Are Virtual Social Relationships independent
from Reality?
Yung-Chu Yeh
Jar-Der Luo
Graduate School of Social Informatics, Yuan-Ze University
Abstract
Following the thought of Wellman, we are trying to examine how social relationships within the cyber-community differ from those in the real world. For general internet users, we are also interested in whether their behavior of making friends on the internet is similar to that when off-line? In our findings, it would appear that a pair of friends has the same types of interactions when on the internet as those demonstrated in the real world. We also find that behind an on-line intimate tie with high interaction frequency, there exists a high probability of finding a person with a high degree of centrality within friendship networks in the real world. Our findings do not deny the possibility that there is a large group of "disembodied" internet users. But for an average user, life in cyberspace is not in large contrast to their real daily life.
Keywords:Social Networks, Cyberspace, Internet Relations, Cyber-Community.
I. The Theoretical Background
The newly emergent lifestyle on the internet has been under the spotlight of many academic researches, especially those topics pertaining to social communications and social relations in cyberspace (Poster 1995; Bayam 1995; Correll 1995). Some studies focus on how social interaction of this type impacts the real business process (Eccles and Nohria 1992), or how it influences group dynamics in meetings (Sproull and Kiesler 1994), so several comparisons between face-to-face and internet interactions have been made. Since the internet provides us with multi-mediated communications like those face-to-face interactions, it is believed that there has emerged a new form of community in cyberspace. Like communities in the real world, the cyberspace community can also satisfy human needs for emotional support derived from social interactions, and its scope extends beyond limited geographical boundaries (Rafaeli and Sudweeks 1996; Bromberg 1996; Rheingold 1994). Is this true? Emotional support has been heavily studied by sociologists since the early 70's (Cassel 1974; Cobb 1976; Dean & Lin 1977), and it is believed to be critical for human mental and physical health. Social interaction within personal relationship network provides the main component of emotional support. Can face-to-face interactions be replaced by cyberspace interactions in this regard? Some scholars have voiced their objections to this mode of thinking (Robins 1995). Some researches also found most deep and continuous social relations on the internet soon turned into genuine social ties (Park and Floyd 1996), and that cyberspace can be only treated as "third spaces" complimenting the real world (Beamish 1995).
Another important research topic forms around role-playing and self-identification on the internet. Since a role in cyberspace can be anonymous and a social situation on the internet can be totally unreal, people may play multiple roles in different internet realms, and their self-identification becomes fluid (Pile and Thrift 1995). Observing this
phenomenon, a group of scholars who asserted "disembodiment" suggested that a person, in escaping from reality, can disembody his own real role in order to experience a new life in cyberspace. Playing multiple roles and changing identities become a significant phenomenon in many case studies, especially those studies about internet an game MUD (Reid 1995; Turkle 1996). However, another group of scholars who asserted "embodiment" proposed their questions against this view. They believed that an individual's role on the internet more or less reflects his personality in real the world (Argyle and Shields 1996), and most internet users in cyber-communities are lurkers who do not actively play a role on the internet.
From computer-nuts to cyberpunks, a group of people who more or less addict themselves to using the internet is also the focus of sociological researches. They escape the vexes of the real world seek out the brave new world on the internet. "Cyberia" was structured as their homeland, and so a new culture in a new society was formed (Dery 1996; Rushkoff 1994). Similar research has also been done in Taiwan. Wang and Luo (1998) have done a comparison between those college students who are addicted to BBS and those who are not. They found that those addicted to BBS generally attempt to derive emotional support, self confidence, and even sexual satisfaction from this virtual world, and believed BBS to be more real than society itself. The cyber-society represents nothing less than reality for these addicts, and its culture is socializing them. This finding is similar to a study of their American net-dwelling counterparts done by psychologist Young. One focus of these studies was to determine whether internet addiction is a common phenomenon, or confined to a small group of internet users? To what extent is an individual's behavior influenced by "Cyberia", and to what extent are his social relations affected by internet interactions? This remains a large field awaiting further investigation.
