, boundary coordination on Facebook could be executed via privacy setting control and privacy protection strategies. First of all, privacy setting control offered by the social networking site was only useful to provide users with a base point and a psychological sense of security (Liu et al., 2014). However, since one of the main motivations for users to use social media was to engage in social interactions with others, inevitably users would be disclosing personal and private information with others (Christofides et al., 2009). Therefore, aside from making use. 政 治 大 un-tagging undesirable content. of the privacy settings, users were also found to utilize protection strategies such as social “pruning,” namely deleting and. 立. about themselves, or. removing Facebook friends were also frequent actions taken by users in U.S.A. (Madden,. ‧ 國. 學. 2012).. ‧. However, the world was not a perfect place and rules could be broken, therefore there. y. Nat. was a possibility of boundary turbulence. Boundary turbulence referred to the dynamic. er. io. sit. process in managing one’s privacy, in which turbulence was characterized as something that disrupted the coordination of privacy rules or when the privacy boundary was violated. For. al. n. v i n C hto the times whenUan individual had his identity taken instance, boundary turbulence referred engchi. over online, or experienced negative social consequences online. Boundary turbulence could then cause the decrease in trust, anger and uncertainty for sharing private information (Petronio, 2002). When there was an occurrence of boundary turbulence, the owners and co-owners of the private information needed to take actions in order to return to the boundary back to its original coordination. To sum up, CPM encompassed three main tenets to examine the process in the rule-based management system and to look at the process of how privacy boundaries were set, managed and affected (Petronio, 2002). CPM was a theory detailing how people, either individuals or collectives believed they owned their private information. Since individuals 17.
(26) and collectives had the right to own their private information, they also had the right to control it. This was referred to as control and ownership of one’s privacy. Furthermore, in the boundary coordination process, there were also dialectical tensions, in which people, either individuals or collectives had to decide between how private or how open they wanted the boundaries to be when sharing private, personal information with others (West & Turner, 2007). Nonetheless, with the occurrence of boundary turbulence, or when the preexisting rule was disturbed, the individuals or collectives would try to renegotiate new rules for the boundaries to bring back the original order.. 政 治 大 one’s privacy entirely, but only to a certain degree. Moreover, privacy management was not a 立 According to Petronio (2002), disclosing personal information did not mean giving up. purely individual process since people needed to coordinate collectively-owned boundaries.. ‧ 國. 學. In addition, though Facebook users may not have the absolute control over their privacy, they. ‧. did have the choice, consent and power of correction to limit disclosure of information. As. y. Nat. Tavani (2007) stated, individuals were entitled to privacy when they were “protected from. storage of information in an online, computer environment.. al. er. io. sit. intrusion, interference and information access by others” (p. 10) in regards to activities and. n. v i n Unlike the legal and classical C views of privacy, from h e n g c h i Uwhich a person’s right to privacy. was defined by absolute and stable boundaries separating the “private” from the “public,”. privacy defined in CPM was a highly dynamic and situational process through which people maintained social distance with other individuals (Rotenberg & Solove, 2003; Liu et al., 2014). Since the introduction of CPM was a framework to understand how individuals managed their privacy, it had also been applied to many different situations. According to Hesse & Rauscher (2013), studies investigating privacy in the disclosure process using CPM had increased throughout the communication discipline and expanded to the online environment as well.. 18.
(27) 2.4. Previous research on users’ privacy management on Facebook Due to its great number of audience, Facebook had become a subject of interests in. many fields. In a comprehensive literature search by Wilson et al. (2012), 412 journal articles regarding Facebook were reviewed. Among them, five categories of research were identified as the following: descriptive analysis of users, motivations for using Facebook, identity presentation, the role of Facebook in social interactions, and privacy and information disclosure. Among them, the literature on privacy and information disclosure only accounted for 18% of the articles collected. For the purpose of this study, the following section would. 政 治 大 According to the current policy on Facebook, the only information necessary to sign up 立. review previous research on users’ privacy management on Facebook.. for a Facebook account would be the users’ name, gender and email address. Other than that,. ‧ 國. 學. users had the liberty to choose whether or not to provide additional information. On users’. ‧. profiles, there were many pieces of information that can be showcased. For instance, users. sit. y. Nat. could disclose contact information, educational backgrounds, family and interpersonal. io. er. relationships, as well as their interests and the content they posted. Basically, users were given the options to choose either to share their information with the public, with friends,. al. n. v i n with friends but not acquaintancesC or just to themselves. h e n g c h i UAs one can see, users could also choose not to provide the information at all, in which it would be the most private option available right now. In addition to the privacy settings, research has also found that users would employ privacy protection strategies through removing, deleting and un-tagging unwanted content about themselves (Madden & Smith, 2010; Madden, 2012). In terms of predicting Facebook users’ boundary management on Facebook, results from previous research showed that different uses of social media (such as social interaction, social browsing, and entertainment) could be an influence to how an individual manage his privacy online. In addition, users’ personalities as well as privacy literacy and concern about privacy also showed significant influences (Liu et al., 2014). In fact, a number of empirical studies 19.
