無線行動裝置環境下的動態多媒體樣版之設計與製作
全文
(2) The Design and Implementation of Dynamic Web-Based Multimedia Templates for Empowering Users of Wireless Pervasive Computing Devices. 研究生: 馬志南 指導教授: 陳登吉教授. Student: Edouard Ma Poon Advisor: Dr. Deng-Jyi Chen. 國立交通大學 資訊工程研究所 碩士論文. A Thesis Submitted to Department of Computer Science and Information Engineering College of Electrical Engineering and Computer Science National Chiao Tung University In Partial Fulfillment of the Requirements For the Degree Master of Science In Computer Science and Information Engineering June 2004 Hsinchu, Taiwan, Republic of China. 中華民國九十三年六月 ii.
(3) 博碩士論文授權書 本授權書所授權之論文為本人在國立交通大學資訊工程研究所系所__組 93 學年度第 2 學期 取得碩士學位之論文。 論文名稱: The Design and Implementation of Dynamic Web-Based Multimedia Templates for Empowering Users of Wireless Pervasive Computing Devices 指導教授: 陳登吉教授 1. □同意 □不同意 本人具有著作財產權之上列論文全文(含摘要)資料,授予行政院國家科學委員會科學技術 資料中心(或改制後之機構),得不限地域、時間與次數以微縮、光碟或數位化等各種方式 重製後散布發行或上載網路。 本論文為本人向經濟部智慧財產局申請專利(未申請者本條款請不予理會)的附件之一,申 請文號為: _____________,註明文號者請將全文資料延後半年再公開。 2. □同意 □不同意 本人具有著作財產權之上列論文全文(含摘要)資料,授予教育部指定送繳之圖書館及國立 交通大學圖書館,基於推動讀者間「資源共享、互惠合作」之理念,與回饋社會及學術 研究之目的,教育部指定送繳之圖書館及國立交通大學圖書館得以紙本收錄、重製與利 用;於著作權法合理使用範圍內,不限地域與時間,讀者得進行閱覽或列印。 本論文為本人向經濟部智慧財產局申請專利(未申請者本條款請不予理會)的附件之一,申 請文號為: _____________,註明文號者請將全文資料延後半年再公開。 3. □同意 □不同意 本人具有著作財產權之上列論文全文(含摘要),授予國立交通大學與台灣聯合大學系統圖 書館,基於推動讀者間「資源共享、互惠合作」之理念,與回饋社會及學術研究之目的, 國立交通大學圖書館及台灣聯合大學系統圖書館得不限地域、時間與次數,以微縮、光 碟或其他各種數位化方式將上列論文重製,並得將數位化之上列論文及論文電子檔以上 載網路方式,於著作權法合理使用範圍內,讀者得進行線上檢索、閱覽、下載或列印。 論文全文上載網路公開之範圍及時間 – 本校及台灣聯合大學系統區域網路: 93 年 7 月 31 日公開 校外網際網路: 93 年 7 月 31 日公開 上述授權內容均無須訂立讓與及授權契約書。依本授權之發行權為非專屬性發行權利。依 本授權所為之收錄、重製、發行及學術研發利用均為無償。上述同意與不同意之欄位若未 鉤選,本人同意視同授權。 研究生簽名: 學號:9117615 日期:民國 93 年 7 月 15 日 本授權書請以黑筆撰寫並影印裝訂於書名頁之次頁。. iii.
(4) 國家圖書館博碩士論文電子檔案上網授權書 本授權書所授權之論文為本人在國立交通大學資訊工程研究所系所__組 93 學年度第 2 學期 取得碩士學位之論文。 論文名稱: The Design and Implementation of Dynamic Web-Based Multimedia Templates for Empowering Users of Wireless Pervasive Computing Devices 指導教授: 陳登吉教授 □同意 □不同意 本人具有著作財產權之上列論文全文(含摘要),以非專屬、無償授權國家圖書館,不限地域、 時間與次數,以微縮、光碟或其他各種數位化方式將上列論文重製,並得將數位化之上列 論文及論文電子檔以上載網路方式,提供讀者基於個人非營利性質之線上檢索、閱覽、下 載或列印。 上述授權內容均無須訂立讓與及授權契約書。依本授權之發行權為非專屬性發行權利。依 本授權所為之收錄、重製、發行及學術研發利用均為無償。上述同意與不同意之欄位若未 鉤選,本人同意視同授權。 研究生簽名: 學號:9117615 日期:民國 93 年 7 月 15 日 本授權書請以黑筆撰寫,並列印二份,其中一份影印裝訂於附錄三之一(博碩士論文授權書) 之次頁﹔另一份於辦理離校時繳交給系所助理,由圖書館彙總寄交國家圖書館。. iv.
(5) 國立交通大學. 論文口試委員會審定書 本校資訊工程研究所碩士班. 馬志南君. The Design and Implementation of Dynamic Web-Based Multimedia Templates for Empowering Users of Wireless Pervasive Computing Devices 合於碩士資格水準、業經本委員會評審認可。. 口試委員. 指導教授. 系主任. 中華民國九十三年七月十五日. v.
(6) The Design and Implementation of Dynamic Web-Based Multimedia Templates for Empowering Users of Wireless Pervasive Computing Devices. Student: Edouard Ma Poon. Advisor: Dr. Deng-Jyi Chen. Department of Computer Science and Information Engineering National Chiao Tung University. ABSTRACT. In this study, we present an approach to reach and augment users of pervasive computing devices to create powerful multimedia presentations using dynamic web-based multimedia templates (DWMT). In a pervasive computing environment, templates provide flexibility for mobile users with little time and resources at their disposal by assisting them when creating such presentations. We designed and implemented a traffic incident system (MobileCampus) that effectively demonstrates the practicability of DWMT and extends the use of these templates beyond the desktop PC to reach users of pervasive computing devices. We note that while several applications for pervasive computing devices have been implemented and deployed, a successful application should also identify specific challenges in a computing environment that contributes towards the vision of pervasive computing and enhances the user experience. In our approach, we take an application-centric viewpoint of these challenges, as well as the characteristics of the mobile user and device limitations into account when designing our system.. vi.
(7) ACKNOWLEDGEMENTS. I would like to extend my appreciation and thanks to the following people, for without whom; this research thesis would not have been possible:. First and foremost, to my advisor, Professor Deng-Jyi Chen, for his continuous encouragement, insight, guidance, support and invaluable contribution throughout this research project. Thank you for helping me achieve goals that were beyond the scope of expectations.. My family, for providing me with the opportunity to undertake my studies at National Chiao Tung University. They have provided me with endless support and opportunity to reach new heights.. Lastly, my friends. I am indebted to them for their understanding, encouragement and patience.. I acknowledge that all references are accurately recorded and that, unless otherwise stated, all work contained herein is my own.. Edouard Ma Poon. vii.
(8) TABLE OF CONTENTS. ABSTRACT........................................................................................................................................vi ACKNOWLEDGEMENTS ...............................................................................................................vii TABLE OF CONTENTS ..................................................................................................................viii LIST OF FIGURES ............................................................................................................................xi LIST OF TABLES ............................................................................................................................xiii CHAPTER ONE ..................................................................................................................................1 Introduction..........................................................................................................................................1 1.1. The Mobile Opportunity ..................................................................................................1. 1.2. Motivation........................................................................................................................3. 1.3. 1.4. 1.2.1. Challenges for Pervasive Computing and Mobile Users .....................................3. 1.2.2. Dynamic Web-Based Multimedia Templates (DWMT) ......................................5. 1.2.3. Features of a Successful Pervasive Computing Application................................6. The Problem and it’s Setting............................................................................................7 1.3.1. The Statement of the Problem..............................................................................7. 1.3.2. The Statement of the Sub- Problems....................................................................7. The Scope of the Research...............................................................................................8 1.4.1. Delimitations........................................................................................................8. 1.4.2. Assumptions.........................................................................................................8. 1.5. Research Methodology ....................................................................................................9. 1.6. Thesis Organization .......................................................................................................10. CHAPTER TWO ............................................................................................................................... 11 Challenges for Pervasive Computing and Related Work ................................................................... 11 2.1. Introduction.................................................................................................................... 11. 2.2. The Evolution of Pervasive Computing......................................................................... 11. 2.3. 2.2.1. Distributed Systems ...........................................................................................12. 2.2.2. Mobile Computing .............................................................................................13. 2.2.3. The Pervasive Computing Model ......................................................................14. Pervasive Challenges .....................................................................................................15 2.3.1. Mobility Challenges...........................................................................................15 viii.