Many studies pertaining to community formation, social support, multi-role playing, self-identification in cyberspace along with addiction to the internet have proposed the possibility of escaping from the real world. Internet users may re-establish their new life experiences in a totally different manner from those which may be possible in the natural surroundings. On the opposite end of views regarding these topics, there are also some scholars taking a different perspective--such as the above-mentioned "embodiment" argument. Regarding the example of social relations on and off line, Wellman (1993) thought that social ties on the internet are the extension of a real relationship network. Behind the computer network, there is a large social network entangled with real daily life. What people do on the internet reflects what they are doing in the real world. Which friends people choose in cyberspace indicate their preferences in daily social interactions. Following the thought of Wellman, we are trying to examine how social relationships within the cyber-community differ from those in the real world. For general internet users, we are also interested in whether their behavior of making friends on the internet is similar to that when off-line? We therefore put forth two propositions for investigation:
First, for a certain pair of friends, is the interaction contents the same whether on or off line?
Second, for a certain social relation on the internet, is the tie strength determined by the social activity of the person behind the tie in real life?
II. Research Strategy and Analytical Methods
1. Testing interaction contents on-line and off-lineNetwork theory and network analyses are proposed here for investigating these two propositions.
How can we categorize any given interaction contents? In studying organizational behavior, Krackhardt and Hanson (1993 ) analyzed the effects of social networks on various types of management behavior in many case studies, and categorized these social networks into three types--consultant, informational and trust networks. Different behavior outcomes then are relevant only to one or two of the three networks, for example, informal power and personal influence are generated from trust network (Krackhardt and Martin 1990). Knowledge exchange and information flows are relevant to the information network. Social ties used to be categorized into two types--strong and weak ties, emotional support being the key component in forming strong ties (Granovetter 1973; Marsden and Campbell 1984). In further studies of trust, many researchers pointed out that trust is mainly derived from stronger ties, rather than from arm-length, business relations (Uzzi 1996, 1997). Krackhardt also found that the trust network is highly correlated to the friendship network (Krackhardt and Porter 1985), and personal influence in informal power struggles can be vividly explained by friendship patterns (Krackhardt 1992). In the following, we therefore suggest a typology for three types of interaction contents--consulting homework, exchanging information, and developing friendship.
Granovetter once used four factors--that is, friendship duration, interaction frequency, intimacy, and service contents--to define tie strength (1973). In further studies of tie strength, intimacy was surveyed by asking several questions separately about high degree and low degree intimacy (Marsden and Campbell 1984). Following this categorization, we used two themes in investigating friendship networks--eating lunch together (or chatting on the internet) to indicate low intimate behavior, and talking privately to each other in order to indicate high-degree emotional support. Therefore, data from eight whole social networks was collected in the final analysis; they were consultant, information, lunch meeting and privacy-talk networks in the real world, as well as consulting
homework, exchanging information, chatting and talking privacy on the internet.
We then collected whole network data of the four social networks (Marsden 1989, 1990) so as to analyze interaction contents both on-line and off-line. To analyze network data, a logistic model is utilized as the following:
Y = α + γZ + ε
Y is the logit function of probability of no relation on the internet over probability of having relation. Y includes four variables—they are consulting homework, exchanging information, chatting and talking privacy on the internet separately. The analytical units are ties between certain pairs of persons.
Z, representing a 4-by-n matrix composed by the ties between any two persons. 0 indicates no relation between the two persons, and 1 indicates having relation. The measures are accounted for separately:
Having lunch-eating relation or not in the real world
Having consulting-homework relation or not in the real world Having information-exchanging relation or not in the real world Having privacy-talking relation or not in the real world
γ is a 4-by-1 vector composed of the four estimators of explanatory variables, and ε is a 1-by-n vector of random variables.
After running the above-stated logistic model, we use the estimated coefficients of the four explanatory variables to compute the probability of having relations on the internet due to having relations in the real world by the following equations:
1 .... 1 , log ⎟⎟= = − ⎠ ⎞ ⎜⎜ ⎝ ⎛ k j a P P j k j
K is motivational mode, the reference category. Pj is the probability of jth category. According to logistic model:
∑
= + = ⎟⎟ ⎠ ⎞ ⎜⎜ ⎝ ⎛ = n i i ji j k j j X p p a 1 log α ββji is the regression coefficient. Xi is the ith independent variable.