(28) had indicated that there were several factors that would influence users’ privacy settings on Facebook. For instance, gender (Stutzman & Kramer-Duffield, 2010), users’ attitudes toward privacy protection (Christofides et al., 2009), awareness of privacy protection (Dey et al., 2012), privacy concerns (Acquisti & Gross, 2006; Stutzman & Kramer-Duffield, 2010; Tufekci, 2008), and perceived likelihood of a privacy violation (Krasnova, Kolesnikova, & Guenther, 2009). Keeping that in mind, this thesis would look at how different factors in boundary development, boundary coordination and boundary turbulence would predict users’ privacy management.. 政 治 大 decision criteria for revealing or concealing private information. In terms of users’ boundary 立 According to West & Turner (2007), boundary development was guided by people's. management on Facebook, Stutzman & Kramer-Duffield (2010) identified in their study a. ‧ 國. 學. range of factors associated with privacy behavior on Facebook. Particularly, they found that. ‧. gender, network size, weak tie expectance violations and increasing levels of interpersonal. y. Nat. privacy practices were associated with having a friends-only Facebook profile. Among them,. er. io. sit. gender difference was proven to be a factor in users’ privacy practice. Stutzman et al. (2011) also found that male tended to disclose more than female. More recently, according to the. al. n. v i n C h control on social latest research by PEW Internet, privacy networking sites was prevalent. engchi U. Madden (2012) wrote that whilst a majority (58%) of social network site users restricted access to their profiles, women were significantly more likely to choose private settings than public. Women who maintained social media profiles were also more likely than men to keep their profiles private. In addition, two-thirds of online adults had a profile on a social networking site, while most of them restricted the access of those profiles to friends only. Moreover, Dey et al. (2012) found that there was a gender difference in how private users were. Therefore, this study proposed the first set of hypotheses in regard to gender as the following: H1a: Female Taiwanese users are more likely to have stricter profile settings than male. 20.
(29) H1b: Female Taiwanese users will use privacy protection strategies more frequently than male. In addition to the gender difference, Madden & Smith (2010) also found that users between 18-29 years of age were more likely to actively restrict access to the information they shared. They were more likely to change their privacy settings, delete unwanted comments or remove their names from photos when compared to other age groups. Another study also found that young and middle aged people tended to be more private than older users (Dey et al., 2012). It was apparent that demographics such as gender and age may be. 政 治 大 This thesis thus proposed the second set of hypotheses in regard to age as the following: 立. underlying factors that contributed to how individuals managed their privacy on Facebook.. H2a: The younger the users are, the stricter the profile privacy settings.. ‧ 國. 學. H2b: The younger the users are, the more frequently they will use privacy protection. ‧. strategies.. sit. y. Nat. On the other hand, the amount of time users spent on Facebook may contribute to the. io. er. data they provided to the social networking site (Debatin et al., 2009; Madden & Smith, 2010). In a study conducted by Stutzman et al. (2012), it was conveyed that Facebook users. al. n. v i n in their survey data sets did exhibitCincreasingly privacy-seeking behavior. However, policy hengchi U. and interface changes by Facebook could also alter the outcome and countered the privacy-seeking behavior. Anyhow, over time, the amount and scope of personal information that Facebook users revealed to their friends did increase. Users’ years of using Facebook and average hours per day spent on Facebook may also be an influence to how they coordinated their boundary. Therefore, this thesis proposed the fourth set of hypotheses as the following, H3a: The more time the users spend on Facebook, the stricter the profile privacy settings. H3b: The more time the users spend on Facebook, the more frequently they will use privacy protection strategies. 21.