(9) 2.4. 2.5. 2.3.2. Device Challenges..............................................................................................17. 2.3.3. Usability Challenges ..........................................................................................17. 2.3.4. Business Challenges...........................................................................................19. 2.3.5. Application Challenges ......................................................................................20. Mobilizing a Successful Application .............................................................................21 2.4.1. The Pervasive Computing Environment ............................................................23. 2.4.2. Specific Application Challenges ........................................................................23. 2.4.3. Mobile Users’ Characteristics ............................................................................24. 2.4.4. Pervasive Computing Device Constraints and Limitations ...............................25. Summary ........................................................................................................................25. CHAPTER THREE............................................................................................................................27 System Design and Implementation ..................................................................................................27 3.1. Introduction....................................................................................................................27. 3.2. System Design and Implementation: MobileCampus....................................................28. 3.3. 3.4. 3.5. 3.2.1. MobileCampus ...................................................................................................28. 3.2.2. The Multimedia Capturing Service....................................................................31. 3.2.3. The Template Management Service...................................................................34. 3.2.4. The File Transfer Service...................................................................................35. 3.2.5. The Template Creation Service..........................................................................38. 3.2.6. The Content Management Service.....................................................................39. 3.2.7. The Internet Service ...........................................................................................40. 3.2.8. Other System Functionality ...............................................................................43. Dynamic Web-Based Multimedia Templates (DWMT) ................................................44 3.3.1. Approaching Templates .....................................................................................44. 3.3.2. Static vs. Dynamic Templates and Device Independence..................................45. 3.3.3. The Translation and Transformation Process.....................................................46. Scenario Demonstrations ...............................................................................................51 3.4.1. Scenario One ......................................................................................................52. 3.4.2. Scenario Two......................................................................................................56. Summary ........................................................................................................................62. CHAPTER FOUR..............................................................................................................................64 Discussion and Evaluation .................................................................................................................64 4.1. Introduction....................................................................................................................64. 4.2. Criteria for Evaluation ...................................................................................................64 ix.
(10) 4.3. Limitations .....................................................................................................................67. 4.4. Summary ........................................................................................................................67. CHAPTER FIVE................................................................................................................................69 Conclusions and Future Research ......................................................................................................69 5.1. Research Summary ........................................................................................................69. 5.2. Major Contributions of this Research ............................................................................69. 5.3. Future Research..............................................................................................................70. 5.4. In Closing.......................................................................................................................71. DEFINITION OF TERMS.................................................................................................................72 REFERENCE APPENDIX ................................................................................................................75 APPENDIX I .....................................................................................................................................79 Sample XML Transaction File ...........................................................................................................79 APPENDIX II ....................................................................................................................................80 Sample XSLT Template File ..............................................................................................................80 APPENDIX III...................................................................................................................................83 Sample CSS Device Profile File ........................................................................................................83. x.
(11) LIST OF FIGURES. Figure 1. Overview of pervasive computing .....................................................................................2 Figure 2. The continuing evolution of computing ..........................................................................12 Figure 3. System view of pervasive computing ..............................................................................14 Figure 4. Pervasive computing framework ....................................................................................14 Figure 5. MobileCampus system overview .....................................................................................30 Figure 6. MobileCampus system architecture................................................................................31 Figure 7. The Multimedia Capturing Service ................................................................................32 Figure 8. Multimedia Capturing Service screenshots ...................................................................33 Figure 9. Hardware device components..........................................................................................34 Figure 10. The XML Data Type Declaration..................................................................................34 Figure 11. The Template Management Service ..............................................................................35 Figure 12. The File Transfer Service ...............................................................................................36 Figure 13. File Transfer Service screenshots ..................................................................................37 Figure 14. File Transfer Service Server screenshots......................................................................38 Figure 15. The Template Creation Service .....................................................................................39 Figure 16. The Content Management Service................................................................................40 Figure 17. The Internet Service .......................................................................................................41 Figure 18. The web portal (desktop view) ......................................................................................42 Figure 19. Viewing the violation (device view) ...............................................................................43 Figure 20. The translation and transformation process................................................................47 Figure 21. The translation process ..................................................................................................48 Figure 22. Sample multimedia script file........................................................................................49 Figure 23. Sample XSLT blueprint .................................................................................................50 Figure 24. The transformation or content aggregation process ...................................................51 Figure 25. Scenario One ...................................................................................................................52 Figure 26. The first four steps of the transaction (screenshots)....................................................53 Figure 27. The fifth step of the transaction (screenshots) .............................................................54 Figure 28. Steps six to eight of the transaction (screenshots)........................................................55 Figure 29. The end user steps of the transaction (screenshots) ....................................................56 xi.
(12) Figure 30. Scenario Two ...................................................................................................................57 Figure 31. The first four steps of the transaction (screenshots)....................................................59 Figure 32. The fifth step of the transaction (screenshots) .............................................................59 Figure 33. Steps six and seven of the transaction (screenshots)....................................................61 Figure 34. Steps eight and nine of the transaction (screenshots)..................................................61 Figure 35. The end user steps of the transaction (screenshots) ....................................................62. xii.
(13) LIST OF TABLES. Table 1. A comparison of static and dynamic templates ...............................................................45 Table 2. The first four steps of the transaction ..............................................................................53 Table 3. The fifth step of the transaction........................................................................................54 Table 4. Steps six to eight of the transaction ..................................................................................54 Table 5. The end user steps of the transaction ...............................................................................55 Table 6. The administrator steps of the transaction ......................................................................57 Table 7. The first four steps of the transaction ..............................................................................58 Table 8. The fifth step of the transaction........................................................................................59 Table 9. Steps six to nine of the transaction....................................................................................59 Table 10. The end user steps of the transaction .............................................................................61 Table 11. Summary of evaluation against the application challenges..........................................65. xiii.
(14) CHAPTER ONE Introduction. 1.1. The Mobile Opportunity. Pervasive computing extends the traditional computing infrastructure to a new class of devices, mobilizing itself beyond the desktop PC, enabling delivering of on-demand information wherever, whenever and on any device a user prefers. It is about accessing information, applications, and services — solutions that enable anywhere, any time, access to people, information, and processes over any network [1].. The term, pervasive computing, still means different things to different people. It is often used interchangeably with ubiquitous computing. For some, pervasive computing is about mobile access and the mechanism needed to support a mobile community of nomadic users. For others, it is about smart environments or active spaces, context awareness and the way people use devices interact with their surrounding environments [2]. Pervasive computing encompasses all of these areas, but at its core, it is about three things. First, it is concerned about how people view mobile computing devices and use them within their environments to perform tasks. Second, it is concerned about the way applications are created and deployed to enable such tasks to be performed. And third, it concerns the environment and how it is enhanced by the emergence and ubiquity of new information and functionality.. The vision of pervasive computing from an application-centric perspective, according to Banavar et. 1.