( )
∑
= = = → k i i j k j p constrain a p p 1 1 , exp( )
1 exp 1 1 1 = ⎟ ⎠ ⎞ ⎜ ⎝ ⎛ + →∑
− = k i i k a p( )
( )
( )
∑
∑
− = − = + = → + = → 1 1 1 1 exp 1 exp exp 1 1 k i i j j k i i k a a p a p2. Testing degree of social activity on-line and off-line
An individual's social activity can be measured along several dimensions. In this paper, we measure only the degree of activity in an individual's social life. What was the index used to measure how active an individual is in the real world? Since we had network data obtained from a closed community, centrality of a person within his community can be used to indicate his level of social activity (Wasserman and Faust 1994). Freeman (1979) compared two types of centrality--degree centrality and betweenness centrality Degree centrality was the number of social connections a person has, serving as a good index of their social prestige. Betweenness centrality indicated how important a person was as a medium of social resources (Burt 1992). Since our intent was to measure a person's social connections, we chose degree centrality for our purposes.
Does an active person in the real world develop active relations on the internet as well? How can we measure the tie strength of an internet relation? An ego-center network questionnaire was distributed among those who are in network data as stated above. Each of them was asked to list three to six of the most intimate contacts they had on the internet. We chose two of the four indicators of tie strength--intimacy and interaction
frequency--to measure the strength of a tie on the internet. At the same time, gender data of the person behind a tie, relationship origin and convenience in accessing the tie were also analyzed for controlling their effects on the ties that the person may develop.
The analytical method was to use a logistic model regressing the strength of an internet relation in the involvement degree of social activity of the person who develops the internet relation. We have used UCINET to compute the centrality of a person in the four social networks as the explanatory variables for the model. Gender, source of relationship of the person and media types used by the person were the controls. The logistic model is as follows:
Y = α + β1X1 + β2X2 + β3X3 + γZ + ε
Y is the logit function of probability of weak tie over probability of strong tie. Y, as a measurement of tie strength, is indicated by two variables: 1) degree of intimacy and 2) frequency of interaction. The questions concerning intimacy include chatting, discussing homework, seeking emotional support, and invitation for face-to-face meetings. The interaction contents for the later two represent a high degree of intimacy. There are three categories of frequency: low frequency is less than one contact on the internet per week, medium frequency is one to three times, and high frequency is more than three times a week.
The control variables are:
X1, representing the gender of the person behind the tie. X2, representing relationship origin for the tie’s source.
X3, representing the media types involved in the interaction,
indicating how convenience in accessing the tie.
Z, representing a 4-by-n matrix composed by the degree of activity
of the persons behind the ties.
The measures are accounted for separately:
Degree centrality of the consulting network in the real world Degree centrality of the information network in the real world Degree centrality of the privacy-talking network in the real world
γ
is a 4-by-1 vector composed of the four estimators of explanatoryvariables, and
ε
is a 1-by-n vector of random variables.Finally, by the same token, we also compute the probability of building strong ties on the internet due to active social participation in the real world.
3. Data Collection
The purpose of this paper is to understand the relationship between social ties in cyberspace and the real world for the common the internet user. Since we needed to collect network data, a group of internet users as a closed system was needed for our investigation. College classmates served well for our research purposes, since they all made use of the internet and a class can be treated as a closed system. We purportedly select two classes of sophomores, since students of this stature tend to be most active on campus. So the level of activity on campus is generally able to represent their social life. One class had 61 students and one had 55, so total, 116 students were surveyed. Totally 6630 ties are collected from the whole network of the two classes (60*61+54*55=6630).
A network questionnaire was distributed. The first line of the questionnaire was a name list of all students in the class, and the first column listed eight questions pertaining to the social networks of the classmates. The questions were asked separately as follows: 1) With whom do you eat lunch? 2) Whom do you discuss your private issues with in person? 3) With whom do you discuss homework in person? 4) Whom do you pass information about classmates to? The other four questions were the same, but replaced "face-to-face" with "on the internet", while the question regarding eating-lunch was substituted with
chatting on BBS. Each interviewee was asked to point out his connections in the name list of his classmates.