(30) While Petronio (2002, 2007) had established that privacy management was a rule-based system, there were many factors that may influence one’s decision in terms of boundaries were coordinated. As Hesse & Rauscher (2013) pointed out, individuals’ personal privacy orientations were also believed to play a role in determining users’ privacy tendencies, namely the revealing and concealing of personal information in an online environment. Having considered the research framework of this thesis, in which users in Taiwan would be the main subject of interests, the third set of hypotheses were as the following, H4a: The more privacy-oriented the users are, the stricter the profile privacy settings.. 政 治 大. H4b: The more privacy-oriented the users are, the more frequently they will use privacy protection strategies.. 立. Meanwhile, users’ knowledge toward the privacy policy on Facebook may also play a. ‧ 國. 學. role in determining users’ privacy management. Butler et al. (2011) suggested from their. ‧. research that it also required adequate knowledge regarding Facebook’s privacy policy as. sit. y. Nat. well as how Facebook utilized the user information in order to know how to manage the. io. er. boundary accordingly. Furthermore, according to Ou (2011), it was important to look at how users actually understood the current privacy policy in order to determine how it may affect. al. n. v i n users’ decisions to carry out privacyCmanagement. Therefore, h e n g c h i U the thesis proposed the fifth set of hypotheses as the following,. H5a: The more knowledgeable the users are toward Facebook’s privacy policy, the stricter the profile privacy settings. H5b: The more knowledgeable the users are toward Facebook’s privacy policy, the more frequently they will use privacy protection strategies. Having considered the CPM theory proposed by Petronio (2002, 2007), boundary turbulence such as the disruption or violation of one’s privacy could result in the decrease in the individuals’ trust in disclosing privacy information. In fact, Madden (2012) suggested that while users could manage the content that others posted about them, around 11% of social 22.
(31) networking site users posted content they regretted What that meant was that one in ten profile owners actually voiced regrets about their own posts. Negative experience associated with Facebook such as having their accounts taken over could be perceived as boundary turbulence since it disrupted the original order in the boundary. Young & Quan-Hasse (2013) also found that negative social consequences would lead to users’ change in their privacy management. Therefore, this thesis proposed sixth set of hypotheses below. H6a: The more negative experiences the users have on Facebook, the stricter the profile privacy settings.. 政 治 大 they will use privacy protection strategies. 立. H6b: The more negative experiences the users have on Facebook, the more frequently. Stutzman et al. (2011) investigated into factors mediating disclosure in social network. ‧ 國. 學. sites. In their study, they found that people who had greater concern about privacy would. ‧. disclose less information on Facebook. Hence there was a negative relationship between. sit. y. Nat. concerns with privacy and disclosure of information. Secondly, people who had greater. io. er. concern about privacy would be more likely to engage in privacy protecting behaviors by changing default setting or customizing which friends could see the content. Therefore, the. n. al. i n C h as the following, study proposed the seventh set of hypotheses engchi U. v. H7a: The more privacy concerns the users have on Facebook, the stricter the profile. privacy settings. H7b: The more privacy concerns the users have on Facebook, the more frequently they will use privacy protection strategies. As detailed before, users’ privacy management was composed of boundary development, boundary coordination and boundary turbulence. As an outcome, users could choose to manage their privacy through profile privacy settings and privacy protection strategies. In an online survey questionnaire to 119 college students from a Midwestern university in the U.S.A., Debatin et al. (2009) found that most users tended to decrease profile visibility 23.
(32) through restricting access to friends in order to protect their privacy. Though this was the most common strategy for privacy management at the time, the researchers also suggested that it was a very weak mechanism since it was “a quick fix rather than a systematic approach to protecting privacy” (p. 103). The survey findings also indicated that while the majority of Facebook users reported having an knowledge toward privacy settings and make use of their privacy settings, users they may have a skewed sense of what that exactly entails. Most users were not aware of the fact that restricting access to their data did not mean they are well-protected (Debatin et al., 2009; Madden & Smith, 2010).. 政 治 大 previous research indicated how users were protecting their privacy online. According to 立 With the growing concerns over user’s privacy on social networking sites like Facebook,. Boyd (2008, p. 18), “most of the times users’ protection of privacy on Facebook [was] social,. ‧ 國. 學. not structural.” According to Raynes-Goldie (2010), social privacy was defined as the. ‧. control of information flow about how and when personal information was shared with other. sit. y. Nat. people, and access of personal identifiable information and user information by social. io. er. networking sites and other third parties as institutional privacy. Most studies found that users often chose to alter the privacy settings available to them to protect their privacy from social. al. n. v i n C h Gross, & Acquisti, contacts (Kramer-Duffield, 2010; Stutzman, 2012). Moreover, Madden engchi U (2012) summarized that it had become a norm for people to opt out of the default setting on. Facebook and used restricted access for most of their content. In addition, users’ privacy management also included “profile ‘pruning’”. Profile pruning referred to the deletion of unwanted content by users on their profiles as part of their reputation management. More recently, Young & Quan-Hasse (2013) described online privacy protection in terms of social strategies and structural strategies. They found that privacy protection strategies were used primarily to guard against social privacy threats and consisted of excluding contact information, using the limited profile option, un-tagging and removing photographs, and limiting Friendship requests from strangers. Apparently, these means of 24.