(15) al. and Couloris et al. [2, 3], presumes that a device can be a portal into an application-data space, not a repository of custom software that a user must manage. An application is viewed as something by which a user performs a task, not as software that is written to exploit a device’s capabilities. Furthermore, a computer environment is referred to as an “information-enhanced physical space”, not a virtual environment that exists to store and run software. The need for perceptual information about the environment further differentiates pervasive computing from traditional computing. An overview of the vision of pervasive computing is depicted in Figure 1 [4].. Figure 1. Overview of pervasive computing. Recently, pervasive computing has been maturing from its origins as an academic research area to a technical and commercial reality [2, 8, 15]. Recent hardware developments and advances in location sensors, wireless communications infrastructures and global networking [8] have made this possible. To complement this, we have seen an increase in the number of mobile users [1] as access becomes pervasive. Their ease of use concerns are driving new forms of interaction, the infrastructure is extending to new devices, new devices are demanding access to information-rich applications over high-speed networks and applications are becoming increasingly connected. The diversity of these. 2.
(16) technologies coming together has contributed towards the vision of pervasive computing – anywhere, anytime data access on any device [9].. An increasing amount of electronic information takes place in the form of multimedia – a mixture of animation, images, video, audio and text. As users become more reliant on pervasive computing devices, there will be a growing need to bring multimedia information to these devices [4, 9, 10]. These advances have opened several new challenges, opportunities and perspectives for developing and interacting with pervasive computing applications that allow these devices to effectively access, store and process multimedia information [1, 2, 8,15]. In addition, applications will have a greater awareness of the user context and environment, and thus be able to provide more intelligent services on behalf of the user by exploiting these rich sets of services available within the computing environment, reducing the burden of the user having to direct and interact with applications [11].. It is also becoming obvious that the nature of interactions between users and computers must evolve [11]. The way mobile computing devices and applications are developed, deployed, managed and used today does not meet the expectations of the user community and falls short of the potential for pervasive computing [2]. In the realm of pervasive computing, every aspect of development creates a challenge that is intermittently linked with other challenges that realize the potential and vision of pervasive computing.. 1.2. Motivation. 1.2.1 Challenges for Pervasive Computing and Mobile Users Enterprises and academic institutions are realizing the advantage of mobile computing and are. 3.
(17) beginning to mobilize existing applications and implementing new mobile applications [12]. The proliferation of heterogeneous devices over recent years has spurred the need for increasingly complex applications that demand access to information-rich resources. While such diversity has led to different vendors pursuing different standards, the challenges for pervasive computing remain, essentially the same. These challenges are divided into several categories [1, 8, 13], namely:. z. Mobility challenges;. z. Device challenges;. z. Usability challenges;. z. Business challenges; and. z. Application challenges.. The exploration areas for each of these challenges are vast, but together, they contribute towards and strengthen the vision of pervasive computing. We discuss these challenges in more detail in the following chapter.. When developing, deploying, managing and using applications, we are also concerned about the way mobile users performs tasks as well as the imposed device limitations. Mobile users are identified as having the following characteristics:. z. They are constantly on the move;. z. They have little time and resources at their disposal to perform tasks; and. z. They need to perform tasks with the least amount of time, effort and skill.. Device heterogeneity poses unique constraints and limitations. In particular, we identified the. 4.
(18) following relevant characteristics:. z. Screen size, resolution and color depth. z. Processing power and battery power. z. Other unique device capabilities. From an application-centric view, the successful development and deployment of a pervasive computing application is dependent on primarily two areas. First, how well the system addresses particular application challenges, supports the vision of pervasive computing and enhances the user experience, and second, how well the system assists the user perform tasks efficiently and effectively given the above-mentioned characteristics while considering the device limitations.. 1.2.2 Dynamic Web-Based Multimedia Templates (DWMT) According to Webster’s [14], a template is defined as “a document or file having a preset format, used as a starting point for a particular application so that the format does not have to be recreated each time it is used”. Templates are useful, because they save time and create flexibility and opportunity for end users to customize them according to their preferences.. The focus of this research is on dynamic web-based multimedia templates or DWMT (herewith referred to as templates) for pervasive computing devices. Templates contain a specific set of criteria that describe the structure of the template, the semantic relationships between multimedia elements and rules for customization. The purpose of this research is to propose extending these templates to users of pervasive computing devices as a way of assisting users to create powerful multimedia presentations from their devices, relieving them of intensive task duties and limitations posed by these devices.. 5.
(19) It is believed that the dynamic feature of these templates is particularly suitable for the pervasive computing environment that enables on-demand information. Dynamically assembled templates have several advantages over static-based templates, specifically in terms of managing, integrating and communicating information to constituents in real-time. By implementing dynamic templates we can also address different device specifications and user requests at run-time without having to create several presentations of a single template to support different devices or possible user requests. Section 3.3 will present a detailed explanation on DWMT.. 1.2.3 Features of a Successful Pervasive Computing Application A successful pervasive computing application is perceived as one that addresses the challenges for pervasive computing set out in section 1.2.1. In such an environment, great emphasis is placed on the user and the user tasks rather than on the goals of the application [8]. In summary, a successful pervasive computing application can be considered as one that:. z. Addresses specific application challenges found relevant to the purpose of the application, supports the vision of pervasive computing and enhances the user experience. z. Identifies the characteristics of users that will use such an application and take these into account in the development of the application; and. z. Considers device limitations by working around them to achieve desired outcomes. As a result, in designing and implementing the proposed system, we focus our efforts on addressing the above-mentioned properties of a successful pervasive computing application from an application-centric perspective.. 6.
(20) 1.3. The Problem and it’s Setting. 1.3.1 The Statement of the Problem This study is to design and implement a system that uses dynamic web-based multimedia templates to assist users to create powerful multimedia presentations with the aim of contributing towards the vision of pervasive computing and enhancing the user experience.. 1.3.2 The Statement of the Sub- Problems z. Investigate and identify certain challenges of developing and deploying successful applications in a pervasive computing environment. z. Establish some of the specific criteria from an application-centric viewpoint with particular focus on the application challenges, mobile user characteristics and device limitations; and analyze and study the attributes of related applications considered necessary for the development and deployment of successful pervasive computing applications. z. Design and implement a system that demonstrates the use of dynamic web-based multimedia templates and addresses the criteria for successful pervasive computing applications; Integrate the proposed system with the BestWise International Computing Company Multimedia Visual Authoring Tool [5] with the intention of extending the use of this tool to users of pervasive computing devices. z. Discuss and evaluate how the proposed system’s use of templates and its implementation as a whole contributes to the vision of pervasive computing and enhances the user experience. 7.
(21) 1.4. The Scope of the Research. 1.4.1 Delimitations Currently, there is no major supported open standard supported by vendors developing pervasive computing applications. While the proposed system was developed for the Microsoft Windows CE platform for PDA and Smartphone devices, the concept and goal of the application remains applicable across all development platforms and devices.. The proposed system attempts to conform to open standards wherever possible to support seamless interoperability and platform independence. Templates were developed using XML/XSLT, two open standard technologies supported by all major vendors. Furthermore, the proposed system conforms to standards specified by open standard consortiums such as the World Wide Web Consortium (w3C). However, standards do have some drawbacks, such as limiting some capabilities that could resolve some problems by vendor-specific platforms. The proposed system combines these capabilities by offering integrated customized applications and web content to deliver a rich application and content delivery environment to address the mobile users’ tasks.. Considering all the challenges for pervasive computing is extremely complex and not economically practical. Thus, the proposed system considers an application-centric viewpoint of the specific challenges, characteristics of mobile users and device limitations – this viewpoint is deemed credible for the determination of a successful pervasive computing application – and defines the scope of the computing environment.. 1.4.2 Assumptions It is assumed that the proposed system operates on a pervasive computing infrastructure centered on. 8.