An ego-center network questionnaire as stated above was also distributed among these 116 students. Three to six of each student's most intimate ties on the internet were surveyed, since we were investigating the factors behind strong ties. We have used degree centrality of a person in his class to indicate the degree of his involvement in social activities, so those who had a very low degree of centrality in class but were active outside of class were the outliers. They were active, but the reaches of our data was not able to illustrate their degree of activity. To correct the distortion caused by these outliers, we have excluded them from our analysis. Fortunately, there was only one student whose friendships were all established off-campus and who also displayed low-degree centrality in his class. 396 ties on the internet were surveyed from the remaining 115 students, among which 15 ties had missing values, resulting in 383 ties being analyzed.
III. Analytical Results
1. Descriptive statistics of samples
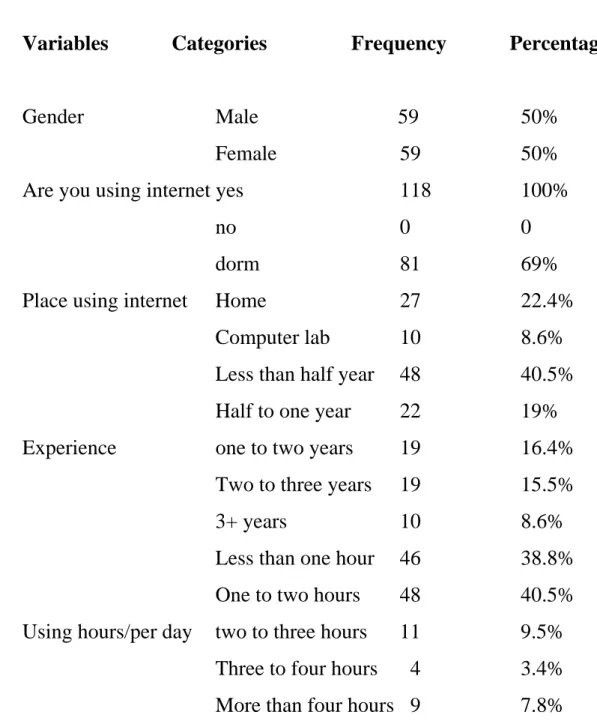
In our samples shown on Table 1, the male to female ratio was one to one. All students were found to make use of the internet, especially BBS, to chat. 40% had internet experience spanning back less than half a year, while 20% had less than one year's experience. That means 60% began their use of the internet in college. About 39% reported using the internet less than one hour a day, and another 49% from one three hours a day. There were 12% categorized as heavy users, the criteria for which required more than three hours of internet use per day.
Variables Categories Frequency Percentage(%)
Gender Male 59 50%
Female 59 50%
Are you using internet yes 118 100%
no 0 0
dorm 81 69%
Place using internet Home 27 22.4%
Computer lab 10 8.6%
Less than half year 48 40.5% Half to one year 22 19% Experience one to two years 19 16.4%
Two to three years 19 15.5%
3+ years 10 8.6%
Less than one hour 46 38.8% One to two hours 48 40.5% Using hours/per day two to three hours 11 9.5%
Three to four hours 4 3.4% More than four hours 9 7.8%
Table 1: Descriptive data of Samples
2. Association between interaction contents on and off line
In linking on and off-line behaviors, what friends in our sample did on the internet generally tended to reflect what they did in their day to day activities. From Table 2, those who discussed homework face-to-face with peers were also the persons who could be consulted regarding the same topics on the internet. Those who exchanged personal issues in daily talk were also the persons who tended to be able to share intimate
talk on the internet. The only exception was that established strong ties in the real world were fist required before the passing of information in cyberspace could occur. Those who exchanged information in daily talk may not have formed social connections on the internet.
Dependent Variable: Information Network on the internet Log{Pr(no relation on the internet)/Pr(having relation on the internet)}
Model Intercept 3.5318
Friendship Network (eat lunch together) -1.0490*** Friendship Network (Privacy talk) -0.8480***
Consulting Network -1.3124*** Information Network Observations(unit: ties) -1.2222*** 6630 * P<0.025 **P<0.005 ***P<0.000 (two-tailed test)
Table 2: Logistic Analysis of no relation/ having relation of Information-Exchanging on the Internet
From Table 2, we find that all the four kinds of relations in the real world impacts on information relations on the internet significantly. If there is no relation between a certain pair of persons in the real world, the probability of having relation of information-exchange on the internet is 2.8%. If there is friendship relation (eat lunch together), the probability increases to 7.7%. If there is privacy-talk relation, the probability increases to 6.3%. Consulting relation in the real world makes the probability 9.8%, and information-exchanging relation, 9%. If there are all four relations between two persons in real world, the probability that they exchange information on the internet will be as high as 71%.