(33) privacy management mostly geared toward users’ social privacy, rather than institutional privacy. Therefore, this thesis also proposed the following research question, RQ 1: Are Taiwanese Facebook users more likely to mitigate social privacy concerns rather than institutional privacy concerns?. 立. 政 治 大. ‧. ‧ 國. 學. n. er. io. sit. y. Nat. al. Ch. engchi. 25. i n U. v.
(34) CHAPTER THREE: METHODOLOGY Given the prevalence of Facebook in Taiwan along with increasing privacy concerns proven evident in previous research, this thesis utilized Communication Privacy Management (CPM) Theory as the theoretical framework to see how Facebook users in Taiwan managed their privacy on this particular social networking site. Since Facebook was noted as a suitable place to observe naturalistic behavior, this thesis would also employ the survey technique to collect data from active Facebook users in Taiwan. According to Wimmer & Dominick (2011, p. 185), there were several advantages of survey research, detailed the following: (1) this. 政 治 大 could be generated with relative ease, (3) the cost for conducting survey research was 立 method was often used to investigate problems in realistic settings, (2) large amount of data. reasonable, having considered the amount of data collected, and (4) it was not limited by the. ‧ 國. 學. geographic constraint. Prior to the prevalence of Internet, survey research was often. ‧. conducted via telephone landlines or cellphones. However, it was much easier to conduct. sit. y. Nat. online survey nowadays. Since the topic of this thesis aimed at predicting users’ privacy. io. online survey approach was deemed reasonable.. al. er. management via profile privacy settings and privacy protection strategies on Facebook, an. n. v i n However, one main issue withC online survey was theU h e n g c h i low response rate due to the lack of. incentives for participants. To overcome the problem of incentivizing respondents, the study used an online survey to approach Facebook users via InsightXplorer, a marketing research. firm targeted at respondents in Taiwan. The survey questionnaire was distributed to active daily Facebook user in Taiwan, in which the respondents would receive points for monetary exchange provided by InsightXplorer. In the survey, respondents were inquired into their demographic information, years of using Facebook and average hours per day on Facebook, personal privacy orientation, negative experiences on Facebook, privacy concern and current settings on their profiles on Facebook. Also, the questionnaire contained questions regarding users’ privacy protection strategies. After the data collection, this thesis performed a 26.
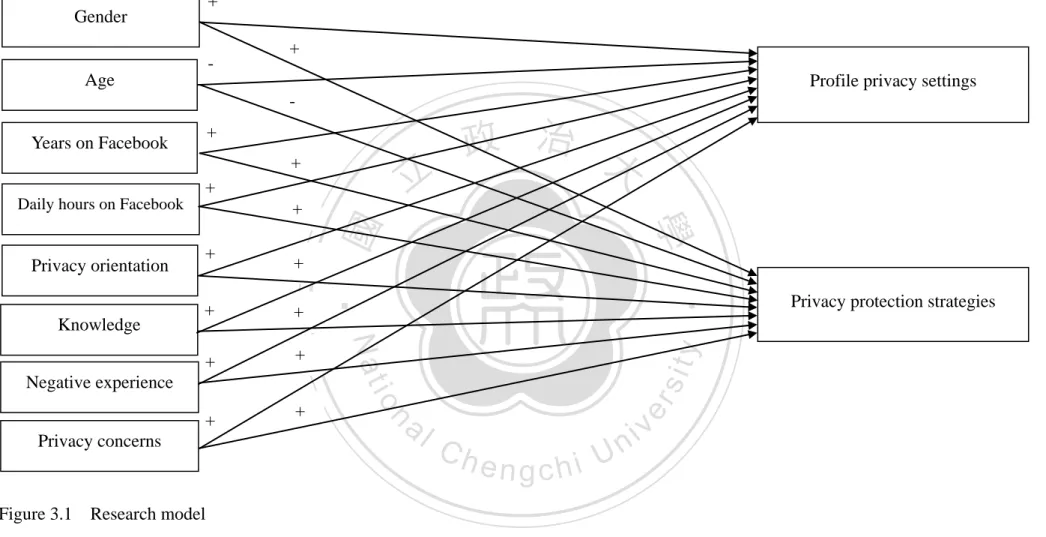
(35) hierarchical linear regression to see how different factors predicted users’ strictness of privacy settings on profiles and the frequency of using privacy protection strategies.. 3.1 Survey questionnaire design For the purpose of this study, an online survey questionnaire was devised after reviewing relative theoretical literature, as well as previous and current research relevant to users’ privacy management on Facebook. The survey was composed of seven dimensions, including (1) demographic information, (2) strictness of their privacy settings on profiles, (3) personal. 