(22) a high-level conceptual model consisting of integrated devices, users, software components and user interfaces.. The proposed system is dependent on Wi-Fi (IEEE 802.11b technology) that guarantees continuous connections wherever and whenever necessary. Network traffic, stability, signal strengths and other hardware issues are not taken into specific account in this study.. 1.5 Research Methodology. In this research, we propose designing and implementing a pervasive computing application, MobileCampus, which demonstrates the use of web-based multimedia presentation templates to assist mobile users perform tasks efficiently and effectively. In addition, we integrate the proposed system with the Multimedia Visual Authoring Tool [5] so that the functionality of this tool is extended to users of pervasive computing devices. The success of the proposed system is evaluated from a qualitative perspective in terms of the set application challenges, mobile user characteristics and device limitations as well as its contribution towards the vision of pervasive computing and enhancing of the user experience.. The rest of study will employ the use of qualitative methods whereby an extensive literature study will contribute to the part of the dissertation. Books, journals, website publications, magazines, newspapers, conference proceedings and other articles will be used to study different perspectives. The research thesis will be covered by an extensive literature review of the identified problem in order to validate the problem. Discussions will be subjective, expressive and flexible and provide a holistic view of the topic.. 9.
(23) The primary mode of communication used to discuss these issues with researchers in the field and professionals will be through e-mail and use of electronic discussion groups. A classification matrix will be used to identify professionals and their perspectives and how their studies or opinions relate to the sub-problems identified.. This study will be discussed and evaluated from an application-centric perspective.. 1.6. Thesis Organization. The organization of this paper is divided into two discrete parts. The first part is concerned with the importance of the challenges for pervasive computing. Chapter Two provides a clear outline of the evolution of pervasive computing and the general challenges associated with the development and deployment of successful pervasive computing applications. It provides a background to the understanding of the thesis. In addition, we emphasize the specific criteria for the successful development and deployment of the proposed system from an application-centric viewpoint and define this as our scope.. The second part of the study is concerned about the design and implementation of the proposed system. Chapter Three describes the proposed system, MobileCampus, in detail. This is followed by a detailed discussion and qualitative evaluation of the system in terms of the specific criteria identified for the successful development and deployment of the proposed system in Chapter Four. Chapter Five concludes the thesis and offers suggestions for future research.. 10.
(24) CHAPTER TWO Challenges for Pervasive Computing and Related Work. 2.1. Introduction. Creating successful pervasive computing applications is dependent on several factors, which we identify as challenges. These challenges do not exist in isolation but together, contribute towards the vision of pervasive computing. This chapter explains the evolution of pervasive computing from its basic beginnings to where it stands today and how it fits into our lives; it also discusses the properties of pervasive computing and how these might apply to the proposed system. Based on this, we identify the general challenges for pervasive computing and explain these in detail. As a result, this chapter forms as a basis for the groundwork towards stressing the specific challenges, characteristics of mobile users and limitations imposed by devices that need to be addressed from an application-centric viewpoint and define the scope of the proposed system.. 2.2. The Evolution of Pervasive Computing. The continuing evolution of computing (Figure 2) has led to an explosion of information collection and access. Pervasive computing defines a major evolutionary step in the work that began in the mid 1970s when the PC first brought computers closer to people [4, 8].. 11.
(25) Figure 2. The continuing evolution of computing. Although the PC has not delivered the full potential of information technology to users, it has certainly taken the first step towards making computers popular (if not pervasive). It has also been an instrumental factor in the phenomenal growth of hardware components and the development of graphical user interfaces as well as the beginnings of distributed systems and mobile computing devices.. In the rest of this section, we try to sort out the complex relationships between distributed systems and mobile computing and develop a taxonomy of issues characterizing each phase of this evolution towards pervasive computing.. 2.2.1 Distributed Systems Networking provided the opportunity for personal computers to evolve into distributed computing. Computers connected by network – whether mobile or static, wired or wireless, sparse or pervasive – offered sharing capabilities [8, 15]. Distributed computing marked the next step towards. 12.
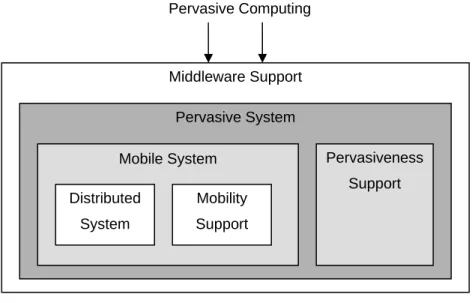
(26) pervasive computing by introducing seamless access to remote information resources and communication with fault tolerance, high availability and security [15]. The advent of the World Wide Web’s networking ubiquity made it an attractive choice for experimenting with distributed computing concepts. The ad-hoc nature of the Web’s growth proved we can distribute computing capabilities in a big way without losing scalability. But, most importantly, the Web pioneered the creation of a nearly ubiquitous information and communications infrastructure creating an essential starting point for pervasive computing.. 2.2.2 Mobile Computing Mobile computing emerged from the integration of cellular technology and the Web [16]. This has extended to wireless networks and different types of devices that operate in these environments. In mobile computing, the basic principles of distributed systems design continued to apply [15], but four key constraints of mobility forced the development of specialized techniques: unpredictable variation of network quality, lowered trust and robustment of mobile elements, limitations on local resources imposed by weight and size constraints, and concern for battery power consumption [17].. Mobile Computing’s goal, according to Saha and Mukherjee [8], of “anytime, anywhere” is essentially a reactive approach to information access but prepares for pervasive computing’s proactive approach. As Figure 3 shows, pervasive computing forms as a superset of mobile computing and an extension of distributed computing. Pervasive systems require support for interoperability, scalability, smartness and invisibility to ensure that users have seamless access to computing whenever they need it.. 13.
(27) Pervasive Computing. Middleware Support Pervasive System Pervasiveness. Mobile System. Support Distributed. Mobility. System. Support. Figure 3. System view of pervasive computing. 2.2.3 The Pervasive Computing Model Technological advances necessary to build a pervasive computing environment fall into four broad areas: devices, networking, middleware and applications. Figure 4 shows the relationships between these areas concerned.. Figure 4. Pervasive computing framework. Pervasive computing addresses these areas in the following way: devices will be heterogeneous, and intelligent; networks will be integrated, middleware will act as an interface between the networking 14.
(28) kernel and end-user applications and the applications will be environment-centric, either web-based or mobile computing or a combination of both [8].. 2.3. Pervasive Challenges. To migrate from a pervasive computing vision to reality, fundamental issues in numerous areas need to be addressed from both technical and non-technical viewpoints. We identified previously in section 1.2.1, five primary categories of challenges that need to be considered when developing and deploying applications in a pervasive computing environment: mobility challenges, device challenges, usability challenges, business challenges, and application challenges. We discuss these in more detail to determine their applicability and emphasize some of the specific challenges found important to the development and deployment of the proposed system, MobileCampus.. 2.3.1 Mobility Challenges Mobility challenges associated with pervasive computing encompass a range of issues that are associated with the nomadic user of pervasive computing devices. These issues are largely hardware related and depend much on the state of the wireless environment, for example, the maintenance of connections as devices move between areas of differing network connectivity, and the handling of network disconnections [11]. While protocols for wireless networking do handle some of the problems associated with mobility, such as routing and handovers, there are some problems that cannot be solved at the network level as they require knowledge of application semantics. According to Henricksen et al. [11], the computing infrastructure needs to co-operate with applications in order to perform tasks related to the device mobility. Some of the mobility challenges are outlined below [4]:. 15.