Dependent Variable: Privacy-talk Network on the internet
Log{Pr(no relation on the internet)/Pr(having relation on the internet)}
Model Intercept 5.2563
Friendship Network (eat lunch together) 0.2236 Friendship Network (Privacy talk) -3.4364***
Consulting Network -0.7582 Information Network Observations(unit: ties) -1.2685*** 6630 * P<0.025 **P<0.005 ***P<0.000 (two-tailed test)
Table 3: Logistic Analysis of no relation/ having relation of Talking Privacy on the Internet
Table 3 shows that only friendship and information networks are significant explanatory variables. Without any relation in real world, the probability of two persons talking privacy on the internet is only 0.5%. Privacy talking in the real world sharply increases this number to 14%. On the contrary, information exchanging makes only mild change 1.8%, and the other two variables are not significant.
Dependent Variable: Chat Network on the internet
Log{Pr(no relation on the internet)/Pr(having relation on the internet)}
Model Intercept 3.6866
Friendship Network (eat lunch together) -1.2830*** Friendship Network (Privacy talk) -1.0509***
Consulting Network -1.0536***
Observations(unit: ties) 6630 * P<0.025 **P<0.005 ***P<0.000 (two-tailed test)
Table 4: Logistic Analysis of no relation/ having relation of Chatting on the Internet
From Table 4, we know that without any relation in the real world, two persons has only 2.4% chances to chat with each other on the internet. Eating lunch together makes the probability increase to 8.2%. Privacy talking is 6.6%, consulting homework, 6.7%, and information-exchanging, 12.3%. If the two persons have all the four relations in the real world, they may have the probability of chatting on the internet go extremely high, 80.6%.
Dependent Variable: Consulting Network on the internet
Log{Pr(no relation on the internet)/Pr(having relation on the internet)}
Model Intercept 5.0632
Friendship Network (eat lunch together) -0.4713 Friendship Network (Privacy talk) -0.9772**
Consulting Network -2.4731*** Information Network Observations(unit: ties) -0.9261*** 6630 * P<0.025 **P<0.005 ***P<0.000 (two-tailed test)
Table 5: Logistic Analysis of no relation/ having relation of Consulting on the Internet
If there are no relations between two persons in the real world, they have the probability of consulting on the internet as low as 0.6%. Only consulting relations in the real world make this number significant higher, that is 7%. The other two significant factors have only mild influence— 1.6% for privacy talk and 1.5% for information exchange.
For a connection in real world, what friends do on internet in general reflect what they are doing in daily life. Those who are discussed with homework face-to-face are also the persons who can be consulted on internet. Those who can exchange privacy in daily talk are also the persons who can share intimate talk on internet. The exceptions are information exchanging and chatting in cyberspace. Both of the two variables are impacted significantly by all the four predictors in the real world. In other words, information exchange and chatting in cyberspace require only weak ties, which can be built up by any social relation in the real world.
3. The factors behind an intimate tie on the internet1 Dependent Variable:
Log{Pr(low intimacy on the internet)/Pr(high intimacy on the internet)}
Model Intercept Gender 0.9141 0.7469** Relationship Source -0.2772 Interaction Media 0.0191
Emotional support network in the real world -0.1136** Consulting network in the real world -0.0854*** Information network in the real world 0.0429 Eat-lunch network in the real world
Observation (units: ties)
-0.0181 383 * P<0.1 **P<0.05 ***P<0.01 (two-tailed test)
Table 6: Logistic Analysis of low intimacy/high intimacy on the Internet
From Table 6, we established that gender was a significant factor. 0 indicates female, and 1 indicates male in our coding. Being male increased the probability of an internet connection being a weak tie. In other words, females liked to develop intimate ties on the internet, while males tended to keep only weak ties.