政 治 大 concerns, (6) negative experience on Facebook, and (7) frequency of using privacy protection 立 privacy orientation, (4) understanding toward Facebook’s privacy settings, (5) privacy. strategies. Under each dimension, questions were adapted from previous studies or. ‧ 國. 學. Facebook’s privacy policy on the settings. A pretest was administered via convenience. ‧. sampling, and to test for the reliability of the items. After the pretest, some items were deleted. sit. y. Nat. in order to yield better reliability prior to constructing the indices. In brief, the research. io. n. al. er. framework was illustrated as the following. (Figure 3.1). Ch. engchi. 27. i n U. v.
(36) +. Gender. -. +. Age. Profile privacy settings +. Years on Facebook. +. 立. + Daily hours on Facebook. +. Privacy concerns. +. al. n. +. io. Negative experience. y. +. sit. +. Nat. +. er. +. ‧ 國. +. ‧. Knowledge. +. 學. Privacy orientation. 政 治 大. Ch. engchi. Figure 3.1 Research model. 28. i n U. v. Privacy protection strategies.
(37) 3.2 Measurement While demographic information such as gender, age, educational level, employment status served as control variables in this study, the independent variables were measured by users’ years of using Facebook and average hours per day spent on Facebook, personal privacy orientation, knowledge toward Facebook’s privacy policy, privacy concerns and negative experiences on Facebook. Meanwhile, the dependent variables were users’ profile privacy settings and privacy protection strategies, namely the frequency of the measures they took to manage their privacy on Facebook. The measurement for the variables was detailed as. 政 治 大 Respondents’ demographic information included their gender, age (M=3.34; SD=1.26), 立. the following.. educational level (M=3.91; SD=0.63), and status of employment. Time spent on Facebook. ‧ 國. 學. included their years of using Facebook (M=4.71; SD=1.62) and average hours spent on. ‧. Facebook on a daily basis (M=3.06; SD=1.64).. sit. y. Nat. Personal privacy orientation (Cronbach’s alpha=0.81; M=16.09; SD=2.48) was. io. er. measured by four (4) items adapted from Marshall (1972). Users were asked to evaluate the following statements such as “I do not usually share personal information with my. al. n. v i n C hpersonal information acquaintances,” “I do not like sharing with others, unless they are my engchi U. close friends,” “I find my privacy on Facebook important” and “I find my privacy on Facebook important.” Respondents then answered the question based on a 5-point Likert scale, ranging from “1=strongly disagree” to “5=strongly agree.” Knowledge toward Facebook’s privacy policy (Cronbach’s alpha= 0.38; M= 1.23; SD=0.83) was measured by three (3) items, which were knowledge-type questions adapted from the current privacy policy on Facebook. Respondents were presented with specific questions on posts, timelines and account deletion, such as “[whenever] you post on Facebook, you can choose among three privacy settings: Sharing with the public, with friends or with a customized list,” “whenever you hide a post from your page, it is equivalent to 29.