(29) z. Connection state. As users migrate from location to location, they will not always receive continuous connections. Protocols and the computing infrastructure need to be able to intelligently handle connected, intermittent and disconnected states with applications.. z. Authentication, authorization and security. Wireless environments are often vulnerable to eavesdropping and are considered less secure than their wired counterparts. This makes authentication and access to secure services important.. z. Voice and data access. The ability to access information using different modes of information transfer presents a challenge, not only for enhancing user interaction but also an infrastructure challenge.. z. Device management. Devices in a pervasive computing environment will not only include devices that users will interact directly with such as handheld organizers, mobile phones and traditional PCs, but also include devices such as sensors and actuators that mediate between physical and virtual environments; embedded devices in objects such as watches and shoes; and home and office appliances such as videos, toasters and telephones [11]. These devices will demand a computing infrastructure that can manage them well.. z. Scalability. Scalability is a universal challenge for pervasive computing, both from a hardware and software perspective [4, 11]. As the number of devices increase and decrease and demand services at irregular intervals, the computing infrastructure, the interactions between components and the software services provided must all be scalable. According to Henricksen et al. [11], a powerful software platform would have characteristics such as scalability, fault-tolerance and distributed components. The Ninja service architecture [19] is an example of one such platform.. z. Services. The need for integrated services that communicate with each other to support mobile users is an essential characteristic of pervasive computing. Messaging services, location and. 16.
(30) context awareness (invisibility) as well as intelligent notification are all properties of pervasiveness.. 2.3.2 Device Challenges The heterogeneity in computing systems will not disappear in the future, but instead increase as the range of computing devices widens. Heterogeneous devices will be required to interact seamlessly, despite the varying differences in hardware and software capabilities. This will require an infrastructure that maintains knowledge of device characteristics and capabilities and manages the integration of devices into a coherent system that enables arbitrary interactions [4, 11]. Some of the more specific challenges include:. z. Unique device challenges. Each device creates a new pervasive computing challenge as new devices have unique characteristics and capabilities. Support for existing and future devices presents challenges for developing and deploying pervasive computing applications.. z. Varying programming models. There are several existing programming models, languages and frameworks for developing pervasive computing applications. Currently there are no dominant or major standards for programming models.. z. Wide range of target environments. Varying operating systems and underlying software infrastructures pose integration challenges for deploying universal pervasive computing applications.. 2.3.3 Usability Challenges Pervasive computing presents an increasingly difficult challenge when developing and deploying pervasive computing applications. Many analysts argue that usability is the number one barrier to the successful deployment of pervasive computing applications [20]. Without a simple, intuitive and. 17.
(31) efficient user experience, organizations may end up with huge investments in applications that mobile workers refuse to use. As mentioned earlier, a pervasive computing application is whereby a user performs a task rather than software written to exploit a device’s capabilities [8, 15]. The heterogeneity and the particular characteristics of mobile users make the interaction challenges extremely complex. Demand for ubiquitous access will create a requirement for universal interfaces [11]. Device heterogeneity will introduce a further requirement that user interfaces are highly adaptable. And, the diminishing amount of user interaction with applications and the changing nature of interactions will mandate the creation of new types of user interfaces.. Universal interfaces refer to the creation of generic interfaces that will allow the semantics of user interaction to be specified without reference to rendering or input modalities. Currently, there are attempts to create a special language that meets this challenge, such as MoDAL [21].. Highly adaptable interfaces needed to cope with different user contexts (for example, when a user switches from working in an office to driving a car) are one of the usability challenges for pervasive computing applications. Novel application behaviors are needed to cope with this demand.. User interfaces for pervasive computing must be designed carefully with several factors in mind. First, the ergonomics of the interface must be designed to keep the user’s attention focused on the task at hand rather than on peripheral matters. Second, it should be enjoyable to use. Third, the user interface must allow novel types of interaction that will become more common as computing tasks become more ubiquitous, such as the delegation of tasks and provision of guidance to software agents. And finally, user interfaces should be designed for ordinary people, rather than for technologists [22].. 18.
(32) 2.3.4 Business Challenges Taking advantage of the pervasive computing opportunity means leveraging non-traditional, embedded computing technologies – both wired and wireless – to enable, integrate and extend e-business opportunities and new applications [23]. Improving productivity, developing and applying better cost-management strategies, finding new markets, adding value to existing customer relationships and maintaining competitive advantage in an ever-changing marketplace are all part of the business challenges. While the business challenges aren’t new, circumstances have changed dramatically. One misconception about migrating to pervasive devices as simply screen scraping or content transformation [13], the challenge lies in reconfiguring the business logic necessary to process the workflow of the application.. Pervasive computing has enabled and created a demand for mobile business capabilities. Enterprises are establishing strategies for mobilizing their businesses and integrating them with existing solutions and business partners to maximize returns.. By mobilizing workforces, pervasive computing applications provide several advantages, including less room for error, relaying critical data residing on corporate networks to devices when an immediate decision needs to be made, and delivering information in a time and format that is useful to mobile workforces [23]. By assisting workforces, pervasive computing can help bring valuable productivity gains to the enterprise and adding value to customer relationships.. There are several ways in which pervasive computing can meet the business needs in a mobile environment [12, 23]. There exist several opportunities both in terms of customer and enterprise perspectives.. 19.
(33) 2.3.5 Application Challenges Although all challenges for pervasive computing are linked in one way or another, application challenges remain one of the most important challenges when creating applications for pervasive computing devices. We place great emphasis on specific application challenges in this project, and discuss them in more detail later.. In the area of service platforms in a pervasive computing environment, there are currently studies on adaptation, context awareness, smart environments, scalability, integration and interoperability, invisibility and so forth [8, 9, 11, 23, 24], however, on the specific challenges for pervasive computing applications, the following issues are relevant [4, 9, 20, 24]:. z. Automation. The idea of doing more by doing less is achieved through three things [24]: new technologies should be brought into our lives, not vice versa; new technologies must increase human productivity; and integrating technologies so that they become ubiquitous and require minimal intervention. A thin client approach supports this vision – by minimizing the client’s functionality and providing support within the network at servers [15, 25]. Client thickness is usually determined by the worst-case environmental conditions under which the application must run satisfactorily. For example, a very thin client suffices if one can always count on a high bandwidth, low latency wireless communication to nearby computing infrastructure and batteries that can be recharged or replaced easily [15]. On the other hand, thin client approaches, from a usability perspective, can assist users with their tasks by transferring processing of data to back-end systems and hiding system complexity. This optimizes the user experience by allowing the user to do less to achieve more.. z. Content aggregation. In a pervasive computing environment that enables on-demand information, content aggregation offers aggregating of disparate data dynamically from. 20.
(34) different sources or services and converting it to a single presentation for the users’ pervasive computing device. z. Customization and personalization. Customization and personalization solve individual user preferences adds value to the overall user experience.. z. Multi-device capability. An impedance mismatch is apparent between devices in terms of capability and support. Supporting existing and future devices is a challenge for any pervasive computing application. Applications should be able to handle multi-device profiles.. z. Web content and custom applications. Combining the use of both types empowers users with a rich application and content delivery environment. This provides rich context information that is gathered from a wide range or sources, interpreted, and disseminated in a scalable fashion to end users [11].. z. Integration of services. Integration across heterogeneous protocols and services should be seamless and unnoticeable to the user.. 2.4. Mobilizing a Successful Application. Creating successful pervasive computing applications is always a possibility, however, special attention needs to be paid on how such applications might adapt and be effective in a particular pervasive computing environment [9]. One can argue with the notion that mobile devices will always be one order of magnitude weaker than their desktop counterparts. As a result, any application expected to run on pervasive computing devices has to account for smaller screen sizes, lower processing power, smaller storage and memory capacity and lower network bandwidth [9]. Clearly, there is a need for alternative thinking how applications can be architected to provide reasonable levels of responsiveness despite the device hardware limitations.. 21.