There were two real social networks that bore significant influence to intimacy on-line. High degree centrality in private-talk networks decreased the probability of an internet connection being a weak tie. The same was true of consulting networks. In other words, behind each
1
The definition of strong tie: Interaction contents include emotional support. The definition of weak tie: Interaction contents include chat and consulting homework.
intimate internet tie, there was a high probably of finding a socially active person involved in a real friendship and consulting networks.
4. The factors behind a tie with high interaction frequency2 Dependent Variables:
Model 1: Log{Pr(Low interaction frequency)/Pr(High interaction frequency)} Model 2: Log{Pr(Medium interaction frequency)/Pr(High interaction frequency)}
Model 1 Model 2 Intercept Gender 2.0543*** -0.9617* 0.7957 -0.2099 Relationship Source -0.4716 -0.2770 Interaction Media -0.0748 0.1146
Emotional support network in the real world
-0.2133*** -0.0365
Consulting network in the real world 0.0166 -0.0403 Information network in the real world 0.1123** 0.095** Eat-lunch network in the real world
Observation (units: ties)
0.1209 -0.0576 383 * P<0.1 **P<0.05 ***P<0.01 (two-tailed test)
Table 7: Logistic Analysis of Low Frequent/ High Frequent interactions on the Internet
From Table 7, we find that gender and degree centrality in privacy-talk networks are also significant factors behind internet ties with high interaction frequency in Model 1. Being female along with high degree centrality in privacy-talk networks increases the probability of a tie being
2
The definition of low frequency means less than one time/per week interaction on the internet, medium frequency means one-to-three times/per week interactions on the internet, and high frequency means more than three times/per week interactions on the internet.
transformed from low interaction frequency to high frequency. But in Model 2, the effects of these two factors appear to be no longer significant. The most interesting point is that degree centrality in the information network had a significant positive effect on both Model 1 and 2. That means, active persons in the information network increased the probability of a tie being transformed from high or medium frequency to low frequency. Information centers in the real world keep comparatively silent relationships with their internet friends. This finding is contrary to the general findings regarding the effects of social activity.
IV. Conclusions and Discussions
What can we conclude from these analytical results? For our first supposition, it would appear that a pair of friends has the same types of interactions when on the internet as those demonstrated in the real world. But weak friendship ties and information ties in the real world do not transfer back to cyberspace in the same manner. In our study, those who exchanged personal issues with each other not only shared these issues between themselves, but also passed other types of information on the internet.
As our second proposition, we find that behind an on-line intimate tie with high interaction frequency, there exists a high probability of finding a person with a high degree of centrality within friendship networks in the real world. It seems that a person active in his natural friendship networks also tends to develop active relations with net friends. For any particular individual, can his behavior pattern of social activity within the cyber-community be proven similar to that demonstrated in their real life? Our evidence cannot support the answer "no", but we are also not able to rush into a positive conclusion, either. We have measured only involvement of social activity rather than all dimensions of social activity, and so our samples do not have the capacity to represent all common internet users.
In order to clearly test this proposition, a wider range of data and measurement of more dimensions of individual social life are required.
For average internet users, our findings illustrate that an individual's deep involvement in internet relations generally reflects his or her tendency to develop active social networks in real life. However, one exception occurred in information networks in the real world. Our interpretation is that those information centers in a student's daily life tend to build up many weak ties for the purpose of catching flowing information, and that they carry this habit over to internet relations so that strong on-line ties are rarely established.
Our findings do not deny the possibility that there is a large group of "disembodied" internet users. But for an average user, social life in cyberspace is not in large contrast to their real daily life. This paper is far away from concluding the arguments between "disembodiment" and "embodiment" scholars, since we compare only a small part of human behaviors on and off line. The sampling scope and quantity were also insufficient to make strong inference of generalization. We must include more testable hypotheses and analytical methods in future research agenda, and unveil the secrets of internet user's behavior piece by piece. There remains a long road to travel before we may be able to vividly interpret the existing phenomenon within the expansive cyberspace world.
Reference
Argyle, K. and R. Shields.(1996). "Is There a Body in the Net?" In
Cultures of Internet: Virtual Spaces Real Histories and Living Bodies, edited by R. Shield, pp. 58-69. London: Sage.