(38) deleting the post,” and “whenever I delete my Facebook account, all of my records will be removed immediately.” Respondents would then choose whether or not the statements were correct. The items were dichotomous in nature, and the questions that were answered correctly would be recoded as “1,” whereas the ones mistaken would be coded as “0.” Negative experience (Cronbach’s alpha= 0.75; M= 0.13; SD=0.61) was measured by a total of eight (8) items, which are modified from the Madden (2012) on privacy management on social media sites. Participants were asked if they had any of the experiences such as “losing a job/ academic opportunity,” “threatened financially,” “threatened physically,” and. 政 治 大 what others posted or shared on my page.” In the questionnaire, respondents selected all that 立. “damaged their reputation” because of “what I posted or shared on my page” and “because of. apply to them. For the ones they selected, the items were recoded as “1.” For the ones they. ‧ 國. 學. did not select, they were recoded as “0.”. ‧. Privacy concerns on Facebook (Cronbach’s alpha=0.94; M=46.62; SD=7.86) was. sit. y. Nat. measured by twelve (12) items adapted from Krasnova, Kolesnikova & Guenther (2009) and. io. er. Mcknight, Lankton & Tripp (2011). Respondents were asked about how concerned they were regarding particular types of information they submitted on Facebook, such as the location. al. n. v i n and timestamp that they logged inCon Facebook. In addition, h e n g c h i U they were asked about how. concerned they were with the content (texts, photos and videos) either they posted or others posted on the respondents’ profiles, which could be misused or used by third parties without the respondents’ consent. Statements included “the location I am at when I use Facebook is known by others,” “the timestamp of my Facebook activities are known by others,” “I cannot control what others post about me on Facebook,” “others finding my personal information on Facebook,” “the texts other posted on my wall being misappropriated by the third party,” “the photos other posted on my wall being misappropriated by the third party,” “the videos other posted on my wall being misappropriated by the third party,” “the texts I posted on my wall being misappropriated by others,” “the photos I posted on my wall being misappropriated by 30.
(39) others,” “the videos I posted on my wall being misappropriated by others,” “Facebook may share my personal information with advertisers,” and “Facebook may share my user information (such as which pages I browse) with advertisers.” Based on the statements, the respondents would then choose a response from a 5-point Likert scale ranging from “1=not concerned at all” to “5=very concerned.” Privacy settings on their profiles (Cronbach’s alpha=0.93; M=59.14; SD=20.32) were measured by twenty (20) items. Respondents were inquired regarding the privacy setting on their profiles, including work information, education information, with whom respondents. 政 治 大 year, relationship status, blood type, interests, religious views, political views, mobile phone 立 were in a relationship with, family relationship, places respondents had lived, birth date, birth. number, address, photos respondents uploaded, videos respondents uploaded, tags, music. ‧ 國. 學. they liked, movies they liked and notes they uploaded. Given the current privacy setting on. ‧. Facebook, respondents then selected their current settings to share the 20 items among. y. Nat. “1=public,” “2=friends,” “3=friends except acquaintances,” “4=only [themselves]” or. er. io. sit. “5=never provided that information on Facebook.” Also, the more private the settings, the stricter the setting since it meant the audience was more strictly monitored.. al. n. v i n C h(Cronbach’s alpha=0.86; strategies M=19.83; engchi U. Privacy protections. SD=6.23) were. measured by nine (9) items. The items were partially adapted from Madden (2012) on privacy management on social media sites. The items included the following such as “hid status updates from particular Facebook friends,” “deleted a Facebook friend,” “removed the name tags of yourself from a certain photos,” deleted posts on your page which were made by your Facebook friends,” “asked a Facebook friend to delete content about you,” “ignored or refused someone’s friend request on Facebook,” “selectively blocked someone on Facebook that are your family members or friends,” “turned off cookies on [their computers],” and “deleted [their] Facebook account.” The respondents then selected the ones that applied to them from a 5-point scale, where “1=never,” “2=seldom,” “3=sometimes, “4=usually” and 31.
數據

Outline
相關文件
First, when the premise variables in the fuzzy plant model are available, an H ∞ fuzzy dynamic output feedback controller, which uses the same premise variables as the T-S
The purposes of this research are to find the factors of raising pets and to study whether the gender, age, identity, marital status, children status, educational level and
This research uses 28 ITHs as the DMUs of DEA to assessment relative operating efficiency of model 1 (input variables are full time employees, cost of labor,
Through the enforcement of information security management, policies, and regulations, this study uses RBAC (Role-Based Access Control) as the model to focus on different
In order to partition the GPS market into different segments, this paper used purchase motives, product attributes and consumer lifestyle as the variables for market
Therefore, in this study, organizational justice was adopted as independent variable, leader-member relationship as mediator, extrinsic satisfaction as dependent
Based on the Technology Acceptance Model (TAM), the study was undertaken to understand whether the characteristics of social networking, which are defined as external variables
In different gender、time for study、time for cram、the parents education level and household income of junior high school students , some aspects of the academic stress were