(35) In the previous chapter, we discussed the aspects of pervasive computing environments and how they differed compared to traditional computing environments. What is important to note at this stage is that while pervasive computing devices will almost never achieve the power of their desktop counterparts, they cannot be compared directly because their environment of use, purpose of use, and approach is altogether different. We approach our problem by exploiting these limitations and taking advantage of alternatives to achieve the reasonable results from a pervasive computing perspective.. There have already been several successful commercially deployed pervasive computing applications, such as at National Express [26], The Waterbury Police Department [27], Lotte Sam Kang [28], Kudos Restaurant [29] and Enning GmbH [30]. In the previous chapter, we identified three specific criteria that we identified as necessary for the development of successful pervasive computing applications within a particular computing environment; a successful pervasive computing application is considered as one that:. z. Addresses specific application challenges found relevant to the purpose of the application, supports the vision of pervasive computing and enhances the user experience. z. Identifies the characteristics of users that will use such an application and take these into account in the development of the application; and. z. Considers device limitations by working around them to achieve desired outcomes. In the following sub-sections we attempt to discuss the relevant properties of successful pervasive computing applications and define the scope of the proposed system.. 22.
(36) 2.4.1 The Pervasive Computing Environment The pervasive computing environment extends beyond the traditional networked environment to utilize wireless technologies such as IEEE 802.11, CDMA, GPRS, GSM and so forth. Such an environment addresses the goal of providing “anytime, anywhere” information access by decoupling users from devices and viewing applications as entities that perform tasks on behalf of users. There are a number of ongoing projects in this area that focus on holistic pervasive computing environments, including PIMA [2], Carnegie-Mellon University’s Aura project [31], The University of Washington’s Portolano project [32], HP’s CoolTown project [33], MIT’s Project Oxygen [34], The University of California at Berkeley’s Endeavour project [35] and IBM’s Websphere Anyplace project [36].. Most of these projects focus their efforts on creating a platform or environment in which pervasive computing applications might adapt and excel. Other efforts include infrastructure issues, dynamic service discovery, device independent models and so forth.. Due to the extensive and complicated process of setting up a pervasive computing environment, the proposed system will not focus on the network or hardware infrastructure, but rather, as mentioned in the previous chapter, approach the problem from an application-centric perspective and assume such an environment.. 2.4.2 Specific Application Challenges In Section 2.3.5, we identified the application challenges that we found necessary to the development and deployment of successful pervasive computing applications. We focus our efforts on these challenges:. 23.
(37) z. Automation;. z. Content aggregation;. z. Customization and personalization;. z. Multi-device capability;. z. Web content and custom applications; and. z. Integration of services.. The proposed system will address each of these application challenges in an attempt to support the vision of pervasive computing from an application-centric perspective. Each of these challenges will be discussed in greater detail in the concluding chapters and will be critically evaluated to identify particular contributions and limitations.. 2.4.3 Mobile Users’ Characteristics Usability is an expansive topic in pervasive computing. While it is a research topic on its own, it does not exist in isolation and needs to be considered when developing and deploying pervasive computing applications. In the previous chapter, we identified the characteristics of mobile users and earlier discussed the usability challenges. In a pervasive computing environment, great importance is placed on the user, how users perform tasks [2] and how results are achieved. We define our target users have the following characteristics:. z. They are constantly on the move;. z. They have little time and resources at their disposal to perform tasks; and. z. They need to perform tasks with the least amount of time, effort and skill.. While there are several usability aspects concerned with the development of such applications, the. 24.
(38) proposed system is particularly focused on how the users perform tasks and enhance the user experience rather than on other aspects associated with usability. In the development of the proposed system, we hope to address these characteristics.. 2.4.4 Pervasive Computing Device Constraints and Limitations In addition to considering how users perform tasks, we also need to consider the devices they use and how we can exploit each device constraints and limitations to maximize user efficiency while maintaining a reasonable computing performance. We address the following device limitations:. z. Screen size, resolution and color depth. z. Processing power and battery power. z. Other unique device capabilities. 2.5. Summary. This chapter presented an overview of the evolution of pervasive computing which provided insight into the realm of developing applications for such an environment. Challenges facing the development and deployment of pervasive computing applications were identified and discussed in detail. It is understood these challenges do not exist in isolation and by taking into account and addressing these challenges presents opportunity for successful development and deployment of applications in a pervasive computing environment. This chapter provided a foundation and understanding about the context of pervasive computing in which we outlined criteria (application challenges, characteristics of the mobile user and the limitations imposed by devices) considered important for the success of the proposed system.. 25.
(39) The following chapter introduces and discusses, in detail, the proposed system, MobileCampus.. 26.
(40) CHAPTER THREE System Design and Implementation. 3.1. Introduction. The previous chapter introduced background to the evolution of pervasive computing and the concept of a successful pervasive computing application. As a result, specific criteria were determined from an application-centric viewpoint that needs to be considered for the proposed system to be successful. It defined the scope for the system deployment as well as the foundation for evaluation.. This chapter introduces the proposed system, MobileCampus. While the proposed system is conceived to be application for general multimedia data applications, MobileCampus is a specific demonstration of the applicability of the system in such an environment. MobileCampus is discussed in great detail from a high and low level viewpoint to provide a holistic view of the system from various perspectives. The translation and transformation process of templates explain how we integrate MobileCampus with the Multimedia Visual Authoring Tool and deliver these templates to users of pervasive computing devices. To demonstrate the practicability of the application in such an environment, we present two scenarios that fully exploit the functionality of MobileCampus.. 27.
(41) 3.2. System Design and Implementation: MobileCampus. 3.2.1 MobileCampus In this research, we design and implement a system that uses dynamic web-based multimedia templates to assist users to create powerful multimedia presentations from their pervasive computing devices. The use of this application is not limited and can be conceived to be applicable for general multimedia data applications. MobileCampus is a traffic incident management system that demonstrates the use of templates and how they might assist mobile users and enhance the user experience while considering device limitations.. Business Situation In a university, parking is often an ongoing day-to-day problem because the number of vehicles often exceeds the number of parking places available. In the case of conferences or exhibitions, the problem usually gets worse. Often, vehicles are found to be in the wrong place at the wrong time and officers are not equipped to deal with the situation immediately. One problem is that owners are unable to be contacted at that time causing disruptions in traffic and instability to the traffic situation on campus. Another problem is, even if an officer can produce a ticket and leave it on the car, the owner may only be notified once he or she returns to his or her car in the late evening. In addition, in the case of campus speeding, officers are often in poor positions to deal with such situations. MobileCampus utilizes the university wireless environment by equipping campus officers with mobile devices that interact in this environment and capture necessary information about the traffic violation, for example, parking and speeding on campus, and uploaded this information to a database and make the violation available to violators online. By having a central repository of vehicle registration numbers and owner’s contact details, campus officers can, at anytime and anywhere access such information and inform owners of their violations in real time. In addition, we demonstrate how templates can be used to assist the officer perform tasks efficiently. 28.
(42) and effectively.. MobileCampus is divided into six services that operate dependently and independently of one another:. z. Multimedia Capturing Service. z. Template Management Service. z. File Transfer Service. z. Template Creation Service. z. Content Management Service. z. Internet Service (Web and E-mail). The Multimedia Capturing Service resides on the end users’ client device and incorporates the capturing of multimedia. This service communicates with the File Transfer Service to transfer files and templates between the server and the client device. The File Transfer Service connects to the Template Management Service (and the template library), which handles the template selections, importing of templates and storing of media files from the client device. The Content Management Service is activated when the end user requests to view a presentation. It dynamically assembles the content, data, layout and style to a single presentation using the Internet Service which in turn renders the presentation for the client device. Figure 5 depicts a system overview of MobileCampus and how each of the system’s services relates to each other.. 29.