Bayam, N. K.(1995). "From practice to culture on Usenet." In The
Cultures of Computing, edited by Star, pp. 29-52.
Beamish, A. (1995). Communities on-Line: Community-Based Computer
Network, MA thesis, MIT.
Bromberg, H. (1996). Are MUDs Communities? Identity, Belonging and Consciousness in Virtual Worlds. In Cultures of Internet: Virtual
Spaces, Real Histories and Living Bodies, edited by Shields, R, pp.
143-152. New York: Sage.
Burt, Ronald L. (1982). Toward a Structural Theory of Action. New York: Academic Press.
Correll, S. (1995). "The Ethnography of an Electronic Bar: the Lesbian Café." Journal of Contemporary Ethnography 24: 270-298.
Dery, M. (1996). Escape Velocity: Cyberculture at the End of Century. London: Hodder & Stoughton.
Freeman, L. C. (1979), Centrality in Social Networks: Conceptual Clarification, Social Network 1:215-239
Granovetter, Mark. (1973). “The Strength of Weak Tie.” American
Journal of Sociology 78: 1360-80
Krackhardt, David and Jeffrey R.Hanson .(1993). "Informal networks: The Company Behind the Chart." Harvard Business Review July-Aug:104-111.
Krackhardt, David and Martin Kilduff. (1990). "Friendship Patterns and culture: the control of organizational diversity." American
Wasserman Stanley and Katherine Faust. (1994). Social Network Analysis:
Methods and Applications. Cambridge: Cambridge University Press.
Marsden P. V. (1989). "Methods for the Characterization of Role Structures in Network Analysis." in Research Methods in Social
Network Analysis, Freeman. pp.489-530.Fairfax, VA:George Mason
University Press.
Marsden P. V. (1990). "Network Data and Measurement." Annual Review
of Sociology 6:79-141.
Masden, Peter and Karen Campbell. (1984) "Measuring Tie Strength."
Social Forces 63(2): 483-501.
Nohria, Nitin and Robert Eccles. (1992). "Face to Face: Making Network Organizations Work." In Network and Organizations, edited by Nohria and Eccles. Boston:Harvard Business School Press.
Park, M.R. and K. Floyd. (1996). "Making friends in cyberspace."
Journal of Computer-Mediated Communication 1(4).
Pile, S. and N. Thrift. (1995). Mapping the Subject: Geographies of
Cultural Transformation. London: Routledge.
Poster, M. (1995). The Second Media Age. Oxford: Polity Press.
Rafaeli, S. and F. Sudweeks. (1996). Networked Interactivity. Journal of
Computer-Mediated Communication.
Reid, E. (1995). Virtual Worlds: Culture and Imagination. In
Cybersociety: Computer Mediated Communication and Community,
edited by Jones, pp. 164-183, London: Sage.
Robins, K. (1995). "Cyberspace and the World We Live In." In
Cyberspace, Cyberbodies and Cyberpunk: Cultures of Technology
Embodiment, edited by M. Featherstone and R. Burrows. New York: Sage.
Rheingold, H. (1994). The Virtual Community: Surfing the Internet. London: Minerva.
Rushkoff, D. (1994). Cyberia: Life in the Trenches of Hyperspace. London: Flamingo.
Sproull, Lee and Sara Kiesler. (1994). Connections: New Ways of
Working in the Networked Organization. Cambridge: The MIT Press.
Turkle, Sherry. (1996). Life on the Screen: Identity in the Age of Internet. Translated by Tan, Taipei: Yuan-Lion Publishing Co.
Uzzi, Brian. (1996). “The Sources and Consequences of Embeddedness for the Economic Performance of Organizations” ASR 61: 674-698. Uzzi, Brian. (1997). “Social Structure and Competition in Interfirm
Networks: The Paradox of Embeddness” ASQ 42: 35-67.
Wang, Whi-Zan and Luo Hwi-Chun. (1998). "A survey on social communication on BBS in Taiwan". Newsletter for Research of
Applied Ethics。
Wasserman, Stanley and Katherine Faust, (1993). Social Network
Analysis: Methods and Applications. Cambridge University Press.
Wellman BS. (1996). An electronic group is virtually a social network. In
Research Milestones on the Information Highway, ed. S Kiesler.