(43) Figure 5. MobileCampus system overview. Figure 6 presents the system architecture of the proposed system mapped from the system overview and how each service constitutes to the system as a whole and the interactions between end users and system services.. 30.
(44) Figure 6. MobileCampus system architecture. We first describe each of these services in detail and later run through two scenarios to demonstrate the applicability of MobileCampus.. 3.2.2 The Multimedia Capturing Service The Multimedia Capturing Service is client-oriented and works on the pervasive computing device. This service facilitates the capturing of multimedia such as the acquiring of audio, images, text and video on the PDA and compresses them for optimal bandwidth transfer. Figure 7 depicts the process of acquiring multimedia. For this service, the pervasive computing device needs a camera attached to the device in order to acquire images and video. The built-in microphone facilitates the voice recordings and stylus input for text. 31.
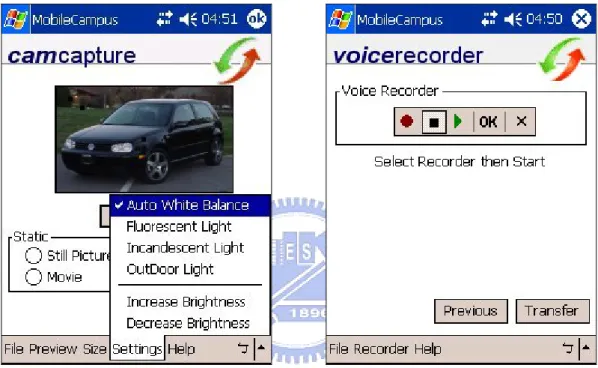
(45) Figure 7. The Multimedia Capturing Service. The user can specify the following resolutions:. z. 640 x 480;. z. 320 x 280; and. z. 160 x 120.. In addition, the user can specify certain lighting and color conditions such as:. z. Auto-white balance;. z. Fluorescent light;. z. Incandescence light;. 32.
(46) z. Outdoor light; and. z. Increase and decrease brightness.. Figure 8 depicts the screenshots of the Multimedia Capturing Service. Its simplistic interface makes it very convenient for users to capture multimedia.. Figure 8. Multimedia Capturing Service screenshots. Figure 9 depicts the hardware components of the device used by the end user. The entire set includes the handheld device [7], the expansion pack and the Veo PhotoTraveler [6], used for capturing multimedia. The built-in voice recorder in the handheld device facilitates the acquiring of audio.. 33.
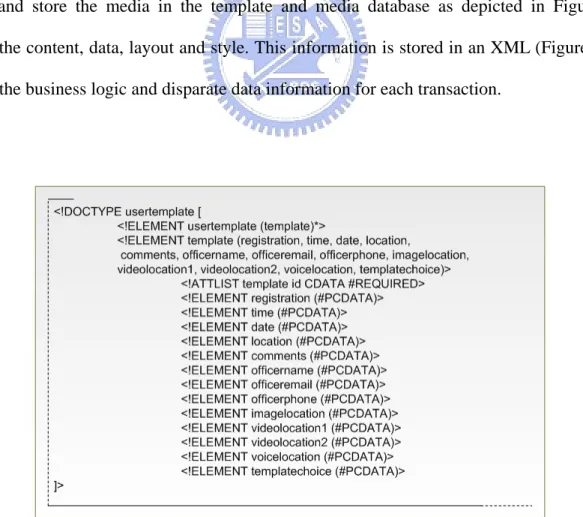
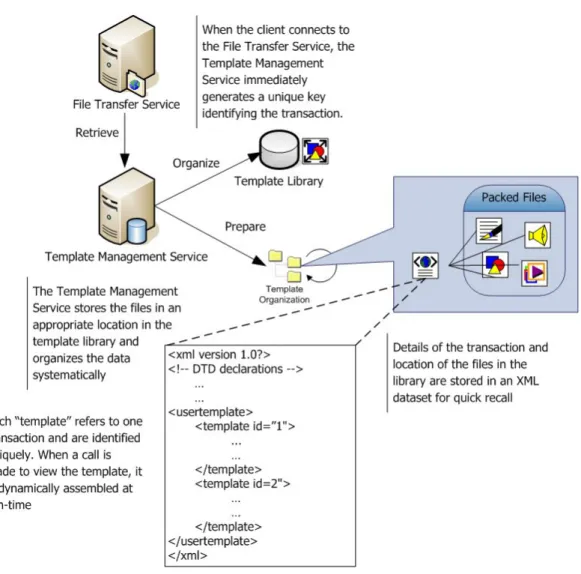
(47) Figure 9. Hardware device components. 3.2.3 The Template Management Service The Template Management Service is called by the File Transfer Service when the files are transferred from the client to server. The purpose of the Template Management Service is to organize and store the media in the template and media database as depicted in Figure 11. It separates the content, data, layout and style. This information is stored in an XML (Figure 10) that describes the business logic and disparate data information for each transaction.. Figure 10. The XML Data Type Declaration 34.
(48) In addition, the Template Management Service encodes video into popular formats such as MPEG-4 [45] and WMV for optimal playback on devices.. Figure 11. The Template Management Service. The Template Management Service also handles the importing of new templates created by the Multimedia Visual Authoring Tool into the template and media library.. 3.2.4 The File Transfer Service The File Transfer Service operates on both the client and server sides over the FTP protocol. The. 35.
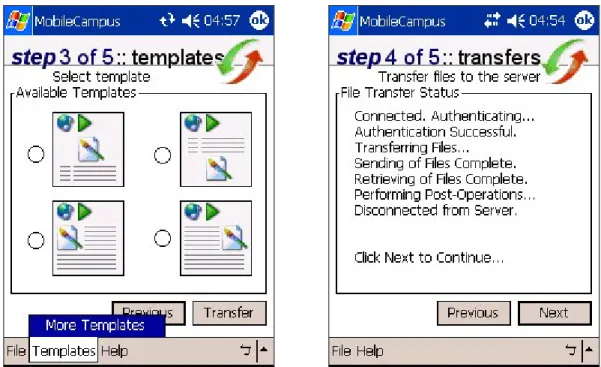
(49) File Transfer Service can handle multiple clients and deals primarily with the user authentication and the transferring of files to and from the server. It also connects to the e-mail server when necessary, for example, if the owner of a vehicle is registered in the database, the owner is e-mailed immediately and notified of the violation. At the same time, the File Transfer Service connects to the Template Management Service to store necessary information about the transaction and organize the transferred files on the server.. Figure 12. The File Transfer Service. In particular, the File Transfer Service is called in the following two situations (Figure 13):. z. When the user wishes to transfer acquired multimedia to the server. z. When the user wishes to access on-demand templates and preview them. 36.
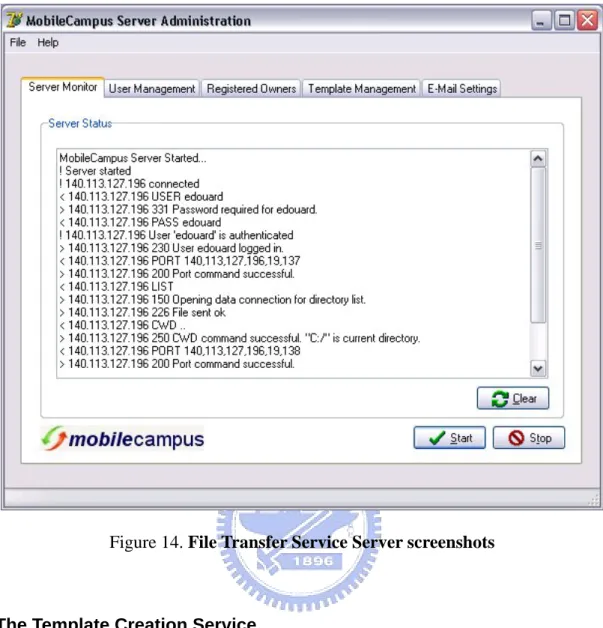
(50) Figure 13. File Transfer Service screenshots. Figure 14 depicts a screenshot of the transactions on the server side.. 37.
(51) Figure 14. File Transfer Service Server screenshots. 3.2.5 The Template Creation Service The Template Creation Service is directly configured under the Multimedia Visual Authoring Tool. It handles the creation of templates and the translation process from the template specification to XML and XSLT for support on pervasive computing devices. While the Multimedia Visual Authoring Tool has powerful capabilities to create entire multimedia presentations, it is also effective for creating basic templates that can be exported into various formats, including formats supported by pervasive computing devices, in this case XSLT.. 38.
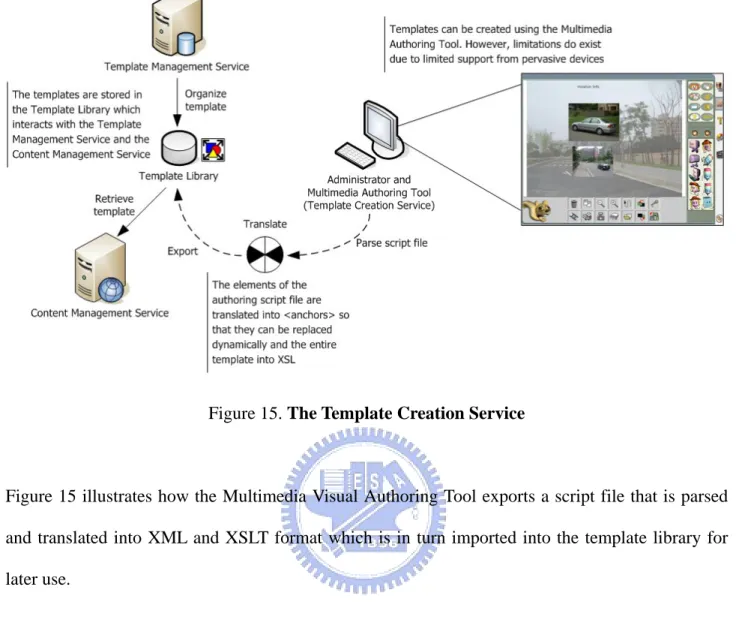
(52) Figure 15. The Template Creation Service. Figure 15 illustrates how the Multimedia Visual Authoring Tool exports a script file that is parsed and translated into XML and XSLT format which is in turn imported into the template library for later use.. 3.2.6 The Content Management Service The Content Management Service is called when a user requests to view the presentation. It dynamically assembles the content, layout, style and data and aggregates the content to present a coherent web presentation to the end user.. 39.
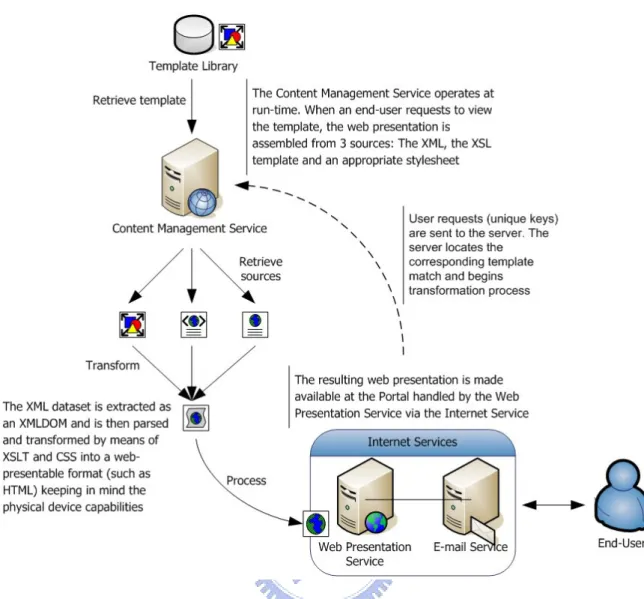
(53) Figure 16. The Content Management Service. Figure 16 illustrates the process of gathering information from disparate data sources and dynamically assembling them at run-time and aggregating the content and rendering it for presentation to the end user.. 3.2.7 The Internet Service The Internet Service consists of both the web presentation service and e-mail service. It works at the presentation layer and renders the final presentation format for end users. The web server acts as a portal and calls the content management service when processing a user request. The file transfer service utilizes the e-mail server when needed to communicate with end users.. 40.
(54) Figure 17. The Internet Service. Figure 17 illustrates the request from the end user to the portal. This request is passed on to the Template Management Service where the presentation is assembled and presented to the end user via the web presentation service.. Figure 18 contains a screenshot of the portal. End users enter the key received through e-mail or written on their violation tickets to view their violation online.. 41.
(55) Figure 18. The web portal (desktop view). Figure 19 illustrates a view of the final presentation using templates from the device perspective.. 42.
(56) Figure 19. Viewing the violation (device view). 3.2.8 Other System Functionality The proposed system contains other general functionality used to manage the system. These include:. z. User Management. User management contains campus officer information as well as authentication information needed to access templates and transfer files.. z. Registered Owner Management. This is the database containing registered vehicle owner information. If the vehicle’s owner is registered in the database, an immediate e-mail notification is sent to the owner to inform him or her that their vehicle has received a violation notice.. z. Template Management. This functionality deals with importing templates from the Multimedia Visual Authoring Tool into the template and media database. It is made available to end users to download and preview.. z. E-Mail Settings. This functionality contains the relevant settings for outgoing e-mail.. 43.
(57) 3.3. Dynamic Web-Based Multimedia Templates (DWMT). In Chapter One, we briefly discussed DWMT as the focus of this research and how it could be used to assist users to create powerful multimedia presentations from their devices. In this section, we will discuss, in detail, our approach to dynamic web-based multimedia templates and how they might assist users and address device limitations, the advantages and disadvantages of static and dynamic templates, and finally the translation and transformation process.. 3.3.1 Approaching Templates In this study, we propose using templates as a method of assisting users and addressing device limitations. Templates are particularly useful because they provide a starting point and create options for the user to create powerful multimedia presentations without needing much effort, knowledge or skills about multimedia presentations. In addition, the dynamic approach of creating templates helps address device limitations such as screen size and supported color depth. Templates contain a specific set of criteria that describe the structure of the template, the semantic relationships between multimedia elements and rules for customization. In this study, templates have the following properties:. z. They are dynamic;. z. They are web-based; and. z. They support multimedia. Templates are dynamic because it was found that dynamically assembled templates are better suited. 44.
數據

相關文件
The min-max and the max-min k-split problem are defined similarly except that the objectives are to minimize the maximum subgraph, and to maximize the minimum subgraph respectively..
Mount Davis Service Reservoir Tentative cavern site.. Norway – Water
Although the research of problem-based learning (PBL) and the integration of PBL and Zuvio IRS in Japanese pedagogy are trending, no related research has been found in Japanese
The share of India & Taiwan in the World economy and discussed how world export-import market is increasing year by year.. The data shows us that the business between these
Therefore, the focus of this research is to study the market structure of the tire companies in Taiwan rubber industry, discuss the issues of manufacturing, marketing and
(英文) In this research, we will propose an automatic music genre classification approach based on long-term modulation spectral analysis on the static and dynamic information of
First we explain how to implement CMOS current-mode quadratic circuits and design the proposed circuit in the way of multiple corrections.. We use the best
The purpose of this study is to analyze the status of the emerging fraudulent crime and to conduct a survey research through empirical questionnaires, based on